11
Roadmap of Digital Forensics Investigation Process with Discovery of Tools
Anita Patil*, Soumi Banerjee†, Dipti Jadhav‡ and Gautam Borkar§
Department of Information Technology, Ramrao Adik Institute of Technology, DY Patil deemed to be University, Nerul, Navi Mumbai, India
*Corresponding author: [email protected]
†Corresponding author: [email protected]
‡Corresponding author: [email protected]
§Corresponding author: [email protected]
Abstract
Traditional Computer Forensics seems to be no longer as trivial as decades ago, with a very restricted set of available electronic components, entering the age of digital formation of hardware and software too. It has recently been shown how cyber criminals are using a sophisticated and progressive approach to target digital and physical infrastructures, people and systems. Therefore, the analysis approach faces many problems due to the fact that billions of interconnected devices produce relatively at least small bits of evidence that comprehend the Data Analysis paradigm effortlessly. As a consequence, the basic methodology of computer forensics requires to adapt major attention to develop smart and fast digital investigation techniques. Digital forensics investigation frameworks are occupied with lots of toolkits and applications according to the need of any criminal incident. Using the Digital Forensics Process’s microscope, specific objects are discussed and ana-lysed with respect to which tools are needful. Also, where the scope of attention is required to enhance the feature in it. This research leads to increased awareness, challenges and opportunities for Digital Forensics process with respect to different fields such as networks, IoT, Cloud computing, Database system, Big data, Mobile and handheld devices, Disk and different storage media, and Operating system.
Keywords: Cyber-attacks, anti-forensics, faraday’s bag, data carving, disk forensics, SQL injection, digital forensics
11.1 Introduction
Since the invention of computer and internet facilities researchers have been working on finding vulnerabilities in software and hardware devices. Hackers are continuously trying to bypass the conventional security for personal gain or profit. A criminal uses advanced tools to command and control over a computer system; also, such criminals are trained for how to exploit the vulnerabilities in order to commit any cybercrime activity. There are four factors that are always affected by cybercriminal activities: People, Property, Business and Government agencies. Figure 11.1 shows how different entities are targeted by cybercriminals using different categories of attacks and techniques.
Any computer that is exposed or connected to the Internet is at risk of being hacked and compromised. The popularity of the Internet is not only a shift in our view of life, but also a change in the view of crime in our community or around the world. The growing number of computer criminal activities every day is the justification for a forensic investigation. Digital technology is undergoing an explosion in development and applications. This explosion has given rise to a new concept of cybercriminals and the need for security and forensics specialists in the digital world. The aim of digital forensics is to address investigative or legal questions in order to prove or disprove a court case. In order to ensure that innocent people are not prosecuted and guilty parties are convicted, a full forensic process must be carried out by a competent prosecutor who applies quality control procedures and meets guidelines. With respect to this Digital Forensics play an important role in law enforcement.
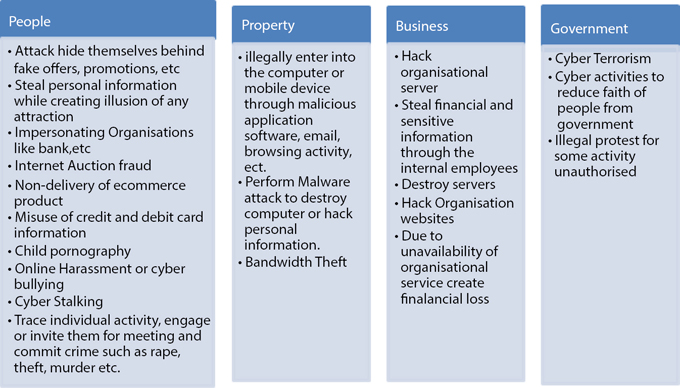
Figure 11.1 Entities affected by criminal activity.
Digital forensics technologies are categories of various domain fields which are listed as follows:
- ➢ Networks Forensic – tracking, recording, preserving and examining network activities to determine the source of security threats, invasions of privacy or other attacks, such as malware, worms or malicious code, suspicious network traffic and privacy violations.
- ➢ Computer and Disk Forensic – Identification, preservation, processing, examination and reporting of information found on computers, gadgets and nonvolatile memory in support of enforcement and court action. Disk forensics is gathering the evidence from volatile memory (RAM) of working desktop or laptop which is considered as live data acquisition.
- ➢ Database system Forensics – Forensic methodology involves data carving from file system and registry also.
- ➢ Big-Data Forensic – Properly gathering and evaluating evidence in big data environments involves a careful approach such that reliable, repeatable findings can be generated for analysis or use in legal proceedings.
- ➢ IOT and smart device Forensic – In-service platforms for IoT systems, such as home automation, intelligent transportation, Agriculture field, medical systems process the data and storage in cloud-based environment. That is one challenge to investigator to manage accuracy and privacy of evidence. In IoT every device is interconnected with each other and stored at least piece of information. The method and techniques are required to make secure interaction between the devices [1].
- ➢ Cloud Computing Forensic – Cloud forensics is a branch of digital forensics focused on a special approach to cloud analysis. Service providers have databases servers all over the world to host user information. In the case of a cyber incident, legal authority and the laws regulating the area raise specific challenges in cloud forensics process.
- ➢ Mobile OS and Storage Forensic – Recovery of electronic data from smartphones, tablets, SIM cards, PDAs, GPSs and handheld devices [2].

Figure 11.2 Domain-wise hierarchy of digital forensics.
According to domain-wise analysis of forensics techniques experts handle and investigate different category of devices and application software. (Figure 11.2 shows a detailed description of evidence collection from different category of digital forensics) [3–6]. There are multiple tools combinedly available for multiple forensic steps. Activities depend on personnel expertise, laboratory conditions, and availability of kits, current regulations and contractual obligations.
Often attackers are now using Artificial Intelligence, Machine Learning, Deep Learning concepts to circumvent traditional security controls. Conventional toolkits are no longer effective over smart criminal activities and another challenge for investigators is anti-forensics.
11.2 Phases of Digital Forensics Process
Working of digital forensics process is divided into four main phases: Identification, Acquisition, Analysis and Reporting as shown in Figure 11.3 [7, 8] and described as follows:
11.2.1 Phase I - Identification
Experts are looking for the equipment involved in the execution of the crime. These gadgets were then carefully examined to obtain information from them. Cyber investigators require a warrant from the police to search the digital properties of the victim or attacker. In addition, they need to comply with the laws established for the processing of devices. At this stage nvestigators involved in this process are officers from law enforcement, network administrator, and Forensics experts. Experts have the responsibility of Identifying and preserving the incident place, storing digital evidence, acquiring data from website and browser, conducting interviews to obtain useful information, and preparing documentation of obtained information.
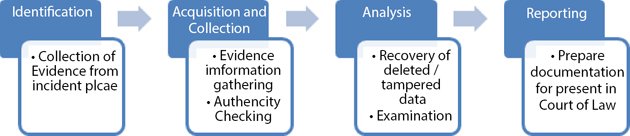
Figure 11.3 Phases of digital forensics process.
11.2.2 Phase II - Acquisition and Collection
Just after the identifying and seizure procedure, experts use forensics toolkits to capture the data. Also, experts have well-defined forensic methods for the handling of evidence. For example, techniques for gathering necessary documents and digital data. Forensic professionals should have access to a secure area where evidence can be collected. They assess if the data collected is precise, genuine and accessible. As proof is a vulnerable type of data, it can easily be altered and destroyed. It is important that digital evidence is treated with care by professionals.
11.2.3 Phase III - Analysis and Examination
The digital forensics investigation must include the evaluation, review and description of the proof. The investigator decides how the data is generated, collects hidden data, matches the pattern, and translates the data into a more acceptable size for examination.
11.2.4 Phase IV - Reporting
First, the findings are based on validated data collection methods; second, other professional forensics experts should be able to reproduce and validate the same results. All the information obtained during the examination process is presented through a written or reported case study. The investigators must summarize all the analytical data from the incident examination phase, explain the validity of the theory, defend it against criticism and competition, and convey the importance of the examination results to a court of law and other law enforcement agencies.
Every phase of the digital forensic process requires a different category of toolkit understanding and knowledge as shown in Figure 11.4. A forensic expert always trusts authenticated and validated tools [8, 9].
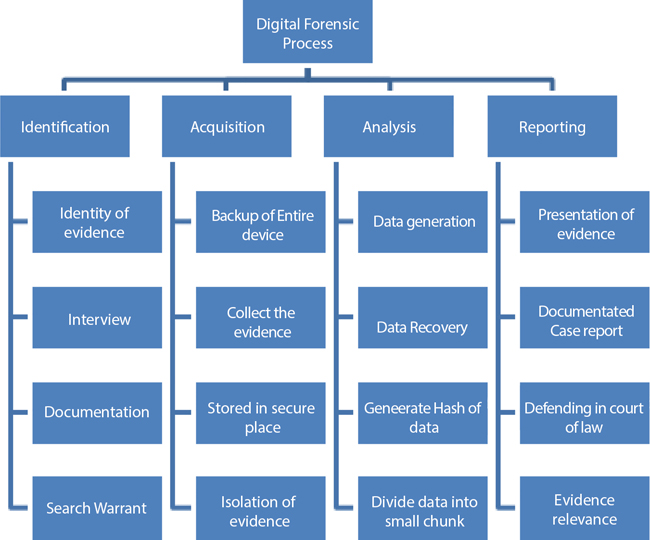
Figure 11.4 Elaboration of digital forensics phases.
11.3 Analysis of Challenges and Need of Digital Forensics
Nowadays almost every single crime is related to a computer or mobile device. As an investigator, digital forensics play an import role to find the evidence from mobile and computer system. There are lots of challenges and limitations which require the attention to improve the forensic process [10, 11].
11.3.1 Digital Forensics Process has following Challenges
- ➢ Increasing usage of electronic gadgets and internet accessibility and continuous change in technology and version.
- ➢ Hacking and anti-forensic tools are easily available.
- ➢ Physical evidence is not properly handled or acquired so it creates difficulty in law enforcement.
- ➢ Required large storage capacity to store evidence image file.
- ➢ Rapid changes in technology requires latest updates and invention in forensics toolkit.
11.3.2 Needs of Digital Forensics Investigation
As digital devices such as computers are vulnerable to criminal attacks, the importance of digital forensics is growing. Understanding automated forensic techniques can help to collect valuable details that can be used to prosecute a criminal who exploits a digital computer or network. Most organizations rely heavily on digital devices and the Internet to run and develop their business, and they rely on digital devices to process, store and recover data.
A cyber-attack is an effort to disrupt or infect computer networks for the purpose of extracting or extorting money or for other malicious purposes, such as obtaining the necessary information as shown in Figure 11.5. Cyber-attacks change computer code, data, or logic by malicious code as shown in Figure 11.6, resulting in problematic results that could compromise the information or data of companies and make it available to cybercriminals [12].
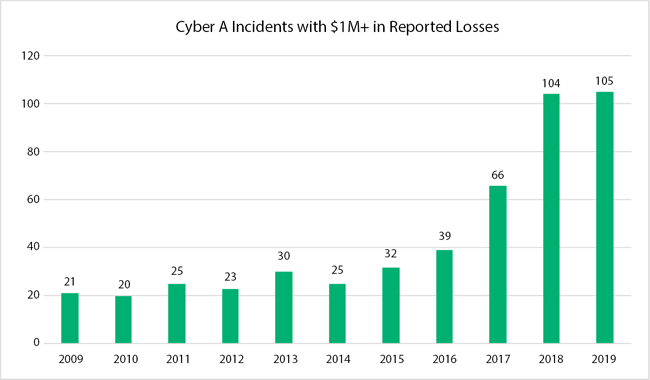
Figure 11.5 Cyber-attack incidents with more than $1 million losses [13].

Figure 11.6 Growth of malware and phishing websites which are used to commit criminal activity [14].
11.3.3 Other Common Attacks Used to Commit the Crime
- ➢ Intellectual Property (IPR) breaching
- ➢ Industrial espionage
- ➢ Employee/Employer dispute
- ➢ Financial Fraud
- ➢ Internet misuse and email fraud or crime
- ➢ Image/video/audio forgeries or morphing
- ➢ Child pornography
- ➢ Violation of Indian IT Act of rules and regulations
11.4 Appropriateness of Forensics Tool
Various options are available for forensic investigation, but it’s tough to pick the proper tool which will suit investigation needs. The following are criteria to decide which tool is better for accurate investigation results.
11.4.1 Level of Skill
Expert technical skill is a key factor when choosing a digital forensic technique and tools. Many resources require basic skills, while others can require specialized expertise. The above Table 11.1 shows how cyber criminals perform malicious activity by performing security attack. The golden thumb rule is to compare good outcomes against what the tool demands, so always select the most effective tool that will simply have the ability to function.
Table 11.1 Criminals and attackers usually perform malicious activity by using the following security attack [15, 16].
| Attack | Activity | Example |
| Hacking | Gain physical command and control over the system | Ransomware |
| Alter functions of hardware and software to cause destructive activity | Stuxnet attack on SCADA system | |
| Steal financial information | Credit card fraud | |
| Steal personal and sensitive information | Harassment cases | |
| SQL injection | Exploit security vulnerability | Valve software industry paid out $25,000 after an SQL injection attack was reported in report_xml. php |
| Attack on less protected SQL database system | SQL injection vulnerability in Vanilla forum website | |
| Access user login details | www.drivegrab.com affected due to SQL injection attack | |
| Retrieve credit and debit card information from vulnerable websites | Uber website is exploited for login credentials | |
| Cross-site scripting | Infect web pages with malicious client-side program code | XSS in steam react chat client |
| Inject malicious script on unprotected applications to steal sensitive or confidential information | Reflected XSS in lert.uber. com | |
| Steal FTP password | Attack happened at website | Many times, attackers use dictionary attack or brute force attack to find the password of around 50 network protocol such as telnet, ftp, http, https, smb to bypass the conventional security logs. |
| Steal FTP login details where the developer stored website login details on unprotected server or PC. | ||
| Virus diffusion | Virus attached with any document or file and spread rapidly over the network | In 2017, Union Bank of India affected due to virus-infected mail attachment opened by bank employee. |
| Virus generally spread through network, USB, RAM, storage media, HDD, emails, infected websites and application software. | ‘Dtrack’ malware use to hacked Kudankulam Nuclear Power Plant (KKNPP) | |
| Logic bomb | Insert malicious code into application software to trigger unauthorised activities | Friday the 13th virus only attack on that specific date |
| Denial of service attack (DoS) | Breached availability of authenticated service | Mirrai Bot attack |
| Flooded network to consume band width of network | DoS attacks specially target high-profile web server handling financial gateways | |
| Phishing | Use to extract banking credentials such as card number, password, etc. | Many bank customers are affected like HDFC, Union Bank of India, Citibank, etc. |
| Use email spoofing | ||
| Email spamming | Attacker send bulk of emails to victim email ID and email server crashes, like DoS attack. | It violates Customer Acceptance User Policy. Almost every user is affected by this attack. |
| Session hijacking | Unauthorizedly take a control over the victim website. | Cracker is using this attack to ransomware or post abusive material on website. |
| Cyber-stalking | Attacker observes the victim’s online activity and performs harassment or blackmailing incident. | Cybercriminal harassed victim through email, chatting, web-site, discussion forum, blogs. Many times this type of attack happened on women. It even leads to suicide condition. |
| Data diddling | Unauthorizedly modify the user entered data and create confusion between users. | Electricity boards in India are affected due to data diddling by attackers. Many cyber attackers use this technique. |
| Identity theft | Steal the personal details and banking information and pretended an authenticated use to perform illegal transactions | Credit and debit card fraud |
| Salami fraud attack | Criminals steal bits of services or money so it is undetected with respect to huge volume of data. | Banking fraud like HDFC, etc. |
| Privacy breaching | Crackers use software, download free movies, use crack key values to use applications, etc., are belongs to this category | Pirated downloads such movie, song, software may consist of attachment of malicious code. |
| SIM swapping | Unauthorizedly gain access to victim SIM cards and illegally stealing financial details. | Hacker blocked victim’s SIM card and performed transaction via online banking so OTP number does not go to victim. |
11.4.2 Outputs
Tools are not built as equivalent, so outputs can differ even within an equivalent group. A few of the toolkits generate data; some tools generate a whole report. Data generated by a tool is sufficient to present in a court of law but sometimes it requires processing of information.
11.4.3 Region of Emphasis
According to examination procedure tool requirement is dependent on what task is to be performed. Like in network analysis Wireshark is used to collect log file dumpit used to analyze the log files.
11.4.4 Support for Additional Hardware
Many tools require some additional software support or live-CD to run and work with it. Like mobile forensics, a toolkit depends on hardware and software version and also requires support from third-party software.
11.5 Phase-Wise Digital Forensics Techniques
11.5.1 Identification
Identification defines possible repositories of sensitive information/evidence as well as key custodians and data locations. Identification process must follow the things listed below:
- ➢ Search warrant release from authorized body to seize the evidence from incident place as shown in Figure 11.7.
- ➢ It is important to conduct other forensic procedures on the evidence, e.g., Analyzing DNA, fingerprinting, etc.
- ➢ Decide if other forensic paths need to be followed, such as giving an Internet service provider (ISP) a conservation order, discovering remote storage facilities, acquiring e-mail.
- ➢ Define the essence of the possible proof being pursued (e.g., images, spreadsheet applications, documentation, records, accounting transactions, etc.
- ➢ It is possible to acquire detailed information (such as email IDs, ISP, network configuration details, system logs, password files, user details, etc.) through interviews with the system administrator, customers, and personnel.
- ➢ Non-computer devices or material could be used in cases of crime or theft, such as for banking details, credit/debit cards, scans documents, scanners data, and printers and buffering information.
- ➢ Professional users can use sophisticated methods to hide or destroy evidence (e.g., data encryption, traps, Steganography technique).

Figure 11.7 Evidence bag and faraday bags [15].
11.5.2 Acquisition
Digital forensics evidence is fragile and sensitive. As such, the improper handling of this evidence will undermine the whole law enforcement operation. Owing to the vulnerability and volatility of forensic evidence, certain protocols must be followed to ensure that the data are not altered during collection, transition and storage. These defined procedures detail the data handling phases and the protocols to be followed during data acquisition as shown in Figure 11.8. Digital information is sensitive and by careless processing or inspection, may be quickly distorted, damaged or lost. Even the process of opening files will modify the timestamp records, removing information about the last time the file was opened. Failure to do so will make it unusable or lead to an incorrect inference evidence, including the duplication and reconstruction of evidence from any evidence. It includes generating a disk image from digital devices, including CD-ROMs, hard drives, portable hard drives, laptops, flash drives, gaming consoles, server, and other computer technology that can store digital information. Figure 11.9 shows Disk Partitioning for recovery of tampered and deleted file/document.
The data acquisition phase creates an image of extracted data without missing a single bit. If available evidence is 1TB size then same size of information is retrieved. This information extracted from all parts of disk drive such as a blank, unused and unallocated space. The same procedure applies on a different operating system platform and third-party software. Figure 11.10 shows USB drive scanning using Autopsy software to recover deleted files [19, 20].
Figure 11.11 shows creation of memory image of hard drive. This image file can be examined using Encase or FKT toolkit.
USBD view use to find the information about connected external drives or devices to computer or laptops as shown in Figure 11.12. This information is useful to analyze and examine the data transmission from one device to other.

Figure 11.8 Procedure of data acquisition.

Figure 11.9 Disk partitioning for recovery of tampered and deleted file/document [17].
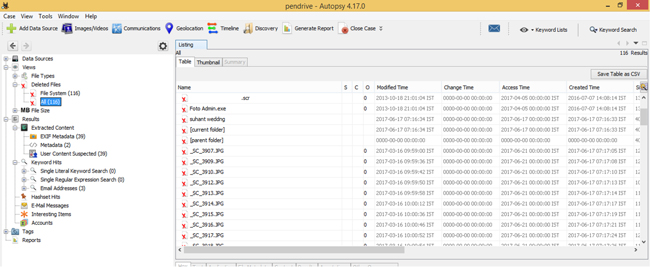
Figure 11.10 Sample of recovery of deleted data from USB using autopsy tool.
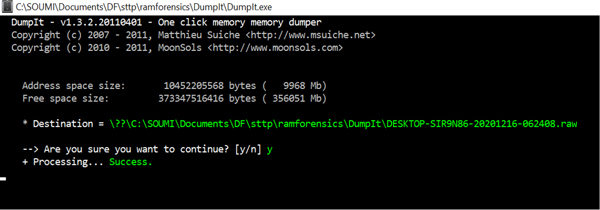
Figure 11.11 Collection of memory dump using Dumpit software.
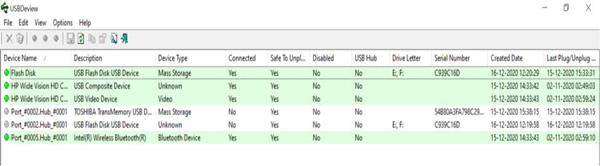
Figure 11.12 Collection of information about the USB devices connected to a system.
11.5.3 Analysis
Digital Forensics is examining the evidence which will be acceptable or admissible in a court of law. Analysis is essential for investigating the incident so digitally recorded evidence must be preserved with proper precaution. Proof must be maintained and no one can alter evidence during the investigation process. For this reason, the best legal outcome would be the study of the forensic image or the duplicate of the device as opposed to the original device or source. Analysis is the process to answer when, what, who, where and why questions related to evidence. This phase is Documented with the following details:
- ➢ General information about the incident: Information about infrastructure of organization and incident place. Many court disputes have also emerged with regard to client lists, which can be considered valuable intellectual property like dispute in staff, misappropriation of company documents, theft or divorce, etc.
- ➢ Goal analysis: Identify the actors involved on the victim and attacking side.
- ➢ Timeline of chain of custody: The time, date data usage log, employee behavior on digital platform taken into custody with respect to acquiring time and date.
- ➢ Recovered and infected data: Logical data is actual information available on evidence device. Such as document files (Word, Excel, pdf), images, email, information available on social media, temporary deleted files available in trash. Deleted or infected files require special software to recover them.
- ➢ Data leakage: Illegal transmission of data from one organization to the other. Use of USB or other storage media or IoT devices in company premises.
- ➢ Important keyword: Special keywords used to perform malicious activity like the name of authenticated employees [18].
11.5.3.1 Data Carving
Data carving is a technique to recover the deleted and hidden files from digital evidence. Hidden files are available in unused space, slack space, lost cluster of a disk. File header is extracted from disk to recover the hidden file. This continues until file gets completely extracted while detecting end of file. Carving also validates the file to be retrieved from a disk. Data carving is not taking any information related to the file system.
In an advanced operating system, without user permission file or document is not deleted. It always prompts a message to the user about deletion of a file. Such files are recoverable because the space of a deleted file is not allocated to another file. In case of tampered and damaged file recovery it is difficult if the file is overwritten. To recover such a file system structure is used to identify the file system like FAT, NTFS, etc., and analyses the information about deleted file and recovers it like image file, pdf, Word doc, etc. File system always stores, recovers and upgrades according to the different data presentation format. The following Table 11.2 shows how different file systems are analyzed and data is recovered.
Table 11.2 Different file system uses to analyze and recover the file [21].
| Operating system | File system type | Description |
| Windows | FAT, FAT12, FAT16, FAT32 | Boot-sector, allocation table, storage media, files and directory. File system size is up to 32GB |
| NTFS | File system size is more than 32GB Support to encryption and access control policies | |
| Linux | Ext2, Ext3, Ext4 | Support to transactional file write. It also optimized file allocation and file attribute information. |
| Reiser FS | Stored large number of small size documents Searching is easy Use metadata allocation to search any file | |
| XFS | IRIX server developed by SGI Use in storage media | |
| JFS | Mostly use in Linux platform It uses in powerful computing server systems. | |
| MacOS | HFS, HFS+ | Use in Mac iPods, iPhones, Apple X server, desktop, etc. |
| Apple Xscan | Use in advanced server system | |
| clustered FS | Developed from StorNext or CentraVision It is used to store file, folder, metadata about file (such as view, access and window position of file handler). |
11.5.3.2 Different Curving Techniques
The digital forensic investigator is dealing with a big challenge to analyse data from different category devices with variety of hardware and software platform. Acquired data is always not in a specific format such as sms, mails, electronic records, framework log files, and mixed media records. Data carving depends on structure and form of information [22]. The following Table 11.3 shows the details of different carving techniques.
Table 11.3 Details of different carving techniques [23, 24].
| Type of carving | Description | How to investigate | Tools |
| Header/footer carving | Recover files based on known header and footer or size of file is maximum |
| Scalpel FTK Encase Foremost PhotoRec Revit TestDisk Magic Rescue F-Engrave |
| File structured base carving | Uses internal layout of document |
| |
| Contentbased carving | Content structure (MBOX, HTML, XML) is not in proper format |
|
In following Figure 11.13, JPEG file starts with header FFD8FFE0 which is the identification of data or recovery evidence in an image file.
Footer value is ended with FFD9, shown in Figure 11.14, which mention the end of .jpeg file and collect evidence.
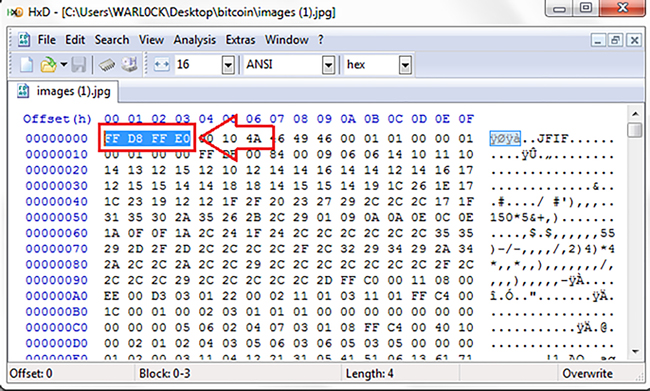
Figure 11.13 Recovery of JPEG image file with detailed information about starting header FFD8FFE0 [24].

Figure 11.14 Recovery of JPEG image file with detailed information about starting Footer is ended as FFD9 [24].
11.5.3.3 Volatile Data Forensic Toolkit Used to Collect and Analyze the Data from Device
Forensic analysis is also dependent on memory type like volatile and non-volatile. Table 11.4 and Table 11.5 describe the functioning of different volatile and non-volatile memory analysis tools.
Table 11.4 Description of volatile data forensic toolkit [25].
| Tools | Use | Outcome |
| Rootkit revealer | Detect information about system and user mode kernel | Date and time of system, volatile storage information about RAM. |
| Process explorer | Extract information about daemon, running and interconnected processes. | Details of user’s logging, running processes, loaded libraries, use of resources, etc. |
| TCPview | Collect network configuration details | Information about open port, Wi-Fi, Bluetooth, wired network, etc. |
| Blacklight | Analyze computer and mobile device memory. Work with Android OS, Window, iOS and MacOS X. | Detailed information about user access logs, content search from phone numbers, addresses, URLs, etc. |
| Volatility | Analyze runtime system using data collected from volatile memory. Available for Windows, MacOS X and Linux OS. | Gather information about network connection and configuration, open socket, running process, process DLL process, cached registry hives, etc. |
| SANS SIFT | Use for perform in depth forensic examination. Support to AFF, dd, E01 format. | Toolkit consists of:
|
Figure 11.15 shows analysis of memory dump collected in WinHex tool. WinHex generates a hexadecimal file which uses an editor tool for Windows OS. This tool is very important in digital forensic use for recovering deleted data and tampered data.
Figure 11.16 shows Image duplication of a USB using FTK toolkit. The FTK Imager is used to recontruct the image or backup of available evidences in hard disk. This image file is stored as single file such as a conversion of .E01 file into RAW file. The FTK Imager toolkit also recovers deleted files.
Table 11.5 Description of non-volatile data forensic toolkit [26].
| Tools | Use | Outcome |
| SANS SIFT | Log2timeline used to generate timeline from syslog, Scalpel for carving files, Rifiuti use for examine recycle bin. Compactible with Linux and Windows OS | Analyze E01, AFF, dd proof format |
| CrowdStrike Crowd Response | Consist of directory list, active running process, and YARA process module. It scans memory, loaded module file and disk files. | Collect contextual records and files consist of procedure list, scheduled task and Cache records. |
| The Sleuth Kit (+Autopsy) | Complete analysis of file system. Provides timeline analysis, hash filtering, keyword analysis. Sleuth Kit is works in Linux OS and Autopsy work in Windows OS. | Retrieve and analyze information from SMS, call log, contact details, chat. |
| FTK Imager | Provide support for mounting image of drives. It creates hash using MD5 or SHA1. It works in Windows OS. | Analyze image of complicated drives, hardware support drives, CD/DVD, and snapshot or memory dump. |
| dd command | It works in Linux OS. It can erase a disk completely so always use carefully. | Cloning of data across file/document, device, partition, and memory. |
| CAINE | It works in Linux platform. Provides user pleasant GUI, semiautomatic documents description, Mobile Forensic, Network Forensic, Data Recovery, etc. | Gives in-depth forensic analysis report which are easily editable and exportable. |
| Free hex editor neo | Search pattern from large database system. Image forensics is also analyzing. | Data carving, identify low stage document modification, collect records and retrieve hidden files. |
| Bulk extractor | Use for laptop forensics to scans a disk, files, or listing document and extracts information such as credit score card number, domain, email address, URL, and ZIP document, etc. | Collect and analyze all information available in hidden format in textual content script format. |
| DEFT | Works in Linux OS, Android and IOS. Provide support to network, mobile, database forensics. Also support hashing of image file. | Provide incident response details. |
| Xplico | Work as network forensics toolkit and extract data from network traffic. It extract e-mail message from POP, IMAP and SMTP protocol traffic. | Provide log details from HTTP, SIP, IMAP, TCP, UDP, SQL and SQLite database system. |
| Last activity view | Extract user activity on computer or another handle device. Works on only Windows 200 and high versions. | Extract an executable program, Explorer folder, details of crash application or device and software installer. |
| DSi USB write blocker | It prevents write access to the USB media. | It avoids alteration of available evidence in metadata, date and timestamp. |
| FireEye RedLine | Perform analysis in host memory and file system. | Collect and analyze threat assessment profile, running process, drivers, metadata of file system, registry, event logs, network, facilities details, tasks, and browsing history. |
| PlainSight | Recover files such as jpg, png, pdf, mov, wav, zip, rar, exe. | Extract data from broswer history, carving data, gathering information about USB media use, examine physical memory dump, extracting hash of password, etc. Generate result in plaintext and HTML format. |
| Paladin forensic suite | It is Ubuntu based toolkit. There are more than 80 tools are available. Works with MacOS, Windows Linux platform. | Provide result of image, mobile, network, cloud, IoT imaging tools, malware analysis, social media analysis, hashing tool, etc. |
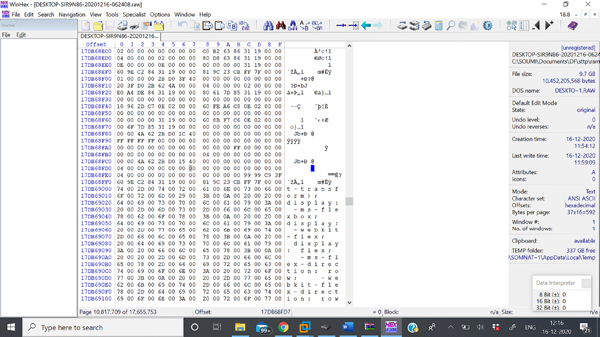
Figure 11.15 Analyzing the memory dump collected Dumpit in WinHex tool.
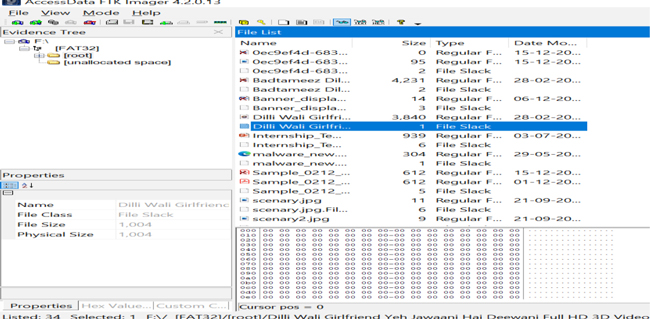
Figure 11.16 Image duplication of a USB using FTK toolkit.
11.5.4 Report Writing
Digital forensic investigation is more effective when evidence is presented in a court of law in an admissible manner. There are different types of documentation of evidence such as
- 1. Summary report: Forensic expert written report as step-bystep execution of investigation process and summarized the proof with proper conclusion of incident response. Summary report consists of analysis report generated by forensic toolkit, which evidence/devices are examined, gathered information, etc.
- 2. Report must be clear and avoid confusion regarding date of acquisition, format, heading to document, avoid misguidance to opposite party.
- 3. Report should be accurate to answer the following question:
- ➢ Image file of all analyzed files
- ➢ Verify the system time during acquiring
- ➢ Operating system details
- ➢ Forensics toolkit details
- ➢ Technical details of forensic hash image
- 4. The examiner verifies the search contents are not tampered during the acquiring and investigation process. Summary report gives all detailed information about data received to the law enforcement officer; it is the same as found by the forensics examiner. In the referred to case, there were supposedly illegal pictures downloaded from the litigant by the police; however, no pictures were discovered anyplace on the PC framework. That in itself is fascinating from a criminological viewpoint and perceive what the proof appeared.
- 5. Given a perfect conclusion about how evidence is collected, examined and presented with detailed explanation, all detailed information should be admissible in a court of law.
11.6 Pros and Cons of Digital Forensics Investigation Process
With respect to good forensic expert knowledge and resource availability investigation process provides better accuracy and faith on law of enforcement.
11.6.1 Advantages of Digital Forensics
- ➢ Avoid alteration of acquired evidence such as mobile phone, laptop, etc.
- ➢ Appropriate evidence handling and identification makes juristic process more clear and trustworthy.
- ➢ Business organization can use to analyze the network traffic identify the attacker’s activities if system get affected.
- ➢ Use to trace criminal activities with instant record of criminal.
- ➢ It is used to protect intellectual property, financial transactions.
- ➢ Digital forensics is used to retrieve, analyze the process, and identify actual evidence to present against cybercriminals in the court.
11.6.2 Disadvantages of Digital Forensics
- ➢ If digital evidence is tampered or altered during acquisition and analysis phase then it is not admissible in a court of law.
- ➢ Digital evidence requires large storage capacity so it increases the cost of resources and hardware requirement.
- ➢ Law enforcement officers and technical team have to be well trained and have expertise in computer handling.
- ➢ Process has to generate a trustworthy and authenticated report which is easily accepted by a court of law.
- ➢ Lack of resource availability disallows following proper toolkit standard.
- ➢ Due to lack of technical background evidence and device are not properly handled by examiner.
11.7 Conclusion
The study of digital evidence poses a variety of primary challenges. Current digital forensic methods have the ability to resolve these issues. Also using Machine learning and Artificial Intelligence current techniques will provide better accuracy. However, much of the study carried out focuses on processes and threads in memory forensics. But, aside from these records, memory retains a variety of other data that have forensic value when investigating crimes. Since malware writers have begun to reduce their footprint on victims’ hard drives, it is difficult to track the activities conducted by these malwares from the examination of hard drives. Improvements in traditional forensic methodologies have also become important in the investigation of crimes. In volatile memory forensics method, the instability of RAM data leads to different challenges in analyzing and acquiring data. This chapter presented an analysis of different forensics techniques and toolkit used to investigate the incident and present evidence in a court of law. This chapter focused on a survey of how experts can decide and identify the need of forensics toolkits and the direction of the investigation process.
References
1. Shalaginov A., Iqbal A., Olegård J., IoT Digital Forensics Readiness in the Edge: A Roadmap for Acquiring Digital Evidences from Intelligent Smart Applications. In: Katangur A., Lin SC., Wei J., Yang S., Zhang LJ. (eds.) Edge Computing – EDGE 2020. Lecture Notes in Computer Science, Volume 12407. Springer, Cham., 2020.
2. A. Al-Dhaqm, S. A. Razak, R. A. Ikuesan, V. R. Kebande and K. Siddique, “A Review of Mobile Forensic Investigation Process Models,” in IEEE Access, Volume 8, pp. 173359-173375, 2020.
3. Mohammmed S., Sridevi R., A Survey on Digital Forensics Phases, Tools and Challenges. In: Raju K., Govardhan A., Rani B., Sridevi R., Murty M. (eds) Proceedings of the Third International Conference on Computational Intelligence and Informatics. Advances in Intelligent Systems and Computing, Volume 1090. Springer, Singapore, 2020.
4. J. Hou, Y. Li, J. Yu and W. Shi, A Survey on Digital Forensics in Internet of Things, in IEEE Internet of Things Journal, Volume 7, pp. 1-15, 2020.
5. Rupali Chopade, V. K. Pachghare, Ten years of critical review on database forensics research, Digital Investigation, Volume 29, pp 180-197, ISSN 17422876, 2019.
6. Konstantia Barmpatsalou, Tiago Cruz, Edmundo Monteiro, and Paulo Simoes, Current and Future Trends in Mobile Device Forensics: A Survey. ACM Computing Survey Volume 51, Issue 3, Article 46, pp. 1-31, 2018.
7. Rodney Wilson and Hongmei Chi, A Case Study for Mobile Device Forensics Tools. In Proceedings of the South-East Conference (ACM SE ‘17). Association for Computing Machinery, New York, NY, USA, pp. 154–157, 2017.
8. G. Shrivastava, K. Sharma and R. Kumari, Network forensics: Today and tomorrow, 3rd International Conference on Computing for Sustainable Global Development (INDIA Com), New Delhi, pp. 2234-2238, 2016.
9. L. Chen, L. Xu, X. Yuan and N. Shashidhar, Digital forensics in social networks and the cloud: Process, approaches, methods, tools, and challenges, International Conference on Computing, Networking and Communications (ICNC), Garden Grove, CA, pp. 1132-1136, 2015.
10. N. Raza, Challenges to network forensics in cloud computing, Conference on Information Assurance and Cyber Security (CIACS), Rawalpindi, pp. 22-29, 2015.
11. Ameer Pichan, Mihai Lazarescu, Sie Teng Soh, Cloud forensics: Technical challenges, solutions and comparative analysis, Digital Investigation, Volume 13, pp. 38-57, ISSN 1742-2876, 2015.
12. Ademu Inikpi & Imafidon Chris., The Need for Digital Forensic Investigative Framework. International Journal of Engineering Science, Volume 2, Issue 3, pp. 388-392, 2012.
13. Casey Crane, 42 Cyber Attack Statistics by Year: A Look at the Last Decade, https://sectigostore.com/blog/42-cyber-attack-statistics-by-year-a-look-at-the-last decade/, 2020.
14. Google Transparency Report, https://transparencyreport.google.com/safe-browsing/, 2020.
15. Patil A., Shinde S., & Banerjee S., Stuxnet-Tool for Zero-Day Attack, Handbook of Research on Cyber Crime and Information Privacy, pp. 652-675, IGI Global, 2021.
16. Banerjee S., Shinde S., & Patil A., An Experimental Analysis on Detection of Corona Virus Malware Attacks and Its Preventive Measures, Handbook of Research on Cyber Crime and Information Privacy, pp. 66-87, 2021.
17. Black Hole Faraday Bag Kit, https://images.app.goo.gl/JYihsisVj8Jttsx7A
18. Guido, M. & Buttner, J. & Grover, J., Rapid differential forensic imaging of mobile devices. Digital Investigation, Volume 18, pp. 46-54, 2016.
19. Casey, Eoghan & Stellatos, Gerasimos, The impact of full disk encryption on digital forensics. ACM SIGOPS Operating Systems Review, Volume 42, Issue 3, pp. 93-98, 2008.
20. Balakrishnan Subramanian, An Overview of Autopsy: Open-Source Digital Forensic Platform https://datascience.foundation/sciencewhitepaper/an-overview-of-autopsy-open-source-digital-forensic-platform-1, 2020.
21. Nadeem Alherbawi, Zarina Shukur, Rossilawati Sulaiman, Systematic Literature Review on Data Carving in Digital Forensic, Procedia Technology, Volume 11, pp. 86-92, ISSN 2212-0173, 2013.
22. Raghavan, Sriram, Digital forensic research: Current state of the art. CSI Transactions CSIT, Volume 1, Issue 1, pp. 91–114, 2013.
23. Povar, D. and Bhadran, V. K Forensic Data Carving, in Digital Forensics and Cyber Crime, Volume 53, pp. 137-148, 2012.
24. Warlock, File Carving, https://resources.infosecinstitute.com/topic/file-carving/, 2018.
25. Spafford E. Some Challenges in Digital Forensics. In: Olivier M.S., Shenoi S. (eds.) Advances in Digital Forensics II. Digital Forensics 2006. IFIP Advances in Information and Communication, Volume 222, pp. 3-9, Springer, Boston, MA, 2006.
26. Adrian Lane, Database tools for auditing and forensics published in SearchSecurity.com E-Guide Database tools for auditing and forensics, 2010.
