Authentication is the process of determining if someone is in fact who he says he is. There are several different types of authentication technologies. For example, in computer networks, typically authentication is done by the use of logon passwords. However, passwords can be stolen or accidentally revealed. For this reason, there is a more stringent authentication process. For example, digital certificates issued and verified by a certificate authority (CA) as part of a public key infrastructure (PKI) provides stronger authentication on the Internet.
The following sections discuss in more detail authentication technologies—such as Transport Layer Security (TLS), certificates, NTLM and Kerberos—that are used by Office Communications Server.
You can configure TLS and certificates within your Office Communications Server 2007 deployment. Using TLS and certificates has the following benefits:
Confidentiality Data that is transferred between clients and servers needs to be encrypted to prevent its exposure over public Internet links.
Mutual Server authentication Servers need a way to verify the identity of each other during communication.
Office Communications Server 2007 uses certificates for the following purposes:
TLS connections between client and server
Mutual transport layer security (MTLS) connections between servers
Federation between partners
Remote access
Note
Certificates are discussed in more detail in Chapter 3.
Transport Layer Security (TLS) is a protocol that ensures privacy between communicating applications and their users on the Internet. TLS ensures that no third party can eavesdrop or tamper with any message between the client and the server.
As described in RFC 2246, TLS is composed of two layers: the TLS Record Protocol and the TLS Handshake Protocol. The TLS Record Protocol provides connection security with some encryption method, such as the Data Encryption Standard (DES). The TLS Record Protocol can also be used without encryption. The TLS Handshake Protocol allows the server and client to authenticate each other and to negotiate an encryption algorithm and cryptographic keys before data is exchanged.
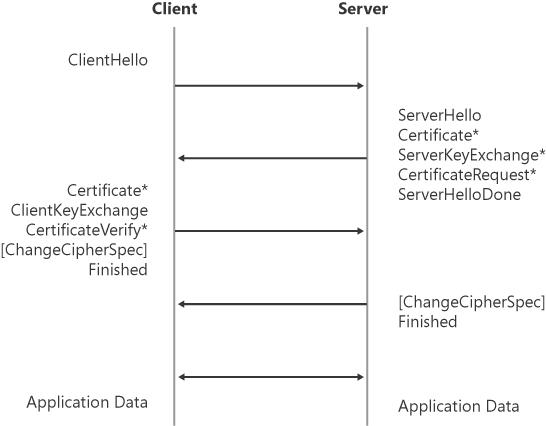
Figure 18-8 is an example of the call flow of a TLS handshake over the network as described in RFC 2246.
Note
In Figure 18-8 an asterisk (*) indicates optional or situation-dependent messages that are not always sent.
The TLS Handshake Protocol as described in RFC 2246 involves the following steps:
Exchange hello messages to agree on algorithms, exchange random values, and check for session resumption.
Exchange the necessary cryptographic parameters to allow the client and server to agree on a premaster secret.
Exchange certificates and cryptographic information to allow the client and server to authenticate themselves.
Generate a master secret from the premaster secret and exchanged random values.
Allow the client and server to verify that their peer has calculated the same security parameters and that the handshake occurred without tampering by an attacker.
The client sends a client hello message to which the server responds with a server hello message. The client hello and server hello are used to establish security enhancement capabilities between client and server. The client hello and server hello establish the following attributes: Protocol Version, Session ID, Cipher Suite, and Compression Method. Additionally, two random values are generated and exchanged: ClientHello.random and ServerHello.random.
The actual key exchange uses up to four messages: the server certificate, server key exchange, client certificate, and client key exchange. New key exchange methods can be created by specifying a format for these messages and defining the use of the messages to allow the client and server to agree upon a shared secret. This secret should be long. Currently defined key exchange methods exchange secrets that range from 48 to 128 bytes in length.
Following the hello messages, the server sends its certificate if it needs to be authenticated. Additionally, a server key exchange message might be sent if it is required. If the server is authenticated, it might request a certificate from the client, depending on the cipher suite selected. The server then sends the server hello done message, which indicates that the hello-message phase of the handshake is complete. The server then waits for a client response. If the server has sent a certificate request message, the client must send the certificate message. The client key exchange message is now sent, and the content of that message depends on the public key algorithm selected between the client hello and the server hello. If the client has sent a certificate with signing ability, a digitally-signed certificate verify message is sent to explicitly verify the certificate.
At this point, a change cipher spec message is sent by the client, and the client copies the pending Cipher Spec into the current Cipher Spec. The client then immediately sends the finished message under the new algorithms, keys, and secrets. In response, the server sends its own change cipher spec message, transfers the pending Cipher Spec to the current Cipher Spec, and sends its finished message under the new Cipher Spec. At this point, the handshake is complete and the client and server can begin to exchange application layer data.
TLS connections are recycled every 24 hours between servers. Similarly, idle TLS connections are recycled every 15 minutes.
Note
For more information on how to adjust the cipher suites and the key exchange algorithms, see http://support.microsoft.com/kb/216482 and http://support.microsoft.com/kb/245030.
There are two enterprise user authentication mechanisms supported in Office Communications Server: NTLM and Kerberos. Anonymous conference participants are authenticated using Digest authentication.
NT Lan Manager (NTLM) is a Microsoft authentication protocol that is the successor of Microsoft Lan Manager (LANMAN). NTLM is a challenge/response authentication protocol. NTLM was followed by NTLM v2, the strongest authentication protocol of these three. NTLM v2 is a cryptographically strengthened replacement for NTLM v1.
Kerberos is a considerably more secure authentication protocol than NTLM v2. Kerberos provides mutual authentication as opposed to only client authentication. With NTLM, the client is challenged to provide credentials, but the client could be providing credentials to a bogus server. Kerberos, on the other hand, provides server authentication in addition to the client authentication. Unlike NTLM, Kerberos makes use of a trusted third party, called a Key Distribution Center (KDC), which maintains a database of secret keys. These secret keys are known only by the KDC, as well as by the client and the server. Knowledge of these keys prove the client or server identity.
Where possible, the client should always try to use the most secure authentication mechanism. However, when the client is accessing the server via an external network, the server will offer only NTLM v2 authentication because the client will be unable to assess the internal KDC or Active Directory.
The Direct from the Source: How NTLM and Kerberos Work in SIP sidebar describes in more detail the process of authentication using NTLM and Kerberos.
In the event that problems occur while signing into Office Communications Server 2007, a "401" response might be sent back even though users have provided valid sign-in credentials. This can occur if you have configured Office Communications Server 2007 to use Kerberos authentication and one of the following is true:
NetBIOS is disabled on the computer.
The computer is running Microsoft Windows XP Home Edition.
The computer is configured to run behind an Internet Connection Sharing device or behind another Universal Plug and Play (UPnP) Network Address Translation (NAT) device.
The computer is not joined to the same domain as the Office Communications Server computer.
The account is disabled, or time-based restrictions apply to the account login.
In certain Office Communications Server topologies, you cannot successfully sign in by entering your credentials in the user principal name (UPN) format ([email protected]). Additionally, you might have to specify the FQDN together with your user name when you enter it in Universal Naming Convention (UNC) format to successfully sign in. For example, when you type your user name information into a dialog box, you might have to use the following format to successfully sign in:
domain.example.comusername
In this format, domain.example.com is the FQDN of your domain, and username is your user name. If entering the FQDN of your domain does not work, try enabling NTLM instead of Kerberos.
NTLM version 1 was used in legacy operating systems such as Windows NT and Windows 98. Recent improvements in computer hardware and software algorithms have made these protocols vulnerable to widely published attacks for obtaining user passwords. In its ongoing efforts to deliver more secure products to its customers, Microsoft has developed an enhancement, called NTLM version 2, that significantly improves both the authentication and session security mechanisms. You can enable NTLM version 2 on these legacy operating systems, thereby preventing the weaker NTLM version 1 from being used. For more information on how to enable NTLM version 2, see http://support.microsoft.com/kb/239869.