Chapter 2
Up-leveling the Conversation: Security Culture Is a Board-level Concern
Management is efficiency in climbing the ladder of success; leadership determines whether the ladder is leaning against the right wall.
Stephen Covey
Let's be honest—no organization will ever be fully secure. Security is a management process. It's the process of managing all the risks and threats that arise minute by minute, hour by hour, and day by day. You are never done. You can be more secure than you were yesterday, but you never arrive. You're always a zero-day threat, misconfiguration, or employee-related incident away from being less secure than you were just a minute ago.
This is a critical concept for organizational leaders and their boards of directors. So, if you are one of those leaders, or if you have influence over one of those leaders, read on. This chapter will serve as an overview of why security culture and your human-layer defenses deserve attention at the highest levels of your organization. And, while we don't want to be fear mongers or party killers, we will also briefly discuss the cost of ignoring your security culture or taking it for granted. Lastly, we'll point you to some valuable resources that you can begin using right away.
A View from the Top
If there is one good thing that comes from all the media reporting about cyber breaches around the world, it is that virtually every organization now recognizes the need to shore up their cyber defenses. Along with that recognition comes the need to communicate clearly throughout the executive team and board of directors about the organization's risks and cyber readiness. This isn't to say that every member of the board of directors and executive team needs to become an expert in cybersecurity in addition to their current expertise, but they do need to become experts in understanding the risks that cyber-related events might have on the business.
Risk is the key word. Executives manage based on risk, reward, and opportunity. Conversations about security for the sake of security will have limited value. They might be interesting, but they aren't particularly useful. Useful conversations are those that provide context about how cybersecurity concepts and decisions might impact the business, either positively or negatively.
Here's a way of framing conversations we've found works for making virtually any topic understandable and relatable at an executive level. Think of it as a simple filter or formula you can use to improve your executive communication:
Information informs your story/narrative, which is then interpreted clearly and honestly via the metrics and anecdotes you use, leading to insights and future direction. We know that formula might feel obvious; you might have even thought something along the lines of, “Well, duh!” But now be honest with yourself and remember that you (like most people) very likely tend to try to dazzle with details. And that's the problem. Stories might include details, but details are not stories. Context might include details, but details don't provide context on their own. Any time you provide a data point, you need to clearly state what that means and why that matters in the grand scheme of things. This is where most security executives fail.
If you aren't clearly telling your own story and articulating what your data and details imply, then your audience is left to interpret things for themselves. They form an alternate story in their minds, and that's not usually to your benefit.
They make assumptions, and those assumptions might not align with reality. That's why it's so important to have a clear understanding of the information you need to share and the story that it tells. After you understand your information and broader narrative, you can work on underpinning that story with relevant metrics and anecdotes. And then you can point back to your metrics, anecdotes, and story to bring your audience to the ultimate conclusions. This is your chance to celebrate your successes, set future expectations, gain feedback, solicit support, and more.
Telling the Human Side of the Story
When it comes to cybersecurity, there is a story about securing your organization's future by providing long-term resilience and sustainability. And, yeah, there are certainly aspects of that story that are technology-centric, but there are also many, many aspects that are people-centric. When leaders hyper focus on the technology side of the story, they risk forgetting that technology is only part of the equation. And they risk forgetting that humans are at the center of everything.
Much of the cybersecurity narrative revolves around technology. We talk about firewalls being bypassed, data being leaked, or servers being hacked; we show images of cybercriminals in dark rooms surrounded by screens filled with indecipherable computer code. When that's the picture of cybersecurity that our people get, it is very easy for them to feel overwhelmed. Making human-layer vulnerabilities and defenses a frequent and explicit part of your organization's cybersecurity conversations paves the way for more human-centric policies, processes, and technologies.
By consistently referring to the importance of the human layer, you can reinforce the need to engage people. It gives everyone the message that your people share a proactive role helping protect the organization. It opens up more meaningful conversations and helps pave the way to gain buy-in for initiatives that will help foster a stronger security culture.
What's the Cost of Not Getting This Right?
Organizations can't afford to neglect the importance of the human side of cybersecurity. As we mentioned in Chapter 1, organizations have been investing more and more each year trying to combat cybercrime and data breaches, and yet the breaches keep on coming. In fact, as we showed in Figure 1.1, the rise in breaches is outpacing the global spend on cybersecurity “solutions.” Why is that spend not paying off? The reason becomes clear when you look at where the security spend is going.
Figure 2.1 illustrates the problem well. We know that 85 percent of data breaches are being caused by social engineering or human error (Verizon, 2021). But, when you look at organizational spending on security, it becomes clear that leaders have been placing their faith (as reflected by spend) in the wrong areas. Organizations have been focusing on an outdated perimeter-based model of security—one that virtually ignores the human element or hopes that technology-based defenses will suddenly become effective at addressing social engineering and human error in a meaningful way.
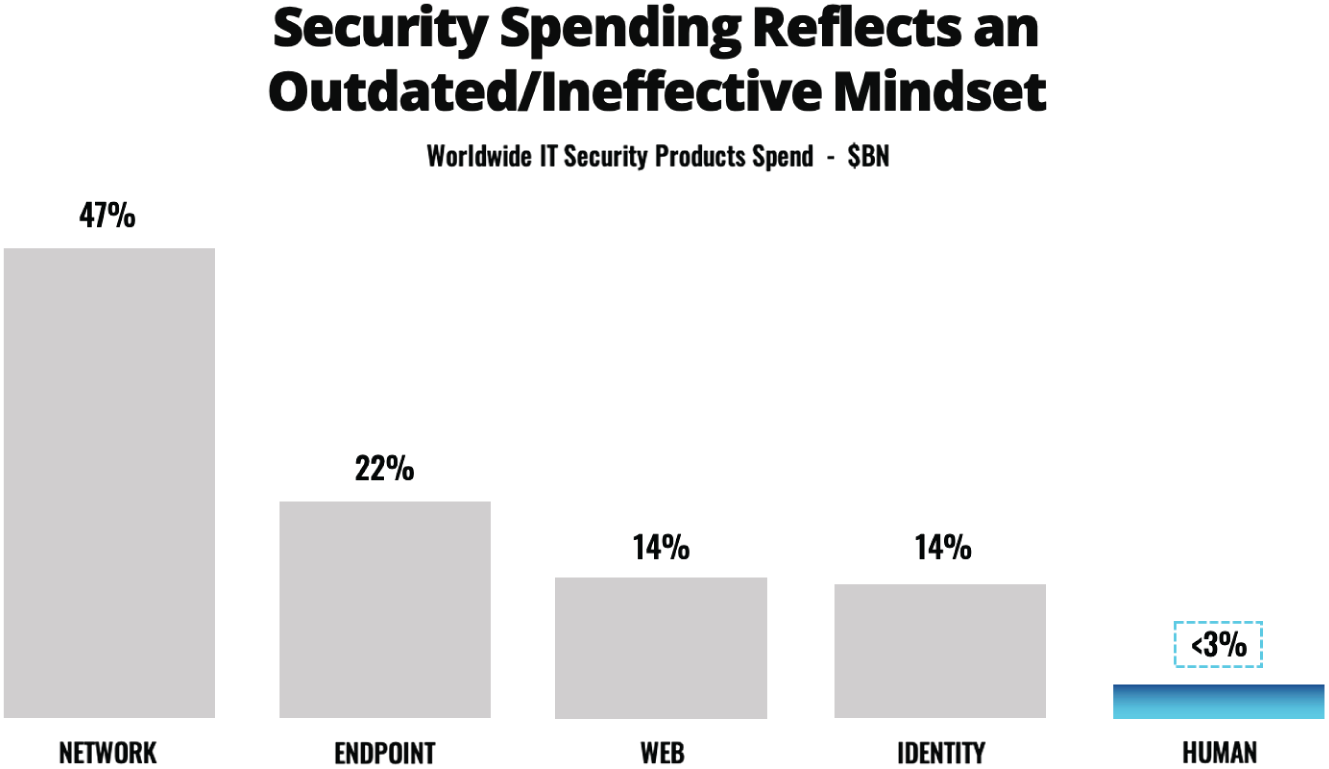
Figure 2.1 Cybersecurity spending has effectively ignored the main cause of data breaches
Let's think about this for a minute. Less than 3 percent of security spending is focused on the human layer, but more than 85 percent of breaches are traced back to humans. That stark contrast between the problem area and where organizations are focusing is shocking.
For decades, security leaders have known that humans are the most enticing and vulnerable attack surface; nonetheless, we, as an industry, have tried everything but doing the actual work needed to improve our situation.
And here we are.
Cybercriminals Are Doubling Down on Their Attacks Against Your Employees
Over the past few years, we've seen a meteoric rise in attacks seeking to bypass technology by targeting humans. And it's working. Ransomware continues to make headlines due to large-scale attacks like those that targeted Colonial Pipeline (Fung, 2021), JBS Foods (Reuters, 2021), and Kaseya (Hill, 2021). The recent global pandemic only added fuel to the fire. All of a sudden, organizations and employees were having to adapt to a new normal: working from home. Organizations scrambled to find ways to allow employees to work remotely and safely.
The added confusion and chaos of a global pandemic, employees facing new routines and dealing with new systems, and people feeling more stressed and less connected than ever have all come together to create an enticing playground for social engineers. And they are taking advantage of it.
Here are a just a few points to help put the problem into perspective (as of 2021):
- Over one-third of organizations globally have been hit by ransomware (International Data Corporation, 2021).
- Of those hit, roughly 87 percent ended up paying the ransom (International Data Corporation, 2021).
- We are now at a point where ransomware isn't just about making your data inaccessible; it's about exfiltrating the data, using it for extortion against multiple parties, and generally doing everything possible to gain leverage and destabilize your organization. You have no choice but to assume that a ransomware incident is a data breach (Sjouwerman, 2021).
- Social engineering via phishing, vishing (voice phishing), smishing (phishing via text message), and social media are all on the rise (Phishlabs, 2021; Martens, 2021).
- The global average cost of a data breach is $4.24 million (IBM, 2021).
- The global average cost of a ransomware attack is $4.62 million (IBM, 2021).
- The average per-record cost of a data breach is $161. That goes up to $180 if the record contains customer personally identifiable information (PII) (IBM, 2021).
All of this rises to the level of materiality. And material risk is one of the most important things that an executive team and board of directors is concerned with. This is why it is so important to make your human layer of defense a central part of your cybersecurity narrative.
Your People and Security Culture Are at the Center of Everything
Your people are the most important element of your cybersecurity program; ignore them at your peril. Technology will only get you so far. So it's time to elevate human-layer defense to the forefront of the conversation. And it's time to deliberately and methodically focus on security culture.
Human knowledge, beliefs, values, behaviors, expectations, and social pressures are involved in everything that matters within your organization:
- Humans decide what technologies to purchase.
- Humans decide what risks to focus on and how to gain visibility into those risks.
- Humans determine the need for new processes.
- Humans review and tweak the settings of business technologies.
- Humans are in charge of running, patching, and maintaining your security technologies.
- Humans design and code the applications you develop in-house.
- Humans review your third-party risk.
- Humans decide how they will respond to something that looks suspicious.
- Humans decide (both consciously and unconsciously) how they will react to the systems and information they interact with each day.
- Everyone you hire, contract, interact with, or sell to is human.
- Everything you design, sell, or develop business from is ultimately in service of humans.
- Everything and everyone in your organization is impacted by the decisions, behaviors, and expectations of other humans.
Your people and your security culture are the heart of your cybersecurity program. In this book, we'll share a number of interesting (and maybe even shocking) insights related to how your security culture will either be a net benefit or a huge liability for your organization. Here's an example.
While evaluating our security culture dataset, Kai's team recently made an interesting discovery. They took a sample of just over 1,100 organizations and nearly 100,000 employees and looked at employee susceptibility to phishing (measured via a simulated phishing test) as it relates to an organization's overall security culture (as measured by our Security Culture Survey) (Eriksen, 2021). There was one obvious correlation, which you are probably already anticipating: Organizations with a “poor” security culture had more employees who opened and interacted with phishing emails in various ways than employees in organizations with a “good” security culture. Yeah, we would expect that. But here's what we didn't expect: Employees of organizations rated as having a “poor” security culture were 52 times more likely to enter credentials as part of a phishing scam than organizations with a “good” security culture.
Let's put that into raw numbers. In organizations with a “good” security culture, one employee out of 1,000 is likely to be tricked into giving away their credentials or entering other sensitive data as part of a phishing scam. But, in organizations with a “poor” security culture, that number jumps to 1 out of 20.
That's just one stat and one way of measuring the benefit of having a good security culture, but it makes the point: Focusing on your security culture is critical to your overall cybersecurity program and critical to the overall risk posture of your organization.
The Implication
Executive teams and boards of directors need to view security culture as a critical priority. While cybersecurity is a top-of-mind issue for many companies, it can be difficult to ensure that the right information is being shared at the top levels of the organization. To an extent, that's understandable; cybersecurity can seem like an abstract concept. It requires technical knowledge and expertise that can be difficult to translate into business-speak. And, when you don't know how to ask about or measure something, it's easy to ignore it altogether.
Traditionally, the board of directors required reporting based on an increasing risk to the business. For example, back in the early 2000s, the threat of computer viruses wasn't on the radar at the board level; it rarely rose higher than senior IT leadership. However, as the impact of data breaches, destruction of complete networks, and direct monetary theft became a reality, corporate boards took notice. They ramped up the reporting requirements, wanting increased visibility into their defenses. They even created new roles, such as CISO, that often had direct reporting to the CEO or even the board.
Ransomware, social engineering, and human error have proven to be an existential threat to businesses of all sizes.
Ransomware, social engineering, and human error have proven to be an existential threat to businesses of all sizes.
Intellectual property theft, multi-step extortion, customer and employee data theft, multimillion dollar ransom payoffs, brand and reputation damage via released emails, and other public shaming are all taking a toll; and boards of directors are looking for visibility into how vulnerable their organization is and what needs to be done to decrease risk and increase resilience.
Organizations must address ransomware as one of the primary overall risks to the business that must be mitigated, similar to natural disasters. The most common (and easiest path) for ransomware infection is through social engineering attacks on an organization's employees. So, social engineering, which is mitigated only by a mature security culture, deserves board-level attention.
Boards of directors need transparency and accuracy (Internet Security Alliance, 2020). To that end, we'll show you how to accurately measure your security culture. Further, we'll give you the information and tools you need to actively begin strengthening the weak areas and fostering sustainability in the areas where your people are already doing well.
Measuring security culture with the tools and methods we'll show you provides the board a very objective measurement for the company's proactive security measures for the company's largest vulnerability: attacks that succeed by exploiting your human layer.
Getting It Right
We know that traditional technology-centric approaches to cybersecurity haven't proven effective, and the traditional information-centric approach to security awareness hasn't adequately prepared employees for the onslaught of social engineering attacks targeting them. If 85 percent of breaches are being caused by social engineering or human error, and less than 3 percent of spending is focused on the human layer, then it is clearly time to put more focus on the human side.
Information-centric security awareness isn't sufficient. We need a broader approach. We need to focus on the ABCs of cybersecurity: awareness, behavior, and culture. In Chapter 3, we'll discuss key reasons why traditional security awareness programs have fallen short and show how you can transform your program, making it truly effective. You'll learn how principles from marketing, behavior science, and organizational culture management can all be used to drive secure behaviors and foster a workforce that values security.
Takeaways
- Human-layer defenses and your organization's security culture should be key conversation topics within the executive team and board of directors.
- If you aren't clearly telling your own story and articulating what your data and details imply, then your audience is left to interpret things for themselves.
- Ransomware, social engineering, and human error have proven to be an existential threat to businesses of all sizes.
- Less than 3 percent of security spending is focused on the human layer, but over 85 percent of breaches are traced back to humans. It's time to invest more time, money, and effort in the human layer.
- Human knowledge, beliefs, values, behaviors, expectations, and social pressures are involved in everything that matters within your organization.
