Chapter 15. Collecting and Preserving Digital Evidence
Introduction
In previous chapters, we discussed methods of detecting that cybercrimes have occurred and tracking down the person(s) responsible. The next and perhaps most important step in prosecuting the offender is to collect the evidence that will be used to build the case to be presented at trial.
The field of computer forensics involves identifying, extracting, documenting, and preserving information that is stored or transmitted in electronic or magnetic form (that is, digital evidence). Like fingerprints, digital evidence can be visible (such as files stored on disk that can be accessed via the normal directory structure using standard file management tools such as Windows Explorer) or it can be latent (not readily visible or accessible, requiring some sort of processing—via special software or techniques—to locate and identify it). An important aspect of computer forensics involves finding and evaluating this “hidden data” for its evidentiary value.
Standards have been developed that apply to the collection and preservation of digital evidence, which differs in nature from most other types of evidence and thus requires different methods of handling. Following procedures that are proper, accepted, and, in some cases, prescribed by law in dealing with evidence is vital to the successful prosecution of a cybercrime case. The proper handling of these procedures comes into play at two different points in a trial:
If evidence is not collected and handled according to the proper standards, the judge may deem the evidence inadmissible when it is presented (usually based on the opposing attorney's motion to suppress) and the jury members will never get a chance to evaluate it or consider it in making their decision.
If the evidence is admitted, the opposing attorney will attack its credibility during questioning of the witnesses who testify regarding it. Such an attack can create doubt in jury members' minds that will cause them to disregard the evidence in making their decision—and perhaps even taint the credibility of the entire case.
The entire investigation will be of little value if the evidence that shows the defendant's guilt is not allowed into the trial or if the jury gives it no weight. Thus, proper handling of evidence is one of the most important issues facing all criminal investigators and, because of the intangible nature of digital evidence, cybercrime investigators in particular.
Because this is such an important topic—not only for investigators, but also for prosecutors, judges, and justice system professionals involved in cybercrime cases—many organizations and publications are devoted solely to issues concerning digital evidence. The International Organization on Computer Evidence (IOCE; www.ioce.org) was established in 1995 to provide a forum for law enforcement agencies around the world to exchange information about issues regarding computer forensics; its U.S. component is the Scientific Working Group on Digital Evidence (SWGDE; www.swgde.org). The International Association of Computer Investigative Specialists (IACIS; www.cops.org) is a nonprofit organization that is dedicated to educating law enforcement professionals in the area of computer forensics. The International Journal of Digital Evidence (www.ijde.org/) is an online publication devoted to discussions of the theory and practice of handling digital evidence. Many other similar resources that focus on computer forensics are available, and more broad-based organizations such as the American Academy of Forensic Sciences (www.aafs.org) address computer crimes and digital evidence along with other topics in that area.
A glance at any of these resources will reveal that digital evidence handling is a huge topic that could easily fill several books (and already has). It is far beyond the scope of this chapter to cover every aspect of collecting and preserving digital evidence. This chapter provides additional material to what we've already covered regarding the role evidence plays in a criminal case (particularly in a cybercrime case) and discusses standard procedures for dealing with digital evidence, as well as specific evidence location and examination techniques. We also outline procedures for documenting digital evidence and discuss some of the legal issues involved in evidence collection and handling. Finally, we provide many excellent online resources that furnish detailed instructions for performing the tasks described in this chapter and provide information about commercial services and equipment that can aid in the evidence recovery process.
Understanding the Role of Evidence in a Criminal Case
The process of collecting, examining, preserving, and presenting evidence is a legal process and is governed by the laws of the jurisdiction of the court in which the evidence will be introduced. Thus, it is extremely important for investigators to become familiar with the applicable laws. These rules are adopted by statute and are usually codified into a document titled “Rules of Evidence.”
The rules of state courts may differ from those of federal courts, and the rules for evidence in criminal trials may differ from those for civil trials. Generally, evidence must be authenticated, which in this context usually means that some witness must testify to its authenticity. In the case of digital evidence, this could be a witness who has personal knowledge of the evidence (for example, a person who shared the computer with the accused and observed the document or file in question on the computer). It could also be the first responder who saw the evidence on-screen when responding to the incident or an expert who examined the computer and evidence after it was seized. One of the most important aspects of preparing to introduce evidence in court is determining which witnesses will testify as to its existence and validity, describe the circumstances of its discovery, and verify that it has not been tampered with.
When Authentication Is Not Required
Certain types of evidence are sometimes held by the rules of evidence to be self-authenticating. This means testimony as to authenticity isn't required and usually refers to such things as public documents under seal, certified copies of public records, official publications, and the like. It is also possible for both sides at trial to agree to stipulate as to the authenticity of a piece of evidence, in which case it does not have to be authenticated through testimony. When both sides agree to the stipulation of a fact (such as the fact that the evidence is authentic), the judge will advise the jury that they are to presume the fact is true and that it is not a matter that has to be proved or disproved at trial.
Defining Evidence
Evidence can generally be defined as the means by which an alleged fact, the truth of which is subjected to scrutiny, is established or disproved. The legal significance of any given piece of evidence lies in its influence on the judge or jury at trial. There are three categories of evidence:
▪ Physical evidence (sometimes called real evidence) Consists of tangible objects that can be seen and touched
▪ Direct testamentary evidence The testimony of a witness who can give an account of facts based on personal experience through the use of the five senses
▪ Circumstantial evidence Not based on personal observation of the offense but on observation or knowledge of facts that tend to support a conclusion indirectly but do not prove it definitively
It's “Only” Circumstantial
The news media and (via movies and novels) the entertainment industry—not to mention defense attorneys—often refer to evidence as “merely circumstantial,” with the implication that circumstantial evidence does not really constitute evidence or that it is inherently inferior to direct evidence. In fact, circumstantial evidence is equally admissible in court, and most criminals are convicted based on circumstantial evidence. This is because in many cases criminals do not commit their offenses in front of witnesses, so there is no one to testify to having seen or heard the offense occur. It is the totality of the evidence in the minds of the jury members that matters—whether all that evidence, taken together, persuades them beyond a reasonable doubt that the defendant committed the crime.
Here is an example of direct evidence as compared to circumstantial evidence:
▪ Direct evidence John Smith testifies under oath that he was in the room with his friend, Joe Hacker, when Joe broke into the ABC Corporation's computer network and that John saw the break-in take place on Joe's computer screen.
▪ Circumstantial evidence The network administrator of ABC Corporation testifies that an intruder using the Internet Protocol (IP) address xxx.xxx.xxx.xxx penetrated the network at 2:20 a.m. on December 12, 2001. Internet service provider (ISP) records show that the IP address in question was assigned via Dynamic Host Configuration Protocol (DHCP) to Joe Hacker's computer at that time on that date. Joe's girlfriend testifies that Joe was in the study “doing something on the computer” between the hours of midnight and 4:00 a.m. on that date. No one actually saw Joe perform the intrusion, and none of the evidence definitively proves that he did, but taken together, the evidence supports the conclusion that Joe Hacker broke into the ABC Corporation network.
In a computer crime case, evidence tends to be one of the following types, as classified by the SWGDE/IOCE standards:
▪ Digital evidence Information of value to a criminal case that is stored or transmitted in digital form
▪ Data objects Information of value to a criminal case that is associated with physical items
▪ Physical items The physical media on which digital information is stored or through which it is transmitted or transferred
Digital evidence can be classified as original digital evidence (that is, the physical items and data objects associated with those items at the time the evidence was seized) and duplicate digital evidence (referring to an accurate digital reproduction of all the data objects contained on an original physical item).
“Written” evidence is also sometimes classified as either demonstrative evidence or documentary evidence. Demonstrative evidence is that which reconstructs the scene or incident in question and allows jurors to view it, using visual aids such as graphs, charts, drawings, and models. Documentary evidence usually refers to written documents that constitute evidence. For example, a letter or photograph is generally considered documentary evidence. As we'll discuss in Chapter 17, when documents are introduced as evidence, the entire document must generally be admitted even though only part of it might be read to the court. In some cases of digital evidence, there is debate among legal scholars as to whether it should be classified as documentary or demonstrative. Computer evidence is not quite like other documentary evidence (which is usually paper) for several reasons: A copy of a digital file is generally identical to the original, and a document can be copied without physically removing it from its location or leaving behind any indication that it has been copied. Many legal experts consider digital evidence to be more demonstrative than documentary, because the field of computer forensics basically concerns itself with reconstructing the crime scene. However, this view could vary depending on the type of digital evidence associated with a particular crime.
Under the best-evidence rule, the original document must be presented as evidence unless it has been destroyed or falls under other exceptions. However, the Federal Rules of Evidence recognize that computer evidence is different from other written evidence. Rule 1001-3 addresses this issue, saying, “If data are stored by computer or similar device, any printout or other output readable by sight, shown to reflect the data accurately, is an original.” The burden is on the party introducing the evidence to show that it does indeed reflect the data accurately. It must be proven that the evidence is what it is claimed to be and that it hasn't been changed since it was taken into custody. Otherwise, the evidence will be deemed inadmissible.
Admissibility of Evidence
There are a number of requirements for evidence to be admissible in court. The evidence must be competent (that is, reliable and credible), it must be relevant (it tends to prove a fact of the case), and it must be material (it substantiates an issue that is in question in the case).
In addition, to be admissible in U.S. courts, evidence must be obtained legally. That is, it must be obtained in accordance with the laws governing search and seizure, including laws expressed in the U.S. and state constitutions. If evidence is obtained through an illegal search, even though it proves the guilt of the defendant, the evidence is considered to be “tainted.” This is known as the “fruits of the poisonous tree” doctrine, or the exclusionary rule.
Case law in some jurisdictions sets special rules for the admissibility of scientific evidence. Under the Federal Rules of Evidence, Rule 402, all relevant evidence is admissible except as otherwise provided under the U.S. Constitution, by Act of Congress, or under the Federal Rules of Evidence themselves (for example, evidence obtained in violation of a suspect's constitutional rights). Rule 401 defines relevant evidence as “any evidence having a tendency to make the existence of any fact that is of consequence to the determination of the action more probable or less probable than it would be without the evidence.” This is known as the relevancy test. Another standard sometimes applied to scientific evidence is the general acceptance test, also known as the Frye standard, which holds that a scientific technique must be generally accepted in the field before the results of the technique can be admitted as evidence.
Forensic Examination Standards
Although the rules of evidence regarding digital data are not clear-cut, it is always safest to exceed the minimum requirements for admissibility. When investigators take extra precautions to ensure the integrity of evidence, above and beyond what the court might find acceptable, not only will the possibility of having the evidence excluded by the judge be avoided, but the impression on the jury will be more favorable as well.
As we mentioned earlier in this chapter, a number of organizations provide standards governing forensic examination procedures for their members. Showing in court that you adhered to such high standards in conducting the investigation will enhance your case.
Most organizations and experts involved in computer forensics agree on some basic standards regarding the handling of digital evidence, which can be summarized as follows:
▪ The original evidence should be preserved in a state as close as possible to the state it was in when found.
▪ If at all possible, an exact copy (image) of the original should be made to be used for examination so as not to damage the integrity of the original.
▪ Copies of data made for examination should be made on media that is forensically sterile—that is, there must be no preexisting data on the disk or other media; it should be completely “clean” and checked for freedom from viruses and defects.
▪ All evidence should be properly tagged and documented and the chain of custody preserved, and each step of the forensic examination should be documented in detail.
Collecting Digital Evidence
A network administrator or another member of the IT staff will often be the first person to become aware of a cybercrime in a corporate setting, and the IT incident response team (if the company has one) will take the initial steps to stop the crime in progress and “freeze” the crime scene before law enforcement personnel take over. Even after the police are called in, the process of collecting digital evidence usually involves several people, who we previously discussed in detail in Chapter 5:
▪ First responders, who are officers or official security personnel who arrive first at the crime scene. These people are responsible for identifying the crime scene, protecting it, and preserving evidence.
▪ Investigators, or an investigative team, who is responsible for establishing a chain of command, conducting a search of the crime scene, and maintaining the integrity of the evidence.
▪ Crime scene technicians and specialists, who are called out to process the evidence, and who are responsible for preserving volatile evidence (which we'll discuss later in this chapter), duplicating disks, and preparing evidence for transport (including shutting down systems, and packaging, tagging, and logging evidence).
It is important that one person be designated in charge of the scene and be given the authority to make final decisions as to how the scene will be secured, how the search will be conducted, and how the evidence will be handled. This is usually the role of the senior investigator. It is equally important that each member of this team understand his or her role and adhere to it. The ability of the team to work together is essential to the successful collection of evidence.
Evidence Collection
Collection is a practice consisting of the identification, processing, and documentation of evidence. When collecting evidence, a crime scene technician will start by identifying what evidence is present and where it is located. For example, if someone broke into the server room and changed permissions on the server, the room and server would be where you would find evidence. When establishing this, the crime scene technician will then ensure that the crime scene has been secured, and that others have been prevented from entering the area and accessing the evidence. If the area wasn't secured, suspects could enter the area and alter or contaminate evidence. For example, if fingerprints were being taken to determine who broke into the server room, merely touching the door and other items would distort any findings. Maybe the perpetrator left the fingerprints while in the process of breaking in, or maybe someone else left them when the crime scene was not secure.
Once the evidence that is present has been identified, the next step is to identify how the evidence can be recovered. Evidence on computers may be obtained in a variety of ways, from viewing log files to recovering the data with special forensic software. If data recovery is needed, the computer's operating system should be identified, along with the media used to store the evidence. Once you've determined this, it is then possible to decide on the techniques and tools needed to recover the data.
In addition to photographing the screen of a computer to record any volatile data that's displayed, you should also photograph how the equipment is set up. When you've transported the equipment and are ready to begin examining it, you will need to set it up exactly as it was at the crime scene. After the case is completed, setup may also be required if the equipment is returned to the owner. To ensure that the equipment is set up properly, you should photograph the front and back of the machine upon seizing it. Photographs or diagrams should be made showing how cables and wires were attached.
Backup media should also be collected, as analyzing any backup tapes may show that an incident began earlier than expected. In some cases, you may find that data that was backed up days or even weeks before shows that an intruder entered a system, or a virus infected data on hard disks. If this were undetected, it is possible that you could unknowingly restore a virus to the system as part of the recovery process, and create a repeat of the initial incident.
Preserving Digital Evidence
Digital evidence is, by its nature, fragile. Some data is volatile—that is, it is transient in nature and, unlike data stored on disk, will be lost when the computer is shut down. Data on a computer disk can be easily damaged, destroyed, or changed either deliberately or accidentally. The first step in handling such digital evidence is to protect it from any sort of manipulation or accident. As we discussed in Chapter 6, the best way to do this is to immediately make a complete bitstream image of the media on which the evidence is stored.
As we've mentioned in previous chapters, a bitstream image is a copy that records every data bit that was recorded to the original storage device, including all hidden files, temp files, corrupted files, file fragments, and erased files that have not yet been overwritten. In other words, every binary digit is duplicated exactly onto the copy media. Bitstream copies (sometimes called bitstream backups) use cyclic redundancy check (CRC) computations to validate that the copy is the same as the original source data.
The “mirror image” should be an exact duplicate of the original, and the original should then be stored in a safe place where its integrity can be maintained. (See the “Environmental Factors” section later in the chapter.) The copy is made via a process called disk imaging. In some cases, evidence could be limited to a few data files that can be copied individually rather than creating a copy of the entire disk. In the following sections, we review a number of factors in preserving evidence and ensuring the integrity of disks used for imaging or copying. We consider environmental factors that can affect the integrity of evidence, as well as preservation concerns related to specific types of storage media.
Preserving Volatile Data
The data that is held in temporary storage in the system's memory (including random access memory [RAM], cache memory, and the onboard memory of system peripherals such as the video card or network interface card [NIC]) is called volatile data because the memory depends on electric power to hold its contents. When the system is powered off or if power is disrupted, the data disappears. According to the IEEE Internet draft titled “Guidelines for Evidence Collection and Archiving,” the most volatile evidence should be collected first. This makes sense because the most volatile evidence is the most likely to disappear before it can be documented or collected. The draft lists the “order of volatility” as follows:
Collecting volatile data presents a problem because doing so changes the state of the system (and the contents of the memory itself). Some experts recommend that investigators or crime scene technicians capture such data as running processes, the network status and connections, and a “dump” of the data in RAM, documenting each task or command they run to do so. You can do some of this work by running such commands as netstat (on both Windows and UNIX systems) and nbtstat (on Windows only) to view current network connections. The arp command will tell you what addresses are in the ARP cache (and thus have recently connected to the system). You can use the dd command to create a snapshot of the contents of memory on UNIX machines, and the ps command to view the currently running processes. On Windows machines, you can use the downloadable pslist utility to list running processes, or you can view them in the Task Manager. You can use other commands such as ipconfig (Windows) and ifconfig (UNIX) to gather information about the state of the network. You should run these programs from a special CD that you bring with you (instead of running the same commands from the hard disk of the suspect computer), and they should not require any programs or libraries from the computer's hard disk to run.
Special Considerations
Because certain kinds of digital evidence can be incredibly volatile, and all digital evidence can be damaged or compromised by improper copying, storage, or handling, it's essential to exercise extreme care and diligence when gathering and handling such evidence. Therefore, numerous special considerations can come into play, including environmental factors, retention of timestamps and date stamps, and ways to preserve specific types of data. We discuss these concerns in the following sections.
Environmental Factors
Magnetically encoded data can be destroyed or damaged (scrambled) by exposure to a magnet or an electromagnetic field generated by many types of electronic equipment. Radio frequency (RF) transmissions can also damage digital data, as can exposure to static electricity or extreme heat.
It is very important for investigators and crime scene technicians to be aware of environmental factors that can affect the integrity of data. They must be sure that digital evidence is packaged in such a way as to protect it from damage and that it is stored in an electromagnetically “clean” environment that is properly cooled.
When you're packaging magnetic or optical media (tapes, CDs, DVDs, hard disks, diskettes, ZIP/Jaz disks, and so on), first place the media inside an antistatic bag, and then place it in a box that has enough extra room so that you can “pad” it with bubble wrap, Styrofoam “peanuts,” or other protective material. Try to anchor the media against the bottom or side of the box so that it won't move around in transit. Be sure to list the contents on the outside of the box and identify it as evidence (with the case number). Labels warning carriers to handle the package carefully might also be appropriate. If you are shipping or mailing the package, use a method that allows tracking (registered mail when using the U.S. Postal Service).
Retaining Timestamps and Date Stamps
The time and date of creation or modification of a file can be an important issue in a criminal case. Remember that the timestamp and date stamp on the files will be in accordance with the time and date set on the system clock. Some systems default to a particular time zone (usually Greenwich Mean Time, or GMT). If the user set up the system without configuring the proper time zone or if the user deliberately changed the date and time settings, the timestamp and date stamp on the files might not correlate to “real-world” occurrences regarding when the files were created.
This can be a problem if, for example, the system records show that a file was created on a particular date and the suspect is able to prove that he or she was nowhere near the computer on that date. For this reason, you should note the system time and date settings before shutting down the computer and document them with a photograph, if possible; otherwise, with written notes.
Opening a file changes the file's time and date records. Thus, it might be prudent to photograph the screen showing the file access or modification times prior to opening the file. You should be prepared to testify as to your actions and provide expert testimony that the actions you took changed the timestamp and date stamp but did not modify the contents of the file in any way. When you do all your work on an image rather than the original, the original times and dates will be on the original disk. You can create a second copy of the original to illustrate this fact.
Write Protection
Write protection prevents any data from being written to storage media so that in the case of a forensic investigation, the data on the original hard disk isn't modified or deleted. Write protection is important in forensics, because even the slightest modification to a file could destroy information that might be important in an investigation, and bring the validity of the data into question in court.
Probably one of the easiest examples of showing how write protection works is a floppy disk. As shown in Figure 15.1, on the upper-left corner of the back of a 3.5-inch floppy disk is a tab that you can switch to an open or closed position. When you slide the tab to a bottom position so that the hole is closed, you can write to the disk. If you were to open a file that was saved on the disk, the LastAccessed Date property of the file would be modified, showing that it was last accessed at the current date and time. To avoid modifying the disk, you could slide the tab to the top position, creating a hole in the disk and write-protecting the disk. In doing so, if the file were opened, the file and its properties could not be modified, so the date that the file was last accessed would still show a previous date.
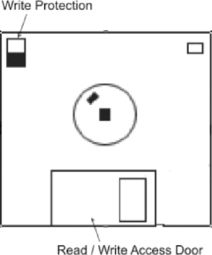 |
| Figure 15.1 Write Protection on a Floppy Disk |
Other media may not even require that you worry about modifying the data. For example, when a CD-R or DVD-R is being examined, it cannot be modified because once the data has been stored on the disk, it cannot be written to again. This may not be the case, however, if you were accessing rewritable optical disks, such as a DVD-RW or CD-RW, which can be written to and modified multiple times.
When dealing with hard disks and other storage devices that can be written to over and over again, simple measures such as flipping a tab aren't available, so you must use other methods. To ensure write protection, you can use hardware- or software-based solutions. Some forensic software provides write protection so that any data suspect's computer isn't modified as an image is being created on another storage device. An even better solution is hardware-based write blockers. The hard disk is connected to the hardware, while a Universal Serial Bus (USB), FireWire, serial, or parallel cable is used to connect the write blocker to the examiner's computer. The forensic software connects to the hard disk through this device, which passes data from the hard disk to the examiner's computer, where an image of the disk is created. In doing so, no data is modified on the original drive.
Recovering Digital Evidence
In some computer crime cases, the evidence you need will be neatly stored on the hard disk (or on easily accessible removable media), with the files conveniently labeled to indicate their contents. In other cases, the investigator is not quite so lucky. Cybercriminals might get wind of the fact that they're about to be “busted” and delete incriminating data or even format and/or repartition the disk. Some particularly tech-savvy cybercriminals use sophisticated techniques to hide data in unlikely or nontraditional areas. Other times, the data that would be useful to the investigator is never stored on disk at all—at least, not to the computer user's knowledge. However, a great deal of ambient data is stored in locations such as cache files, swap/page files, and temporary (temp) files, as well as “leftover” data that occupies the “unallocated” space on the disk, the “slack” space in clusters that are larger than the files they hold, and the “gaps” between partitions or sectors. In the following sections, we review and expand on some of the ways that investigators can recover data that is not immediately apparent when browsing the file structure but that can prove critical to building a criminal case.
Deleted Files
Many computer users—including cybercriminals—think that when they delete a file, it is erased from the hard disk. Even so-called computer experts have been heard to say on television and radio that once the Windows “trash” has been emptied, the files there are gone from the disk. As we saw in Chapter 7, this simply isn't true. Deleting a file does not remove the contents of the file; it merely removes the pointer to that file from the File Allocation Table (FAT), Master File Table (MFT), or other scheme that the operating system uses to pinpoint the location of a particular file on the disk. Data is stored on the disk in clusters, which are units consisting of a set number of bits. Because parts of a file are not always stored in contiguous clusters on the physical disk, but instead parts of it could be spread across the disk in separate locations, removing the pointer makes it difficult for the file to be reconstructed—but difficult does not equal impossible.
When the file is deleted, the disk location in which it is stored is marked as unallocated space, which means that it is available when new data needs to be written. However, on a large disk it might be a long time before that particular part of the disk is used to write new data. In the meantime, the old data is still there and can be recovered if the investigator has the proper tools.
A brand-new disk is thought of as being “clean,” or completely empty, but in reality it is full of format characters, which are repeated characters that are made by the test machine at the factory. When files and directories are created and saved to disk, they overwrite the format characters. When the files or directories are deleted, the clusters in which they are stored are not reallocated until new data is written there. Formatting the disk does not remove this data. Even if the disk is repartitioned, the data is still there until those clusters are overwritten.
Supposedly erased data can be located in many places on a computer. For example, when a disk is repartitioned, it is possible for data from the previously configured partitions to end up in the space between partitions, called the partition gap. Disk search tools can locate this hidden data, which can then become a potential source of evidence for investigators.
Data Recovery Software and Documentation
In Chapter 6 and Chapter 7, we discussed a number of different tools that you can use to acquire evidence using disk imaging, or perform other tasks related to a forensic investigation. To make it easier to analyze data acquired with these tools, many of these tools include features that allow you to review the data stored in the image files. Tools such as X-Ways Forensics, EnCase, and other include the following features:
▪ A gallery view so that you can view thumbnails of images recovered from a suspect computer or other media
▪ A calendar view to view when data was stored on specific areas of the computer
Many of these tools provide documentation features so that the actions taken while acquiring the data are recorded and can be printed in a report. EnCase will document when the acquisition of data from a suspect machine began and ended, can generate a report with thumbnails and other information about pictures found on the computer, lists files and their locations, and generates other reports that reduce the amount of information you manually have to keep track of.
Decrypting Encrypted Data
As you learned in Chapter 12, encryption is a method of scrambling data so that it can't be read by anyone who doesn't have the password or key to decrypt it. Cybercriminals often use encryption to conceal the criminal nature of their data. They could encrypt e-mail messages that include incriminating statements, or they could encrypt documents that could be used as evidence or pornographic pictures of children that constitute contraband.
Cryptanalysts specialize in “cracking” encryption algorithms. Strong encryption is difficult to break, but in many cases cybercriminals use relatively weak methods such as the password protection for Office documents that comes built into the applications. As we discussed in Chapter 11, a number of “password recovery” programs exist ostensibly for use by legitimate users who protect documents and then forget their passwords. These programs can also be used to crack the passwords on Word or Excel documents. They are basically brute force/dictionary attacks. Some programs are designed to crack the passwords used by the Outlook Express e-mail client, Internet Explorer passwords for protected Web sites, files created by Quicken and QuickBooks financial management programs, password-protected PDF files, password-protected .zip files and other archives, and many more. For information about many of these password-cracking programs, see www.crackpassword.com.
Finding encrypted documents stored on a suspect machine can be relatively easy. Tools such as X-Ways Forensics provide a feature that automatically detects encrypted Microsoft Office and PDF files. Paraben (www.paraben-forensics.com) also markets a “decryption collection” software suite as part of its line of forensic programs. The suite is designed to crack passwords for a large number of popular software programs and file types, including the Windows operating systems, Exchange, VBA Visual Basic modules, and many more.
Documenting Evidence
Throughout this book, we've stressed the importance of documenting how evidence is collected and acquired through the use of forensic hardware and software. According to Digital Evidence Standards and Principles, developed by the SWGDE and IOCE in 1999 and published in the April 2000 issue of Forensic Science and Communications (a publication of the FBI), “[C]ase notes and observations must be in ink, not pencil, although pencil (including color) may be appropriate for diagrams or making tracings. Any corrections to notes must be made by an initialed, single strikeout; nothing in the handwritten information should be obliterated or erased. Notes and records should be authenticated by handwritten signatures, initials, digital signatures or other marking systems.”
As we'll discuss in Chapter 17, documentation may also be useful as a personal reference, should the need arise to testify in court. Because of the technical nature involved, you may need to review details of the evidence before testifying at trial. Without it, your memory may fail you at a later time, especially if a case doesn't go to court until months or years later. You can also refer to these notes on the stand, but doing so will have them entered into evidence as part of the court record. As the entire document is entered into evidence, you should remember not to have notes dealing with other cases or sensitive information about the company in the same document, as this will also become public record.
In the following sections, we discuss the evidence documentation procedures in a cybercrime investigation. We look first at how evidentiary items should be tagged or marked and the practice of keeping an evidence log. Then we discuss how the analysis of evidence should be documented by the person(s) performing the forensic examination. Finally, we discuss the chain of custody and the importance of documentation to preserving the integrity of the chain.
Documentation plays a vital role in any investigation. You should remember that documentation must be maintained throughout an investigation, and that it may be used in court. Documentation may be referred to, it may be used to challenge what you did, or you may use it when providing testimony as a personal reference.
Evidence Tagging and Marking
Evidence management begins at the crime scene, where it is bagged and/or tagged. When the crime scene is being processed, each piece of evidence should be sealed inside an evidence bag. An evidence bag is a sturdy bag that has two-sided tape that allows it to be sealed shut. Once the bag is sealed, the only way to open it is to damage the bag, such as by ripping or cutting it open. The bag should then be marked or a tag should be affixed to it, identifying the person who initially took it into custody. The tag would provide such information as a number to identify the evidence, a case number (which shows the case with which the evidence is associated), the date and time, and the name or badge number of the person taking it into custody. A tag may also be affixed to the object, providing the same or similar information to what's detailed on the bag. However, this should be done only if it will not compromise the evidence in any manner.
Information on the tag is also written in an evidence log or chain of evidence form, which is a document that inventories all evidence collected in a case. In addition to the data available on the tag, the chain of evidence form will include a description of each piece of evidence, serial numbers, identifying marks or numbers, and other information that's required by policy or local law.
Evidence is tagged and/or marked by the person who originally takes it into custody. That person places his or her initials or name on the item, along with the date and time and the case number. Physically marking the evidence is preferable when possible, because tags can become separated from items, thus damaging the chain of custody. Items that can't be physically inscribed can be placed in a bag or contained and sealed, and then the container can be marked. The mark should be made using a permanent ink or marker.
Evidence Logs
The evidence log is a document that lists all evidence collected in a criminal case, with a description of each piece of evidence, who discovered and collected it, the date and time of collection, and the disposition of the evidence. The description should be detailed enough to differentiate the item from others like it and should include serial numbers and other identifying numbers when possible. The log should show all transfers of custody of the evidence from one person to another. This process of logging the transfer of evidence is tangible proof of the preservation of the chain of custody.
Documenting the Chain of Custody
The term chain of custody refers to continuity of the evidence. That is, you must be able to trace the route that the evidence has taken from the moment it was collected until the time it is presented in court, every person whose hands it has passed through, and when and where it was transferred from one person to another. Documentation of the chain of custody is one of the most important purposes of the evidence log.
Any break in the chain of custody opens the prosecution to allegations that the evidence has been tampered with or that other evidence has been substituted for it. Proof of chain of custody is provided by testimony of the person who collected the evidence, establishing that the item presented in court is in fact the same evidence that was collected (or is an exact representation of that evidence), that the evidence was not tampered with while in his or her custody, and when and where custody of the evidence was transferred to the next person in the chain. This same process can be followed with each person who had custody of the evidence.
Obviously, the fewer people who handle the evidence, the easier it will be to preserve the integrity of the chain. It is a best practice to designate one person as the custodian of the evidence. Sometimes computer evidence must be delivered to a lab or service that handles data recovery/computer forensics, however. If the designated custodian is unable to stay with the evidence (keeping it within his or her sight) while it is processed, the lab or technician should provide a receipt when the evidence is delivered, and the evidence should be examined by the custodian when it is retrieved, to ensure that it is the same evidence. The lab technicians will also need to testify as to what happened to the evidence while it was in their custody and how it was stored and protected at the lab.
The Chain of Custody Form
A chain of custody is also sometimes referred to as a chain of evidence, as it shows how evidence made it from the crime scene to the courtroom. To prove where a piece of evidence was at any given time, and who was responsible for it, a chain of custody form is often used to document who had possession of it and to establish that the integrity of evidence wasn't compromised.
The chain of custody form provides a log that details who had custody of the evidence. This document will be used to describe who had possession of the evidence after it was initially tagged, transported, and locked in storage. To obtain possession of the evidence, a person will need to sign in and sign out evidence. Information is added to a chain of evidence form to show who had possession of the evidence, when, and for how long. The form will specify the person's name, department, date, time, and other pertinent information.
In many cases, the investigator will follow the evidence from crime scene to court, documenting who else had possession along the way. Each time possession is transferred to another person, it is written on the form. For example, the form would show the investigator had initial custody, and the next line might show that a computer forensic examiner took possession on a particular date and time. Once the examination is complete, the next line would show that the investigator again took custody. Even though custody is transferred back to the investigator, this is indicated in the log so that there is no confusion over who was responsible on any date or at any time.
Documenting Evidence Analysis
When the bitstream image of the suspect computer's disk(s) is analyzed, a log should be kept documenting the evidence analysis. This log should show each step of the analysis process, including who was present, what was done (for example, running a software utility to remove binary data from a swap file), the result of the procedure, and the time and date. As the data on the disk is assessed for its evidentiary value, you should document all potential evidence that is found. For example, if you open a .jpg file that appears to be a pornographic photo of a child, document the filename, where on the disk it was located, the date stamp and timestamp, and other file properties. In addition to the volatile data and obscure areas on the disk where data hides that we discussed earlier (slack space, unallocated space, partition gaps, and so forth), some of the data that should be examined for evidence, depending on the type of cybercrime offense, includes:
▪ A list of Uniform Resource Locators (URLs) recently visited (obtained from the temporary Internet files or Web cache and History folders)
▪ E-mail messages and a list of e-mail addresses stored in the suspect's address book; the filename depends on the e-mail program in use—for example, the .pst file for Outlook (in some cases, this information will be stored on an e-mail server, such as an Exchange server)
▪ Word processing documents; the file extensions depend on the programs used to create them—common extensions are .doc, .wpd, .wps, .rtf, and txt
▪ Spreadsheet documents; the file extensions depend on the programs used to create them—examples include .xls, .wg1, and .wk1
▪ Graphics, in the case of child pornography cases; the file extensions include .jpg, .gif, .bmp, .tif, and others
▪ Chat logs; the filename depends on the chat program
▪ The Windows Registry (where applicable)
▪ Event viewer logs
▪ Application logs
▪ Print spool files
The Final Report
Once evidence has been examined, the documentation that has been compiled is used to create a final report that outlines what actions have been taken, and what has been found on the suspect's machine. The final report will include a statement regarding what occurred during the investigation process, information you acquired and generated during the analysis of a suspect machine, and printouts of pertinent data. For example, in an Internet luring case (where an online predator seduces a child into having sex), the chat logs from their conversations would be included in the final report. Excerpts from the chat may be included to indicate important parts of the document that the investigator should be aware of, as well as the complete log. In situations where pornography was found on a machine, printouts of thumbnails would also be included in the report, with information on the filename, full path to its location on the suspect's hard drive, file size, and time and date information. As you can see from this, the specific information included in the final report can depend on what the case involved, and on what was found on the machine.
Computer Forensic Resources
Computer forensics is a relatively young field, with standards that were quickly established and are still evolving. A large number of resources are available to aspiring computer forensic experts. Cybercrime investigators who want to expand their knowledge, corporate IT personnel who are interested in specializing in this area, and crime scene technicians who want to learn to deal with digital evidence will all find a plethora of training programs, equipment, and software available. Investigators who prefer to “farm out” the technical aspects of digital evidence examination will find many commercial services that do imaging, data recovery, and related tasks. Many of these services employ people qualified to testify as expert witnesses in court. Several associations and organizations provide white papers, articles, and other information sources to keep computer forensic personnel updated on the latest developments in the field. The following sections provide an overview of some of these resources.
Computer Forensic Training and Certification
Training programs are available through private companies that make forensic software and equipment, such as NTI (www.forensics-intl.com/training.html) and DIBS (www.dibsusa.com/training/training.html), through community colleges and universities, through some law enforcement in-service academies, and through computer crime/forensic associations and organizations.
There are at least a couple of recognized certification programs in computer forensics:
▪ IACIS provides a Certified Forensic Computer Examiner (CFCE) certification for individuals, both in law enforcement and outside law enforcement, who submit an application demonstrating extensive knowledge, training, and/or experience in the field of computer forensics, along with an understanding of forensic procedures, standards, ethics, and legal and privacy issues. Candidates must have technical knowledge and skills and have the equipment necessary to conduct forensic examinations. To earn the certification, candidates undergo a rigorous testing process in which they must complete a number of hands-on problem-solving exercises, prepare reports and present the evidence obtained, and then pass a written examination. For more information about the CFCE certification, visit the IACIS Web site at www.cops.org.
▪ The High Tech Crime Network (HTCN) offers basic and advanced Certified Computer Forensic Technician and Certified Computer Crime Investigator certifications. To obtain the certifications, applicants must demonstrate a minimal level of combined education and experience (in either law enforcement or corporate environment) and submit documentation derived from at least 10 cases. For more information, see www.htcn.org/cert.htm.
A good computer forensic training course should cover theory, process, and methodology and include hands-on practice in techniques and tools.
Computer Forensic Equipment and Software
A number of companies including Guidance Software (www.guidancesoftware.com) and DIBS (www.dibsusa.com) market special equipment to aid in forensic examinations. The following types of equipment can be useful to investigators and forensic technicians:
▪ Imaging equipment These devices allow you to rapidly make bitstream copies of hard disks onto another hard disk, an optical cartridge, or a tape. Portable units that fit into a suitcase are available and can be easily transported to the crime scene to make disk copies on-site before the computer is shut down. The target media include write-protection features to ensure that data cannot be tampered with after the copies are made.
▪ Forensic workstations These are complete computer workstations set up for easy reconstruction and analysis of copied drives, usually with removable drive racks that allow booting of the “working copies” of suspect disks. Analysis software is installed to assist in searching for particular types of data using artificial intelligence techniques or fuzzy logic to conduct searches when the investigator isn't sure of the text strings or file types he or she is looking for. Data recovery software is installed to locate data from “deleted” or “erased” files. Mobile workstations set up on portable computers are also available. Examples include the DIBS forensic workstations and F.R.E.D., the Forensic Recovery of Evidence Device, which is made by Digital Intelligence (www.digitalintel.com/fred.htm).
▪ Forensic software Packages provided by companies such as Guidance Software, NTI, and DIBS include imaging software, “undelete” programs, comprehensive file and text string search programs, programs that can verify the accuracy of bitstream copies, programs that can remove binary characters from data to ease analysis of the data, programs that quickly document lists of files and directories, programs that can capture the data in unallocated space or file slack space, programs that can rebuild cache, uncompression tools, system-checking utilities, steganography detection software, password recovery programs, and much more. For a list of some of the best computer forensic software programs, see the Timberline Technologies Web site at www.timberlinetechnologies.com/products/forensics.html. Also, NTI provides several free forensic tools at www.forensics-intl.com/download.html.
Building a Forensic Workstation
You can build your own forensic workstation using either a portable or a desktop computer instead of buying the prepackaged hardware/software combination. The system should be powerful enough to run forensic application software, and to avoid having to upgrade the equipment too soon, it should have the most powerful processor and most amount of RAM available (or at least that you can afford). To store evidence files that are created, you will also need a significant amount of hard disk space. It is not uncommon for computer forensic labs to have terabytes of hard disk space to store the evidence files, which will also need to be backed up on a regular basis in case of a hard disk failure or other problems.
The workstation should run an operating system compatible with your forensic application software. You might find it useful to set up a dual-boot configuration so that you can boot into either Windows or Linux, or you can run VMware (www.vmware.com) virtual machines to allow you to view an New Technology File System (NTFS) formatted disk, for example, from within the Linux operating system using a Windows virtual machine.
Computer Forensic Services
A huge number of companies offer data recovery and other computer forensic services. Many of these services work on a consultant basis and provide expert witnesses for court testimony. Services might bill by the hour or by the job, and some services offer discounts or even free services to law enforcement agencies. Full-service companies might also rent forensic equipment to investigators who want to do their own forensic work, and they might provide training in computer forensics.
Most medium-size to large U.S. cities have one or more local firms specializing in computer forensics or offering these services as part of their businesses. From one-person operations to large, well-known companies such as Ernst & Young, this hot field is expected to expand even more as computer crime awareness continues to grow. This is particularly true in the wake of terrorist attacks and subsequent information that terrorist networks use the Internet and might plan future attacks on critical IT infrastructures.
We recommend that when you consider employing a computer forensic service or expert, you inquire about his or her training and certification, professional association memberships, and past experience and ask for references from past clients. Law enforcement agencies should also keep in mind that in many cases, other law enforcement agencies will provide forensic services, either as a courtesy or for a fee, to smaller agencies that don't have the equipment or personnel to do their own computer forensic work. Check with larger municipal and county agencies in your area, the state police or department of public safety, and, in cases of high-profile or important cases, the FBI and other federal agencies for assistance.
Computer Forensic Information
Computer forensics is a field that is not only growing fast but changing fast as well. New techniques and technologies are being developed and proven all the time, and it's important that investigators keep up with the latest news in the field. There are several ways to stay current, including:
▪ Reading computer security information available through government and computer security sites on the Internet.
▪ Attending seminars and conferences that focus on computer crime and cybercrime, which may be hosted by law enforcement organizations or private companies. An example of one such conference is the Techno-Security Conference, of which information is available at www.techsec.com.
▪ Joining associations of computer forensic and cybercrime investigation professionals, such as IACIS (www.cops.org), the International High Technology Crime Investigation Association (http://htcia.org/), the High Tech Crime Consortium (www.hightechcrimecops.org), and others.
Understanding Legal Issues
Computer forensics is concerned as much with complying with the law and following prescribed procedures for evidence collection as it is with the technical aspects of collecting digital evidence. Evidence that is inadmissible in court is worse than useless; not only can illegal search and seizure damage or destroy the prosecution's case and result in a cybercriminal going free, but it can also result in administrative or even criminal actions against officers who violate the rules.
Thus, it is imperative that law enforcement officers and others who will be involved in the collection and preservation of evidence understand the legal issues under which they operate. The laws vary from one jurisdiction to another and change on a regular basis, so all cybercrime investigators should make it a practice to stay up-to-date on passage of statutes and court decisions that apply to their jurisdictions.
This chapter does not purport to give legal advice. The following sections are intended only to provide an overview of some of the laws and court cases that pertain to search and seizure of computers and digital evidence.
Searching and Seizing Digital Evidence
A search was legally defined by the courts in State v. Woodall as “an examination of a man's house or other buildings or premises, or of his person, or of his vehicle, aircraft, etc., with a view to the discovery of contraband or illicit or stolen property, or some evidence of guilt to be used in the prosecution of a criminal action for some crime or offense with which he is charged” (according to Black's Law Dictionary). A seizure was defined in Molina v. State as “the act of taking possession of property, e.g., for a violation of law or by virtue of an execution” [of a warrant].
Traditional ideas of search and seizure did not take into account the ways in which computers are used today as a repository of information (and potential evidence). The courts have had to develop interpretations of the law to apply to the unique aspects of these digital “places” and the types of evidence that can be found there. For example, the laws generally restrict entering a person's private premises to conduct a search without a warrant, except under certain restricted circumstances. Courts have generally held that a person has a reasonable expectation of privacy when information is stored in a computer, similarly to the contents of a closed container. On the other hand, when evidence is in plain view in a public place, the law allows officers to seize it.
Some general principles govern search and seizure in the United States based on the federal laws and the U.S. Constitution. Be aware, however, that states can impose further restrictions on police powers within their boundaries, so understanding federal guidelines is only the starting point. In the following sections, we discuss these general principles with these caveats in mind.
U.S. Constitutional Issues
The Bill of Rights of the U.S. Constitution consists of 10 amendments designed to protect the citizenry from government oppression and guarantee certain basic human rights to the people of the United States. One of the most important amendments in terms of its impact on law enforcement is the fourth, violation of which is common grounds for suppression of evidence in criminal trials.
Understanding the Fourth Amendment
The Fourth Amendment to the U.S. Constitution prohibits “unreasonable” searches and seizures. Specifically, it states: “The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no warrants shall issue, but upon probable cause, supported by oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.”
Perhaps one of the most important things to understand about the Fourth Amendment is that its restrictions apply only to agents of the government such as the police and other public employees or public officials. A private party cannot violate a suspect's Fourth Amendment rights unless acting at the direction of the police or another government agency. In other words, if a landlord searches a tenant's home or an employer searches an employee's office, it is not a Fourth Amendment violation. However, such a search could be a violation of privacy and a basis for a civil suit in some cases and not in others; for example, courts have held that an employee generally does not have an expectation of privacy in an office owned by the employer.
How does this interpretation apply to search and seizure of computers? Again, only an agent of the government is prohibited by the Fourth Amendment from searching a computer's hard disk. In United States v. Hall, a case involving a computer repair person who found child pornography on a client's computer, the court held that “the Fourth Amendment does not apply to searches conducted by private parties who are not acting as agents of the government,” and in United States v. Jacobsen, the court held that “the Fourth Amendment is wholly inapplicable to a search or seizure, even an unreasonable one, effected by a private individual not acting as an agent of the Government or with the participation or knowledge of any governmental official.”
Thus, if a private party searches a computer and finds evidence of a crime, and then contacts law enforcement authorities who obtain a search warrant based on the private party's information, this does not constitute a violation of the computer owner's constitutional rights.
In fact, the Supreme Court has held (United States v. Jacobsen) that law enforcement agents can reenact the original private search without a warrant and that this does not constitute a violation of reasonable expectation of privacy. However, if officers exceed the scope of the original search, evidence can be suppressed, as it was in United States v. Barth, when a computer repair technician found child pornography on a customer's computer and agents looked at additional files that the technician had not viewed in his original search. The evidence originally viewed by the technician should have been used to obtain a search warrant to seize and view the additional files.
Case Law Governing Search and Seizure
We can look to many court cases for guidance in regard to search and seizure in general and search and seizure regarding computer equipment and electronic evidence in particular. Katz v. United States held that a search is considered to be constitutional if it doesn't violate a person's reasonable or legitimate expectation of privacy. Circumstances under which a person does or does not have a reasonable expectation of privacy are open to debate and generally must be decided by the courts in a particular case, although there is case law that establishes certain premises:
▪ In Payton v. New York, the Supreme Court held that there is a reasonable expectation of privacy when a person is inside his or her own home.
▪ In United States v. Ross, the Supreme Court held that there is a reasonable expectation of privacy regarding the contents of closed opaque containers.
Some court cases have established that a person has a reasonable expectation of privacy in the data stored on the hard disk of a computer (United States v. Barth and United States v. Blas). On the other hand, courts have ruled that when a person makes computer information publicly available, the reasonable expectation of privacy is lost. Katz v. United States held that “what a person knowingly exposes to the public, even in his own home and office, is not a subject of Fourth Amendment protection.” Posting information on a Web site open to the public would obviously eliminate the expectation. Generally, information in transit (such as a message sent across the Internet) has been held not to constitute public exposure or sacrifice the expectation of privacy. However, the expectation might be lost when the message reaches the recipient. It has also been generally held that a person relinquishes the expectation of privacy if he or she turns information over to someone else whose use of it he or she cannot reasonably expect to control. Other cases have found that “mere information” revealed to third parties does not fall under reasonable expectation of control or privacy.
When there is no reasonable expectation of privacy, such as when property is abandoned or when evidence of a crime is displayed in plain view in a public place, officers generally can search and seize without a warrant. When circumstances create a reasonable expectation of privacy, a search warrant is required.
Search Warrant Requirements
A search warrant is a document signed by a magistrate giving law enforcement officers the authority to search a specified place for specific items that are particularly described in the warrant. A warrant must be based on another document called an affidavit, which is signed under oath by some person (a police officer or any other person) expressing the belief that certain items will be found at the location to be searched and giving facts that support the belief. Those facts must constitute probable cause that the objects of the search will be found at the described location. Only those items specifically named in the warrant can be searched for. A warrant can authorize the search and seizure of computer hardware, digital information, or both. Overly broad language (such as authorization to seize “all records” or “all computers”) can result in the warrant being invalidated; the warrant must specify the crime(s) to which the evidence pertains.
Affidavit Checklist
The affidavit for a search warrant should articulate probable cause that:
▪ An offense has been committed (specify by name and penal code number).
▪ Digital evidence is located at the named location.
▪ The digital evidence is associated with the crime (tell how).
▪ The digital evidence is associated with a particular person/suspect (name or describe).
The affidavit should be specific enough to satisfy the legal requirements but remain as general as possible so as not to exclude any evidence that might be found.
Search warrants can be obtained to search for specific types of property or for a person. State laws usually define exactly for what things a search can be issued. For example, under the Texas Code of Criminal Procedures, section 18.02, search warrants can be issued to search for any of the following:
▪ Property that was acquired illegally (through theft, fraud, and so on)
▪ Property that was made, designed, or adapted for use to commit an offense and implements or instruments that were used in committing a crime (the tools of the crime, such as a computer used to launch a network attack)
▪ Contraband (property that is illegal to own; this would include child pornography intended for the suspect's own use)
▪ Illegal drugs, prohibited weapons, and illegal gambling equipment
▪ Obscene material for commercial distribution (this would include child pornography intended for commercial distribution as well as other materials deemed “obscene” that are intended for commercial distribution)
▪ A person
Search warrants and the supporting affidavits must follow strict guidelines as to form and content, and the reliability of the affiant (the person signing the affidavit) must be established to the satisfaction of the magistrate who issues the warrant. From the officer's point of view, it is always preferable to have a search warrant rather than searching without a warrant, because a warrant relieves the officer of the responsibility of showing that probable cause and/or applicable exceptions to the search warrant requirements existed.
Generally, a copy of the search warrant must be served on the person in control of the premises being searched or left or posted in a prominent place if there is no one there to accept service. In some cases, courts have authorized so-called “sneak and peek” warrants that do not require officers to provide notification that a search has been conducted.
A related matter is the “no-knock” warrant. Generally, officers are required to announce their presence when they serve a search warrant and identify themselves as law enforcement officers. However, courts have held that the announcement is not required if it would result in danger to the life of some person or destruction of evidence. Because computer evidence can be so easily and quickly destroyed, officers with search warrants for digital evidence are often held to be justified in foregoing the announcement.
Special problems can arise in constructing search warrants for electronic evidence, because of the intangible nature of the evidence. For example, a suspect can move or destroy computer data quickly and easily without leaving the premises. A person with technical expertise should advise the officers and magistrate regarding the technical aspects of searching for and collecting digital evidence based on the facts of a particular case. It is just as important, if not more important, to gather all the information possible about the object of the warrant in a computer-related case as in one involving the search of a physical location. This includes the hardware platforms, operating system environment, and software applications in use, as well as the network connections and configuration. This specificity will help pinpoint the types of files to look for in the search and possible locations where they might be stored.
Searches without Warrants
In some circumstances, Fourth Amendment protections don't apply because the action is deemed not to be a search. If police take a vehicle into custody (for example, because they have arrested the person who was driving it), they are allowed to inventory the contents of the vehicle as a standard procedure. This does not constitute a search because it is not done for the purpose of looking for evidence of a crime but for the purpose of protecting the owner's property (and protecting the agency against claims of theft). However, this exception does not allow police to open locked containers, such as a briefcase, as part of the inventory process. To do so, they would generally need a warrant (unless some other exception, such as exigent circumstances, applies). A laptop or other computer that is in the vehicle when it is seized would generally be treated like a closed container in that in most cases law enforcement agents should obtain a warrant to open it and view the data on it.
There are a number of other exceptions to the requirement for a search warrant, as established by statutes and court cases. These include:
▪ Consent searches
▪ Abandoned property
▪ Exigent circumstances
▪ Plain view
▪ Search incident to arrest
Consent Searches
If the party who has control over the premises or thing to be searched gives voluntary consent to the search, officers don't need a warrant. This is called a consent search. Officers don't even need to show probable cause of a crime; they can legally search with consent even if there is no reason whatsoever to believe that a criminal offense has occurred. The key element here is that the consent must be voluntary. If consent is obtained under duress, threat, or intimidation, it is not voluntary and thus is not valid.
Furthermore, the person giving consent must have the authority to do so. For example, courts have held that a landlord cannot give consent for officers to search a tenant's home. On the other hand, courts have also held that employers can give consent to search employees' offices and school administrators can give consent to search students' lockers. In determining the legality of a search, courts consider the authority of the person giving consent and the scope of the consent. That is, if a person gives consent to search his house, does that include searching the contents of his computer's hard disk?
The Joint Ownership Dilemma
Generally, if two or more people have joint ownership of a computer (for example, two roommates), consent has to be obtained from only one of the owners to conduct a legal search. The computer is then considered to be a “common area,” much like the shared areas of a home. However, one party does not have the authority to give consent to search the other's “private areas” such as a bedroom used exclusively by one roommate. Likewise, the roommate could not legally give consent to search a computer solely owned by the other roommate. Even on a commonly owned computer, the use of password protection or file encryption by one roommate can establish that those files are part of a “private area” on the computer, and if the other roommate has not been given the password or key, he or she does not have authority to consent to a search of those files.
Generally, a spouse can give valid consent to search the property of the other spouse, and parents can give consent to search the property of their children who are under 18 years old. In the case of adult children who live with their parents and pay rent, the situation becomes more like that of roommates, in that parents can consent to searches of common areas but not private areas where the children have demonstrated expectation of privacy (for example, by putting locks on the doors or encrypting files).
In most cases, system administrators have been held to have the authority to give consent to search files stored on a network, if network users have no reasonable expectation of privacy in files stored on the network (as in the case in which the files are created in the course of an employee's job and are stored on the employer's network). If the administrator does not have clear authority to give consent, it must be determined who does (such as senior management).
Abandoned Property
Law enforcement officers are generally allowed to search property that has clearly been abandoned without obtaining a warrant. For example, if a suspect is carrying a CD or USB flash drive and, upon observing that police are in the area, throws the disc in a public trashcan, officers can lawfully retrieve it.
Exigent Circumstances
Another situation in which searches can be conducted without a warrant is the case of exigent circumstances—that is, an emergency in which there is no time to get a warrant and the search is required immediately to save a life or prevent physical injury to some person, to keep the suspect from escaping, or to prevent evidence from being destroyed. This last situation is most applicable to digital evidence because of its fragile nature. It is very easy to destroy evidence that consists of computer data. In United States v. David and United States v. Romero-Garcia, the courts held that seizure of electronic evidence without a warrant was legal because the evidence was about to be destroyed.
An important tenet regarding the exigent circumstances exception is that law enforcement officers cannot create the exigency. In United States v. Reyes, the court ruled against the government when the argument was made that incoming messages or battery failure could destroy the evidence in a pager, because the officers created the exigency by turning the pager on.
Plain-View Searches
The concept of plain view (sometimes also referred to as the open fields doctrine) rests on the premise that the law enforcement officer is legally in a particular place where he or she can see obvious evidence of a crime in plain view. Because the contents of a file stored on a computer are usually not in plain view (unless the officer lawfully entered the room where the suspect had the file open on the screen), this doctrine is not often applied to electronic evidence.
This issue has come into play when officers had a warrant to search for evidence of one crime (for example, child pornography) and during that legal search came across evidence of a different crime (for example, a photo indicating that the suspect had committed a murder). Courts have generally held that the plain-view doctrine applies, but upon finding the evidence of the second offense, officers should return with that evidence to the magistrate to establish probable cause for issuance of a search warrant to search for further evidence of the second crime.
Searches Incident to Arrest
Officers may search a person and his or her immediate surroundings when making an arrest, without obtaining a search warrant. The courts have interpreted this to mean that officers can go through a person's wallet or purse, address books, and the like. The courts have held that information stored in a pager may be accessed when arresting the person wearing the pager. A number of cases support this ruling, including United States v. Reyes, United States v. Thomas, and United States v. Lynch. Whether this ruling would also apply to personal digital assistants (PDAs) and handheld or laptop computers is not clear.
Yet another exception to the requirement for a search warrant is the border inspection. Routine searches of persons entering or leaving the United States are allowed without probable cause or any indication of criminal activity. This was held to apply in a case where a computer disk was seized and accessed as part of a “routine export search” of a man who was leaving the country (United States v. Roberts).
Seizure of Digital Evidence
There are several different ways digital evidence can be seized when it is located. Early computer crime investigators often printed incriminating files or made digital copies (on floppy disks or other removable media) of the files in question. Another option is to seize all the computer equipment and go through the data stored on it at another location. As we mentioned previously, the best accepted practice today is to first make a complete exact bitstream copy of the hard disk(s) before shutting down the computer. These copies can be used to reconstruct the suspect disk and analyze it at another location later. After making the copies, investigators should seize the equipment and original disk, mark it as evidence, and store it in a secure location.
The search and seizure process should be well planned in advance. Determine the best day and time of day for the process, and estimate the number of officers and technicians and levels of expertise that will be needed on-site when the search and seizure are conducted.
Forfeiture Laws
Computer equipment used as a tool or instrumentality of certain crimes (for example, illegal drug trafficking) can be subject to state and federal asset forfeiture laws. This means that the ownership of the equipment is transferred to the state or the law enforcement agency making the seizure and can be converted to their own use or sold.
Privacy Laws
The U.S. Privacy Protection Act (PPA) covers search and seizure of items that fall under the First Amendment (freedom of speech and freedom of the press) protections. The Privacy Act was intended to protect journalists, publishers, and other such people who might have evidence of criminal activity but are not suspected of having committed any criminal act. This law applies to materials that are created for the purpose of disseminating information to the public (which could apply to writings intended to be posted to Web sites, because this is a form of publishing to a public forum).
If there is reason to suspect that the person who has the materials is committing the crime that the materials pertain to, or if there is a danger to some person of physical injury or death that could be prevented by seizing the evidence, the search and seizure are not a violation of the Privacy Act. Violation of the act is a civil rather than a criminal matter. Violators of the act are subject to civil lawsuit, but a violation does not mean that the evidence will be thrown out of court, as is the case with a violation of constitutional rights.
The Electronic Communications Privacy Act (ECPA) was passed to protect the privacy rights of customers of ISPs when their personal information is disclosed. Penalties for violation include civil damages and, in some cases, criminal charges. The ECPA provisions are laid out in Title 18 of the U.S. Code. However, the passage of the U.S. Patriot Act made changes to some of the provisions of the ECPA, which we discuss in the next section.
Some states have their own privacy statutes that can be applicable in specific cases in addition to the federal Privacy Protection Act. Furthermore, special rules under both federal and state laws govern information held to be confidential or privileged by statute, such as that arising from the physician/patient, attorney/client, or clergy/parishioner relationship. These are called legally privileged documents.
Summary
Evidence is the foundation of every criminal case, including those involving cybercrimes. The collection and preservation of digital evidence differs in many ways from the methods law enforcement officers are used to using for traditional types of evidence. Digital evidence is intangible, a magnetic or electronic representation of information. Its physical form does not readily reveal its nature. In addition, digital evidence is fragile. It is very easy for a criminal to deliberately delete crucial evidence in an instant or for an officer or technician to unintentionally damage or destroy it.
Fortunately, in many cases, evidence that appears to be gone is still on the disk or other media and can be recovered. A number of data recovery software packages are on the market, several of which are designed specifically for computer forensic work and are marketed with law enforcement use in mind. Also, many commercial data recovery services will perform the recovery operation for a fee, using sophisticated equipment that might be beyond the budget of many law enforcement agencies.
Computer forensics is still a relatively new field, but standards have been established and continue to evolve. To ensure that digital evidence is admissible in court, it is best to adhere to accepted current standards and practices and to use software that has been tried and tested. The primary objective in conducting an examination of a suspect computer's data is to leave the original in the same condition in which it was found. This means that, whenever possible, disk-imaging technology should be used to create an exact duplicate of the suspect hard disk, and this duplicate alone should be used for examination. To recover data that might be hidden in obscure areas of the disk or left behind after deletion or erasure, the copy must be a bitstream image, in which every bit is copied, sector by sector, from the original disk to the duplicate. This duplicate ideally should be made on-site when the computer is seized, before the computer is shut down. At the same time, steps should be taken to record or preserve volatile data that will be lost when the computer's power is turned off.
Once one or more duplicates have been made, the original can be locked up securely in an evidence locker or evidence room until needed. Chain of custody must be maintained throughout the entire process. The duplicate disk can be examined for evidence of criminal activity. This examination not only should address those files that are visible in the file system, but also should include a search for ambient data that is not obvious and that the user of the computer might not know still exists on the disk. For this task, you will need special forensic software, which can be installed on a forensic workstation set up for this purpose.
Collection of evidence involves not just technical know-how; it also requires knowledge of the laws pertaining to evidence. Violation of those laws can result in the evidence being thrown out of court, regardless of its technical quality and regardless of how definitively it proves the guilt of the defendant. In the United States, admissibility of evidence often hinges on the Fourth Amendment to the Constitution, which protects citizens against unreasonable search and seizure. If the search and seizure of computer equipment and/or digital data violate the suspect's constitutional rights, the judge will suppress the evidence and the jury will never see it. Other federal laws and state laws govern the admissibility of evidence in criminal trials as well. These laws are generally collected in codifications called rules of evidence, which we'll discuss in greater detail in Chapter 17 and every investigator should be intimately familiar with the laws in his or her jurisdiction.
Frequently Asked Questions
A In many computer-related criminal cases, the evidence speaks a language that most of the members of the jury (and often the judge, prosecutor, and law enforcement officers) don't understand. At one time, juries were likely to accept the testimony of expert witnesses without question, but as the public has become more technically sophisticated and expert testimony has been called into question in high-profile cases such as the O.J. Simpson case, juries have become more skeptical of experts' infallibility and are more likely to accept the opposing attorney's challenges that raise doubts about evidence-processing methods and forensic techniques. This is why it is so important to document the actions of law enforcement officers and technicians every step of the way. Documentation is also important to refresh the memories of people who must testify in the case. Often, trials are delayed for months or even years, and by the time an officer or technician is required to take the stand, he or she has handled many other cases.
Q Why is it important that all the software used by law enforcement officers be licensed and registered? Law enforcement budgets are often tight; why not use freeware as much as possible?
A Some freeware and shareware tools that are available on the Internet are good tools, and the price is certainly right. However, there are some dangers in using these programs for forensic purposes. First, you never know exactly what you're getting when you download a free program (and you certainly can't ask for your money back if it doesn't work properly). Downloads can be infected with viruses or Trojans that can damage the systems on which you use them. Using unlicensed software (illegal copies) is even worse. The opposing attorney(s) will have a field day if they discover that the police used pirated or “borrowed” software in the investigation. This behavior can destroy the credibility of the people who conducted the forensic examination and can even result in losing the case. In addition, with properly purchased and registered software, you will be able to get technical support from the vendor if necessary. Makers of computer forensic software often offer discounts to law enforcement agencies, making it easier to afford the proper tools for the job. After all, officers and agencies probably wouldn't suggest saving money by buying their duty weapons from a pawnshop; that's because these are essential tools of the trade and they must be as reliable as possible. For the cybercrime investigator or technician, the same is true of the forensic software that is used to collect and preserve evidence that can make or break a criminal case.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
