Chapter 11. IPv6 Security
This chapter covers the following topics:
• Spoofing
• Header Manipulation and Fragmentation
• Broadcast Amplification or Smurf Attacks
Internet Protocol Version 6 (IPv6) is often called the next generation protocol and is designed to replace the widely deployed Internet Protocol Version 4 (IPv4). Despite that, IPv6 has only been implemented in a few places, but it is expected to grow over time. For example, Microsoft Windows Vista includes support for IPv6.
IPv6 enables easier support and maintenance of service provider networks than previous versions. The large address space improves the usage of online support systems and enables the inexpensive provision of address space to end users. Many service providers in Europe, Asia, and the United States are currently working on providing IPv6 services to enterprises and small businesses. This chapter includes several IPv6 security topics. It also provides a comparison with IPv4 from a threat and mitigation perspective.
Note
This chapter requires a basic knowledge of the IPv6 protocol.
IPv6 is defined in RFC 2460, "Internet Protocol, Version 6 (IPv6) Specification." The following are some of the main differences between IPv6 and IPv4:
• Expanded addressing: The IP address size is increased in IPv6 to 128 bits from the 32 bits supported in IPv4. This introduces considerable flexibility while supporting more levels of addressing hierarchy. Multicast routing scalability is also improved by the addition of a "scope" field to multicast addresses.
• Simplified header format: Several of the header fields used in IPv4 are not used in IPv6. These fields include check sum, Internet header length (IHL), identification flag, and fragment offset.
• Improved support for extensions and options: IPv6 encodes information into separate headers.
• Fragmentation performed at the end hosts: Unlike IPv4 packets, routers do not perform packet fragmentation on IPv6 packets. IPv6 supports payloads that are longer than 64 Kilobytes (KB).
• Authentication: IPv6 supports built-in authentication and confidentiality.
Tip
Several sites include good information about IPv6, including the following:
• Cisco IPv6 information on IOS: http://www.cisco.com/go/ipv6
• IPv6 Forum: http://www.ipv6forum.com
• 6Net IPv6 International Research: http://www.6net.org
• Internet2 IPv6 Working Group: http://ipv6.internet2.edu
The first thing you need to learn about IPv6 security is the different types of security threats that may affect your IPv6 deployment. This chapter covers the most common types of threats in IPv6 and other security topics, such as:
• Spoofing
• Header manipulation and fragmentation
• Broadcast amplification or smurf attacks
Reconnaissance
Reconnaissance in IPv6 is not as easy to perform as in IPv4 networks. Do not forget that IPv6 has many more addresses than IPv4 (2^64 to be exact, or 128-bit addresses). Performing a network scan for that many addresses is not feasible for an attacker because it takes a considerable amount of time to scan millions of addresses.
Attackers use different techniques to gain more visibility of your network. Inevitably, many network administrators may adopt addresses that are easy to remember to assign to network devices (for example, ::10, ::20, ::F00D). Attackers may use these types of addresses in specific scans or reconnaissance methodologies. Instead of standardizing on host addresses, try something that is more difficult for attackers to guess. For example, you may want to use something like ::DEE1 for default gateways. Some people refer to this technique as security through obscurity. That technique can be beneficial, because it does not require administrative complications. Standardizing on a short, fixed pattern for interfaces that should not be directly accessed from the outside allows for a short filter list at the border routers.
Because Domain Name System (DNS) is still used to map systems to IPv6 addresses on external and internal networks, an attacker can obtain information on your IPv6 network addresses if he compromises the DNS infrastructure/application.
Just as for IPv4, it is recommended that you filter all IPv6 services at the perimeter router or firewall in an effort to protect the internal networks.
Privacy becomes a problem when you use DHCPv6 on an IPv6 network. An IPv6 address has two parts. The first part is the subnet prefix, and the second part is a local identifier. This identifier is typically derived from your MAC address. The subnet prefix is a fixed 64-bit length for all current definitions. DHCP is not suitable for some IPv6 environments because you can technically get an IPv6 address via DHCPv6 in your corporate network and then get the same address when you are at home or at a hotel. Attackers can track you down with the use of web cookies that can retain your address information. That is why it is recommended that you use IPv6 Privacy Extensions for external communication. RFC 3041 defines the use of IPv6 Privacy Extensions.
Filtering in IPv6
Filtering of unauthorized access in IPv6 is similar to IPv4. This section includes examples of IPv6 access control lists (ACL), in addition to best practices when filtering ICMPv6 unnecessary packets and extension headers.
Filtering Access Control Lists (ACL)
You can configure the filters or ACLs using Layer 3 and Layer 4 information. You can configure an IPv6 ACL in a Cisco IOS router using the ipv6 access-list command. The command uses the permit and deny subcommands with the following options:
ipv6 access-list command and its subcommands
permit protocol {source-ipv6-prefix/prefix-length | any |host source-ipv6-address}
[operator [port-number]] {destination-ipv6-prefix/prefix-length | any |host
destination-ipv6-address} [operator [port-number]] [dest-option-type [doh-number |
doh-type]][dscp value] [flow-label value] [fragments] [log] [log-input] [mobility]
[mobility-type [mh-number | mh-type]] [reflect name [timeout value]] [routing]
[routing-type routing-number][sequence value] [time-range name]
deny protocol {source-ipv6-prefix/prefix-length | any | host source-ipv6-address}
[operator [port-number]] {destination-ipv6-prefix/prefix-length | any | host
destination-ipv6-address} [operator [port-number]] [dest-option-type [doh-number |
doh-type]] [dscp value] [flow-label value] [fragments] [log] [log-input] [mobility]
[mobility-type [mh-number | mh-type]] [routing] [routing-type routing-number]
[sequence value] [time-range name] [undetermined-transport]
Example 11-1 shows an ACL in a Cisco IOS router allowing HTTP traffic (TCP port 80) from a trusted IPv6 host and denying all other traffic.
Example 11-1. IPv6 Access Control List
ipv6 access-list outside_acl
permit tcp 2001:1234:0300:0101::/32 any eq 80
interface FastEthernet 0/0
ipv6 traffic-filter outside_acl in
In the previous example, the ACL name is outside_acl, and it is applied inbound to the FastEthernet 0/0 interface.
Note
Standard IPv6 ACLs are supported starting with Cisco IOS Version 12.2(2)T and 12.0(21)ST and later.
In the Cisco ASA and Cisco PIX security appliances, the IPv6 ACLs are similar to IOS. To create an IPv6 ACL to allow the same host to pass HTTP traffic on the Cisco ASA or Cisco PIX, use the ipv6 access-list command, as shown in the following example:
ipv6 access-list asa_outside_acl permit tcp 2001:1234:0300:0101::/32 any eq www –
access-group asa_outside_acl in interface outside
Notice that the IPv6 access list is applied to the outside interface using the access-group command just as for IPv4 access lists.
Note
IPv6 has been supported on the Cisco PIX since Version 7.0. The Cisco ASA supports IPv6 in all versions, because the first version of Cisco ASA software is 7.0.
ICMP Filtering
You may also want to filter unnecessary ICMPv6 messages, just as with ICMPv4. It is recommended that you configure your ICMPv6 filters and policies in a manner that is similar to your ICMPv4 policies, with the following additions:
• ICMPv6 Type 2: Packet too big
• ICMPv6 Type 4: Parameter problem
• ICMPv6 Type 130-132: Multicast listener
• ICMPv6 Type 133/134: Router solicitation and router advertisement
• ICMPv6 Type 135/136: Neighbor solicitation and neighbor advertisement
Make sure that, if you need to allow these options, you only allow trusted sources and deny everything else.
Extension Headers in IPv6
In IPv6, IP options are replaced with extension headers. An attacker may use these extension headers to evade your security configuration. All devices running IPv6 must accept packets with a routing header. In some cases, it may be possible for end-host devices to also process routing headers and forward the packet somewhere else. Attackers can take advantage of this and use routing headers to evade the ACLs configured on your routers and firewalls.
As a best practice, you should designate specific devices that are allowed to act as Mobile IPv6 (MIPv6) home agents. MIPv6 is a protocol developed as a subset of IPv6 to support mobile connections. You should typically only assign the default router for a specific subnet to act as an MIPv6 home agent. If MIPv6 is not needed, packets with the routing header can easily be dropped at your firewalls and routers without relying on the end host not to forward the packets.
Spoofing
One of the most common techniques that attackers use is spoofing. Spoofing is the technique of modifying your source IP address or the ports to appear as your packets are initiated from another location. From a Layer 3 spoofing perspective, IPv6 presents a huge benefit because the allocations of IPv6 addresses are designed to easily be summarized allowing service providers to at least ensure that their own customers are not using addresses outside their allocated range. You can use filtering techniques such as those defined in RFC 2827.
The following are the most common best practices suggested to protect against IPv6 Layer 3 and Layer 4 spoofing:
• Implement filtering techniques as defined in RFC 2827. In Chapter 2, "Preparation Phase," you learned how to create antispoofing ACLs for your IPv4. You should do the same for your IPv6 addresses by denying all traffic from your own network range to be sourced from outside your networks.
• In an IPv6 subnet, an attacker has numerous options to select an IP address to spoof. It is critical to have tools to determine the true physical source of the traffic within your network. This generally entails some combination of Layer 2 and Layer 3 information gleaned from switches and routers.
Header Manipulation and Fragmentation
IPv6 is susceptible to fragmentation and other header manipulation attacks. With these types of attacks, the attacker uses fragmentation to evade network intrusion detection systems (IDS), intrusion prevention systems (IPS), and firewalls.
An attacker can also use out-of-order fragments to try to avoid an IDS/IPS device that is deployed to detect attacks based on the enabled signatures on the system. RFC 2460 prohibits fragmentation of IPv6 packets by intermediary network devices.
As is the case with IPv4, you should always deny IPv6 fragments destined to an internetworking device whenever possible. On the other hand, you should test this in the lab and make sure that this does not cause problems with specific applications in your particular network environment.
The combination of multiple extension headers and fragmentation in IPv6 creates the potential that the Layer 4 protocol will not be included in the first packet of a fragment set. Make sure that your IDS/IPS system or any other security monitoring device accounts for this possibility and reassembles fragments. Today, Cisco IPS/IDS devices support multiple extension headers and fragmentation.
Broadcast Amplification or Smurf Attacks
Broadcast amplification attacks are typically referred to as smurf attacks. These are denial of service (DoS) attacks where the attacker sends an echo-request message with a destination address of a subnet broadcast and a spoofed source address using the host IP address of the victim. This causes all the devices on the subnet to respond to the spoofed source IP address and flood the victim with echo-reply messages. RFC 2463 prohibits IP-directed broadcasts within IPv6. In addition, it states that an ICMPv6 message should not be generated as a response to a packet with an IPv6 multicast destination address, a link-layer multicast address, or a link-layer broadcast address.
Smurf attacks should not be a threat if all the devices within your network are compliant with RFC 2463. On the other hand, you should always implement ingress filtering of packets with IPv6 multicast source addresses.
IPv6 Routing Security
Some routing protocols change in respect to security in IPv6; however; others do not. This section lists the routing protocols that change as well as those that remain the same.
Border Gateway Protocol (BGP) continues to have authentication mechanisms such as MD5 authentication but what, if anything, changes with IPv6? The Intermediate System-to-Intermediate System (IS-IS) protocol was extended in a draft specification to support IPv6. In IPv4, the simple password authentication of IS-IS was not encrypted. However, RFC 3567 defines the IS-IS cryptographic authentication. IS-IS in IPv6 also supports this cryptographic authentication mechanism.
The Open Shortest Path First Version 3 (OSPFv3) protocol changed to support IPv6. The authentication fields were removed from the header of OSPF messages/packets. Another protocol that removed authentication capabilities was the Routing Information Protocol Next-Generation (RIPng). For this reason, it is recommended that you use traditional authentication mechanisms for BGP and IS-IS. OSPF for IPv6 requires the use of IPsec to enable authentication. It is always a best practice to use OSPF in conjunction with IPsec to secure routing protocol updates in OSPF for IPv6.
Note
Cisco IOS routers support the use of IPv6 IPsec to authenticate OSPFv3 starting with Versions 12.3(4)T, 12.4, and later.
IPsec and IPv6
IPsec is available with IPv6. IPv6 headers have no security mechanisms themselves, just as in IPv4. Administrators rely on the IPsec protocol suite for security. The same security risks for man-in-the-middle attacks in Internet Key Exchange (IKE) in IPv4 are present in IPv6. Most people recommend using IKE main mode negotiations when the use of preshared keys is required. On the other hand, IKE Version 2 (IKEv2) is expected to address this issue in the future. IKEv2 supports different peer authentication options with built-in support for asymmetric user authentication through the Extensible Authentication Protocol (EAP).
The IPv6 IPsec packet format is basically the same as in IPv4. Figure 11-1 illustrates an IPv6 packet where Authentication Header (AH) and Encapsulation Security Payload (ESP) protocols are used. IPv6 AH and ESP extension headers are used to provide authentication and confidentiality to IPv6 packets.
Figure 11-1. IPv6 IPsec Packet
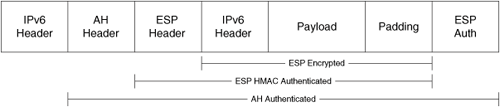
Cisco IOS supports IPv6 IPsec for VPN tunnels starting with IOS Version 12.4(4)T. Figure 11-2 illustrates a topology where two Cisco IOS routers are configured to terminate a site-to-site IPv6 IPsec tunnel. The IPv6 address of the router in New York is 2EEE:1001::DCBA:BBAA:DDCC:4321, and the IPv6 address of the router in London is 2EEE:2002::ABCD:AABB:CCDD:1234.
Figure 11-2. IPv6 IPsec Configuration Example
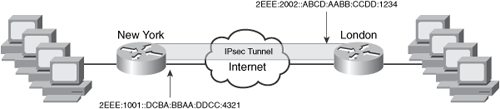
Virtual tunnel interfaces (VTI) are configured on each router in this example. Example 11-2 shows the configuration of the router in New York. Notice that the configuration is almost identical to the IPv4 VTI implementation. In this example, routers use preshared keys with SHA for hashing, and Diffie-Hellman group 1 for Phase 1. AH-SHA-HMAC and ESP-3DES are used for Phase 2.
Example 11-2. New York Router Configuration
crypto isakmp policy 1
authentication pre-share
!
crypto isakmp key 1qaz2wsx address ipv6 2EEE:2002::ABCD:AABB:CCDD:1234/128
!
crypto ipsec transform-set 3des ah-sha-hmac esp-3des
!
!
crypto ipsec profile myprofile
set transform-set 3des
!
ipv6 cef
!
interface Tunnel0
ipv6 address 2EEE:1001::/64 eui-64
ipv6 enable
ipv6 cef
tunnel source FastEthernet0
tunnel destination 2EEE:2002::ABCD:AABB:CCDD:1234
tunnel mode ipsec ipv6
tunnel protection ipsec profile myprofile
Example 11-3 shows the configuration of the router in London. Notice that the configuration is almost identical for the exception of the IP addresses.
Example 11-3. London Router Configuration
crypto isakmp policy 1
authentication pre-share
!
!
crypto isakmp key 1qaz2wsx address ipv6 2EEE:1001::DCBA:BBAA:DDCC:4321/128
!
crypto ipsec transform-set 3des ah-sha-hmac esp-3des
!
crypto ipsec profile myprofile
set transform-set 3des
!
ipv6 cef
!
interface Tunnel0
ipv6 address 2EEE:2002::/64 eui-64 –
ipv6 enable
ipv6 cef
tunnel source FastEthernet0
tunnel destination 2EEE:1001::DCBA:BBAA:DDCC:4321
tunnel mode ipsec ipv6
tunnel protection ipsec profile myprofile
The IKE and IPsec Security Associations (SA) are negotiated and established before the line protocol for the tunnel interface is changed to the UP state. The remote IKE peer is the same as the tunnel destination address; the local IKE peer will be the address picked from the tunnel source interface, which has the same IPv6 address scope as the tunnel destination address.
Summary
This chapter introduced security topics in IPv6. Although it is assumed that you already have a basic understanding on IPv6, this chapter covered fundamental topics of IPv6 including how to filter IPv6 traffic in infrastructure devices such as the Cisco ASA and Cisco IOS routers. When deploying IPv6 on your network, you should pay attention to several security considerations. These considerations include the use of authorization for automatically assigned addresses and configurations, protection of IP packets, host protection from scanning and attacks, and control of traffic that is exchanged with the Internet. In many cases, these security considerations also exist for IPv4 traffic. Understanding the IPv6 security threats is a must for every security professional. This chapter included the most common IPv6 security threats and the best practices adopted by many organizations to protect their IPv6 infrastructure.
Many IPv6-enabled devices also support IPsec. This chapter covered how to configure Cisco IOS routers to terminate IPsec in IPv6 networks. It provided sample configurations to enhance the learning.
