Chapter 3. Create and manage Group Policy
Group Policies enable you to centrally configure and manage objects within your Active Directory Domain Services (AD DS) network infrastructure. To implement Group Policy Objects (GPOs) within AD DS, you must know how to create and manage GPOs; how to configure Group Policy processing, including order, precedence, inheritance, and enforcement; how to configure specific settings within a GPO; and how to implement GPO preferences, including configuring printer preferences, network drive mappings, and power options.
Skills covered in this chapter:
![]() Create and manage Group Policy Objects
Create and manage Group Policy Objects
![]() Configure Group Policy processing
Configure Group Policy processing
![]() Configure Group Policy settings
Configure Group Policy settings
![]() Configure Group Policy preferences
Configure Group Policy preferences
Skill 3.1: Create and manage Group Policy Objects
With GPOs linked to your sites, domains, and organizational units (OUs), you can quickly and easily manage large numbers of both users and computers that require the same settings. Examples include: computers at the same physical location, users in the same department, or computers with a specific base configuration that require particular settings.
After you have devised and implemented your organization’s OU infrastructure, and moved the user and computer objects into the relevant OUs, you can create GPOs, configure the desired settings, and then link them to the appropriate OU.
Using GPOs enables you to more easily manage many aspects of your AD DS infrastructure, including:
![]() Windows and app settings Use GPOs to provide a consistent interface for Windows and the installed apps. By standardizing settings, you can more easily support your users’ needs.
Windows and app settings Use GPOs to provide a consistent interface for Windows and the installed apps. By standardizing settings, you can more easily support your users’ needs.
![]() Software deployment You can use GPOs to deploy, update, and remove desktop apps from your organization’s computers.
Software deployment You can use GPOs to deploy, update, and remove desktop apps from your organization’s computers.
![]() Folder redirection Windows enables users to configure a Start menu, to customize their desktop appearance, and to store files in a personal storage area, sometimes referred to as a home folder. With folder redirection in GPOs you can redirect these local folders to a network location. This can help make back up of user data easier, and can enable user roaming between computer devices, while retaining the users’ personalized settings.
Folder redirection Windows enables users to configure a Start menu, to customize their desktop appearance, and to store files in a personal storage area, sometimes referred to as a home folder. With folder redirection in GPOs you can redirect these local folders to a network location. This can help make back up of user data easier, and can enable user roaming between computer devices, while retaining the users’ personalized settings.
![]() Security settings Many of the configurable settings in GPOs relate to operating system security. You can use GPOs to apply standard security settings to collections of users or computers.
Security settings Many of the configurable settings in GPOs relate to operating system security. You can use GPOs to apply standard security settings to collections of users or computers.
![]() Infrastructure settings GPOs also contain configurable settings for things like wireless network profiles, and Windows Firewall rules and settings.
Infrastructure settings GPOs also contain configurable settings for things like wireless network profiles, and Windows Firewall rules and settings.
This section covers how to:
![]() Configure multiple local Group Policies
Configure multiple local Group Policies
![]() Back up, restore, import, and copy GPOs
Back up, restore, import, and copy GPOs
![]() Create and configure a migration table
Create and configure a migration table
![]() Delegate Group Policy management
Delegate Group Policy management
![]() Detect health issues using the Group Policy Infrastructure Status dashboard
Detect health issues using the Group Policy Infrastructure Status dashboard
Configure multiple local Group Policies
Although this chapter focuses on domain-based GPOs, Windows Server 2016 and Windows 10 both support local Group Policies. Using local GPOs enables you to apply settings to a computer and its local user accounts; this can be useful if the computer is not part of your AD DS forest.
 Exam Tip
Exam Tip
If you apply local GPOs to a computer that is part of your AD DS forest, site-based and domain-based GPOs also apply. Any settings you configure using local GPOs that are also configured as part of a site or domain GPO are overridden.
You can create multiple local GPOs. These are:
![]() Local Group Policy This GPO contains the settings that apply to the local computer, irrespective of which user signs in. This policy contains both a computer and user node.
Local Group Policy This GPO contains the settings that apply to the local computer, irrespective of which user signs in. This policy contains both a computer and user node.
![]() Administrators and Non-Administrators Local Group Policy These user-specific policies apply to users based on whether they belong to the local administrators group or not. This enables you to customize settings for administrators. These two policies contain only a user node.
Administrators and Non-Administrators Local Group Policy These user-specific policies apply to users based on whether they belong to the local administrators group or not. This enables you to customize settings for administrators. These two policies contain only a user node.
![]() User specific Local Group Policy Windows 8 and Windows Server 2012 and newer enable support for user specific local Group Policies. This contains only a user node.
User specific Local Group Policy Windows 8 and Windows Server 2012 and newer enable support for user specific local Group Policies. This contains only a user node.
If you implement multiple local GPOs, they are processed in the following order:
1. Local Group Policy
2. Administrators and Non-Administrators Group Policy
3. User-specific Local Group Policy
 Exam Tip
Exam Tip
If settings apply in several policies, the policy that is applied last takes precedence.
To create multiple local GPOs, use the following procedure:
1. Sign in as a local administrator.
2. Click Start, type mmc.exe and then press Enter.
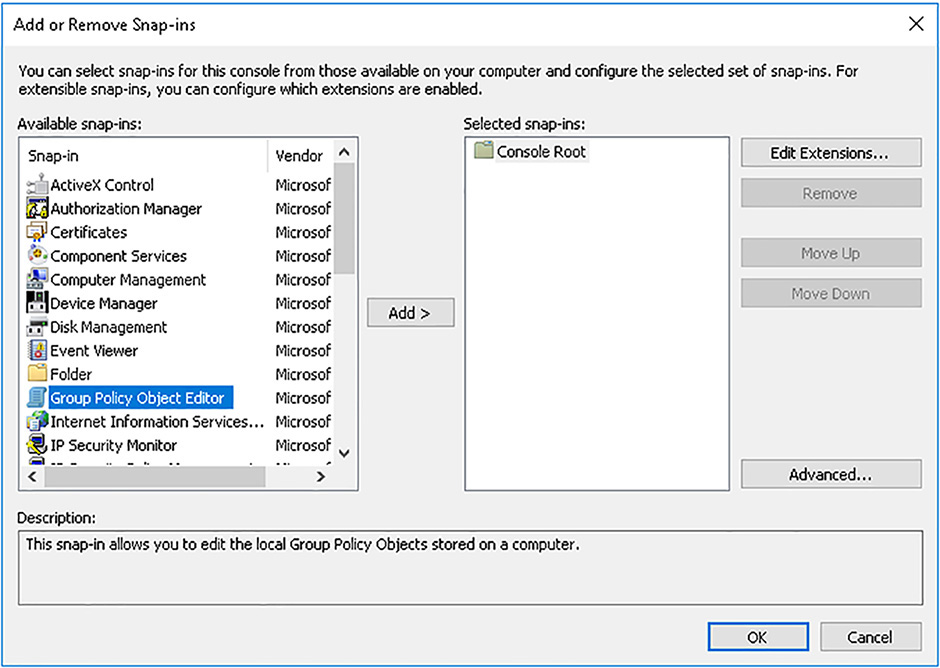
3. In the management console, click File, and then click Add/Remove Snap-In.
4. In the Add Or Remove Snap-ins dialog box, shown in Figure 3-1, in the snap-in list, click Group Policy Object Editor, and then click Add.
5. In the Select Group Policy Object dialog box, on the Welcome To The Group Policy Wizard page, shown in Figure 3-2, click Browse.
6. In the Browse For A Group Policy Object dialog box, on the Computers tab, click This Computer, as shown in Figure 3-3, and then click Finish.
7. In the Add Or Remove Snap-ins dialog box, click Group Policy Object Editor, and click Add.
8. In the Select Group Policy Object dialog box, on the Welcome To The Group Policy Wizard page, click Browse.
9. In the Browse For A Group Policy Object dialog box, on the Users tab, shown in Figure 3-4, click Administrators, click OK, and then click Finish.
10. In the Add Or Remove Snap-ins dialog box, click Group Policy Object Editor, and click Add.
11. In the Select Group Policy Object dialog box, on the Welcome To The Group Policy Wizard page, click Browse.
12. In the Browse For A Group Policy Object dialog box, on the Users tab, click Non-Administrators, click OK, and then click Finish.
13. If you want to configure local GPOs for specific users, in the Add Or Remove Snap-Ins dialog box, click Group Policy Object Editor, and click Add.
14. In the Select Group Policy Object dialog box, on the Welcome To The Group Policy Wizard page, click Browse.
15. In the Browse For A Group Policy Object dialog box, on the Users tab, click the specific user account for which you want to create a GPO, click OK, and then click Finish.
 Exam Tip
Exam Tip
You cannot apply local GPOs to security groups.
16. In the Add Or Remove Snap-ins dialog box, shown in Figure 3-5, click OK.
17. In the Console 1 – [Console Root] dialog box, shown in Figure 3-6, expand the relevant policy, and configure the required settings.
To configure one of the local policies, such as the Local Computer Policy, use the following procedure:
1. In the Console 1 – [Console Root] dialog box, in the navigation pane, expand the Local Computer Policy, and then click Computer Configuration.
2. Under the Computer Configuration node, expand the required folder. For example, expand Windows Settings, and locate the appropriate setting, as shown in Figure 3-7.
3. In the details pane, double-click the required setting and configure the desired value, and then click OK.
4. Under the User Configuration node, expand the required folder(s), locate the appropriate setting(s), and configure the desired value.
5. When you have configured all the local GPOs, you can close the console. If you are likely to reconfigure the policies, consider saving the management console with the configured snap-ins.
Although the ability to configure multiple local GPOs is a significant improvement over only being able to configure a single local GPO, the process still lacks the flexibility and centralization offered by using domain-based GPOs. Also, remember that any settings configured using local GPOs can be overwritten by domain-based GPOs.
Overview of domain-based GPOs
Domain-based GPOs apply to computer and user objects that are part of an AD DS domain. Using domain-based GPOs enables you to more easily manage the user and computer objects in your AD DS infrastructure.
Structure of GPOs
GPOs consist of two components stored in two different locations. These components are:
![]() Group Policy container This is an object stored in the AD DS database. It is replicated to other domain controllers using the intrasite or intersite AD DS replication schedule, as appropriate. This object defines the fundamental attributes of the GPO. Each GPO is assigned a globally unique identity (GUID) by AD DS.
Group Policy container This is an object stored in the AD DS database. It is replicated to other domain controllers using the intrasite or intersite AD DS replication schedule, as appropriate. This object defines the fundamental attributes of the GPO. Each GPO is assigned a globally unique identity (GUID) by AD DS.
![]() Group Policy template This is a collection of files and folders stored in the SYSVOL shared folder on all domain controllers. These files contain the actual GPO settings. The settings for a specific GPO are stored in:
Group Policy template This is a collection of files and folders stored in the SYSVOL shared folder on all domain controllers. These files contain the actual GPO settings. The settings for a specific GPO are stored in:
%SystemRoot%SYSVOLDomainPolicies{GUID}
The {GUID} is the globally unique identity of the GPO. The contents of the SYSVOL folder, including the Group Policy template folders, are replicated between domain controllers using a different replication agent. In Windows Server 2008 and earlier, SYSVOL is replicated by the File Replication Service (FRS). In newer versions of Windows Server, SYSVOL replication is handled by the Distributed File System Replication agent (DFSR).
 Exam Tip
Exam Tip
Because these two GPO components are replicated between domain controllers using different replication agents, you can occasionally get temporary synchronization issues between these two components. Generally, these issues automatically resolve.
Available GPO management tools
You can create and manage GPOs in your domain using several different tools. These are:
![]() Group Policy Management This management console, shown in Figure 3-8, enables you to perform all GPO-related management tasks, including creation, linking, filtering, modeling, and troubleshooting.
Group Policy Management This management console, shown in Figure 3-8, enables you to perform all GPO-related management tasks, including creation, linking, filtering, modeling, and troubleshooting.
![]() Group Policy Management Editor You can launch this console from within Group Policy Management by selecting a GPO, and then selecting Edit. You can view and configure available settings in the GPO using this console, shown in Figure 3-9.
Group Policy Management Editor You can launch this console from within Group Policy Management by selecting a GPO, and then selecting Edit. You can view and configure available settings in the GPO using this console, shown in Figure 3-9.
![]() Windows PowerShell You can also use a number of Windows PowerShell cmdlets to create, link, and configure GPOs. For example, the new-gpo cmdlet is used to create a GPO, as shown in Figure 3-10.
Windows PowerShell You can also use a number of Windows PowerShell cmdlets to create, link, and configure GPOs. For example, the new-gpo cmdlet is used to create a GPO, as shown in Figure 3-10.
Need More Review? Group Policy cmdlets in Windows PowerShell
To review further details about using Windows PowerShell to manage GPOs, refer to the Microsoft TechNet website at https://technet.microsoft.com/library/ee461027.aspx.
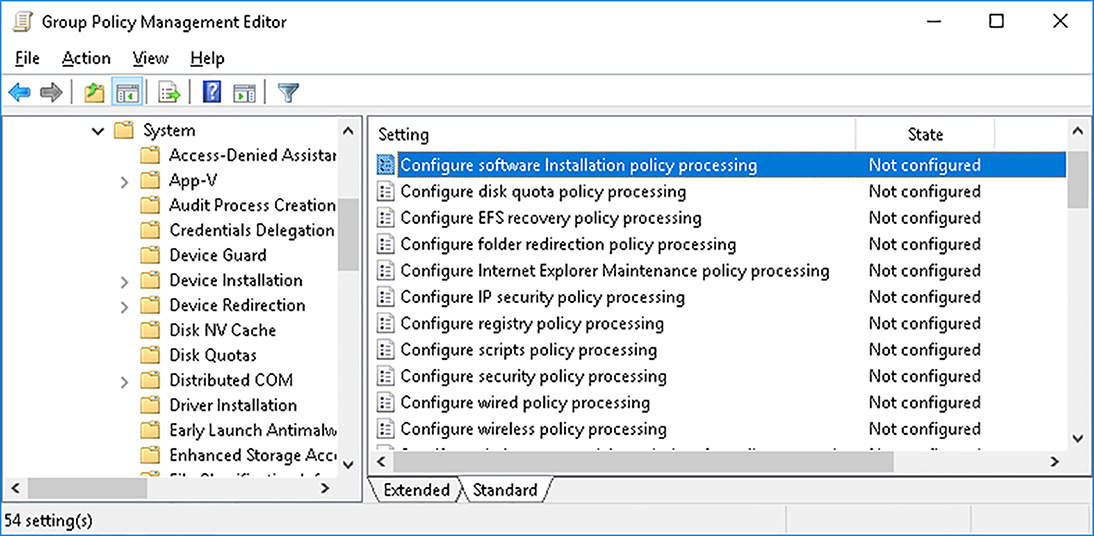
Configuring specific settings
After you have created your GPOs, you must configure the available settings. You use the Group Policy Management Editor to perform this task.
As shown in Figure 3-9, a GPO consists of several nodes, each containing folders and subfolders. These folders contain collections of related settings. This structure helps make it easier for the administrator to locate the desired setting.
A policy consists of two top-level nodes:
![]() Computer Configuration Contains the settings that are applied to the computer objects in a container to which this GPO is linked. These settings are applied on affected computers during startup and thereafter, and are automatically refreshed every 90 to 120 minutes.
Computer Configuration Contains the settings that are applied to the computer objects in a container to which this GPO is linked. These settings are applied on affected computers during startup and thereafter, and are automatically refreshed every 90 to 120 minutes.
![]() User Configuration Contains the user-related settings. These are applied when a user signs in and thereafter, and are automatically refreshed every 90 to 120 minutes.
User Configuration Contains the user-related settings. These are applied when a user signs in and thereafter, and are automatically refreshed every 90 to 120 minutes.
Even if a policy setting is applied, it does not necessarily mean that it is immediately effective. Often, computer settings only apply after a restart, and user settings sometimes only apply following a sign out and sign in procedure.
Beneath each of these nodes, there are some folders and many subfolders that group settings, including:
![]() Software Settings Enables you to deploy, update, and remove software from computers in your domain. Contains a single subfolder:
Software Settings Enables you to deploy, update, and remove software from computers in your domain. Contains a single subfolder:
![]() Software Installation Enables you to add packages for deployment in your organization.
Software Installation Enables you to add packages for deployment in your organization.
![]() Windows Settings Enables you to configure the basic settings for your computers or users. Contains several subfolders, including:
Windows Settings Enables you to configure the basic settings for your computers or users. Contains several subfolders, including:
![]() Scripts You can configure startup and shutdown or logon and logoff scripts that process when a computer starts or a user signs in.
Scripts You can configure startup and shutdown or logon and logoff scripts that process when a computer starts or a user signs in.
![]() Security Settings Consolidates the various security settings that you can apply, including: account policies and user rights; event log settings; restricted groups; system services; registry and file system permissions; Windows Firewall rules and settings; software and application control settings, and many others.
Security Settings Consolidates the various security settings that you can apply, including: account policies and user rights; event log settings; restricted groups; system services; registry and file system permissions; Windows Firewall rules and settings; software and application control settings, and many others.
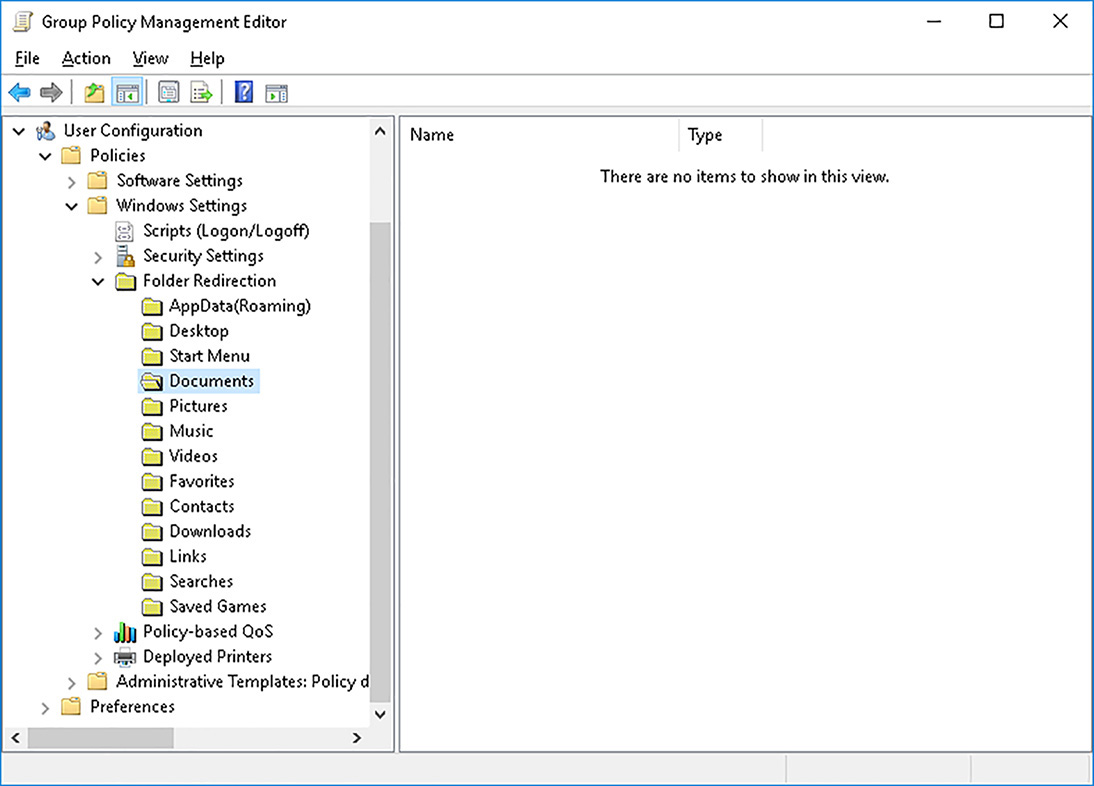
![]() Folder Redirection You can redirect desktop, Start menu, and the user’s personal folder, amongst others.
Folder Redirection You can redirect desktop, Start menu, and the user’s personal folder, amongst others.
![]() Administrative Templates Contains registry settings that control user, computer, and app behavior and settings. There are many thousands of settings, but these have been grouped logically into folders to help make their purpose more obvious. These include:
Administrative Templates Contains registry settings that control user, computer, and app behavior and settings. There are many thousands of settings, but these have been grouped logically into folders to help make their purpose more obvious. These include:
![]() Control Panel
Control Panel
![]() Desktop
Desktop
![]() Network
Network
![]() Shared Folders
Shared Folders
![]() Start Menu and Taskbar
Start Menu and Taskbar
![]() System
System
![]() Windows Components
Windows Components
![]() All Settings
All Settings
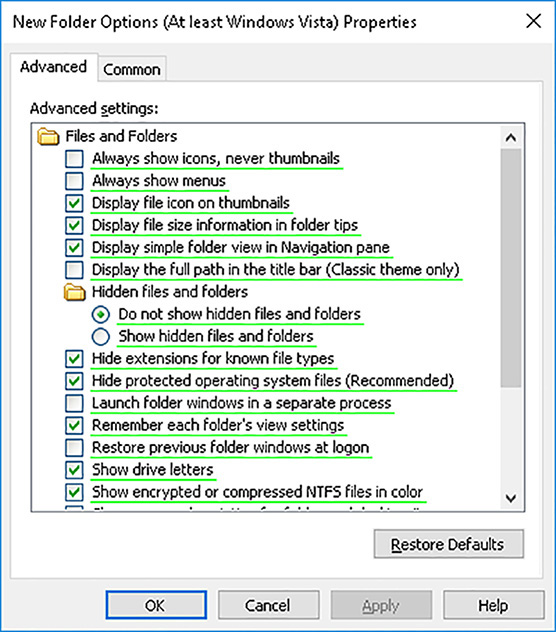
When you start to configure specific settings, you see that they fall into several different types. Some require that you configure one or more values, as shown in Figure 3-11.
Others require that you turn on or turn off a setting by enabling or disabling it, as shown in Figure 3-12. These settings have three possible values: Enabled, Disabled, and Not Configured (usually the default). The last of these three is rather interesting because the resultant value on a client computer (or signed in user) depends on whether the same setting is configured elsewhere; that is, in another GPO that also affects this computer or user. We learn about this behavior in more detail later.
Linking GPOs
When you have created a GPO and you have configured its settings, you must then link it to a container object in AD DS for it to apply to objects. You can link GPOs to:
![]() Sites
Sites
![]() Domains
Domains
![]() OUs
OUs
Linking a GPO to a container object is known as scoping. The scope determines which computers and users are impacted by the settings in a GPO. For example, if you link a GPO to the domain container, all computer and user objects within the domain are impacted by the configuration settings within that GPO. If you link the GPO to an OU, only objects within that OU (and any sub-OUs) are affected.
Note Inheritance
Settings configured at the domain level are inherited by objects in OUs within that domain. You can control this inheritance behavior; this is discussed in Skill 3.2: Configure Group Policy processing.
It is important that you understand that proper OU planning is required before you begin to create, configure, and link GPOs.
Client-side extensions
Although domain controllers store and make available the various GPOs that you create and configure, it is the responsibility of the client computer to connect to the domain controller and request and apply the necessary GPOs. A service called the Group Policy Client connects and downloads the required GPOs. Then, a series of components on the client, known as client-side extensions, process the GPO settings.
There are several client-side extensions on a Windows computer that process different GPO settings. These include:
![]() Registry policy
Registry policy
![]() Internet Explorer maintenance policy
Internet Explorer maintenance policy
![]() Software Installation policy
Software Installation policy
![]() Folder Redirection policy
Folder Redirection policy
![]() Scripts policy
Scripts policy
![]() Security policy
Security policy
![]() Internet Protocol security (IPsec) policy
Internet Protocol security (IPsec) policy
![]() Wireless policy
Wireless policy
![]() Encrypting File System recovery policy
Encrypting File System recovery policy
![]() Disk quota policy
Disk quota policy
Open the registry and navigate to the HKLMSoftwareMicrosoftWindows NTCurrentVersionWinlogonGPExtensions key in the registry. You can see a list of the available client-side extensions here.
Manage starter GPOs
In larger organizations, you might find that you must create many GPOs, some of which share many settings. If this is the case, you can consider using Starter GPOs. A Starter GPO is a template GPO that you can use for creating a new GPO.
If you populate the Starter GPO with the most common settings, you can quickly create additional GPOs that contain those common settings. To create Starter GPOs, use the following procedure:
1. Open the Group Policy Management console and navigate to the Starter GPOs node beneath your domain node, as shown in Figure 3-13.
2. In the details pane, click Create Starter GPOs Folder. The Starter GPOs folder is created and populated with two default Starter GPOs:
![]() Group Policy Remote Update Firewall Ports
Group Policy Remote Update Firewall Ports
![]() Group Policy Reporting Firewall Ports
Group Policy Reporting Firewall Ports
You must now create and configure the required Starter GPOs:
1. Right-click the Starter GPOs node in the navigation pane, and then click New.
2. In the New Starter GPO dialog box, type the name for your Starter GPO, and then click OK.
3. In the Starter GPOs folder, shown in Figure 3-14, right-click the new Starter GPO, and then click Edit.
4. In the Group Policy Starter GPO Editor, shown in Figure 3-15, configure the required settings.
5. Close the Group Policy Starter GPO Editor.
To create a new GPO based on a Starter GPO:
1. In the Starter GPOs folder, right-click the appropriate Starter GPO, and then click New GPO from Starter GPO.
2. In the New GPO dialog box, type the GPO name, and click OK.
3. Click the Group Policy Objects node in the navigation pane, shown in Figure 3-16, and your new policy is listed along with default GPOs and any others previously created.
Note Import and export
It’s possible to export Starter GPOs to a .CAB file. It is also possible to import Starter GPOs from a .CAB file. Use the Load Cabinet and Save As Cabinet buttons in the Starter GPOs folder, as shown in Figure 3-14.
Configure GPO links
To make a GPO effective, you must link it to a container. To link a GPO to a container, you can use the Group Policy Management console or the Windows PowerShell New-GPLink cmdlet.
As mentioned earlier, you can link GPOs to the following AD DS containers:
![]() Sites Use site-linked GPOs for settings that apply to computers or users based on their specific location. Obviously, you must have defined both subnet and site objects in AD DS and moved your domain controllers into the appropriate sites.
Sites Use site-linked GPOs for settings that apply to computers or users based on their specific location. Obviously, you must have defined both subnet and site objects in AD DS and moved your domain controllers into the appropriate sites.
 Exam Tip
Exam Tip
Be aware that site-linked GPOs can sometimes impose delays on the application of GPOs for clients in a specific site location but in a different domain from the domain controllers situated at the site.
![]() Domains Use domain-linked GPOs for settings that apply to most, or all, of the users and computers in your domain. If the same settings apply to multiple domains in your forest, you should copy the GPOs from one domain to the other and then link them at the other domain.
Domains Use domain-linked GPOs for settings that apply to most, or all, of the users and computers in your domain. If the same settings apply to multiple domains in your forest, you should copy the GPOs from one domain to the other and then link them at the other domain.
![]() OUs For settings that are more specific, consider linking your GPOs to an OU. Then place the appropriate users and computers into the OU. Note that all objects in the OU receive settings from the linked GPO by default, unless you choose to configure some form of GPO filtering.
OUs For settings that are more specific, consider linking your GPOs to an OU. Then place the appropriate users and computers into the OU. Note that all objects in the OU receive settings from the linked GPO by default, unless you choose to configure some form of GPO filtering.
The procedure for linking an existing GPO to a container is as follows:
1. In the Group Policy Management console, right-click the appropriate container, and then click Link An Existing GPO.
2. In the Select GPO dialog box, shown in Figure 3-17, in the Look In This Domain list, select the current domain, and then in the Group Policy objects list, click the appropriate GPO, and click OK.
Note Creating and linking in a single step
You can also create and link a GPO in one step. Right-click the container, and then click Create A GPO In This Domain, and Link It Here. Enter the GPO name, and click OK. You must then edit the GPO and configure the required settings.
You can use the Windows PowerShell New-GPLink cmdlet to link a GPO to a container. For example, to link the GPO called IT Managers to the IT OU in the Adatum.com domain, use the following command:
New-GPLink -Name "IT Managers" -target "ou=IT, dc=Adatum,dc=com"
To create the same GPO and link it in one step, use the following command:
New-GPO -Name "IT Managers" | New-GPLink -target "ou=IT,dc=Adatum,dc=com" -LinkEnabled
Yes
If multiple GPOs are linked to the same container, you must configure the link order. The link order determines in which order the GPOs apply. This becomes important if the same setting is configured in several different GPOs as it determines which setting applies. Link order is discussed in Skill 3.2: Configure Group Policy processing.
 Exam Tip
Exam Tip
You can link a single GPO to multiple AD DS containers simultaneously.
Back up, restore, import, and copy GPOs
It is important that you back up your GPOs when you have made significant changes to them, or, indeed, are about to make significant changes. You should also be aware of how to restore your GPOs should the need arise, perhaps due to corruption, or human error when making configuration changes.
Back up GPOs
You can perform all backup and restore operations using the Group Policy Management console, or with Windows PowerShell cmdlets. To back up all GPOs in your domain, perform the following procedure:
1. Open the Group Policy Management console and navigate to the Group Policy Objects node.
2. Right-click the Group Policy Objects node, and then click Back Up All.
3. In the Back Up Group Policy Object dialog box, in the Location box, type a valid path to a folder where you want to store your backups, as shown in Figure 3-18. Optionally, enter a description, and then click Back Up.
4. On the Backup progress page, click OK.
To back up all GPOs to a shared folder called \LON-DC1Backup using Windows PowerShell, run the following command:
Backup-Gpo -All -Path \LON-DC1Backup
To back up a specific GPO, in the Group Policy Objects node, click and then right-click the specific GPO you want to back up, and then click Back Up. The process is like the process for backing up all GPOs. To use Windows PowerShell to back up a specific GPO, in this case, called Sales Managers, use the following command:
Backup-Gpo -Name "Sales Manager" -Path C:UsersAdministrator -Comment "Weekly Backup"
Restore GPOs
To restore a GPO, use the following procedure:
1. Right-click the appropriate GPO in the Group Policy Objects node, and then click Restore from Backup.
2. In the Restore Group Policy Object Wizard, on the Welcome page, click Next.
3. On the Backup Location page, enter the location where you saved your backup GPOs, and then click Next.
4. On the Source GPO page, shown in Figure 3-19, select the appropriate version of the backed up GPO. Click Next.
5. On the Completing The Restore Group Policy Object Wizard page, click Finish, and when prompted, click OK.
You can also use the Windows PowerShell restore-gpo cmdlet. To restore the Sales Managers GPO from the \LON-DC1Backup folder, use the following command:
Restore-GPO -Name "Sales Managers" -Path \LON-DC1Backup
Manage backups
You can also manage your backups from the Group Policy Management console. You can use the Manage Backups option to view the settings in a backup, to delete a backup, and to restore a backup.
To access the Manage Backups tool, in the Group Policy Management console:
1. Right-click the Group Policy Objects node, and then click Manage Backups.
2. In the Manage Backups dialog box, shown in Figure 3-20, select the backup you want to manage, and then click Restore, Delete, or View Settings, as required.
Import a GPO
Although you can link the same GPO to multiple containers, including domains, it is not always advisable to do this. Usually, it is better to import a GPO from another domain. The import process requires that you effectively restore the settings of another GPO into a newly created, empty GPO. The process therefore starts with you creating a backup of the source GPO, as described above.
Then, to import the settings, use the following procedure:
1. In the Group Policy Management console on the target domain, create a new GPO in the Group Policy Objects node.
2. Right-click the new GPO, and then click Import Settings.
3. In the Import Settings Wizard, on the Backup GPO page, click Next. You do not need to back up your GPO because it currently contains no settings.
4. On the Backup location page, select the folder where you backed up your source GPO, and click Next.
5. On the Source GPO page, select the appropriate GPO from the Backed Up GPOs list, and then click Next.
6. Click through the wizard to complete the import process. Click Finish when prompted.
You can also use the import-gpo Windows PowerShell cmdlet. For example, to import the IT Managers GPO from the \LON-DC1Backup folder to a new GPO called Sales Managers, use the following command:
Import-GPO -BackupGpoName "IT Managers" -TargetName "Sales Managers" -Path \LON-DC1
Backup
Copy a GPO
You can duplicate the settings in one GPO for reuse in another. A convenient way to do this is to copy a GPO. The procedure is as follows:
1. In the Group Policy Management console, in the Group Policy Objects node, right-click the source GPO, and then click Copy.
2. Right-click the Group Policy Objects node, and then click Paste.
3. In the Copy GPO dialog box, shown in Figure 3-21, choose either to Use The Default Permissions For New GPOs, or choose Preserve The Existing Permissions. Click OK.
4. When prompted, click OK.
5. In the Group Policy Objects node, rename the newly created GPO. It has the same name as the source GPO with the prefix Copy Of.
You can also use the copy-gpo Windows PowerShell cmdlet. For example, to copy the IT Manager’s GPO to the Sales Manager’s GPO, use the following command:
Copy-GPO -SourceName "IT Managers" -TargetName "Sales Managers"
Create and configure a migration table
Migration tables can help when you wish to use the same GPO in multiple domains. Some GPOs might contain folder redirection settings, which often contain universal naming convention (UNC) folder names, such as \LON-SVR1UsersStart-Menu. Others settings might contain security principals, such as computer names.
If you import a GPO from another domain, these UNC names might not be relevant in the target domain. By using migration tables, you can more easily maintain the accuracy of GPO settings when copying between domains. Using migration tables, you can reference and update the following objects types:
![]() Users
Users
![]() Groups
Groups
![]() Computers
Computers
![]() UNC paths
UNC paths
To create a migration table, use the following procedure:
1. In the Group Policy Management console, right-click the Domains node, and then click Open Migration Table Editor.
2. In the Migration Table Editor – New dialog box, shown in Figure 3-22, click Tools, and click Populate From GPO.
3. In the Select GPO dialog box, shown in Figure 3-23, in the Look In This Domain list, select the source domain. In the Group Policy objects list, click the source GPO. Select the During Scan, Include Security Principals From The DACL On The GPO. Click OK.
4. In the Migration Table Editor – New dialog box, shown in Figure 3-24, in the Destination Name column, enter the replacement UNC name(s) as needed.
5. When you have made all the required changes, click File, and then click Save.
6. In the Save As dialog box, enter a valid path, enter the name of the file, and then click Save. Make sure you save the migration table to a network accessible location.
7. Close the Migration Table Editor.
 Exam Tip
Exam Tip
Consider using the Validate Table option before saving your table. This is accessible from the Tools menu.
You can use the migration table when you import a GPO into a different domain. Use the following procedure:
1. First, back up the source GPO that you referenced in the migration table. For details on this process, see the section in this chapter titled “Back up, import, copy, and restore GPOs.” Place the backup files into a network accessible folder.
2. On the target domain, open the Group Policy Management console, navigate to the Group Policy Objects node, and create a new GPO. Use a meaningful name; this does not need to be the same as the source GPO.
3. Right-click the new GPO, and then click Import Settings.
4. In the Import Settings Wizard, on the Welcome page, click Next.
5. On the Backup GPO, click Next. You do not need to back up your GPO because it contains no settings now.
6. On the Backup Location page, in the Backup folder box, type the UNC name to the shared folder that contains the backup of the source GPO, and then click Next.
7. On the Source GPO page, shown in Figure 3-25, in the Backed Up GPOs list, click the appropriate GPO, and then click Next.
8. On the Scanning Backup page, observe the message that the backup contains security principals and/or UNC paths, as shown in Figure 3-26, and then click Next.
9. On the Migrating References page, as shown in Figure 3-27, click Using This Migration Table To Map Them In The Destination GPO, and then browse and select the migration table from the shared folder where you saved it. Click Next.
10. On the Completing The Import Settings Wizard page, click Finish.
11. On the Import Progress page, when the Succeeded message displays, click OK.
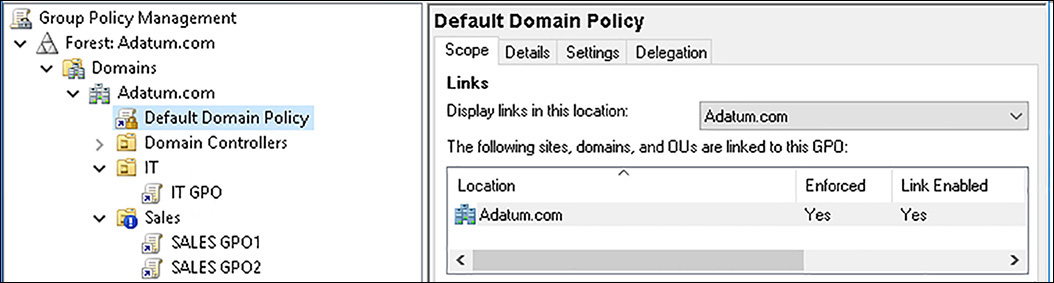
![]() Default Domain Policy This policy is linked to the domain object.
Default Domain Policy This policy is linked to the domain object.
![]() Default Domain Controllers Policy This policy is linked to the Domain Controllers OU.
Default Domain Controllers Policy This policy is linked to the Domain Controllers OU.
Generally, in most AD DS environments, it is often advisable to create and customize GPOs to suit your business requirements rather than editing the two default GPOs. However, there is nothing preventing you from editing the default GPOs. Indeed, in some circumstances, it makes sense to use the default GPOs. If, however, you decide that you want to revert your default GPOs to their initial state, perhaps because that’s quicker than editing them manually, or because there is a problem or corruption in the GPOs, you can reset one or both of them.
To reset the default GPOs, open an elevated command prompt, and run the DCGPOFix command. As shown in Figure 3-28, you are prompted to confirm the operation.
If you wish to restore only one or the other default GPO, run the DCGPOFix command with the following parameters:
![]() /target:Domain Resets only the Default Domain Policy.
/target:Domain Resets only the Default Domain Policy.
![]() /target:DC Resets only the Default Domain Controllers Policy.
/target:DC Resets only the Default Domain Controllers Policy.
Delegate Group Policy management
In smaller organizations, it is likely that the same person who creates GPOs is the person responsible for configuring the settings within the GPO, and for linking the GPO to the appropriate container objects in a domain. By default, in Windows Server 2016, members of the following groups have full control over all GPO management tasks:
![]() Domain Admins
Domain Admins
![]() Group Policy Creator Owners
Group Policy Creator Owners
![]() Local System
Local System
 Exam Tip
Exam Tip
Users must be able to apply GPOs for the GPO to configure their settings; this requires at least Read and Apply Group Policy permissions, which are applied by default to all newly created GPOs. These are not management permissions.
However, in larger organizations, the ability to split the administrative tasks associated with GPO management is useful. This splitting of administrative effort is known as delegating control. In Windows Server 2016, you can delegate control of the following GPO administrative and management tasks:
![]() Creating GPOs You can grant the required permissions to perform this task by using the Group Policy Management console.
Creating GPOs You can grant the required permissions to perform this task by using the Group Policy Management console.
![]() Editing GPOs To edit the settings in GPOs, users require the Read and Write permission on the GPO. Use the Group Policy Management console to assign these permissions.
Editing GPOs To edit the settings in GPOs, users require the Read and Write permission on the GPO. Use the Group Policy Management console to assign these permissions.
![]() Managing GPO links for sites, domains, or OUs Linking allows you to enable the GPO settings on a specified container object. In Group Policy Management, use the Delegation tab on the specified container to assign these permissions. Alternatively, use the Delegation Of Control Wizard in Active Directory Users and Computers as described in Chapter 1.
Managing GPO links for sites, domains, or OUs Linking allows you to enable the GPO settings on a specified container object. In Group Policy Management, use the Delegation tab on the specified container to assign these permissions. Alternatively, use the Delegation Of Control Wizard in Active Directory Users and Computers as described in Chapter 1.
![]() Performing GPO modeling analyses for specified domain or OU Modeling enables an administrator to perform ‘what if’ analysis for the application and processing of GPOs within the AD DS infrastructure. On a specific container, use the Delegation tab in Group Policy Management to assign these permissions. You can also use the Delegation Of Control Wizard in Active Directory Users and Computers.
Performing GPO modeling analyses for specified domain or OU Modeling enables an administrator to perform ‘what if’ analysis for the application and processing of GPOs within the AD DS infrastructure. On a specific container, use the Delegation tab in Group Policy Management to assign these permissions. You can also use the Delegation Of Control Wizard in Active Directory Users and Computers.
![]() Reading GPO results data for objects in specified domain or OU GPO result analysis allows you to generate reports on the effect of GPO settings on target objects within your AD DS environment. As before, use the Delegation tab on a specific container to assign these permissions, or use the Delegation Of Control Wizard.
Reading GPO results data for objects in specified domain or OU GPO result analysis allows you to generate reports on the effect of GPO settings on target objects within your AD DS environment. As before, use the Delegation tab on a specific container to assign these permissions, or use the Delegation Of Control Wizard.
![]() Creating WMI filters Windows Management Instrumentation (WMI) filters enable you to determine whether a GPO applies to an object in an OU based on the characteristics of that object. For example, the GPO applies if the computer object is running Windows 10 and has 8GB of physical memory. In Group Policy Management, use the Delegation tab on the container to assign these permissions. You can also use the Delegation Of Control Wizard.
Creating WMI filters Windows Management Instrumentation (WMI) filters enable you to determine whether a GPO applies to an object in an OU based on the characteristics of that object. For example, the GPO applies if the computer object is running Windows 10 and has 8GB of physical memory. In Group Policy Management, use the Delegation tab on the container to assign these permissions. You can also use the Delegation Of Control Wizard.
You can use the Windows PowerShell Get-GPPermissions cmdlet to view current GPO permissions, and the Set-GPPermissions cmdlet to modify permissions.
To use the Group Policy Management console to delegate permissions to manage GPOs, use the following procedure:
1. In the Group Policy Management console, select the container object on which you want to delegate control. For example, in the navigation pane, click the domain.
2. In the details pane, click the Delegation tab, as shown in Figure 3-29.
3. In the Permission list, click the permission that you want to delegate. Choose between: Link GPOs, Perform Group Policy Modeling Analyses, and Read Group Policy Results Data.
4. Click Add, and in the Select User, Computer, or Group dialog box, in the Enter The Object Name To Select Text box, type the group or user name to which you want to delegate the permission, and then click OK.
5. In the Add Group Or User dialog box, shown in Figure 3-30, in the Permissions list, select the required inheritance. Choose between: This Container Only and This Container And All Child Containers. Click OK.
6. Review the changes, as shown in Figure 3-31. You can use the Advanced button to fine tune the required permissions.
To use the Delegation Of Control Wizard to delegate permissions to manage GPO links, use the following procedure:
1. In Active Directory Users and Computers, locate and right-click your target container, and then click Delegate Control.
2. In the Delegation Of Control Wizard, on the Welcome page, click Next.
3. On the Users Or Groups page, click Add, and locate the user or group to which you want to delegate the specific task you are configuring. Click OK, and then click Next.
4. On the Tasks To Delegate page, shown in Figure 3-32, in the Delegate The Following Common Tasks list, select the check box for the Manage Group Policy links, and click Next.
5. AD DS permissions are configured. Click Finish.
Delegating the other permissions, such as creating WMI filters, is a broadly similar process.
Note Groups not users
It is important to use best practice and, unless strictly necessary to do otherwise; always delegate permissions to groups rather than to user accounts directly. This enables you to more easily, and more securely, make changes in the future by moving users between groups to change their delegated permissions rather than having to modify delegated permissions to take account of employee structural changes.
Detect health issues using the Group Policy Infrastructure Status dashboard
Windows Server 2016 AD DS provides a GPO Infrastructure Status page. This is accessible in the Group Policy Management console. To view the status, use the following procedure:
1. Select the domain object, and then click the Status tab.
2. To view the current status, click Detect Now.
3. Review the information in the details pane, as shown in Figure 3-33.
Skill 3.2: Configure Group Policy processing
When you start thinking about using GPOs to configure user and computer settings, you must think about implementing a meaningful OU structure. This is because it is OUs (and to a lesser extent, domains and sites) to which you link GPOs. By default, this means that all objects that you place in the OU (or domain or site) are affected by the linked GPOs.
As we mentioned earlier, since each policy linked to a container might contain conflicting settings—that is, in GPO1, policy setting X is Enabled, while in GPO2, policy setting X is Disabled—we must consider factors that determine in which order GPOs are applied. Indeed, we must also consider factors such as inheritance, precedence, and both WMI and security filtering to make a proper determination.
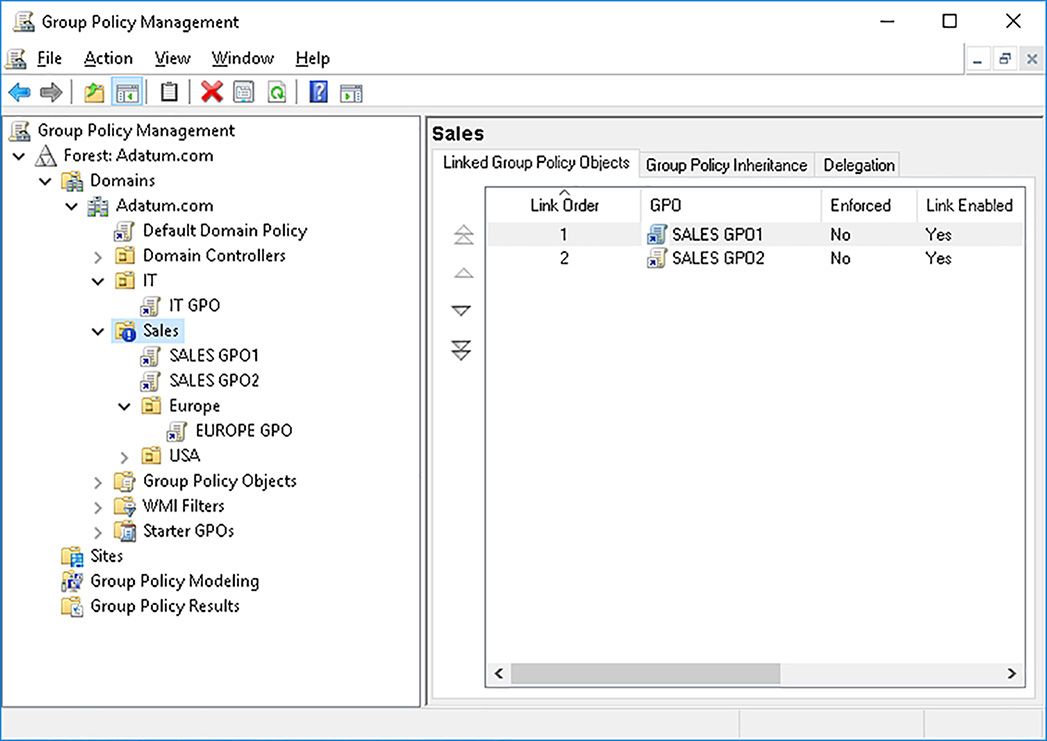
You should group objects together into OUs because you want to delegate management permissions on those objects, or because you want to configure common settings on the objects. Figure 3-34 shows a representation of the Adatum.com forest, and shows several OUs and linked GPOs.
In Figure 3-35, the Group Policy Management console shows the same structure. We discuss this infrastructure throughout this skill.
This section covers how to:
![]() Configure processing order and precedence
Configure processing order and precedence
![]() Configure security filtering and WMI filtering
Configure security filtering and WMI filtering
![]() Configure and manage slow-link processing and Group Policy caching
Configure and manage slow-link processing and Group Policy caching
![]() Configure client-side extension behavior
Configure client-side extension behavior
Configure processing order and precedence
By default, if multiple GPOs apply to objects in an OU, the settings in the GPO that has the lowest link order (1 being the lowest) takes precedence. That is not to say that the whole GPO overwrites all previously applied settings. What happens depends on how the settings are configured.
For example, suppose you create a GPO that configures only the Security Settings in the Computer Configuration node. Then suppose you create another GPO linked to the same container in which you configure only the Windows Components under the Administrative Templates folder. None of these settings conflict with one another. Therefore, it doesn’t matter which has the lowest link order.
However, let’s suppose you configure the same two GPOs linked to the same container. This time, both GPOs configure the same settings; for example, in Windows Components in the Administrative Templates folder under the Computer Configuration node. In this instance, the setting that is applied to objects in the OU is determined by the link order.
 Exam Tip
Exam Tip
If you link only a single GPO to any given container, you do not need to consider the processing order of the GPOs.
You must also consider the fact that settings are, by default, inherited from higher-level containers to which GPOs are linked. So, in our example, settings applied to the Default Domain Policy also apply to objects in the Sales OU. Likewise, objects in the Europe OU receive their settings, by default, from the Default Domain Policy as well as from both the SALES GPO1 and SALES GPO2. These settings are in addition to the settings applied to the EUROPE GPO, which is linked to the Europe OU. In the case of any conflicting settings (and only in the case of conflicting settings), the GPO applied last takes precedence, and those settings are applied. In this scenario, the last-applied GPO would be the one linked to the Europe OU.
Therefore, to configure precedence, you must link your GPOs to the correct OU. Those at the lower levels in our diagram have the higher precedence. To configure link order, open the Group Policy Management console, as shown in Figure 3-36, and use the arrow buttons to change the link order in OUs with multiple linked GPOs.
Configuring inheritance
By default, any GPOs you create and link to high-level objects in your OU tree also apply to all objects beneath that link. For example, in our scenario in Figure 3-34, the Default Domain Policy linked to the domain is applied to all objects in all OUs beneath that point.
Again, in our example, the computers and users in the Europe OU beneath the Sales OU receive settings not only from the directly linked EUROPE GPO, but also inherit settings from the Default Domain Policy, and both SALES GPO1 and SALES GPO2.
In fact, it is beneficial that this inheritance occurs because it enables you to link GPOs high up in the OU tree with settings that you want to apply to all computers (or users), knowing that these settings apply to subordinate objects. Best practice, therefore, is to plan to take advantage of this inheritance behavior and configure the settings in high-level GPOs to apply to all objects. Then, as you move down the OU tree to sub OUs, create and link specific GPOs with settings that affect only the objects in that container.
 Exam Tip
Exam Tip
Inherited GPOs have a lower precedence value than directly linked GPOs. This is because of the last processed principle: GPOs that apply last overwrite conflicting settings from higher-level GPOs.
Block inheritance
Occasionally, however, despite the best-planned OU structure, you might find that you want to block the inheritance of GPO settings from further up the OU tree. You can do this on a per-container basis. That is, you can block inheritance on a specific OU.
When you choose to block inheritance, you block the settings for all GPOs linked to containers above the OU you are blocking. For example, as shown in Figure 3-37, inheritance is blocked on the SALES OU. Whereas the DEFAULT DOMAIN POLICY once applied to objects in the SALES OU, as well as the EUROPE OU and the USA OU, now, the settings in the DEFAULT DOMAIN POLICY do not apply in the SALES OU and beyond.
To configure this behavior, complete the following procedure:
1. Open the Group Policy Management console.
2. In the navigation pane, as shown in Figure 3-38, right-click the relevant OU, and then click Block Inheritance.
3. In Group Policy Management, as shown in Figure 3-39, the blue exclamation point indicates that inheritance is blocked.
You can verify which GPOs settings are inherited by selecting the appropriate GPO in the Group Policy Management console, and then, in the details pane, clicking the Group Policy Inheritance tab. Only policies that are applying are displayed, as shown in Figure 3-40.
 Exam Tip
Exam Tip
You can use the Windows PowerShell Get-GPinheritance cmdlet to view current GPO inheritance, and the Set-GPinheritance cmdlet to modify inheritance.
Configure enforced policies
Given that an administrator of an OU can block inheritance on that OU, effectively preventing all configured settings in GPOs linked higher up the OU tree, this might not always be desirable. For example, as a domain-level administrator, you might want to ensure that your domain-linked GPO settings apply to all computers (or users) irrespective of any block settings configured by down-level admins.
This is where enforcement is useful. GPOs can be enforced, which is to say that using block inheritance cannot block them.
 Exam Tip
Exam Tip
Whereas you configure blocking on a per-OU basis, you configure enforcement on a per-policy basis.
To configure GPO enforcement, use the following procedure:
1. Open Group Policy Management.
2. Locate the GPO you want to enforce, and right-click it, as shown in Figure 3-41.
3. Click Enforced.
As shown in Figure 3-42, the padlock symbol on the GPO indicates enforcement. In the details pane, the Enforced column is set to Yes.
You can see the effect of the enforcement on lower level OUs. In the Sales OU, there is a block configured. But due to the enforcement of the Default Domain Policy, this policy appears, as shown in Figure 3-43, on the Group Policy Inheritance tab in the details pane for the Sales OU. This means that enforcement trumps blocking.
 Exam Tip
Exam Tip
When you enforce a GPO, you also change its precedence. In Figure 3-43, the Default Domain Policy now has the highest precedence (but the lowest precedence value). Conflicting settings in the Default Domain Policy override those in the other linked GPOs.
Configure security filtering and WMI filtering
Until now, we have assumed that all of the configured settings in one or more GPOs should apply to all objects in an OU, either directly through a link, or indirectly, through inheritance. By using Block Inheritance and Enforced, you can control the default behavior, but this is still at the whole container level.
What if you want to apply the settings of a GPO to most, but not all the computers in a specific OU? Or maybe you want a restrictive security GPO to apply to most users in a department, but not all of them. Perhaps you create a GPO to distribute software updates, but don’t want it to apply to computers that do not meet the minimum hardware requirements for the software. These are all examples of situations in which GPO security or WMI filtering can be useful.
Configuring security filtering
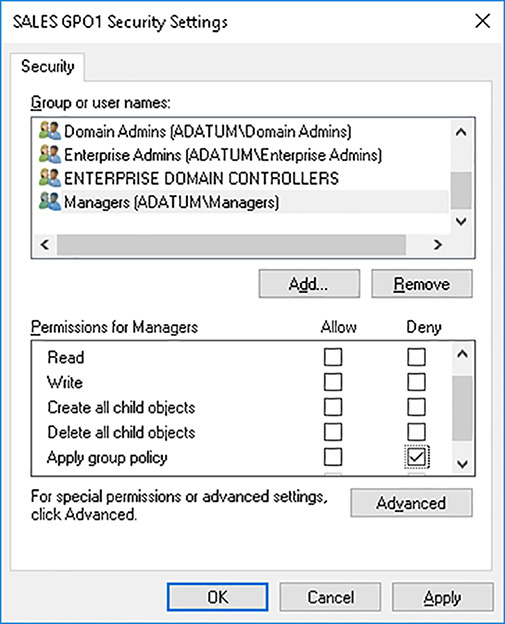
A security filter for a GPO works on the simple premise that for a policy to apply to an object, that object requires at least Read and Apply group policy permissions on the GPO. These permissions are applied by default, of course, to all GPOs. You can see the permissions assigned to the Authenticated Users group in Figure 3-44.
You can use security filtering to implement one of two strategies:
![]() Applies To Everyone But In this scenario, you want your GPO settings to apply to all users (or computers) except for one (or a couple) of users or computers. To achieve this, you grant the specific user (or computer) the Deny Apply Group Policy permission. This prevents that user (or computer) from applying the policy.
Applies To Everyone But In this scenario, you want your GPO settings to apply to all users (or computers) except for one (or a couple) of users or computers. To achieve this, you grant the specific user (or computer) the Deny Apply Group Policy permission. This prevents that user (or computer) from applying the policy.
![]() Applies To Only In this scenario, you want the policy to apply only to a specific user or computer. This begs the question as to whether the user or computer should be in the OU in the first place. Assuming there are sound reasons for the object’s presence in the OU, you can remove the Allow Apply group policy permission from the Authenticated Users group. Next, grant the user or computer the Allow Read and Allow Apply Group Policy permissions on the GPO.
Applies To Only In this scenario, you want the policy to apply only to a specific user or computer. This begs the question as to whether the user or computer should be in the OU in the first place. Assuming there are sound reasons for the object’s presence in the OU, you can remove the Allow Apply group policy permission from the Authenticated Users group. Next, grant the user or computer the Allow Read and Allow Apply Group Policy permissions on the GPO.
Be careful that you do not remove the Allow Read permission for the Authenticated Users group. This is because unless this group has Read permissions, the policy is not processed by the client at all.
Note Security update 3159398, June 2016
Without this update, GPOs are retrieved in the security context of the user account. With this update applied to your computers, client computers retrieve GPOs within the security context of the computer account. If you remove the Allow Read permission from the Authenticated Users group, your computers cannot retrieve the policy from the domain controller.
Implement the ‘Applies to Everyone But’ Strategy
To implement this strategy, you must grant a user or group the deny Apply Group Policy permission. To do this, use must use the Delegation tab:
1. In the Group Policy Management console, in the Group Policy Objects container, select the appropriate GPO.
2. In the details pane, click the Delegation tab, as shown in Figure 3-45.
3. Click Advanced, and in the GPO Security Settings dialog box, click Add.
4. In the Select Users, Computers, Service Accounts, Or Groups dialog box, type the name of the user or group you want to exclude, and then click OK.
5. The user or group that you select is granted the Allow Read permission automatically. Clear the Allow Read permission check box, and then select the Deny check box for Apply Group Policy, as shown in Figure 3-46, and then click OK.
6. You receive a security warning that Deny permissions override other permissions. Click Yes to continue.
7. The user or group you specified is listed on the Delegation tab with Custom permissions, as shown in Figure 3-47.
Implement the ‘Applies to only’ strategy
To implement this strategy, you must remove the Authenticated Users security setting and then grant a specific security group the Allow Apply Group Policy permission. Use the following procedure:
1. In the Group Policy Management console, in the Group Policy Objects container, select the appropriate GPO.
2. On the Scope tab, in the Security Filtering section, select the Authenticated Users group, as shown in Figure 3-48, click Remove, and then click OK.
3. Click Add, and in the Select User, Computer, Or Group dialog box, type the name of the user or group to which you want the GPO to apply, and then click OK. The Security Filtering list contains only the object to which the GPO will apply, as shown in Figure 3-49.
You can view the configured permissions by using the Delegation tab, as shown in Figure 3-50, and selecting the appropriate security principal.
Configuring WMI filtering
Security filtering works well when you can select a security principal that readily identifies the collection of users, groups, or computers that you want to configure. Sometimes, however, there is no such security principal. This is where using WMI filtering can be useful. For a GPO to apply to a computer, it must meet the conditions of a WMI filter.
A WMI filter is based on a WMI query that defines the properties of the objects that you are seeking. For example, you might want to select only those computers installed with Windows 10 or Windows Server 2016. The WMI filter looks something like this:
SELECT * FROM Win32_OperatingSystem WHERE Version LIKE "10.%"
To create a WMI filter, use the following procedure:
1. In the Group Policy Management console, in the navigation pane, click the WMI Filters node.
2. Right-click WMI Filters, and then click New.
3. In the New WMI Filter dialog box, in the Name box, type the name of your WMI filter, type a Description, and then click Add.
4. In the WMI Query dialog box, shown in Figure 3-51, in the Query box, type the WMI query, and then click OK.
5. In the New WMI Filter dialog box, shown in Figure 3-52, click Save.
6. Your newly defined WMI filter is listed in the Group Policy Management console in the WMI Filters node, as shown in Figure 3-53.
After you have created the filter, you apply the filter to the GPO using the following procedure:
1. In the Group Policy Management console, in the Group Policy Objects container, select the appropriate GPO.
2. On the Scope tab, in the WMI Filtering section, in the This GPO Is Linked To The Following WMI Filter list, click your WMI filter.
3. In the Group Policy Management pop-up dialog box, click Yes.
4. In Group Policy Management, the WMI Filtering is configured, as shown in Figure 3-54.
In this example, we created a WMI filter with a single WMI query. However, you can easily build complex, multi-condition queries for more complex situations. In addition, once you have created your WMI filters, you can apply them to multiple GPOs; you do not need to create them separately for each GPO.
Need More Review? Create the WMI filters
To review further details about using WMI filters, refer to the Microsoft TechNet website at https://technet.microsoft.com/library/jj899801(v=ws.11).aspx.
Configure loopback processing
In some organizations, users sign in from more than one computer. If you are using GPOs to configure these users’ desktop settings, it is important to understand how GPOs apply when a user, in one OU, signs in at a computer from another OU. When you use GPOs to configure desktop settings, by default, a user’s settings are applied from the GPOs linked to the user object in AD DS. In other words, the settings that apply are determined by the OU in which the user object is stored.
However, there might be situations in which you want certain computers to present a standard desktop, irrespective of who signs in. For example, you might have kiosk computers in a public area within your organization, and it might be desirable for these computers to have an enforced, standard desktop.
Loopback processing enables you to change the default behavior so that instead of the desktop settings applying based on the user’s OU, the settings that apply are determined by the location of the computer object in AD DS.
Note Desktop settings
Remember that desktop settings are stored in the User Configuration node of a GPO, and that it is therefore logical, in most situations, that the GPO that applies the User Configuration be the GPO(s) linked to the user’s location in AD DS.
To enable GPO loopback processing, you edit the following location in the Administrative Templates folder of an appropriate GPO:
1. Open the appropriate GPO for editing.
2. In the Group Policy Management Editor, under the Computer Configuration node, navigate to PoliciesAdministrative TemplatesSystem, and then select the Group Policy folder, as shown in Figure 3-55.
3. In the details pane, double-click the Configure User Group Policy Loopback Processing Mode policy setting.
4. In the Configure User Group Policy Loopback Processing Mode dialog box, shown in Figure 3-56, click Enabled, and then select the Mode. You can choose between:
![]() Replace Replaces the user list of GPOs entirely with the list of GPOs obtained for the computer during startup. Only the User Configuration settings of the computer’s GPOs apply to the user. Use this mode to apply standard configurations, such as on a kiosk computer; for example, in a library or classroom.
Replace Replaces the user list of GPOs entirely with the list of GPOs obtained for the computer during startup. Only the User Configuration settings of the computer’s GPOs apply to the user. Use this mode to apply standard configurations, such as on a kiosk computer; for example, in a library or classroom.
![]() Merge Appends rather than overwrites the User Configuration node settings from the GPO list obtained for the computer during startup to the list of user GPOs obtained for the user during sign in. The computer settings have precedence because they apply last. Use this mode to apply additional settings to users’ desktop configurations. For example, when a user signs in at a conference room computer, they receive their usual desktop settings, but the computer GPOs configure certain restrictions, or appearance settings.
Merge Appends rather than overwrites the User Configuration node settings from the GPO list obtained for the computer during startup to the list of user GPOs obtained for the user during sign in. The computer settings have precedence because they apply last. Use this mode to apply additional settings to users’ desktop configurations. For example, when a user signs in at a conference room computer, they receive their usual desktop settings, but the computer GPOs configure certain restrictions, or appearance settings.
5. Click OK.
Client computers must receive this GPO update before the loopback processing mode is configured on the local computer. This might require a restart.
Configure and manage slow-link processing and Group Policy caching
If your users work from home, or branch offices connected by slow links, you might need to configure GPO processing to account for those slow links. You can configure two options:
![]() Slow Link Detection If a link between the client and the domain controller serving the GPOs is slower than 500 kilobits per second, and the Configure Group Policy slow link detection setting is enabled, the client processes GPOs differently. Specifically, some client-side extensions are disabled and do not process related policy settings. This helps optimize the available bandwidth. When a slow link is detected, the following client-side extensions are disabled:
Slow Link Detection If a link between the client and the domain controller serving the GPOs is slower than 500 kilobits per second, and the Configure Group Policy slow link detection setting is enabled, the client processes GPOs differently. Specifically, some client-side extensions are disabled and do not process related policy settings. This helps optimize the available bandwidth. When a slow link is detected, the following client-side extensions are disabled:
![]() Internet Explorer maintenance
Internet Explorer maintenance
![]() Software Installation policy
Software Installation policy
![]() Folder Redirection policy
Folder Redirection policy
![]() Scripts policy
Scripts policy
![]() Internet Protocol security (IPsec) policy
Internet Protocol security (IPsec) policy
![]() Wireless policy
Wireless policy
![]() Disk quota policy
Disk quota policy
![]() Caching When a client detects a slow link, and caching is enabled, a cached version of the applicable GPOs are applied by the client-side extensions. Two values are used to determine whether a link is slow, and therefore whether to use caching. These are:
Caching When a client detects a slow link, and caching is enabled, a cached version of the applicable GPOs are applied by the client-side extensions. Two values are used to determine whether a link is slow, and therefore whether to use caching. These are:
![]() Slow Link Value The default is 500 milliseconds. If the GPO client does not receive a response from a domain controller in this interval, the link is determined to be slow.
Slow Link Value The default is 500 milliseconds. If the GPO client does not receive a response from a domain controller in this interval, the link is determined to be slow.
![]() Timeout Value The default is 5000 milliseconds. After this period, the client assumes there is no network connectivity and caching is used.
Timeout Value The default is 5000 milliseconds. After this period, the client assumes there is no network connectivity and caching is used.
To enable and configure slow link detection, use the following procedure:
1. Open the appropriate GPO for editing.
2. In the Group Policy Management Editor, under the Computer Configuration node, navigate to PoliciesAdministrative TemplatesSystem, and then select the Group Policy folder, as shown in Figure 3-55.
3. In the details pane, double-click the Configure Group Policy slow link detection setting policy setting.
4. In the Configure Group Policy slow link detection setting dialog box, shown in Figure 3-57, click Enabled, and then configure the connection speed. Remember the default is 500 kbps. Click OK.
To enable and configure caching, use the following procedure:
1. In the details pane, double-click the Configure Group Policy Caching policy setting.
2. In the Configure Group Policy Caching dialog box, shown in Figure 3-58, click Enabled, and then configure the Slow Link Value and Timeout value. Click OK.
Client computers must receive these GPO updates before the slow link and caching settings are configured on the local computer. This might require a restart.
Configure client-side extension behavior
We have already mentioned client-side extensions, but it is worth exploring a little more about the configuration options that you have for controlling them and how they process GPO settings.
Generally, client-side extensions only apply GPO settings if those settings are changed since they were last applied. This improves performance. However, you can control this behavior with the Process Even If The Group Policy Objects Have Not Changed value in the appropriate client-side extension setting in a GPO.
For example, use the following procedure to enforce application of GPO settings for the security client-side extension:
1. Open the appropriate GPO for editing.
2. In the Group Policy Management Editor, under the Computer Configuration node, navigate to PoliciesAdministrative TemplatesSystem, and then select the Group Policy folder.
3. In the details pane, double-click the Configure Security Policy Processing policy setting.
4. As shown in Figure 3-59, click Enabled, and then select the Process Even If The Group Policy Objects Have Changed check box.
5. You can also determine whether the setting is updated while the computer is in use during the automatic refresh intervals for GPOs. The default behavior is that the client-side extension will process updates. If you want to change this, select the Do Not Apply During Periodic Background Processing check box. Click OK.
To configure all client-side extensions, locate the appropriate setting in the Group Policy folder, and configure the two values described above. The required settings are shown in Figure 3-60.
Force a Group Policy update
When you are making changes to GPOs and want to verify the application of those settings, you probably don’t want to wait for the settings to automatically refresh. If you don’t want to wait, you can restart a computer, or for many user settings, you can sign out and sign back in.
However, you can also use the GPUpdate.exe command-line tool from a command prompt to force the updates to apply. To refresh GPOs settings, use the following procedure:
1. Open a command prompt.
2. Run the gpupdate /force command, as shown in Figure 3-61.
Note Windows PowerShell
You can also use the Windows PowerShell invoke-gpupdate cmdlet.
3. You might need to sign out or even restart your computer, depending on the setting.
To review further details about the gpupdate syntax and usage, refer to the Microsoft TechNet website at https://technet.microsoft.com/library/hh852337(v=ws.11).aspx.
Skill 3.3: Configure Group Policy settings
So far, we have looked at how to create and link GPOs to your AD DS container objects, such as sites, domains, and OUs. But to properly manage the users and devices in your organization, you must also know how to configure common settings by using GPOs.
In this skill, you learn how to use GPOs to deploy software, how to create and configure startup and login scripts, how to enforce security settings, and when to use administrative templates to control other settings.
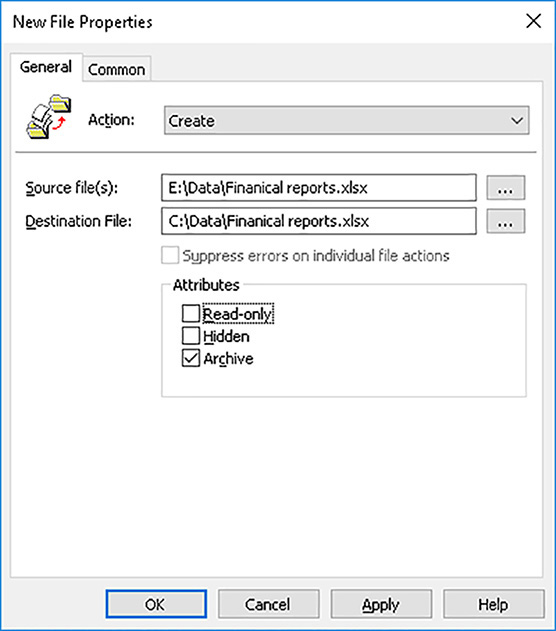
Configure software installation
One of the most common tasks for any network administrator is that of deploying and maintaining software. Windows Server 2016 provides several different ways for you to achieve this objective, including using GPOs.
With GPO-based software deployment, you can deploy software to either computers, irrespective of who is using the computer, or to users, irrespective of which computer they are using. This is possible because the Software Settings folder exists under both the Computer Configuration and User Configuration nodes in the Group Policy Management Editor, as shown in Figure 3-62.
Using GPOs to deploy software offers several benefits:
![]() It is relatively simple and certainly quick to set up.
It is relatively simple and certainly quick to set up.
![]() You don’t need any additional infrastructure because GPOs are part of AD DS.
You don’t need any additional infrastructure because GPOs are part of AD DS.
![]() You require no client-side agent software because the built-in GPO client-side extensions handle the deployment.
You require no client-side agent software because the built-in GPO client-side extensions handle the deployment.
However, before deciding whether to use GPOs to deploy software, you should consider the following potential disadvantages:
![]() You can only deploy certain types of packages using GPOs; specifically, you must use .msi installer packages.
You can only deploy certain types of packages using GPOs; specifically, you must use .msi installer packages.
![]() There are no controls over when software deployment takes place.
There are no controls over when software deployment takes place.
![]() If you are deploying multiple packages, you have no control over which package is deployed first.
If you are deploying multiple packages, you have no control over which package is deployed first.
![]() There are no reporting features in GPO software deployment making it difficult to determine whether deployment was successful.
There are no reporting features in GPO software deployment making it difficult to determine whether deployment was successful.
Given these considerations, it is likely that using GPOs to deploy and maintain application software is only suitable for organizations supporting relatively few computers within their AD DS forest.
Preparation
The first stage in using GPOs to deploy software is to store the apps that you want to deploy in an accessible location. Remember that your apps must be in the form of Windows Installer files; that is, .msi files. Place the .msi files into a shared folder on a network server. Ideally, this folder is part of a DFSR folder structure to ensure high availability of the installation files. If you are using the same shared folder for software deployment, configure the default package location. To do this, use the following procedure:
1. Open the appropriate GPO for editing, and in the Group Policy Management Editor, navigate to the Computer Configuration, Policies, Software Settings folder, and then click Software Installation.
2. Right-click Software Installation, and then click Properties.
3. In the Software Installation Properties dialog box, shown in Figure 3-63, in the Default Package Location box, type the path to the software .msi files, and then click OK.
4. If you want, repeat these steps for the User Configuration, Policies, Software Settings, and Software Installation Properties.
Deployment
Next, you must decide how you want the software to be deployed. You have two choices, which are:
![]() Assigning Assigned software is automatically installed without user intervention.
Assigning Assigned software is automatically installed without user intervention.
![]() Publishing Published software is available only if the user chooses to install it.
Publishing Published software is available only if the user chooses to install it.
You can assign software to both users and computers. However, you can only publish software to users. To assign a software application to a computer, use the following procedure:
1. Open the appropriate GPO for editing, and in the Group Policy Management Editor, navigate to the Computer Configuration, Policies, Software Settings folder, and then click Software Installation.
2. Right-click Software Installation, point to New, and then click Package.
3. In the Open dialog box, browse and locate your software installation package, as shown in Figure 3-64.
4. Click Open, and then in the Deploy Software dialog box, shown in Figure 3-65, click Assigned, and then click OK.
Your software package is now ready for deployment, and is listed in the Software Installation folder. As clients refresh the GPO, the new setting applies. In this instance, because you are deploying a package by assigning to a computer, the package deploys following the next computer restart after the GPOs refresh on the computer. The process for assigning to a user is broadly the same.
To deploy a package by publishing to a user, use the following procedure:
1. Open the appropriate GPO for editing, and in the Group Policy Management Editor, navigate to the User Configuration, Policies, Software Settings folder, and then click Software installation.
2. Right-click Software installation, point to New, and then click Package.
3. In the Open dialog box, browse and locate your software installation package, and then click Open.
4. In the Deploy Software dialog box, shown in Figure 3-66, click Published, and then click OK.
Your software package is now ready for deployment, and is listed in the Software Installation folder. As clients refresh the GPO, the new setting applies. In this instance, because you are deploying a package by publishing to a user, the package is available for deployment by using the Control Panel once the GPOs are refreshed, as shown in Figure 3-67.
If you plan on deploying many software packages by using Publishing, you can create application categories and designate an appropriate category for your package during the deployment phase. To configure categories, click the Categories tab in the Software Installation Properties node shown in Figure 3-63, and add the required categories.
Aside from deploying software using assignment or publishing, you can also make software available by using file extension deployment. This works when a user attempts to open a file of a specific type; for example, they double-click on a .doc file. You can configure GPO software installation to deploy a specific application when a user invokes a specific file type. To do this, you configure the File Extensions tab of the Software Installation node.
Maintenance
After you have successfully configured and deployed the required software, you must be ready to maintain that software. This might involve upgrading or redeploying the software.
To redeploy a software package:
1. In the Group Policy Management Editor, in the Software Installation folder, right-click the appropriate software package, and then click Redeploy Application.
2. At the confirmation prompt, click Yes.
To upgrade a package, use the following procedure:
1. Right-click Software Installation, point to New, and then click Package.
2. In the Open dialog box, browse and locate your software installation package.
3. In the Deploy Software dialog box, click Advanced, and then click OK.
4. Click the Upgrades tab.
5. Click Add, and select the software package that is getting upgraded.
6. As shown in Figure 3-68, in the Add Upgrade Package dialog box, choose whether the existing package is removed before installation of the new package, or whether the new package can upgrade over the existing package. Click OK.
7. In the New Package Properties dialog box, shown in Figure 3-69, click OK.
Removal
Once a package reaches the end of its useful life in your organization, you must remove it. You can achieve this by using GPO software installation. Use the following procedure to remove any unwanted package from your organization:
1. In the Group Policy Management Editor, in the Software Installation folder, right-click the appropriate software package, and then click Remove.
2. In the Remove Software dialog box, shown in Figure 3-70, select one of the following options, and then click OK:
![]() Immediately uninstall the software from users and computers.
Immediately uninstall the software from users and computers.
![]() Allows users to continue to use the software, but prevent new installations.
Allows users to continue to use the software, but prevent new installations.
Configure scripts
It’s often very useful to be able to run a script during logon, or when a computer starts up. You might want to use the script to set the user’s environment, to map network drives, or to install software updates.
Windows Server 2016 enables you to use GPOs to configure scripts to run during computer startup or shutdown, and during user sign in or sign out. The procedure for configuring these various scripts is essentially the same. For example, to configure a logon script to run, use the following high-level procedure:
1. Open the Group Policy Management Editor for the appropriate GPO.
2. To configure sign in and sign out scripts, expand the User Configuration node, and navigate to Policies, Windows Settings, Scripts (Logon/Logoff), as shown in Figure 3-71.
3. In the details pane, double-click the appropriate node. For example, to setup a script that runs at sign in, double-click Logon.
4. In the Logon Properties dialog box, to use a Windows PowerShell script, click the PowerShell Scripts tab.
5. Click Add.
6. In the Add A Script dialog box, click Browse, locate your Windows PowerShell script, and then click OK.
Note Paths
You must place your scripts in a shared folder to which the client computers have access and at least read permissions. Specify the path in the form of a UNC.
7. See the Logon Properties dialog box, on the PowerShell Scripts tab, shown in Figure 3-72; in the For This GPO, Run Scripts In The Following Order list, specify whether you want your Windows PowerShell script to run first or last. Otherwise, click Not Configured.
8. If you have additional scripts to run, add them to the PowerShell Scripts list, and then click OK.
9. Refresh the GPOs on the target computers, and then sign in to test that the script runs correctly.
The process for creating and configuring scripts for logoff, and also for startup and shutdown, are almost identical. In addition to using Windows PowerShell, you can also use other scripting languages, including VBScript.
Need More Review? Script Center Home
To find out more about using scripts, refer to the Microsoft TechNet website at https://technet.microsoft.com/scriptcenter/bb410849.aspx.
Import security templates
One of the most important responsibilities of network administrators is maintaining the security of their organization’s network infrastructure. To help you make this task easier, you can use GPOs to secure your network. However, even using GPOs to secure network and related settings can be a tedious and time-consuming process, especially if you want to apply the same settings to other parts of your organization. For example, if, having secured one domain in your forest with GPO-based security settings, you had to repeat the process with the same, or very similar, settings. You can use security templates to help mitigate this issue.
With the Security Templates console, shown in Figure 3-73, you can configure the following security settings:
![]() Account Policies Includes password, account-lockout, and Kerberos policies.
Account Policies Includes password, account-lockout, and Kerberos policies.
![]() Local Policies Includes audit, user rights, and security options polices.
Local Policies Includes audit, user rights, and security options polices.
![]() Event Log Enables you to define event log settings.
Event Log Enables you to define event log settings.
![]() Restricted Groups Allows you to define and configure restricted groups.
Restricted Groups Allows you to define and configure restricted groups.
![]() System Services Enables you to define startup behavior for system services.
System Services Enables you to define startup behavior for system services.
![]() Registry Allows you to define registry security settings.
Registry Allows you to define registry security settings.
![]() File System Enables you to centrally define file and folder permissions.
File System Enables you to centrally define file and folder permissions.
To create and use security templates with GPOs, use the following procedure:
1. Open the management console, and add the Security Templates snap-in.
2. Expand the Security Templates node in the navigation pane, and then click the top-level folder beneath that node. Right-click the folder, and then click New Template.
3. In the unlabeled dialog box, in the Template Name text box, type the name. For example, type High Security Settings, and then click OK.
4. Click on the High Security Settings node, or whatever you named your template.
5. Configure the required security settings to help to secure your organization.
After you have created your template and configured the required security settings, save the template. To do this, right-click the template, and click Save. You can now apply the template to your GPO(s). To do this, use the following procedure:
1. Open the required GPO for editing.
2. In the Group Policy Management Editor, select the Security Settings folder in the Computer ConfigurationPoliciesWindows Settings node in the navigation pane.
3. Right-click the Security Settings folder, and then click Import Policy, as shown in Figure 3-74.
4. In the Import Policy From dialog box, shown in Figure 3-75, double-click the policy you earlier created.
5. Your settings are applied.
You can use the Security Compliance Manager to help you choose and configure appropriate security settings for your organization. The Security Compliance Manager is regularly updated with security baselines helping to make it easier for you to select and implement appropriate security settings in your organization.
Need More Review? Security Compliance Manager
To find out more about using the Security Compliance Manager, visit the Microsoft TechNet website at https://technet.microsoft.com/solutionaccelerators/cc835245.aspx.
Configure folder redirection
Administrators have long sought to centralize and sometimes standardize their users’ desktops. All versions of Windows Server have supported the notion of roaming desktop profiles; these enabled users to sign in at any computer in the AD DS forest and automatically apply their user-related settings. Administrators could also assign a home folder on a network server for their users; this enables users to store their personal data on a file server, making their data accessible from other computers where they can sign in.
Although you can still use roaming profiles and home folders, in Windows Server 2016, you can use Folder Redirection to help to centralize and, if desired, standardize your users’ desktop and app settings. You implement Folder Redirection as a feature of GPOs.
Folder Redirection gets its name from the fact that a number of local folders, stored as part of a user’s personal data and settings, can be stored on file server shared folders through redirection. The following local folders can be redirected in this way:
![]() AppDataRoaming
AppDataRoaming
![]() Desktop
Desktop
![]() Start Menu
Start Menu
![]() Documents
Documents
![]() Pictures
Pictures
![]() Music
Music
![]() Videos
Videos
![]() Favorites
Favorites
![]() Contacts
Contacts
![]() Downloads
Downloads
![]() Links
Links
![]() Searches
Searches
![]() Saved Games
Saved Games
Folder preparation
Before you can redirect folders, you must create the underlying shared folder structure. It is usual to redirect users’ folders to a common shared folder; this folder is referred to as the root folder.
Generally, you assign permissions to security groups that contain the relevant users on the required folders. For example, if you redirect folders by department, you might assign the Sales global security group the required permissions on the root folder for sales users; likewise, the marketing security group for users in that department, and so on.
Table 3-1 shows the correct NTFS folder permissions.
Because your users will access the root folder and its subfolders through a Windows Server shared folder, you must assign shared folder permissions. Table 3-2 shows the appropriate shared folder permissions.
Thereafter, each user requires their own subfolder beneath the root folder. If you create the root folder with the correct permissions, Windows Server creates the user folders automatically during configuration of folder redirection, and applies the correct permissions. However, Table 3-3 shows the required permissions on the users’ individual folders.
Available redirection options
When you enable folder redirection, you can configure its behavior in a number of different ways depending on what you want to achieve. The available options are:
![]() None When you select this setting, which is the default value, folder redirection is disabled.
None When you select this setting, which is the default value, folder redirection is disabled.
![]() Basic Used when you want to:
Basic Used when you want to:
![]() Redirect users’ folders to a common area. That is, you do not want to redirect users’ folders to a different folder based on their departmental membership. In this instance, all users’ folders are redirected to a single folder root. Each user has a unique folder beneath the root.
Redirect users’ folders to a common area. That is, you do not want to redirect users’ folders to a different folder based on their departmental membership. In this instance, all users’ folders are redirected to a single folder root. Each user has a unique folder beneath the root.
![]() Ensure privacy of user data. Because each user has their own folder, and because Windows Server assigned the appropriate permissions (see Table 3-3), each user can access only their own folder contents.
Ensure privacy of user data. Because each user has their own folder, and because Windows Server assigned the appropriate permissions (see Table 3-3), each user can access only their own folder contents.
![]() Advanced Used when you want to redirect groups of users to a common shared folder.
Advanced Used when you want to redirect groups of users to a common shared folder.
![]() Follow The Documents Folder If you choose to redirect users’ Documents folder as part of your folder redirection implementation, you can redirect the following folders to the same location without needing to individually configure them: Pictures, Music, and Videos.
Follow The Documents Folder If you choose to redirect users’ Documents folder as part of your folder redirection implementation, you can redirect the following folders to the same location without needing to individually configure them: Pictures, Music, and Videos.
Enabling and configuring basic folder redirection
You use the Group Policy Management Editor to enable and configure folder redirection. To enable and configure basic folder redirection, use the following procedure:
1. In the Group Policy Management console, locate the appropriate GPO, and open for editing.
2. In the Group Policy Management Editor, navigate to the User Configuration node, and then select the Policies folder.
3. Expand Windows Settings, and then expand Folder Redirection.
4. Select the appropriate folder from the list, as shown in Figure 3-76.
5. Right-click the selected folder, and then click Properties.
6. In the Folder Properties dialog box, shown in Figure 3-77, on the Target tab, in the Setting list, click Basic. You redirect your users’ folders to the same location.
7. In the Target folder location section, select from the following options.
![]() Create A Folder For Each User Under The Root Path If you select this option, Windows Server creates a folder in the form \servershare\%Username%Folder, where %Username% is the user account name, and Folder is the name of the folder being redirected. For example: \LON-SVR1RedirectedClaireDocuments.
Create A Folder For Each User Under The Root Path If you select this option, Windows Server creates a folder in the form \servershare\%Username%Folder, where %Username% is the user account name, and Folder is the name of the folder being redirected. For example: \LON-SVR1RedirectedClaireDocuments.
![]() Redirect To The Following Location If you select this option, Windows Server creates a single folder for multiple users, and all users use the same path for the redirected folder.
Redirect To The Following Location If you select this option, Windows Server creates a single folder for multiple users, and all users use the same path for the redirected folder.
![]() Redirect To The Local Userprofile Location If you select this option, Windows Server moves the location of the redirected folder to the user’s local profile under the local Users folder.
Redirect To The Local Userprofile Location If you select this option, Windows Server moves the location of the redirected folder to the user’s local profile under the local Users folder.
![]() Redirect To The User’s Home Directory This option is only available for the Documents folder. Windows Server redirects the folder to the user’s home folder.
Redirect To The User’s Home Directory This option is only available for the Documents folder. Windows Server redirects the folder to the user’s home folder.
8. Enter the UNC for the root folder.
9. Click OK, and in the Warning dialog box, click Yes.
When a user signs in that is affected by your GPO, their folder is redirected to the desired location, and Windows Server creates the required user folder beneath the root folder you specified, assuming you created it with the correct permissions.
Note When to use basic folder redirection
It is common to use basic redirection for folders that contain users’ personal data. That means you are using folder redirection to move the contents of personal folders to a server. Typical folders to redirect using basic are: AppData/Roaming, Documents, Pictures, Favorites, Contacts, Links, and Searches. Music, Videos, Downloads, and Saved Games are less typical because of the potential size of the content.
Enabling and configuring advanced folder redirection
To enable and configure advanced folder redirection, use the following procedure:
1. In the selected GPO, in the Group Policy Management Editor, navigate to the Folder Redirection folder under the User Configuration node.
2. Select the appropriate folder from the list.
3. Right-click the selected folder, and then click Properties.
4. In the Folder Properties dialog box, on the Target tab, in the Setting list, click Advanced, as shown in Figure 3-78.
5. Under the Security Group Membership heading, click Add.
6. In the Specify Group And Location dialog box, shown in Figure 3-79, in the Security Group Membership text box, type the name of the security group.
7. In the Target Folder Location section, select from the following options:
![]() Create A Folder For Each User Under The Root Path
Create A Folder For Each User Under The Root Path
![]() Redirect To The Following Location
Redirect To The Following Location
![]() Redirect To The Local Userprofile Location
Redirect To The Local Userprofile Location
![]() Redirect To The User’s Home Directory
Redirect To The User’s Home Directory
8. Enter the UNC for the root folder, and then click OK.
9. In the Folder Properties dialog box, repeat this procedure for other groups that you want to configure.
10. When you have configured all groups, in the Folder Properties dialog box, shown in Figure 3-80, click OK, and at the Warning, click Yes.
Note When to use advanced folder redirection
It is common to use advanced redirection to create standard desktops or Start menu settings. Therefore, it is more common to implement advanced folder redirection for the Desktop and Start Menu folders. If you use advanced redirection in this way, it is common to use the Redirect to the following location option so that all users in each department use the same Desktop and Start Menu.
The Settings tab
For both basic and advanced redirection, when you select and configure the folder redirection targets, as shown, for example, in Figure 3-80, you can also configure options on the Settings tab, shown in Figure 3-81:
![]() Grant The User Exclusive Rights To Folder Ensures that each user has exclusive rights to his own folder. Enabled by default.
Grant The User Exclusive Rights To Folder Ensures that each user has exclusive rights to his own folder. Enabled by default.
![]() Move The Contents Of Folder To The New Location If the local user profile contains content in the redirected folder, that content is moved to the redirected folder. Enabled by default.
Move The Contents Of Folder To The New Location If the local user profile contains content in the redirected folder, that content is moved to the redirected folder. Enabled by default.
![]() Also Apply Redirection Policy To Windows 2000, Windows 2000 Server, Windows XP, And Windows Server 2003 Operating Systems Enables support for older operating systems, which is not enabled by default.
Also Apply Redirection Policy To Windows 2000, Windows 2000 Server, Windows XP, And Windows Server 2003 Operating Systems Enables support for older operating systems, which is not enabled by default.
![]() Policy Removal If you remove the folder redirection setting(s) from the GPO, this option determines what happens to the content in the redirected folder(s).
Policy Removal If you remove the folder redirection setting(s) from the GPO, this option determines what happens to the content in the redirected folder(s).
![]() Leave the folder in the new location when policy is removed.
Leave the folder in the new location when policy is removed.
![]() Redirect the folder back to the local userprofile location when policy is removed.
Redirect the folder back to the local userprofile location when policy is removed.
Configure administrative templates
Much of the configuration that you can achieve with GPOs is made available through the use of Administrative Templates. All the changes you make in the Administrative Templates nodes of a GPO result in changes to the affected computers’ registry settings.
As with all other GPO settings, these changes are grouped into computer-related settings that modify the system elements of the registry, and user-related settings that modify the user elements of the registry. However, some settings in Administrative Templates have duplicate settings in both the Computer Configuration, and User Configuration nodes.
 Exam Tip
Exam Tip
In the situation where you configure both these settings, the Computer Configuration takes precedence.
Because directly editing the registry can be complex, and potentially error-prone, the Administrative Templates nodes are represented in a more logical, simpler-to-navigate folder-like structure, as shown in Figure 3-82.
This structure groups related elements together:
![]() Computer Configuration:
Computer Configuration:
![]() Control Panel
Control Panel
![]() Network
Network
![]() Printers
Printers
![]() Server
Server
![]() Start Menu and Taskbar
Start Menu and Taskbar
![]() System
System
![]() Windows Components
Windows Components
![]() All Settings
All Settings
![]() User Configuration:
User Configuration:
![]() Control Panel
Control Panel
![]() Desktop
Desktop
![]() Network
Network
![]() Shared Folders
Shared Folders
![]() Start Menu and Taskbar
Start Menu and Taskbar
![]() System
System
![]() Windows Components
Windows Components
![]() All Settings
All Settings
Both of the All Settings folders represented a consolidated view of all the settings in that particular node.
Administrative template files
Although administrative templates are represented as folders in the Group Policy Management Editor, they are, in fact, stored as files on the file system of the domain controller. In earlier versions of Windows Server, these filenames had a .adm extension. In Windows Server 2016, these files have a .admx extension.
These .admx files are language neutral and in multilingual organizations, they are associated with .adml files that contain the language specific elements required to configure settings. For example, the .admx files are stored in the WindowsPolicyDefinitions folder, and the .adml files are stored in subfolders beneath the WindowsPolicyDefinitions folder, such as en-US for the US English locale.
Configure a central store
Understanding the structure of the .admx files enables you to create your own administrative templates, if needed, to configure specific settings for your users, computers, and installed apps. However, rather than creating the .admx files on a domain controller and manually copying them to all domain controllers in your forest, you can implement a central store of the Administrative Templates files. Using a central store helps to ensure that:
![]() All administrative templates are the same on all domain controllers.
All administrative templates are the same on all domain controllers.
![]() It is easier to update your administrative templates because you need to only update a single .admx file—in the central store—when changes are needed.
It is easier to update your administrative templates because you need to only update a single .admx file—in the central store—when changes are needed.
The central store is located in the SYSVOL shared folder. Specifically, for the Adatum.com domain:
1. In the \Adatum.comSYSVOLAdatum.comPolicies folder, create a PolicyDefinitions subfolder.
2. Populate this new PolicyDefinitions folder with the existing contents of the WindowsPolicyDefinitions folder on a domain controller.
3. Add new or changed .admx and .adml files to the SYSVOL version of PolicyDefinitions.
 Exam Tip
Exam Tip
When a new operating system or service pack is released, you must update the PolicyDefinitions subfolder. For example, Windows 10 and Microsoft Office 2016 have new configuration options available that can be made use of by updating your PolicyDefinitions folder.
Import a custom administrative template file
If you want to use your own .admx files, or simply add new ones that you downloaded, you must know how to make them available in the Group Policy Management Editor console. This process is known as importing a custom template.
1. Download or create your administrative template .admx file.
2. Copy them to the central store.
3. Configure the Administrative Template settings in the Group Policy Management Editor for the appropriate GPO(s).
4. Link the GPOs to the required AD DS containers, such as a relevant OU.
Need More Review? Creating a custom base ADMX file
To review further details about creating custom .admx files, refer to the Microsoft TechNet website at https://technet.microsoft.com/library/cc770905(v=ws.10).aspx.
Configure property filters for administrative templates
The number of settings that you can configure with administrative templates is vast. By default, the Group Policy Management Editor shows all policy settings, whether the setting is managed or unmanaged, configured or not configured, and commented.
 Exam Tip
Exam Tip
The Group Policy Client service controls managed policy settings but not unmanaged settings.
Wading through dozens of unmanaged settings to locate the managed setting that you want to change is time-consuming. Likewise, looking for a specific configured setting among thousands of unconfigured settings is also time-consuming. Fortunately, you can change how Group Policy Management Editor shows your Administrative Templates policy settings by using property filters. To configure a filter, select the Administrative Templates folder beneath either the Computer Configuration or User Configuration node, as required. Then complete the following procedure:
1. Right-click Administrative Templates, and then click Filter Options.
2. In the Filter Options dialog box, shown in Figure 3-83, configure the following options, and then click OK:
![]() Managed Yes, No, or Any.
Managed Yes, No, or Any.
![]() Configured Yes, No, or Any.
Configured Yes, No, or Any.
![]() Commented Yes, No, or Any.
Commented Yes, No, or Any.
![]() Keyword Filter(s) Enter the keyword to filter for. Specify whether the word appears in the policy setting title, the policy help text, and/or the comment. Then choose to search for exact match, all words, or any words.
Keyword Filter(s) Enter the keyword to filter for. Specify whether the word appears in the policy setting title, the policy help text, and/or the comment. Then choose to search for exact match, all words, or any words.
![]() Requirements Filter(s) Configure specific requirements for the platform or application you want to filter. After selecting the appropriate filters, choose whether they must all match, or any to match.
Requirements Filter(s) Configure specific requirements for the platform or application you want to filter. After selecting the appropriate filters, choose whether they must all match, or any to match.
3. The filter applies to the current view immediately.
Skill 3.4: Configure Group Policy preferences
As we have seen, you can use logon scripts to prepare your users’ desktop environment, perhaps by mapping network drives, or connecting to peripherals, such as printers. You can even deliver those scripts to your users’ computer by using GPOs.
However, maintaining scripts can be a complex and time-consuming management task. It also requires knowledge of scripting languages, which you might not have available in your organization. In Windows Server 2016, you can use Group Policy preferences to deliver settings more typically made available through scripting.
There are many similarities between GPO settings and Group Policy preferences, but there are some notable and important differences. These are:
![]() GPO settings are strictly enforced, whereas preferences are not. It is possible, for example, for a user to reconfigure Start Menu settings configured by Group Policy preferences.
GPO settings are strictly enforced, whereas preferences are not. It is possible, for example, for a user to reconfigure Start Menu settings configured by Group Policy preferences.
![]() GPOs tend to disable the area of the user interface, which has been configured by a GPO setting. Preferences do not do this.
GPOs tend to disable the area of the user interface, which has been configured by a GPO setting. Preferences do not do this.
![]() GPOs are automatically refreshed on a periodic basis. While this is also true for preferences, you can also configure preferences to apply only once and never refresh.
GPOs are automatically refreshed on a periodic basis. While this is also true for preferences, you can also configure preferences to apply only once and never refresh.
Configuring Group Policy preferences
You can use Group Policy preferences, shown in Figure 3-84, to configure the following settings:
![]() Applications
Applications
![]() Environment settings
Environment settings
![]() Files and folders
Files and folders
![]() Drive maps and network shares
Drive maps and network shares
![]() Registry settings
Registry settings
![]() Shortcuts
Shortcuts
![]() A range of Control Panel settings, including:
A range of Control Panel settings, including:
![]() Data sources
Data sources
![]() Devices
Devices
![]() Folder options
Folder options
![]() Internet settings
Internet settings
![]() Local Users and Groups
Local Users and Groups
![]() Network Options
Network Options
![]() Printers
Printers
![]() Regional options
Regional options
![]() Scheduled Tasks
Scheduled Tasks
![]() Services
Services
![]() Start Menu
Start Menu
To configure a Group Policy preference, use the following high-level procedure:
1. Open the Group Policy Management Editor for the appropriate GPO, select the User Configuration or Computer Configuration node, open the Preferences folder, and then select one of the items from the list shown earlier.
2. Perform one of the following tasks:
![]() Create a new preference setting.
Create a new preference setting.
![]() Replace an existing preference setting.
Replace an existing preference setting.
![]() Update an existing preference setting.
Update an existing preference setting.
![]() Delete an existing preference setting.
Delete an existing preference setting.
 Exam Tip
Exam Tip
The Preferences folder is not available in the Local Group Policy Editor.
Define network drive mappings
You configure Drive Maps in the User Configuration node. To add a drive mapping, complete the following procedure:
1. Select the Preferences folder, and then under Windows Settings, right-click Drive Maps, point to New, and then click Mapped Drive.
2. Then, in the New Drive Properties dialog box, on the General tab, as shown in Figure 3-85, in the Action list, click Create.
3. In the Location text box, type the UNC path to the shared folder.
4. Optionally, select the Reconnect check box to ensure that the drive mapping reconnected each time a user signs in.
5. Under Drive Letter, select the appropriate driver letter from the Use list.
6. If required, use the Connect As (Optional) section to define credentials to use to map the drive.
7. Click the Common tab, shown in Figure 3-86.
8. Configure the available options, and then click OK:
![]() Stop Processing Items In This Extension If An Error Occurs If an error does occur, all other preferences configured in a GPO are not processed.
Stop Processing Items In This Extension If An Error Occurs If an error does occur, all other preferences configured in a GPO are not processed.
![]() Run In Logged-On User’s Security Context Preferences run either in the context of the System account or the logged in user. This setting is useful when configuring drive mappings.
Run In Logged-On User’s Security Context Preferences run either in the context of the System account or the logged in user. This setting is useful when configuring drive mappings.
![]() Remove This Item When It Is No Longer Applied Preferences continue to apply even after the preference item is removed. This option changes that behavior.
Remove This Item When It Is No Longer Applied Preferences continue to apply even after the preference item is removed. This option changes that behavior.
![]() Apply Once And Do Not Reapply This setting overrides the default GPO refresh behavior.
Apply Once And Do Not Reapply This setting overrides the default GPO refresh behavior.
![]() Item-Level Targeting This is discussed at the end of this skill.
Item-Level Targeting This is discussed at the end of this skill.
If you want to modify the drive mapping, open its properties, and then on the General tab, in the Action list, click Replace, and repopulate the settings. The item is deleted from clients and replaced with the new item. Choose Update if you want to modify a setting. Finally, if the preference item is no longer needed, choose Delete.
Configure printer preferences
You can configure Printers in Group Policy preferences in both the Computer Configuration and User Configuration nodes. To setup a printer preference, complete the following procedure:
1. In the Group Policy Management Editor, navigate to the User Configuration node, and then expand the Preferences folder, expand the Control Panel Settings folder, and then click the Printers node.
2. Right-click Printers, point to New, and then click Shared Printer, TCP/IP Printer, or Local Printer depending on the way that you want to connect, as shown in Figure 3-87.
3. For example, click Shared Printer, and then in the New Shared Printer Properties dialog box, on the General tab, in the Action list, click Create.
4. In the Shared printer section, in the Share path, browse and locate the shared printer.
5. Optionally, select the Set This Printer As The Default Printer check box, as shown in Figure 3-88.
6. Click the Common tab, and configure the common options, and then click OK.
Configure power options
Configuring power options with Group Policy preferences is broadly the same as for printers and drive mappings. To deploy power options, use the following procedure:
1. Select the Power Options folder in the Control Panel Settings node.
2. Right-click the Power Options folder, point to New, and then click Power Plan (At least Windows 7).
3. In the New Power Plan (At least Windows 7) Properties dialog box, shown in Figure 3-89, select the appropriate plan, and configure the required power settings.
4. Click the Common tab, and configure the required options, and then click OK.
Configure shortcut deployment
It’s convenient to place shortcuts to files, folders, or other objects on users’ desktops. You can do this with Group Policy preferences in either the Computer Configuration or User Configuration node. To create a shortcut, use the following procedure:
1. In the Windows Settings folder in either the Computer Configuration or User Configuration node, right-click the Shortcuts folder, point to New, and then click Shortcut.
2. In the New Shortcut Properties dialog box, shown in Figure 3-90, on the General tab, select Create in the Action list.
3. In the Name box, type a name for the shortcut.
4. In the Target type list, select the type of object to which the shortcut points. Choose between File System Object, URL, or Shell Object.
5. In the Location list, select where the shortcut is to appear. For example, Desktop, Start Menu.
6. In the Target path box, enter the path to the object.
7. Configure the remaining options as needed, and then click the Common tab.
8. Configure the Common options, and then click OK.
Configure file and folder deployment
You can also configure files and folder deployment in Group Policy preferences. Again, you can also use either the Computer Configuration node or the User Configuration node.
With the Files and Folders preferences, you can use Group Policy to deploy specific files or folders to target users or computers, depending on which GPO node you select. To add a file to a user’s desktop, use the following procedure:
1. In the Windows Settings folder in the User Configuration node, right-click the Files folder, point to New, and then click File.
2. In the New File Properties dialog box, shown in Figure 3-91, on the General tab, select Create in the Action list.
3. In the Source file(s) box, type the path and name of the file you want to use as a source.
4. In the Destination File box, type the path and name of the file you want to create.
5. Optionally, configure the attributes for Read-only, Hidden, and Archive.
6. Click the Common tab, and configure the common options.
7. Click OK.
Creating folders is broadly the same. However, when you are replacing or deleting a folder, you have some additional options over how the folder is to be managed, as shown in Figure 3-92. These are:
![]() Delete This Folder (If Emptied)
Delete This Folder (If Emptied)
![]() Recursively Delete All Subfolders (If Emptied)
Recursively Delete All Subfolders (If Emptied)
![]() Delete All Files In The Folder(s)
Delete All Files In The Folder(s)
![]() Allow Deletion Of Read-Only Files/Folders
Allow Deletion Of Read-Only Files/Folders
![]() Ignore Errors For Files/Folders That Cannot Be Deleted
Ignore Errors For Files/Folders That Cannot Be Deleted
Configure custom registry settings
Using preferences, you can perform the following registry-based management tasks:
![]() Add a registry item Enables you to add a specific registry entry to the appropriate registry hive and key.
Add a registry item Enables you to add a specific registry entry to the appropriate registry hive and key.
![]() Add a collection item Enables you to group a collection of registry items. This is useful if you want to add multiple registry entries to target users or computers.
Add a collection item Enables you to group a collection of registry items. This is useful if you want to add multiple registry entries to target users or computers.
![]() Run a registry wizard Enables you to use a wizard on target computers to configure multiple user or computer settings in the registry on target computers.
Run a registry wizard Enables you to use a wizard on target computers to configure multiple user or computer settings in the registry on target computers.
The specific procedure for creating custom registry settings is very similar to all the other preference-based procedures.
Configure Control Panel settings
You can use preferences to configure the following Control Panel items under the User Configuration node:
![]() Data Sources Add or configure data sources.
Data Sources Add or configure data sources.
![]() Devices Add or configure hardware devices.
Devices Add or configure hardware devices.
![]() Folder Options Configure the way files and folders are presented in File Explorer, including options such as Show Hidden Files And Folders, and Hide Extensions For Known File Types, as shown in Figure 3-93.
Folder Options Configure the way files and folders are presented in File Explorer, including options such as Show Hidden Files And Folders, and Hide Extensions For Known File Types, as shown in Figure 3-93.
![]() Internet Settings You can configure defaults and settings for Internet Explorer, as shown in Figure 3-94.
Internet Settings You can configure defaults and settings for Internet Explorer, as shown in Figure 3-94.
Note Green lines and red dashes
By default, in certain Control Panel preferences, not all settings are available for configuration. If a setting is available, it is underlined with a solid green line. If a setting is not available for preference configuration, it is underlined with a red dashed line. You can change whether an item is configurable by using the function keys on your keyboard. F5 enables all settings on a tab, F6 enables the selected setting, F7 disables the selected setting, and F8 disables all settings on a tab.
![]() Local Users And Groups You can use preferences to manage local users or local groups, as shown in Figure 3-95.
Local Users And Groups You can use preferences to manage local users or local groups, as shown in Figure 3-95.
![]() Network Options Using Network Options, you can add and configure virtual private network (VPN) connections.
Network Options Using Network Options, you can add and configure virtual private network (VPN) connections.
![]() Power Options Enables you to add and configure power plans.
Power Options Enables you to add and configure power plans.
![]() Printers Enables you to add and configure printer connections.
Printers Enables you to add and configure printer connections.
![]() Regional Options Enables you to configure regional settings.
Regional Options Enables you to configure regional settings.
![]() Start Menu Enables you to configure some aspects of the Start screen.
Start Menu Enables you to configure some aspects of the Start screen.
You can use preferences to configure the following additional Control Panel items under the Computer Configuration node:
![]() Scheduled Tasks Add, configure, and maintain scheduled tasks.
Scheduled Tasks Add, configure, and maintain scheduled tasks.
![]() Services Configure service startup behavior.
Services Configure service startup behavior.
Configure item-level targeting
When you use GPOs, you can target specific groups or users by implementing Security filtering. You can target specific computers with WMI filters. These filters determine whether the entire GPO applies to a specific user or computer.
When you implement Group Policy preferences, you can use item-level targeting to determine whether a specific preference applies. This gives you far greater control over the application of specific settings.
Throughout this section, when looking at a particular preference, after configuring the General properties, you could optionally configure the settings on the Common tab, including the Item-level targeting option, shown in Figure 3-96.
After you have enabled this option, you can then configure targeting of the preference by using the following procedure:
1. In the Targeting Editor dialog box, click New Item, and then select from the list of objects how you want to target the preference. For example, you can select Battery Present, or Domain, or RAM, or even to use a WMI query. For example, click RAM.
2. Next, define the condition. For example, if you selected RAM, specify the amount of RAM required for the condition to bet met in order than the preference applies, as shown in Figure 3-97. Use the Item options list to define operators. For example, that total RAM is greater 2GB, or is not greater than 2GB.
3. Add any additional items that you require. Note that all conditions must be met for the preference to apply. Define the relationship between the conditions using the Item Options list. The default is the AND operator, as shown in Figure 3-98.
4. When you have defined all conditions, click OK.
5. In the Preference Properties dialog box, click OK.
There are 27 available categories with which you can target your preference. These are: Battery Present, Computer Name, CPU Speed, Date Match, Disk Space, Domain, Environment Variable, File Match, IP Address Range, Language, LDAP Query, MAC Address Range, MSI Query, Network Connection, Operating System, Organizational Unit, PCMCIA Present, Portable Computer, Processing Mode, RAM, Registry Match, Security Group, Site, Terminal Session, Time Range, User, and WMI Query.
Chapter summary
![]() You can use GPOs to centrally configure and manage your AD DS forest’s devices and user settings.
You can use GPOs to centrally configure and manage your AD DS forest’s devices and user settings.
![]() You use the Group Policy Management console, the Group Policy Management Editor console, and Windows PowerShell to create, configure, and maintain GPOs.
You use the Group Policy Management console, the Group Policy Management Editor console, and Windows PowerShell to create, configure, and maintain GPOs.
![]() GPOs enable you to configure the following common settings: software installation, scripts, folder redirection, security settings, and registry-based configuration.
GPOs enable you to configure the following common settings: software installation, scripts, folder redirection, security settings, and registry-based configuration.
![]() You can link GPOs to sites, domains, and OUs.
You can link GPOs to sites, domains, and OUs.
![]() Settings in OUs are, by default, inherited from GPOs linked to parent OUs and the domain.
Settings in OUs are, by default, inherited from GPOs linked to parent OUs and the domain.
![]() You can use a migration table to help import GPOs into one domain from another domain where security principal names or UNC paths must be changed.
You can use a migration table to help import GPOs into one domain from another domain where security principal names or UNC paths must be changed.
![]() For a GPO to apply to a user, the user must have the Read and Apply policy permissions.
For a GPO to apply to a user, the user must have the Read and Apply policy permissions.
![]() Where multiple GPOs apply to a container in AD DS, the policy that applies last has the highest precedence.
Where multiple GPOs apply to a container in AD DS, the policy that applies last has the highest precedence.
![]() When you block inheritance, you block at the container level and block all GPOs linked above the selected container.
When you block inheritance, you block at the container level and block all GPOs linked above the selected container.
![]() When you enforce a policy, you do so at the policy level, and enforcement overrides blocked inheritance.
When you enforce a policy, you do so at the policy level, and enforcement overrides blocked inheritance.
![]() For situations where you want a specific user or computer to not receive their configuration from a policy that is linked to their container, use WMI filters or security filters.
For situations where you want a specific user or computer to not receive their configuration from a policy that is linked to their container, use WMI filters or security filters.
![]() You can use preferences to apply drive mappings, desktop shortcuts, and Internet Explorer settings.
You can use preferences to apply drive mappings, desktop shortcuts, and Internet Explorer settings.
![]() Preferences assigned through GPOs are not enforced in the same way as GPO settings.
Preferences assigned through GPOs are not enforced in the same way as GPO settings.
Thought experiment
In this thought experiment, demonstrate your skills and knowledge of the topics covered in this chapter. You can find answers to this thought experiment in the next section.
You work in support at A. Datum. As a consultant for A. Datum, answer the following questions about implementing and configuring Group Policies within the A. Datum organization:
1. It is necessary for all computers within the London Head Office to receive the same security settings. Computers in the other European offices receive different settings. How can you go about achieving this?
2. Users in the Paris office in France require drive mappings to be configured when they sign in. What methods could you use to address this issue?
3. You want all users throughout the single domain A. Datum organization to receive the same security settings. How is this possible?
4. The sales department in Milan has a restrictive GPO in-place. Unfortunately, this is impacting the sales manager’s ability to work. It is decided that the policy should not apply to the manager. However, her user and computer account must not be moved from the MilanSales OU where they currently reside. How could you deal with this request?
Thought experiment answers
This section contains the solution to the thought experiment. Each answer explains why the answer choice is correct.
1. You could implement a security GPO for each of the locations in the A. Datum organization. You would configure the required security settings, perhaps using the Security Template snap-in to import similar settings between GPOs. Finally, assuming that the A. Datum forest is properly configured with AD DS sites, you could link the security GPOs to the appropriate AD DS sites.
2. There are two possible solutions. One is to implement a Logon script using GPOs and link the GPO that contains the Logon script setting to the appropriate AD DS container, perhaps a site, or appropriately configured OU. The second possibility is to implement Group Policy preferences and use the Drive Maps node to create a new drive mapping. Link the GPO containing the Group Policy preference to an appropriate AD DS container.
3. Configure the security settings that must be applied throughout the organization in a GPO that you link to the domain object. Then, enforce the GPO to ensure that the settings override any others that are configured in other GPOs.
4. One solution is to use security filtering to stop the policy from applying. Use the Applies to everyone BUT strategy. To achieve this, grant the Milan sales manager the Deny Apply group policy permission. This prevents her from applying the policy.