Chapter 6: GRC/Privacy Analyst
This chapter focuses on the governance, risk, and compliance (GRC) analyst and privacy analyst roles. These roles are commonly overlooked as a cybersecurity role given their focus on policies and procedures rather than hands-on keyboard technical skills, but they are a great path into the world of cybersecurity and provide exposure to many different areas of the field.
The following topics will be covered in this chapter:
- What is a GRC/privacy analyst?
- How much can you make in this career?
- What other careers can this type of role lead to?
- What certifications should be considered?
- Common interview questions for a GRC/privacy analyst
What is a GRC/privacy analyst?
A GRC analyst is responsible for the assessment and documentation of an organization's policies and regulations associated with the compliance and risk posture of information assets. The overall goal of an individual in this role is to ensure alignment between technology decisions and business outcomes while working to continuously improve operational efficiencies. GRC analysts may function as part of an organization's internal security team or in more of a consultative capacity in which they would provide guidance to a company's internal security team as a representative of a third-party organization.
Specific responsibilities may include risk identification and analysis, policy development, auditing, reporting, and maintaining regulatory compliance. A privacy analyst role is similar to that of a GRC analyst from an activity and responsibility perspective. The difference, however, is that a privacy analyst, as the name implies, is specifically focused, ensuring that a company's business operations, policies, and procedures meet privacy requirements and regulations pertaining to the protection of critical information.
How much can you make in this career?
At the time of writing, the average annual salary for both GRC and privacy analyst falls within the range of $60,000 to $115,000. Salary influencers for this type of role are based on factors such as level of experience, specialization, industry, and location.
What other careers can this type of role lead to?
GRC/privacy analysts require a very broad perspective into corporate functions and processes. Although the role is not directly responsible for the management and deployment of technology, individuals in this role must possess a solid understanding of risk management and the technology used as mitigating controls, thereby making the possibilities endless.
In addition, GRC/privacy analysts can potentially be exposed to companies that span a broad range of industries, which, in turn, may lead to working with various laws and regulatory requirements, providing a path to focusing on a career as a security auditor (see Chapter 7, Security Auditor, for more details).
From a soft skills perspective, constant effective communication (both written and verbal) is required for this type of role due to interviewing and documentation requirements. This type of experience can help build confidence and the skills required to lead and manage teams.
What certifications should be considered?
To get started in the role of a GRC/privacy analyst, you can consider the following courses:
- CompTIA Security+ helps establish a baseline of security knowledge when pursuing an information security/cybersecurity career. For more information, visit https://www.comptia.org/certifications/security.
- CSA's Certificate of Cloud Security Knowledge (CCSK) is similar to Security+ in that it is a vendor-agnostic, baseline-level exam with a specific focus on cloud security. For more information, visit https://cloudsecurityalliance.org/education/ccsk/.
- ISACA's Certified Information Security Auditor (CISA) is suited for professional and experienced auditing, monitoring, controlling, and assessing the business and IT systems of organizations. For more information, visit https://www.isaca.org/credentialing/cisa?utm_source=google&utm_medium=cpc&utm_campaign=CertBAU&utm_content=sem_CertBAU_certification-cisa-na-exam-google&cid=sem_2006830&Appeal=sem&gclid=Cj0KCQiAraSPBhDuARIsAM3Js4qgEODANZqgpbLCevK4RamBq_e0aTSNQdX5No0JnnmSpkJ2V_B8Lm0aAjhbEALw_wcB.
- ISACA's Certified Information Security Manager (CISM) validates expertise in areas such as security program governance, development, and management, as well as incident and risk management. For more information, visit https://www.isaca.org/credentialing/cism?utm_source=google&utm_medium=cpc&utm_campaign=CertBAU&utm_content=sem_CertBAU_certification-cism-na-product-google&cid=sem_2006855&Appeal=sem&gclid=Cj0KCQiAraSPBhDuARIsAM3Js4ro26VfkP8QA_RtNFpyYUAeKM1yyAdOGivCHGy9g9uCfNvPWaRXlTEaAreFEALw_wcB.
Next, let's look at a few interview questions that will help you with your interview.
Common interview questions for a GRC/privacy analyst
As a GRC/privacy analyst, it is important to understand common frameworks, standards, and regulations relative to the industry vertical of the company being pursued as an employer. For example, knowledge of the Health Insurance Portability and Accountability Act (HIPAA) would be necessary for an analyst pursuing a career in the healthcare industry, while Sarbanes-Oxley (SOX) would be more suited for an analyst headed down the path of finance.
The following is a list of interview questions that could prove useful in preparing for a GRC/privacy analyst interview:
- What is GRC and why is it important to an organization?
Seems like a silly question, right?! Well, has anyone ever asked you your age and you had to stop and think about it for a moment? Yeah, you don't want that to happen to you in an interview. A very simple question, and sure, you know exactly what it is in your mind, but have you practiced articulating it verbally?
Let's start with the easy part. GRC is a strategy used by organizations to manage governance (ensuring IT processes align with business goals), risk (events or situations that could be damaging to the organization), and compliance (meeting legal and regulatory requirements). GRC is critically important to a company's success and sustainability as it directly impacts an organization's ability to achieve its goals and align with the desired outcomes of stakeholders.
Benefits include the following:
- It improves activities associated with managing, identifying, and evaluating risk.
- It aids in strategic planning related to policy and corporate management activities.
- It focuses on adherence to legal and regulatory compliance requirements.
Now, let's dig a bit more into risk management.
Risk management
The purpose of risk management is to inform the development of strategic security initiatives aimed at identifying and evaluating organizational risk and then reduce the risk to an acceptable level. Sources of corporate risk are not limited to technology, however. When assessing organizational risk, it is essential to consider all aspects of risk (logical, physical, internal, external, and so on), so that the organization is not vulnerable due to blind spots. For example, when evaluating a manufacturer's organizational risk, analysts should consider intellectual property and data privacy in addition to critical infrastructure.
After identifying and evaluating the risk posed to an organization, a decision will need to be made regarding the appropriate action to take in response; this informs the risk mitigation strategy. The four most commonly exercised risk responses are as follows:
- Risk acceptance – When a risk is accepted, security leaders and business decision makers have agreed to own the consequences and loss associated with a risk that is realized. A company may elect to accept an identified risk because the cost associated with the loss does not outweigh the countermeasure cost, for example.
- Risk transfer – Companies transfer risk by assigning ownership of the cost of a loss to a separate entity. Examples of this include purchasing cybersecurity insurance and outsourcing.
- Risk avoidance – Avoiding risk involves replacing the risk with a less risky alternative or removing it altogether. An example of this is building a data center in a location other than Florida to avoid hurricanes. Another example is avoiding File Transfer Protocol (FTP) attacks by disabling the FTP protocol across the organization.
- Risk reduction/mitigation – Implementing controls and countermeasures to protect the organization from threats and eradicate vulnerabilities is the goal of risk reduction. The approach should be cost-effective and based on the cost/benefit analysis performed during risk identification and evaluation.
Cybersecurity approaches
The risk management process should lead to risk-reducing outcomes, which aligns with the need to communicate security program effectiveness in risk-reducing terms. Security teams find it increasingly difficult to identify, monitor, and measure organizational risk due to complex architecture, a lack of standardized information system policies, and the uncertainties of unknown security threats and unpredictable user behavior.
Maturity-based and cyber risk-based (or threat-focused) are the two most common approaches to cybersecurity. While both processes offer the ability to monitor and measure program effectiveness, they produce very distinct outcomes.
Maturity-based approach
Maturity-based programs focus on building defined capabilities to achieve a desired level of maturity. Although the technique is not explicitly targeting risk reduction as an outcome, it is still considered the industry norm for cyber risk management. While organizations seeking to establish an operation have seen success with this approach, as the model matures, the constant requirement to monitor and improve all program capabilities often results in inefficient spending and unmanageable tool sprawl.
Cyber risk-based approach
A cyber risk-based focus positions companies to identify the most significant vulnerabilities and threats and implement countermeasures to reduce the most critical organizational cyber risks. Following this path allows security teams to prioritize program investments (driving cost-effective decisions) and articulate risk-reducing outcomes. Many industry experts argue that when compared to the maturity-based approach, it is, in fact, the cyber risk-based operating model that is better suited to help security teams keep pace with the evolving threat landscape due to its flexibility and specificity. However, the inherent challenge for security teams when leveraging this approach is the lack of well-defined metrics due to the wide range of actions companies may choose to prioritize.
Finally, we will dive into frameworks.
Frameworks
In general, frameworks exist to enable business leaders and professionals to communicate in a common language, leveraging a defined set of standards. Similarly, cybersecurity frameworks aid security leaders in securing digital assets by providing a reliable and logical process for reducing cyber risk. It is important to note that there are three types of security frameworks:
- Control frameworks offer guidance on assessing the state of an organization's technical controls, establishing a baseline of technical controls deemed appropriate for the business, and prioritizing implementation. A widely used control framework is the Center for Internet Security's Critical Security Controls. The following is a list of the CIS controls in v8, and how many safeguards in each apply to each of the control implementation groups:

Figure 6.1 – CIS controls in v8 (Source: https://www.cisecurity.org/controls)
- Program frameworks provide a process for assessing, building, and measuring an organization's security program. An example of a program framework is the National Institute of Standards and Technology (NIST) framework for improving critical infrastructure cybersecurity (NIST Cybersecurity Framework). The following diagram shows version 1.1 of the NIST CSF:

Figure 6.2 – NIST Cybersecurity Framework 1.1
- Risk frameworks offer a structured approach to managing cyber risk by identifying, measuring, and quantifying risk, and then prioritizing mitigation activities. The NIST Risk Management Framework (RMF) is a common framework used by defense contractors to manage and demonstrate cyber risk mitigation activities and security posture improvements. The following diagram is a snapshot of the NIST RMF and the definitions of each of the stages:

Figure 6.3 – NIST Risk Management Framework (Source: https://csrc.nist.gov/Projects/risk-management)
- How does preventive control differ from detective control?
As the names imply, the purpose of preventive control is to actively prevent a threat, while detective control will only detect a threat. You might ask yourself why an organization would want to use a control only capable of detecting, but not capable of taking any action, and that's a great question. It really boils down to taking a layered or defense-in-depth approach to security and using the right tool for the job.
For example, consider modern-day endpoint protection (EPP), which typically offers a combination of a next-generation antivirus (NGAV) and endpoint detection and response (EDR). Together, they are incredibly powerful because the NGAV will prevent malicious activity, and the EDR records all of the process-level activity so that in the event a threat can bypass the NGAV, the activity can still be detected, and detailed forensics are available to assist in determining the appropriate response action. The following diagram aligns the different control types to their place in the life cycle of a cyber attack:
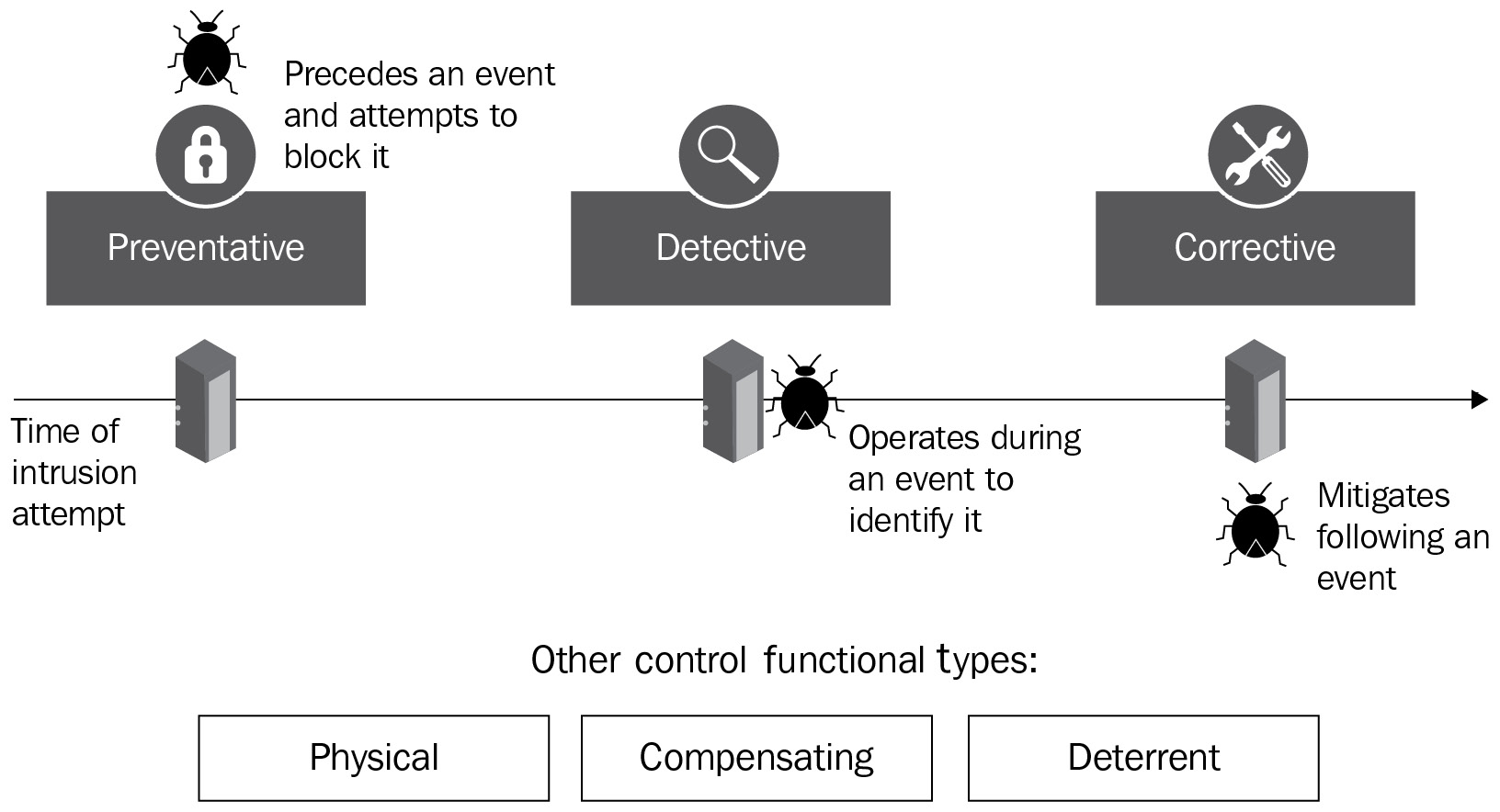
Figure 6.4 – Control types
- Describe how GRC risk management is used.
GRC risk management aims to identify, classify, and quantify organizational risk. As part of the process, the appropriate risk responses (avoid, mitigate, accept, transfer) are determined and, in the case of mitigation, preventive and detective mitigation control methods are performed.
- What makes a successful GRC/privacy analyst?
In addition to understanding the necessary framework, methodologies, regulatory requirements, and more, successful GRC/privacy analysts are able to build relationships and communicate with a broad range of teams possessing varying levels of technical and business acumen. The analyst must be able to serve as a bridge and interpreter between cross-functional teams and different organizational units.
- Provide an example of a risk management framework.
A popular and widely adopted risk management framework is NIST RMF (https://csrc.nist.gov/projects/risk-management/about-rmf). According to NIST, the framework provides a method for integrating security, privacy, and cyber supply chain risk management activities into the system development life cycle. The goal of the framework is to aid in selecting and integrating security controls in a risk-based fashion. The steps of the framework are as follows: Prepare, Categorize, Select, Implement, Assess, Authorize, and Monitor.
- What is the difference between a threat and a vulnerability?
In short, a vulnerability represents a weakness in an organization's environment. This weakness can exist in software, hardware, and even in processes. A threat, on the other hand, is anything that can exploit a vulnerability.
The terms threat, vulnerability, and risk are often confused, so be sure you're clear on each term as a standalone entity, as well as in relation to one another. We've already touched on threat and vulnerability, but it's also good to know that within the context of this question, risk is defined as the potential for damage, or the loss of data, or the destruction of assets caused by a threat.

Figure 6.5 – Risk formula
- How should a risk be classified?
This question can be a trap. The answer is very simple, but in the right moment, could lead a candidate down a long and dark path of overexplaining. The very simple answer is that while risk should ultimately be classified according to priority (critical, high, medium, and low), the specifics of the classifications should align with company policy.
- Define and provide examples of risk response within the context of risk management.
When managing an organization's cybersecurity risk, the overall outcome is to determine a cost-effective solution for reducing or mitigating the risk to a level that is acceptable according to the organization's priorities and tolerance levels. The four most common responses are as follows:
- Accept – This typically means the cost of mitigation outweighs the cost of risk realization.
- Mitigate/reduce – Implement controls to reduce the risk to a level that is within the organization's tolerance level.
- Transfer – Make it someone else's problem (in other words, cybersecurity insurance).
- Avoid – The process or solution being assessed is rejected because it is not worth the risk it poses to the organization.
- What is GDPR and when does it apply?
GDPR stands for General Data Protection Regulation and is viewed as the toughest privacy and security law in the world. The effective date of the regulation was May 25, 2018, and although it was drafted and passed by the European Union (EU), its impact is global.
The regulation is intended to protect the privacy and security of data and targets any organization that handles data related to people in the EU.
- What is the ARR?
ARR stands for audit risk rating and is used to establish the criteria to be leveraged by an organization for risk rating and ranking.
- What is the difference between security and privacy?
Although the two are very closely related, they are not one and the same. Privacy refers to an individual's right to control the use of their personal information, whereas security refers to how information is protected; use versus protection. There is a clear overlap between the two, but they are still two separate and very important considerations. The following scenario illustrates a few examples of the differences.
Scenario: You walk into a car dealership and purchase a car. The dealer collects your personal information and stores your payment details for future use. What's the worst that could happen? Let's take a look…
- The dealer uses your personal information to open a loan with the bank to cover the cost of your vehicle. They charge the card you left on file $2,500 to cover the down payment. Your data is stored on a secure server and only accessible by individuals who require access to perform their daily job. Outcome: Your information is secure, and your privacy is maintained.
- You signed a bunch of paperwork when you were there and one of the documents was the dealer's privacy disclosure. The dealer sells your information to an agency that provides marketing services to major auto insurance companies. Outcome: Your information is still secure, but your privacy is now compromised.
- The dealership is breached, and attackers steal the account details of everyone that has ever considered purchasing a car from this location since its doors first opened 15 years ago. Outcome: The security and the privacy of your data are compromised.
- What privacy laws are you familiar with and what industries are they applicable to?
These laws include the following:
- HIPAA (Health Insurance Portability and Accountability Act of 1996) – This is the standard that governs the protection of patient health information (PHI) and applies to the healthcare industry.
- FERPA (Family Educational Rights and Privacy Act) – This is a federal law applicable to all schools receiving funds through a US Department of Education program. The law protects the privacy of student education records.
- GDPR (General Data Protection Regulation) – Protects the privacy and security of data of people in the EU. It does not apply to a specific industry. The regulation has a very broad reach and applies to any organization in any industry that handles data related to people in the EU.
Also of note, three states have introduced consumer data privacy laws:
- California's Consumer Privacy Act of 2018 (CCPA)
- Colorado's Privacy Act (which was created within its Consumer Protection Act)
- Virginia's Consumer Data Protection Act
At a high level, the laws are in place to provide consumers with the right to access, delete, update, and/or obtain a copy of their personal data. There are some slight differences within the laws, so it would be worthwhile having a solid understanding of any and all laws that apply to your potential employer.
Additional details on these and other key consumer privacy laws can be found on the NCSL (National Conference of State Legislatures)'s website: https://www.ncsl.org/.
- What is CIA and why is it important?
CIA in the context of cybersecurity refers to the confidentially, integrity, and availability of data and systems. The CIA triad serves as the foundation- or base-level principle for development security policies and systems. The focus of confidentially is to ensure that data can only be viewed by authorized entities. The goal of integrity is to ensure that data remains tamper-free and trustworthy. Integrity is lost if data is not authentic, accurate, and reliable. If data is inaccessible, the importance of confidentiality and integrity diminishes somewhat. Availability efforts are aimed at ensuring that data, applications, systems, networks, and so on are available and function properly.
- Explain how encryption can be leveraged to ensure data privacy.
Data privacy refers to an individual's right to control the use of their personal information. Encryption makes this possible by scrambling plain text into an unreadable format with an encryption key. This hides the data from potential eavesdroppers because only the person or entity with the decryption key can convert the unreadable data back into plain text.
- How does technical control differ from administrative control?
Simply put, technical control is a tool (firewall, IDS/IPS, antivirus, and so on), whereas administrative control is a policy (data classification, employee onboarding/offboarding, acceptable use, and more).
The preceding questions are intended to offer insights into the types of questions you might be asked in an interview for a role as a GRC/privacy analyst. You should now have a better understanding of how to narrow your focus in preparation for interviews of this type.
An important tip to remember: it is not enough to simply understand the history and key points within laws and regulations. It is also important to understand the problem being solved in addition to the potential business impact and implications. This will vary from organization to organization, as well as from industry to industry.
Lastly, a great way to differentiate yourself in an interview is to be aware and well informed of upcoming changes to laws and regulations, especially those that directly impact the organization that has called you in for an interview. For example, the CPRA expands California's consumer data privacy laws and is set to take effect on January 1, 2023.
Summary
In this chapter, you learned what a GRC/privacy analyst is and what the average salaries are in the United States for roles of this type, along with certification considerations, career path options, and common questions you might be asked during an interview. While understanding the questions and answers as stated is important, be sure to explore beyond the specifics in the questions themselves to ensure you understand the surrounding concepts.
In the next chapter, we will learn about a career as a security auditor.
