Chapter 3
The Foundations of Transformation
Nothing happens until the pain of remaining the same outweighs the pain of change.
Arthur Burt
We've discussed why security culture is becoming a hot topic and why it is so important that it deserves board-level attention. But what about awareness? And what about all the other things generally associated with awareness, like simulated phishing tests? Where do they fit in?
Those are great questions.
The answer is both simple and complex. Those things are important to culture, but they are not culture. They are pieces of the puzzle, but they are not the entire puzzle. They are both artifacts of culture, and instruments that can be used to influence culture. Culture exists anywhere there are people. And a security culture exists anywhere there are people. You have a security culture even if you aren't focusing on it. The question comes down to whether your security culture is one that reflects the knowledge, values, norms, and behaviors you want—and what you need to do about it.
Back in 2019, I (Perry) wrote a book titled, Transformational Security Awareness: What Neuroscientists, Storytellers, and Marketers Can Teach Us About Driving Secure Behaviors (Wiley). The book was rattling around in my head for 10 years or so. It was the book I hoped to find when I started out as an awareness practitioner. Since its publication, Transformational Security Awareness has gone on to become a standard reference within the security awareness community and was even inducted into the Cybersecurity Canon Hall of Fame (Institute for Cybersecurity & Digital Trust, 2022).
Since its publishing, Transformational Security Awareness has gone on to become a standard reference within the security awareness community and was even inducted into the Cybersecurity Canon Hall of Fame.
If you are looking for a book that really gets into the nuts and bolts of running a security awareness campaign, choosing content, developing behavioral interventions, and having a culture mindset, then you'll want to add that book to your reading list.
This book—the book you are reading right now—narrows in on the topic of security culture. It's about tackling the topic of security culture with laser focus and in much more depth than currently available in other books. But, because any serious discussion of security culture cannot exist within a vacuum, I believe there are a few foundational concepts I need to bring forward from Transformational Security Awareness. I'll also use this chapter as an opportunity to extend a few of these concepts and help set the stage for areas that we'll cover later in the book.
The Core Thesis
The ideas in Transformational Security Awareness revolve around a central thesis: that we cannot afford to ignore the human side of the cybersecurity equation; that technology alone will never be enough to create secure scenarios; and that everything we do or create needs to account for human nature.
“Security awareness” has gotten a bad rap not because it is ineffective but because many organizations running security awareness programs mistakenly believed that simply telling employees what's expected of them or simply alerting employees to threats will lead to a more secure environment.
Let's face it, giving people information doesn't guarantee that they will do any of the following:
- Understand the information
- Remember the information
- Ascribe value to the information
- Apply the information
- Act on the information
Giving people information is just that. We've transferred the information but have little control over what happens to the information after that. This understanding is encapsulated in what I refer to as the knowledge-intention-behavior gap.
The Knowledge-Intention-Behavior Gap
Here's a fundamental truth: We all struggle with behaviors. Sometimes our bodies run on autopilot, not consulting the logical/reasoning part of our minds. That can sometimes help us (like when we instinctively swerve our car to avoid an accident), and at other times, that type of automatic behavior can hurt us. Here's an example that I gave in Transformational Security Awareness:
Think about times when an object—let's say a pen—has started to roll off your desk, and your arm seemed to quickly reach over and try to catch the pen before it falls to the floor, maybe even knocking over your coffee mug along the way and causing a bigger mess than if you did nothing. What happened? Many times, you didn't consciously decide to try to catch the pen. Your mind quickly processed the situation and made the decision to intervene without consulting your logical self.
Transformational Security Awareness: What Neuroscientists, Storytellers, and Marketers Can Teach Us About Driving Secure Behaviors, by Perry Carpenter
In such situations, we are dealing with what I call the knowledge-intention-behavior gap. This gap exists because there are so many things that compete for our attention at the point of behavior. We have a whole set of prewritten shortcuts that our minds like to take, and we often make quick, in-the-moment trade-offs that prioritize our short-term comfort over our long-term good. All of this means that we often act in ways that work completely against any knowledge and/or intentions we have.
If you don't believe that's true, just think about the last time you tried to keep a set of New Year's resolutions. You had things that you knew were important, and you fully intended to act differently based on that knowledge. Alas, it's extremely likely that the behavior didn't follow. That very relatable situation is what it is to be human. That is the knowledge-intention-behavior gap in action.
When it comes to the human side of security, we must treat the knowledge-intention-behavior gap as a fundamental law of reality. We need to stop expecting to make people more secure by simply exposing them to more information. Yes, information still has a place, but information isn't our end goal. The ultimate end goal is to influence value systems and behaviors.
Three Realities of Security Awareness
Out of the knowledge-intention-behavior gap flow three realities of security awareness:
- Just because I'm aware doesn't mean that I care.
- If you try to work against human nature, you will fail.
- What your employees do is much more important than what they know.
It can be tempting to simply read these three statements and move on. That would be a mistake. I believe that virtually every security program failing related to the human side of things comes back to one or more of these statements. If your program sends out a lot of great information but your people don't change their behavior, it's because you haven't given them a reason to care. The information was quickly forgotten, or the action/behavior that the information was intended to encourage wasn't designed for it. If your people aren't following your security policies or using the proper tools or procedures to perform certain actions, then it is likely that your policies, processes, or tools are somehow conflicting with human nature. And, I'll say this as clearly as possible: No amount of knowledge has ever prevented a data breach; it is only what someone does at the point of decision (with or without specific knowledge) that will prevent a breach or allow a breach to happen.
No amount of knowledge has ever prevented a data breach; it is only what someone does at the point of decision (with or without specific knowledge) that will prevent a breach or allow a breach to happen.
Program Focus
The implications of these three realities of security awareness point toward the need to focus on behavioral and cultural patterns rather than being satisfied with information-based training. Figure 3.1 first appeared in Transformational Security Awareness. It depicts four types of program focus and the benefit associated with each.
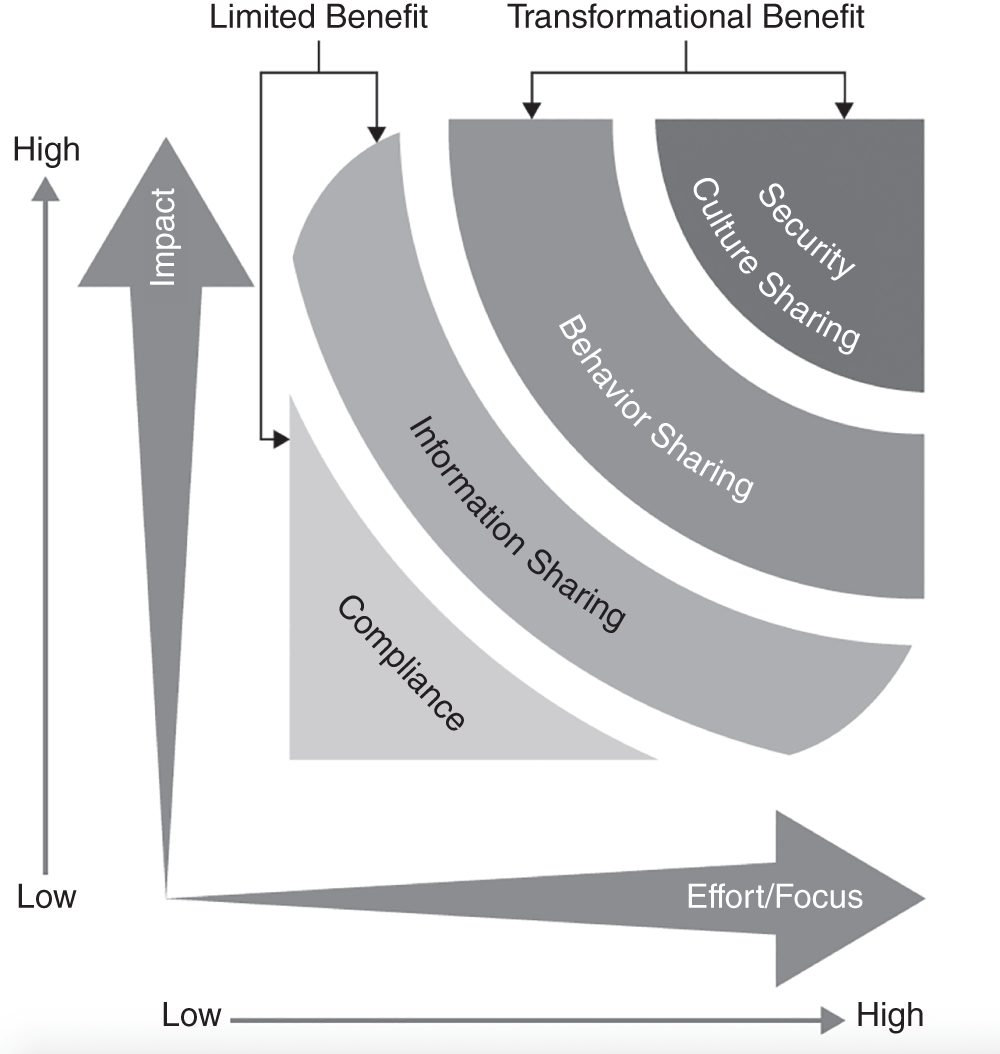
Figure 3.1 Your program's focus will either produce limited benefit or be transformational for your organization.
As you can see, the first type is compliance; that's a “check-the-box” approach that produces very little benefit for an organization other than satisfying a regulatory mandate. The next focus type is information sharing. This is generally done by well-meaning organizations that believe that sharing information will provide a meaningful result; however, that type of focus will also produce only limited benefit.
The next two program focus types are behavior shaping and security culture shaping. Each of these require more intentional focus and energy but have the potential of providing a truly transformational benefit to the organization. As you move across the program focus types shown, it's important to note that each of the program types to the right will naturally include all the benefits of the previous types. For instance, information-sharing programs include all the elements required for compliance but also focus on broadening communication. Behavior-shaping programs have done what needs to be done to achieve compliance: add robust communication elements where those can be beneficial, and focus on using behavior design techniques to address human risk. And a security culture shaping focus encompasses all those elements and leverage techniques to measure and influence the knowledge, beliefs, values, behaviors, and social norms of the employees within an organization.
Extending the Discussion
Okay, now that you have digested the core thesis of Transformational Security Awareness, we are ready to spend the rest of this book narrowing in on what a program designed to influence security culture is all about. Before we turn to the Chapter 4, “Just What is Security Culture, Anyway?”, however, I first want to introduce an evolution of what was presented in Figure 3.1.
Over the past several months, Kai, myself, and the KnowBe4 Research team have been working on an evidence-backed, data-driven model for accurately measuring the maturity of an organization's security culture. We'll cover this in greater detail in Chapter 12, but it makes sense to introduce you to the model now so that you can see how the material in the forthcoming chapters fits in.
Introducing the Security Culture Maturity Model
As with many maturity models, the Security Culture Maturity Model (SCMM) is loosely based on a Capability Maturity Model (CMM) framework (CMMI Institute Resource Center, 2019). Our model is unique in that it is highly data-driven, based on the insights gathered from over 40,000 global organizations (and growing). As with the CMM, the SCMM has multiple levels, ranging from a level representing very low maturity and progressing up to the pinnacle of achievement. Figure 3.2 depicts the basic structure that most maturity models follow.
Figure 3.2 Example visualization of a standard/generic maturity model
Figure 3.3 represents another way such models are often represented.

Figure 3.3 Another common maturity model visualization
Each of these representations are good at communicating the building blocks of maturity. They are good at showing the high-level concept, but they lack some of the specific granularity that is useful for business and security leaders. As such, for the purpose of representing maturity within the context of security culture, we created the model represented in Figure 3.4.
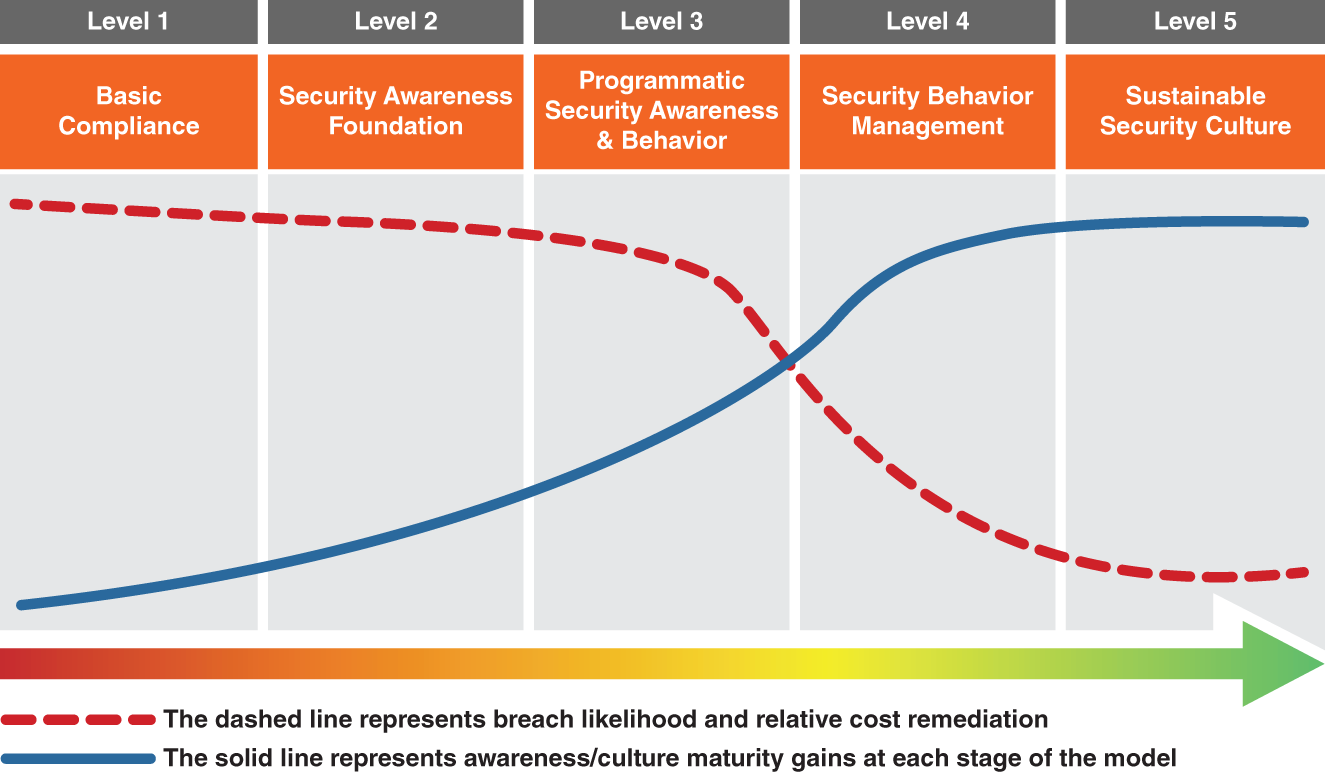
Figure 3.4 The Security Culture Maturity Model
The Security Culture Maturity Model in Brief
The SCMM is an evidence-driven framework for understanding and benchmarking the current security-related maturity of an organization, industry vertical, region, or any measurable group. It comprises five levels. The model's range accounts for organizations with no formal or intentional awareness, behavior, or culture plan other than to achieve basic compliance (level 1), all the way up to the most sophisticated organizations that seek to push beyond the pack and are actively working to shape even the unwritten rules and social dynamics of how their employees value security.
An organization's level of maturity within the SCMM is determined by analyzing all available information regarding an organization's security culture. We call each data point a Culture Maturity Indicator (CMI). We'll take a deeper look at CMIs a bit later in the Chapters 4 and Chapters 12. It is important to note that, although much of this analysis can be done automatically using the tools and datasets that Kai and I are developing at KnowBe4 Research, the value of this model is not restricted to KnowBe4 customers. Our intent was to create a model that is vendor agnostic, so we'll be providing suggestions and methods for calculating maturity that can be adopted by non-KnowBe4 customers. We'll make these resources available on the companion website for this book: https://SecurityCultureBook.com.
The S-Curves
One aspect of the SCMM that immediately stands out are the two distinctive S-curves, each of which tells a story. The solid blue S-curve represents the specific awareness, behavior, and culture benefits an organization will achieve at each stage. Notice the inflection points and crossover point for each of the S-curves. The inflection points and crossover point each represent the real behavioral gains that an organization can expect as it begins to focus on shaping employee behavior through a combination of training, frequent simulations, and reinforcement tactics.
Also notice the relationship between the two curves. As security awareness, behavior, and culture increase, the likelihood of human-related breach and cost of remediation (the dotted red S-curve) decrease. Again, there is a sharp inflection point as organizations move beyond knowledge-based awareness and begin intentionally focusing on behavior and the social aspects of how employees value security.
Lastly, there is an additional point reflected in the placement of the curves. There is a gap between the top of the blue line and the top right of the chart, and there is an even more noticeable gap between the very end point of the dotted red line and the bottom point of the final level. These represent a simple truth: No organization will fully “arrive,” and no organization will ever fully be beyond the possibility of experiencing a human-related breach. That's the nature of any security measure, technology-based or human-based. No security layer (technical or human) can make an organization 100 percent secure, but each additional layer of security you add provides additional resilience.
To keep from getting too far in the weeds right now, we'll save the detailed discussion of the maturity levels, CMIs, and the application of data to the model for Chapter 12. For now, you can probably see the parallels between this data-driven model (Figure 3.4) and the conceptual model from Transformational Security Awareness (Figure 3.1).
The Value of the Security Culture Maturity Model
The SCMM has some interesting properties in that it can communicate at multiple levels. For instance, there is value in being able to quickly communicate what level an organization or vertical is in. There is also value in comparison, where organizations can benchmark themselves against their industry, organizations of comparable size, region, etc.
As you'll see in Chapter 12, the SCMM can be used to communicate at a glance or in extreme detail backed up by rich data. Organizational leaders can visualize their journey and plan the steps required to progress from one level to another. The names of each level are guideposts pointing toward the types of activities that will help the organization progress.
You Are Always Either Building Strength or Allowing Atrophy
Your security awareness, behavior, and culture journey is all about building strength, motor memory, and a sustainable ecosystem. The physical equivalent to this is going to the gym. You don't get in shape by only exercising once. And, if you only exercise once per year, or even once per quarter, you aren't going to see results. The way to create long-term change is to make exercise a part of your lifestyle. This is what traditional security awareness programs get wrong and what organizations that have a check-the-box approach to training get wrong. They implement programs that are the equivalent of going to the gym only once per year.
Lasting change requires lasting commitment. If you stop, you don't stand still—you lose ground.
Lasting change requires lasting commitment. If you stop, you don't stand still—you lose ground.
In the same way that if you stop exercising, your muscles begin to atrophy, your people's awareness, security-related behavior patterns, and security culture maturity will regress if you stop putting in the effort. That's the physics of the situation; as with all things, the law of entropy holds.
Takeaways
- The components of your security awareness program are both artifacts of your security culture and instruments that can be used to influence your culture.
- When it comes to the human side of security, we must treat the knowledge-intention-behavior gap as a fundamental law of reality.
- There are three realities of security awareness. 1) Just because I'm aware doesn't mean that I care. 2) If you try to work against human nature, you will fail. 3) What your employees do is more important than what they know.
- Your approach to security culture must be comprehensive and human-centric.
- Security culture can be measured, influenced, and improved.
- We developed the Security Culture Maturity Model (SCMM) as an evidence-driven framework for understanding and benchmarking the current security-related maturity of an organization, industry vertical, region, or any measurable group.
- At all times you are either building strength or allowing atrophy.
