1
A Comprehensive Study of Security Issues and Research Challenges in Different Layers of Service-Oriented IoT Architecture
Ankur O. Bang1*, Udai Pratap Rao1 and Amit A. Bhusari2
1Computer Science and Engineering Department, Sardar Vallabhbhai National Institute of Technology, (NIT) Surat, Gujarat, India
2MCA Department, Trinity Academy of Engineering, Pune, Maharashtra, India
*Corresponding author: [email protected]
Abstract
Service-Oriented Architecture (SOA) has proven its applicability on technologies like the Internet of Things (IoT). The major benefits of SOA architecture are flexibility, better information flow, re-usability and scalability, which make it worthy to use in IoT. This concept, when adopted with generic IoT architecture, creates layers that ask and deliver service to each other. Communication protocols play an important part here, but security always remains a major concern while dealing with a huge number of heterogeneous components of IoT. This chapter provides a survey of enabling protocols, the taxonomy of layer-wise attacks and security issues of the service-oriented IoT architecture. The chapter also describes major vulnerabilities related to the adaption of SOA into IoT. We feel that this chapter can give directions to researchers for enhancing security and privacy in IoT.
Keywords: Internet of Things, service-oriented architecture, protocols, security, privacy, attacks vulnerabilities
1.1 Introduction and Related Work
Progression in technology like the Internet of Things (IoT) leads to use of intelligent devices for improvement of people’s lifestyles and optimizing the effectiveness of resources [1]. IoT is a technology that has evolved from technologies that already exist. Wireless sensor networks (WSNs), radio frequency identification (RFID), cloud computing and end-user applications are a few among them. These things, when being connected, must follow some set of predefined rules. Besides this, the diverse nature of devices both in terms of resources and computational power remains an issue to be addressed. To do so, different IoT architecture, which has many elements like sensors, actuators, cloud services, protocols, etc., are used in the present.
As far as IoT architecture is concerned, Service-Oriented Architecture (SOA) will be the future [2, 3] as reducing time and computational cost remains the main concerns while designing any IoT application. Various studies as in [4, 5] had stated the benefits of this kind of architectural technique. The functionality of service-oriented IoT architecture depends upon the request and delivery of services through various communication protocols. Nevertheless, security and privacy remain a major concern in any IoT Architecture [6], as billions of things (smart objects) which are interconnected [7], and can also exchange information, make IoT-based systems more vulnerable to different types of threats [8, 9].
There are a few studies that advocate the use of SOA in IoT. In [10] A.S. Pillai et al. developed a service-oriented architecture that provided early warning. This entire implementation was aided with machine learning (ML) algorithms that was used on a cloud server. In [11] D. Georgakopoulos et al. presented an idea of a future IoT that uses service discovery across various layers of IoT. Service-oriented architecture for home area network (SoHAN) is proposed in [12], V. Issarny et al. in [13] showed how the service-oriented architecture can be utilized to address challenges for developing of distributed IoT applications. C. Cambra et al. in [14] stated the use of service-oriented architecture for agriculture monitoring. The authors in [15] used a service-oriented virtual network and designed a smart campus system. The authors in [16] suggested how different aspects of the service-oriented approach can be used in present city infrastructure. A model for IoT that emphasizes explicitly the use of the service-oriented aspect is presented with applications [17]. The study in [18] presented a smart grid base on a service-oriented IoT architecture.
This chapter mainly targets researchers working in the security area of IoT and service-oriented IoT architecture. In our opinion, this work will provide readers with a cohesive survey to keep up with the most current information, which does not exist in a single survey in the current literature. This work facilitates the following:
- - For the novices, they will grasp the concepts of IoT, its evolution, various protocols, things (IoT devices), service-oriented IoT architecture, and its major security concerns.
- - This chapter is a one-stop place where targeted readers can find state-of-the-art material on current protocol standards and enabling technologies for IoT.
- - We also presented a novel anatomy of attacks and discussed some of the existing mitigation methods with their limitations.
- - This chapter will aid investigators who are working on SOA for IoT. Further, this work presents a well-organized section on major security issues at each layer of this type of architecture.
In the following subsections the highlights of the most successful surveys are shown.
As far as protocols and security issues in IoT are concerned, there are many surveys exploring protocols as in [19] that cover all the major protocols and their application in IoT till 2012. In [20, 21] the authors made a survey of application layer protocols. In [22] M. Collina et al. explored application layer protocols for IoT. However, this work mainly focused on MQTT and CoAP protocols. Network layer protocols and 6LoWPAN protocol stack and their shortfalls are explored in [23] but many new protocols are not a part of this work. In [24] by Jorge Granjal et al. the main focus is on physical and link-layer protocols, and this work also explores some of the existing security features of those protocols. A quite old study, from 2013 [25] is made on some standardized protocols at that time. In [26] the authors cover a majority of protocols in their work till 2017. In the same year, a good survey was done [27] by Pallavi Sethi et al.
We also explored some of the latest surveys as of [28], which discusses only a few protocols in their work. The authors in [29] cover some protocols and analyze their performance in various IoT applications. Some researchers have also highlighted the prominent security and privacy threats in IoT as in [30–36]. However, literature is evident that still a lot of work can be done related to the study of various protocols that connect a wide range of things, and security issues with the adoption of SOA with IoT. The authors of this article have tried to extend these studies by aggregating the study of protocols belonging to all these layers in one article. Moreover, very few of the articles in the literature have focused on attacks in these protocols. Considering the utility of SOA in IoT, we have attempted to make a study of threats and vulnerabilities at each layer on the respective architecture.
The major and unique contribution of this chapter can be summarized as:
- - The primary purpose of this work is to make readers familiar with various protocols used in service-oriented IoT architecture and major security concerns in it.
- - Besides this, the work also focuses on some other major attacks like software attacks and attacks on devices.
- - This work explores the relation between protocols concerning their applicability to different use cases, security features, and briefs about the attacks on them.
- - Our work emphasises the adaption of service-oriented IoT architecture and tries to find out layer-wise security issues in it.
The rest of the chapter is arranged as follows. The second section is titled regarding the brief history and evolution of IoT. The same section covers an introduction about various real-life applications of IoT, different “Things” in IoT, and its fundamental security requirements and specific attacks on them. The third section covers the introduction of SOA and describes the function of each layer when SOA is adapted in IoT. Along with it, a complete protocol stack with a detailed survey of all exiting protocols at each functional layer is made in its second subsection. In the fourth section, this article presents a complete taxonomy of attacks on a service-oriented IoT architecture. The fifth section highlights specific security issues at each level of service-oriented IoT architecture. This section is followed by the conclusion.
1.2 IoT: Evolution, Applications and Security Requirements
This section describes a brief history and evolution of the IoT, followed by an overview of some of its real-life applications and various IoT devices and platforms. No doubt, security is a big concern with the IoT. So, we focus on the basic security requirements of IoT and also map separate attacks on each specific security requirements.
1.2.1 IoT and Its Evolution
The term IoT evolved from RFID (radio-frequency identification) technology [37], when during World War II British researchers established “Identify Friend or Foe” (IFF); through which whenever a British plane received signals from British Army radar it would broadcast a signal back to identify the plane as a friend. From 1950 to 1960, researchers from the United States, Europe, and Japan succeeded [38] in using RF energy to identify objects remotely. Soon this technology was commercialized with the development of anti-theft systems. In the 1970s, the Los Alamos National Laboratory deployed a device for monitoring radioactive materials and transporting vehicles using a transponder The technology was commercialised in the mid-1980s. The U.S. Department of Agriculture was facing the problem of identifying cattle, like cows, uniquely to determine if they got the right dose and to ensure that no cow got a double dose by mistake. Los Alamos National Laboratory solved this problem by using passive RFID with UHF radio waves tag [37] to uniquely identify each cow. After this, many companies [39] developed such a system, using smaller transponders which were encapsulated in glass and injected in a cow’s skin; this technology is used till date. Kevin Ashton [40] in 1999 for the first time coined the term “Internet of Things” in the context of the smart transportation system, and soon the era of connecting things began. Sarma and Brock molded RFID into an interacting technology by connecting objects to the Internet through tags [39]. I-frequency transponders with cards were also used to implement controlled access to the building. Besides this, wireless ad-hoc and sensor networks can be considered as the ancestors of IoT without IP addresses. The first decade of the twenty-first century was the era of microelectronics and communication; WSNs and wireless Ad-hoc networks were emerging. WSNs enable wide support for interactions between people and their surroundings, by giving the freedom of wireless communication, the capability of sensing and collecting data from a large area. Generally, the deployment of such a network collects data and transfers it to the sink. The present-day definition of the IoT is “Anything”, “Anytime” and “Anywhere”.
1.2.2 Different Applications of IoT
The history and evolution of IoT show that, right from its beginning, this technology was found suitable for commercial applications. The property to connect and interact with different things makes IoT suitable for a variety of applications, which can be used to solve many real-life problems. A few of its real-life applications are summarized below.
- • Healthcare: This application of IoT refers to the healthcare monitoring system, telehealth [41] where doctors can remotely monitor patients.
- • Smart Home: To improve luxury and quality of life, household appliances like washing machines, toasters, coffee machines, ACs, TVs, refrigerators, security cameras, etc., can be monitored and controlled [42] using a smartphone, tablet, or laptop connected to the Internet.
- • Wearables: These are devices that are implanted with sensors and actuators and can communicate [43] over technology like Bluetooth. They are normally worn on the wrist or connected to the body with smartphones for tracking human activities.
- • Agriculture: In order to enhance crop yields and financial gains, smart farming is introduced. IoT in Agriculture is used for [44] irrigation control, monitoring warehouse and farm animals.
- • Smart Supply Chain Management: In order to reduce operational cost, proper management of real-time data and enabling multi-way and secure communication between suppliers of raw material, shippers, production houses and customer this [43] application of IoT came into the picture.
- • Smart Grids: As IoT enabled the communication between smart meters and remote power outlet [45], which provides height quality of energy at the lowest cost, analysis of consumption patterns and load balancing.
- • Industrial Internet and Smart Manufacturing: Use of IoT in industry enabled better power management, optimization of resource [46], which helps in cost-cutting. Some applications of IoT involve use of robots to enhance accuracy and smart logistic management.
- • Smart City: This application of IoT involves all services which solve problems in the sector of healthcare, water, energy, transport management and thus, enables smart city.
- • Smart Transportation: IoT has a significant role in enabling fast and secure transportation by connecting transport vehicles, roadside assets, traffic signals, and dynamic traffic management systems.
- • Connected Cars: Under this heading comes the application where a car and other vehicles are connected with each other and things around them to share data both inside and outside the vehicle, in order to enhance safety and luxury while travelling.
- • Smart Safety: IoT applications which are used for the safety of women, security systems in buildings and disaster management are a few of the many uses to enhance safety.
- • Environment Protection: IoT can play a vital role in environmental monitoring, as WSNs can be used for monitoring air and water quality, atmospheric and soil conditions.
1.2.3 Different Things in IoT
The applications that are mentioned in the above section comprise a huge set of a variety of things [47]. In this section we have classified them into different categories; these devices are as stated below. Figure 1.1 illustrates different IoT devices and platforms.
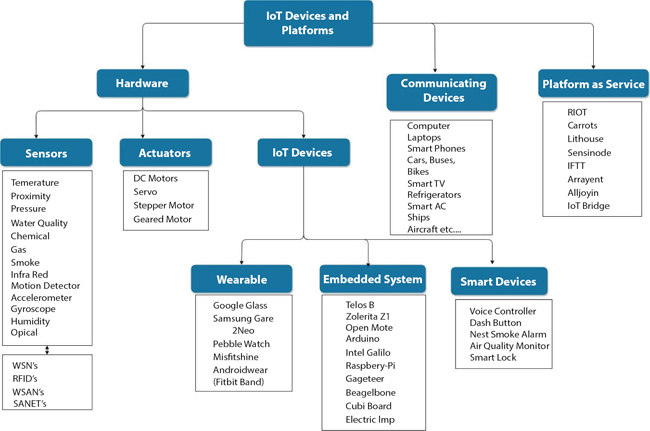
Figure 1.1 IoT devices and platforms.
- - Sensors are the devices used to ‘sense’; the main task of a sensor is to perceive events or variations in the physical environment, and to guide another gadget or computer system.
- - WSNs are a group of dedicated sensors deployed over a wide geographical area for monitoring and recording change in physical conditions. They send collected data to a central location.
- - RFID is a technology to collect data to computer systems with the help of Radio Frequency
- - Actuators, which convert the signal to some movement like linear, rotational, etc., that have a desired stimulus on the physical world. Sensor/Actuator network (SANET) Wireless Sensor and Actuator Networks (WSAN) are some networks that can sense a change in the environment and take appropriate action using actuators.
- - IoT Devices
- • Wearables: This category involves the devices which can be worn on the body, and are also able to communicate.
- • Embedded System: Comprises objects having sensors, actuators, and processors which are handled by software systems and APIs, which together create a connected environment.
- • Smart Devices: Electronic devices, generally connected to other devices, that can function interactively and autonomously.
- - Communicating Devices are capable of communicating with other devices using wired or wireless medium. Usually, they are rich with computing resources and enabled with technologies like GPS.
- - IoT platform-as-a-service (PaaS) allows renting cloud infrastructure suitable for various IoT applications.
1.2.4 Security Requirements in IoT
Up till now, readers might have got a clear idea about how IoT has evolved, what different “things” are in IoT and what real-life applications of IoT are. Before focusing on security issues, let us discuss the essential security requirement and attacks that can be done on them. The major security requirement for IoT [48] are as mentioned below:
- - Confidentiality: Information must not be disclosed to any unauthorized entity. As connected devices may transmit confidential data, confidentiality is of vital importance.
- - Integrity: Refers to the security of asset used in an IoT system. Sensitive data is also stored locally on IoT devices. This data comprises sensitive and personal data, medical records, manufactures data, media decryption keys, logs, and so on that makes integrity a primary security requirement.
- - Authorization: Determines whether a person or computer may access a resource or problem commands. If an unauthorized person does so, it may lead to malfunctioning of the IoT System.
- - Availability: Alternatively, when an authorized entity requests to access any resource, it must always be accessible or else this may cause several problems related to functionality and Quality of Service.
- - Authenticity: When a device asks for services to a remotely located server authentication becomes important. The information coming from the source must be authenticated; this verification is usually done through authentication techniques that involve proof of identity.
- - Non-repudiation: When two IoT entities transfer message between them, one must not deny after sending it; this property is usually achieved using a trusted third party.
- - Accountability: Ensures that every action of each user or device can be looked after so that the misacting entity can be easily found out. In other words, it helps to look after ’who did what’.
- - Reliability: Is the requirement that assures a consistent and reliable working of the IoT system so as to provide various services. It refers to the property that guarantees stable behavior of IoT systems.
- - Privacy: Privacy in IoT refers the control of disclosure of user’s private data. It is a vital property in the context of IoT.
- - Physical Security: Majority of IoT devices are remotely deployed, so physical protection is required to save them from unauthorized physical access, damage and side-channel attacks.
Figure 1.2 gives a clear idea about the primary security requirements and the respective attacks on them. In this subsection, we do not describe any of the attacks in detail. However, we have mapped the respective attacks with each of the basic security requirements. Some of the attacks are described in the forthcoming part of this chapter.
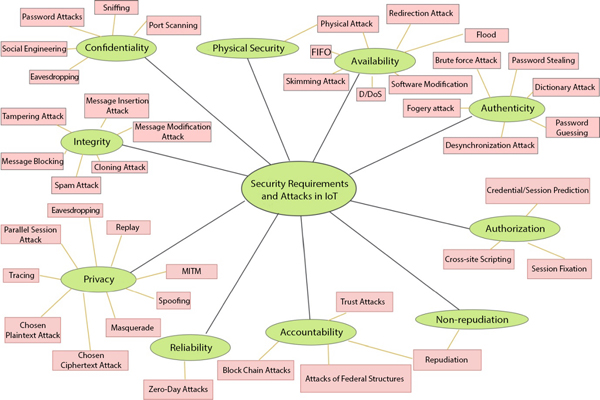
Figure 1.2 Security requirements and attacks in IoT.
1.3 Service-Oriented IoT Architecture and IoT Protocol Stack
This section describes SOA and also gives a brief overview of various layers in generic service-oriented IoT Architecture. In the next subsection, layer-wise protocol of an IoT protocol stack with a complete briefing of each protocol is made.
1.3.1 Service-Oriented IoT Architecture
To start with, let us understand SOA and its advantages. SOA is an architectural approach in which a service consumer asks for service that is provided by a service provider, and the entire communication is done via communication protocols. Figure 1.3 shows an idea of the same. SOA has many advantages like service reusability, easy maintenance, availability, reliability, and scalability. These advantages make SOA best suited for an IoT scenario.

Figure 1.3 General service-oriented architecture.
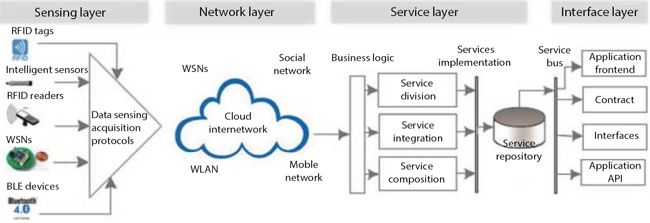
Figure 1.4 Service-oriented IoT architecture [49].
Connecting a huge number of things which are heterogenetic in nature, both in computational power and in the sense of connectivity properties, is a challenging task in itself. Along with it, to satisfy the requirements of discrete IoT applications services like data analytics, context-aware computing and cloud-based service also have to be indulged in IoT architecture. In order to serve all such applications, a generic service-oriented IoT architecture in Figure 1.4 was proposed by [49].
SOA is generally based on components that can be designed with interfaces and protocols [49, 50]. SOA concentrates on designing the work flow of respective services. This helps software and hardware devices to be reused in the IoT architecture [49]. SOA can be easily integrated into the conventional three-layer IoT architecture, where data services provided by the sensing and network layer and the business logic is governed by service layer, which is also known as a middleware layer, and lastly, it has an interface layer which fetches and give data to the service layer. Thus, in SOA-based IoT architecture, there are four layers and they connect with each other [51].
To make SOA work, communication protocols are essential, as the protocols enable the demand and delivery of service to connect devices. SOA is divided into different layers, each with a specific purpose. To enable the working of all these layers, IoT has various protocols, designed to satisfy specific purposes at each layer. A detailed protocol stack with a brief description of each is given in the next subsection.
1.3.2 IoT Protocol Stack
Figure 1.5 shows the IoT protocols stack comprising all the technologies and services which are used to connect various devices in IoT. IoT protocol stack has various protocols at different layers of operation. To make the study easy we have studied layer-wise protocols that are as listed below.

Figure 1.5 IoT protocol stack [52].
1.3.2.1 Application Layer Protocols
IoT application developers have a very large set of the protocols [53] available at the applications layer, which comes from the traditional Internet and those built specifically for supporting IoT applications.
Hypertext Transfer Protocol (HTTP) is an application-layer web-based protocol which was developed in 1989 by Internet Engineering Task Force (IETF).
Representational State Transfer (HTTP REST) is popular because of its simplicity in use as it is built on top of HTTP [54, 55]. Its state transfuse property is useful in IoT as actuators can send a message on state transfuse.
WebSocket was standardized by the IETF as of 2011. More generally it is used for message exchange between Application and Transport Layer. It is mainly a computer communication protocol that provides bidirectional communication over a single TCP connection [56].
Simple Text Oriented Messaging Protocol (STOMP) is a text-orientated messaging protocol. STOMP was released in 2012 [57]. STOMP delimits the interoperability issue among languages, platforms and brokers.
Simple Object Access Protocol (SOAP) is a message protocol built on XML and used for information exchange among computers and was released in 1998. It is an application based on XML specification [51] and can extend HTTP for XML messaging. SOAP is a protocol for communicating through the Internet. SOAP can be used to send a message which is independent of the platform and language.
Extensible Messaging and Presence Protocol (XMPP) is an instantaneous messaging protocol also called as Jabber on XML streaming protocols [51]. XMPP is an abstraction XML protocol, which makes it extensible, and possesses several security capabilities. Its highlighting features include multiparty chatting, speech, video and file transmission.
Constrained Application Protocol (CoAP) is a messaging protocol released in June 2014, which is based on REST (REpresentational State Transfer) architecture [58]. CoAP is a protocol for web transfer, particularly useful for resource-constrained IoT devices. It is secured and can even work when TCP fails to work [59].
Advanced Message Queuing Protocol (AMQP) AMQP is an open standard message queuing protocol released in October 2011. It is used to provide messaging service for business applications [51]. AMQP is designed to solve real problems [60].
Message Queue Telemetry Transport (MQTT) is ISO standard lightweight publish-subscribe architecture that transports messages between devices [61]. It is a messaging protocol for collecting measured information from distant sensors and transmitting information to servers. MQTT protocol requires two components – message broker and clients.
Data Distribution Service (DDS) is an application layer publish-subscribe model-based protocol for supporting machine-to-machine communications [62]. This protocol provides reliable, fast, real-time, scalable data exchanges.
Table 1.1 gives a description of several main features of the application layer protocols.
1.3.2.2 Transport Layer Protocols
The main task of protocols in this layer is to provide a host-to-host communication. We have discussed here different protocols with their prominent features.
User Datagram Protocol (UDP) is a transport layer protocol designed in 1980 by David P. Reed (RFC 768). It uses datagrams to send a message over an Internet Protocol network. UDP [63] is a connectionless protocol with minimum header size, and no handshaking is required before sending the message. UDP is lightweight and mostly preferred for IoT application faster communication.
Quick UDP Internet Connection (QUIC) emerged as an experimental general-purpose transport layer protocol [65]. However, it was publicly announced by IETF in 2013. It is equivalent to TCP but has less latency. It is implemented at the top of UDP and does not suffer from limitation like data loss. QUIC can be deployed with HTTP/2’s multiplexed connections. This enables several data sources to reach all endpoints independently.
Table 1.1 Summary of application layer protocols.
| Protocols | Released / Invented by | Release year | Key features | Architecture | Security |
| HTTP | IETF | 1989 | Collaborative, Distributed and Hypermedia Information Systems | Request / Response | HTTPS |
| HTTP REST | Roy Fielding | 2000 | Actuators Can Send Message on State Transfuse. | Request / Response | HTTPS |
| WebSocket | IETF | 2011 | Provides Full-duplex Communication Channels | Client / Server | HTTPS |
| STOMP | IETF | 2012 | Overcomes Problem of Interoperability | Publish / Subscribe | HTTPS |
| SOAP | IETF | 1999 | Provides Platform In-dependency | Client / Server | HTTPS |
| XMPP | IETF | 2011 | Supports Bidirectional Communication Between two Parties | Publish / Subscribe | TLS/SSL |
| CoAP | IETF | 2014 | Enables Push Notifications, Group communications and RESTful Interactions | Client / Server | TLS/SSL |
| AMQP | OASIS | 2011 | Robust Interaction with middle-ware Messages, | Publish / Subscribe | DTLS |
| MQTT | OASIS | 2013 | Collects Information from Distant Sensors and Transmitting to Servers | Request / Response | TLS/SSL |
| DDS | OMG | 2001 | High performance for real-time M2M devices | Publish / Subscribe | TLS/SSL |
Table 1.2 Summary of transport layer protocols and features.
| Protocol | Connection establishment | Congestion control | Fragmentation | Rate control | Return route check |
| UDP | No | No | No | No | No |
| QUIC | Yes | Yes | Yes | Yes | No |
| RSVP | No | No | Yes | No | No |
| SCTP | No | Yes | Yes | Yes | No |
| DCCP | Yes | Yes | Yes | Yes | No |
| TCP | Yes | Yes | Yes | Yes | Yes |
Resource Reservation Protocol (RSVP) a transport layer [66] protocol operates over internet protocol version IPv4 or IPv6. It is designed for multicast or unicast data flow. RSVP provides Quality of Service (QoS) using the cohesive services model.
Stream Control Transmission Protocol (SCTP) exhibits characteristics of both UDP with sequencing [67], acknowledgement generation and secure message communication along with congestion controlling mechanism [68].
Datagram Congestion Control Protocol (DCCP) is a transmission layer-oriented message protocol. This protocol provides reliable, secure, congestion-free communication suitable for streaming media IoT applications [69, 70].
Transmission Control Protocol (TCP) exchanges messages with reliable service and error detection with correction techniques to assure error-free communication [64]. Major Internet applications depend on TCP. But, the use of TCP in an IoT scenario is limited due to larger header length.
Table 1.2 has a summary of all these protocols and their features.
1.3.2.3 Network Layer Protocols
Network layer has two major tasks to perform: Encapsulation and Routing. Each is briefly described below.
- (a) Encapsulation
Internet Protocol version 4 (IPv4) is the fourth version of Internet Protocol which was initiated in 1980 by IETF [71], which is widely used in an Internet application. However, the first version of this protocol was ARPANET, which was deployed in 1983. IPv4 uses 4 bytes (32-bits) addressing, that provides 232 addresses and has 20 bytes packet size. But, IPv4 has limitations regarding use in IoT as the devices that will be connected are much more in number than the capacity of IPv4.
Internet Protocol version 6 (IPv6) IPv6 [72] is planned to replace IPv4. It is a web layer convention for packet exchanged and gave a start to datagram transmission across different IP networks. IPv6 utilizes 128 bits tending to and 40 octets to the Payload Length. This conquers the difficult shot location yet increments the payload size. Thinking about the size of the network, among IPv4 and IPv6 selection of IPv6 is evident for IoT environment [73].
6LowPAN was introduced so that IPv6 packets can be transmitted over IEEE 802.15.4 network [74]. In 2016, IETF launched 6Lo [75] in order to use IPv6 with a network of resource-constrained nodes. This protocol stack is considered to be well adapted for applications such as Bluetooth, IEEE 1901.2 and IEEE 802.11ah. Adoption of IPv6 over Time Slotted Channel Hopping (TSCH) makes 6TiSCH a key technology. 6TiSCH is found suitable for industrial purposes [76]. - (b) Routing
Routing Protocol for Low-Power and Lossy Networks (RPL) is a routing protocol for WSNs with low power released in 2011 and updated in 2013. It is a proactive vector-based protocol works on IEEE 802.15.4 [77]. It has optimized behavior for multi-hop network and many-to-one system, but also promotes an end-to-end communication. RPL was designed for static sensor networks. Further, CORPL is an extension of the cognitive network based on RPL protocol, [78]. CORPL utilizes topology from DODAG, which utilizes opportunistic forwarding between nodes of the packet.
1.3.2.4 Link Layer and Physical Layer Protocols
This subsection gives a brief overview of various protocols and standards that are used to connect the end devices. As per the utility and range of protocols, we have summarized them as long-range and short-range protocols. But, taking SOA under consideration, one must know the best-suited protocol. So, to give readers a clear idea about that, protocols are categorized as below.
• Wireless Body Area Network (WBAN)
Radio Frequency IDentification (RFID) was invented in 1983. But it became a crucial component of the IoT when in 1999 Kevin Ashton understood its potential. Low price and vitality of its use made RFID a promising technology for [79] various IoT applications.
Near Field Communication (NFC) is a technology-based on RFID [80] and it’s important for IoT. This technology enabled one-to-one communication for very short range.
Insteon released in 2005 by Smartlab [81] is a proprietary protocol mainly used for home automation and supports a dual mesh topology. It is capable of using radiofrequency and electrical wiring.
• Wireless Personal Area Network / Personal Area Network (WPAN / PAN)
Bluetooth: Nils Rydbeck initiated Bluetooth in 1989. The main features of Bluetooth [82] are, it uses short-wavelength from 2.400 to 2.485 GHz and is used to connect both fixed and mobile distance up to a significant range of distance.
• Wireless Home Area Network (WHAN)
Bluetooth Low Energy (BLE) [83], also called as Bluetooth Smart, is designed for application with low power and needs to be connected within a small range. The low energy feature of BLE makes it more suitable for IoT devices.
MiWi is a networking protocol stack created by Microchip Technology Inc. [84]. This protocol stack was introduced to address the problem of high memory footprint; MiWi stack came into the picture [85].
Z-Wave protocol was developed by Zensys, in 1999 and is mainly used in [86] home monitoring IoT applications. Compare to Zigbee, Z-wave is simple to implement so many product manufacturers use it in their products which need low energy and reliability.
ANT/ANT+ is a proprietary protocol primarily architecture for remote monitoring applications [87]. It has the physical, data link, and network layers. At the same time, the application layer is managed by Ant+, which is an extension that regulates communication between different devices.
• Wireless Factory Area Network (WFAN)
WirelessHART was initiated in early 2004. It is an open standard protocol stack having four layers. This protocol is one of the standards and prominent protocols for industrial automation system.
Weightless was released in 2012. Weightless is an open standard for wireless technology mainly build for exchanging data among the base station and end nodes. It has a significant level of security [88].
DigiMesh is a proprietary technology that follows the IEEE 802.15.4 standard. In Digimesh network, all devices are kept similar, and so they can function as end-device, router or coordinator [89, 90].
EnOcean enables M2M communication and mainly used for home and building automation purposes. In order to serve battery-free devices, this protocol is to be kept lightweight.
• Wireless Local Area Network (WLAN)
The WLAN network links two or more wireless devices to establish a local area network (LAN) in a restricted zone. This allows users to move around within the region while still connecting to the network.
• Wireless Neighborhood Area Network (WNAN)
WiMax came into existence in 2005 and belonged to the class of wireless broadband communication standards. MiMax is constructed over the IEEE 802.16 standards.
Wi-Sun: Wi-Sun Alliance promoted this protocol to provide a secure, optimized mesh network. Wi-Sun promoted the adaption of this protocol to become an open industry standard for smart utility and smart city applications.
ZigBee is a standard protocol [91] built by adapting IEEE 802.15.14 physical and data link layers. There are three variants: ZigBee PRO, ZigBee RF4CE, and ZigBee IP to serve different networking requirements. This protocol was specifically intended for short-term communication and low-power devices. It supports mesh, star and tree topologies with up to 65,000 end devices.
• Wireless Wide Area Network (WWAN)
When a very long range of communication is required, these set of protocols are required. WWAN comes with both licensed and unlicensed network protocols.
- (i) Low Power Wireless Wide Area Network (LPWAN) – Unlicensed LoRaWAN initiated in 2015, and defined by the LoRa Alliance which are protocols intended for wireless and battery-operated devices. This is a MAC protocol for Wide Area Network. Long Range Wide Area Network (LoRaWAN) operates on the third and second layer of the OSI model [92].
Sigfox was initiated in 2009 by the French global network. This protocol has a wide range of coverage but works well with simple devices that transmit less frequently and usually sends a few amounts of data. But the main feature of Sigfox [93] is that it can be deployed anywhere, so it can be used with a variety of use cases.
DASH7 is open-source developed from 2013 to 2015. It operates between 315 MHz and 915 MHz. DASH7 performs well at connecting mobile things, unlike other wireless data protocols which operated well with the fixed device. - (ii) Low Power Wireless Wide Area Network (LPWAN) – Licensed Narrow Band-IoT is a standard developed by 3GPP in June 2016. This protocol has empowered a diverse variety of cellular devices [94].
- (iii) Cellular Licensed
LTE-Machine Type Communication (LTE-MTC) is a standards family introduced in 2018 by 3GPP which comprises several other technologies like Cat-1 and CatM1, suitable for the IoT [94].
Extended Coverage-GSM-IoT (EC-GSM-IoT) was introduced in 2016 for enhancing the capabilities of present cellular networks for IoT usages [94].
The summary of these protocols is done as short-range protocols in Table 1.3 and long-range protocols in Table 1.4.
All these protocols that are discussed contribute to IoT and are best suited for various purposes. To make a proper IoT architecture it is important to choose a proper technology that can support the architectural requirement, optimize available resources, and can be securely integrated with other services.
As IoT is a gradually evolving from the existing Internet, the protocol stack has many protocols that are already being used while others are developed exclusively for IoT. In order to support security of constrained nodes and satisfy the variety of requirements which are not same for all IoT application, selection of protocol at each layer becomes crucial.
But, all these protocols have security issues that need to be taken care of. A protocol is a set of rules that governs communication; these sets of rules may have some issues that make every protocol vulnerable to many attacks. The listing of attacks [95–102] on each protocol of every layer is made in the forthcoming section.
Table 1.3 Summary of link layer and physical layer protocols (short range).
| Protocols | Standard | Licensing | Data rate | Topology | Application used in | Security |
| RFID | ISO | Free | 500Kb/s | P2P / star | Tracking and identification | Clandestine tracking |
| NFC | ISO | Free | 106 – 848 Kb/s | Peer to peer | Healthcare, smart environment, mobile | Encryption, secure channel, key agreement |
| BLE | IEEE 802.15.1 | Free | 1 Mbps | Single-hop | Multimedia data exchange | AES - 128 |
| Ant | Garmin | Proprietary | 1Mbps | P2P / star / tree / mesh | Sports, wearables and fitness | AES - 128 |
| EnOcean | EnOcean alliance | Proprietary | 125 kbps | Mesh | Home and building automation | AES - 128 |
| Zigbee | Open standard zigbee alliance | Free | 250 kbps | Star / mesh / tree | Home automation, smart environment | AES - 128 |
| Insteon | Smartlabs | Proprietary | 37.5 kbps | Star / mesh / tree | Industry automation | AES - 128 |
| MiWi | Microchip technology | Proprietary | 250 kbps | Star / mesh / tree | Industry automation | AES - 128 |
| DigiMesh | Digi international | Proprietary | 250 kbps | P2P / mesh | Industry automation | AES - 128 |
| IEEE 802.15.4 | IEEE 802.15.4 | Free | 250 kb/s @2.4 GHz | Mesh | Multi hop networks | AES - 128 |
| WirelessHART | IEEE 802.15.4 | Free | 250 kb/s | Star / cluster / mesh | Industrial automation | CCM – AES 128 |
| Z-Wave | ITU G.9959 | Free | 100 kb/s | Mesh | Home automation | AES - 128 |
| Weightless (w) | Weightless SIG | Free | 10 Mb/s | Star | M2M application | AES - 128 |
| IEEE 802.11ah | IEEE 802.11ah | Free | 7.8 Mb/s @ 2 MHz | Star | One-Hop network with many nodes | WPA |
Table 1.4 Summary link layer and physical layer protocols (long range).
| Protocols | Standard | Licensing | Data Rate | Maximum nodes | Topology | Applications used in | Security |
| NB-IoT | 3GPP | Freely available for chip/device vendor | 200 kb/s | 52,000 | Star | M2M, tracking, smart things, mobile application, Point of Sales (POS) terminals | NSA AES 256 bit |
| Cat-M/Cat-0 | 3GPP | Freely available for chip/device vendor | 1 Mb/s | 52,000 | Star | M2M, tracking, smart things, mobile application, Point of Sales (POS) terminals | AES 256 bit |
| LoRaWAN | LoRaWAN | Licensed for device vendors & loyalty to be paid by network operators | 25-30 kb/s @500 kHz 22 b/s @7.8 kHz | >1,000,000 | Star of Star | Building automation, security, smart metering, agriculture, house monitoring, environment tracking, transport monitoring | AES CCM 128 bit |
| Sigfox | Sigfox | Freely available for chip/device vendor & loyalty to be paid by network operators | UL 100 b/s DL 600 b/s | >1,000,000 | Star | Building automation, security, smart metering, agriculture, house monitoring, environment tracking, transport monitoring | Key generation, message encryption, MAC verification, sequence checking |
| DASH7 | DASH7 | open standard | 167 kbps | —— | Star / tree | Building automation, security, smart metering, agriculture, house monitoring | AES 256 bit |
1.4 Anatomy of Attacks on Service-Oriented IoT Architecture
IoT architecture comprises different layers, and each individual layer has a specific task. When SOA is taken into consideration, communication protocols and other services play a vital role. The previous section has given a brief overview of the protocol stack used in IoT. To get a better idea about security issues and research challenges, let us look at the anatomy of attacks on service-oriented IoT architecture.
Attacks on service-oriented IoT architecture can be categorized into three major classes [103]: software attacks, attacks on devices, and communication protocols. Software and services play a very significant role in the application and interface layer of service-oriented IoT architecture.
1.4.1 Attacks on Software Service
Figure 1.6 gives a detailed idea of various types of software attacks.
1.4.1.1 Operating System–Level Attacks
Phishing Attack: This is a common attack in which an assailant aims to get passwords, One Time Password (OTP), Personal Identification Number (PIN) and other sensitive data via emails, social engineering, etc. [104].
Backdoors Attack: With the development of IoT, many operating systems are coming into the picture, and such operating systems may contain some backdoor vulnerabilities [105] that may cause a threat to sensitive data. Lack of proper update mechanisms give a space for viruses and worms like mirai, stuxnet and brickerbot to attack IoT objects.
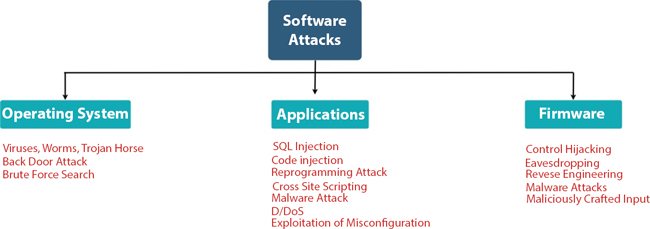
Figure 1.6 Attacks on software services.
Brute Force Attack: This attack aims to break security implemented by cryptography and harms data confidentiality. Mitigation techniques for such kind of attacks entirely depend on OS level security [104]. The use of anti-virus software, intrusion detection systems, storing encrypted passwords, implementation of architectural security, etc., can provide defence against this attack.
1.4.1.2 Application-Level Attacks
Attack through Misconfiguration: IoT is dependent on elements such as operating systems, repositories and servers, misconfiguration of which causes threats to security [106].
Malicious Code Injection: Malicious software code inserted into certain packets for the stealing or manipulation of confidential data [107]. Path-based DoS is also a type of attack where malicious code is injected into some network packets.
Reprogramming: As the devices are connected through a network, hackers may reprogram the connected devices to do unwanted tasks.
Malware Attack: Is done through the malicious programs [107] that are specially designed to attack IoT Applications.
Botnet: Is the main technique to mount D/DoS attack. These kinds of attacks can be mitigated using securing bootstrapping algorithms and other techniques [102, 106].
1.4.1.3 Firmware-Level Attacks
IoT systems lacking in design principles and lacking standard Firmware updating leads to Firmware Attacks [100] as follows:
Control Hijacking: When an attacker can change an object’s normal flow by injecting malicious code, it is called a control hijacking attack.
Reverse Engineering: This is an active attack which aims to get sensitive data by analyzing firmware [99].
Eavesdropping: Is a passive attack where attacks aim to get packets less protected and use these packets to create replay attacks.
Malware Attack: Is done through the malicious programs that are specially designed to attack IoT Applications. Several malware attacks [101] are found in firmware like BASHLITE, Hydra, and Darlloz.
1.4.2 Attacks on Devices
Physical Attacks: Here, the attacker tampers the IoT Devices [100]. Practically performing this kind of attack is more challenging, as it requires a set of expensive tools. De-packaging chip in order to steal keys, micro-probing and practical beaming are some examples of physical attacks.
Side-channel Attack: Is a security exploit that gathers data about a computer device while performing cryptographic activities [102]. Further, this technique uses the obtained data to reverse engineer the device’s cryptography scheme.
1.4.3 Attacks on Communication Protocols
In this section, we have classified attacks on each layer of IoT protocol stack, as explained in the previous section. Some of the common attacks on communication protocol are discussed below.
1.4.3.1 Attacks on Application Layer Protocols
Following are some attacks on application layer protocol. All the different protocols and respective attacks on them are shown in Figure 1.7.
Man In The Middle (MITM): Is an attack in which the attacker secretly replies and modifies communication packets.
Spoofing: Is a state in which a person or program successfully masquerades as another entity using falsified data. This allows the attacker to gain an advantage as a legitimate user.
Buffer Overflow: Is a situation where the memory of a device is exhausted by indulging repetitive storage activity on memory space.
Flooding: Is an attack in which the attacker sends continuous synchronization requests to the targeted system and attempts to consume resources. This makes the system unavailable to legitimate users.
Sniffing Attack: Corresponds to capturing of network traffic using some packet capturing tools. Using such tools allows the attacker to analyze the network and gain information about the traffic.
Pre-shared Key Attack: Keys are usually shared between two parties using a secure channel; attacks on these keys through various means come under this category.
Denial of Service (DoS): Is an attack where the offender tries to make a device or network resources unavailable to the legitimate users.

Figure 1.7 Attacks on application layer and transport layer protocols.
Distributed Denial of Service (DDoS): This attack is an effort to make device and service unavailable to the user. This attack mainly targets websites and online services.
1.4.3.2 Attacks on Transport Layer Protocols
Transport layer protocols suffer from attacks like flooding, port scan, and spoofing attack carried through the application layer. Along with this on UPD, breaking security on TLS and DTLS and attacks on SSL through XMPP and MQTT protocol are prominent. Security at this level relies on IPSec and TLS 1.3, which uses AES security. Figure 1.7 describes more about those attacks on each specific protocol.
1.4.3.3 Attacks on Network Layer Protocols
Network layer performs two main tasks, namely, encapsulation and routing. We have classified attacks according to these functions. Figure 1.8 explains more about it.
(a) Attacks on Encapsulation Protocols
6LoWPAN is used to allow connectivity between resource-constrained devices and the IPv6 network. It acts as an adaption layer that connects the network and data link layer—the main task during adaption, header compression and encapsulation. However, 6LoWPAN suffers from the below-mentioned attacks [109].

Figure 1.8 Attacks on network layer protocols.
Fragmentation Attack: 6LoWPAN has a fragmentation mechanism that facilitates the transmission of IPv6 packets over IEEE 802.15.4. However, as this mechanism does not have proper authentication mechanism a fragmentation attack can be done.
Authentication Attack: 6LoWPAN network does not have a proper authentication mechanism. Because of this reason, any unauthorized attack may join the network and get unauthorized access.
Confidentiality Attack: 6LoWPAN, by default, does not have any encryption technique. Hence, an attacker may launch attacks like Man in the Middle (MITM), eavesdropping and spoofing.
(b) Attacks on Routing Protocols
Jamming Attack: This kind of attack aims to stop the communication between node by engaging the communication channels [108]. In this attack, the attacker engages communication channel, which creates a delay in communication [109].
Selective Forwarding Attack: Is an attack in which a malicious node denies to transmit some packets, which results in the disturbance of a routing path [110]. This attack can be classified into cases like blackhole attack, where malicious node rejects all packets from forwarding [111, 112].
Sinkhole Attack: In a sinkhole attack, the aim of the malicious node is to direct the network traffic to a particular node. Typically, these nodes advocate the use of a particular route in the network and tempt another node to utilize this route [110].
Wormhole Attack: This attack uses two malicious nodes and creates a direct communication link and uses this link to forward network traffic and thus ignores intermediate nodes.
Sybil Attack: In this attack, the malicious nodes create multiple identities and mislead other nodes [113].
HELLO Flood Attack: When a node joins a network, a HELLO message is used. However, the same message is used by an attacker node to mislead another node to identify it as a neighbor.
Traffic Analysis: This is an attack in which advisory captures and analyze network packet and aims to gather sensitive information. This attack is usually made through traffic analysis software like Wireshark, TCP dump, Kismet, Scapy, etc.
Man In The Middle (MITM) Attack: Attacker illegitimately controls the communication messages exchanged between the two parties.
1.4.3.4 Attacks on Link and Physical Layer Protocols
When we studied the Link and Physical layer protocols many similar attacks were found. Figure 1.9 gives a clear idea about various protocols available at the link layer and physical layer. Some of the prominent attacks on these protocols are:
Eavesdropping: Eavesdropping attack, also known as a sniffing or snooping attack. The attacker is supposed to know the topology of the network and try to discover the node through which an attack can be launched.
Side Channel Attack: To mount this attack, the attacker collects the information about the cryptographic operation implemented in the computer system. Specifically, the information about the timing, electromagnetic emission, power and even heat and sound information can be exploited to mount this attack.
Denial of Service: The attacker here attacks the infrastructure and disrupts or prolongs its regular activity and prohibits any users from accessing the services. The most common aim of a DoS attack is an internet service like a website. However, this attack can be made on networks or IoT devices.
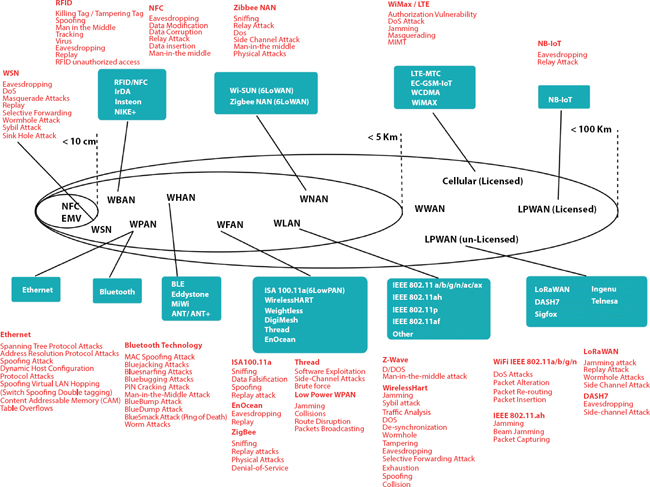
Figure 1.9 Attacks on link and physical layer protocols.
Jamming: Jamming assault is one of the threats to WSNs running over IEEE 802.15.4 standard. In such an attack, the jammers that initiate the attack can significantly degrade the efficiency of the network by interference with transmitting packets or by weakening the signal power.
Masquerading: A masquerade assault is an attack that uses a false identity called spoofing to obtain unauthorized access to personal computer information without legal access recognition. If an authorization mechanism is not secure, this makes the system highly vulnerable to this attack.
Data Corruption: It is a type of ransomware attack in which the data on the computer system is attacked for corrupting the records or file.
Packet Crating: Packet crafting is the art of generating a packet according to different specifications for carrying out attacks and leveraging weaknesses throughout a network. It is primarily used to infiltrate the structure of the network. Various vulnerabilities assessment techniques are used to render such packets.
Physical Attacks: Physical attacks are deliberate offensive acts which attempt to damage, disclose, modify, disable, capture or obtain unauthorized access to physical objects. Thus, a physical attack attempt to trace the hole through which it can break the system.
1.5 Major Security Issues in Service-Oriented IoT Architecture
In the service-oriented IoT architecture, the bottom layer, also known as the perception layer, collects data from the physical devices [2]. When the data is sensed, it is to be provided to centralized storage through various routing paths of heterogeneous and integrated networks. At the same time, the topmost layer (the application layer) is dependent on the service layer. This layer prevails between the network and the application layer. The service layer serves various desired services both to the top and bottom layers. Based on this architecture and enabling technologies, the following are significant challenges in each layer.
To get a better idea about the security concerns in each layer of the service-oriented architecture, we present top security concerns as listed in Table 1.5.
Table 1.5 Security issues in each layer of service oriented IoT architecture.
| Issues related to | Application and interface layer | Service layer | Network layer | Sensing layer |
| Security of web interface | ✓ | ✓ | ✓ | X |
| Authentication | ✓ | ✓ | ✓ | X |
| Uncertain network amenities | X | ✓ | ✓ | X |
| Weak or no encryption | X | ✓ | ✓ | X |
| Confidentiality and privacy of data | X | ✓ | ✓ | ✓ |
| Cloud services | ✓ | X | X | X |
| Mobile services interface and | ✓ | X | ✓ | ✓ |
| Configuration of devices | ✓ | ✓ | ✓ | X |
| Unsecure software and firmware | ✓ | X | ✓ | X |
| Devices’ physical security | X | X | ✓ | ✓ |
✓: Yes, X: No
1.5.1 Application – Interface Layer
This layer has various applications that involve a discrete set of protocols and various service alignment technologies to serve different purposes. However, main security issues in these layers are: remote and safe configuration of IoT devices, software middle-ware downloading, updating of security patches through proper channel, providing a unified security platform that can support a variety of applications. Table 1.6 shows security threats and existing security methods to mitigate them.
Table 1.6 Major threats in application - interface layer.
| Security threats | Physical security | Access control | Confidentiality | Authentication | Non-repudiation |
| Unauthorized access | ✓ | ✓ | ✓ | ✓ | ✓ |
| Failure of node | ✓ | ✓ | ✓ | ✓ | ✓ |
| Masquerading | ✓ | ✓ | ✓ | ✓ | ✓ |
| Privacy leakage | X | ✓ | ✓ | ✓ | ✓ |
✓: Yes, X: No
1.5.2 Service Layer
This layer mainly relies on middle-ware and provides IoT to reuse hardware and software, which increases cost-effectiveness. The design of this service is usually based on APIs and service protocols. It has to provide services like events, ontologies, analytics, service discovery, service composition, etc. The security requirements at the service layer are:
- - Authorization that involves the authentication of service, and security of encryption keys.
- - The principal issue in this layer is privacy leakage, as it includes monitoring locations, receiving personal and confidential data.
- - Service mishandling remains a major issue that involves getting access to unsubscribed service or illegal use of service.
- - Service information leakage is also among the significant challenges at this layer.
- - There is a need to be aware of and prevent other attacks like DoS, replay, routing, node masquerade, and repudiation.
1.5.3 Network Layer
This layer connects the various devices and makes them aware of surrounding nodes. In SOA, this layer aggregates data from existing infrastructure and then transmit it to layers like sensing and service. But, while doing so, there are many security issues. Security and privacy of sensitive data become crucial as mobility and connectivity come into action. Over connectedness means exhausting communication bandwidth with authentication message and providing higher security to keys; this may affect the quality of service. Other issues like MITM attack, false message signaling, and replay attack are of major concern. Table 1.7 maps the security threats and main causes of those threats in the network layer.
Table 1.7 Major threats in network layer.
| Security threats | Physical security | Transmission security | Over-connected | Cross-layer working |
| Privacy leakage | ✓ | X | ✓ | X |
| Confidentiality | ✓ | ✓ | X | ✓ |
| Integrity | X | ✓ | ✓ | X |
| DoS | X | ✓ | ✓ | X |
| Public key infrastructure | X | ✓ | ✓ | X |
| Man-in-the-middle | X | ✓ | X | ✓ |
| Request forgery | ✓ | ✓ | X | ✓ |
✓: Yes, X: No
1.5.4 Sensing Layer
This layer comprises end devices, end node, and gateway, which are heterogeneous in nature and have to be connected through various connecting technologies. This layer also involves a fusion of technologies like RFIDs, WSN and many other connected devices which send and receive continuous data. The primary security concern is that these devices are:
- - Physical security as these devices are deployed in a physical environment.
- - Tampering of these devices can be done easily, so tamper detection techniques are required.
- - These devices are resource concern, so lightweight cryptographic algorithms are a major need.
- - Besides this, device authentication, trust management of devices, and routing security are of major concern.
Table 1.8 Major threats in sensing layer.
| Security threats | IoT devices | IoT nodes | IoT gateways |
| Unauthorized access | ✓ | X | ✓ |
| Selfish nodes | ✓ | ✓ | X |
| Spoofing attacks | X | ✓ | ✓ |
| Malevolent code | X | ✓ | ✓ |
| Denial of service | X | ✓ | ✓ |
| Communication threats | X | ✓ | X |
| Attacks on routing process | ✓ | ✓ | X |
✓: Yes, X: No
The following Table 1.8 shows the vulnerabilities and the device which can be affected through it.
1.6 Conclusion
This chapter provides a review of security issues and research challenges for service-oriented IoT architecture. In the beginning, this chapter provides an introduction to IoT and presents a summary of IoT’s evolution, its security requirements, different components and applications. Further, this chapter briefly describes the service-oriented IoT architecture and IoT protocol stack. The same subsection contains an in-depth summary of the layer-wise protocol involved in different layers. Further, the next section investigates and present the anatomy of attacks on Service-Oriented IoT architecture. Furthermore, the chapter presents the layer wise-security issues. We conclude that the highlighted security issues need to be focused on while designating service-oriented IoT architecture- based IoT applications.
References
1. M. Mital, V. Chang, P. Choudhary, A. Papa, and A. K. Pani, “Adoption of internet of things in india: A test ofcompeting models using a structured equation modeling approach,” Technological Forecasting and Social Change, vol. 136, pp. 339–346, 2018.
2. D. Guinard, V. Trifa, S. Karnouskos, P. Spiess, and D. Savio, “Interacting with the soa-based internet of things: Discovery, query, selection, and on demand provisioning of webservices,” IEEE transactionson Services Computing, vol. 3, no. 3, pp. 223–235, 2010.
3. H. Lee, E. Jeong, D. Kang, J. Kim, and S. Ha, “A novel service-oriented platform for the internetof things,” in Proceedings of the Seventh International Conference on the Internet of Things, 2017, pp. 1–8.
4. M. Rosen, B. Lublinsky, K. T. Smith, and M. J. Balcer, Applied SOA: service-oriented architecture and design strategies. John Wiley & Sons, 2012.
5. S. de Deugd, R. Carroll, K. Kelly, B. Millett, and J. Ricker, “Soda: Service oriented device architecture,” IEEE Pervasive Computing, no. 3, pp. 94–96, 2006.
6. L. Patra and U. P. Rao, “Internet of things—architecture, applications, security and other major challenges,” in 2016. 3rd International Conference on Computing for Sustainable Global Development (INDIACom). IEEE,2016, pp. 1201–1206.
7. K. Kimani, V. Oduol, and K. Langat, “Cyber security challenges for iotbased smart grid networks,” International Journal of Critical Infrastructure Protection, vol. 25, pp. 36–49, 2019.
8. S. A. Kumar, T. Vealey, and H. Srivastava, “Security in internet of things: Challenges, solutions and future directions,” in 2016 49th Hawaii International Conference on System Sciences (HICSS). IEEE, 2016, pp. 5772–5781.
9. A. Tewari and B. Gupta, “Security, privacy and trust of different layers in internet-of-things(iots) framework,” Future Generation Computer Systems, 2018.
10. A. S. Pillai, G. S. Chandraprasad, A. S. Khwaja, and A. Anpalagan, “A service oriented iot architecture for disaster preparedness and forecasting system,” Internet of Things, p. 100076, 2019.
11. D. Georgakopoulos, P. P. Jayaraman, M. Zhang, and R. Ranjan, “Discoverydriven service oriented IoT architecture,” in 2015 IEEE Conference on Collaboration and Internet Computing (CIC). IEEE, 2015, pp. 142–149.
12. M. R. Abd Rahim, R. A. Rashid, A. M. Rateb, M. A. Sarijari, A. S. Abdullah, A. H. F. A. Hamid, H. Sayuti, and N. Fisal, “Service-oriented architecture for iot home area networking in 5 g,” 5G Networks: Fundamental Requirements, Enabling Technologies, and Operations Management, pp. 577–602, 2018.
13. V. Issarny, G. Bouloukakis, N. Georgantas, and B. Billet, “Revisiting service-oriented architecture for the iot: a middleware perspective,” in International conference on service-oriented computing. Springer, 2016, pp. 3–17.
14. C. Cambra, S. Sendra, J. Lloret, adularia, “An IoT service- oriented system for agriculture monitoring,” in 2017 IEEE International Conference on Communications (ICC). IEEE, 2017, pp. 1–6.
15. Y. Guo, H. Zhu, and L. Yang, “Service-oriented network virtualization architecture for internet of things,” China Communications, vol. 13, no. 9, pp. 163–172, 2016.
16. S. Clement, D. W. McKee, and J. Xu, “Service-oriented reference architecture for smart cities,” in 2017 IEEE symposium on service-oriented system engineering (SOSE). IEEE, 2017, pp. 81–85.
17. R. K. Behera, K. H. K. Reddy, and D. Sinha Roy, “Modeling and assessing reliability of service-oriented internet of things,” International Journal of Computers and Applications, vol. 41, no. 3, pp. 195–206, 2019.
18. M. A. Zaveri, S. K. Pandey, and J. S. Kumar, “Collaborative service oriented smart grid using the internet of things,” in 2016 International Conference on Communication and Signal Processing (ICCSP). IEEE, 2016, pp. 1716–1722.
19. O. Hersent, D. Boswarthick, and O.Elloumi, The internet of things: Key applications and protocols. John Wiley & Sons, 2011.
20. V. Karagiannis, P. Chatzimisios, F. Vazquez-Gallego, and J. Alonso-Zarate, “A survey on application layer protocols for the internet of things,” Transaction on IoT and Cloud computing, vol. 3, no. 1, pp. 11–17, 2015.
21. L. Nastase, “Security in the internet of things: A survey on application layer protocols,” in 2017 21st International Conference on Control Systems and Computer Science (CSCS). IEEE, 2017, pp. 659–666.
22. M. Collina, M. Bartolucci, A. Vanelli-Coralli, and G. E. Corazza, “Internet of things application layer protocol analysis over error and delay prone links,” in 2014 7th Advanced Satellite Multimedia Systems Conference and the 13th Signal Processing for Space Communications Workshop (ASMS/SPSC). IEEE, 2014, pp. 398–404.
23. O. Bello, S. Zeadally, and M. Badra, “Network layer inter-operation of device-to-device communication technologies in internet of things (iot),” Ad Hoc Networks, vol. 57, pp. 52–62, 2017.
24. J. Granjal, E. Monteiro, and J. S. Silva, “Security for the internet of things: a survey of existing protocols and open research issues,” IEEE Communications Surveys & Tutorials, vol. 17, no. 3, pp.1294–1312, 2015.
25. I. Ishaq, D. Carels, G. K. Teklemariam, J. Hoebeke, F. V. d. Abeele, E. D. Poorter, I. Moerman, and P. Demeester, “Ietf standardization in the field of the internet of things(iot): a survey,” Journal of Sensor and Actuator Networks, vol. 2, no. 2, pp. 235–287, 2013.
26. T. Salman and R. Jain, “A survey of protocols and standards for internet of things,” arXiv preprint arXiv:1903.11549, 2019.
27. P. Sethi and S. R. Sarangi, “Internet of things: architectures, protocols, and applications,” Journal of Electrical and Computer Engineering, vol. 2017, 2017.
28. S. T. Siddiqui, S. Alam, R. Ahmad, and M. Shuaib, “Security threats, attacks, and possible countermeasures in internet of things,” in Advances in Data and Information Sciences. Springer, 2020, pp. 35–46.
29. J. Dizdarevi´c, F. Carpio, A. Jukan, and X.Masip-Bruin, “A survey of communication protocols for internet of things and related challenges of fog and cloud computing integration,” ACM Computing Surveys (CSUR), vol. 51, no. 6, pp. 1–29, 2019.
30. W. H. Hassan et al., “Current research on internet of things (iot) security: A survey,” Computer Networks, vol. 148, pp. 283–294, 2019.
31. D. M. Mendez, I. Papapanagiotou, and B. Yang, “Internet of things: Survey on security and privacy,” arXiv preprint arXiv:1707.01879,2017.
32. Y.Yang, L. Wu, G. Yin, L.Li, and H. Zhao, “A survey on security and privacy issues in internet-of-things,” IEEE Internet of Things Journal, vol. 4, no. 5, pp. 1250–1258, 2017.
33. K. Zhao and L. Ge, “A survey on the internet of things security,” in 2013 Ninth international conference on computational intelligence and security. IEEE, 2013, pp. 663–667.
34. S. Kraijak and P. Tuwanut, “A survey on internet of things architecture, protocols, possible applications, security, privacy, realworld implementation and future trends,” in 2015 IEEE 16th International Conference on Communication Technology (ICCT). IEEE, 2015, pp. 26–31.
35. A. R. Sfar, E. Natalizio, Y. Challal, and Z. Chtourou, “A roadmap for security challenges in the internet of things,” Digital Communications and Networks, vol. 4, no. 2, pp. 118–137, 2018.
36. D. E. Kouicem, A. Bouabdallah, and H. Lakhlef, “Internet of things security: A top-down survey,” Computer Networks, vol. 141, pp. 199–221, 2018.
37. M.Roberti, “The history of rfid technology,” RFID journal, vol. 16, no. 01, 2005.
38. D.B. Harris, “Radiotransmission systems with modula table passive responder,” Mar. 1, 1960, USPatent 2,927,321.
39. E.C. Jones and C.A. Chung, RFID in logistics: a practical introduction. CRC Press, 2007.
40. K. Ashton et al., “That ‘internet of things’ thing,” RFID journal, vol. 22, no. 7, pp. 97–114, 2009.
41. S.R. Prabhu, “Digital technologies are driving a new generation of telehealth,” March 2014.
42. S. K. Viswanath, C. Yuen, W. Tushar, W.-T. Li, C.-K. Wen, K. Hu, C. Chen, and X. Liu, “System design of the internet of things for residential smart grid,” IEEE Wireless Communications, vol. 23, no. 5, pp. 90–98, 2016.
43. D. Koziol-, F. S. Moya, L. Yu, V. Van Phan, and S. Xu, “Qos and service continuity in 3gpp d2d for iot and wearables,” in 2017 IEEE Conference on Standards for Communications and Networking (CSCN). IEEE, 2017, pp. 233–239.
44. L. E. Nugroho, A. G. H. Pratama, I. W. Mustika, and R. Ferdiana, “Development of monitoring system for smart farming using progressive webapp,” in 2017 9th International Conference on Information Technology and Electrical Engineering (ICITEE). IEEE, 2017, pp. 1–5.
45. M. S. Kiran, P. Rajalakshmi, K. Bharadwaj, and A. Acharyya, “Adaptive rule engine based iot enabled remote health care data acquisition and smart transmission system,” in 2014 IEEE World Forum on Internet of Things (WF-IoT). IEEE, 2014, pp. 253–258.
46. K. A. Kurniadi and K. Ryu, “Development of iot-based reconfigurable manufacturing system to solve reconfiguration planning problem,” Procedia Manufacturing, vol. 11, pp. 965–972, 2017.
47. D. Hanes, G. Salgueiro, P. Grossetete, R. Barton, and J. Henry, IoT fundamentals: Networking technologies, protocols, and use cases for the internet of things. Cisco Press, 2017.
48. A. Mosenia and N. K. Jha, “A comprehensive study of security of internet-ofthings,” IEEE Transactions on Emerging Topics in Computing, vol. 5, no. 4, pp. 586–602, 2016.
49. Z. Bi, L. Da Xu, and C. Wang, “Internet of things for enterprise systems of modern manufacturing,” IEEE Transactions on industrial informatics, vol.10, no.2, pp. 1537–1546, 2014.
50. M. H. Miraz, M. Ali, P. S. Excell, and R. Picking, “A review on internet of things (iot), internet of everything (ioe) and internet of nano things (iont),” in 2015 Internet Technologies and Applications (ITA). IEEE, 2015, pp. 219–224.
51. A. Al-Fuqaha, M. Guizani, M. Mohammadi, M. Aledhari, and M. Ayyash, “Internet of things: A survey on enabling technologies, protocols, and applications,” IEEE communications surveys & tutorials, vol. 17, no. 4, pp. 2347–2376, 2015.
52. J.Mocnej, A.Pekar, W.K.Seah, and I.Zolotova, “Network traffic characteristics of the iot application use cases,” School of Engineering and Computer Science, Victoria University of Wellington, June, vol. 20, p. 2018.
53. M. B. Yassein, M. Q. Shatnawi et al., “Application layer protocols for the internet of things: A survey,” in 2016 International Conference on Engineering & MIS (ICEMIS). IEEE, 2016, pp. 1–4.
54. R. Fielding, J. Gettys, J. Mogul, H. Frystyk, L. Masinter, P. Leach, and T. Berners-Lee, “Hypertext Transfer Protocol – HTTP/1.1,” pp. 1–176.
55. R.T. Fielding and R.N.Taylor, Architectural styles and the design of network-based software architectures. University of California, Irvine, Doctoral dissertation, 2000, vol. 7.
56. I.Fette and A. Melnikov, “Rfc6455: The websocket protocol,” IETF, December 2011.
57. “The simple text-oriented messaging protocol,” 2012. [Online]. Available:” http://stomp.github.io/” Accessed: 2019-07-30.
58. W. Gao, J. Nguyen, W. Yu, C. Lu, and D. Ku, “Assessing performance of constrained application protocol (coap) in manet using emulation,” in Proceedings of the International Conference on Research in Adaptive and Convergent Systems. ACM, 2016, pp. 103–108.
59. C.Bormann, A.P. Castellani, and Z. Shelby, “Coap:An application protocol for billions of tiny internet nodes,” IEEE Internet Computing, no. 2, pp. 62–67, 2012.
60. O. Standard, “Oasis advanced message queuing protocol (amqp) version 1.0,” International Journal of Aerospace Engineering Hindawi www.hindawi.com, vol. 2018, 2012.
61. S. Schneider et al., “Understanding the protocols behind the internet of things,” Electronic Design, vol. 9, no. 10, 2013.
62. O. A. Specification, “Data distribution service for real-time systems version 1.2,” Object Management Group (OMG), 2007.
63. U.D. Protocol, “Rfc768j.postelisi28august1980,” Isi,1980.
64. J. Postel, “Rfc 791: Internet protocol, september 1981,” DarpaInternet Protocol Specification, 1990.
65. J. Iyengar and M. Thomson, “Quic: A udp-based multiplexed and secure transport,” Internet Engineering Task Force, Internet-Draft draft-ietf-quictransport-01, 2017.
66. R. Braden, L. Zhang, S. Berson, S. Herzog, and S. Jamin, “Resource reservation protocol (rsvp)–version 1 functional specification,” Tech. Rep., 1997.
67. R. Stewart, Q. Xie, K. Morneault et al., “Ietf rfc 4960 stream control transmission protocol,” [Online] Available: Onlineverfu¨gbarunter:https://tools.ietf.org/html/rfc4960, letzterZugriffam, vol.1, p. 2018, 2007.
68. R. Stewart, Q. Xie, K. Morneault, C. Sharp, H. Schwarzbauer, T. Taylor, I. Rytina, M. Kalla, L. Zhang, and V. Paxson, “Rfc4960,stream control transmission protocol (sctp),” Internet Engineering Task Force (IETF), 2007.
69. E. Kohler, M. Handley, and F. Floyd, “Rfc4340: Datagram congestion control protocol (dccp),” 2006.
70. S. Floyd and E. Kohler, “Profile for datagram congestion control protocol (dccp) congestion control id 2: Tcp-like congestion control,” Tech. Rep., 2006.
71. K. Nichols, D. L. Black, S. Blake, and F. Baker, “Definition of the differentiated services field (ds field) in the ipv4 and ipv6 headers,” 1998.
72. M. Crawford, “Transmission of ipv6 packets over ethernet networks,” 1998.
73. J. Tan and S. G. Koo, “A survey of technologies in internet of things,” in 2014 IEEE International Conference on Distributed Computing in Sensor Systems. IEEE, 2014, pp. 269–274.
74. M. R. Palattella, N. Accettura, X. Vilajosana, T. Watteyne, L. A. Grieco, G. Boggia, and M. Dohler, “Standardized protocol stack for the internet of (important) things,” IEEE communications surveys & tutorials, vol. 15, no. 3, pp. 1389–1406, 2012.
75. C. Gomez, J. Paradells, C. Bormann, and J. Crowcroft, “From 6lowpan to 6lo: Expanding the universe of ipv6 supported technologies for the internet of things,” IEEE Communications Magazine, vol. 55, no.12, pp. 148–155, 2017.
76. M. R. Palattella, P. Thubert, X. Vilajosana, T. Watteyne, Q. Wang, and T. Engel, “6tisch wireless industrial networks: Determinism meets ipv6,” in Internet of Things. Springer, 2014, pp. 111–141.
77. T. Winter, P. Thubert, A. Brandt, J. Hui, R. Kelsey, P. Levis, K. Pister, R. Struik, J.-P. Vasseur, and R. Alexander, “Rpl: Ipv6 routing protocol for low-power and lossy networks,” Tech. Rep., 2012.
78. A. Aijaz, H. Su, and A.-H. Aghvami, “Corpl: A routing protocol for cognitive radio enabled ami networks,” IEEE Transactions on Smart Grid, vol. 6, no. 1, pp. 477–485, 2014.
79. K. Finkenzeller, RFID handbook: fundamentals and applications in contactless smart cards, radio frequency identification and near-field communication. John Wiley & Sons, 2010.
80. V. Coskun, B. Ozdenizci, and K. Ok, “A survey on near field communication (nfc) technology,” Wireless personal communications, vol. 71, no. 3, pp. 2259–2294, 2013.
81. P. Darbee, “Insteon the details, smarthouse,” Inc., Aug, vol.11, p.68, 2005.
82. K.-H. Chang, “Bluetooth: a viable solution for iot? [industry perspectives],” IEEE Wireless Communications, vol. 21, no. 6, pp. 6–7, 2014.
83. J. Nieminen, C. Gomez, M. Isomaki, T. Savolainen, B. Patil, Z. Shelby, M. Xi, and J.Oller, “Networking solutions for connecting bluetooth low energy enabled machines to the internet of things,” IEEE network, vol.28, no.6, pp. 83–90, 2014.
84. D. Flowers and Y. Yang, “Microchip miwi™ wireless networking protocol stack,” MicrochipTechnology Inc, 2010.
85. Y. Yang, “Microchip wireless(miwi™) application programming interface–miapp,” MicrochipInc. [online] Available at: http://ww1.microchip.com/downloads/en/AppNotes, 2009. Accessed: 2019-10-30.
86. B. Fouladiand S. Ghanoun, “Security evaluation of the z-wave wireless protocol,” Black hat USA, vol. 24, pp. 1–2, 2013.
87. Dynastream Innovations, “ANT Message Protocol and Usage,” pp. 1–34, 2014. [Online] Available: https://www.thisisant.com Accessed: 2019-10-30.
88. R. Sokullu, O. Dagdeviren, and I. Korkmaz, “On the ieee 802.15. 4 mac layer attacks: Gts attack,” in 2008 Second International Conference on Sensor Technologies and Applications (sensorcomm2008). IEEE, 2008, pp. 673–678.
89. I. ISA, “100.11 a-2009: Wireless systems for industrial automation: Process control and related applications,” International Society of Automation: Research Triangle Park, NC, USA, 2009.
90. S. Digimesh, “WIRELESS MESH NETWORKING: Both Zigbee and Digi Mesh offer unique advantages.”
91. S. Farahani, ZigBee wireless networks and transceivers. Newnes, 2011.
92. A. J. Wixted, P. Kinnaird, H. Larijani, A.Tait, A. Ahmadinia, and N. Strachan, “Evaluation of lora and lorawan for wireless sensor networks,” in 2016 IEEE SENSORS. IEEE, 2016, pp. 1–3.
93. S. Sigfox, “Sigfox technology overview,” 2018. [Online] Available: https://www.sigfox.com/ Accessed: 2019-07-30.
94. L.Oliveira, J.J. Rodrigues, S.A. Kozlov, R.A. Rabˆelo, and V.H.C.d. Albuquerque, “Mac layer protocols for internet of things: A survey,” Future Internet, vol. 11, no. 1, p.16, 2019.
95. V. Adat and B. Gupta, “Security in internet of things: issues, challenges, taxonomy, and architecture,” Telecommunication Systems, vol. 67, no. 3, pp. 423–441, 2018.
96. P. Radmand, M. Domingo, J. Singh, J. Arnedo, A. Talevski, S. Petersen, and S. Carlsen, “Zigbee/zigbee pro security assessment based on compromised cryptographic keys,” in 2010 International Conference on P2P, Parallel, Grid, Cloud and Internet Computing. IEEE, 2010, pp. 465–470.
97. Y. Oren and A. Shamir, “Remote password extraction from rfid tags,” IEEE Transactions on Computers, vol. 56, no. 9, pp. 1292–1296, 2007.
98. A. M. Lonzetta, P. Cope, J. Campbell, B. J. Mohd, and T. Hayajneh, “Security vulnerabilities in bluetooth technology as used in iot,” Journal of Sensor and Actuator Networks, vol.7, no. 3, p. 28, 2018.
99. S. Tweneboah-Koduah, K. E. Skouby, and R. Tadayoni, “Cyber security threats to iot applications and service domains,” Wireless Personal Communications, vol. 95, no. 1, pp. 169–185, 2017.
100. M. B. Barcena and C. Wueest, “Insecurity in the internet of things,” Security Response, Symantec, 2015.
101. O. Arias, J. Wurm, K. Hoang, and Y. Jin, “Privacy and security in internet of things and wearable devices,” IEEE Transactions on Multi-Scale Computing Systems, vol. 1, no. 2, pp. 99–109, 2015.
102. J. A. Stankovic, “Research directions for the internet of things,” IEEE Internet of Things Journal, vol. 1, no.1, pp. 3–9, 2014.
103. H. A. Abdul-Ghani, D. Konstantas, and M. Mahyoub, “A comprehensive iot attacks survey based on a building-blocked reference model,” International Journal of Advanced Computer Science and Applications (IJACSA), vol. 9, no. 3, 2018.
104. M.Nawir, A. Amir, N. Yaakob, and O.B. Lynn, “Internet of things(iot): Taxonomy of security attacks,” in 2016 3rd International Conference on Electronic Design (ICED). IEEE, 2016, pp. 321–326.
105. Q. Gou, L. Yan, Y. Liu, and Y. Li, “Construction and strategies in iot security system,” in 2013 IEEE international conference on green computing and communications and IEEE internet of things and IEEE cyber, physical and social computing. IEEE, 2013, pp. 1129–1132.
106. N. Cam-Winget, A.-R. Sadeghi, and Y. Jin, “Can iotbe secured: Emerging challenges in connecting the unconnected,” in Proceedings of the 53rd Annual Design Automation Conference. ACM, 2016, p. 122.
107. J. Deogirikar and A. Vidhate, “Security attacks in iot: A survey,” in 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC). IEEE, 2017, pp. 32–37.
108. W. Xu, K. Ma, W. Trappe, and Y. Zhang, “Jamming sensor networks: attack and defense strategies,” IEEE network, vol. 20, no. 3, pp. 41–47, 2006.
109. P. I. R. Grammatikis, P. G. Sarigiannidis, and I. D. Moscholios, “Securing the internet of things: challenges, threats and solutions,” Internet of Things, 2018.
110. L.Wallgren, S. Raza, and Teviot, “Routing attacks and counter measures in the rpl-based internet of things,” International Journal of Distributed Sensor Networks, vol. 9, no. 8, p. 794326, 2013.
111. L. K. Bysani and A. K. Turuk, “A survey on selective forwarding attack in wireless sensor networks,” in 2011 International Conference on Devices and Communications (ICDeCom). IEEE, 2011, pp.1–5.
112. A. D. Wood and J. A. Stankovic, “Denial of service in sensor networks,” computer, vol. 35, no. 10, pp. 54–62, 2002.
113. K. Zhang, X. Liang, R. Lu, and X. Shen, “Sybil attacks and their defenses in the internet of things,” IEEE Internet of Things Journal, vol. 1, no. 5, pp. 372–383, 2014.
