CHAPTER 4 The Basic Information Security Model
Overview
This chapter introduces the basic framework used to implement information security. This framework consists of four elements – assets, vulnerabilities, threats, and controls. We define each of these terms, provide examples for each, and describe how they are related to each other. At the end of this chapter, you should know:
- The elements of the basic information security model
- The relationships between the elements of the basic information security model
- The common classification of information security controls
Introduction
The previous chapters have highlighted the importance of information security. In most organizations, system administrators take on the bulk of the responsibilities of maintaining information security. In anticipation of your continued interest in information security, these chapters have therefore also introduced you to the basic tasks performed by system administrators and the skills required to complete these tasks. In subsequent chapters, you will continue to build on these technical skills.
Information security is a very wide subject area because most information security incidents exploit some new weakness in an organization. Maintaining information security therefore requires attention to almost every aspect of the organization. To provide structure to these efforts, it is useful to organize all the activities associated with maintaining information security into a framework or model. In this book, we call this framework the basic information security model. It is shown in Figure 4.1.
Components of the basic information security model
A model is a representation of the real world. Models are useful in drawing attention to the essential elements of a problem. A model for information security includes the core components of information security, shows the relationship of these components to each other, and excludes everything else. The basic information security model we use in this book is shown in Figure 4.1. The model has four components – (1) assets, (2) vulnerabilities, (3) threats, and (4) controls. Every activity related to information security falls into one of these components.
Assets
At the center of the figure are assets. In the context of information security, an asset is defined as a resource or information that is to be protected. All security scenarios, whether related to information security or simply related to securing one's home, start with an asset that is considered valuable enough for you to put forth special efforts on protecting it from harm. Information security is no different. If some information or related resource is valuable to the organization, the organization needs to put forth special effort to secure the information.
There are, however, two important differences between conventional assets and information assets – invisibility and duplicability. In most security scenarios that you are likely to be familiar with, the items to be protected can be seen and felt. For example, you lock your cars to prevent theft. You install home alarm systems to prevent break-ins into your home. In both cases, the assets are visible to the naked eye. The damage is also visible. If someone breaks into your car or home, the damage is immediately visible. If there are closed-circuit cameras in the vicinity, they will capture the act of vandalism.
But information security is different. The assets in information security are not tangible artifacts that can be seen and felt. Instead, they are data and information stored as 0s and 1s on computers, tapes, phones, and other devices. While the hard drives and other devices are themselves visible, the valuable data stored on these devices is invisible. If the data is stolen over the network, the transfer of data is not visible to cameras or other conventional security devices. The thieves will typically operate from another country, thousands of miles away, safe from the scrutiny of conventional security agencies.
The second important difference between conventional assets and information assets is duplicability. Continuing with the car example, if your car is stolen, you will notice the missing car in the morning. This is because the car can only exist in one place at any given time. However, information can be duplicated perfectly. If your data is stolen, you will not notice the theft until it is brought to your notice. For example, if someone finds your laptop unattended, emails a copy of your assignment to himself and submits the copied assignment as his own work, you will have no idea of the act of plagiarism if the instructor does not bring it to your notice.
These two differences between conventional assets and information assets – invisibility and duplicability – make information security a considerably different challenge than conventional security. Conventional security methods such as locks and guards are not very effective at maintaining information security. For example, conventional locks will do little to prevent the theft of data over the network. A stolen conventional asset such as gold can be recovered and restored to its owner. But stolen data may be copied to a hundred locations and even if a few of these copies are destroyed, it is almost impossible to deny the thief the benefit of having access to the data. Information security controls therefore have to try to prevent the theft in the first place, and detect and block thefts as they occur through constant monitoring.
Gold has been the standard measure for value for centuries. Accordingly, to denote the value of information, information assets are shown in our basic model (Figure 4.1) as gold bars (though for many organizations, the information in their possession may actually be more valuable than gold!).
In the most common scenario you will encounter, the information assets are stored in an IT system. Paper-based systems simply cannot provide the density of information storage required by modern organizations. An IT system is defined as an assembly of computer hardware, software and firmware, configured for the purpose of processing, storing or forwarding information. In a small family-owned business, this IT system may be as simple as an Excel spreadsheet. In a slightly larger business, the IT system may be dedicated software such as QuickBooks and in the largest businesses, the IT system would be an enterprise application such as an ERP system. The IT system is shown in Figure 4.1 as the bucket holding the assets.
Vulnerabilities
Information security becomes important because all systems have vulnerabilities. A vulnerability is a weakness in an information system that gives a threat the opportunity to compromise an asset.1 In the case of the Excel-based IT system discussed above, such vulnerabilities include unauthorized access which may cause loss of confidentiality or integrity and hard drive failures which may cause loss of availability. If we reached some state of utopia where no vulnerabilities existed in IT systems, we would not have to study information security and would not need a cadre of professionals dedicated to information security. However, modern software products are large. For example, Windows Vista had around 50 million lines of code.2 It is difficult to anticipate and eliminate all possible vulnerabilities in such large products. Additional vulnerabilities are created in the interactions between products. Even if all software vulnerabilities are eradicated, user-created vulnerabilities can remain. For example, many users do not protect their administrative accounts with good passwords.
Considering the spreadsheet based small-business accounting system described above, what in your opinion is its greatest information security vulnerability?
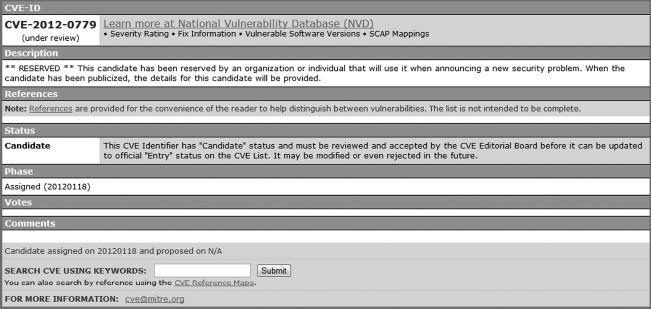
To deal with vulnerabilities, the software industry in collaboration with the federal government has invested considerable resources to create an inventory of known software vulnerabilities. This is the Common Vulnerabilities and Exposures (CVE) list. The CVE list aims to provide common names and identifiers for all publicly known software vulnerabilities. The list is maintained by Mitre, a non-profit federally funded research and development organization. An example vulnerability in the CVE list (the most recent entry at the time of this writing) is shown in Figure 4.2.3
FIGURE 4.3 NVD entry4 for the CVE listing
While the community is interested in being alerted to vulnerabilities, most users are more interested in learning about the likely impacts of vulnerabilities and recommended measures to remove the vulnerability. This information is maintained in a parallel effort called the National Vulnerabilities Database (NVD). You can see the link from the CVE listing to the NVD entry in Figure 4.2. Figure 4.3 shows the NVD entry corresponding to the listing in Figure 4.2.
Some features of the above entry are notable. The vulnerability was added to the database after it was announced on the web. The announcement was made by the vendor of the software. More information about the vulnerability could be found at the vendor's website by following the link on the CVE listing. The CVE list and NVD database are not whistleblowers. They essentially act as a central repository of all vulnerabilities reported publicly, and the vulnerability is often first reported by the vendor of the software itself.
Given the large number of software products in use and the increasing size of modern software, it should not be surprising that the NVD database is very active. As of May 2012, it was averaging 11 reported vulnerabilities per day. On May 4, apart from the vulnerability reported above, there were vulnerabilities reported by VMWare and IBM. All eight vulnerabilities reported that day were first announced by the vendor firms themselves.
Further, each year, the industry publishes the top 25 most dangerous software errors from this database.5 This publication is exhaustive and for the convenience of developers, it provides code samples and suggested solutions for each of the identified vulnerabilities. Code samples from this publication are used later in this chapter.
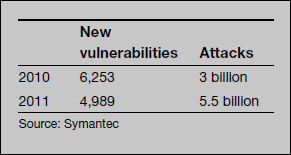
The efforts by the industry seem to be paying off. According to Symantec, the company that develops many popular information security products, 4,989 new vulnerabilities were discovered in 2011 compared to 6,253 in 2010, a drop of about 20%.6,7
Threats
The vulnerability of an asset creates threats. A threat is defined as the capabilities, intentions and attack methods of adversaries to exploit or cause harm to assets. In the Excel example, a worker may want to exploit the lack of password protection on the file and modify their hourly rate. These threats are shown in the framework of Figure 4.1 as arrows.
The nature of threats has changed dramatically in recent years. In the early days of the Internet, the threats were mostly pranks such as those perpetrated by the gang of 414's. In the early 2000s, these threats became more disruptive (e.g., the ILOVEYOU virus) and widespread. The software industry and user community responded by reducing software vulnerabilities and improving user training. As of 2011, trends indicate that the remaining threats are highly directed and commercially driven.
A popular tool developed by the industry to visualize the important threats facing organizations is ATLAS.8 ATLAS uses sensors deployed at ISPs around the world to gather real-time information about threats being faced by organizations. This information is then processed and displayed on the web. System administrators can quickly identify the dominant attacks and ensure that they have the necessary defenses in place to counter these attacks. The ATLAS web interface is shown in Figure 4.4.
Symantec released its threat report for 2011 in April 2012. The company's products blocked 5.5 billion attacks in 2011, compared to 3 billion attacks in 2010, an increase of over 80%. Therefore paradoxically, while software is becoming more and more secure and the number of vulnerabilities is decreasing, the number of attacks is increasing.
This paradox has been facilitated by the industrialization of the “attack industry.” Integrated development environments (IDEs) and toolkits have emerged (e.g., Zeus, Spyeye) to help attackers quickly create new attacks and to exploit existing vulnerabilities more efficiently. Less expertise is needed to create successful attacks using these toolkits than using first principles, so threats are becoming accessible to a wider population to exploit. This may explain to some extent the rise in attacks driven by political motivations. This is the information security environment we live in today.
FIGURE 4.4 ATLAS web interface. This information was obtained from Arbor Networks' ATLAS Initiative on May 12, 2012 and permission to republish has been obtained. ATLAS initiative data is dynamic and therefore, the information may have changed since the date of publication of the data.
© Arbor Networks, Inc. ALL RIGHTS RESERVED. Atlas is a trademark of Arbor Networks, Inc.
Controls
All IT systems will be vulnerable for the foreseeable future. Also in this timeframe, there will be dedicated attackers threatening to exploit these vulnerabilities for personal gain or other motives. What does a system administrator do to defend the computers in his charge?
What in your opinion, is your best defense against the vulnerability you identified in the spreadsheet-based accounting system?
The role of information security is to minimize the impact of these threats. This is done by deploying security controls around the vulnerable IT system. Security controls are safeguards used to minimize the impact of threats. In our framework of Figure 4.1, these controls are shown as the ring around the IT system. In Figure 4.1 the width of the arrows indicate the relative frequencies of the different categories of threats seen by a typical organization. Most threats are blocked by the controls commonly adopted by organizations. For example, most operating systems now come with a firewall configured with some default settings and encourage users to use a strong password to secure the administrative user account on their computers. Commercially, even the smallest businesses backup their important files on external hard drives or other Internet services and keep their computers locked to prevent unauthorized access.
Even rudimentary controls such as those listed above can successfully block a large majority of the threats facing organizations. These are shown by the wide arrow at the bottom of Figure 4.1.
However as shown in Figure 4.1, even the best security controls have holes. For example, users often prefer memorable passwords over secure passwords. They are also often irregular in backing up their data even if they have spent hundreds or thousands of dollars to purchase backup systems. Threats exploit these weaknesses in security controls to reach the vulnerable IT systems. These threats are shown by the arrow on the right, which has breached the controls and reached the IT system. Fortunately, many of these threats may yet do no harm, as shown by the inability of the arrow on the right of Figure 4.1 to reach the IT system.
Returning to our Excel-based IT system, one such threat is a theft of the laptop in which the business keeps its records. In many such cases, the thieves are just interested in selling the laptop for money, and the buyer may simply reinstall the operating system on the machine for performance. In this case, while the information was vulnerable to the threat of being stolen, no compromise on confidentiality was eventually done. If the firm had good backups, there will also be no loss of availability.
A very small fraction of the threats will cause real damage to the organization. These threats will succeed in getting past any security controls and exploiting vulnerabilities to compromise the information of interest. These threats are shown by the arrow at the top of Figure 4.1. An example in our Excel-based system would be an employee being able to reach the laptop when the manager is not around and successfully manipulate the number of hours worked to increase his compensation.
The information security profession revolves around systematically identifying the information assets, vulnerabilities, threats, and controls and deploying controls appropriately so that the money spent on these controls delivers the greatest possible benefits to the organization. The rest of this book focuses on each of these components in detail. The rest of this chapter surveys the important vulnerabilities, threats, and controls. It may be seen as an exercise in building your vocabulary on information security.
The popular literature on information security often uses the words “vulnerability,” “threat,” and “risk” interchangeably. This is unfortunate. Risks involve both a potential for loss and a measure of the loss if the loss in fact occurs. Vulnerabilities are related to the first half of risk – they create a potential for loss. Threats are related to the second half of risk – if successful, threats can lead to losses. Managers are interested in mitigating risk. Threats and vulnerabilities become risks only when they put valuable information assets at risk.
An example is “A taxonomy of operational cyber security risks” from the SEI at CMU. The risks identified in the document such as “actions of people,” would generally be classified as vulnerabilities.9
In our spreadsheet-based accounting system for example, a risk may be the inability of the business to repay business loans due to manipulation of data on an unprotected computer by a disgruntled employee. The vulnerability in this example is the unprotected computer and the threat is the disgruntled employee.
We cover risk management in detail in Chapter 14. In that chapter, we will write a few risk statements to clearly distinguish between the three. It is hoped that readers of this book will distinguish between “vulnerabilities,” “threats,” and “risks” and use the correct terms as appropriate.
Common vulnerabilities, threats, and controls
As we proceed through the chapters, we will look at the important information security controls in more detail. At this time, it is useful to introduce the most common vulnerabilities, threats, and controls so that you can start thinking about the different dimensions of the information security challenge.
Vulnerabilities
Vulnerabilities are exploitable weaknesses in information systems. Innumerable vulnerabilities exist and new ones are being discovered every day. A convenient way to understand these vulnerabilities is to classify them in some manner. In fact, many vulnerability classification systems exist. For example, one system classifies vulnerabilities based on the stage at which they are introduced in the software development life cycle (SDLC). Another set of classification schemes organizes vulnerabilities based on the threats they create. Unfortunately, all these classification schemes suffer from one weakness or the other. For example, a weakness of the SDLC-based systems is that in large systems, it is difficult to precisely identify the stage at which a vulnerability was introduced. A weakness of the threat-enumeration systems is that the classification mechanism is necessarily incomplete because new kinds of threats are discovered all the time.10
For our purposes, we should find it convenient to broadly classify vulnerabilities into software vulnerabilities and procedural vulnerabilities.
Software vulnerabilities
A software vulnerability is an error in the specification, development or configuration of software such that its execution can violate the security policy.11 Some of the most common software vulnerabilities include the following.
Lack of input validation: The input validation vulnerability refers to a situation where user input is used in the software without confirming its validity. A common use of software, particularly web software, is to access data from databases. Examples include retrieving lists of movies at sites such as sonypictures.com, or webpage text from content management systems (CMS) at sites such as PBS Frontline and HB Gary, a computer security firm, providing expert solutions for several government agencies. Users of these sites typically use the search box or other user input fields to specify their information needs, and the software running the site processes this user input to generate the appropriate response. If the user input is not properly validated, users can access information they were not supposed to get access to. A source code example is given below. In this example, the software uses a simple SQL query to return items matching a username and itemname. If the user input is not validated for correctness, the user can obtain all items in the items table.12
query = “SELECT * FROM items WHERE itemname = ‘“ + ItemName.Text + ”’”; // expected user input for ItemName: pencil; // actual user input for ItemName: pencil OR ‘a’=‘a’; // query result is: SELECT * FROM items WHERE itemname = pencils OR ‘a’=‘a’; // which translates to: SELECT * FROM items;
A common factor among the sites listed here (PBS Frontline, HB Gary Federal, and Sony Pictures) is that they were compromised in embarrassing fashion in 2011 due to improper input validation in their web software.
The specific form of the input validation vulnerability shown in the example above is called the SQL injection vulnerability. The SQL injection vulnerability refers to the use of unvalidated SQL input in applications.
Unrestricted uploads: The unrestricted uploads vulnerability occurs when files are accepted by software without verifying that the file follows strict specifications. For example, many e-commerce websites encourage users to upload photographs of their use of products sold by the website. If these sites do not check that the uploaded photographs are indeed .jpg or .gif or other similar file formats, it is possible for an attacker to upload software programs to the site instead of images. These programs may then attempt to compromise the site, for example, by stealing usernames and passwords.
To prevent such attacks from taking place, it is recommended that all files uploaded by users should be treated as malicious and all such files should be searched for malicious code. This search is not trivial since some file types (e.g., .gif files) have comment fields that may be used by attackers to hide malicious code.
Cross-site scripting: The cross-site scripting vulnerability occurs when user-supplied input is used without verification as part of the output served to other users. The vulnerability gets its name because the most common way in which it is exploited is by attackers getting their victims, who are browsing on one website, to supply malicious JavaScript code (scripting) as input to another, targeted website (cross-site). The following example from the top 25 software errors database demonstrates the vulnerability.
Consider a simple webpage written in php as follows:
$username = $_GET[‘username’]; echo ‘<div class=“header”> Welcome, ’ . $username . ‘<div>’;
This intention of this page is to gather the user's name from a web form on the previous page or a URL ending in “?username = John” to create a welcome message such as “Welcome, John” for the user. However, an attacker can enter some scripting code in the username textfield:
http://trustedSite.example.com/welcome.php?username=<Script Language=“Javascript”> alert (“You've been attacked!”); <Script>
This will display an alert dialog to the user. To have the same dialog box displayed to another user, the attacker can send an email to the victim with the appropriate URL. When the victim clicks on the email, the alert dialog will be displayed to the victim.
The above example is innocuous. However, a real attacker can exploit this vulnerability to get victims to activate more damaging scripts. Cross-site scripting is one of the most common vulnerabilities of web applications, so much so that it has an abbreviation of its own – XSS. This vulnerability has been present in one form or the other on most of the popular websites, including such well-known names as Facebook, Barracuda Spam Firewall, Mediawiki (the software behind Wikipedia), etc.
Buffer overflow: The buffer overflow vulnerability refers to the situation where a program puts more data into a storage location than it can hold. This is one of the most common software vulnerabilities. Normally, such a situation should only lead to a software crash. However, an attacker with detailed knowledge of the program can inject custom-created input such that the overflowed contents compromise the computer in predictable ways. The compromise usually allows the attacker to connect to the computer remotely and steal information.
Buffer overflows are common in programs written in unmanaged languages such as C and C++. Managed languages such as Java and C# manage memory and data such that buffer overflows are not possible in programs written in these languages. However, most software programs (including modern browsers such as Chrome and Firefox) are written in C/C++ for cross-platform compatibility.13 Therefore, eliminating buffer overflows in most modern applications requires extremely careful programming practices.
Missing authorization: The missing authorization vulnerability happens when a software program allows users access to privileged parts of the program without verifying the credentials of the user. Attackers are always trying to find parts of financial information systems that they can reach without credentials. If such a part is found, it is likely to be exploited to steal financially sensitive information. Many large data thefts are indeed the result of a missing authorization vulnerability. For example, according to the “top 25 dangerous errors” publication, hundreds of thousands of bank accounts were compromised in May 2011 at Citigroup as a result of a missing authorization vulnerability.
Unencrypted data: An unencrypted data vulnerability occurs when sensitive data is stored locally or transmitted over a network without proper encryption. Sensitive data includes user credentials and other private information. Unencrypted data flowing over a network can be read easily using software called sniffers. Unencrypted data stored in a database can be stolen if missing authorization or unvalidated input allows users to read the data. Unencrypted data is often an element of major data thefts.
Procedural vulnerabilities
A procedural vulnerability is a weakness in an organization's operational methods, which can be exploited to violate the security policy. Procedural vulnerabilities can compromise information even if all software vulnerabilities have been removed. The most important kinds of procedural vulnerabilities are the following.
Password procedures: The standard procedure used to minimize the impact of many software vulnerabilities including “missing authorization,” “invalid input,” and “unrestricted uploads” is password protection. Users are required to create passwords that are known only to themselves and to provide these passwords before they are allowed to access sensitive information. However, these passwords may not provide adequate security if the organization is not careful about its password procedures.
For example, if passwords are very short (e.g., “abcd”), easily guessable (e.g., “password” or “admin”), use words found in the dictionary (e.g., “computer”), or use parts of user information (e.g., “john”), they do not provide much protection. Attackers usually try various combinations of these passwords when challenged to provide a password.
Password tips
Using good passwords is also advisable in personal life. Tips for good passwords include:14
- Length: Use at least eight characters.
- Complexity: Use numbers, letters, symbols, and punctuations. Long and complex passwords are difficult to compromise.
- Variation: Change passwords regularly so that even if a password is compromised, the vulnerability is eventually removed.
- Variety: Use a different password for every site. At the very least, use two passwords – one for sensitive sites (e.g., banks, online stores) and another for web forums, chat rooms, and other less-sensitive sites. Attackers commonly steal credentials from these less-sensitive sites (which are often less carefully developed) and try them on sensitive sites such as banks and online stores. For an interesting and detailed account of one such incident, read the experience of James Fallows, a national correspondent for The Atlantic magazine and a former speechwriter for President Jimmy Carter.15
Since this is such a widespread concern, most software vendors allow system administrators to specify password procedures to prevent the use of weak passwords.
Training procedures: As software gets increasingly secure, attackers are sharpening their focus on the gullibility of end users. They may send emails that appear to arrive from the organization's chief executive, but which in fact use XSS (cross-site scripting) and other methods to get user credentials. These credentials can then be used to bypass password protections and access sensitive information. At the very least, organizations must make it very clear that they will never send any unsolicited email to users, asking them for their password or other credentials. Such requests will always be made more formally, e.g., by a letter in the mail, or by a memo sent through the organizational hierarchy, etc.
Minimal information security training procedure
Organizations must maintain a policy of never asking employees for sensitive information such as usernames or passwords in an unsolicited email or phone call. Employees at all levels of the organization must know this policy. Employees should know that they can safely trash such emails no matter what the source and no matter what the situation are.
Threats
A discussion of all information security threats could fill an entire book. However, some threats have become famous for the havoc they have created over the years and have earned a place in the information security “Hall of Fame.” As a professional in this field, it is advisable that you be aware of them. These are briefly described below.
Viruses/worms: Most people are familiar with viruses and worms, and most computers sold today come with trial versions of antivirus software. Viruses and worms are computer programs that adversely affect computers and propagate through the network without the user's consent. The difference between the two is that a virus uses other programs (e.g., the user's email client) to spread, whereas the worm can propagate all by itself. Since the authors of worms and viruses know that most users use antivirus software, modern-day worms and viruses are designed to cause all possible damage within minutes of release. For example, the Slammer worm, which was released on Saturday, January 25, 2003, exploited a buffer overflow vulnerability in Microsoft's SQL Server. The vulnerability had been discovered in July 2002 and Microsoft had released an update to patch the vulnerability soon thereafter. Only unpatched hosts were vulnerable and the worm reached 90% of these vulnerable targets in less than 10 minutes,16 infecting at least 75,000 hosts. The interesting story of the ILOVEYOU virus is described in the example case.
Denial of service (DOS): Denial of service is the unauthorized prevention of access to resources or the delaying of time-critical operations. This is usually accomplished by making a large number of unnecessary requests of an information system. The resources of the target system are then preoccupied with responding to these unnecessary requests, which prevents the system from being able to respond to legitimate requests in a timely manner. The impact of a DOS attack can be strengthened by deploying multiple computers to make these unauthorized requests. Such attacks are called distributed denial of service (DDoS) attacks. Distributed denial-of-service (DDoS) is the use of many compromised systems to cause denial of service for users of the targeted system. Fortunately, it is relatively easy to recognize the flood of incoming requests to a single target as a DOS attack and most ISPs can easily block these requests. For an absolutely hilarious but very informative and detailed investigation of a DOS attack, read Steve Gibson's report on the DOS attack against his company.17
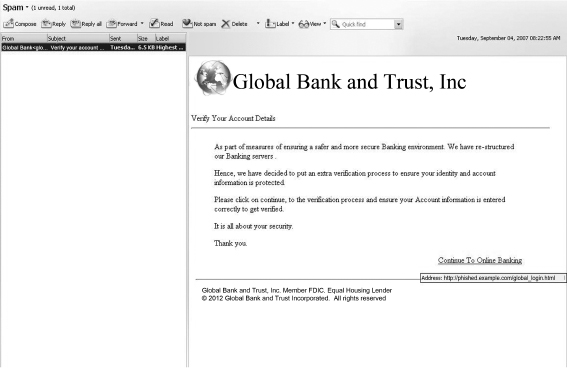
Phishing: Attempting to compromise a user by masquerading as a trustworthy entity in electronic communication is called phishing. Early phishing attacks attempted to acquire information such as usernames, passwords, and credit card details. Most people receive at least one or two of these emails every week. An example is shown in Figure 4.5. The emails appear to originate from banks and lead users to visit a website that looks like the bank's website. At the website, users are asked to provide their username and password in order to make some correction at the bank. While the emails and target website appear to be legitimate, they really aren't. A careful look at the URL will show that the website has been hosted at a compromised server. In Figure 4.5 for example, the website has been hosted at a school district in Alabama.
More recently, phishing is used in combination with social engineering and zero-day exploits to initiate advanced persistent threats. The RSA attack of 2011 discussed with zero-day exploits later in this section is an example.
Malware: Malware (malicious software) is a general term used to describe software or code specifically designed to exploit a computer, or the data it contains, without the user's consent. A very common way for malware to reach computers is via free downloads where the malware author creates a computer software that appears to be very useful and distributes it for free. When unsuspecting users download and install this apparently useful software, the malware is installed along with it. This is called the Trojan horse technique. There are many kinds of malware including key loggers, zombie clients, and root kits. Key loggers track (log) the keys struck on a keyboard, typically trying to gather usernames and passwords. The zombie client is software that takes directions from a remote computer and uses the infected computer to perform malicious tasks as directed. The infected computer is called a zombie. Zombies are usually used to send email spam, launch denial of service attacks, and compromise computers at sensitive installations such as banks and the military. Zombies, or robots (bots), get their name because they blindly comply with instructions from their master.
Rootkits: Rootkits are collections of software programs used to hide the existence of malicious software on computer systems. The term “rootkit” refers to a software toolkit that gives an unauthorized user root access (root is the administrative account on UNIX systems), while hiding the actions of the unauthorized user. Typically, rootkits replace existing system tools (such as those used to list processes (top) and folder contents (ls)) such that the modified versions conceal the existence of the unauthorized user. One of the goals of malware programs is to install a rootkit on the victim machine.
Rootkits are generally used by intruders to hide the existence of other malware such as zombie clients so that the owner of the computer is not even aware that this computer has been compromised and is being used to send spam or launch denial of service attacks.
Of all software threats, rootkits are particularly insidious because of their ability to subvert standard operating system protections. For this reason, it can be almost impossible to remove rootkits from a compromised machine and it may be advisable to completely reinstall the operating system.
Zero-day exploits: A zero-day exploit compromises a previously unknown vulnerability in computer software. The term implies that developers had zero days to address the exploited vulnerability. Though developers are not aware of the vulnerability at the time of the attack, someone is aware of it and has had the opportunity to identify a way to successfully exploit the vulnerability.18
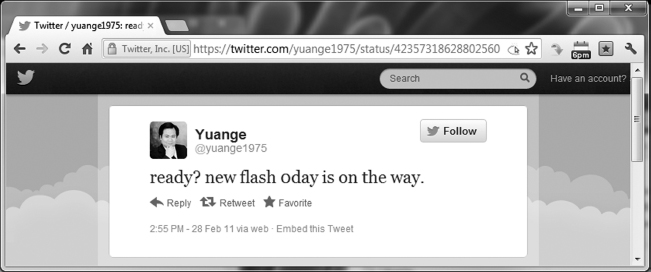
One famous zero-day exploit relates to RSA, one of the leading vendors of SecureID tokens. This technology is used for 2-factor authentication in corporate environments. On March 17, 2011, the company reported that its IT system responsible for generating the tokens had been compromised, potentially compromising the security of its customers. Industry experts believe that the compromise was the result of a zero-day exploit involving Adobe's flash technology.19 Interestingly, 18 days earlier, on February 28, 2011, an attacker with the Twitter handle @yuange1975 had announced the launch of a zero-day Adobe Flash exploit (Figure 4.6), suspected to be the exploit used in the incident.20
Zombies: A zombie is a computer connected to the Internet that has been compromised in such a way that it performs malicious tasks at the direction of a remote controller. Their unquestioning compliance with remote directions gives them the name of zombies. Zombies are sometimes also called bots. The owners of zombie computers are generally unaware of the compromise until they are informed by their system administrators. Botnets are quite affordable. Twenty-four-hour rental rates for 100,000–2,000,000 zombies are approximately $200.21 Zombies are generally used to perform three kinds of activities – send spam, launch denial of service attacks, and perform dictionary attacks to break passwords. The vignette of Oleg Nikolaenko and the Mega-D botnet sheds some light into this world.22
Mega-D botnet
As of 2011, there is a mini-industry around installing Trojan horses on hundreds of thousands of computers and renting the processing capability of these computers to spammers and hackers. The collection of compromised computers is called a botnet. An example is the Mega-D botnet. It was a network of about 500,000 infected zombie computers, which was responsible for sending over 30% of all spam in 2008. The bot net was run by Oleg Nikolaenko, a young Russian national, who was paid $459,000 for his services by Lance Atkinson, a convicted spammer from New Zealand. Oleg was arrested by federal agents at the Bellagio hotel in Las Vegas on November 4, 2010, for violating provisions of the CAN-SPAM Act of 2003.
Packet sniffing: Packet sniffing is the act of intercepting and monitoring data passing through a computer network. Packet sniffing is an important threat to wireless networks because unencrypted data sent through wireless networks may be read easily using freely available software (Wireshark) and standard computer equipment such as a laptop. Attackers are on the lookout for such unencrypted wireless access points at stores and other business establishments to steal user credentials for later exploitation. One of the best-known information security incidents of recent times, the T.J.Maxx incident, was the result of password theft through packet sniffing of an unencrypted wireless access point.
Password guessing: Password guessing is the act of repeatedly trying different passwords associated with a user account until the correct password is found. Sensitive computers are constantly being probed to guess passwords. The attacker tries different passwords until the correct password is found. This attack is so prevalent that most systems ignore repeated failed login attempts originating in quick succession from the same machine. However, occasionally a system administrator may omit the protection leading to compromise. For example, in early 2009, an 18-year-old student ran a password guessing program all-night and discovered that a system administrator at Twitter with username “Crystal” used a password of “happiness.”23 Several other threats related to passwords are discussed later in the book.
In the example above, normally, the system should have found it unusual for a user to try different passwords at the rate of perhaps one new password per second for 8–10 hours. Upon detection, the user should have been blocked. This would be one of the technical controls, discussed in the next section.
Social engineering: Social engineering is the art of manipulating people into performing desired actions. Social engineering exploits the human desire to be helpful and the natural human instinct to be trusting. As the technologies become increasingly secure, social engineering is becoming ever more important to hackers as a way to get into systems of interest.
Social engineering is commonly used to initiate other attacks. Since around 2010, a common mechanism is to send a customized email to a small group of unsuspecting victims, usually at modest levels of the organizational hierarchy. The emails contain attachments containing zero-day exploits. When any user opens the attachment, the exploit installs some kind of scanning software on the victim's computer. This software passes on information to a remote controller and can also act in response to commands received from the controller. The RSA attack of March 2011 followed this methodology.
Advanced persistent threat (APT): An advanced persistent threat is a sustained, human intensive attack that leverages the full range of computer intrusion techniques. APTs are designed to breach organizations even when they are protected by well-designed and well-maintained information security controls. For this reason, APTs require a high degree of target-specific customization, which usually implies that a well-funded group of attackers is responsible for the threat. Since no two APTs are alike, the term APT generally refers to the team behind the attack rather than the attack itself. The most common goal of an APT is to use the attack to obtain and maintain a foothold within the organization for ongoing use and control.
Figure 4.7 is a plot of the usage frequency in April 2011 of two popular vulnerabilities commonly used in APTs. Both are vulnerabilities in MS Word, highlighting the fact that vulnerabilities in popular software are particularly dangerous. The vulnerability discovered in 2010 continued to be used a year after being announced, demonstrating the fondness of attackers to use time-tested exploits and the widespread slackness in applying updates. Figure 4.7 also demonstrates the swift adoption of new exploits, indicating the importance of quick application of updates.24
Controls
Information security controls are the safeguards used to minimize the impacts of information security threats. In modern IT systems, implementing appropriate and cost-effective controls is one of the most important tasks of a system administrator. The rest of this book is almost exclusively devoted to describing the various controls and their uses. This section provides a quick overview of the different controls available.
As in the case of vulnerabilities, there are many popular schemes used to classify the various controls available. One scheme, popular in the industry, is to classify controls as physical, procedural, and technical.
Physical controls: Physical controls use traditional non-technical methods of preventing harm. Typically, they prevent unauthorized users from being able to enter technical facilities. Examples of such controls include locks, fire extinguishers, background checks, and doors.
Procedural controls: Procedural controls are prescribed plans of action that govern the use of computer resources. Procedural controls follow two established principles of security:
- Enforce personal accountability: When people know that they are liable for their actions, and that actions can be traced back to them, they are generally vigilant about their actions.
- Require cooperation of more than one person to commit a fraud: “When thieves fall out honest men get their dues.”25 Experience suggests that there is usually a fallout over the spoils of crime, and the right procedural controls can use this human weakness to enhance security. This is the rationale for the standard accounting procedure of double-entry book-keeping.
Examples of procedural controls include the procedures for obtaining computer accounts, procedures for escalating privileges, procedures for modifying programs, procedures for hiring, and requirements that users change their passwords periodically.
As organizations get larger and larger and the core information technologies become increasingly secure, the primary challenge for information security is to ensure that the most important weaknesses have been eliminated from the organization. The most effective way to do this is to develop effective procedures and then to consistently apply these procedures. On a day-to-day basis, therefore, information security professionals are most focused on procedural controls.
Technical controls: Technical controls are the security measures built into the information system itself. Common examples include passwords, firewalls, intrusion detection systems, system updates, and antivirus software. The rest of this book largely focuses on these technical controls in detail.
Most information security controls straddle multiple categories. For example, passwords may be seen as either procedural controls (procedure to access resources) or technical controls (controls built into the information technology itself). In sensitive industries (e.g., banking), most employees are required to go through extensive background checks. These checks could be considered as physical (non-technical and designed to control physical access) or procedural (procedures followed to control access) controls.
This is one of the weaknesses of most classification schemes in the information security domain – many items can easily fall into multiple categories.
Example case–ILOVEYOU virus
On May 5, 2000, many users received strange emails from people they knew. The subject lines of the emails were “ILOVEYOU.” The emails contained a virus. If users opened the emails, the virus corrupted image files on the hard disk and sent itself as an email to users in the victim's contact list. Given the interesting subject line, the email has also entered the information security folklore as the “love bug” virus. The virus affected an estimated 50 million computers worldwide.
The legal follow up to the virus was interesting and highlights the limitations of law enforcement in dealing with cybercrimes. The FBI quickly identified Manila, Philippines, as the source of the virus and a recent college student, Onel de Guzman, as the author of the virus. However, virus dissemination was not a crime in the Philippines at the time. Therefore, De Guzman could neither be prosecuted in the Philippines nor be extradited to the United States for prosecution under US laws for the act of creating the virus.
Under heavy international pressure, De Guzman was charged with theft and credit card fraud in June 2000. However, on August 21, 2000, all charges were dismissed for lack of evidence.
Philippines eventually created a law criminalizing virus dissemination, but it is relatively weak. The maximum punishment is 2 weeks imprisonment and a fine equivalent to $100.
REFERENCES
Arnold, W. “Philippines to drop charges on e-mail virus,” New York Times, August 22, 2000
Brenner, S.W. “Cybercrime jurisdiction,” Crime, Law and Social Change, 2006, 46: 189 – 206
SUMMARY
This chapter described the essential information security environment and described the four components of the environment – the information assets, system vulnerabilities, threats, and security controls. Prominent examples of each of these components highlighted the issues you are likely to confront in your careers.
In this and the previous chapters, you have been introduced to the important issues faced by organizations and systems administrators. You have also been introduced to some basic technical skills to perform common system administration tasks. The remaining chapters in this book focus on helping you apply these technical skills to implement the common technical controls.
CHAPTER REVIEW QUESTIONS
- Briefly describe the information security model shown in Figure 4.1.
- What is an information asset? Give some examples from your personal life (it is enough to list some categories of assets, please do not violate your own privacy while responding to questions).
- What are some important differences between conventional assets (e.g., gold, real estate) and information assets? How do these differences impact information security?
- What are vulnerabilities? List some vulnerabilities to the assets identified in question 2.
- What is the National Vulnerability Database (NVD)? Why is it useful?
- What is the latest vulnerability recorded by the NVD? (to answer this question, visit the NVD at http://nvd.nist.gov/, click on the link to the “vulnerability search engine” and click “search,” leaving default values in all fields.)
- What are threats? List some threats to the assets identified to the assets identified in question 2
- Visit the ATLAS threat index site (atlas.arbor.net as of 05/21/12). What is the top attack on the day of your visit?
- What are controls? What are some important controls you can implement to minimize the impact of the threats in the previous question.
- Briefly describe the “lack of input validation” vulnerability. Why is it dangerous?
- Briefly describe the “unrestricted upload” vulnerability. What harms can this vulnerability cause?
- Briefly describe the “buffer overflow” vulnerability.
- Briefly describe the “missing authorization” vulnerability. In what industries is this vulnerability particularly harmful?
- What are procedural vulnerabilities?
- What are the recommendations for creating good passwords?
- What are viruses and worms? What is the primary difference between them?
- Provide a brief summary of the ILOVEYOU virus and its impacts.
- What is phishing?
- What is malware?
- What are rootkits? Why are they dangerous?
- What are zombies? What are they commonly used for?
- What is social engineering? Why is it an increasingly important threat?
- What are physical controls? Why are they important?
- What are procedural controls? Why are they important?
- What are technical controls? Give some examples of technical controls.
EXAMPLE CASE QUESTIONS
- What was de Guzman's motivation for releasing the ILOVEYOU virus?
- What is the penalty for creating and/or disseminating a virus in your country?
- Laws typically allow judges considerable latitude in awarding sentences based on the facts of the case. Based on your response to question 2 above, what penalty would you award de Guzman?
- Why did you choose this penalty?
HANDS-ON ACTIVITY–WEB SERVER SECURITY
As part of a website redesign at Sunshine State University, a directory search application was developed. It allows any-one to search for Sunshine State students, staff, and faculty names and email addresses. Before the website is released to the public, you have been asked to work with the team evaluating the security.
- Using the Linux virtual machine you configured in Chapter 2, open a web browser by clicking on the Firefox icon in the bar at the top of the screen (Figure 4.8).
- In the address bar, type in http://www.sunshine.edu/directory
- In the First Name field, type in william and click Submit.
- Click the “Back” button to return to the search screen.
- Type the following into the First Name field:
william!’ OR ‘a’= 'a
QUESTIONS
- How many search results were returned in the first search?
- Are there more search results after changing the input?
- Write a brief (one to two paragraphs) summary of your findings that could be presented to the administration of Sunshine State University. Make sure to include:
- What vulnerability or vulnerabilities this application suffers from?
- Reasons that you feel this vulnerability is present.
- Possible harm that could come from this vulnerability.
CRITICAL THINKING EXERCISE–THE INTERNET, “AMERICAN VALUES,” AND SECURITY
In conventional thinking, one of the big reasons for our information security problems is that the designers of the Internet did not build security in the underlying Internet technologies such as TCP and IP. If only TCP and IP also incorporated security, we would have a much more secure information infrastructure.
However, writing for the IEEE Security and Privacy magazine in 2011, Dan Geer, Chief Information Security officer for In-Q-Tel, a non-profit venture capital firm for technologies that support the CIA, stated that the developers of the Internet embedded their interpretations of “American values” in the underlying Internet technologies. This is why IP, the Internet technology that transfers data across the Internet, is “open, non-hierarchical, and self-organizing.” Once the data leaves your computer, you have no control over how it is delivered to the destination. The protocol provides no mechanisms for governments to impose restrictions on the flow of information on the Internet, other than restricting user access to the Internet. Dan suggests that the Internet may also be a very successful American cultural export, bringing openness and freedom of information wherever it is adopted.
Adopting this view, Dan believes that the lack of security in the underlying Internet protocols is a strength, not a weakness. The Internet requires end users to take responsibility for their own security, instead of relying on security provided by the fabric of the Internet. An Internet that does not take responsibility for security also does not restrict any user from connecting to any other user, protecting the users’ rights to freedom of association. A secure Internet could curtail this freedom in the name of security, requiring permission from the Internet provider for access to a desired resource.
Reference
Geer, D.E. Jr. “A time for choosing,” IEEE Security and Privacy, January/ February 2011, 96–95
CRITICAL THINKING QUESTIONS
- How could our information infrastructure been more secure if the underlying Internet incorporated security technologies such as encryption?
- How could the usability of the Internet been crippled if the underlying Internet technologies had incorporated more security?
- Based on your responses to these two questions, do you agree with Dan Geer's assessment that leaving security to be the responsibility of end users is a good idea?
DESIGN CASE
The MIS Department of the Sunshine University asked you to drop by for a visit. They are concerned about overall data security in the department and would like an outside opinion on (1) any glaring, major problems found and (2) what could be done to lessen their exposure.
Here are some of the things you found during your visit:
- The “server room” is a janitorial closet with one UPS in the corner, with seven rack-mounted servers.
- Three of these servers have only one network card. The other four servers have their network cable plugged in to the same network switch.
- The UPS seems to be running at 80% capacity. Local techs estimate a 5-minute uptime before it fails.
- Many research professors house their own server in their offices.
- Desktop Support techs use the same admin password to access all workstations in the department.
List a minimum of five threats you can find in the list above. Then, suggest five controls that can be added to diminish the threats. Be as complete as possible.
1This is a simplified version of the definition in technical documents. For example, RFC 2828, the Internet security glossary defines a vulnerability as “a flaw or weakness in a system's design, implementation, or operation and management that could be exploited to violate the system's security policy.”
2http://www.nytimes.com/2006/03/27/technology/27soft.html?pagewanted = all
3http://www.cve.mitre.org/cgi-bin/cvename.cgi?name = CVE-2012-0779
4http://web.nvd.nist.gov/view/vuln/detail?vulnId = CVE-2012-0779
5http://www.sans.org/top25-software-errors/
6Symantec Internet Security Threat Report, Trends for 2010.
7Symantec Internet Security Threat Report, 2011 Trends.
8http://atlas.arbor.net/about/
9http://www.cert.org/archive/pdf/10tn028.pdf (accessed 07/22/2013).
10Meunier, P. Classes of vulnerabilities and attacks (download). In: Handbook of Science and Technology for Homeland Security, Wiley, 2007.
11Krsul, I. “Software vulnerability analysis,” unpublished PhD dissertation, Purdue University, 1988.
12http://cwe.mitre.org/top25/index.html#CWE-89
13The interested student may browse the Chrome browser source code at http://src.chromium.org/viewvc/chrome/trunk/src/chrome/browser/?sortby = file
14http://www.microsoft.com/security/online-privacy/passwords-create.aspx
15http://www.theatlantic.com/magazine/archive/2011/11/hacked/8673/
16Moore, D., Paxson, V., Savage, S., Shannon, C., Staniford, S., and Weaver, N. “Inside the Slammer worm,” IEEE Security and Privacy, July/ August 2003.
17Gibson, S. “The strange tale of the denial of service attacks against GRC.com,” http://www.crime-research.org/library/grcdos.pdf (accessed 01/13/2012).
18There is a market for such exploits. Greenberg, A. “Shopping for zero-days: a price list for hackers’ secret software exploits,” http://www.forbes.com/sites/andygreenberg/2012/03/23/shopping-for-zero-days-an-price-list-for-hackers-secret-software-exploits/ (accessed 07/22/2013).
19http://blogs.rsa.com/rivner/anatomy-of-an-attack/
20http://jeffreycarr.blogspot.com/2011/06/18-days-from-0day-to-8k-rsa-attack.html
21Ollman, G. “How criminals build botnets for profit,” Damballa, US Department of Defense Cybercrime Conference 2011, Atlanta, GA.
22http://en.wikipedia.org/wiki/Oleg_Nikolaenko
23http://www.theregister.co.uk/2009/01/07/twitter_hack_explained/
24http://blog.trendmicro.com/snapshot-of-exploit-documents-for-april-2012/
25The complete quote is “When thieves fall out honest men get their dues, but when honest men fall out lawyers get their fees,” http://en.wikipedia.org/wiki/Lying_Jim_Townsend