2
Quantum and Post-Quantum Cryptography
Om Pal*, Manoj Jain, B.K. Murthy and Vinay Thakur
Ministry of Electronics and Information Technology (MeitY), Government of India, New Delhi, India
*Corresponding author: [email protected]
Abstract
Broadly, Cryptography refers to the passing of secret information from one place to another securely so that only intended receivers can decrypt it. Security of the modern public key cryptographic algorithms and protocols is mainly dependent on the complexity of the factorization of the product of large prime numbers. But due to technological developments in the field of computation and evolution of new mathematical techniques, the problem of the factorization of the product of integers is not complex anymore nowadays. The growing research interests in Quantum computing technology is also making the modern public cryptographic algorithms unsafe. Researchers have proved that modern cryptographic algorithms such as RSA are breakable using quantum computers in polynomial time complexity. Therefore, attempts are being made to design new cryptographic algorithms using Quantum Computing techniques. Quantum cryptography is an emerging field which works on principles of quantum physics. In this paper, an attempt has been made to introduce quantum cryptography, analysis on supremacy of quantum cryptography over modern cryptography, discussion on key distribution using quantum physics, and implementation challenges in quantum key distribution. We have proposed two key verification mechanisms for BB84 protocol, analysis on quantum attacks on modern cryptographic digital signatures, Post-quantum digital signatures and finally discussion on future directions of this technology.
Keywords: Quantum cryptography, quantum key distribution, QKD, post-quantum digital signature, quantum computing, quantum mechanics
2.1 Introduction
In 1965, Gordon E. Moore observed that every year the density of the transistors on a microchip doubles. Computational power of the personal computer also doubled every 1.5 years between 1975 and 2009 [1]. However, there are many problems which have exponential computational complexity and these cannot be solved in polynomial time by today’s super computers. In 1982, physicist Richard Feynman thought about a quantum computing. Feynman observed that some problems which have exponential computational complexity can be solved in polynomial time using the quantum phenomena [2]. In 1994, Peter Shor proposed a quantum algorithm and showed that using quantum computer, factorization of product of large prime numbers could be done in polynomial time [3].
The strength of modern cryptographic systems is based on the complexity of factorization of large integers, the discrete logarithmic problem and the irreversible nature of hashing algorithms. Due to the reality of quantum computing power, there is a threat to some of the modern cryptographic algorithms and protocols. Any cryptographic system or protocol whose strength is based on integer factorization and discrete logarithm is vulnerable to quantum attacks. In modern cryptography, efficient and secure key distribution is still a challenge. In the quantum scenario, key is distributed using the quantum features of a particle. Digital signature algorithms such as Digital Signature Algorithm (DSA) and Elliptic curve Digital Signature Algorithm (ECDSA) are based on complexity of integer factorization; therefore, these signatures are also vulnerable to quantum attacks [4–7].
The rest of the paper is organized as follows: in section 2.2: security of present cryptographic systems is analyzed in quantum scenario; in section 2.3, analysis of key distribution in present cryptographic system and quantum system is given; in section 2.4, post-quantum digital signatures are presented. Finally in section 2.5, the conclusion and future directions are given.
2.2 Security of Modern Cryptographic Systems
Modern cryptographic systems are broadly divided into two categories: 1) Asymmetric key cryptographic systems, and 2) Symmetric key cryptographic systems.
Asymmetric key Cryptography: In asymmetric key cryptographic systems, two cryptographic keys are used; out of these two keys, one is used for encryption and another for decryption. Both keys are mathematically inverse of each other; when plaintext is encrypted by one key then corresponding cipher text is decrypted using the second key. Encryption key is called Public key, which is made available publicly. Decryption key is called Private key and the owner of this key keeps this key secretly. Strength of asymmetric cryptographic systems is directly proportional to the complexity of integer factorization and discrete logarithmic problem. Some well-known asymmetric algorithms are RSA, DH, DSA, ECDH, ECDSA [8, 9].
Symmetric key Cryptography: In symmetric key cryptographic systems, the same key is used for encryption and decryption. In symmetric key cryptographic systems, distribution of the common key is a challenge. AES, DES, 3-DES, SHA-1, MD5, SHA-256, etc., are some variants of symmetric cryptographic systems [9, 10].
The major breakthrough in the field of quantum computing is the development of Shor’s algorithm for integer factorization and Grover’s algorithm for searching of an element from a large dataset [3, 11]. However, there is no uniform mechanism to design the quantum algorithms. Considering it, this is the view of researchers that not all modern cryptographic algorithms are under the threat of quantum computing. Other than Grover’s searching algorithm, no quantum algorithm exists which can be considered as a threat to the symmetric cryptographic systems. Hashing algorithms such as SHA-1, MD5 are considered weak against the quantum attacks, since Grover quantum search algorithm could be used to get hash collisions faster. However, algorithms with 256 bit hash outputs or more are considered safe. Symmetric algorithms such as AES with key length of 256 bits are considered safe against the quantum attacks. Therefore, it is the belief of researchers that Symmetric key algorithms and its variations are in the safe state and quantum computing is not a threat to these cryptosystems. But it is not denied that there will be a quantum threat in the near future to these symmetric crypto systems [12–15]. Comparison of security level of various cryptographic systems is given in Table 2.1.
2.2.1 Classical and Quantum Factoring of A Large Number
Recently (February 2020), RSA-250 number (250 decimal digits/829 binary digits) has been factored successfully by Boudot et al. [16]. To factor this number, Grid 500 (experimental testbed, France) computing resource [17] with Field Sieve algorithm and CADO-NFS software were used. Total computation time on Gold 6130 CPUs (2.1GHz) was roughly 2700 core-years.
Table 2.1 Security level of cryptographic systems.
| Public crypto scheme | Equivalent symmetric key length (in classical computing scenario) | Quantum security | Equivalent symmetric key length (in Quantum computing scenario) |
| RSA-1024 | 80 | Not secure | 0 |
| ECC-256 | 128 | Not secure | 0 |
| AES-256 | 256 | Secure | 128 |
| 3-DES-112 | 112 | Not secure | 56 |
| SHA-256 | 256 | Secure | 85 (Grover’s algorithm with birthday paradox) |
| DSA, ECDSA, ECDH | Secure | Not secure | 0 |
To the date, best complexity of field sieve (GNFS) algorithm, for a decimal number N, is in asymptotic order of
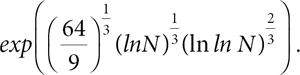
With this computing power, it is estimated that to factor a number of 1000 digits, it would require much longer than the age of the universe. Therefore, it is not feasible to crack the RSA-1000 with present computing power.
In 1994, Peter Shor proposed a quantum algorithm which can factor an integer N by utilizing the quantum gates in order of ((log N)2 (log log N)(log log log N)). This is a probabilistic polynomial time algorithm with maximum error probability of 1/3. As modern public cryptographic systems such as RSA-1000 are using the hardness of integer factorization for security, therefore these public cryptographic algorithms are not secure after practical implementation of Shor algorithm [3].
Elliptic Curve Cryptography (ECC) is a family of Public key cryptographic system. At equivalent security level, ECC uses smaller key length compared to RSA crypto system. Due to Shor’s algorithm, ECC is also not secure in quantum computing environment. To break the ECC security of size N, total number of required logical qubits is 6N [18].
2.2.2 Classical and Quantum Search of An Item
Average complexity of searching an element in a classical bit space of n bits is 2n−1 and worst case complexity is 2n. In present classical computing scenario, classical bit space of 80 bits can be considered as a safe key space. But in quantum computing scenario, 80 bits key space cannot be considered a safe key space.
So far no quantum algorithm exists to break the symmetric cryptographic systems. However, Grover’s Quantum algorithm reduces the security level of symmetric cryptographic systems. By using Grover’s algorithm symmetric key space can be reduced to 2n/2 from 2n [11]. Therefore, to maintain the same level of security, double symmetric key length is required in quantum computing environment. It is also concluded that quantum computing is not a threat to symmetric key cryptographic systems [12].
2.3 Quantum Key Distribution
The Diffie-Hellman key exchange protocol of modern cryptographic systems provides the opportunity to arrive at a common key by exchanging texts over insecure medium without meeting in advance. Security of Diffie-Hellman key exchange is dependent on discrete logarithmic problem [19]. Using quantum Shor algorithm, discrete logarithmic problem is solvable in polynomial time complexity; therefore Diffie-Hellman key exchange protocol is under the threat of quantum attack.
In 1984, Bennett, F. Bessette [20] proposed a Quantum Key Distribution (QKD) protocol which is based on Heisenberg’s Uncertainty Principle in quantum physics. Heisenberg’s Uncertainty Principle states that it is not possible to measure the momentum and position of a quantum particle with absolute precision [21]. To leverage this principle, quantum cryptography uses the photon particles on different bases. Heisenberg’s principle cannot be circumvented due to non-cloning feature of quantum state. Non-cloning theorem states that it is impossible to make the identical copies of any quantum state. Recently (June 2020), an article on advances in quantum cryptology was accepted in the Journal of Advances in Optics and Photonics [22]. In the article, the authors analysed the satellite challenges for quantum communication, device independence challenges, key distribution challenges, etc., and discussed the limitations associated with quantum repeaters and networks.
2.3.1 BB84 Protocol
In BB84 quantum key distribution protocol [20] bits 0 and 1 are encoded in the state of polarized photon. At the sender’s end transmitted photon is polarised in one of the four states namely horizontal (0 degree polarization), vertical (90 degree polarization), diagonal (45 degree polarization) and anti-diagonal (135 degree polarization) state. For the purpose of encoding, horizontal and diagonal polarisation of photon represents the bit 0 and, vertical and ant-diagonal polarisation represents the bit 1. At receiver end, to measure the state of the photon, photon detector with two basis (rectilinear and diagonal) is used. Rectilinear basis detects photon at 0 degree and 90 degree polarization. Diagonal basis detects photon at 45 degree and 135 degree polarization. Receiver measures the state of photon at one of the two basis randomly [23].
Let Alice transmit a sequence of photons randomly in one of the four polarized states. Alice selects the polarized state randomly, hence the probability of photon being in a particular state is 25%. Bob uses photon detector with two bases, namely rectilinear and diagonal. He chooses basis randomly, therefore in 50% cases, Bob is able to measure the state of polarised photon correctly. After transmission phase is over, Bob shares the sequences of used bases to Alice through classical or insecure channel. Alice informs Bob which bases he used correctly and subsequently Alice and Bob both discard the bits corresponding to photons which were measured by Bob at different bases. The remaining bit stream is the key [24]. Steps of quantum key distribution are illustrated in Figure 2.1.
It is also necessary to ensure that there was no eavesdropper or measurement error during the key exchange. If there is any transmission error or eavesdropper measures the state of any photon during the transmission then the key owned by Alice will be different from the key owned by Bob. If Eve measures the state of photons then due to Heisenberg’s Uncertainty Principle momentum of the photon will be changed. Therefore, Bob will read the bits incorrectly 50% of the time and approximately 25% bit sequence of Bob will differ from bit sequence of Alice. To verify the correctness of bit stream, Bob can share a few random bits of key to Alice; if shared random bits are correct then it indicates that no eavesdropper was present during the transmission. Hence, Alice and Bob both discard the shared bits and the remaining bit stream is the final secret key [12].

Figure 2.1 BB84 key exchange protocol.
2.3.1.1 Proposed Key Verification Phase for BB84
We are proposing two mechanisms for verification of final key in BB84 protocol.
- (a) A universal statement or a set of few universal statements can be encrypted using the final secret key; if both parties are able to decrypt the cipher of opposite party correctly then no error occurred and no eavesdropper was present during the formation of key.
- (b) In second verification mechanism, Bob takes the hash of final key, encrypts the hash with final key and sends the encrypted hash to Alice. If computed hash at Alice’s end matches with received hash from Bob then it is confirmed that no eavesdropper was present during the formation of key, and Alice passes the message to Bob regarding the correctness of key through insecure channel.
2.3.2 E91 Protocol
In 1991, Artur Eckert [25] proposed an Entanglement-based quantum key distribution protocol. In this protocol, source releases a pair of entangled photons and from this entangled pair, one particle is received by Alice and another is received by Bob. Alice and Bob both use random basis for measurement of photon and discuss the used basis through classical channel. If both use the same basis for measurement then they will get the opposite result. To check the presence of an eavesdropper, Alice and Bob can check the Bell’s inequality. If Bell’s inequality principle does not hold then it indicates that photons are truly entangled and no eavesdropper is present. Detailed steps of the protocol are given in Figure 2.2.
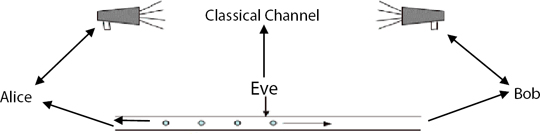
Figure 2.2 E91 key exchange protocol.
Let Alice use 0° and 45° polarization to represent bit 0, and 90° and 135° to represent bit 1 then Bob gets the same key if he uses 0° and 45° polarization to represent bit 1, and 90° and 135° to represent bit 0. This result is achieved only if entangled state |ψ> is used. Entangled state |ψ> is represented as follows:
If diagonal bases are passed to receivers then |ψ> will be
2.3.3 Practical Challenges of Quantum Key Distribution
Quantum key distribution is unconditionally secure because no assumptions are made regarding the capability of Eavesdropper. It is assumed that Eve has best resources and computing power to guess the key but due to law of mechanics, he is not able to deduce the key. However, man-in-themiddle attack cannot be denied in QKD. Eve can pretend to be Alice to Bob and at the same time can pretend to be Bob to Alice [26]. To prevent the man-in-the-middle attack, authentication of each other is the only way. Another challenge of QKD is to set up an error-free key distributing environment. If measurements of Alice and Bob are not matching with each other then there is no way to decide whether mismatch occurred due to the presence of Eve or noisy and imperfect equipments.
In 2010, Lydersen et al. [27] proved that in principle BB84 protocol is unconditionally secure but secret key can be deduced if hardware implementation is faulty. Authors blinded the avalanche photodiode-based detector and successfully inspected the secret key without the notice of receiver. Therefore, exchange of key is not secure if equipment is imperfect.
Other challenges in QKD includes high quantum bit error rate, Photon Number Splitting (PNS) attack, etc.
These are Photon Number Splitting (PNS) attack launched by an eavesdropper, high Qubit Error Rate, and low Raw Key Efficiency. In Photon Number Splitting (PNS) attack, Eve split the photon and can keep extra photon with him. Eve can measure the stored photon at chosen basis and can deduce the key. To protect against the PNS attack, there are variations of BB84 such as SARG04 who are resilient against the PNS attack [26].
2.3.4 Multi-Party Quantum Key Agreement Protocol
In Quantum key distribution, a party generates the bits of key and transfers to the other party using the quantum channel [20]. In QKD, there is an influence of single party in formation of secret key. But in case of key agreement protocol, two or more parties influence the quantum key. For the first time, in 2010, Zhou, et al. [28] proposed the idea of quantum key agreement protocol for two parties. The later idea of two-party key agreement was extended for multi-parties and to date, various multi-party quantum key agreement protocols have been proposed [29–32].
2.4 Post-Quantum Digital Signature
Digital Signature schemes such as DSA and ECDSA are built on the hardness of integer factorization and discrete logarithmic problems; therefore, these are under threat of quantum computing. The goal of post-quantum cryptography is to design quantum attack resistant encryption, key management and signature schemes. In December 2016, the National Institute of Standards and Technology (NIST) called for proposals for short-listing of quantum resistant encryption, key management and signature schemes and their standardization. Out of 69 complete proposals received, 26 proposals (which included 9 quantum digital signature proposals) were short-listed for the second round [33]. Details of short-listed digital signature schemes for the second round is given in Table 2.2.
Table 2.2 Round two candidates.
| Signature category | Signature schemes |
| Lattice | 1. CRYSTALS-DILITHIUM 2. FALCON 3. qTESLA |
| Multivariate Quadratic | 4. GeMSS 5. LUOV 6. MQDSS 7. Rainbow |
| Hash-based | 8. SPHINCS+ 9. Picnic |
Table 2.3 Round three candidates.
| Public key encryption/key Encapsulation Mechanisms (KEMs) | Signature schemes |
| 1. Classic McEliece 2. Crystals-Kyber 3. NTRU 4. SABER | 1. CRYSTALS-DILITHIUM 2. FALCON 3. Rainbow |
On 22 July 2020, NIST announced the result of the second-round candidates. Seven candidates moved to the third round [37]. Details of finalists for round three is given in Table 2.3.
2.4.1 Signatures Based on Lattice Techniques
These signature schemes are constructed based on the hardness of lattice problems like hardness of decisional ring learning with error, or those based on finding shortest vectors in lattices. Falcon, DILITHIUM and qTesla were the NIST round two candidates belonging to this category [34]. Now Falcon and DILITHIUM are the finalists for round three [37].
2.4.2 Signatures Based on Multivariate Quadratic Techniques
The fundamental hard problem in the Multivariate Quadratic (MQ) domain is the NP-completeness of the MQ-problem. This problem does not yet have a poly-time quantum algorithm. The problem instance comprises a system of quadratic equations in many variables and the challenge is to find one solution to the system. The Unbalanced Oil-Vinegar (UOV) and Hidden Field Equations (HFE) are two basic paradigms. There were four MQ-based signatures in the NIST round two, namely, Rainbow, GeMSS, LUOV and MQDSS. The signature scheme MQDSS is based on rewinding techniques [35]. Now Rainbow is the only finalist for round three in this category.
2.4.3 Hash-Based Signature Techniques
These signatures use classical techniques for their construction. SPHINCS+ and Picnic were two signature schemes in the NIST round two list which fall in this category. From this category, no signature scheme qualified for round three. Picnic uses the ciphertext-plaintext pair under a block cipher as the public key and the secret key used in the encryption as the corresponding secret key for the signature. A zero knowledge proof of knowledge binds the secret key and the message [36].
2.5 Conclusion and Future Directions
In today’s world, Information & Communication Technologies play a major role in every field of life. Without proper security of present cryptographic systems, no one can imagine the online transactions, Defence & satellite communication, e-Governance services, etc. Present cryptographic algorithms and protocols such as RSA, DSA, DH, ECDSA, ECDH are under threat of Quantum computing. To protect the collapse of present cryptographic systems, there is a need to develop quantum resistant cryptographic algorithms, protocols and signatures such as BB84 key distribution protocol, E91 key distribution protocol, lattice-based signature, Multivariate Quadratic signature, Hash-based signature, etc. The major challenge in post-quantum cryptography is the practical implementation of quantum protocols and quantum signatures algorithms. To provide the stable post-quantum cryptographic systems, there is a need of extensive research and development of efficient quantum computing devices, quantum sensors and quantum equipments.
References
1. M. Roser and H. Ritchie, Technological Progress, https://ourworldindata.org/technological-progress, 2013.
2. R. P. Feynman, Simulating physics with computers, Int. J. Theor. Phys., vol. 21, pp. 467–488, 1982.
3. P. W. Shor, Algorithms for Quantum Computation: Discrete Logarithms and Factoring, in 35th Annual Symposium on Foundations of Computer Science, 1994, pp. 124–134.
4. X. Tan, Introduction to Quantum Cryptography, in Theory and Practice of Cryptography and Network Security Protocols and Technologies, 2013.
5. R. Stubbs, Quantum Computing and its Impact on Cryptography, https://www.cryptomathic.com/news-events/blog/quantum-computing-and-itsimpact-on-cryptography, 2018.
6. Classical Cryptography and Quantum Cryptography, https://www.geeks-forgeeks.org/classical-cryptography-and-quantum-cryptography, 2020.
7. J. P. Mattsson and Erik Thormarker, What next in the world of post-quantum cryptography?, https://www.ericsson.com/en/blog/2020/3/post-quantum-cryptography-symmetric-asymmetric-algorithms, 2020.
8. E. payments Council, Guidelines On Cryptographic Algorithms Usage And Key Management, European payments council, pp. 1–73, 2018.
9. T. Bala and Y. Kumar, Asymmetric Algorithms and Symmetric Algorithms: A Review, in International Conference on Advancements in Engineering and Technology, 2015.
10. S. Chandra, S. Paira, S. S. Alam, and G. Sanyal, A comparative survey of symmetric and asymmetric key cryptography, Int. Conf. Electron. Commun. Comput. Eng. ICECCE 2014, no. November, pp. 83–93, 2014.
11. L. Grover, A Fast Quantum Mechanical Algorithm For Database Search, New Jersey, 1996.
12. Vasileios Mavroeidis, K. Vishi, M. D. Zych, and A. Jøsang, The Impact of Quantum Computing on Present Cryptography, Int. J. Adv. Comput. Sci. Appl., vol. 9, no. 3, pp. 1–10, 2018.
13. M. Campagna, Quantum Safe Cryptography and Security, An introduction, benefits, enablers and challenges, France, 2015.
14. W. Buchanan and A. Woodward, Will Quantum Computers be the End of Public Key Encryption, J. Cyber Secur. Technol., vol. 1, no. 1, pp. 1–22, 2016.
15. M. Möller and C. Vuik, On the impact of quantum computing technology on future developments in high-performance scientific computing, Ethics Inf. Technol., vol. 19, pp. 253–269, 2017.
16. P. Zimmermann, Factorization of RSA-250, https://lists.gforge.inria.fr/pipermail/cado-nfs-discuss/2020-February/001166.html, 2020.
17. Grid5000:Home, https://www.grid5000.fr/w/Grid5000:Home, 2020.
18. V. Stolbikova, Can Elliptic Curve Cryptography be Trusted? A Brief Analysis of the Security of a Popular Cryptosystem, https://www.isaca.org/resources/isaca-journal/issues/2016/volume-3/can-elliptic-curve-cryptography-be-trusted-a-brief-analysis-of-the-security-of-a-popular-cryptosyste, 2020.
19. N. Li, Research on Diffie – Hellman Key, Exchange Protocol, in IEEE 2nd International Conference, on Computer Engineering and Technology, pp. 634–637, 2010.
20. C. H. Bennett, F. Bessette, G. Brassard, L. Salvail, and J. Smolin, Experimental Quantum Cryptography, J. Cryptol., vol. 5, no. 1, pp. 3–28, 1992.
21. E. Panarella, Heisenberg uncertainty principle, Ann. la Fond. Louis Broglie, vol. 12, no. 2, pp. 165–193, 1987.
22. S. Pirandola et al., Advances in Quantum Cryptography, Adv. Opt. Photonics, pp. 1–118, 2020.
23. A. P. Bhatt and A. Sharma, Quantum Cryptography for Internet of Things Security, Electron. Sci. Technol., vol. 17, no. 3, pp. 213–220, 2019.
24. A. I. Nurhadi and N. R. Syambas, Quantum Key Distribution (QKD) Protocols: A Survey, in International Conference on Wireless and Telematics (ICWT), 2018.
25. A. K. Ekert, Quantum cryptography based on Bell’s theorem, Phys. Rev. Lett., vol. 67, no. 6, pp. 661–663, 1991.
26. M. Haitjema, A survey of the prominent Quantum Key Distribution Protocols, https://www.cse.wustl.edu/~jain/cse571-07/ftp/quantum, 2007.
27. L. Lydersen, C. Wiechers, D. E. C. Wittmann, J. Skaar, and V. Makarov, Hacking Commercial Quantum Cryptography Systems by Tailored Bright Illumination, Nat. Photonics, pp. 686–689, 2010.
28. N. Zhou, G. Zeng, and J. Xiong, Quantum key agreement protocol, Electron. Lett., vol. 40, no. 18, pp. 1149–1150, 2004.
29. Z. Sun, J. Yu, and P.Wang, Effcient multi-party quantum key agreement by cluster states, Quantum Inf. Process, vol. 15, no. 1, pp. 373–384, 2016.
30. Z. Sun, C. Zhang, P. Wang, J. Yu, Y. Zhang, and D. Long, Multi-party quantum key agreement by an entangled six-qubit state, Int. J. Theor. Phys, vol. 55, no. 3, pp. 1920–1929, 2016.
31. W. Huang, Q.-Y.Wen, B. Liu, Q. Su, and F. Gao, Cryptanalysis of a multiparty quantum key agreement protocol with single particles, Quantum Inf. Process, vol. 13, no. 17, pp. 1651–1657, 2014.
32. B. Liu, D. Xiao, H.-Y. Jia, and R.-Z. Liu, Collusive attacks to ῾circle-type’ multi-party quantum key agreement protocols, Quantum Inf. Process, vol. 15, no. 5, pp. 2113–2124, 2016.
33. L. Chen et al., NIST: Report on Post-Quantum Cryptography, NIST, Tech. Rep, 2016.
34. H. Nejatollahi, N. Dutt, S. Ray, F. Regazzoni, I. Banerjee, and R. Cammarota, Post-quantum Lattice-based Cryptography Implementations: A Survey, ACM Comput. Surv., vol. 51, no. 6, 2019.
35. J. Ding and B.-Y. Yang, Multivariate Public Key Cryptography. Springer, Berlin, Heidelberg, 2009.
36. C. Dods, N. P. Smart, and M. Stam, Hash Based Digital Signature Schemes, in International Conference on Cryptography and Coding, 2005, pp. 96–115.
37. PQC Standardization Process: Third Round Candidate Announcement, https://csrc.nist.gov/News/2020/pqc-third-round-candidate-announcement, July, 2020.
