16
Ransomware: Threats, Identification and Prevention
Sweta Thakur, Sangita Chaudhari* and Bharti Joshi
Department of Computer Engineering, Ramrao Adik Institute of Technology,
D. Y. Patil Deemed to be University, Nerul, Navi Mumbai, India
*Corresponding author: [email protected]
Abstract
Ransomware is a form of malware that encrypts a victim’s files. The attacker then demands a ransom from the victim to restore access to the data upon payment. Ransomware is a way of stealing money in which a user’s files are encrypted and the decryption key is held by the attacker until a ransom amount is paid by the victim. Organizations need to have a full inventory of all the devices that are connected to the network and protect with an updated security solution. It is mandatory to study ransomware and its strategies to protect your computer system from being infected. Various types of ransomware attacks along with their features are studied by highlighting the major methodology used in the launching of ransomware attacks. Also, the comparative analysis of various ransomwares, detection mechanisms as well as prevention policies against ransomware attacks are summarized.
Keywords: Ransomware, malware, locker ransomware, crypto ransomware, MAC ransomware, ransomware lifecycle, ransomware traits
16.1 Introduction
For decades, Ransomware has attracted great attention of cybersecurity experts due to the fast growth in its attack periphery and creation of lots of new variants capable to bypass security enforcements laid by antiviruses and anti-malwares. Most of them either encrypt the specific files on the victim’s machine or lock the complete system and stop the victim from using it. Ransomware infects all the systems connected to the network. Ransomware has also been developed to attack mobile phones [2]. While attacking mobile phones it locks the mobile phone and demands a ransom amount to unlock the phone by generating a new PIN. According to the research, overall, 95% of organizations that paid the ransom had their data restored. Paying the ransom doubles the cost of dealing with a ransomware attack. Of attacks where the data was encrypted, 59% involved data in the public cloud. Most of them target businesses, agencies, data servers storing and dealing with sensitive and confidential data.
There are various ways through which ransomware can enter your network such as spam email attachment, infected pen drives or malicious links. It starts encrypting files once the system is infected through malicious software [33]. Once the ransomware gets installed on the system it affects all the systems connected through the network. Once installed on the system it adds its own extension to the file making it inaccessible to the user. More dangerous types of ransomware can also work without user interaction (Figure 16.1) [35].
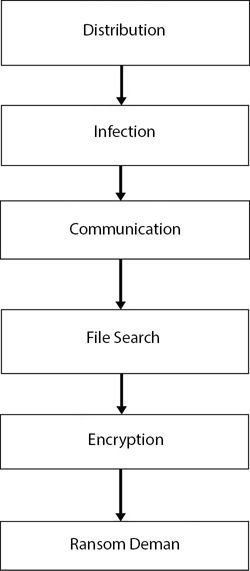
Figure 16.1 Working of ransomware.
Stage 1: Distribution: Ransomware is distributed through various ways like phishing emails, malicious websites or infected pen drives. Pay Per Install (PPI) model was introduced, in which whenever the ransomware gets installed on the host machine, the agent gets paid. The following techniques are used to distribute the software: Traffic Distribution System (TDS), Spam-email, Malicious attachments, Botents.
i. Traffic Distribution System (TDS):
Whenever the user clicks the ad on a legitimate website, the user redirects to the destination URL through TDS. The computer then gets compromised because of the drive-by-download exploits.
ii. Malvertisement:
Malicious Advertisements are used to distribute a malware with little to no user interaction required. It hits the user’s system without their knowledge. When it strikes, it turns common software programs against users to infect machines. Malicious Advertisements can get posted onto legitimate web-sites. The system gets infected by clicking such advertisements.
iii. Spam Email:
Spam email is the old way to deliver ransomware to a victim’s devices. Botnets are used to send spam emails by targeting some email ids. They may include some links through which malicious attachments can be downloaded that contain an exploit kit.
iv. Downloaders and Botnets:
Their job is to download malicious software on the system. Sometimes it may use Trojans to spread the ransomware.
Stage 2: File Search: It identifies the files that have common extensions like JPG, PDF, PPTX, etc., which are important to the user. To complete the malicious activities the following steps are used:
- i. To identify the computer uniquely, generate a unique code.
- ii. The program is set to run-at-startup using some scheduled tasks.
- iii. Deactivate shadow files, windows error recovery, and start-up repair.
- iv. Stop Antivirus software, Windows update, etc.
- v. Inject into explorer.exe and sychost.exe file.
- vi. Retrieve the IP address of the computer.
Stage 3: Communication: It is a unique feature of ransomware. The backup files are removed from the system to prevent it from recovery. In this phase, the ransomware search for the files that have common extensions like JPG, PDF, PPTX, etc., which might be important to the user. The ransomware will communicate to the command-and-control server and generate the keys required for encryption. The data can be encrypted using various algorithms like RSA, RC4, etc.
Stage 4: Encryption: The files identified on the target machine are encrypted in this phase. Strong encryption algorithms like AES 256 are used for encrypting the files. Files are renamed, moved, and encrypted. The scope of encryption is different for different types, e.g., CryptoWall v3 doesn’t encrypt filename, CryptoWall v4 gives random filenames, etc. Also, the file extensions are changed before applying the encryption algorithm.
Stage 5: Ransom demand: It is the final stage, the instructions for payment are displayed on the screen once the files are encrypted. The user has the only choice of opening the note and follow the steps given by the attacker to pay the ransom amount. The user is given few days to pay the ransom to get back the original data.
16.2 Types of Ransomwares
The effect of Ransomware is continuously increasing day-by-day, and it’s hard to keep track of the different strategies of ransomware. Each ransomware variant has its own way of spreading. We can categorize ransomwares based on various parameters like their way of encryption, how they are executed, the encryption algorithm they used and the operating system on which the ransomware gets executed. There are various types of ransomware (Figure 16.2). The way of spreading and working of each attack varies for each of them [35].
16.2.1 Locker Ransomware
Locker ransomware is a virus that infects PCs making the computer inaccessible to the victim until the ransom amount is paid. Locker ransomware locks and shuts down the entire computer. Typically, the infected system gives limited access to the victim, e.g., some sections of the computer may get locked. It only allows the victim to respond to the ransomware demands. Locker ransomware usually does not infect the entire computer network. The severity of this ransomware is medium [35].
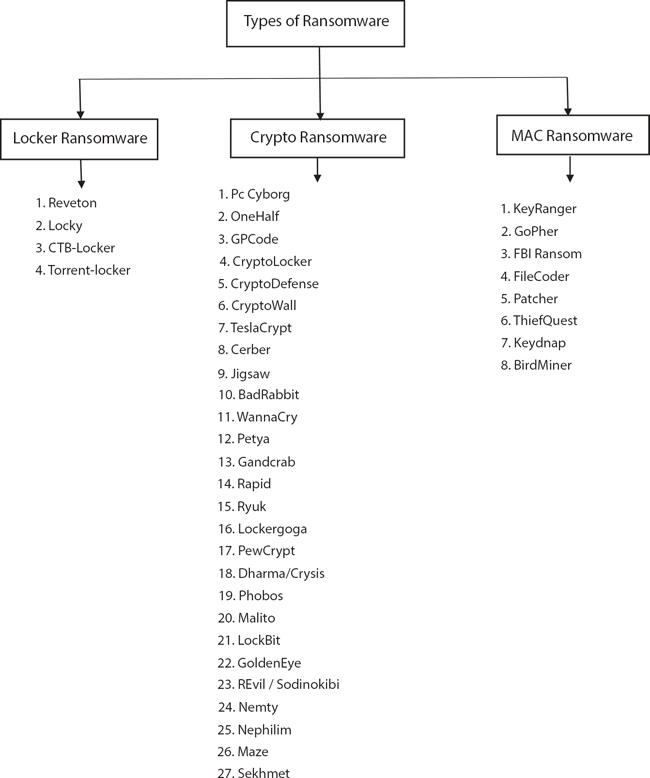
Figure 16.2 Types of ransomwares.
16.2.1.1 Reveton Ransomware
This is a locker ransomware. It displays the fake message on the screen showing that the system is locked due to an illegal activity happening on the system, once the system gets infected. It also displays a ransom note on the locked screen. This ransomware is spread by Drive-by downloads, compromised webserver. Along with the ransom amount, this ransomware also steals some user credentials. The ransom amount is to be paid within 48 hours from the attack.
16.2.1.2 Locky Ransomware
Locky ransomware can be spread through malicious text documents using the macros. Once the user has opened such kind of document it is not in a readable format, so the popup is displayed in the document which contains the enable macro-option. If the user clicks the option, the system gets infected [24].
16.2.1.3 CTB Locker Ransomware
CTB locker stands for “Curve-Tor-Bitcoin-Locker”. It uses public key cryptography based on elliptic curves. It uses cryptographically secured keys for encryption. It uses elliptic curve cryptography (ECC). It is more beneficial to use ECC over RSA. To generate the public keys AES algorithm is used and to decrypt the files ECC public key is used.
16.2.1.4 TorrentLocker Ransomware
TorrentLocker is spread through infected spam emails. And to make it more interesting, with these infected emails, the creators of TorrentLocker specifically target countries rather than as many countries around the world as possible. The popular technique, often referred to as “process hollowing,” is used by TorrentLocker, where a legitimate Windows system process is started in a suspended state, malicious code is inserted into the process, the main thread’s ThreadContext structure is modified to point to the malicious code and the process is resumed [41]. TorrentLocker communicates with its command and control server via HTTPS POST requests. The ransom request will be shown after all the available files on the device have been encrypted. The data that was initially downloaded when TorrentLocker first contacted its command and control server is the text of the ransom demand note [42].
16.2.2 Crypto Ransomware
Crypto ransomware finds valuable data on the computer, encrypts it and locks the victim’s access [23]. This type of ransomware is very severe. Crypto ransomware is the most dangerous type of ransomware; it uses advance encryption and cryptography techniques which makes it more difficult to detect [35]. Crypto Ransomware looks for weaknesses and flaws in the computer system, searching out data that has not been backed up. Crypto Ransomware typically does not lock the entire computer. Victims can be able to access the files which are not encrypted.
16.2.2.1 PC Cyborg Ransomware
PC Cyborg Ransomware is distributed via a disk known as the Introductory Diskette AIDS data. This ransomware substitutes autoexec for this. The Bat file was used to count the number of reboots in the system. This hides all folders until it hits the count of 90 and then encrypts the name of all the files that are on the drive files. The victim is asked to pay the ransom by sending it via a post office box in Panama once the files are encrypted. There is more than one version of AIDS, but after AIDS is installed, another version does not wait until 90 boots; instead it operates once the first boot.
16.2.2.2 OneHalf Ransomware
OneHalf is a destructive virus. This is the incremental type of ransomware based on cryptology concepts. Whenever the infected system gets started, it encrypts the two more files which are not encrypted yet. It is hard to remove this attack as it has a unique payload. You cannot recover your system even if you have a backup of the data.
16.2.2.3 GPCode Ransomware
GPCode ransomware uses symmetric key for encryption, through which the user can easily recover the encrypted data. The RSA algorithm is used to generate the public keys. Once the GPCode ransomware gets installed on the system, the user can no longer access anything from the MyDocuments space. Once the ransom amount is paid, the victim can get the data back.
16.2.2.4 CryptoLocker Ransomware
If the CryptoLocker is mounted on the victim’s computer, it encrypts all the files stored on the desktop and some network files and waits for the ransom amount to be paid by the consumer [30]. The ransom note is shown to the user if the user attempts to open the infected file. To generate the encryption keys, it uses the RSA 2048 algorithm [33]. The decryption process is written using .html or .txt files. This ransomware uses stronger encryption methods that only offer access to those users that have the secret key. Encryption can also allow contact with the c2 server stronger [31].
16.2.2.5 CryptoDefense Ransomware
CryptoDefense ransomware uses RSA 2048 technique for key generation. Unlike CryptoLocker instead of generating keys in command-and-control server, it generates the keys using Windows CryptoAPI. The normal user can think this a bit difficult, but a technical user can easily bypass this tool to decrypt the data.
16.2.2.6 CryptoWall Ransomware
CryptoWall is the improved version of CryptoDefense ransomware. It is generally spreading through spam mails. CryptoWall spreads extremely fast, and it is the easiest type of ransomware which comes with low costs. It also deletes the shadow volume copies of the files alongside the encryption files.
16.2.2.7 TeslaCrypt Ransomware
TeslaCrypt does not encrypt files that are larger than 268 MB. The encryption of the files is done using Advanced Encryption Standard (AES) algorithm [14]. The Tesla Crypt C2 servers and ransom payment server work as hidden servers which provide anonymity. Communication between a compromised system and the c2 infrastructure is encrypted by the Secure Socket Layer protocol [24].
16.2.2.8 Cerber Ransomware
Cerber is a Ransomware-as-a-service model. Cerber ransomware takes control of your desktop screen displaying the ransom note. The Key backup is one of the best options to recover from the Cerber Ransomware [9, 28].
16.2.2.9 Jigsaw Ransomware
Jigsaw is an encryption-based ransomware. Jigsaw is a type of ransomware which tries to delete the files if the user does not pay the ransom amount within one hour.
16.2.2.10 Bad Rabbit Ransomware
Bad Rabbit ransomware spreads through drive-by-downloads. The target of this ransomware is to visit the legitimate website and attach the malicious software executable into the website. This ransomware is installed with the user interactions [18].
16.2.2.11 WannaCry Ransomware
WannaCry is a type of Crypto Ransomware. It works in two ways, either by encrypting files or locking your data. It adds WCRY extension to the file. The ransom note indicates that if the ransom is not paid, then it gets doubled after three days. It also claims that if the ransom is not paid within 7 days, then the encrypted files will be deleted [3].
16.2.2.12 Petya Ransomware
Petya is a type of encrypting malware. Petya Ransomware spreads through EternalBlue vulnerability in Microsoft Windows. It spreads more easily than WannaCry. It uses the Master Book Record of the windows system to encrypt the data.
16.2.2.13 Gandcrab Ransomware
GandCrab Ransomware uses ransomware-as-a-service model. It encrypts only one document at a time. The encryption algorithms such as RSA, AES and RC4 are used to generate the encryption keys. Gandcrab ransomware generates the public key by communicating to the command-and-control server [51]. It also deletes the copies of the encrypted files’ shadow amount. The traffic is encrypted with a hard-coded RC4 key. Once they get hold of this key, and if they also have everything, they need to decrypt the user’s files. Unfortunately, it is very difficult if the average user does not keep traffic logs [14].
16.2.2.14 Rapid Ransomware
Rapid ransomware stays active on the system, once the system is infected. It encrypts each newly generated file on the system. This is done by setting auto-run. It is better if the victim shuts down the system as early as possible. Once encryption is done, it opens a text file which is a ransom note saved as a recovery.txt. Its data recovery rate is extremely high, once the ransom is paid to the attacker.
16.2.2.15 Ryuk Ransomware
Once the attacker finds a suitable system, two files with two keys such as RSA public key and Hardcoded key are uploaded within the subfolder. Here the Ryuk encryption starts. Ryuk Ransomware does not encrypt the files with .dll or .exe extensions. Its encryption is based on AES-256 technique [8].
16.2.2.16 Lockergoga Ransomware
Once Lockergoga Ransomware is installed on the system, it changes the system’s password. The currently logged in users on the systems are forcefully logged off from the system by Lockergoga Ransomware. It leaves the ransom note on the desktop once the encryption is done. Lockergoga ransomware also tries to change the system’s Wi-Fi password [26].
16.2.2.17 PewCrypt Ransomware
In PewCrypt Ransomware, the data is encrypted through the AES-256 algorithm. The newly generated decryption key is also generated using RSA-2048 technique. To decrypt the data, the victim must have these two keys. Sometimes, these keys are hidden from the victim by storing it on the remote server [19].
16.2.2.18 Dhrama/Crysis Ransomware
Dharma ransomware follows Ransomware-as-a-service Model. This is one of the dangerous ransomwares based on cryptology. Asymmetric Cryptography technique is used to generate the keys used for encryption. Dharma ransomware can also spread through the Remote Network. This ransomware is easily available to everyone [49].
16.2.2.19 Phobos Ransomware
Once installed on the system, it generates an application folder on the specific location where the executable is installed. Phobos Ransomware generates a unique ID and email for victim. AES cryptography is used for the encryption by phobos ransomware. To display the ransom note on the infected machine, it generates the .html file [6].
16.2.2.20 Malito Ransomware
Malito ransomware typically spreads through Word or Excel files. It uses PowerShell Dropper to spread the ransomware. Once the files are encrypted, Malito ransomware renames it with developer’s email address. Along with this, it also adds file extensions which is a victim’s Unique ID generated by the attacker [20].
16.2.2.21 LockBit Ransomware
LockBit exploits SMB, ARP tables, and PowerShell to spread the malware through a compromised network. To retrieve their data, an anonymous ransomware survivor refused to back up his data and was forced to pay the ransom. LockBit files encrypts the file and renames it with .abcd extension [21].
16.2.2.22 GoldenEye Ransomware
GoldenEye is a mixture of ransomware-type viruses like Petya and MISCHA. GoldenEye is spread using a spam email message, just as with Petya and MISCHA [50].
16.2.2.23 REvil or Sodinokibi Ransomware
REvil distributes ransomware via exploit kits, scan-and-exploit techniques, RDP servers, and backdoored software installers. Ransomware is reportedly hitting organizations and demanding cryptocurrency ransom to return the decryption key to unlock infected files. To encrypt sensitive data, it is important to know how ransomware attacks and invades information systems.
16.2.2.24 Nemty Ransomware
Nemty runs on a RaaS model (Ransomware-as-a-Service). Nemty is a new variant of ransomware which adds .EMPTY extension to the encrypted file names. Nemty is a ransomware that detects and eliminates shadow copies of files until they are encrypted, making it harder for users to recover files without paying the ransom.
16.2.2.25 Nephilim Ransomware
Nephilim adds a unique extension to all encrypted files on the network. The extension is different per victim. At present, vulnerable RDP services are the primary method of delivery. AES-128 and RSA-2048 algorithms are used for encryption. The only way to recover the data is to decrypt it with the tools that can only be bought from the developers of NEPHILM [52].
16.2.2.26 Maze Ransomware
Not only does Maze ransomware demand payment for a decryptor, but it exfiltrates victim data and threatens to publicly leak it if the target does not pay up. The user infected with this ransomware cannot access any files or data until a ransom is paid [53]. It adds random extensions to the encrypted files. This ransomware creates a “DECRYPT-FILES.html” file by changing the desktop wallpaper along with the ransom message. The wallpaper notes that Maze encrypts files with RSA-2048 and ChaCha algorithms, and buying a decryption tool is the only way to recover locked/encrypted files [35].
16.2.2.27 Sekhmet Ransomware
Sekhmet Ransomware operates by encrypting data and demanding ransom payments for decryption. Random extensions are added to the file names after successful encryption. Note that these extensions do not simply vary from infection to infection; on the same computer, they may be different. As a result, victims may find that some of their files have one extension, while others are different. A ransom message (“RECOVER-FILES.txt”) is dropped into any compromised folder after the encryption process is complete [36].
16.2.3 MAC Ransomware
These are the ransomwares that infect only the MAC Operating System. These are rare cases of ransomwares, but if found it becomes more dangerous [5].
16.2.3.1 KeRanger Ransomware
It is the first ransomware targeted on the MAC OS. This ransomware can spread through infected applications. It the malicious application is installed on the system containing KeRanger binded into it, along with the application, it also gets installed on the system. Once installed, it waits for three days before starting to encrypt files. KeRanger ransomware communicates to the Command-and-control server before it starts encrypting. It also tries to encrypt Time Machine Backup files, so that the victim can never get their data back from backup [5].
16.2.3.2 Go Pher Ransomware
Go Pher ransomware is based on Crypto family. Go Pher ransomware uses two asymmetric keys for encryption, so it is more difficult to detect [4].
16.2.3.3 FBI Ransom Ransomware
The ransomware was called FBI Ransomware because it uses the FBI’s name. OS X Mac users are threatened by the latest ransomware versions. This new version is not malware; it appears as a webpage that loads multiple iframes (browser windows) using JavaScript and allows victims to close each iframe. Before understanding that all iframes must be locked, cyber criminals expect victims will pay the requested ransom. The ransomware is pushed to victims’ computers when they browse common websites, specifically when they query popular search terms. The victim’s computer shows a pop-up alert that appears to be from the FBI until the web browser is exploited. In order to make the alert look more legitimate, cyber criminals use ‘FBI.gov’ inside the URL [43].
16.2.3.4 File Coder
FileCoder Trojans are Trojan infections on the victim’s machine that encrypt the content. FileCoder ransomwares spreads through drive-by-download or spam emails. FileCoder infection is a form of ransomware. Essentially, in return for decrypting software, they take the victim’s computer hostage, encrypt the victim’s files and then demand the payment of a ransom.
16.2.3.5 Patcher
Patcher is downloaded via Bit-torrent. The presence on computers of this infection begins with a torrent file that downloads a .zip folder of any software [44]. The user open this file to launch a software crack, but they do not find the software there. Instead, the user is starting the ransomware infection [45].
16.2.3.6 ThiefQuest Ransomware
Not only does this ransomware encrypt the data on the device, it also installs a keylogger, remote shell and steals wallet-related cryptocurrency files from infected hosts. Even after the victim’s ransom has been paid, the attacker continues to have access to the computer and can exfiltrate files and keystrokes. This ransomware is distributed through legitimate applications on torrent websites such as Little Snitch, Ableton, and Mixed in Key. After the installer is launched, ThiefQuest will start encrypting the files by adding a BEBABEDD marker at the end [46].
16.2.3.7 Keydnap Ransomware
This malware installs via a new twist on an old theme. The “dropper” (the program that installs the malware) comes in the form of a harmless document. A lot of different forms have been discovered, masquerading as Microsoft Word files, JPEG images and plain text files. Keydnap ransomware uses a new trick, i.e., it adds a blank space at the end of file extension name, e.g., “logo.jpg” will look like “logo.jpg”. Since the file is really a Mach-O executable file, it will run in the Terminal by double-clicking it instead of opening a JPEG file as the user would expect [47].
16.2.3.8 Bird Miner Ransomware
Bird Miner is the name of a malicious software that mines cryptocurrency via emulation using computer resources. Research shows that two miners are running for this, which means that they consume a large amount of resources. Bird Miner is believed to be spread by cyber criminals using an installer for a hacked (pirated) edition of ValhallaVintageVerb program [48].
16.3 Ransomware Life Cycle
There are various phases of ransomware life cycle (Figure 16.3). First, the ransomware is distributed through various ways such as malicious links, spam emails, etc. Downloading those malicious attachments will infect the system [29]. Once infected, the encryption of the system’s file process starts. Once the files are encrypted, the ransom note is displayed to the victim which demands ransom [3].

Figure 16.3 Ransomware life cycle.
Ransomware goes through the following six-stage life cycle [15]:
- 1. Distribution: In the first stage, the ransomware is distributed and installed on the victim’s system. It includes opening spam e-mail attachments, downloading malicious software, etc.
- 2. Infection: Once the .exe file is downloaded on the user’s system, it starts infecting the system.
- 3. Staging: It is the phase where the ransomware performs various operations like moving itself to a new folder and then starts operating; it also looks for proxy settings, user accessibility. It also deletes shadow copies of its original files from the system using various commands.
- 4. Scanning: Now the ransomware has set itself up. The next step is to scan the local directories and drives to search for the files with some specific extensions. Some ransomwares also look for cloud storage repositories such as Box, Dropbox, etc.
- 5. Encryption: In this phase, local files or network files are encrypted by the ransomware. Upon each file opening, the ransom note is displayed to the user. Some ransomwares display the note on the screen by which the user cannot access the system; all the user can do is follow the steps given in the note and pay the ransom.
- 6. Ransom Demand: Once the encryption is completed, the ransomware displays the ransom note on the screen. The ransom note contains the instructions about the payment. After the payment is completed, the user is provided with the link through which the user can download the decryption key.
16.4 Detection Strategies
16.4.1 UNEVIL
A Novel dynamic analysis system, specially designed for the detection of ransomware. This technique creates an artificial user environment automatically and detects when ransomware interacts with user systems. At the same time, it tracks the changes made to the systems desktop. This technique can detect previously identified ransomwares [11].
16.4.2 Detecting File Lockers
There are various techniques through which file lockers are detected such as Generating Artificial User Environments, File System activity Monitor, I/O Data Buffer Entropy, and Constructing Access Patterns. All these techniques are used to detect the file lockers ransomwares [11].
- i. Generating Artificial User Environments: The user environment is made up of various contents such as digital images, audio files, etc. There are some parameters which are considered for generating user environments such as valid content, File Paths and Time attributes. In valid content, generated files become more difficult for the attacker to detect by adding valid headers and content using standard libraries such as python-docx, OpenSSL, etc. In File Paths, the path length of the generated user file is generated randomly. In time attribute, files are generated with different creation, modification, and access times.
16.4.3 Detecting Screen Lockers
The displayed ransom note is automatically detected by the attackers by monitoring the desktop of the victim’s machine [11].
16.4.4 Connection-Monitor and Connection-Breaker Approach
This approach can detect all the High Survivable Ransomwares before the encryption process starts. In this approach, if any application wants to connect CC, then it is only allowed if it has a Verifies Required Connection Address (VRCA). If the application with no VRCA tries to connect to CC, then it is detected as suspicious activity and all other users can report this suspicious connection address to experts. In addition, the concept of augmented code signing certificate is added, which will calculate the hash of the executables to check its integrity [1].
16.4.5 Ransomware Detection by Mining API Call Usage
Once the executable is received on the system, this technique can identify it whether it is a ransomware or a malicious software which is nonransomware. This method is executed in three steps [32]:
- I. Feature Extraction and Analysis: By performing detail analysis of the executables, features are extracted which are used in the next classification phase.
- II. Dealing with class imbalance: When there are more examples of one target than another, then class imbalance occurs. This problem is solved in this API call mining by using smote technique.
- III. Classification: The data extracted in the feature extraction phase are classified in this phase using some techniques like decision tree classifier. The classified data will then be labelled as Ransomware or Benign application. The application is accessible to the user once the classification of the application is done.
16.4.6 A New Static-Based Framework for Ransomware Detection
This framework is used to detect the various features from files such as API functions rules (A), keywords (K), cryptography signatures (C) and extensions (E). If the match is found with the newly extracted features, then some logical operations are performed on those rules. The logical operations output is classified within the various confidence levels such as “Critical”, “High”, “Moderate” or “Low” [16].
- I. Critical alert: This alert occurs when the rules for API functions (A), Keywords (K) and Extensions (E) match. The critical alert shows that it is highly likely that the application is a ransomware.
- II. High alert: There are various cases of high alert:
API functions (A) and laws for Keywords (K).
Laws for API functions (A) and extensions (E).
The laws of Cryptography (C) and Keywords (K). - III. Moderate alert: If the roles of Cryptography (C) and API (A) are balanced, then the application could be a ransomware.
- IV. Low alert: In this alert, samples are matched with the extensions (E) rules.
16.4.7 White List-Based Ransomware Real-Time Detection Prevention (WRDP)
It works on three principles: live detection of ransomware operations, offline detection of the ransomware and detecting the new ransomwares if they are not yet analyzed by trusted parties [22]. Three system components, File Use Management Manager (FUMM), File Access Control Manager (FACM) and Access Control DB, are managed by WRDP. The I/O manager sends the request packet to the File System Driver until the user attempts to open or edit the file (FSD). FSD asks the cache manager to grant the user an operation if the file is present in the cache. If the file is not present in the cache, it is checked in the virtual memory area and then it is displayed to the user [12].
16.5 Analysis of Ransomware
There are two ways to analyze ransomware (Figure 16.4), i.e., Static Analysis and Dynamic Analysis. To identify the depth of the attack analysis is done [13].
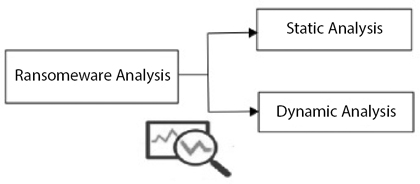
Figure 16.4 Ransomware analysis.
16.5.1 Static Analysis
Static analysis is the code analysis without running an application. Static analysis is performed on the execution code. The Portable Executable (PE) file is read without its execution. Header analysis is performed on the code to identify the static properties of ransomware. On the analysis of the code of the application, it can identify whether the file is malicious or not. The main aim behind static analysis is to check whether there are any windows executables present [25]. Extracting some strings like IP address, Error messages, etc., will provide some more information about the code. Static analysis is like reading a map for directions on where to go. Following this map will let the victim capture notes on some part which might become useful for future analysis or detecting the ransomwares [37].
16.5.2 Dynamic Analysis
Dynamic analysis is useful to extract the behavior of ransomware for detection. In Dynamic analysis, you can execute the code and trace what it does and how it affects the system. The method of evaluating a code by executing it and watching its behavior is dynamic analysis [25]. These behaviors can be detected at different levels, from the lowest possible level (the binary code itself) to the entire system (e.g., changes made to the registry or file system). The aim of dynamic analysis is to expose the executable’s malicious behavior while it is running, without sacrificing the analysis platform’s protection. By putting the system on high risk, the behavior of real malware is analyzed [34]. It is recommended to execute the malware on Virtual Machines which are not connected to the internet, to avoid the risk of infection. So, it will become more beneficial if you execute malware on virtual machines or dedicated systems which are not connected to the internet [27, 10].
16.6 Prevention Strategies
16.6.1 Access Control
This technique uses “Anti-Botics” technique which is an authentication-based access control technique. “Anti-Botics” technique has three components, i.e., Policy Enforcement Driver, Policy Specification Interface and Challenge-Response Generator. The Policy Enforcement Driver performs different types of file modifications. For file modifications a security is provided using CAPTCHA. The next component is the Policy Specification Interface, which configures the system policies through administrators. The third component is the Challenge-Response Generator which controls the challenges generated. It detects the malicious content using CAPTCHA, GUI [22].
16.6.2 Recovery After Infection
Once the system is infected, it recovers the system through different ways. For example, it can secure email by consistently applying security patches because emails are a major source of ransomware [22].
16.6.3 Trapping Attacker
R-Locker technique is used to detect crypto ransomware actions. Trapping attacker technique automatically launches the steps which will detect the ransomware. However, the drawback of using this step is that it considers only some part of the file system [22].
16.7 Ransomware Traits Analysis
Many variants of ransomware have been discovered in the last few decades. Various traits are identified, and ransomwares are analyzed against them. Table 16.1 shows a sample snippet which includes the ransomware variants, their identification date, and various traits [7]. Various traits considered are:
Table 16.1 Ransomware traits.
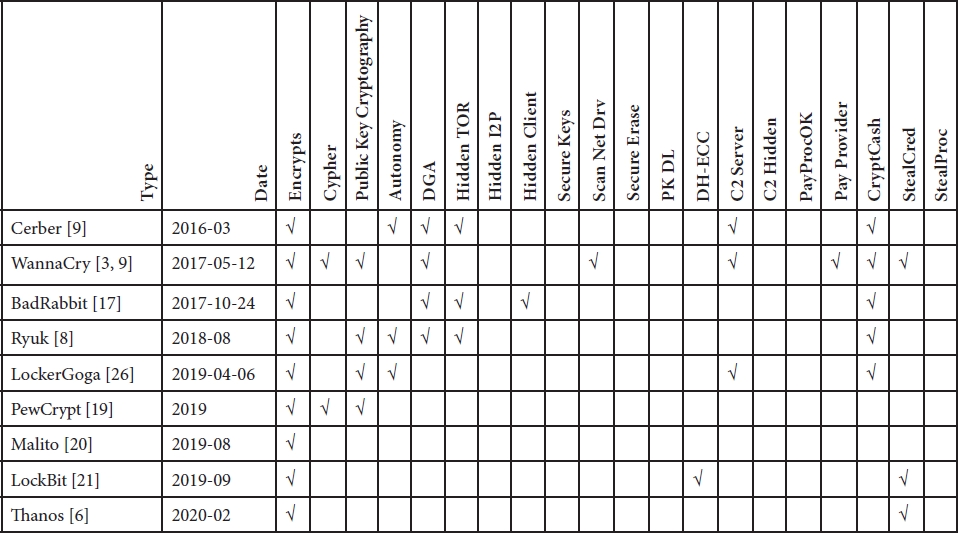
√: fully implemented
- • Encryption: Instead of locking the file for access, user file contents are encrypted.
The encryption key with symmetric algorithm is denoted by C = Ek (M) and M = DkC, where M denotes message (plaintext), C denotes cipher text, E is encryption, D is decryption, and k is a shared key [38, 39].
The encryption key with asymmetric algorithm is denoted by C = Epu.k (M) and M = Dpr.k (C), where pr.k and pu.k are private and public keys respectively [54]. - • Strong Cipher: It indicates use of secure and well implemented cipher.
E (x) = (ax + b) mod m
Where modulus m: size of the alphabet,
a and b: key of the cipher,
a must be chosen such that a and m are co-prime [54]. - • Public key cryptography: Allows ransomware to encrypt contains using public key. The attacker contains the main hold of the key and the data is encrypted using this key only.
- • Let k ∈ N be a security parameter. An encryption scheme is defined by the following spaces (all depending on the security parameter k) and algorithms.
- • Mk is the space of all possible message;
- • PKk is the space of all possible public keys;
- • SKk is the space of all possible private keys;
- • Ck is the space of all possible ciphertexts;
- • KeyGen a randomized algorithm that takes the security parameter k, runs in expected polynomial-time (i.e., 0(ke) bit operations for some constant c ∈ N) and outputs a public key pk ∈ PKk and a private key sk ∈ SKk;
- • Encrypt a randomized algorithm that takes as input m ∈ Mk and pk, runs in expected polynomial-time (i.e., 0(ke) bit operations for some constant c ∈ N and outputs a cipher text c ∈ Ck;
- • Decrypt an algorithm that takes c ∈ Ck and sk, runs in polynomial-time and outputs either m ∈ Mk or the invalid cipher text.
- • It is required that Decrypt(Encrypt(m, pk),sk) = m
- • If (pk, sk) is a matching key pair. Typically we require that the fastest known attack on the system requires at least 2k bit operations [36, 40, 54].
- • Autonomy: Ransomware starts destruction autonomously without contacting any command-and-control server. The functions of ransomwares which require to communicate with command-and-control server can be blocked.
- • DGA: Domain generation algorithms makes the host name of the command-and-control servers unpredictable and it is only known to the attackers. Domain Generation Algorithms [DGA] make it more difficult to take down the C2 server. With the DGA, the host name of the server is unpredictable, known only to the attacker.
- • Hidden TOR: Attackers make use of TOR to anonymize and secure their servers and themselves. It provides high levels of security and anonymity to attackers and their servers.
- • Hidden I2P: Attacker make use of Invisible Internet Project network for secret communication.
- • HiddenClient: Built-in TOR/I2P is the anonymous built-in client. It makes the detection process harder.
- • Secure Keys: The keys are cryptographically secured. Different keys with longer length are utilized to make the cracking the encrypted content impossible.
- • ScanNetDrv: It also scans all the network drives. All network drives including backups are scanned and encrypted.
- • Secure Erase: It stands for securely erases encryption. Files encrypted by users are deleted. Also, files can be recovered from shadow copies using recovery software.
- • PK DL: It stands for Public Key Download. Victims may not have access to the hidden key, rendering it difficult to decrypt.
- • DH-ECC: Diffie-Hellman Elliptic Curve Cryptography algorithm is used to generate keys. Use of this algorithm to generate fast and secure public keys.
- • C2 Server: Command and control server to effectively communicate with victim’s machine.
- • C2 Hidden: Making use of anonymous network to communicate with command-and-control server.
- • PayProcOK: Good Payment Protocols are used for payments. So, no fake payments can be done.
- • Pay Provider: It uses semi-anonymous payment authority. The attackers can receive their cash without leaving a “paper trail” by using secure anonymous payments.
- • CryptCash: Uses cryptocurrencies like Bitcoin to make secure and erasable transactions.
- • StealCred: Steals other personal information in addition to ransom requests, such as login details and banking credentials.
- • StealProc: It Uses the infected machine to perform computing or network operations beyond the demand for ransom. The victimized computer is used to execute malicious activities in addition to ransom demand.
16.8 Research Directions
Ransomware is a malicious software that infects the system once installed on it. Once ransomware is installed, it is spread through different ways such as spam emails. In GandCrab ransomware, if the user analyzes the malware in depth, the RC4 algorithm is used to generate the keys. Traffic is encrypted using a hardcoded RC4 key. Once you get hold of this key, and if you also have traffic logs to record the C&C server check-in, you have everything you need to decrypt your files. Unfortunately, it’s very difficult if the average user doesn’t keep traffic logs. Basic static analysis can confirm whether a file is malicious, provide information about its functionality, and sometimes provide information that will allow you to produce simple network signatures.
16.9 Conclusion
Ransomware is the most dangerous type of attack. It has become a part of our daily lives now. So, one should pursue certain competent methods of using the internet in order to deal with it. There are different forms of ransomware and there is a way of spreading each ransomware. There are several ways to deal with it if the ransomware is found on the device. If the user has sufficient technical expertise, then it is possible to find the decryption key by examining some ransomware files. A comprehensive survey of different ransomware techniques is seen in this analysis. The ransomwares are classified into three main categories, Locker ransomware, Crypto ransomware, and MAC ransomware. To define the parameters present and to know how each function is implemented in the specific ransomware, comparative analysis is performed on the ransomware variants.
References
1. Ahmadian, M. M., Shahriari, H. R., & Ghaffarian, S. M., Connection-monitor & connection-breaker: A novel approach for prevention and detection of high survivable ransomwares. In 2015 12th International Iranian Society of Cryptology Conference on Information Security and Cryptology (ISCISC), 2015.
2. Aldaraani, N., & Begum, Z., Understanding the impact of Ransomware: A Survey on its Evolution, Mitigation and Prevention Techniques. In 2018 21st Saudi Computer Society National Computer Conference (NCC) (pp. 1-5). IEEE, 2018.
3. BROADCOM, “Threat Intelligence”, https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/wannacry-ransomware-attack, 2020.
4. Check Point Research, “macOS Malware Encyclopedia”, https://macos.checkpoint.com/families/Gopher/, 2020.
5. Datarecovery.com, “KeRanger Ransomware Infection and Decryption Services”, https://datarecovery.com/rd/keranger-ransomware-infection-decryption-services/, 2020.
6. Falcone Robert, Paloalto, https://unit42.paloaltonetworks.com/thanosransomware/, 2020.
7. Hampton, N., & Baig, Z. A., Ransomware: Emergence of the cyber-extortion menace, 2015.
8. Hanel Alexander, Crowdstrike.com, https://www.crowdstrike.com/blog/big-gamehunting-with-ryuk-another-lucrative-targeted-ransomware/, 2019.
9. Hull, G., John, H., & Arief, B., Ransomware deployment methods and analysis: views from a predictive model and human responses. Crime Science, 8(1), 2, 2019.
10. Jung, S., & Won, Y., Ransomware detection method based on context-aware entropy analysis. Soft Computing, 22(20), 6731-6740, 2018.
11. Kharaz, A., Arshad, S., Mulliner, C., Robertson, W., & Kirda, E., {UNVEIL}: A largescale, automated approach to detecting ransomware, 25th {USENIX} Security Symposium ({USENIX} Security 16), 2020.
12. Kim, D. Y., Choi, G. Y., & Lee, J. H., White list-based ransomware real-time detection and prevention for user device protection, IEEE International Conference on Consumer Electronics (ICCE), 2018.
13. Lokuketagoda, B., Weerakoon, M. P., Kuruppu, U. M., Senarathne, A. N., & Abeywardena, K. Y., R-killer: an email based ransomware protection tool, 2018 13th International Conference on Computer Science & Education (ICCSE), IEEE, 2018.
14. Malwarebytes, “GandCrab” https://www.malwarebytes.com/gandcrab/#:~:text=First%20observed%20in%20January%20of,with%20PCs%20running%20Microsoft%20Windows.&text=Little%20else%20is%20known%20about%20the%20GandCrab%20crew, 2020.
15. Mechdyne Enabling Discovery, https://www.mechdyne.com/it-services/lifecycle-of-aransomware-attack-part-1/, 2020.
16. Medhat, M., Gaber, S., & Abdelbaki, N, A New Static-Based Framework for Ransomware Detection, 16th Intl Conf on Dependable, Autonomic and Secure Computing, 16th Intl Conf on Pervasive Intelligence and Computing, 4th Intl Conf on Big Data Intelligence and Computing and Cyber Science and Technology Congress (DASC/PiCom/DataCom/CyberSciTech), IEEE, 2018.
17. Orkhan Namedeo, Fedor, Anton, https://securelist.com/bad-rabbit-ransomware/82851/, 2017.
18. Lena Fucks, https://www.proofpoint.com/us/glossary/bad-rabbit, 2019.
19. Meskauskas Tomas, PCrisk, https://www.pcrisk.com/removal-guides/14559-pewcryptransomware, 2020.
20. Meskauskas Tomas, PCrisk, https://www.pcrisk.com/removal-guides/15915-mailtoransomware, 2020.
21. Meskauskas Tomas, PCrisk, https://www.pcrisk.com/removal-guides/16476lockbitransomware, 2020.
22. Moore, C., Detecting ransomware with honeypot techniques, 2016 Cybersecurity and Cyberforensics Conference (CCC), IEEE, 2016.
23. Morato, D., Berrueta, E., Magaña, E., & Izal, M., Ransomware early detection by the analysis of file sharing traffic. Journal of Network and Computer Applications, 124, 14-32, 2018.
24. Mukesh, S. D., An Analysis Technique to Detect Ransomware Threat, 2018 International Conference on Computer Communication and Informatics (ICCCI) IEEE, 2018.
25. Netto, D. F., Shony, K. M., & Lalson, E. R., An integrated approach for detecting ransomware using static and dynamic analysis, 2018 International CET Conference on Control, Communication, and Computing (IC4) IEEE, 2018.
26. Neumann Robert, Natvig Kurt, “Forcepoint”, https://www.forcepoint.com/blog/xlabs/lockergoga-ransomware-how-it-works, 2019.
27. ORI OR-MEIR, NIR NISSIM, YUVAL ELOVICI, LIOR ROKACH, “Dynamic Malware Analysis in the Modern Era- A State of the Art Survey” https://dl.acm.org/doi/fullHtml/10.1145/3329786, Palmer Danny, ZDNet.com, https://www.zdnet.com/article/bad-rabbit-ten-things-youneed-to-know-about-the-latest-ransomware-outbreak/, 2019.
28. Petters Jeff, https://www.varonis.com/blog/cerber-ransomware/, VARONIS,2020.
29. Richardson, R., & North, M. M., Ransomware: Evolution, mitigation and prevention. International Management Review, 13(1), 10, 2017.
30. Saxena, S., & Soni, H. K., Strategies for ransomware removal and prevention, 2018 Fourth International Conference on Advances in Electrical, Electronics, Information, Communication and Bio-Informatics (AEEICB) IEEE, 2018.
31. Sheen, S., & Yadav, A., Ransomware detection by mining API call usage, International Conference on Advances in Computing, Communications and Informatics (ICACCI) IEEE, 2018.
32. Sittig, D. F., & Singh, H., A socio-technical approach to preventing, mitigating, and recovering from ransomware attacks. Applied clinical informatics, 7(2), 624, 2016.
33. Skynet Corp Team, “Malware analysis”, https://skynetcorp.ae/cyber-security/gandcrab-504ransomware--static-and-dynamic-malware-analysis, 2020.
34. Sultan, H., Khalique, A., Alam, S. I., & Tanweer, S., A SURVEY ON RANSOMEWARE: EVOLUTION, GROWTH, AND IMPACT, International Journal of Advanced Research in Computer Science, 9(2), 2018.
35. PCRisk, https://www.pcrisk.com/removal-guides/17463-nephilim-ransomware, 2020.
36. PCRisk, https://www.pcrisk.com/removal-guides/17443-sekhmet-ransomware, 2020.
37. Theta432, https://www.theta432.com/post/malware-analysis-part-1-static-analysis, 2020.
38. https://www.math.nyu.edu/faculty/hausner/cryptography.pdf, 2020.
39. H. Lee Kwang, Basic Encryption and decryption, https://www.apprendre-en-ligne.net/crypto/bibliotheque/PDF/Kwang.pdf, 2020.
40. https://www.math.auckland.ac.nz/~sgal018/crypto-book/main.pdf, 2020.
41. Knowbe4, https://www.knowbe4.com/torrentlocker, 2021.
42. SophosNews, https://news.sophos.com/en-us/2015/12/23/the-current-state-of-ransomware-torrentlocker/, 2015.
43. Federal Bureau of Investigation, https://www.ic3.gov/Media/PDF/Y2013/PSA130718_2.pdf, 2013.
44. 411-spyware.com, https://www.411-spyware.com/remove-patcher-ransomware, 2021.
46. Certin, https://www.cyberswachhtakendra.gov.in/alerts/ThiefQuestRansomware.html, 2020.
47. MalwarebytesLABS, https://blog.malwarebytes.com/cybercrime/2016/07/mac-malware-osx-keydnap-steals-keychain/, 2016.
48. PCRisk, https://www.pcrisk.com/removal-guides/19029-bird-miner-malware-mac, 2020.
49. MalwarebytesLABS, https://blog.malwarebytes.com/threat-analysis/2019/05/threat-spotlight-crysis-aka-dharma-ransomware-causing-a-crisis-for-businesses/, 2019.
50. MalwarebytesLABS, https://blog.malwarebytes.com/threat-analysis/2016/12/goldeneye-ransomware-the-petyamischa-combo-rebranded/, 2017.
51. Infoblox, https://insights.infoblox.com/threat-intelligence-reports/threatintelligence--60, 2019.
52. Coveware, https://www.coveware.com/nephilim-ransomware, 2021.
53. PCRisk, https://www.pcrisk.com/removal-guides/15133-maze-ransomware#:~:text=People%20who%20have%20computers%20infected,jpg%22%20might%20become%20%221, 2020.
54. Behrouz A., Forouzan and Mukhopadhay D., Cryptography and Network Security, McGraw Hill Education Pvt. Ltd., 2007.
