More About Signatures
“Explain to me again what a signature actually is. Because when I sign a file, the output seems to be encrypted, not just signed,” says Bob as the conversation turns back to cryptography. Though Sam’s earlier comments about Alice bother him, Bob knows better than to let it get to him, at least not yet.
“One thing to remember,” says Sam, “GnuPG gives you three ways to sign, and two of those produce what looks like encrypted output.”
5.1 “Decrypting” a Digital Signature
Sam says: “Consider GnuPG’s roots as a tool for facilitating communication in the early Internet, and it’s obvious why GnuPG compresses output. That’s what you did when generating files transmitted over a network back in 1991 or so, because networks were slower back then1. The compressed file looks as if it’s ciphertext, but it’s just compressed--and easily uncompressed into plaintext that a human can recognize or an application program can open.” Sam pauses, and says, “Decrypt a signed file, and GnuPG extracts the original file--and lets you know it was signed, though it can only verify the signature if you’ve got the signer’s public key. See?”
![]()
“This is a typical GnuPG behavior: it looks as if nothing happened, maybe even an error that prevented anything from happening. But the gpg: messages tell me testing.txt.gpg was signed by someone whose key I don’t have, so the signature can’t be checked. I can still extract the plaintext (use the --output option to save a file) by commanding GnuPG to decrypt. The output file testing.txt holds the ‘decrypted’ plaintext that GnuPG uncompressed from the original ‘ciphertext’ file.”
5.2 More About Signatures
Sam explains: “When signing, the first thing GnuPG calculates is the signature itself, on the original data. Next, it compresses the data along with the signature. So if you have a text file with 1,000 lines repeating the same message (‘this is a test’), your plaintext file will be 16,000 bytes but the signed output file will only be a few hundred bytes. That’s because right after signing, GnuPG compresses the whole thing (original data file+signature data).”
Sam continues: “The signature is done on the original plaintext, because that is what is being signed--the signature is meant to be proof that the public key owner created or approved the data being signed. Compression is done after that, so if the signed file will also be encrypted there is less to encrypt. If it’s not encrypted, the compressed file is still easier to handle (less data to download or process).”
“If you wanted to, you could probably have GnuPG encrypt something and then sign it, but that’s not usually a good idea. Signing before encrypting means the signature is also encrypted, keeping details about the source of the data (who signed it) private. If you compress after encrypting, the file, which will already be mostly random-seeming data, won’t compress very much if at all.”
Bob asks, “But that seems to make things difficult--what about signing a message in e-mail? Is there some way to sign something without turning it into ciphertext?”
“Yes, and that’s why there are three different types of GnuPG signatures,” says Sam, “not just one or two.”
5.3 Digital Signature Types
“When signing data, GnuPG takes input (a file or chunk of text) as a single unit, then signs it. That is, it generates a hash on the data to be signed and then generates the digital signature, and then adds the signature to a copy of the original data. It’s like wrapping a package: you can’t see the inside without taking the wrapping paper off. After generating the signature, GnuPG takes the signed data, plus the signature, and compresses it. That’s like taking the wrapped package and putting it inside another box. And then, GnuPG takes the signed and compressed data, and encrypts it--like taking the whole thing and putting it inside a locked container.”
Sam continues: “The default type of signature is called an attached signature, and the ‘signature’ is actually a file (or block of data) that contains the cryptographic data generated when signing the plaintext plus the plaintext. This is what you get when you use the basic GnuPG command gpg --sign.”
“The only way to get any data out of the signature itself is to ‘verify’ the file--but that is done by extracting the plaintext after verifying the signature, and extracting the compressed data prior to verifying. And you can verify two ways, first, with the gpg --verify command, which reports back on whether the signature is good or not (or with an error if the file being verified isn’t recognized as a signed file). Second, GnuPG will verify as well as decrypt the file if you use the gpg --decrypt command.”
“As you say, Bob, this is a pain: the obvious difficulty is that a signed plaintext file becomes a file that is, if not encrypted, no longer accessible as plaintext. You must extract the plaintext before you can see what’s been signed.”
Sam continues: “Two problems with default GnuPG signatures are, first, how to validate downloaded files without forcing all downloaders to extract the desired file from a signature file. The second is how to generate ASCII-armored output to include signed plaintexts in e-mails or other text-oriented applications.”
“Wrapping plaintext with the signature means that the signed file, if it’s a program or application data, has to be extracted to be used, and thus is no longer the ‘same’ file as signed2.” Sam pushes his plate away and goes on:
“So, three types of signatures are supported in GnuPG: clearsigned signatures, detached signatures, and attached signatures. To generate ASCII-armored output, without any compression, use gpg --clearsign. For example, I can clearsign a quick message to my mom3, and it will look like this:”
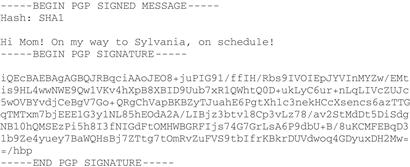
“I can copy that whole thing into an e-mail message, or even take a picture of it and send the picture--as long as the whole thing is entered back into GnuPG and verified.” Sam says, “My mother doesn’t have to verify the text to read it, but if she wants to be certain it was I who sent it, she can verify it at her leisure.”
“With detached signatures you can access plaintext without verification, but more often used to sign downloaded files, especially software. For example, when you download GnuPG, you download a separate signature file. If you’re not worried about integrity of the program, you can use it without verification--or if you are worried, you can use the detached signature to verify the file without changing the downloaded file4. This is how to do a detached signature on a file”:

“It’s a typical GnuPG command: --detach-sign (abbreviated as -b). GnuPG signs the thing after the command (in this case, the file linuxdistro.iso, though it could also be a block of text you enter interactively5), and outputs to a file called linuxdistro.iso.sig (default: the signed filename plus .sig).”
Sam continues: “GnuPG generates the detached signature, but instead of writing it out as GnuPG output file (which implies compression, by the way), GnuPG writes signature data into a small separate file. You can’t authenticate the signature without both the original file and the .sig file. To verify the detached signature, put both files in the same directory and use the --verify command”:
![]()
“Could I use the --decrypt command too?” asks Bob.
“Yes, but if you’re not sure what’s in a GnuPG file6, just run GnuPG without specifying a command; for more information about what happens, use the -v (verbose) option,” says Sam, “and add v’s for more verbosity (e.g., -vvv).”
“OK,” Bob says, “Now, tell me about verifying the different kinds of signatures.”
5.4 Signing and Verifying, Summarized
“I have been giving examples along the way, but here it is all in one place,” replies Sam as he hands Bob a printed page, “And for good measure, also a summary of how to sign things.”
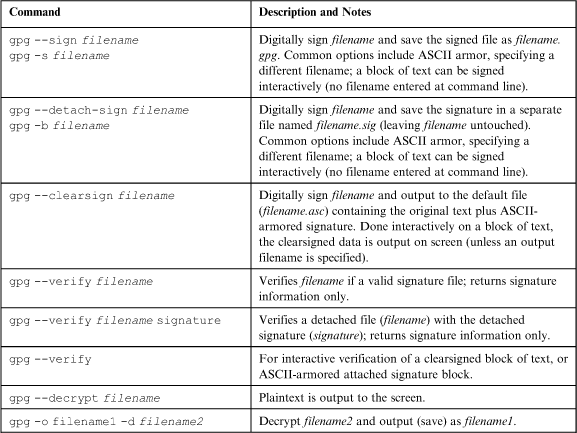
Note: Default filenames are noted above, but signatures and plaintext can be written to nondefault filenames using the--output filename option.
5.4.1 Verifying a Digitally Signed File (Attached Signature)
Sam says, “Most digital signatures I see are digitally signed text blocks in e-mail or newsgroups, and digitally signed downloaded files with detached signatures—but the simplest to verify is a digitally signed file with attached signature.”
“An attached digital signature may make verification easier, but it also makes verification mandatory to use the file or data. Detached signatures (for files) or ASCII armoring (for text messages) allow the files or data to be used without verification.” Sam goes on, “To verify an attached digital signature, you can use the raw GnuPG command, and it should verify and write a plaintext file”:
![]()
“GnuPG identifies that the file specified in the command, example.txt.gpg, contains a signature for a file called example.txt; that file is automatically extracted into the same directory as the signature file.” Sam continues: “To verify the file without extracting it”:
![]()
“and to output the file to a different filename from the original”:
![]()
“And by the way, Bob, that was an adorable message you sent to your wife,” Sam says, watching Bob carefully.
Bob, looking surprised, says, “I would have e-mailed her from the airport, but I was preoccupied, so I thought it would be alright. Is it a problem? She expects always to be notified when I board my flight. I did not think you would mind.”
Satisfied with Bob’s response, Sam says, “No problem--your message arrives soon in Eve’s mailbox. I like cats, too. Will she actually bring Walter to the airport?”
“She might, Sam; if she does you will find him to be quite adorable,” answers Bob. “You are monitoring my Internet activity through your wi-fi hotspot, correct? It means I cannot keep my data private from you, I suppose.”
“You suppose correctly, Bob,” says Sam, “You know, ‘Trust, but verify’.”
“I will be very careful in that regard, then, Sam,” says Bob as he nods, to himself.
5.5 Review Questions
1. What are the three different types of GnuPG digital signatures? Why are there different types?
2. What does GnuPG do when a filename is listed and no command is specified?
3. When signing and encrypting, in what order are things done? What about compression? Is it always that way?
4. What are three filename extensions that identify a file as being output from GnuPG?
1Actually, it’s more to do with bandwidth, which is the carrying capacity of a network, but the point being that smaller files are easier to send over any network, and require less storage, so compression is a standard function for many networking tools.
2The extracted plaintext file’s contents will be the same as the original plaintext, but the file’s metadata (e.g., the date it was created) will be different. It’s a minor issue, but still an issue.
3Sam uses the command gpg --clearsign and enters his message interactively. The output shown is displayed on the terminal screen, and can be copied and pasted into a message.
4You should verify all downloads, especially if the download relates to security.
5Not something you would do often; to do it, use gpg -ab, save the block of text into a file (e.g., example.txt), and paste the resulting ASCII-armored signature into a file too (e.g., example.txt.sig). There are other ways to do this using the --output option.
6GnuPG files are identified by their extensions; most common are: *.asc for ASCII-armored output, *.gpg for binary output ciphertext, and *.sig for detached signatures.
