ELECTRONIC DATA INTERCHANGE (EDI) SYSTEMS AND THE RISKS AND CONTROLS (STUDY OBJECTIVE 7)
Electronic data interchange is the inter-company, computer-to-computer transfer of business documents in a standard business format. Three parts of this definition highlight the important characteristics of EDI. Inter-company refers to two or more companies conducting business electronically. The computer-to-computer aspect of the definition indicates that each company's computers are connected via a network. A standard business format is necessary so that companies can interact and trade with a variety of vendors and sellers using EDI. The standard business format allows all vendors and sellers to “speak the same language.” The American National Standards Institute (ANSI) has developed standard formats for the usual documents needed in a sales process, including purchase orders, sales invoices, price quotations, and shipping schedules. The standard in the United States is ANSI X.12.
ANSI X.12 standards divide EDI data transmissions into three parts: header and trailer data, labeling interchanges, and data segments. Header data contain information about the file or transmission being sent. The header identifies the beginning and end of a particular transaction data set. Trailer data also contain data about the file or transmission and identify the end of a particular transaction data set. Labeling interchanges identify the type of transactions in the set, such as a set of sales invoices. Data segments include the actual data within the invoices, such as quantities and prices.
Although two companies may have a network connection that allows them to be directly linked to each other, it is expensive to develop and maintain such a system. The majority of companies using EDI communicate with trading partners by a third-party network like the one illustrated in Exhibit 8-18.
The two companies in Exhibit 8-18 are not directly connected to each other, but they communicate EDI data through a third-party network via mailboxes in the third party's computer system. These third-party networks are termed value added networks (VANs) because they provide other valuable services such as translation and encryption of the EDI data and authentication of a valid and authorized trading partner.
There are many advantages to an EDI system within the revenue and cash collection processes:
- Reduction or elimination of data keying
- Elimination of keying errors
- Elimination of costs related to keying and keying errors
- Elimination of the time needed to key in orders
- Elimination of mail delays
Exhibit 8-18 EDI Using a Third-Party Network

- Elimination of postage costs
- Reduction in inventory levels as a result of shorter order cycle
- Competitive advantage through better customer service
- Preservation of business with existing customers who have adopted EDI
The first four advantages listed relate to time and costs savings from reducing or eliminating data keying. Since EDI transmits data between computers without paper documents, no data entry clerks are needed to key details of a sale from paper documents into the computer system. This saves time and dollars, as well as the errors that are inherent in keying data. Advantages numbered five and six arise because data are sent electronically rather than by mail. Mail delays and the costs of mailing are completely avoided. Advantage number seven occurs because there is a significant amount of time saved by avoiding keying, keying errors, and mail delays. This time savings can cut days from the time cycle to enter an order, ship it, and receive payment. Thus, the seller can maintain lower inventory levels and replenish those inventory levels more quickly. Finally, the last two advantages relate to getting or keeping competitive advantages. Sometimes, a company needs EDI in order to survive—for example, to satisfy the transaction processing vendors or sellers it already deals with. In other cases, EDI offers a competitive advantage by allowing a seller to more quickly and accurately service customers.
Newer EDI systems use the Internet, rather than third-party networks, to transmit EDI documents. Companies using Internet EDI realize large cost savings because they avoid the fees paid to a third-party network.
THE REAL WORLD
Northern Telecom (Nortel) switched to an Internet EDI system in the late 1990s. Nortel has customers all over the globe, and the use of the Internet by Nortel customers to transmit purchase orders is a low-cost transmission option for those customers. This was especially beneficial to Nortel in expanding its customer base in Europe and Asia. As Nortel works to gain new customers, a low-cost way to order is an enticement to those customers.
There are also other benefits to Nortel. The use of Internet EDI eliminated the need for customers to fax purchase orders or supplier information to Nortel. Michael Keef, the senior manager of electronic business solutions at Nortel, said, “Errors occur when people fax things. We won't have to rekey shipment notices.”3 Details of Internet EDI are described in a later chapter on e-commerce.
EDI systems cause risks that may be different from those found in traditional manual or IT systems. EDI eliminates much of what would be the traditional paper audit trail of documents, such as sales orders, shipping documents, and invoices. Risks in an EDI system are as follows:
Security and Confidentiality
- 1. Unauthorized access
- 2. Trading partners gaining access to unauthorized data
- 3. Hackers or other network break-ins
- 4. Repudiation of sales transactions
Processing Integrity
- 5. Invalid data entered by trading partners
- 6. Incomplete audit trail
- 7. Errors when integrating data into back-end systems such as accounting, payment processing, and order fulfillment software systems
Availability
- 8. System failures such as hardware and software failures that block customers from access to the EDI system
IT controls can lessen these risks. Exhibit 8-19 summarizes these risks and controls for e-commerce and EDI. The controls are authentication, encryption, transactions logging, control totals, and acknowledgments. Authentication is the process of user identification to ensure that only authorized users are accessing the IT system. Authentication occurs through the use of user ID, password, and other unique identifiers. Only valid, authorized trading partners should be allowed to initiate or receive EDI communication. For example, a company would not want an employee to log in from a home computer and submit false orders to be delivered to her home address. Limiting communication to authorized trading partners is accomplished by authentication that uses software-based authentication techniques such as user account IDs and passwords. Authentication can occur at the VAN log-in, within the translation software, and within the application software.
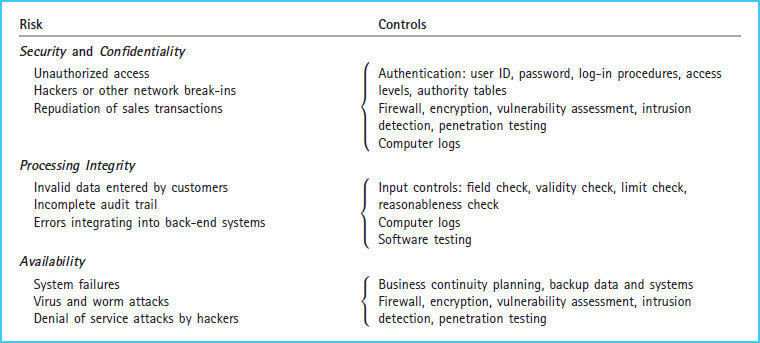
Exhibit 8-19 Risks and Controls for E-commerce and EDI Revenue Processes
Since data travel over network data lines and third-party networks, they are susceptible to network break-ins. Encryption, the coding of data that makes data unreadable to those without the encryption key, is a control that limits risk. Encryption of the data will not prevent these breaches, but will render the data useless. Transaction logging occurs when the IT system automatically produces a log of users and the actions they undertake within the IT system. As a computer conducts EDI transactions, it should automatically log each transaction, and this log should be regularly examined and reconciled to ensure that no transactions are lost or unaccounted for.
Control totals are subtotals of selected fields for an entire batch of transactions. For example, quantity ordered could be added for a batch of orders. The acknowledgment is a reply that echoes the data control totals. The use of acknowledgments and matching control totals can reduce the risk of erroneous or invalid EDI data in transactions. When an EDI transaction is transmitted, the receiving computer should transmit an acknowledgment. These totals can be compared with original data to make sure it was not garbled or lost during transmission.
