7
Digital Forensics as a Service: Analysis for Forensic Knowledge
Soumi Banerjee*, Anita Patil†, Dipti Jadhav‡ and Gautam Borkar§
Department of Information Technology, Ramrao Adik Institute of Technology, DY Patil deemed to be University, Nerul, Navi Mumbai, India
*Corresponding author: [email protected]
†Corresponding author: [email protected]
‡Corresponding author: [email protected]
§Corresponding author: [email protected]
Abstract
Any machine exposed to the Internet today is at the risk of being attacked and compromised. The popularity of the internet is not only changing our life view, but also changing the view of crime in our society and all over the world. The reason for Forensic Investigation is increased computer crime. Digital technology is experiencing an explosion in growth and applications. This explosion has created the new concept of the cyber-criminal, and the need for security and forensics experts in the digital environment. The purpose of digital forensics is to answer investigative or legal questions to prove or disprove a court case. To ensure that innocent parties are not convicted and that guilty parties are convicted, it is mandatory to have a complete forensic process carried out by a qualified investigator who implements quality control measures and follows standards. In this paper, types of Digital Forensics with their tools and techniques of investigation are discussed. This chapter also involves the challenges in carrying out Digital forensics.
Keywords: Cyber-attacks, computer forensics, data forensics, network forensics, mobile forensics, IoT forensics, cloud forensics, digital forensics tools
7.1 Introduction
With the advancement of technologies, a rise in cyber-crime occurs. As a result, Digital Forensics plays a vital role to investigate cyber-attacks.
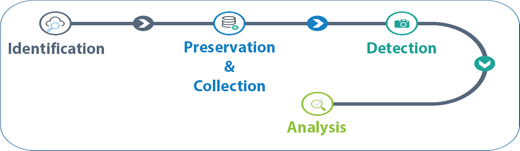
Figure 7.1 Digital forensics steps.
Digital Forensics experts investigate any digital devices and try to find evidences of cyber-attacks. During an investigation each expert should follow the ethics and norms of the investigation. They should follow some proper steps of investigation. The four main phases of digital forensics are shown in Figure 7.1. In each phase of investigation Chain of Custody is followed.
The phases of digital forensics:
- a. Identification: This phase involves the identification of the digital devices which may contain evidences of the cyber-crime. Such digital devices may be used by a victim of cyber-attack or may be used by the cyber-criminal.
- b. Preservation and Collection: In this phase evidences are collected and preserved in a safe place. After collection, the duplication of the original copy is taken and further investigation is carried out with the duplicated copy. This phase also involves data acquisition, that is, recovery of deleted data.
- c. Detection: In this phase the relevant evidences are detected from all the evidences collected.
- d. Analysis: After evidence collection and detection, the evidences are analysed and cause of attack is detected. With analysis, a detailed report is generated. This report contains all the documentation of the investigation along with the summarization and conclusion.
7.2 Objective
Digital forensics involves the processes of identification of the evidences, preservation and collection of evidences, recovery of deleted files, detection and analysis of the evidences and finally generation of reports from those evidences. The main aim of Digital forensics is to investigate a cyber-crime and to find out the motive of crime, how the cyber-crime is performed and who is the cyber-criminal.
The main objective here is to provide a concrete idea about how investigation is carried out in all sections of digital forensics. Also, it deals with the type of digital forensics, the mode of attacks happening in each type, method, tools and techniques used to investigate the attack.
7.3 Types of Digital Forensics
The branches of digital forensic are shown in Figure 7.2.
7.3.1 Network Forensics
It is a branch of Digital Forensics. In this type of forensics an expert monitors and analyses the network and collects useful information. Network Forensics also deals with volatile and dynamic data.
Two different methods are used to collect information from network.
- a. Catch-it-as-you-can: In this method all packets are captured, dumped and analysed in a batch mode.
- b. Stop, look and listen: In this method each packet is analysed and information is collected for future analysis.
Branches of Network forensics:
- • Web Forensics: Web forensics is the investigation and analysis of web browser and web server to collect useful information.
Web browser gives us evidence from web history and cache files of a browser.
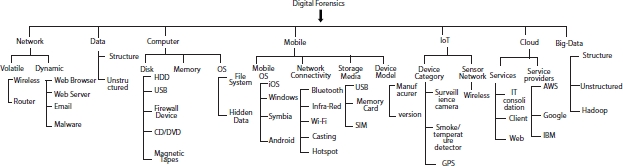
Figure 7.2 Branches of digital forensics.
- ➢ Firefox: In Firefox SSL signature can be recovered, cookies.
- ➢ Explorer: It works the same as Firefox but also can recover the URLs that were entered.
- ➢ Google Chrome: Google Chrome works the same as Explorer.
Web server forensics includes the investigation of Web server, Web application server and database server. Server logs are analysed in this method.
Attacks on Web Application: URL interpretation attacks: In this type of attack the attacker modifies some of the fields of the URL and tries to gain access to the web server. URL contains five fields; first is protocol name, second is the ID, third is name of the server, fourth field contains the port number and the fifth contains the access path. The attacker tries to manipulate any of these five fields.
Input Validation attacks: Improper validation may lead to attack where a cyber-criminal intentionally makes malicious inputs to break the system. Input validation attack is the cause of other attacks like buffer overflow attack, canonicalization attack, XSS attack, and SQL injection. In a buffer overflow attack the attacker intentionally gives large input which crosses the boundary buffer limit and overwrites the program code. In canonicalization the attackers change a file directory to get unauthorised access. XSS is called as Cross Site Scripting where an attacker embeds malicious script in the web page or web browser. In SQL injection the attacker tries to gain access by executing malicious SQL queries.
Impersonation attacks: Here a cyber-criminal modifies the HTTP request in such a way that it impersonates a real HTTP request.
Prevention of Web attacks:
- ➢ Validation of all untrusted input.
- ➢ Define policies to allow to access or block from receiving any requests.
- ➢ Only acceptance of parameterized queries and stored procedures.
- ➢ Use of Object Relational Mapping.
- ➢ Configuration of session cookies and consider HttpOnly attribute.
Steps for Web Forensics: the following parameters are investigated for web attacks:
- • Browsing History: Browsing history can gives the information whether user has browsed any malicious sites.
- • Caches: Browsers store cache data of a browsed website like HTML files, CSS style sheets, JavaScript, graphic image, and other multimedia contents, etc.
- • Cookies: It contains the user information about previous browsing and the actions that the user has performed previously while browsing, like email ids, items viewed, user preferences, etc.
- • Bookmarks: User can bookmark a website which he preferred the most. These bookmarks are also considered as evidence by forensic experts.
- • Sessions: Web sessions are created every time a user makes a request to the server. Server logs store the session IDs. Session signifies the time of browsing of the user.
- • Form information: If any user filled out some form within a website then such information is also stored in the browser.
- • Browser contains many other information-like thumbnails, most visited site, downloaded files, URL typed, etc.
Tools used:
- ➢ DB Browser for SQLite (DB4S)
- ➢ Browsing History View
- ➢ Nirosoft Web Browser Tool
- ➢ ESEDatabaseView
- ➢ BrowserAddonsView
- ➢ Pasco
- ➢ Q Web Historian Web Historian
- ➢ Q Cache View Cache View
- ➢ Q IE History View IE History View
- ➢ Q FTK, Encase FTK, Encase
a. Email Forensic: It deals with the analysis of email, its content, source, email server and client.
Attack on Email or using Email:
Phishing: This is now the most common type of attack. Cyber-criminals target the victim by sending fraud emails. Attackers send bulk emails to different users which look legitimate and try to steal credentials like user-name, password, credit card details, etc., by gaining the victim’s trust. Phishing emails contain malware which steals sensitive information from the victim.
Spear Phishing: This is a type of Phishing but at an advanced level. Here, the attacker gathers information about victims through social engineering or using reconnaissance techniques. Then the attacker performs a Phishing attack impersonating a trusted person or entity of victims by gaining the trust of victims.
Spam: Spam is a junk email. An attacker generally sends junk email from unauthenticated sources. These spam emails contain malicious links or malwares which steal sensitive information of the victim.
Whaling: In this type of attack the attacker targets the high-profile person of a company like a company’s CEO, senior executive, etc., and performs a phishing attack.
Pharming: Pharming is a type of attack which contains malicious codes that gets installed into the victims’ system and lead them to a fake website which behaves as if legitimate. These fraudulent websites trick the victims into entering credentials like username, password, credit card details, etc., which are then stolen by the attacker.
Adware: Adware is pop-ups which are generated as advertisements when something is browsed. These pop-ups may contain malwares which gain information about the victim’s search interests and send such type of spam email to the victim.
Spyware: Attackers may send spyware through emails. These spyware captures all the keys pressed by the victim and sends that information back to the attacker.
Email spoofing: It is a method of sending emails by hiding the original sender’s email id and instead of that using someone else’s authenticated email id. Thus the attacker sends an email using spoofed email id of some other person so that the receiver cannot detect the original email id of the attacker.
Email bombing: Email bombing is somewhat like a DoS attack. The attacker sends innumerable emails to a particular email address so that an overflow of mailbox occurs at the receiver end and at the same time a DoS attack happens at the server end where this email address is hosted.
Prevention of Attacks on email:
- ➢ Using of Antivirus software.
- ➢ Keeping alert on pop-ups.
- ➢ Using Firewall.
- ➢ Keeping browser up to date.
- ➢ Being careful while clicking on any emails.
- ➢ Generating awareness among employees.
- ➢ Encrypting all sensitive information.
- ➢ Developing strong security policies.
Techniques for Email Forensics:
- • Header Analysis: It refers to the analysis of metadata of email header. This technique is used for investing different cyber-crimes like email spoofing, phishing, spam, etc.
- • Server Investigation: This deals with the investigation of an email server and its logs.
- • Network Device Investigation: Deals with investigation of routers, firewalls to search the source of the email.
- • Software Embedded Analysis: Deals with the investigation of custom header or MIME content which gives some useful information about who is the sender of the email, what files or documents are attached with the message, and what email software was used by the sender for composing the email.
- • Sender Mail Fingerprinting: Deals with the investigation Received field, X-Mailer agent or User-agent. The Received field contains the information generated by mail servers tracking from sender end to receiver end. X-Mailer agent or User-agent gives information about what email software and email version was used by the sender.
- • Attachment analysis: Deals with the investigation of email attachments as most of the malwares are embedded in email attachment.
Tools used:
- ➢ eMailTrackerPro
- ➢ EmailTracer
- ➢ Access Data FTK
- ➢ EnCase
- ➢ Aid4Mail Forensic
b. FTP Forensic: It involves the investigation FTP server and FTP client. FTP always uses TCP protocol for communication. It communicates through two ports 20 and 21. The control connection uses port 20 and data connection uses port 21.
Attacks on FTP:
FTP Brute Force Attack: An attacker performs a brute force attack to crack the password of FTP login. In this attack multiple combinations of a password are used by the attacker to find the correct one. Attackers use trial and error method. Using a brute force attack, an attacker can easily crack weak and default passwords.
FTP Bounce Attack: Sometimes users use an FTP proxy server instead of original server. Attacker misuse this and acts as a middleman in between the FTP request and reply, behaving like a proxy server in front of the user.
Packet Capture: In normal FTP communication, data is transferred in plain-text form. So, the attacker tries to sniff the data exchanged in FTP. Using packet sniffing techniques, the attacker captures all the data transferred and tries to read the sensitive data.
Spoof Attack: Attacker spoofs the IP address of an authorised client and tries to connect FTP server.
Port Stealing: The attacker illegally accesses an FTP port number of a victim PC and steals or modifies files or whatever is exchanged between the FTP server and the victim.
Prevention of FTP attacks:
- • Always monitor the FTP logs. Any several times failed logins must be taken under consideration.
- • Instead of using normal FTP, SFTP should be used such that the data is transferred in encrypted form.
- • Strong encryption algorithm should be used.
- • Strong passwords should be used. A password should have a minimum of seven characters and must be alphanumeric.
- • Proper permission should be given to file and folders such that only an authenticated user can access that file or folder.
- • FTP administrator privileges should be given to a limited number of users and multi-factor authentication mechanism must be implemented.
- • Firewall rules must be applied at the FTP server side such that it can detect and block any unwanted traffic.
- • DMZ is used in network to store FTP server. So, it is better to use a Gateway in DMZ which will make the network private. So, any user will connect through the Gateway.
Techniques for FTP forensics:
- ➢ Extracting details about the connections used during FTP communication.
- ➢ Identifying FTP connection types. Connections may be active or passive.
- ➢ Identification source and destination IP address and port number.
- ➢ Identification of files which are transferred in the FTP channel.
- ➢ Identification of Retransmitted packets.
- ➢ Reorder of packets on the basis of sequence number.
- ➢ The contents of the packets which are lost during transmission are reconstructed.
Tools used:
- ➢ Xplico
- ➢ NetworkMiner
- ➢ Password Sniffer Control
- ➢ Wireshark
c. Wireless Forensics: It deals with the monitoring of wireless network, capturing of packets in wireless networks and analysis. Wireless forensics gives information about network anomalies, detects the attacks, and investigates the attacks.
Wireless Network Attacks:
Rogue Wireless Attack: In this case, unauthorised Wi-Fi devices are placed by the attacker in the network hiding from the network administrator. These devices act as a gateway for the attackers to access the network directly.
Wardriving: It is a method of searching Wi-Fi network from a moving car. A cyber-criminal uses portable devices to search such Wi-Fi. Generally, such Wi-Fi contains weak or default passwords. Attackers crack the password easily and perform malicious activities.
War-shipping: It is the act of attacking a Wi-Fi remotely. This means the attacker can attack the Wi-Fi without being in the range of that Wi-Fi.
Peer to Peer Attack: If more than one device is connected to the same access point then those devices may be vulnerable to each other.
Eavesdropping: Attacker hacks the wireless network and silently listens to all the data transferred through the network. Here, the attacker acts as man-in-the-middle attack between the sender and receiver. This type of attack is also called Packet sniffing attack. The cyber-criminal uses sniffing tools to steal data from the wireless network.
Encryption Cracking Attack: Data encrypted with weak encryption algorithms are easily cracked by attacker.
Evil Twining: Attacker creates a fake wireless network the same as an existing network to bluff the victim. A victim connects to this fake network thinking it is an authenticated network.
Jamming: Attacker creates network interference in a wireless network and cause a Denial-of-Service attack.
MAC Spoofing: Attacker Spoofs a MAC address to bypass MAC filtering technique and intrudes into a wireless network.
Denial of Service: Attacker can use Jamming Technique to perform a Denial of Service attack. Attacker can also target an Access Point and send floods of association request and disassociation request messages resulting in a Denial of service attack.
Social Engineering Attack: Attacker tries to learn the Wi-Fi password by gaining the trust of victim.
Prevention of Wireless Network Attack:
- • Default password or Wi-Fi names should not be used and they should be changed regularly.
- • Wi-Fi routers and other devices should be updated periodically.
- • Virtual Private Network or any other firewall should be enabled to access the Wi-Fi remotely.
- • Monitoring of network connected devices can help to detect whether any malicious or unwanted devices are connected to network.
- • Logs should be checked regularly to identify any suspicious or unwanted activity.
- • Two factor authentications should be used to connect a wireless network instead of using a single password.
- • Strong alphanumeric passwords should be preferred.
- • Wireless Network providers must use “Client Isolation” techniques such that the clients connecting to the same access point will not be able to communicate with each other directly.
- • Awareness should be generated among the users regarding the preventive mechanism of wireless attacks.
Techniques for wireless forensics [1]
- • Forensic experts generate a search warrant to investigate a Wi-Fi network.
- • Identification of all devices connected to the network such as routers, access points, etc.
Experts can use manual techniques to find the devices by visiting the places where these devices are placed or they may use wardriving techniques to identify such devices.
Network connected devices can be identified using Active wireless scanning techniques. In this technique a probe message is broadcasted through the network and waits for the reply or response messages from the access points. But in this case if an access point doesn’t give reply then it is not detectable.
Sometimes experts use Passive wireless scanning techniques to find active access points.
- • After detection of the access points the investigator tries to detect whether any rogue access point is there by verifying parameters like MAC address, SSID, vendor name, modems, network adapters, hard drives, network antennas, etc.
- • Investigator may check the wireless field strength by using tool like Field Strength Meter (FSM). It enables an expert to detect the interference.
- • After detection of all the connected devices, a forensic expert may create a static map of the wireless network. This technique maps wireless zones and hotspots.
- • Forensic experts use sniffing tools to capture the network packets and try to analyse those packets.
- • Several Logs are analysed by the investigator like DHCP logs are verified for detecting the IP addresses, Firewall logs are checked to identify any unwanted activities or intrusion activities.
- • Investigator also verifies windows registry to gather information about the wireless network devices used by the computer.
- • Chain of custody is maintained by experts in each step of investigation.
- • Finally, a report is generated on the basis of this investigation.
Tools used:
- ➢ Wireshark
- ➢ TCPdump
- ➢ Xplico
d. Router Forensics: Deals with router investigation. Router provides useful information and evidence like routing table, network block information.
Attacks on Router Forensics:
Denial of Service Attack: Attacker sends a flood of ICMP packets to specific router, which leads to DoS attack in that router. As a result, normal traffic is hampered and the network slows down.
Packet Mistreating Attacks: This attack involves the injection of malicious code in a packet which infects the router. An infected router misjudges the packets and also the flow of the packets. This creates disruption of the network.
Routing Table Poisoning: Hackers illegally manipulate the routing table. As a result, the packets in the network do not follow the proper path. This causes great damage to the network and the servers. Manipulation is done by the attackers by modifying the data in the packets which travels through the router in the network.
Hit and Run attack: This attack involves the testing of a router. This means an attacker sends a malicious packet to a router and tests its behaviour i.e., whether it is working properly. If yes, then the attacker sends more malicious packets from time to time and checks its behaviour each time. This causes a lot of damage to the router. So, this type of attack is also known as a test attack.
Persistent Attack: This attack is somewhat like a hit-and-run attack but the difference is that in this case the attacker goes on continuously sending malicious packets without testing the behaviour of the router.
Bot Attacks: Attacker hacks a network and infects the routers by sending malicious packets. These infected routers act as bots. These bots act according to the commands given by the attacker. Bots are used for DDoS attack.
Prevent Router Attacks:
- • Avoid using Default Admin password: Many times, users didn’t change the default admin passwords set by the manufacturers. Hackers search such routers and try to hack the router having default admin password.
- • Avoiding managing of router remotely: Routers should not be managed remotely. This means it is better if the router cannot be managed outside a LAN. This blocks the access of routers by any intruders from outside. But if necessary, to access the router remotely, then virtual private network should be used.
- • Setting strong password: It is always better to use an alphanumeric password for the Wi-Fi. Even then, passwords should be changed periodically.
- • Updating Router configuration: The router configurations should be updated regularly. It is a good way to check about the updates of routers provided by vendors and update the routers.
- • Enabling Firewall: Firewall can detect any malicious activity within the network. Also, the policies of the firewall can block the unwanted traffic.
- • Generating awareness among the administrators about the security of routers.
- • Developing strong policies in an organization about the router securities.
Techniques for Router forensics:
- • Collecting volatile data from the router by communicating remotely with the router. Below are some of the commands to collect live data.
- ➢ show clock detail
- ➢ show version
- ➢ show running-config
- ➢ show snmp user
- ➢ show snmp group
- • Saving the router configuration.
- • Collecting the information of remote access like Port scan, SNMP scan.
- • Investigating the routing table to detect malicious static routes modified by attacker.
- • Investigation of ARP cache for detecting IP or MAC spoofing.
- • Collecting evidences of network timestamps, difference between the initial configuration and present running configuration of a router.
- • Analysing the Logs like Syslog, SNMP logs, etc.
- • Each phase of investigation proper Chain of custody is maintained.
- • Finally, report is generated.
Tools used:
- ➢ Cisco Router Commands and Tasks
- ➢ Wireshark
- ➢ Netcut
e. Malware Forensics: This type of forensics involves detection of malwares. It gives the information about type, origin and functionality of malwares such as virus, worms, rootkits, trojan, backdoor, etc. Malwares may steal information or encrypt or modify a user’s data.
Types of Malware Attacks:
Virus: Virus is a malicious program which attaches itself in a document. It may modify, delete or encrypt a document. A virus can spread by itself within the network. It requires human activities to propagate through the network.
Worms: Worms are like viruses. But the main difference is that worms can propagate by themselves throughout the network.
Trojan: Trojan is a malicious code. It looks as if it is authenticated but actually it is a malicious code which exploits the victim’s machine. Trojan steals confidential data, damages data, and performs many other malicious activities. Phishing emails contain such Trojans. These emails behave as if legitimate but contain malicious Trojan malwares [2].
Ransomware: Ransomware is special type of Trojan which exploits the victim and encrypts the data also. They demand some money or ransom from the victim for that data.
Adware and spyware: Adware are advertising which pop up when the user is browsing something. Their intention is not always harmful but they are trying to gain information about the interests of the user. This adware may contain malwares which steal information or cause damage to the system. Spyware is similar to Adware; it contains malwares which gather information of each and every activity a user is doing on the system. In this case actually spyware spies on a victim’s activity on the system.
Bots: Bots are automated programs controlled by the attacker. Bots infect a system and the system then acts as a zombie. Such machines are controlled by the attacker not by the administrator. Bots are used to perform a DoS attack.
Rootkits: Such malwares try to gain the privileges of administrator or root. Once an intruder is able to acquire the root privileges it controls the whole system.
Prevention of Malware attacks:
- • Updating System: It is always a good practice to update operating system. Patches are nothing but security measures which are released by the vendors. Users should install such patches. Not only the operating system, it is necessary to updates software which are installed in the system, browser and also the plugins.
- • Enable plugins: Plugin help to prevent malvertising attack. Plugins automatically block the advertising malwares.
- • Users must be careful while clicking on email. They should verify whether an email is fake. User should avoid any links or messages which is asking for credentials like credit card details, PIN number, passwords, etc.
- • Use of Antivirus: Antivirus blocks malwares on the basis of their signatures. So, it prevents a system from a malware attack. Antivirus should also be updated regularly.
- • Use of strong password: Passwords must be a minimum of six characters and must be alphanumeric. The user should avoid using the same password for different logins; especially in the case of online banking, a user must keep password separate.
- • Avoiding fake phone calls which ask for more credentials over the phone.
- • Continuous monitoring and scanning all emails and user accounts can help to prevent malware attacks.
- • Generating awareness among the users regarding malware attacks.
Techniques of malware forensics:
- • Collection and Analysis of Volatile Data: Volatile data may contain the evidences of malware attacks. The user logs can give us information about the users who logged in with time stamp. Volatile information is also collected from the RAM dumps where any process which is under execution can be detected.
- • Collection of Non-Volatile data: Data hard disk forensics. The evidences are collected from registry settings and event logs and history of web browsers.
- • Recovering of all deleted files.
- • Static malware analysis: In this type of analysis the malicious code is disassembled to find hidden action or instruction inside the code. Disassembler like IDA, Ghidra are used to disassembled the code. This method follows signature-based approach to detect malwares.
- • Dynamic malware analysis: This form of analysis is used to detect the behaviour of the malware by executing the code in a sandbox environment. The sandbox environment prevents the malware from infecting the whole system. A dynamic approach is used to detect a malware having a new pattern or signature.
- • Hybrid approach: It is a combination of Static and dynamic approach. This method is used to analyse the malwares better.
Tool used:
- ➢ Pestudio
- ➢ PE Viewer
- ➢ IDA
- ➢ Ghidra
- ➢ GDB
- ➢ Hex editor
- ➢ Cuckoo sandbox
7.3.2 Computer Forensics
Most of the cyber-crime was carried out through computer or laptop. In a cyber-crime a computer is used as a weapon or a computer may be targeted as a point of attack. So, a computer is a main source of evidences in Digital Forensics. Computer Forensics is considered as one of the branches of Digital Forensics. The main aim of Computer Forensics is to investigate digital media thoroughly following the phases of Digital Forensics, which are identification, preservation, collection, examination, analysis, presentations.
Branches of Computer Forensics:
a. Disk Forensics: Disk forensics is the method of extracting evidences from digital storage media like Hard disk, USB devices, Firewall devices, CD, DVD, Flash drives, IDE/SATA/SCSI interfaces, Mobiles, PDAs, SIM, Magnetic tapes, Zip drives, etc.
Attacks on HDD:
DoS attack using Acoustic signal: In this attack the malicious actors try to create an acoustic signal close to the victim PC which causes a vibration in the disk drives. Due to the vibration the disk may get damaged. The acoustic signal is sent by the attacker through a phishing email or webpage or embedded in a widespread multimedia like Television. The acoustic signal range is below the human hearing range.
Malwares: Malwares can damage a hard disk drive (HDD). Specially, the boot sector virus can cause the most damage in a hard disk. These malwares infect the part of the hard drive that contains the operating system information and files allocation tables information.
Disk Filtration attacks: This type of attack also involves malwares which get involved on the computer and collect information.
Physical Attacks: It involves physical failures, a crashed file system, and mechanical failures in the hard disk.
Prevention of attacks on HDD:
- • Disk encryption: Full disk encryption means converting the data in plain text into cipher text. AES algorithm is mostly used to encrypt the data because it provides high security.
- • Antivirus: Use of antivirus can detect the malwares in the system.
Steps used in Disk Forensics:
- • The storage devices are identified from the crime scene.
- • The storage devices are where seizure and data acquisition processes are performed. In this step the hash value of the seized devices is generated at the crime scene. After generating hash value, the storage device is sealed and a data acquisition process is performed. In data acquisition a duplicate copy of the original evidences is created keeping the original copy in write-protected mode. In data duplication bit by bit copying is done in the forensic laboratory.
- • After data duplication the authentication of the duplicated evidences is verified by comparing the hash value of the duplicated evidences with original evidences.
- • The original evidences are kept safe so they are not tampered with. Further processing is carried out with the multiple copies duplicated evidences.
- • Evidences are analysed by proper examination like searching of keywords, analysing the pictures, time-line, registry, mailbox, temporary files, etc. This process also involves recovery of deleted files, data carving and analysis, format recovery and analysis, etc.
- • Case analysis report is prepared based on the analysis and presented in front of court along with all the evidences and documents which is maintained from the beginning [3].
Tools used:
- ➢ SANS SIFT
- ➢ Autopsy
- ➢ Forensic Tool Kit
- ➢ EnCase
- ➢ CAINE
- ➢ ProDiscover Forensics
- ➢ WinHex
b. Memory Forensics: Memory Forensics is the investigation of computer memory dump. Mainly RAM is analysed in memory forensics. Memory forensics can provide details of any open network connections, recently executed commands and processes, running processes, injected code fragments, internet history, any malicious code that is loaded in memory for execution, credentials, encryption keys, etc. Memory Forensics is also called as Live Forensics.
Attacks on Memory:
Cold Boot Attack: In a cold boot attack the attacker gains unauthorised access to a victim’s system and collects the memory dump to collect the encryption keys. Actually, a forensic expert is used to find the encryption keys. But the attacker misuses this technique.
Direct Memory Access (DMA) Malware: DMA Malware exploits the DMA and gathers information. It hides itself from the host also. It attacks kernel and collects information.
Rowhammer Attack: This attack enables an attacker to keep an eye on a row of a transistor in a memory chip for an executing process. The attacker hammers on that particular row several times until it leaks some electricity. Leaking some electricity means the bits in that row flip. So, integrity goal is broken.
RAM Bleed Attack: A RAM bleed attack is a modification of a Rowhammer attack. Here along with integrity, confidentiality is also breached. Attacker also steals information in this attack.
Prevention on RAM attacks:
- • Prevention of Physical access: Blocking the attacker from getting physical access to memory.
- • Boot verification approaches can prevent a cyber-criminal from taking memory dump.
- • Full memory encryption: In this technique the full RAM data is encrypted so that the attackers cannot access easily the encryption keys or credential in plain text.
- • Erasure of memory securely: In this technique the memory confidential data or credential are erased securely which are no longer in use.
Steps involved in Memory Forensics [4]:
- • Identification of the computer, laptop or mobile devices from the crime scene.
- • Maintaining a log which will record all events on a running machine.
- • Photography of the monitor screen of running system is done to document its state.
- • Detecting the operating system running on the victim’s machine.
- • The date and time of the machine are recorded with the current actual time.
- • Memory Dump of RAM is collected.
- • Collection of other volatile data is performed.
- • Original copy is preserved safely and further processing is carried out with duplicate copies.
- • Analysis of Memory dump is conducted to collect several evidences like uptime, date, time, and command history for the security incident, rogue process identification, DLL processes, network artifact, code injection, signs of rootkits, extract processes, drivers, etc.
- • Analysis report is generated with proper documentation and evidences.
Tools used:
- ➢ MAGNET RAM
- ➢ MDD
- ➢ Process Hacker
- ➢ FTK
- ➢ Mac Memory Reader
- ➢ Goldfish
- ➢ Linux Memory Extractor
- ➢ Linux Memory Grabber
- ➢ Volatility Framework
c. Operating System Forensics: In this type of forensics, crucial evidences are collected from the Operating System of a computer or mobile devices. This process also involves data and file recovery techniques, data carving, slack space analysis, extraction of hidden data, file system analysis, etc.
Attacks on Operating system:
Bugs: Bugs are the flaws or errors in a software. These bugs are generated for many reasons like a mistake in program’s design, software is not updated, etc. It causes unexpected results when these software are executed. Sometimes it may cause the program to crash or freeze the operating system. Malicious actors take this opportunity to attack the operating system.
Buffer overflow: Buffer overflow attack occurs when volume of the data cross the allocated buffer size. The attacker gives input whose size is more than the allocated buffer size to a program. As a result, input exceeds the boundary of the buffer and overwrites the code of the program. An attacker can gain access to the victim’s system through this attack.
Unpatched Operating system: Unpatched operating system means the operating systems have security vulnerabilities. Patch is a code which is released by the software vendor periodically to overcome these vulnerabilities. But an unpatched operating system is not updated and has vulnerabilities that can be misused by cyber-criminals.
Attack on authenticated system: User has some authentication mechanism to secure the system. There are several ways of authentication like passwords, PIN number, tokens, biometric. Weakness in these authentication mechanisms can lead to an attack.
Cracking Passwords: Cracking of passwords means guessing the password using some techniques. Weak passwords can be easily cracked. Several tools and techniques are available which help an attacker to crack passwords.
Breaking Filesystem security: Attacker targets the file system of operating system. Several attacks are there in the operating system like race condition attack, using ADS to hide files, directory traversals. Race around condition happens when an attacker changes some features of the file between two operations which modifies the file. A cyber-criminal uses Alternate Data Stream techniques in which malicious payloads are stored as ADS with the legitimate file. Due to vulnerabilities in the operating system attackers try to access the administrative files through directories traversals.
Prevention of Operating System Attack:
- • Operating system must be updated periodically.
- • Use of pirated, unpatched or outdated software should be avoided.
- • Strong authentication mechanisms should be used to secure the system.
- • Strong passwords should be used. A strong password should contain alphanumeric characters and the length of the password should also be sufficient, like a minimum 6 characters. Password should be changed regularly.
- • Proper access control mechanisms should be used. Superusers or administrations should maintain Access Control Lists (ACL) which allow access to a file based on the user’s rights. Only a few should have the rights to modify ACL.
- • File system encryption mechanism can be used to secure the file systems.
Steps for Operating System Forensics:
- • Identification of the Operating System from the computer, laptop or mobile devices at the crime scene.
- • Like disk forensics, the data duplication is conducted and the original copy is preserved safe.
- • Analysis is done on the duplicated copies. Deleted files are recovered and analysed, analysis is made of swap and page files, spool files, slack space, hidden data and also file system analysis.
- • Reports are generated similar to the disk forensics.
Tools used:
- ➢ FTK Imager
- ➢ Sluethkit or Autopsy
- ➢ EnCase
- ➢ Paladin
7.3.3 Data Forensics
Database forensics involves the study and investigation of databases and their metadata. Investigation of Database Forensic is performed with the identification, collection, preservation, reconstruction, analysis, and reporting of database incidents. A database has heterogeneous, structured/unstructured, complex, and ambiguous fields. Due to the complex and multidimensional nature of database systems it is difficult to retrieve data from damaged storage media. Database forensics process consider some facts, such as how to gain access to the system, is a system live or shutdown, integrity of data, images captured, encrypted data, goal of acquisition. Database forensics acquires files, internal structure, logical structure (index).
Digital forensics is a branch of Forensic Data Analysis (FDA). It analyses structured data with respect to financial crime events. The aim is to find and examine trends of fraudulent behaviours. Structured data is referred to as data from an information system or from their involvement with the study.
Unstructured data (or unstructured data) is knowledge that either does not have a data base management system or is not pre-definitely organised. Usually, unstructured information is text-heavy, but could also include data such as dates, numbers, and statistics. In comparison, unstructured data is taken from communication applications and office applications or from mobile devices. There is no overall approach for this knowledge and study of it implies applying keywords or mapping social interactions. Software forensics is commonly defined as the study of unstructured data.
Forensics data analysis (FDA) process takes at least three types of expertise in the team to analyse large structured data sets with the purpose of detecting financial crime: a data analyst to perform the technical steps and write the queries, a member of the team with significant experience of the processes and risk management in the relevant area of the investigated company and a forensic scientist familiar with the style of speaking [5].
Security Threats of database system:
Every person generates approximately 1.7 MB of data per second. As usage of social media and online platforms increases tremendously, the value of data gradually increases. Now the concern of security of information or our private data is important and requires a lot of attention. Data is breached by several threats such as malicious code, bypassing conventional security, natural and technical disaster, etc., as shown in Figure 7.3.

Figure 7.3 Security threats of database system.
Prevention of attacks on database system:
Database security is very important because attackers or criminals are always attracted to sensitive data such as banking details and private information for purposes of blackmailing or money laundering, etc.
Following database security preventive measures plays an important role in securing valuable data:
- • Proper physical database system security: Many times attackers try to attack on a DMZ server and steal all the end user’s information. Access Control policy has to be properly defined.
- • Use web application firewall: To prevent SQL injection attack, web application firewall play a vital role.
- • Autopatch vulnerabilities of Database application software: Software are periodically updated and perform vulnerability assessment to avoid zero-day attacks.
- • Data Encryption: This is a crucial but important measure because it continues backup and data encryption prevents ransomware-like attack.
- • Avoid or minimize data sharing on public mode: Attackers are more interested in trash. They try to track sensitive data from publicly available information. So minimize value of information or data on web.
- • Strong Access Control policy: Set proper password constraints policy, object or data access policy.
- • Proper Auditing: Periodically proper assessment and auditing of database application software is required.
- • Avoid pirated database software: Pirated software have lots of vulnerabilities which lead to many security attacks.
Forensics process of Database system: The following Figure 7.4 shows forensic process of database systems [6, 7].
Tools for database security:
- ➢ Encrypted database system
- ➢ Oracle Database Firewall
- ➢ IBM Guardium
- ➢ Gemalto SafeNet ProtectDB
7.3.4 Mobile Forensics
Nowadays everyone depends on mobile phone not only for calling but also for exchanging data in the form of text, audio, video, images; that is the reason mobile phone are loaded with huge information that might be considered as evidence for investigation of any crime or cyber-attack. Mobile forensics is a sub-category of digital forensics that collects the evidence and investigates it. Other facilities of cell phones are very useful for forensics investigation such as internet usage, email, camera mode, live access of documents, location tracking with GPS, calendar events. These devices are keeping track of our every movement. Due to this data generation has tremendously increased and this is an important source of evidence for forensic investigation related to cyber-crime, civil cases. As per study there is rare case of investigation that does not include cell phone. Mobile forensics is extremely difficult because data acquisition and examination vary according to mobile operating system (iOS, Blackberry, Android, Microsoft, etc.). One of the greatest forensic problems when it comes to the mobile platform is the fact that data can be accessed, processed, and synchronized through several devices. Data can be easily removed during evidence transfer from incident place to forensic lab [8].
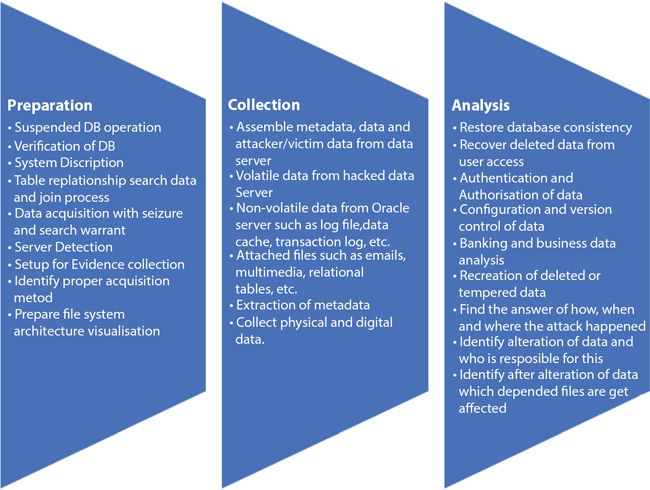
Figure 7.4 Forensic process of database systems.
The mobile forensics investigation process follows steps [9-1]:
Seizure: During seizing mobile device as evidence, investigator has some difficulty to prevent any kind of network connectivity with the mobile phone. So the forensic investigator always keeps the mobile device in a faraday bag to isolate it from another network. If the mobile device is in power on mode then before switching it off the investigator tries to find the PIN or Password or any lock pattern or biometric authentication scheme which will be helpful to again switch on the device. This is very critical because a criminal always try to delete data from a device through remote access. The criminal may be using Bluetooth, Wi-Fi connectivity, or hotspot for execution of remote access command. Investigator may keep the device in flight enabling mode or inactive all network connectivity while seizing.
Extraction: Mobile forensic toolkit such as Oxygen mobile forensics extractor, Cellebrite UFED, etc., is used for extraction of data from Mobile device.
Examination/analysis: Mobile devices are dynamic systems; it is composed of different operating system, hardware configurations, models, manufactures, versions. Due to this it has created difficulty in the investigation process. Therefore, a trained forensic investigator requires special tools to examine it.
Mobile forensic challenges:
Forensic investigators and law enforcement officers always faced the following challenges during acquisition of mobile devices:
Operating System: Forensics methods and process model of mobile devices varies according to operating system such as Android, iOS, BlackBerry, WebOS, BadaOS, Symbian, MeeGo, Windows PhoneOS, Maemo, Palm OS, Sailfish, Ubuntu Touch, Tizen, FireOS, Yun, Nokia Asha Platform and Lune.
- • Recourses availability: With advanced up gradation of technology, the forensic investigator requires a more advanced acquisition toolkit to examine a mobile device. Also, acquisition involves supportive gadgets such as a charger, battery and SD card, USB cable.
- • Dynamic system: Evidence from mobile device may be easily modified intentionally or unintentionally. For example, browsing the internet on a mobile might alter the data stored on the browser history.
- • Mobile Security: Mobile OS provide in-built security credentials to protect the user’s privacy and information. Security credentials create difficulty in the investigation process. The investigator always needs extra efforts to retrieve data from a mobile. Sometimes a vendor didn’t give credentials to penetrate this security policies or features.
- • Communication preventing: Smartphones connect over wireless network, Wi-Fi connectivity, Bluetooth, and Infrared connectivity. As mobile phone connectivity could change the device data, the probability of further connection should be avoided after seizing the device.
- • Malicious code: There may be malicious or harmful code on the device, such as a virus or a Trojan. That malware code can try to infect through wired and wireless connectivity [12].
Mobile device evidence proof extraction process:
The retrieval of evidence and forensic analysis of each mobile device can vary. However, the forensic analyst will encourage assuring that the proof retrieved from each handset is well recorded and that the findings are repeatable and defensible after a consistent analysis process. For mobile forensics, there is no well-established standard procedure. The following Figure 7.5, however, offers an outline of method considerations for mobile device proof extraction.
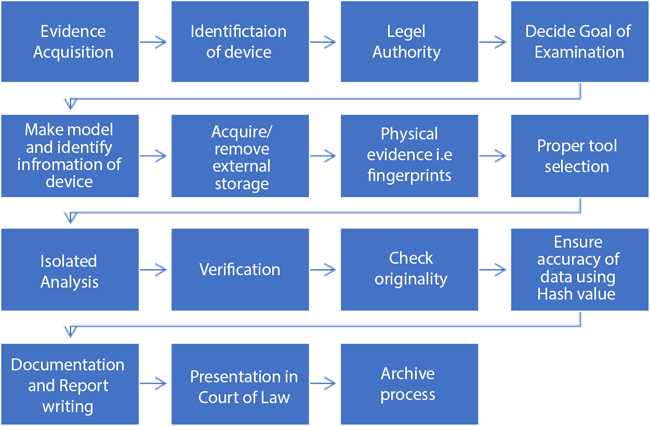
Figure 7.5 Mobile device evidence proof extraction process.
- • Evidence acquisition is the starting step to collect the device from the incident place and generate hash for further verification. Also prepare a document like time, date, device condition (tampered or not) and other details.
- • Identify the device details such as OS, manufacturer, version etc.
- • Investigator always verifies the legal authority present during acquisition of device.
- • Decide the goals of the examination to achieve good and accurate result. Also prevent alteration of evidence data.
- • Analyse the model, version and other device information for further processing.
- • Find other removable and external storage media connected with evidence device like USB, SD cards, etc.
- • Take figureprint or other biological evidence from mobile device. Probably a mobile device provides better physical evidence so investigator always handles it carefully with hand gloves to avoid tampering with the evidence.
- • Prepare a document to identify appropriate tool for analysis and examination of evidence device.
- • Mobile phones are designed to connect through cellular networks, Bluetooth, Infrared, and Wireless Fidelity (Wi-Fi) networks. Fresh data is applied to the phone while the phone is attached to a network, by in-out calls, texts, device information, which modify the evidence on the phone. Via network access or remote wiping orders, complete loss of data is also possible. For this purpose, it is necessary to isolate the system from interaction sources.
- • The alternative approach is physical acquisition, since it collects the raw cache data. During physical acquisition, try to avoid maximum alterations of device on other applications. More effort should be made to obtain the file system of the mobile device if physical acquisition is not appropriate or fails. A logical acquisition can still be done when parsed data is used, and indexing to examine the raw memory should be provided.
- • Check the originality of extracted data.
- • Ensure accuracy of data received from mobile device using hash values which are generated during acquisition and after examining data.
- • Prepare documents and report with detailed information such as mobile condition, start/end time and date of examination, device working status ON/OFF, acquisition and examination tools, data retrieved from device, reviews of the investigator, etc.
- • Present documents and report to the law court in an effective manner. The results should be straightforward, descriptive, and verifiable. Timeline and connection analysis can help in documenting and describing results through various mobile devices, capabilities provided by several commercial mobile forensics tools. These instruments allow the investigator to connect the methods behind the contact of several devices together.
- • Archive the extracted data and entire process for further court process.
Tools used:
- ➢ Elcomsoft Mobile Forensic Bundle
- ➢ Oxygen Forensic Detective
- ➢ MOBILEdit Forensic Express
- ➢ MD-LIVE
- ➢ MD-BOX (Mobile forensic hardware for extracting data directly from the board using JTAG interface)
7.3.5 Big Data Forensics
When Big Data is concerned, the improvements to data sizes and the introduction of Big Data applications have enhanced the specifications of forensics. For the processing of evidence, conventional forensics depends on time-consuming and interruptive procedures. Removing hard drives from computers carrying source evidence, computing MD5/SHA-1 checksums, and executing physical collections that gather all metadata are strategies fundamental to conventional forensics.
One purpose of any kind of forensic investigation is to obtain relevant information in a justified way. In a criminal investigation, the evidence is the data preserved in the device. This data can be file contents, metadata, deleted files, in-memory data, and slack space on the hard drive, among other types. Forensic methods are designed to collect any form of data such as intentionally deleted information, different types of file system, structured and unstructured data, metadata, etc.
Steps of Big data forensics [13]:
Big Data forensics follows the same steps as other digital forensics category (identification, Acquisition, analysis, and presentation of data). Measure challenge of investigation of Big Data systems, the aim is to gather or acquire data from distributed file systems, large-scale datasets, and similar applications. There are certain parallels between conventional forensics and forensics from Big Data, but it is important to consider the distinctions.
Metadata Preservation: Metadata is any file, data container, or device data information that defines its attributes. When concerns emerge about how the file was created, changed, or removed, metadata contains information about the file that can be useful. Metadata may explain who updated a file, when a file was changed, and which data was created by a device or programme. These are critical facts when attempting to understand the history of a single file.
For a Big Data investigation, metadata is not always crucial. When data flows into and through a Big Data system, metadata is always altered or lost. Without retaining the metadata, the ingestion engines and data feeds gather the data. Therefore, the metadata does not include details on who generated the data, when the data was last updated at the source of the upstream data, and so on. In these cases, collecting information cannot serve a function.
Big Data system investigations will rely on the information in the data and not the metadata. Metadata does not serve a function, like structured data structures, when an inquiry is focused solely on the quality of the data. The data itself will address quantitative and qualitative questions; metadata would not be useful in that case as long as the collection was carried out correctly and there are no concerns about who imported and/or modified the data in the Big Data system.
Collection methods: Systems may be taken offline in conventional forensics, and a compilation is done by removing the hard drive to produce a forensic copy of the data. Hundreds or thousands of storage hard drives can be used in Big Data inquiries, and data is lost when the big data device is taken offline.
Collection verification: In order to verify the integrity of the collected data, conventional forensics relies on MD5 and SHA-1, but it is not always feasible to use hashing algorithms to verify large data collections. Both MD5 and SHA-1 are intense with disk-access. A significant percentage of the time devoted to gathering and checking source proof is involved in verifying collections by computing an MD5 or SHA-1 hash. It might not be practical to spend time measuring the MD5 and SHA-1 for a Big Data array.
7.3.6 IoT Forensics
IoT Forensics is an emerging field of Digital Forensics. In the modern technology everybody is using smart IoT devices. Lots of data are generated due to the use of smart devices. IoT devices are less secured compared to a laptop or desktop. So, these devices are easily targeted by cyber-criminals. The forensic expert follows the phases of digital forensics in the same manner while investigating IoT devices. In IoT forensics experts collect evidences from IoT devices, sensors. Experts also collect evidences from cloud [14].
Attacks on IoT:
- • Encryption Attack: The data of IoT devices are in plain text form. The attacker can easily read all the data in the communication channel.
- • DoS Attack: IoT devices are easily targeted for DoS attack. Hackers hacks these IoT devices easily because of their less security and create bots. So, these infected devices act like zombies, controlled by the attacker, and are used for DoS or DDoS attack.
- • Man-in-the-middle attack: An attacker sits in the middle of the communication channel between two devices. He can read the data sent by one device, modifies it and forwards it to the other device.
- • Ransomware attack: Attacker hacks an IoT system and encrypts all the data. They demand ransom from users against that data.
- • Brute Force Attack: Most of the IoT devices have either a default password or a weak password and are susceptible to brute force attack. An attacker easily cracks the password and exploits the system [15].
IoT device Securities:
- • Keeping all IoT devices updated: Users should periodically update all IoT devices. They should install the security patches released by vendors. This prevents cyber-attacks on IoT devices.
- • Use of firewall or IDS: Firewall and IDS can detect any malicious activities and can also prevent them. So, it is a good practice to use place a firewall or IDS before IoT devices.
- • Change of Weak and Default passwords: Most of the IoT devices have a weak or default password. So, these are easily targeted. Users should not use default passwords. Instead of that they should use strong alphanumeric passwords.
- • Avoid buying IoT devices with weak security features: Before buying any IoT devices it is better to search for reviews about the IoT device security. User should avoid purchasing IoT devices having less security features.
Steps of IoT forensics: IoT forensic is done in the following way.
- • Device Forensics: Digital Evidences are collected from IoT devices. The memory dump is taken from these devices.
- • Network Forensics: Evidences are collected from firewall and IDS logs. These logs play a vital role in the investigation.
- • Cloud forensics: Most of the evidences are collected from Cloud. As IoT systems have small storage, all the communications take place with Cloud. So, Cloud forensics play an important role in IoT forensics [15].
7.3.7 Cloud Forensics
Cloud forensics is the application of digital forensics as a subset of network forensics in virtualization to collect and preserve evidence in a manner that is acceptable for presentation in a court of law. Cloud forensics is another big challenge against traditional forensics techniques. Cloud computing categories are PaaS (OS and Applications, Stack server, Storage media, Network), IaaS (Server, Storage Media, Network) and SaaS (Packaged Software, OS and Applications, Stack server, Storage Media, Network). According to category resource utilization is changed and with respect to this forensic investigation requires an advanced toolkit to handle the examination of evidence. There are lots of challenges to store and maintain confidentiality of the evidence from data alteration and deletion. In PaaS and SaaS service models, as customers do not have control over the hardware, consumers always rely on cloud service providers to access the logs. These logs are very important to examine the incident for presenting to the court of law.
Attacks on Cloud:
- • Malware attack: Hackers upload an infected service in SaaS or PaaS type cloud to infect the cloud. They also try to upload malicious virtual machine instance in IaaS type of cloud. These malwares gain control over the cloud and steal confidential information from cloud.
- • Denial-of-Service attack: Hackers give in rent less secured server to cloud providers. These servers are used by the attackers to perform a DoS attack. As a result, many authorised users are not able to access cloud services. DDoS attacks are also performed by cyber-criminals, in which attackers target less secured devices in a cloud platform.
- • Side Channel attack: In this type of attack, a malicious actor tries to gain information like shared hardware caches, electromagnetic emission, and sound emitted from a cryptographic device.
- • Wrapping attack: It is a Man-in-the-middle type of attack. Attackers intercept between the cloud users and services. They steal all the data transferred between the users and cloud services through web browsers.
- • Man-in-the-cloud: Here also the attacker intercepts between the cloud users and services and changes the configuration of cloud services such that when the next synchronization occurs a new token will be generated and that will be accessible to the attacker.
- • Insider attack: An authorised user in a cloud platform violates the security policies and tries to gain access to some unauthorised data.
- • Account/Service Hijacking: After stealing a user’s credentials an attacker can misuse those credentials to gain access to the user’s account. They also can use the cloud services illegally.
- • Spectre and Meltdown attack: It is an advanced level Man-in-the-middle attack. In this attack an attacker intercepts between user and cloud services and tries to decrypt the encrypted data from memory using malicious JavaScript code.
Prevention against cybercrime on Cloud:
- • Strong Security Policies to be implemented to restrict the scope of access. Users should be made aware of the security policies.
- • Multi-factor authentication system should be used for authentication.
- • Strong encryption algorithms to be used to secure data in all stages. This means the data to be secured while storing in cloud as well as while transferring from user to cloud or vice versa.
- • Periodically backup of data stored in cloud should be taken, such that if some damage happens that can be recovered from backup.
- • Use of Intrusion Detection System (IDS) helps to detect intruders in cloud.
- • Cloud developers must allow the users to connect through strong APIs. VPNs can also be used for secure communication through cloud.
- • Accessing of cloud services should be restricted only to authorised users. A strong security mechanism will help the cloud providers to block access of cloud services to unauthorised users.
In a cloud environment, managing a custody chain is very complex relative to a conventional forensics’ environment. The internal security team has power of who performs forensics operations on a server in conventional forensics settings, but in cloud forensics, the security team has no control over who wishes to obtain information from the Cloud service provider. The chain of custody cannot be kept in a court of law if they are not qualified according to a forensic norm [16].
Cloud forensics procedure as shown in Figure 7.6 [17]:

Figure 7.6 Workflow of cloud forensic process.
- • Identification
- • Identify the violations or potentially illegal activity affecting IT-based processes that have taken place.
- • It involves an individual complaint, IDS discovered anomalies, inspection and profiling due to an audit trail, suspicious cloud incidents may rely on the implementation of the application model (i.e., Private, Public, Community and Hybrid), the type of cloud services used (i.e., SaaS, PaaS and IaaS), and the geographic area decided for deployment.
- • Preservation and Collection
- • According to ethical and forensic requirements, evidence is gathered in the source without harming its credibility.
- • Preserve all the proof and documentation for further investigation without diminishing its credibility.
- • There may be a risk that an incredibly large amount of data storage would be needed for data processing.
- • The investigator must then discuss data security and privacy laws and regulations and their effect on the evidence stored in the cloud.
- • When collecting data from the vendor side of the cloud, do remember the data of the other customer or entity. For further analysis, an accurate representation of the cloud service data must be collected.
- • By serving a legal notice to the cloud service provider, an investigator may aim to maintain data residing in the cloud [18].
- • Detection: Identify abnormal activity or malicious code by using several methods and algorithms (i.e., filtering, pattern matching).
- • Analysis
- • Investigate the data and crime by using certain forensic tools.
- • The legal authority can ask the company or an entity a question in order to find any factual information.
Challenges in cloud forensics [19]
- ➢ Presentation at the court of law
- ➢ Verification of external or client-side dependencies over cloud provider
- ➢ Cloud service provider uses different approach to cloud computing
- ➢ Lack of collaboration between different nation and service provider
- ➢ No proper laws and rules to process cloud forensics
- ➢ Lacking of forensics expertise and technological support
- ➢ Difficult to isolate any particular end user from cloud services.
Tools Used:
- ➢ Encase Enterprise
- ➢ Access Data FTK
- ➢ FORST
- ➢ UFED cloud analyzer
- ➢ Docker Forensic Toolkit & Docker Explorer
- ➢ Diffy (by Netflix)
7.4 Conclusion
In Digital Forensics modern technologies are used to investigate a cyber-crime. With the rise of cyber-crime, the Digital Forensics field plays a crucial role in this technological world. Forensic experts are also using new tools and techniques for identification of crime, collection of evidences, analysis of evidences. More bifurcation is carried out in the digital forensics in the modern technological world. Thus this chapter emphasizes an overview of digital forensics, its branches, tools and techniques used for various digital investigations.
References
1. A. Varol and Y. Ü. Sönmez, “The importance of web activities for computer forensics,” International Conference on Computer Science and Engineering (UBMK), Antalya, pp. 66-71, 2017.
2. Anita Patil, Swapnil Shinde and Soumi Banerjee, “Stuxnet-Tool For Zero-Day Attack”, in Handbook of Research on Cyber Crime and Information Privacy, IGI, pp. 652-675, 2020.
3. T. Prem, V. P. Selwin and A. K. Mohan, “Disk memory forensics: Analysis of memory forensics frameworks flow,” Innovations in Power and Advanced Computing Technologies (i-PACT), Vellore, pp. 1-7, 2017.
4. A. Chetry and U. Sharma, “Memory Forensics Analysis for Investigation of Online Crime - A Review,” 2019 6th International Conference on Computing for Sustainable Global Development, New Delhi, India, pp. 40-45, 2017.
5. Mario A. M. Guimaraes, Richard Austin, and Huwida Said., Database forensics, Information Security Curriculum Development Conference (InfoSecCD ‘10), Association for Computing Machinery, New York, USA, pp. 62–65, 2010.
6. A. Al-dhaqm et al., “Database Forensic Investigation Process Models: A Review,” in IEEE Access, volume. 8, pp. 48477-48490, 2020.
7. Muhammad Sadiq et al., “Mobile Devices Forensics Investigation: Process Models and Comparison.”, International Scientific Journal Theoretical & Applied Science. Volume.33, pp. 164-168, 2016.
8. P Chavan, D Jadhav, GM Borkar, “Challenges to Multimedia Privacy and Security Over Social Media”, Handbook of Research on Cyber Crime and Information Privacy, IGI, pp. 118-131, 2020.
9. Wilson, Rodney & Chi, Hongmei, “A Case Study for Mobile Device Forensics Tools”, in Proceedings of the SouthEast Conference, Association for Computing Machinery, New York, NY, USA, 154–157, pp 154-157, 2017.
10. Konstantia Barmpatsalou, Tiago Cruz, Edmundo Monteiro, and Paulo Simoes. 2018. Current and Future Trends in Mobile Device Forensics: A Survey. ACM Comput. Surv. 51, 3, Article 46, pp. 1-31, 2018.
11. A. Al-Dhaqm, S. A. Razak, R. A. Ikuesan, V. R. Kebande and K. Siddique, “A Review of Mobile Forensic Investigation Process Models,” in IEEE Access, volume. 8, pp. 173359-173375, 2020.
12. Artyom Skrobov, Slava Makkaveev “Advanced SMS Phishing Attacks Against Modern Android-based Smartphones”, https://research.checkpoint.com/2019/advanced-sms-phishing-attacks-against-odern-android-basedsmartphones/ 2019.
13. Feng X, Zhao Y (2017) ‘Digital forensics challenges to big data in the cloud’, IoTBDH-2017 - Exeter, pp. 858-862, 2017.
14. V. V. R. G. Saigopal and D. V. Raju, “IoT based Secure Digital Forensic Process according to Process Management,” International Conference on Computational Intelligence (ICCI), Bandar Seri Iskandar, Malaysia, pp. 229-232, 2020.
15. M. Stoyanova, Y. Nikoloudakis, S. Panagiotakis, E. Pallis and E. K. Markakis, “A Survey on the Internet of Things (IoT) Forensics: Challenges, Approaches, and Open Issues,” in IEEE Communications Surveys & Tutorials, volume. 22, issue no. 2, pp. 1191-1221, 2020.
16. Keyun Ruan, Joe Carthy, Tahar Kechadi, Ibrahim Baggili “Cloud forensics definitions and critical criteria for cloud forensic capability: An overview of survey results”, Digital Investigation Journal, pp. 34-43, 2013.
17. Park S. et al., Research on Digital Forensic Readiness Design in a Cloud Computing -Based Smart Work Environment, Sustainability 2018, volume 10, pp. 1-24, 2018.
18. Thankaraja Raja Sree and Somasundaram Mary Saira Bhanu, “Data Collection Techniques for Forensic Investigation in Cloud”, Digital Forensics Science, 2020.
19. Ameer Pichan, Mihai Lazarescu, Sie Teng Soh, “Cloud forensics: Technical challenges, solutions and comparative analysis”, Digital Investigation, volume 13, pp. 38-57, 2015.
