11
Critical Challenges of Designing Software Architecture for Internet of Things (IoT) Software System
NOOR REHMAN1,*, ABDUL WAHID KHAN1
1 Department of Computer Science, University of Science and Technology, Bannu, Pakistan
Email: [email protected], [email protected]
Abstract
Software architecture plays a pivotal role in the utilization of every software system according to user satisfaction. In the initial stage of development, the software architecture design for the internet of things (IoT) is considered essential. Software architecture is also considered the backbone of any software and is the cause of the entire system failing if it is not designed properly. The IoT is a new paradigm in the field of artificial intelligence and the digital world, which is considered the most significant approach for an automated system. In this chapter, we have identified various challenges faced by the software architecture team/vendor for IoT software design. These challenges were analyzed across different continents to determine their significance. The list of the identified different challenges include lack of common development, lack of poor architecting, lack of reliability, lack of management issues, environment issues, development limitation, cost issues, lack of knowledge for highly skilled resource pool, lack of proper technology, traditional co-located model, lack of privacy, lack of communication workflow, lack of trust, market expansion and growth issues, framework integration issues, lack of effectiveness, lack of assessment issues, and poor scheduling. The findings of this chapter demonstrate the similarities and dissimilarities across different continents.
Keywords: Software architecture, internet of things, software outsourcing, challenges/risks, architectural models
11.1 Introduction
Today’s world is a digital world where everything moves with rapid speed, including computations and submissions. Everything needs to be digitized in today’s world, and the internet of things is the latest concept in this regard. Designing such a system from the perspective of a desired angle can fulfill the basic and desired needs of a user [1], which can lead to user satisfaction and ease of work. Software architecture is considered the base of every system. It provides the blueprint of a system regarding its use and its actual operation by the intended user [2]. Software architecture plays a significant role in the development and formulation of a software system for the IoT. In current research technology, the IoT is considered the most prominent technology, which is based on connecting physical objects or things to the digital world’s objects in order to change future objects [3]. Software architecture is a basic part of the system that can express the good scalability and bad scalability of the system. As the technology of the IoT has commercial possibilities, a considerable amount of R&D goes into the technology embedded into devices, along with the endless progression of the number of smart things [4]. However, the issues arise when IoT applications have poor scalability and high coupling, which results in the breakdown of the IoT application [5].
Software architecture is the process of gaining suitable origins and recommendations for the specific software systems that are going to be developed before their actual commencement. Software systems that are affected are likely to be smaller and are associated with the design decisions and the anticipated quality attributes demonstrated in the intended software architecture [6]. This chapter aims to provide an outline of the principles related to software architecture reliability and delivers insights on how the structuring of a software system at the architectural level is important for the development of software systems. With this in mind, our intention is to show how reliability should be considered at the architectural level when developing software systems. Existing architectural approaches do not explicitly consider the dependability aspects, hence the need to know what are the general principles associated with software architectures, what is being developed in terms of dependable technologies, and what are the challenges that lie ahead [7]. The IoT has become an efficient paradigm to overcome all problems faced with manual systems [8]. Recently, there has been a growing trend of using machine learning to expand IoT applications and deliver IoT services such as traffic engineering, security, network management, quality service optimization, and internet traffic classification. As the reputation and widespread use of the IoT continues to grow, devices and sensors are generating considerable amounts of data and many IoT applications are being developed according to their efficient architecture for delivering more precise fine-tuned services to users. Most IoT systems are increasingly vibrant, complex and heterogeneous. Thus, the management of such IoT systems is difficult for the vendor, which may cause the failure of the actual system in the near future [8, 9].
We have achieved many IoT architecture framework issues through the literature with the help of a systematic literature review (SLR). One of the key issues that came up were structuring issues, such as software complexity, requirement, diagram formalization, and module design, for which we have proposed the term “lack of common development”; and the rest were elaborated based on the high frequency of occurrence [10, 11]. To redress the findings with the help of SLR, we formulated the following two research questions:
- RQ1: What are the challenges faced by the software outsourcing vendor organization when designing software architecture for IoT software systems?
- RQ2: How do the identified challenges vary from continent to continent?
We have planned the sections of this chapter as follows: in Section 11.2 we present some background on the topic; in Sections 11.3 and 11.4 we discuss the comprehensive research methodology; in Section 11.5 results of the SLR are analyzed and discussed; in Section 11.5 the challenges of this research are mentioned; in Sections 11.6 and 11.7 we give our conclusions and future direction of this research work.
11.2 Background
Architecture has already developed its own significance for every developer and user who interacts with it. The software architecture design challenges model for IoT software systems has its own significance, which will cover the limitations and issues in the existing architecture models [12]. Software architecture is a supportable part of every software and is an efficient component for the development process of object-oriented software applications [13].
The quality of any system is evaluated according to the architecture model to which it has been developed. Thus, it is of paramount importance to the initial development of any IoT or general software system. The IoT uses everyday devices/objects to gather and share data over networks, with or without human interaction, which is eventually used to create useful information for the specific goal of business [14].
Despite this, the initial stage of developing any kind of system is more important due to its proper architecting. With the help of efficient outsourcing, the developed system could be used freely because it will give results efficiently due to its proper development. Thus, the vendor should consider this stage as the most critical during the development of any software system for a specific job/task, etc. There are many factors that can negatively affect the development of any software with the help of outsourcing, which is nowadays used as a common approach for the development of any software system. Twelve Vietnamese participants in a study identified credibility, cultural understanding, capabilities, and personal visits as significant factors in gaining the trust of a client early on, while communication strategies, cultural understanding, contract conformance, and timely delivery were strong factors in maintaining that trust [15, 16].
Throughout the literature, it was found that the 89% failure of any software system is caused by its improper development, which means its architecting. The disturbance in architecture is mainly caused by the low and unusual communication between two parties, who are the vendor and client. Thus, outsourcing in this stage has been highly preferred due to its efficient role in the successful completion of any project [17]. It has also been observed that in the development of any software architecture, the main factor of the prosperous completion of the project is outsourcing contract management. However, due to the increasing scope and efficiency of outsourcing, it faces a poor understanding of the coordination between client and vendor, which may result in the failure of any system after its utilization [18]. We conducted a systematic literature review and received many challenges faced by software organizations during the development phase of any software. To carry out a systematic literature review means to evaluate or interpret all available evidences for a specific goal or issue. Some of the latest software architecture modeling approaches from the existing literature are illustrated below.
11.2.1 Layered Architecture Pattern
This pattern of architecture is the most commonly used pattern for the development of architecture for a software system. The model view controller (MVC) is also the structure of the layered architecture pattern. Drupal, Java EE, and Express are some examples of models of layered architecture styles or patterns. In this pattern of software architecture style, there are four layers that are led by this architectural pattern. The presentation layer contains the graphical representation and the general design of the system. Whereas, the business layer is concerned with the inclusion of models and logic for the explicit problem of a business. The application layer or database layer is processed between the presentation and business layer for the purpose of providing abstraction. Whereas, the persistence layer processes the code to access the database layer, while it also manipulates database queries and statements of the database, etc. [19]. Figure 11.1 represents the layered pattern of architecture design.
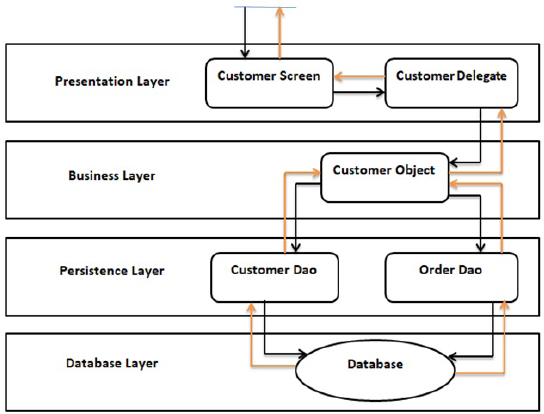
Figure 11.1: Layered architecture.
The majority of developers are more acquainted with the layered pattern of architecture than the others. This pattern also provides easy ways for writing organized and well-defined testable software applications [19]. There are also some drawbacks of this architecture pattern. This pattern of architecture leads to monolithic applications that are hard to split up.
11.2.2 Microservices Software Architecture
This architectural style or pattern is considered as an assemblage of services that are loosely coupled, independently deployable, highly maintainable, and testable, organized around business capabilities, and owned by a small team. Microservices is an architectural pattern that is used to develop services-based applications based on small, loosely coupled services. In this software architecture pattern, microservices have their own divergence responsibilities and a team can develop them autonomously like other microservices [20]. Figure 11.2 represents the graphical overview of microservices architectural style.

Figure 11.2: Graphical representation of microservices architecture pattern.
This layer gives accessibility to the developer for naming and arranging microservices unconnectedly. Microservices architecture is easy to scale because of the less dependent and loosely coupled services modules. There are some drawbacks of this architectural pattern. A user’s action can pass through various microservices, which is why there are more chances of failure when something is done incorrectly in the process.
11.2.3 Event-Driven Software Architecture Pattern
Event-driven architecture pattern is one of the software paradigms used for promoting the detection, production reaction to events, and consumption of events. This architectural model acts like a robotic system and activates when some events occur. An IoT software system is mainly developed using this software architecture pattern due to its artificial intelligence [21]. This software architectural model is also used for developing of those systems which directly interact with humans for the accomplishment of some specific task, etc. Figure 11.3 shows the graphical representation of an event-driven software architecture pattern.

Figure 11.3: Event-driven architecture pattern.
An event-driven architecture pattern works by receiving events from the collector and gives a response accordingly. More than one event is also queued in the event queued box as shown in Figure 11.3.
11.2.4 Blackboard Software Architecture Pattern
A blackboard architecture pattern also deals with the concept of artificial intelligence. This architectural pattern is also considered as a useful pattern for the development of IoT software systems. It has components of a blackboard which act as a central repository of data [22]. This architectural pattern is often useful for those problems which have no deterministic solutions or strategies. Figure 11.4 shows a graphical representation of blackboard software architecture.

Figure 11.4: Graphical representation of blackboard software architecture.
The independent components are communicated exclusively through a common global data repository, or it may be a blackboard. A heuristic problem in artificial intelligence (AI) is the basic core example of the blackboard software architecture pattern.
11.2.5 Systematic Literature Review for SADM
For the process of protocol development, especially for the software architecture designing challenges model (SADCM) for the IoT software system, we studied and analyzed many survey-based approaches in the process of collecting data for analysis. We found that the literature review (SLR) was the most specific approach for data collection, identification, and solution of research questions. Stapić et al. [23] stated that the three phases of SLR are planning, conducting, and reporting. The main focus of this study will be the planning phase. This assessment will help settle quality-related issues and challenges in the field of software architecture outsourcing. The review is totally based on the research questions [24]. After the finalization of our research questions, we will initiate the trial search on different databases and will define a type of strings. After searching the relevant information, we will also specify the inclusion-exclusion measurement for the literature and for the data extracted.
11.3 Research Questions
The main objectives of using a systematic literature review are given in the following research questions:
- RQ1: What are the challenges faced by software outsourcing vendor organization for software architecture designing challenges model for IoT software systems?
- RQ2: What are the practices to handle the identified challenges by software outsourcing vendor organization for designing software architecture for IoT software systems?
- RQ3: What are the real-world practices to handle the challenges by software outsourcing vendor organization for designing software architecture for IoT software systems?
11.4 Research Methodology
For the identification and processing of every object, this is just a unique way through which the said jobs or objects have been processed and completed. Thus, we have found the systematic literature review (SLR) to be the most proficient method for getting the latest results from already published articles whether our research questions fulfill the required amount of data or not for the subject matter [25]. The SLR analyzed the collected data using predefined inclusion and exclusion criteria. There are three phases of SLR: the planning phase, conducting phase, and reporting phase. The results of SLR are considered to be more accurate and reliable with less bias than a manual literature review. Our predefined research proposal [26] has already been validated and published in the International Conference at University of Swabi Journal (USJ), Pakistan, which is available online at the link: (http://www.uoswabi.edu.pk/cms/index/421). The said conference was held under the supervision of international professors and participants.
As mentioned in Subsection 11.4.6, we have found 20 challenges, as highlighted in Table 11.8, where the “lack of common development” and “lack of poor architecture” were marked as the most critical challenges/issues with frequency >= 50%. The same approach has also been utilized in previous articles by many researchers [27, 29, 30].
11.4.1 Constructing Search Term Formulation
The following three basic formulation phases of a search show the details of each question separately. Population, Intervention, and Outcome (PIO) [31] is a particular context-based framework used mostly by researchers to integrate and formulate research questions and to assist the literature review.
| Population | Client, Vendor, Outsourcing |
| Intervention | Challenges, Barriers, Issues, Limitations |
| Relevance outcomes | Software Architecture Designing Challenges Model for IoT software system |
| Exp Approach | Case, empirical studies, SLR, etc. |
Tables 11.2, 11.3 and 11.4 express the search term construction for each question respectively.
11.4.1.1 Characteristics for Research Term Identification
- a) For information gathering, we used research questions for data collection.
- b) We used an alternative term for each string for valid data.
Table 11.2: RQ1 search terms construction.
| Population | Vendor organization for software outsourcing |
| Intervention | What are challenges faced by... vendor |
| Outcomes | Architecture Design... |
Table 11.3: RQ2 search terms construction.
| Population | Software outsourcing... Vendor organization |
| Intervention | What are practices/ways...challenges |
| Outcomes | Solution and things to be avoided when designing software architecture for IoT software |
Table 11.4: RQ3 search terms construction
| Population | Defined in the literature... by vendor organization |
| Intervention | Real-world practices, to handle... challenges |
| Outcomes | To be avoided for software architecture design |
- c) We verified the search strings and their alternatives.
- d) Boolean operators were used for concatenation purposes, where
ORoperators were used for the purposes of providing alternative synonyms and terms for getting meaningful data from the database. The other Boolean operatorANDis also used for providing concatenation and plays the role of conjunction for the combination of two or more adjacent strings.
Results for a:
- RQ1: Software architecture, challenges, hindrance to vendor.
- RQ2: Software architecture designing challenges model practices, and justification of challenges.
- RQ3: IoT Architecture model, real-world practices, handles, challenges, issues, and proposed solutions.
Results for b:
- RQ1:
- – Software architecture: (“Software Architecture”
OR“Software Construction”) - – Software outsourcing: (“Software outsourcing vendor”
OR“Software subcontracting seller”) - – Challenges: (“Challenges”
OR“Issues”OR“limitations”). - – Hindrance to vendor: (“hindrance to the vendor”
OR“difficulties to developers”OR“Constraint to the service provider”OR“restriction to the seller”) - – IoT: (“Internet of things”)
- – Software architecture: (“Software Architecture”
- RQ2:
- – Software architecture design: (“software manner planning”
OR“software scheme development”) - – Practices: (Solution
OR“Solving ways”OR“planned lesion”) - – Justification of challenges: (Exploration of challenges
OR“identification of issues”OR“elaboration of limitations”) - – IoT: (“internet of things”)
- – Software architecture design: (“software manner planning”
- RQ3:
- – Architecture model: (Scheme layout
OR“Pattern layout”OR“design draft”) - – Real-world practices: (“actual universe solution”
OR“Tangible domain rehearses”) - – Software architecture design: (“software manner planning”
OR“software scheme development”) - – Software outsourcing: (“Software outsourcing vendor”
OR“Software subcontracting seller”) - – IoT: (“internet of things”)
- – Architecture model: (Scheme layout
Results for c:
- Software architecture design, constraints, limitations, vendor views, client views, real-world practices, handling critical issues, software architecture designing challenges model for IoT software system.
Results for d:
- RQ1:
((“Software Architecture”
OR“Software Construction”OR“Software structure”)AND(“Software outsourcing”OR“Software deployment”)AND(“Challenges”OR“Issues”OR“limitations”)AND(“Internet of things”)AND(“architecture design”OR“pattern layout”)). - RQ2:
((practice
ORsolutionORexercisesORways)AND(“software architecture”OR“software construction”OR“software structure”)AND(“software planning”OR“software designing”)AND(SolutionsORexercisesORmethods)AND(“Exploration of challenges”OR“identification of issues”OR“elaboration of limitations”)AND(“internet of things”)).
11.4.1.2 Search Process and Practice
The planning for the SLR was conducted as:
- Definition of search terms in the process of identifying population, intervention, and outcomes.
- Identification of substitute spellings and synonyms.
- Validated key words of search terms in pertinent deducted literature.
- Use Boolean operators (AND, OR) for the guidance of search engines (if applicable) for precise search.
A trial search was performed for the identification for getting the relevant literature from different digital libraries. The following trial search was performed in different digital libraries, i.e., IEEE Xplore, ACM, SpringerLink and Google Scholar.
((“Software architecture”
OR“Software Structure”OR“Software Construction”)AND(“Software outsourcing”OR“Software deployment”OR“Software utilization”)AND(“Internet of things”ORIoT)AND(challengesORlimitationORissues)AND(SolutionORmethodsORpracticesORways)).
The search string used for the final search was:
Results from IEEE & Google Scholar: ((“Software outsourcing”
OR“Software deployment”OR“Software utilization”)AND(“Software architecture”OR“Software construction”OR“Software structure”)AND(“internet of things”ORIoT)AND(vendorORdeveloper)AND(challengesORissuesORlimitationsORbarriers)AND(SolutionORRecommendation)).
By applying the final search string, we found the following list of research articles in the different digital libraries shown in Table 11.5.
Table 11.5: Final search results.
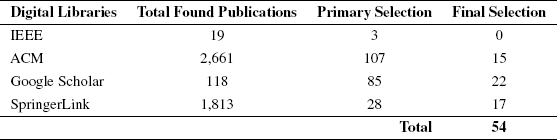
We got low data in the final selection, thus we decided to perform the snowballing technique for the final selection chapter in order to enhance the quality of our research. Adi Bhat [32] stated in his article that snowballing is a referral chain sampling which is defined as a nonprobability sampling technique in which the samples have qualities that are rare to find. This is a sampling procedure in which the existing subjects provide referrals to convert the samples required for a specific research study. After applying successful snowballing, we received the results shown in Table 11.6.
Table 11.6: Snowballing technique results.

The snowballing technique enhanced our results from 55 chapters to 110 chapters, so it has been considered valid for further review to be adopted.
11.4.1.3 Publication Selection and Quality Assessment
The quality of each publication will be determined by its analysis and assessment. The criteria for publication selection will purely be based on the following conditions:
- The authors of publications must recognize the limitations and challenges in software architecture outsourcing.
- Which practices will be conducted and which will be assumed for resolving the challenges faced by the vendor in designing a software architecture model.
11.4.2 Publication Selection Process
In this section of our research, the task to be carried out is of inclusion and exclusion of raw and useful data from the collected materials/data. We will include only those data of research publications which are relevant to our research questions aim of vendor outsourcing for the software architecture designing challenges model for IoT software development.
11.4.2.1 Inclusion Measures
In the data analysis part of the process, we will include only those data considered relevant to our research question. The string of that paper should be related to the research question being searched for. For this purpose, we will use a data extraction strategy.
The inclusion measures would be actionable in the following format:
- Those data would be the part of this study from the found material which is related to our research questions.
- The data that contain challenges and limitations as well as design concepts will be part of this study.
- To consider all those papers which are on software architecture and the internet of things.
- To include all those papers which have the challenges of software architecture and IoT.
11.4.2.2 Exclusion Measures
This part on the measure of data deals with the exclusion of material not related to our research, study or research string. The process of exclusion will likewise occur as follows:
- We will exclude those publications that are found to be duplicates or fakes.
- Those data that are not related to our research study software architecture designing challenges model for IoT software systems and current challenges in software architecture designing challenges model.
- Those data in which there is no citation of client, vendor and outsourcing.
- Papers that are short or not in English mode.
11.4.2.3 Selecting Previewer
At this stage, the preselecting viewer is done by checking the all the material received from the different databases: the title, author, paper type, date of publication, journal, authenticity, abstract and introduction of each research/article paper. Through secondary reviewers, the raw data has been excluded and in the primary study relevant data has been finalized for inclusion in the research study.
11.4.3 Quality Assessment of the Publication
The quality of each publication will be determined by quality analysis and assessment. The criteria for publication selection would purely be based on the following conditions:
- The authors of those publications must identify the challenges and limitations in software architecture outsourcing.
- Which practices will be handled and would be carried on for resolving the challenges faced by the vendor in the software architecture model design?
11.4.4 Data Extraction
11.4.4.1 Initialization of Data Extraction Phase
This phase of extraction of genuine data will be started after receiving data through the primary study on behalf of research question satisfaction. The format of data extraction during the extraction phase will be done under the following categorized conditions:
- We will check the full details of the extracted publication, e.g., its author’s name, publication journal, year, title, keywords; and we will also check whether it is a journal, paper or conference paper, conference location, pages, etc.
- Data that are satisfying and cover RQ1, which is comprised of challenges in software architecture faced by vendors and client-side organizations.
- Data that satisfy RQ2 dealing with practices to be handled in software outsourcing contract for software architecture design.
- Data which express the real-world solution to handle challenges faced by vendor and client-side organizations.
11.4.5 Data Extraction Demonstration
The data which are preserved through primary and secondary studies on the allotted string are expressed in the format shown in Table 11.7.
Table 11.7: Data demo table.

11.4.5.1 Data Extraction Process
The job of data extraction is the responsibility of the primary reviewer. He/she will collect meaningful data from the existing literature. If the individual has problems or issues with the primary data, the secondary reviewer could help by providing related literature publications. The secondary reviewer should provide the literature independently to the primary reviewer. The data extraction will only be performed by the primary reviewer and the secondary reviewer should provide the related material. In case of any mismatch or issue, the secondary reviewer should guide the primary reviewer accordingly.
The review for the aforementioned search was performed both by primary and secondary reviewers. The already predefined protocol illustrated it in detail.
11.4.5.2 Data Synthesis
Data synthesis was performed by the primary reviewer with the help of the secondary reviewers. We found a list of 110 chapters as a final selection. The primary reviewer initially identified a list of 38 categories. These identified categories by the primary reviewer were again reviewed and some of them merged and finally we got a list of 20 risks, as shown in Table 11.8.
Table 11.8: Frequency-wise list of challenges.
| S# | Challenges | Freq N=110 | % (stage) |
| 1 | Lack of Common Development | 67 | 60.9 |
| 2 | Lack of Poor Architecture | 62 | 56 |
| 3 | Lack of Reliability | 46 | 41.8 |
| 4 | Lack of Development Issues | 39 | 36 |
| 5 | Lack of Management Issues | 39 | 36 |
| 6 | Lack of Environment | 38 | 34.5 |
| 7 | Cost Issues | 37 | 33.6 |
| 8 | Lack of Use of Technology | 31 | 29 |
| 9 | Lack of Knowledge for High Skilled Resources | 31 | 28.2 |
| 10 | Lack of Privacy | 30 | 28 |
| 11 | Tradition Co-located Models | 31 | 27.3 |
| 12 | Lack of Assessment Issues | 29 | 27 |
| 13 | Lack of Poor Scheduling | 28 | 26 |
| 14 | Lack of Trust | 27 | 25 |
| 15 | Communication Workflows | 27 | 25 |
| 16 | Market Expansion Growth | 27 | 25 |
| 17 | Framework Integration | 27 | 25 |
| 18 | Lack of Effectiveness | 27 | 25 |
| 19 | Fault Tolerance | 19 | 17.3 |
| 20 | Deliverance Issue | 17 | 15.5 |
11.4.6 Findings
List of Challenges Found Through Systematic Literature Review (SLR): With the help of SLR, we found various issues/challenges faced by the development team, i.e., vendor-side organization, during the development of software. Two issues were noted as the most critical during our search, as they possess high frequency. The first was the “lack of common development” issue, with a frequency index of 61%. The “lack of common development” is further proposed by the group of following challenges: “structuring issues,” “software complexity issues,” “requirement issues,” “diagram formalization issues,” “module design,” moved later in the development process. In 1972, Bengtsson [33] claimed that the way a software system disintegrates into modules affects its capabilities to meet levels of efficiency in certain aspects, e.g. performance, flexibility. Software architecture is concerned with which modules are to be used to develop a system and how these modules are related, i.e., the full structure of the system. The architecture of a software system sets the boundaries for its quality. Hence, to design the software architecture and to meet the quality requirements is to reduce the risk of not achieving the required quality levels. The design team vendor organization partaking in a deep level of situational consciousness in the beginning can also gather relevant information to be adopted and interpret it from different viewpoints of the involved stakeholders, exchange (well-grounded and reasonable) locations based on expectations, assumptions and predictions over the excellence of the resulting architecture with a client, and ultimately agree upon a single decision that will be interpreted later on [34].
The second most critical challenge found with the help of SLR is “lack of poor architecture,” with a frequency index of 56%. Rick Kazman, a professor at the University of Hawaii, raised the well-known observation of John Zachman in his article about architecture that “architecture is architecture is architecture,” which means that in all possibilities the system could be laid down by its scaled architecture [35]. Johan den Haan stated in his article [36] that the explanation of the term “designing” is required for making a distinction between the architecture and the design of a system. These terms refer to how systems will be constructed. According to [36], there are two different system notions present, the ontological and the teleological system notions. The teleological system notion refers to the function and the (external) performance of a system. This notion can be imagined with a black-box model. The teleological system notion is satisfactory for controlling or using a system. The ontological system notion, on the other hand, can also be used for changing or building a system. It is about the operation and the construction of a system and can be modeled with a white-box model. Our findings are presented in Table 11.8, which can facilitate the development team and the clients in overcoming the issue found with the help of SLR.
The third most important challenge found with the help of SLR is “lack of reliability,” which is also considered a significant challenge. The said challenge is fixed with the frequency index of 41.8% as shown in Table 11.8. In his article, Eoin Woods [37] stated that every system is treated according to its reliability. This means that the software architecture should be concerned with enabling evaluation of the developed system.
The fourth and fifth challenges identified with the help of SLR for the development of the framework for software architecture designing challenges model for the IoT are recorded as “lack of development limitation,” and “lack of management issues,” with frequency indices of 36.0%. Both challenges were placed at the same number of frequency index due to their relevancy. Bernardo et al. [38] and Rubrich [39] specified the pivotal role that management plays at the beginning of every task or exercise. They further stated that the lack of management issues include ill-scheduled, unrevealed deliverance and period, unrecognized prices and checklists, and undefined goals, etc. They also emphasized that in software development outsourcing, the parties should adopt the proper checklist of arrangements. Without proper management, the workflow would be faced with failure ahead after the commencement of its utilization by the end user.
The sixth and seventh challenges of the software architecture designing challenges model are “lack of environment issues,” with a frequency index of 34%, and “cost issues,” with a frequency index of 33.6%. According to the statement of López et al. [40]. The IoT’s products and life cycle are important and interoperable for the proposed architecture of software development for IoT software systems. Thus, due to the costly products for the development of an architecture for the IoT software system and the lack of consent from both the parties, i.e., vendor- and client-side organizations, difficulties may be created in outsourcing, which is also known as the failure of unsuccessful software outsourcing. Another important factor influencing the workflow of any software architecture are environmental issues, i.e., without having a proper environment for the development of an architecture for the IoT software system, the correspondence between client- and vendor-side organizations will also be affected. Yvnnx [41] also stated that lack of environmental awareness results in problems in the environment, such as loss of biodiversity, pollution and global warming, etc., which can also affect the flow of outsourcing during the development of software architecture for the IoT software system.
“Lack of technology” is the eighth challenge in Table 11.8 of the software architecture designing challenges model; it maintained the frequency index of 29.0%. Soto and his team [42] discuss the development of software architecture and state that the end-user being unfamiliar with the system they are interacting with and the nontechnical equipment used during the interaction, can also lead to system failure. The lack of technology refers to the improper equipment from the vendor-side organization used for the development of software architecture. As technology nowadays plays a significant role in making the daily lives of humans easier, “lack of knowledge for high skilled resources,” with a frequency index of 28.2%, is known as the ninth uppermost challenge for the development of the software architecture designing challenges model for IoT software systems [43].
A system which doesn’t have specific privacy would also be faced with failure due to the damage caused by lost data. Here, the “lack of privacy,” with a frequency index of 28.0%, is considered as the tenth challenge for the designing software architecture model for the IoT software system. This refers to the highly automated, entirely automated, or even autonomous robot systems or vehicles with earlier unavailable intelligent capabilities requiring new techniques of architecture and development methods to grasp the highest mandatory stages of safety and security [44].
The eleventh and twelfth ranked challenges for the software architecture designing challenges model for the IoT software system are “traditional co-located models,” with a frequency index of 27.3%, and “lack of assessment issues,” with a frequency index of 27%. The traditional co-located model refers to the previous concept of model development and designing which are acting or performing the same task in different shapes and physical faces adapted by the developed system for a particular task [45]. Whereas, the lack of software assessment is the progression assessment, which is a self-controlled inspection of the software processes assumed or used by a company or organization, based on a development model. Our further investigation showed that the software assessment quality and structure is influenced by its development perspective, which is affected by the customer contribution, agility, which allows cooperation among the development teams; outsourcing; and human influences, i.e., innovation, developers’ creativity, art and experience, which are not partial to development approaches but customer claim and feedback systems [46].
“Lack of poor scheduling” is also framed as a 13th challenge for the software architecture designing challenges model for the IoT software system. Earlier negotiations on the fixation of origins and other essential services of a system are also based on the successful system. The poor scheduling challenge also refers to the consequences of poor management scheduling, which is generally seen in the form of stress in the workplace, staff conflicts, time distribution, poor productivity, ultimately poor retention of trained workforce, and increased absenteeism. We mainly focus on the lack of poor scheduling and a random mixture of resource requests for interactive and batch applications in an architecture-independent state or procedure, etc.
The fourteenth, fifteenth, sixteenth, seventeenth, and eighteenth challenges have the same frequency, with only 25% from the extracted data of the literature review. These challenges are “lack of trust,” “‘communication workflow,” “market expansion growth,” “framework integration,” and “lack of effectiveness.” The lack of trust is a common challenge faced by software architecture vendor organizations. Some empirical insights of software practitioners on the role of trust in software outsourcing relationships are when the customer expectations are high, deliverance time is limited, and the other essential resources are found limited, then the vendor organization should ensure the arrangement of the essential services on time for the successful trustworthiness with the client-side organization [47]. Our literature study has also identified another challenge named “lack of communication workflow,” as the source of failure of software development outsourcing. It means that the meager communication capabilities may be separated as the lack of proper language, accent, or slang while one speaks. It can be boosted by unfailing practice and wrought out by refining our soft communication skills [48]. The sixteenth challenge of our explorative study is “market expansion growth.” It means suggesting the flow of a service or product to a broader section of a current market or into a new demographic, psychographic or geographic market. Instead, software architectures must be thoroughly designed and then executed using fragmentary growth, which suggests that software architects need to incrementally and iteratively refine, assess, and improve a software system [49].
The seventeenth challenge of the study is “framework integration issues.” This issue of designing a software architecture involves integration frameworks that deliver a model for statement and interaction between mutually interconnecting software applications in service-oriented architecture (SOA). The management plan is comprised because the plan used by the organization is to achieve goals. As we have already stated, the IoT is trending in the market, so there will be more customer requests. The influence of the IoT on software development is yet to be known; as a part of this research we have composed software development models [50]. The eighteenth challenge of our research investigation is “lack of effectiveness.” The maintenance and restoration of software design and architecture are often defenseless against rapid increases in size and complexity, changing requirements, and insufficient understanding of the required architectural design [51-55].
The nineteenth and twentieth challenges of our study are “fault tolerance,” with a frequency index of 17.3%, and “deliverance issues,” with a frequency index of 15.5%. Both challenges were considered as dropped from our research, investigation and analysis, as our critical percentage for each challenge was 25% and > 25%.
11.5 Continent-Wise Comparison of the Challenges Found
The challenges that were found have been compared continent to continent in order to know whether they are different or the same in each continent. We have selected five continents (Asia, Europe, North America, Africa, Australia). Table 11.9 illustrates the continent-wise presentation with its frequency index. For the analysis of the identified challenges, we used the Chi-square test to find out whether there were significant differences between the identified challenges in these five continents. According to Khan et al. [29], the Chi-square test is considered by researchers to be more powerful than Pearson’s chi-square test.
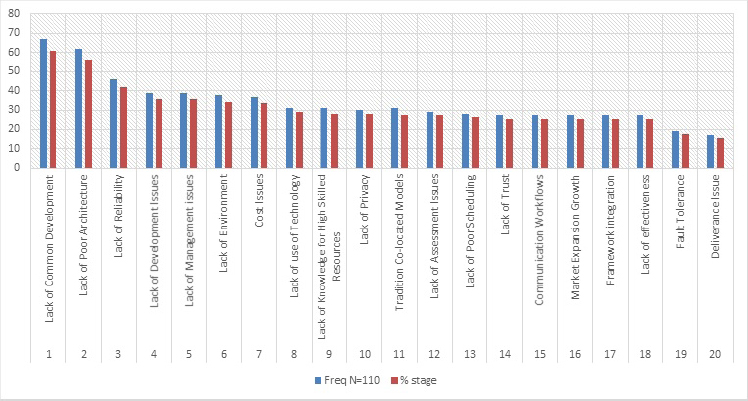
Figure 11.5: Graphical representation of the identified challenges.
In the early stages, we obtained 38 challenges, which have been merged. Finally, we achieved 20 challenges that were received from a different continent. These 20 challenges have been evaluated further and two challenge frequencies were considered less than 25. Therefore, only 20 challenges have been considered as critical, in which two challenges, “lack of common development” and “lack of poor architecture,” have been highlighted as the most critical/considerable challenges among the rest. These two challenges have a frequency which is >= 50, as earlier discussed in detailed. The said frequency has been determined with the help of Statistical Package for Social Sciences (SPSS). The achieved frequency-wise outcomes were evaluated by SPSS while defining different relevant variables. Figure 11.5 gives a graphical representation of the identified challenges.
This research obtained the objective of determining the issues that affect the quality and chances of failure of the IoT software system.
11.6 Limitations
This research study indicates how efficient outsourcing is needed according to the identified challenges faced by vendor-side organizations in the development of a quality software system. We found limited data for extraction, but later applied the snowballing technique for increasing the number of chapters to be extracted for RQ1. A total of 38 groups of challenges were found and then some of them were merged and finally we obtained 20 groups to be considered as the main issues for the failure of any IoT software in the utilization stage. We plan to conduct an empirical study in the architecture and IoT software industry to validate our findings. Our systematic literature review (SLR) process will have missed some of the relevant data/chapters due to the considerable number of chapters.
Table 11.9: Results of data from different continents.
| Continent Name | Frequency | Percentage |
| Asia | 32 | 29.1 |
| Europe | 51 | 46.4 |
| North America | 13 | 11.8 |
| Africa | 5 | 4.5 |
| Australia | 9 | 8.2 |
11.7 Conclusion and Future Work
Our findings will provide safe shade to any IoT software in the initial development stage. Now, these identified challenges would be obvious to the vendor-side organization for preavoiding it in the development and in communication with the client, so the developed system will work properly as per user stratification. We identified a total of 20 challenges in which the 2 challenges indicated as the most critical issues were “lack of common development” and “lack of poor architecture,” due to their high frequency received from multiple continents. The vendor should act according to our identified challenges in Table 11.8, which address the RQ1 for the successful completion of any software development. To address the RQ2, vendor organizations which are busy in the development process on various continents through outsourcing should concentrate on Table 11.10.
We will validate the identified challenges with the help of empirical studies in our future work by getting the consent of different software architecture stockholders for our developed architecture framework for the IoT software system.
In Table 11.10, we obtained three challenges whose P value is less than 0.05, which shows a significant difference between the continents. We considered the initial three continents, i.e., Asia, Europe and North America, as A and Africa and Australia as B. The market expansion growth challenge is considered essential in Continent A while less considered in continent B, where the same is also applicable to the “framework integration,” which is considered highly essential in continent A and less considered in continent B. Another challenge whose P value is less than 0.05 is the “lack of assessment issue,” which is essential in continent A and less essential in continent B.
Table 11.10: Continent-wise frequency.

References
1. Stavropoulou, I., Grigoriou, M., & Kontogiannis, K. (2017). Case study on which relations to use for clustering-based software architecture recovery. Empirical Software Engineering, 22(4), 1717-1762.
2. Knodel, J., & Naab, M. (2017, April). How to Evaluate Software Architectures: Tutorial on Practical Insights on Architecture Evaluation Projects with Industrial Customers. In 2017 IEEE International Conference on Software Architecture Workshops (ICSAW) (pp. 183-184). IEEE.
3. Patel, Z. D. (2018, May). A review on service oriented architectures for internet of things (IoT). Proceedings of the 2nd International Conference on Trends in Electronics and Informatics (ICOEI 2018), (pp. 466-470). IEEE.
4. Ziegler, S., Nikoletsea, S., Krco, S., Rolim, J., & Fernandes, J. (2015, December). Internet of Things and crowd sourcing-a paradigm change for the research on the Internet of Things. In 2015 IEEE 2nd World Forum on Internet of Things (WF-IoT) (pp. 395-399). IEEE.
5. Lin, N., & Shi, W. (2014, September). The research on Internet of things application architecture based on web. In 2014 IEEE Workshop on Advanced Research and Technology in Industry Applications (WARTIA) (pp. 184-187). IEEE.
6. Herold, S., Blom, M., & Buckley, J. (2016, November). Evidence in architecture degradation and consistency checking research: preliminary results from a literature review. In Proccedings of the 10th European Conference on Software Architecture Workshops (pp. 1-7).
7. de Lemos, R. (2006, May). Software architectures for dependable systems: a software engineering perspective. In Proceedings of the 28th International Conference on Software Engineering (pp. 1065-1066).
8. Cui, L., Yang, S., Chen, F., Ming, Z., Lu, N., & Qin, J. (2018). A survey on application of machine learning for Internet of Things. International Journal of Machine Learning and Cybernetics, 9(8), 1399-1417.
9. Nechifor, S., Puiu, D., Târnaucˇa, B., & Moldoveanu, F. (2015). Autonomic aspects of IoT based systems: A logistics domain scheduling example. In Interoperability and Open-Source Solutions for the Internet of Things (pp. 153-168). Springer, Cham.
10. Cusick, J. J., Prasad, A., & Tepfenhart, W. M. (2008). Global software development: origins, practices, and directions. Advances in Computers, 74, 201-269.
11. Dias, J. P., & Ferreira, H. S. (2018). State of the software development life-cycle for the internet-of-things. arXiv preprint arXiv:1811.04159.
12. Woods, E. (2016). Software architecture in a changing world. IEEE Software, 33(6), 94-97.
13. Hasselbring, W. (2018). Software architecture: Past, present, future. In The Essence of Software Engineering (pp. 169-184). Springer, Cham.
14. Burd, B., Barker, L., Pérez, F. A. F., Russell, I., Siever, B., Tudor, L., ... & Pollock, I. (2018, July). The internet of things in undergraduate computer and information science education: exploring curricula and pedagogy. In Proceedings Companion of the 23rd Annual ACM Conference on Innovation and Technology in Computer Science Education (pp. 200-216).
15. Babar, M. A., Verner, J. M., & Nguyen, P. T. (2007). Establishing and maintaining trust in software outsourcing relationships: An empirical investigation. Journal of Systems and Software, 80(9), 1438-1449.
16. Mathrani, A., Parsons, D., & Mathrani, S. (2012). Knowledge Management Initiatives in Offshore Software Development: Vendors’ Perspectives. Journal of Universal Computer Science, 18(19), 2706-2730.
17. Seth, F. P., Mustonen-Ollila, E., Taipale, O., & Smolander, K. (2015). Software quality construction in 11 companies: an empirical study using the grounded theory. Software Quality Journal, 23(4), 627-660.
18. Fraser, S., Anderson, L., Crocker, R., Gabriel, R., Fowler, M., Lopez, R., & Thomas, D. (2004, October). Challenges in outsourcing and global development: how will your job change?. In Companion to the 19th annual ACM SIGPLAN Conference on Object-oriented Programming Systems, Languages, and Applications (pp. 145-147).
19. Belle, A. B., El-Boussaidi, G., Desrosiers, C., & Mili, H. (2013). The layered architecture revisited: Is it an optimization problem?. In SEKE (pp. 344-349).
20. Márquez, G., & Astudillo, H. (2018, December). Actual use of architectural patterns in microservices-based open source projects. In 2018 25th Asia-Pacific Software Engineering Conference (APSEC) (pp. 31-40). IEEE.
21. Filipponi, L., Vitaletti, A., Landi, G., Memeo, V., Laura, G., & Pucci, P. (2010, July). Smart city: An event driven architecture for monitoring public spaces with heterogeneous sensors. In 2010 Fourth International Conference on Sensor Technologies and Applications (pp. 281-286). IEEE.
22. Stegemann, S. K., Funk, B., & Slotos, T. (2007). A blackboard architecture for workflows. In CAiSE Forum (Vol. 247).
23. Stapić, Z., López, E. G., Cabot, A. G., de Marcos Ortega, L., & Strahonja, V. (2012). Performing systematic literature review in software engineering. In Central European Conference on Information and Intelligent Systems (p. 441). Faculty of Organization and Informatics Varazdin.
24. Yulin, D., Shiying, L., & Yi, L. (2006, July). Information relevance management model-a new strategy in information security management in the outsourcing industry. In 5th IEEE/ACIS International Conference on Computer and Information Science and 1st IEEE/ACIS International Workshop on Component-Based Software Engineering, Software Architecture and Reuse (ICIS-COMSAR’06) (pp. 433-438). IEEE.
25. Sampaio, A. (2015). Improving systematic mapping reviews. ACM SIGSOFT Software Engineering Notes, 40(6), 1-8.
26. Rehman, M. N., & Khan (2020). Software architectecture designing challenges model for internet of things IoT software system. USJ, 1.1(1): p.9.
27. Khan, A. A., Keung, J., Hussain, S., Niazi, M., & Kieffer, S. (2018). Systematic literature study for dimensional classification of success factors affecting process improvement in global software development: client–vendor perspective. IET Software, 12(4), 333-344.
28. Magdaleno, A. M., Werner, C. M. L., & De Araujo, R. M. (2012). Reconciling software development models: A quasi-systematic review. Journal of Systems and Software, 85(2), 351-369.
29. Khan, S. U., Niazi, M., & Ahmad, R. (2009, December). Critical barriers for offshore software development outsourcing vendors: a systematic literature review. In 2009 16th Asia-Pacific Software Engineering Conference (pp. 79-86). IEEE.
30. Khan, A. A., Keung, J., Niazi, M., Hussain, S., & Ahmad, A. (2017). Systematic literature review and empirical investigation of barriers to process improvement in global software development: Client–vendor perspective. Information and Software Technology, 87, 180-205.
31. Eldawlatly, A., Alshehri, H., Alqahtani, A., Ahmad, A., Al-Dammas, F., & Marzouk, A. (2018). Appearance of Population, Intervention, Comparison, and Outcome as research question in the title of articles of three different anesthesia journals: A pilot study. Saudi Journal of Anaesthesia, 12(2), 283.
32. Bhat, A. (2020). Snowball sampling: Definition, method, advantages and disadvantages.
33. Bengtsson, P. (1999). Design and evaluation of software architecture. University of Karlskrona/Ronneby: Sweden. p. 152.
34. Nowak, M., & Pautasso, C. (2013, July). Team situational awareness and architectural decision making with the software architecture warehouse. In European Conference on Software Architecture (pp. 146-161). Springer, Berlin, Heidelberg.
35. Clements, P., Kazman, R., & Klein, M. (2011). Evaluating software architectures. Beijing: Tsinghua University Press.
36. Den Haan, J. (2007). Architecture, A Definition http://www.theenterprisearchitect.eu/blog/2007/05/15/architecture-a-definition/, May, 2007: p. 3.
37. Woods, E. (2016). Software architecture in a changing world. IEEE Software, 33(6), 94-97.
38. Bernardo, M., Ciancarini, P., & Donatiello, L. (2002). Architecting families of software systems with process algebras. ACM Transactions on Software Engineering and Methodology (TOSEM), 11(4), 386-426.
39. Rubrich, L. (2020). Lack of Management Leadership, Support Scuttles Lean Effort. https://www.reliableplant.com/Read/21642/lack-of-management-leadership,-support-scuttleslean-effort
40. López, T. S., Brintrup, A., Isenberg, M. A., & Mansfeld, J. (2011). Resource management in the internet of things: Clustering, synchronisation and software agents. In Architecting the Internet of Things (pp. 159-193). Springer, Berlin, Heidelberg.
41. Lack of envromental awareness by yvnnx on prezi next. https://prezi.com/srmmti2jhm0m/lack-of-environmental-awareness/
42. Johnson, A. M., Jacovina, M. E., Russell, D. G., & Soto, C. M. (2016). Challenges and solutions when using technologies in the classroom. ERIC Clearinghouse.
43. Falessi, D., Babar, M. A., Cantone, G., & Kruchten, P. (2010). Applying empirical software engineering to software architecture: challenges and lessons learned. Empirical Software Engineering, 15(3), 250-276.
44. Kugele, S., Hettler, D., & Peter, J. (2018, April). Data-centric communication and containerization for future automotive software architectures. In 2018 IEEE International Conference on Software Architecture (ICSA) (pp. 65-6509). IEEE.
45. Twomey, J. P., Johnston, J., Steinberg, J. L., & Morris, A. (2016). Whole-Person Care: Implementing Behavioral Health Integration in the Patient-Centered Medical Home.
46. Seth, F. P., Mustonen-Ollila, E., Taipale, O., & Smolander, K. (2015). Software quality construction in 11 companies: an empirical study using the grounded theory. Software Quality Journal, 23(4), 627-660.
47. de Andrade, H. S., Almeida, E., & Crnkovic, I. (2014). Architectural bad smells in software product lines: An exploratory study. In Proceedings of the WICSA 2014 Companion Volume (pp. 1-6).
48. Khan, A. A., & Shameem, M. (2020). Multicriteria decision-making taxonomy for DevOps challenging factors using analytical hierarchy process. Journal of Software: Evolution and Process, 32(10), e2263. DOI: 10.1002/smr.2263
49. Khan, A. A., Shameem, M., Kumar, R. R., Hussain, S., & Yan, X. (2019). Fuzzy AHP based prioritization and taxonomy of software process improvement success factors in global software development. Applied Soft Computing, 83, 105648.
50. Murari, B. T. (2016). Impact of Internet of Things on Software Business Model and Software Industry.
51. Schmidt, F. (2014). A multi-objective architecture reconstruction approach (Doctoral dissertation, Auckland University of Technology).
52. Zhou, P., Khan, A. A., Liang, P., & Badshah, S. (2021). System and Software Processes in Practice: Insights from Chinese Industry. In the proceedings of 25th International Conference on Evaluation and Assessment in Software Engineering (EASE’2021).
53. Garg, S., Chatterjee, J. M., & Le, D. N. (2019). Implementation of Rest Architecure-Based Energy-Efficient Home Automation System. Security Designs for the Cloud, Iot, and Social Networking, 143-152.
54. Doss, S., Paranthaman, J., Gopalakrishnan, S., Duraisamy, A., Pal, S., Duraisamy, B., ... & Le, D. N. (2021). Memetic Optimization with Cryptographic Encryption for Secure Medical Data Transmission in IoT-Based Distributed Systems. CMC-COMPUTERS MATERIALS & CONTINUA, 66(2), 1577-1594.
55. Le, D. N., Bhatt, C. M., & Madhukar, M. (Eds.). (2019). Security Designs for the Cloud, IoT, and Social Networking. John Wiley & Sons, Incorporated.
