9
Ensuring Secure Data Sharing in IoT Domains Using Blockchain
Tawseef Ahmed Teli1*, Rameez Yousuf2 and Dawood Ashraf Khan2
1Department of Computer Sciences, Cluster University Srinagar, Srinagar, India
2Department of Computer Sciences, University of Kashmir, Srinagar, India
*Corresponding author: [email protected]
Abstract
Data in IoT domains is significantly analysed and the information is mined as required. The results from the devices are then shared among the interested devices for better experience and efficiency. Sharing of data is rudimentary in any IoT platform which increases the probability of an adversary gaining access of the data. Blockchain, which consists of blocks that are connected together by means of cryptographic hashes, SHA256 being the most popularly used hash function in the blockchain network, is a newly adapted technology for secure sharing of data in IoT domains. A lot of challenges involving the integration for blockchain in IoT has to be addressed that would ultimately provide a secure mechanism for data sharing among IoT devices.
Keywords: IoT, mining, sharing, SHA, adversary, cryptographic, blockchain
9.1 IoT and Blockchain
Internet of Things (IoT) pertinently is comprised of a conglomerate of millions and billions of devices that are connected over the internet throughout the world. The aim of IoT is to make all the objects intelligent and smart and to collect information form the physical devices, share the data and communicate it back for processing and analysis. This notion of making every object around us and sensors intelligent started way back in the 1980s but due to the large-sized chips and ineffective communication technologies this technology did not accelerate much. With the advent of low power and very cheap chips as well as the RFIDs that communicate wirelessly this technology became what it is today.
IoT technology enables problem-solving tools without any human intervention. IoT is a booming technology with sensors that are cheap and easy to install and ubiquitous wireless sensor networks. From a small tablet to a ship everything is now part of IoT facilitating all the devices to provide data in real time, share the data and learn from the data. The architecture of IoT consists of three layers [1] as shown in Figure 9.1 below:
- • Perception Layer: This is the lowest layer in IoT architecture and consists of sensors and actuators. This layer is responsible for the collection of data from the environment where the sensors are deployed such as smart watch, WSN, temperature, humidity, etc.
- • Network Layer: It is the middle layer of the IoT architecture and consists of IoT protocols such as Bluetooth, ZigBee, Z-Wave, 6LoWPAN, Thread, LTE-M1and Dash7. The function of this layer is to connect devices with one another via a network connection. It is also responsible for the transmission and processing of sensor data.
- • Application Layer: This is the top layer in IoT architecture and provides the interface between the IoT devices and the network. Some of the protocols which operate in this layer are MQTT, SMQTT, XMPP, M3DA, JavaScript IoT, and Websocket.

Figure 9.1 Architecture of IoT.
IoT usually consists of devices that would not normally have an internet connection like a light bulb, a thermostat and a toy, etc., and these devices operate independently without any sort of human intervention. The applications of IoT are vast, encompassing not only industry (machine-to-machine) IoT but also smart homes and offices.
The number of devices connected to this technology is a direct estimate of the size of IoT. It is predicted that 41.6 billion devices shall be a part of IoT by 2025. Also, a total of 5.8 billion devices from automotive and industrial sectors alone were connected by the end of 2019. Table 9.1 depicts the size of IoT by 2020 (last three years), the data provided by Gartner.
One must have understood till now that IoT is not just a single technology but a collection of many myriad technologies including electronic technologies, communication and information technologies, etc., as well as the new analytical and computing technologies. The combination of all such technologies tends to make IoT very complex and very hard to manage.
The complexity in the integration of heterogeneous devices and networks as well as the distributed character of devices in IoT makes the process of authentication a nightmare. The solution is a central authority. Allowing any non-authenticated device to connect to the IoT would result in a security risk that might lead to data spoofing and other security concerns. Hence, a central authentication authority is a mandatory body to attain the smooth and secure functioning of IoT. However, this central authority comes with disadvantages, one of the most significant of which is bottleneck. To cater to the security issues in IoT, the central authority can be removed and a distributed ledger-based Blockchain technology can be used. Now, what is Blockchain?
Table 9.1 IoT devices (source gartner).
| Category | Year–2018 | Year–2019 | Year–2020 |
| Services/utilities | 0.98 | 1.17 | 1.37 |
| Automotive | 0.27 | 0.36 | 0.47 |
| Government | 0.40 | 0.53 | 0.70 |
| Building automation | 0.23 | 0.31 | 0.44 |
| Transportation | 0.06 | 0.07 | 0.08 |
| Information | 0.37 | 0.37 | 0.37 |
| Healthcare | 0.21 | 0.28 | 0.36 |
| Wholesale/Retail | 0.29 | 0.36 | 0.44 |
| Manufacturing & Natural Resources | 0.33 | 0.40 | 0.49 |
| Physical Security | 0.83 | 0.95 | 1.09 |
| Total | 3.96 | 4.81 | 5.81 |
Blockchain technology is the single most pertinent technology after the invention of the Internet. After it was used in Bitcoin [2] way back in 2008, the real potential of this technology was seen.
Hence the application area of Blockchain technology has grown far ahead of cryptocurrencies and covers almost anything you can think of, e.g., medical, voting, fraud and intrusion detection and logistics (Supply Chain Management). Unlike IoT, Blockhcain technology is decentralized; no single central authority exists. All the operations and transactions in a blockchain are performed by peer-to-peer devices in the network. This technology is also referred to as distributed ledger because the blockchain ledger is stored on multiple participating computers rather than on a single central server. The consistency of this ledger is maintained using consensus algorithms [3]. Apart from the distributive nature of blockchain, some of the characteristic features are as follows:
- • Immutable
- • Anonymous
- • Transparent
- • Secure
Technically, blockchain is a collection of blocks with links that are essentially cryptographic hashes [4]. One of the most popular hashing techniques used in blockchain network is SHA256 [5]. The information contained in a block of a blockchain comprises data, hash of the previous block and its own hash. The first block of a blockchain is called genesis block or block 0; this block does not contain any previous hash [6]. Figure 9.2 shows the architecture of a block chain.
There are three types of blockchain systems [7–9]:
9.1.1 Public
This type of blockchain is decentralized and visible to every user. It is specifically used for solving fraud and issues related to security that mostly adhere in traditional financial bodies. Also, the code is open to everyone;
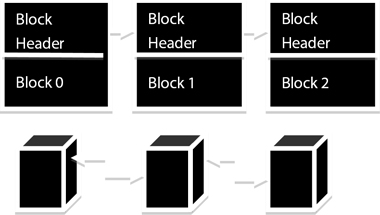
Figure 9.2 Blockchain architecture.
each participant is enabled to access the blockchain and can participate in the consensus process. The transactions are all anonymous in this public blockchain. Also, this technology has zero infrastructure expenses. The consensus algorithms used in this blockchain are as under:
- • Proof of Work (PoW)
- • Proof of Stake (PoS)
- • Delegated Proof of Stake (DPoW)
Bitcoin and Ethereum use public blockchain.
9.1.1.1 Proof of Work (PoW)
The concept of Proof of Work (PoW) comes into play when a difficult task—difficult in terms of the computations and energy required—is given to the miners for solution. After a certain amount of time that is due to solve the problem, the solution is verified easily and the new block is added to the blockchain. PoW is vulnerable to 51% attack in which a miner with the majority of the mining power can control the consensus. It is a direct consequence of computational energy consumption. PoW also suffers from some issues related to latency. Other mechanisms based on Proof of Work for consensus include Leased Proof of Stake (LPoS), Proof of Burn (PoB) and Proof of Importance (PoI).
9.1.1.2 Proof of Stake (PoS)
Proof of Stake (PoS) is another mechanism for consensus in blockchain in which the significance of a person in the network is characterized by the amount of coins he/she holds which directly suggests the work these people shall put in for the normal and smooth functioning of the network. People have to put some units of crypto at stake to verify the transactions. The only drawback of this network is that it tends to make the rich people richer.
9.1.1.3 Delegated Proof of Stake (DPoS)
In Delegated Proof of Stake, witnesses are selected using votes to validate or verify the transactions. The witnesses who would collect the most number of votes are given the authority to validate a transaction. A user has the ability to delegate the voting power to a trustworthy user for the selection of witnesses. It may be noted that the votes are directly consequential to the user’s/voter’s stake.
9.1.2 Private
This type of blockchain is restricted in nature and visible to limited users. It is specifically used for verification of operations internally and database management. Also, the code is not open to everyone. Write permissions are also given to a single central organization. Since it has a central system aspect, private blockchain is vulnerable to security breaches like any other centralized system. Also, this technology has zero infrastructure expenses. The consensus algorithms used in this blockchain are as under:
- • practical Byzantine Fault Tolerance(pBFT)
- • Reliable, Replicated, Redundant, And Fault-Tolerant (RAFT)
MONAX and Multichain use private blockchain.
9.1.3 Consortium or Federated
This type of blockchain is controlled and restricted in nature. It is operated by a group of organizations rather than a single party and any user with access to the internet cannot be involved in the verification process of transactions. Also, this type of blockchain is faster than any of the other types and provides more privacy and scalability. The transactions are all performed at a reduced cost and redundancy. No consensus algorithms used in this blockchain. R3 (Banks) and EWF (Energy) used in Consortium blockchain. Some of the features of consortium blockchain include:
- • Faster speed
- • Scalability
- • Low transaction costs
- • Low energy consumption
- • Risk of 51% attack mitigated
- • Mitigated criminal activity
- • Regulations
9.2 IoT Application Domains and Challenges in Data Sharing
It has already been established that IoT is present everywhere and possibly every device is and will be connected to this technology in the near future. Hence, the applications cover almost every sphere and aspect of life as it uses the cheap, lower power consumption, limited capacity processors and memory [10]. The application domain area of IoT has also been reported by [11]. Some researchers [12] divided the application domains of IoT into five categories. Figure 9.3 depicts the complete domain areas of IoT.
Data in IoT is the single most major entity in the whole paradigm. The data could be any of the following types in IoT:
- • Transformed
- • Data in Transit
- • Stored
- • Generated
Heterogeneity of networks and devices in IoT make data collection and sharing one of the major challenges. Some researchers like [13] have pro-foundly emphasized the challenge of data sharing and the criticality of data exchange among multiple heterogeneous networks. Also, the challenge comes while we try to integrate data that is random and raw in nature to mine something meaningful before sharing it. It was also discussed by [14] that the transformation and exchange of noisy data and data that comes from the real world into meaningful information-rich data poses a grave challenge. Traditional interfaces for data sharing in IoT also present a greater challenge for information exchange in IoT domains.
Before data is shared, it needs to be collected from some source and this was promoted by [15]. They emphasized an authentication scheme and data gathering tools. The researchers also discussed the complexity of simultaneous data collection from a plethora of heterogeneous network elements. A Computer Assisted Mass Appraisal (CAMA) Based Data Collection Model was also proposed by [15] in which data was collected in a cyclic way from the devices. The problem in data collection comes when the radius of access point is larger and is very hard to collect data from all the devices simultaneously and hence sharing also becomes a problem. Since there is a limited storage capability of each device in IoT [16], it was suggested that information mining should be one thing to focus on. Researchers in [17] made the challenge of data collection from myriad devices using trivial techniques a concern.

Figure 9.3 IoT application domains.
The data from devices is shared among multiple devices which are fundamentally heterogeneous and hence pose a challenge while storing sharing and mining of this multidimensional data.

Figure 9.4 Data shared IoT domains.
In IoT, data is categorized into three parts:
- • Stating Data
This type of data contains information mostly that defines the physical object, e.g., owner information, identification number or serial, location tracking information and the state of being idle or busy.
- • Produced Data
This is the type of data that is acquired by the objects and then shared with other objects.
- • Absorbed Data
The sensors sense the data and then share the data. This type of data poses a major challenge in handling and exchange.
Now, Harnessing of data in IoT, for the purpose of sharing and consuming is done by industry as well as researchers in many IoT domains which are also known as Data-shared IoT [18]. Common data shared domains are shown in Figure 9.4 above.
In intelligent transportation, the sensors are installed on vehicles and cities as well. The applications of which encompass smart parking, accident avoidance, lighting control and smart traffic handling. Also, like Tesla, autonomous driving could also be achieved. In this domain, the data must be shared among the entities for proper functioning of the whole ecosystem [19]. The challenge in data sharing comes because the data is time critical and there must be no delays that could possibly jeopardize data integrity.
Smart utilities involve many public services one of the most common being smart grids. Data generated in such networks is heterogeneous which is ultimately required by the applications in real time. Data sharing again poses a great challenge due to the heterogeneity and connectivity issues.
Data in smart industry is generated by sensors for machinery and performance monitoring. Data sharing among various devices to work optimally is a major challenge. Smart farming data works on precision and the challenge in data sharing comes from the sensors [20] with variable accuracy and precision, uncertainties and ambiguities and issues with interoperability [21].
Smart healthcare is one domain which has grown exponentially. The data from wearables and many other applications in healthcare come from, again, heterogeneous devices which are prone to battery and accuracy limitations. Also, data sharing is of vital concern when the privacy of users is taken into consideration.
Smart homes are developed with the intention to assist the homeowner in managing and optimizing the energy consumption as well as providing security solutions. Data sharing is a challenge here because data must be anonymized to cater to the issues related to user data privacy which is done at the cost of processing overheads [9] and cause delays in the data sharing.
9.3 Why Blockchain?
Blockchain technology has gained a lot of popularity after being first implemented in Bitcoin and it is expected to be the next big thing after the Internet. Blockchain offers so many advantages that organizations have started to switch over to this distributed environment. Blockchain technology annihilates the need for a central authority such as a bank to make the transactions happen. The transactions are uploaded in the blockchain network and are verified by the nodes in the network in a real-time fashion. It saves both time and the charges incurred in making the transactions occur. It also eliminates the single point of failure and performance bottleneck issues related to the centralized systems.
Blockchain technology is immutable and append-only in nature so that once the transactions in a Blockchain are stored these cannot be altered with. If an adversary tries to change a transaction in a block, the verifying nodes in the Blockchain network will not allow this change to occur. So blockchain provides the security to our data with which no one can tamper with.
IoT technology in itself faces many challenges and most of all the security challenges that limits the full application capability of such a profound technology. Blockchain was inherently designed to be secure and immutable. The data exchange between sensors could possibly be done using blockchain to keep the malicious and unwanted nodes out. Blockchain in IoT could eliminate the bottlenecks and inaccuracies which in turn would facilitate autonomy. In addition to that, peer-to-peer communication could be made possible as well. Since trust is inherent now and no mediator is required, deployment costs could also be lowered significantly.
Blockchain in IoT can be beneficial in many ways; some of them are as under [22]:
- • Better Security
- • Optimized Data sharing
- • Easy Trust
- • Lesser Costs
The researchers in [23] also discuss the benefits that will be incurred using Blockchain in IoT as new optimized ecosystem, reduced costs and risks, enhanced processing, high trust and security, notion of micro-transactions, anti-counterfeit and validation.
The idea of central authority while sharing of data among devices can be wholly eliminated using blockchain’s smart contracts and hence achieving autonomous functioning. Also, Blockchain’s Proof of Work consensus algorithms and distributive nature for shared record could be exploited for a better and secure IoT [24].
IoT is essentially a centralized network. It faces security challenges which blockchain caters to by providing consensus algorithms, tracking and continuous monitoring and peer-to-peer secure data sharing [25]. The reduced cost for processing transactions and improved security using rule-based consensus mechanisms is also achieved using block-chain [26].
Since blockchain provides a distributive ledger which is shared among multiple nodes and which is immutable in nature, it is not easy to tamper or have identity thefts [27]. Blockchain can also be beneficial in providing an intrusion detection system where the product codes communicate with each other [28]. Blockchain has dramatically improved RFID management using a lightweight authentication protocol [29].
Blockchain provides transparency of transactions in the network. Anyone who has a copy of the blockchain downloaded can view any transaction. The Blockchain is open to everyone and is accessible to all the users. Blockchain technology provides anonymity to the users and to some extent does not reveal the real identity of a user by providing the addresses to the user in the form hashes.
9.4 IoT Data Sharing Security Mechanism On Blockchain
Traditionally, IoT data sharing occurs via cloud or offline which suffers from serious issues such as performance bottleneck, low efficiency, and costly in nature. Moreover, the central authority is vulnerable to a number of attacks which can result in data tampering and privacy breach. The data sharing in IoT systems based on cloud or offline modes can result in security issues which can result in information leakage and tampering. The central servers are unable to cope with the exponential growth of data generated from an IoT information sharing security mechanism based on blockchain technology [30]. To address these issues Blockchain-based security mechanisms have been suggested while sharing IoT data.
The idea of using Blockchain technology in data sharing in IoT devices is to ensure that the security parameter remains intact while the data is being shared. The term security is an umbrella for characteristics such as authenticity, confidentiality, integrity, and non-repudiation. The Blockchain network uses consensus algorithms such Proof-of-Work, Proof-of-Stake, DPBFT to validate the transactions; ensure that no block is forged by attackers, and that the Blockchain is always consistent and updated.
The IoT information sharing is one task that must be accomplished with high security. This security encompasses many parameters like integrity, authentication, reliability and confidentiality, etc. Blockchain makes use of Proof of Work mechanism to shield against attacks and guaranteeing the integrity and consistency of a data block. The use of cryptography by blockchain makes sharing of data secure and protects the data from attacks like man-in-the-middle, etc. Blockchain network uses Merkle trees to store the hashes of the transactions in a block. The Merkle root is used to verify the contents of a block and makes sure that no transaction has changed since it was dumped in the Blockchain.
9.4.1 Double-Chain Mode Based On Blockchain Technology
Making the data from the IoT end device less prone to tampering and guaranteeing the reliability of the source data, since reliability acts as the foundation of the whole information exchange, the nodes with centralized managements permissions may be given the authority to remove, add or falsify data. The first chain which is a data blockchain is required to gather all the data from the IoT node. Consequently, a private consensus is performed to create a data book. The sensor devices that encompass a range of heterogeneous devices have limited resources; processing power, storage and communicative capabilities. Hence the processing and storage of data should not only be done in a way that reduces redundancy but also improves accuracy. Since the data received from heterogeneous devices is heterogeneous in nature, it is vital to classify, standardize data expressions and supply storage operations. After sensing the data, lightweight data is separated from the multimedia data. The latter type of data is then compressed and data quality is improved. Finally, after unifying and standardization of data expressions and data storage respectively, data is shared easily. The data is then categorized into account book data and distributed storage data. The account book data is the summary of the data which is stored in a node and the outsourced data is multimedia data which is stored in a fog node.
It has long been established that any traditional consistency method shall work successfully as there are no byzantine or malicious nodes present in the network. Any network where there is a good possibility that a malicious node could be on the network, a consensus method which is byzantine fault tolerant and distributed in nature, is required. Hence, blockchain-based consensus mechanism is used to solve this problem while the exchange of data is happening among the nodes. It also solves the problem of who is responsible for generating a block and then maintaining the consistency of the blockchain on all the participating nodes. The consensus mechanism in blockchain is based on computations and using the outcome to verify the transaction also known as Proof of Work (PoW) mechanism. This is finally used to establish if a new block is validated or not. It adds some complexity. This mechanism is also required to follow the principles of optimal chain and incentive, which essentially means longest chain, must be the correct chain; it also depicts the maximum workload. This mechanism is significant and mandatory because lack of such a mechanism would let everyone create their own chains which would result in the inconsistency of the whole system. Now the reward-based mechanism in blockchain is used to motivate people to store and create blocks. As far as the trust architecture is concerned, the reader is provided with a label if the reader successfully forwarded the data and executed the command.
9.4.2 Blockchain Structure Based On Time Stamp
Also, the way an intermediate node behaves is reflected in the routing data, it may be true or false. As shown in Table 9.2, a reader’s trust is comprised of two parts: Routing trust and authorization trust.
Table 9.2 Types of trust.
| Type | Reaction |
| Authorization based trust |
|
| Routing based trust |
|
Blockchain involves a series of blocks that are linked together to create an immutable chain of records that is permanent in nature. Each block contains a block header and block body containing the transactions. The block header contains information such as Block number, Merkle tree hash, timestamp, nonce, and parent block hash [31]. The transactions in a blockchain structure are time stamped and avoid the problems with the timestamps provided by the central authorities. The time stamping of transactions in a Blockchain network ensures the integrity and also avoids the double spending problem. As an application scenario in video recording, time stamping can be useful in maintaining the integrity of a video captured over some time and making it impossible to change the contents of a video which can be produced as evidence in a court [32].
The time stamping provides the proof-of-existence for a document or a transaction in a Blockchain network. This process includes two steps: Hashing the document or transactions and recording the hash into the Blockchain. Each document in a Blockchain network is time stamped and hashed to create a Merkle tree which makes it sure that the document becomes tamper-proof and existed some time. The hash produced ensures the security and privacy of the documents in a Blockchain. It is also efficient in terms of storage as the whole document or file need not to be stored; rather a hash which is of fixed length is stored.
After the hash is created for a file, it is stored in the Blockchain where a particular transaction ID, transaction hashes, Block number and time stamping information of a file are created. The transaction ID can later be used to retrieve the file for which the retrieval will be fast.
In the Bitcoin network, the transactions are hashed and submitted to Origin Stamp [33] which submits this hash to a Bitcoin Blockchain network to create a tamper-proof storage of these transactions. When the hash of the transactions or files is submitted to the Bitcoin network, it becomes impossible to tamper the contents stored therein.
9.5 Conclusion
There is no single mechanism in the current IoT information domains which can guarantee a safe and completely secure information exchange. Blockchain with its distributed and immutable properties has a profound potential in providing such a much-needed mechanism. Secure block-chain-based information sharing using a double chain method seems very promising. In this model, two chains are used to secure the transactional data and the source data collection. Also, any sort of human tampering (modification or removing of data) can be avoided using consensus mechanisms. The traceability is also possible. However, the current setting has some performance issues which are due for improvements.
References
1. P. Sethi and S. R. Sarangi, “Internet of Things: Architectures, Protocols, and Applications,” Journal of Electrical and Computer Engineering, vol. 2017, pp. 1–25, 2017.
2. C. S. Wright, “Bitcoin: A Peer-to-Peer Electronic Cash System,” SSRN Electronic Journal, 2008.
3. M. Correia, “From Byzantine Consensus to Blockchain Consensus,” Essentials of Blockchain Technology, pp. 41–80, Nov. 2019.
4. L. Wang, X. Shen, J. Li, J. Shao, and Y. Yang, “Cryptographic primitives in blockchains,” Journal of Network and Computer Applications, vol. 127, pp. 43–58, Feb. 2019.
5. A. Ben Ayed, “A Conceptual Secure Blockchain Based Electronic Voting System,” International Journal of Network Security & Its Applications, vol. 9, no. 3, pp. 01–09, May 2017.
6. Z. Zheng, S. Xie, H. Dai, X. Chen, and H. Wang, “An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends,” 2017 IEEE International Congress on Big Data (BigData Congress), Jun. 2017.
7. X. Xu, I. Weber, M. Staples, L. Zhu, J. Bosch, L. Bass, C. Pautasso, and P. Rimba, “A Taxonomy of Blockchain-Based Systems for Architecture Design,” 2017 IEEE International Conference on Software Architecture (ICSA), Apr. 2017.
8. Z. Zheng, S. Xie, H. Dai, X. Chen, and H. Wang, “An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends,” 2017 IEEE International Congress on Big Data (BigData Congress), Jun. 2017.
9. T. Ali Syed, A. Alzahrani, S. Jan, M. S. Siddiqui, A. Nadeem, and T. Alghamdi, “A Comparative Analysis of Blockchain Architecture and its Applications: Problems and Recommendations,” IEEE Access, vol. 7, pp. 176838–176869, 2019.
10. S. Vongsingthong, and S. Smanchat. Internet of Things: A review of applications and technologies. Suranaree Journal of Science and Technology, 21(4), 359-374. 2014.
11. INFSO D.4 Networked Enterprise, RFID INFSO G.2 Micro and Nanosystems; and Working Group RFID ETP EPoSS. (2008). Internet of Things in 2020: Roadmap for the future. Version 1.1. Brussels, Belgium: European Commission. 2008.
12. C. Perera, C.H. Liu, and S. Jayawardena. The emerging internet of things marketplace from an industrial perspective: A survey. IEEE Transactions on Emerging Topics in Computing, 3(4), 585-598. 2015
13. H.D. Ma. Internet of things: Objectives and scientific challenges. Journal of Computer Science and Technology. 26, 919-924. 2011.
14. J.A. Stankovic. Research directions for the internet of things. IEEE Internet of Things Journal, 1(1), 3-9. 2014.
15. Y. Kawamoto, H. Nishiyama, N. Kato, Y. Shimizu, A. Takahara, and T. Jiang. Effectively collecting data for the location-based authentication in Internet of Things. IEEE Systems Journal, 11(3), 1403-1411. 2015.
16. J. Zhang and Y. Sun. Managing resources in Internet of Things with Semantic hyper-network model. Proceedings of the International Workshop on Enabling Technologies: Infrastructure for Collaborative Enterprises. Hammamet, Tunisia, 318-323. 2012.
17. M.U. Farooq,. M. Waseem.; A. Khairi, and S. Mazhar. A critical analysis on the security concerns of Internet of Things (IoT). International Journal of Computer Applications, 111(7), 6 pages. 2015.
18. J. Byabazaire, G. O’Hare, D. Delaney. Data Quality and Trust: A Perception from Shared Data in IoT. In Proceedings of the 2020 IEEE International Conference on Communications Workshops (ICC Workshops), Dublin, Ireland, 7–11 June 2020; pp. 1–6. 2020.
19. H. Xu, J. Lin, W. Yu. Smart transportation systems: Architecture, enabling technologies, and open issues. In SpringerBriefs in Computer Science; Springer: Singapore, 2017.
20. A. Tzounis, N. Katsoulas, T. Bartzanas, C. Kittas. Internet of Things in agriculture, recent advances and future challenges. Biosyst. Eng. 2017, 164, 31–48. 2017.
21. D. Pivoto, P.D. Waquil, E. Talamini, CPS. Finocchio, VF, Dalla Corte,.; G, de Vargas Mores. Scientific development of smart farming technologies and their application in Brazil. Inf. Process. Agric. 2018, 5, 21–32. 2018
22. E.B. Sasson, A. Chiesa, C. Garman, M. Green, I. Miers, E. Tromer, M. Virza, Zerocash: Decentralized anonymous payments from bitcoin, in: Security and Privacy (SP), 2014 IEEE Symposium on Security and Privacy (SP), USA, IEEE, 2014, pp. 459–474. 2014.
23. Bitcoin average transaction confirmation time. Available online: https://blockchain.info/es/charts/avg-confirmation-time 2017.
24. I. Eyal, A.E. Gencer, E.G. Sirer, R. Van Renesse, Bitcoin-NG: a scalable block-chain protocol, in: 13th USENIX Symposium on Networked Systems Design and Implementation (NSDI 16), Santa Clara, CA, USA, 2016, pp. 45–59. 2016.
25. R. Qiao, S. Zhu, Q. Wang, J. Qin. Optimization of dynamic data traceability mechanism in internet of things based on consortium blockchain. Int. J. Distrib. Sensor Networks, 14(12), 1550147718819072. 2018.
26. S.H Cho, S.Y. Park, S.R.. Lee. Blockchain consensus rule based dynamic blind voting for non-dependency transaction. Int. J. Grid Distrib. Comput. 10 (12), 93–106. 2017
27. N. Kshetri. Can blockchain strengthen the internet of things? IT Prof. 19 (4), 68–72.
28. W. Meng, EW. Tischhauser, Q. Wang, Y. Wang, J. Han. When intrusion detection meets blockchain technology: A review. IEEE Access 6, 10179–10188. 2018.
29. M. Sidorov, MT. Ong, RV. Sridharan, J. Nakamura, R Ohmura, JH. Khor. Ultra lightweight mutual authentication RFID protocol for blockchain enabled supply chains. IEEE Access 7, 7273–7285. 2019.
30. Si. Haiping, Sun, Changxi, Li. Yanling, Lie Shi Hongbo Qiao. Colleges of Information and Management Science, Henan Agricultural University, Henan 450002, China m the IoT devices. 2017.
31. Zheng, Zibin, Shaoan Xie, Hongning Dai, Xiangping Chen, and Huaimin Wang. “An overview of blockchain technology: Architecture, consensus, and future trends.” In 2017 IEEE international congress on big data (BigData congress), pp. 557-564. IEEE, 2017.
32. Gipp, Bela, Jagrut Kosti, and Corinna Breitinger. “Securing video integrity using decentralized trusted timestamping on the bitcoin blockchain.” In Mediterranean Conference on Information Systems (MCIS). Association For Information Systems, 2016.
33. Hepp, Thomas, Alexander Schoenhals, Christopher Gondek, and Bela Gipp. “OriginStamp: A blockchain-backed system for decentralized trusted timestamping.” it-Information Technology 60, no. 5-6 (2018): 273-281. 2018.
