Chapter 18
Software and Hardware Tools
The Following CompTIA Network+ Exam Objectives Are Covered in This Chapter:
- 4.2 Given a scenario, use appropriate hardware tools to troubleshoot connectivity issues.
- Cable tester
- Cable certifier
- Crimper
- Butt set
- Toner probe
- Punch down tool
- Protocol analyzer
- Loopback plug
- TDR
- OTDR
- Multimeter
- Environmental monitor
Specialized tasks require specialized tools, and installing network components is no exception. We use some of these tools, like network scanners, on an everyday basis, but most of the hardware tools I’ll be covering in this chapter are used mainly in the telecommunications industry.
Still, in order to meet the CompTIA Network+ objectives, and also because you’re likely to run across them in today’s networking environments, it’s very important that you’re familiar with them.
For up-to-the-minute updates for this chapter, please see www.lammle.com/forum or www.sybex.com/go/netplus2e.
Understanding Network Scanners
Network scanner has become a broad term often referring to a family of tools used to analyze our networks, but the CompTIA Network+ objectives are much less vague. So with regard to those critical objectives, know that network scanners refer to these three tools:
- Packet sniffers
- Intrusion detection system / intrusion prevention system (IDS/IPS) software
- Port scanners
Packet Sniffers
Unlike port scanners, packet sniffers actually look inside every packet on a network segment. Packet sniffers come in many flavors, and some of them, like Microsoft’s Network Monitor (NetMon), are even free today. Even though NetMon comes in more complex versions that are, well, not exactly free, the version that comes bundled with Windows Server does allow you to analyze network communications traffic. The full version will give you statistics on network utilization and packet traffic data as well as capture individual frames for analysis. These abilities really mean that NetMon is both a packet sniffer and a network analyzer, and it’s common for these to be combined and referred to as one and the same.
All good, but personally, I use Wireshark instead. It’s also free, and you can easily download it from www.wireshark.org. A nice feature of Wireshark is that it runs from Windows, OS X, Linux, and Unix platforms. It easily captures data on all my interfaces, including my wireless and virtual private network (VPN) connections, and looks at all traffic on the network segment. There are tons of packet sniffers available, and to get your hands on most of them, you’ll have to pony up some cash. Sometimes they’re worth it, though, because these higher-end products can even provide solutions to problems you find on your network—nice.
Anyway, free or not, the basic purpose of packet sniffers (or network analyzers) is to collect and analyze each individual packet that is captured on a specific network segment to determine if problems like bottlenecks, retransmissions, and security breaches are happening. Packet sniffers are a must have for every network administrator to troubleshoot and find problems or security holes in a network. For example, you may discover that users are using an application on the network with usernames and passwords being sent unencrypted over the network.
You can also use packet sniffers to see if there is too much traffic on a segment, or even if a broadcast storm has been created by a bad Network Interface Card (NIC). And remember—I do mean on a network segment—you can’t use them to catch packets passing through routers. Yes, they can help you find a hacker stalking around in there, but you’d really have to be looking closely and constantly to discover this. For that level of monitoring, you’d be better off using a tool known as IDS/IPS. It can really help you track and even defeat hackers. (We’ll talk about IDS/IPS software in the next section.) The more expensive network sniffers can help find anomalies in your network, like a hack, and even alert you of these problems. Figure 18-1 shows output from a packet sniffer. Notice that you can identify both the IP addresses and the MAC addresses associated with any of the packets captured as well as identify the protocol in use.
Figure 18-1: Output from a packet sniffer

You can definitely see that a packet sniffer can provide you with huge amounts of information. This means you really need something to narrow things down and help you to more readily find the needle in the haystack that you’re looking for, right?
In this case, help comes in the form of some handy built-in filters that can be used to gather information from just one specific host or server; without them, you’d have to go through possibly thousands of packets to find the problem. For the packet I’ve highlighted, you can see that there’s a probable User Datagram Protocol (UDP) checksum error. And by the way, because UDP is connectionless, this is a pretty common error.

You should download and start working with a network sniffer right away. As I mentioned, you can download Wireshark at www.wireshark.org for free, so what are you waiting for? Go for it!
Now comes the fun stuff—let’s take a look at ways we can find and stop hackers dead in their tracks.
Intrusion Detection and Prevention Software
An IDS detects unwanted attempts to manipulate network systems and/or environments, and an IPS is a computer-security device that monitors network and/or system activities for any strange or malicious behavior. It can react in real time to prevent and even block nasty activities. An IDS identifies, detects, and reports attempts of unauthorized access to the network as well as any suspicious activity, and an IDS is the best software type for identifying an attack. However, if you want to stop the attack in its tracks, you need to add an IPS device. So, unlike IDSs, which can identify an attack and report it, an IPS can stop the attack by shutting down ports or dropping certain types of packets.
A bunch of different IDS/IPS software packages are available on the market, and a lot of them are free. Again, predictably, the best ones aren’t, and they can be a bit pricey. These high-powered versions run on Linux or other proprietary hardware. But there are still many IDS/IPS software applications available for Windows.
Snort is one of the most popular IDS/IPS software products around. It runs on both Linux and Windows, and it’s a free, open-source platform, which happens to be a big reason for its popularity. But that’s not the only reason—just because it is free doesn’t mean it doesn’t offer up some pretty cool features. On the other hand, if you’re dealing with a large, corporate environment, you need some serious weaponry, and Cisco offers an Adaptive Security Appliance (ASA) as an enterprise solution that’s powerful but definitely far from free. It’s worth it, though.
Figure 18-2 shows a picture of the stack of Cisco ASA boxes I use in my security classes.
Personally, I think the Cisco box is the best IDS/IPS box on the market today. Still, Snort isn’t bad; so if cost is an issue, rest assured you can use it, as well as several other tools, and be much better equipped than you would be without them working on your network to help you keep it secure.
Figure 18-3 shows where you’d find a typical IDS/IPS in a internetwork.
Figure 18-2: A stack of Cisco ASAs

Figure 18-3: IDS/IPS placement in an internetwork
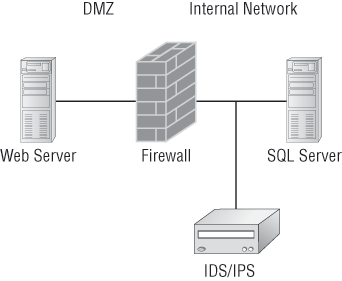
Okay…to be honest, this is a relatively simplistic view of an IDS/IPS working within a network because of the device’s complexity and the many different physical configurations possible. The important thing I want you to pay attention to is the fact that you would typically find the IDS/IPS software positioned between your internal router and the firewall to the outside network (Internet). If you’re using Snort, just add the software to a Linux box, and connect this box between the firewall and the router. This area would typically be your demilitarized zone (DMZ). The Basic Analysis and Security Engine (BASE) displays and reports intrusions and attacks logged in the Snort database in a web browser for convenient analysis.
Port Scanners
A port scanner is a software tool designed to search a host for open ports. Those of us administering our networks use port scanners to ensure their security, but bad guys use them to find a network’s vulnerabilities and compromise them. To port scan means to scan for TCP and UDP open ports on a single target host either to legitimately connect to and use its services for business and/or personal reasons or to find and connect to those ports and subsequently attack the host and steal or manipulate it for nefarious reasons.
In contrast, port sweeping means scanning multiple hosts on a network for a specific listening TCP or UDP port, like SQL. (SQL injection attacks are super common today.) This just happens to be a favorite approach used by hackers when trying to invade your network. They port sweep in a broad manner, and then, if they find something—in this case, SQL—they can port scan the particular host they’ve discovered with the desired service available to exploit and get what they’re after. This is why it’s a really good idea to turn off any unused services on your servers and routers and to run only the minimum services required on every host machine in your network. Do yourself a big favor and make sure this is in your security policy.
Remember that three-way handshake I discussed in Chapter 6 “Introduction to the Internet Protocol”? Well, it just so happens that a SYN scan is the most popular form of TCP scanning. Rather than use the operating system’s network functions, the port scanner actually generates raw IP packets itself and monitors for responses. This scan type is also known as half-open scanning because it never really opens a full TCP connection. The port scanner generates a SYN packet, and if the targeted port is open, it will respond with a SYN-ACK packet. The scanner host responds with an RST (reset) packet, closing the connection before the handshake is completed.
Never use the tools I’m telling you about on computers belonging to any businesses or government agencies without their permission. It’s against the law in a big way, and they do monitor and prosecute! Know that I am not exaggerating here, so please do yourself a favor and use the following tools only to test your own network for vulnerabilities.
Although a free program named Network Mapper (Nmap) can be used as a port scanner, you can use it to do so much more. I give it two thumbs up and recommend that you download Nmap (http://nmap.org) and play with this cool program.
Nmap, like Snort, is open source. But Nmap runs on all platforms and can provide port-scanning ability, check all the open services running on each host, find firewalls, and even help tremendously with network management.
Figure 18-4 shows Nmap running on a Windows Vista platform, performing a Domain Name Service (DNS) resolution and then a port scan to the host being monitored (Zenmap is the name of the GUI interface it uses). Pretty chill, right?
Nmap is very flexible and, again, I really encourage you to check it out. One of the other nice features of Nmap is its documentation capacity. It comes with a complete set of instructions and equips you with documentation to help you troubleshoot and map your network.
Figure 18-4: Nmap in action

Even though Nmap is pretty simple, there are even simpler tools out there—a whole lot of them. Angry IP is a program I also use that provides both IP-scanning and port-scanning abilities. It’s definitely not as complex as Nmap, but because it’s extremely easy to use, you might want to try out this free, open-source program as well. Figure 18-5 illustrates port scanning with Angry IP.
Figure 18-5: Angry IP port scanning
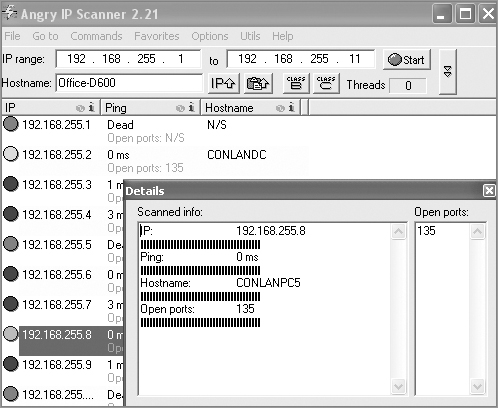
You can see right away that this is a much simpler program than some of the other sniffing and port mapping tools we’ve discussed, but simple doesn’t mean it isn’t powerful. Angry IP slowed the PC I was scanning way down when I performed a full port scan on the host using this program. Check it out at www.angryziber.com/w/Home.
Hacked and Blamed!
I’ve already mentioned that you shouldn’t port scan on hosts that are not yours, but you need to be careful that someone else does not use your hosts or servers to port scan someone else’s servers as well. A few years ago, I had a server at an ISP, and some crackers had hacked into my server and were using it to port scan the Department of Defense (DoD) servers. I received a letter from the DoD informing me of this issue. They were very professional and even mentioned that it probably wasn’t me that was doing the port scanning, but they said that if it happened again, they would prosecute me. They told me that I was responsible for my server and that if I did not stop the attackers, I would be liable.
I was terribly embarrassed, and I was a little freaked out too! After looking at the server logs, I realized that the crackers were from France and that they had been in my server for three months. Instead of just locking down the ports and getting rid of the hackers, I formatted the server. Why? Because crackers/hackers are notorious for creating many backdoors once they are in a system, in case they get caught, so just locking them out would not have solved the problem. If this happens to you, a format is typically what you need to do. I also upgraded to the latest server operating system, which helped with some of the security issues.
After you’ve downloaded all the software tools I just went over with you and practiced honing your skills with them (only on your own network, right?), you’ll be ready to move on and explore the hardware tools that you need to be familiar with to meet the CompTIA Network+ objectives.
A great example of when the hardware tools and testers I’m about to cover would come in really handy is if you’re dealing with failed fiber links between structures. As a system administrator running a network with a server, routers, and switches, it’s entirely possible you’ll never find yourself in a situation that calls for these tools. But if you’re in network design or a field that requires installing cabling, then these hardware tools are going to be really valuable to you. Unlike the software tools we just talked about, none of these goodies are free, but they do come in a variety of flavors that run the gamut from real bargains to “You’re joking—how much?” Some of them can indeed free you of thousands of dollars!
Cable testers are the most widely used hardware tool in today’s LANs, so let’s start with them.
Cable Testers
The best way to deal with a faulty cable installation is to avoid the problem in the first place by purchasing high-quality components and installing them carefully. Still, this isn’t a perfect world—no matter how careful you are, problems are bound to arise anyway. The tools that I’m going to cover can be used to test cables at the time of their installation and afterward, if and when you need to troubleshoot cabling problems. Cable-testing tools can range from simple, inexpensive mechanical devices to elaborate electronic testers that automatically supply you with a litany of test results in an easy-to-read pass/fail format. Figure 18-6 shows an example of an inexpensive cable tester for twisted-pair wiring testing.
Figure 18-6: An inexpensive cable tester

This little box can verify the connection through the cable and tell you if the cable is straight-through or crossover. It can also identify problems such as grounding issues as well. Sometimes the problem is not a complete lack of connectivity. Sometimes performance is slow, which can also be a cabling issue that a cable tester can identify. This tool is as cheap as they come.
Let’s focus on the types of tools available for both copper and fiber-optic cable testing. This is not to say that you need all of the tools listed here. In fact, I’ll try to steer you away from certain types of tools. Sometimes you’ll get lucky and have the luxury of choosing between high-tech and low-tech devices that perform roughly the same function. You can choose which ones you prefer according to the requirements of your network, your operational budget, even your temperament and time constraints. Some of the tools are extremely complicated and require extensive training to use effectively, whereas others can be used by pretty much anybody equipped with a functioning brain.
Other important considerations to keep in mind when selecting the types of tools you need are based on the descriptions of cable tests given earlier in this chapter, the test results required by the standards you’re using to certify your network, and the capabilities of the people who will be doing the actual work. And don’t forget the potentially painful cost of some of them.
Loopback Plug
A loopback test is a diagnostic procedure in which a signal is transmitted and returned to the sending device after passing through all or a portion of a network or circuit. The returned signal is compared with the transmitted signal to evaluate the integrity of the equipment or transmission path. A computer needs a loopback plug that is inserted into a port in order to perform a loopback test.
Loopback plugs are made for both Ethernet and fiber applications. Figure 18-7 shows an Ethernet loopback plug and Figure 18-8 shows a plug for fiber applications.
Figure 18-7: Ethernet loopback plug
Figure 18-8: Fiber loopback plugs

Wire-Map Testers
A wire-map tester is a device that transmits signals through each wire in a copper twisted-pair cable to determine if it’s connected to the correct pin at the other end. Wire mapping is the most basic test for twisted-pair cables because the eight separate wire connections involved in each cable run are a common source of installation errors. Wire-map testers detect transposed wires, opens (broken or unconnected wires), and shorts (wires or pins improperly connected to each other). All of these problems can render a cable run completely inoperable.
Wire-map testing is nearly always included in multifunction cable testers, but sometimes it’s just not worth spending serious cash on a comprehensive device. Dedicated wire-map testers that run about two to three hundred bucks are relatively inexpensive options that enable you to test your installation for the most common faults that occur during installations and afterward. If, say, you’re installing voice-grade cable, a simple wire-mapping test is probably all that’s needed.
A wire-map tester essentially consists of a remote unit that you attach to the far end of a connection and a battery-operated, handheld main unit that displays the results. Typically, the tester displays various codes that indicate the specific type of fault that it finds. You can also purchase a tester with multiple remote units that are numbered so that one person can test several connections without constantly traveling back and forth from one end of the connections to the other to move the remote unit.
The one wiring fault that is not detectable by a dedicated wire-map tester is something known as split pairs. This fault flies under the radar because even though the pinouts are incorrect, the cable is still wired straight through. To detect split pairs, you must use a device that tests the cable for the near-end crosstalk that split pairs cause.
Continuity Testers
A continuity tester is an even simpler and less-expensive device than a wire-map tester; it’s designed to check a copper cable connection for basic installation problems like opens, shorts, and crossed pairs. It will set you back only a few dollars, but such a device usually can’t detect the more complicated twisted-pair wiring faults. It’s still a nice option for basic cable testing, especially for coaxial cables that have only two conductors and so don’t easily confuse whoever is installing them.
Like a wire-map tester, a continuity tester consists of two separate units that you connect to each end of the cable you want to test. Most of the time, the two units can snap together for storage and easy testing of patch cables.
Protocol Analyzer
A protocol analyzer is often confused with a packet sniffer because some products really are both. Remember—a packet sniffer looks at all traffic on a network segment. On the other hand, a protocol analyzer (surprise!) analyzes protocols. These tools come in both software and hardware versions, but compared to the products I listed earlier in this chapter, a network analyzer is likely to give you more information and help than a sniffer will. This is because a bona fide protocol analyzer can actually help you troubleshoot problems, whereas most sniffers just provide information for you to have a ball deciphering.
A network protocol analyzer can perform the following functions:
- Help troubleshoot hard-to-solve problems
- Help you detect and identify malicious software (malware)
- Help gather information, such as baseline traffic patterns and network-utilization metrics
- Help you identify unused protocols so that you can remove them from the network
- Provide a traffic generator for penetration testing
- Possibly even work with an IDS
And last and perhaps most important for you, they can really help you learn about networking in general. This means if you just want to find out why a network device is functioning in a certain way, you can use a protocol analyzer to sniff (there’s that word again) the traffic and expose the data and protocols that pass along the wire.
I’ve found a whole bunch of network analyzers you can use for free at the following location:
www.snapfiles.com/freeware/network/fwpacketsniffer.html
But understand that there’s no way I can verify the validity of this link after this book is published. Again, the terms sniffer and analyzer are used to define the same product found at this link. Both Microsoft’s NetMon and Wireshark are called sniffers and analyzers, and they both are—at least to some degree.
Certifiers
Certification testers—or certifiers—are used to determine whether your network meets specific International Organization for Standardization (ISO) or TIA standards (Cat 5e, Cat 6, or Cat 7). They are the only option for you in this case. Also, if your network is wired with both copper and fiber, you really must use a certification tester.
Basically, a certifier is a combination cable tester and network analyzer, only better, because it comes with more options. This is wonderful because it makes your job easier and makes you seem smarter to everyone around you—you’re only as good as your tools, right? A good certifier will test the performance and response times of network resources like web, file, email, and even DNS and Dynamic Host Configuration Protocol (DHCP) servers. And, at the same time, it will certify your full Category 6 cable installation. After it finishes all this, you can provide your boss with a detailed network test report complete with dazzling, colorful graphics to make it simple to explain and understand—voilà! You’re instantly the genius of the day.
To get these smarts, all you need is a lot of money. These products are not for the small office, home office (SOHO) market because they cost literally thousands of dollars, starting at about $5,000.
Time-Domain Reflectometer
A time-domain reflectometer (TDR) is a tool that finds and describes faults in metallic cables like twisted wire pairs and coaxial cables. The equivalent device for optical fiber is an optical time-domain reflectometer (OTDR), which I’ll talk about in a minute.
A TDR works in the same basic way that radar does. It transmits a short rise time pulse along the conductor, and if it turns out to be of a uniform impedance and properly terminated, the entire transmitted pulse is absorbed in the far-end termination; no signal is reflected back to the TDR. Any impedance interruptions will cause some of the incident signal to be sent back toward the source, letting you know all is not well.
So basically, any increases in the impedance create a reflection that reinforces the original pulse and decreases the impedance, thereby creating a reflection that opposes the original pulse. The resulting reflected pulse that’s measured at the output/input to the TDR is displayed or plotted in measures of time. And because the speed of signal propagation is pretty consistent for a given type of transmission medium, the reading can also tell you about the cable length.
Because of this sensitivity to any variation in impedance, you can use a TDR to verify these things:
- Speed and condition of the cable
- How long it takes to send a signal down a cable and how long it takes to come back
- Cable impedance characteristics
- Splice and connector locations and their associated loss amounts
- Estimated cable lengths
Now, let’s take a look at a device that tests fiber-optic cables.
Optical Time-Domain Reflectometer
An optical time-domain reflectometer (OTDR) is an optoelectronic instrument used to give you the skinny on optical fibers. It works by putting out a series of optical pulses into the specific fiber you want to test. From the same end from which these impulses were sent, it collects and measures the light that is scattered and reflected along the length of the fiber. It then records the change in the amount of refraction at various points. From the same end from which these impulses were sent, it collects and measures the light that is scattered and reflected along the length of the fiber. It then records the change in the amount of refraction at various points. This is a lot like the way an electronic TDR measures reflections caused by impedance changes in a cable that you’re testing. The strength of the return pulses is incorporated into a measure of time, which also conveniently gives you the fiber’s length.
We use OTDRs to give us the following information:
- The fiber’s estimated length
- Its overall attenuation, including splice and mated-connector losses
- The location faults, such as breaks
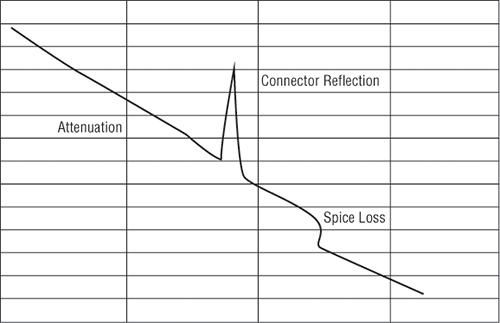
Figure 18-9 shows the output from an OTDR testing a fiber connection.
The spike shows where a splice in the fiber is located, which has resulted in the signal being degraded. This is a very typical output. As the signal attenuates, you see a gradual but quick drop in decibels (db). Any connector will actually show a reflection, which, as mentioned, shows up as a spike in the OTDR output. The connector then creates more attenuation and loss of more db. The more splices, the less distance you can run with fiber.
Figure 18-9: Sample OTDR output
Multimeter
A multimeter or a multitester (also called a volt/ohm meter [VOM]) is a multitasking electronic measuring instrument. Your average multimeter typically includes features like the ability to measure voltage, current, and resistance. Multimeters come in analog and digital versions, and they range from basic handheld devices useful for simple fault-finding and field-service work to more complex bench instruments that will give you measurements with a very high degree of accuracy.
They can be used to troubleshoot electrical problems in a wide array of electrical devices like batteries, motor controls, appliances, power supplies, and wiring systems. Figure 18-10 shows the multimeter that I use to help troubleshoot my networks.
Multimeters come in lots of flavors with different ranges of features and prices. Cheap ones cost less than 10 bucks, but the top-of-the-line models can set you back up to 5 thousand.
Toner Probe
A toner probe, also called a tone generator, is a simple copper cable tester that is simple to use and can be used to trace a wire in a wall. It is a two-piece unit that’s basically a tone generator and probe, sometimes called a “fox and hound” wire tracer. This type of device consists of one part that you connect to a cable with a standard jack—or to an individual wire with alligator clips that transmit a signal over the cable or wire—and another part that’s a penlike probe that emits an audible tone when it touches the other end of the cable, the wire, or even its insulating sheath.
Most often, you will use a toner probe to locate a specific connection in a punch-down block because (annoyingly) some installers run all the cables for a network to the central punch-down block without labeling them. They (or you, if you’re unlucky enough) then have to use a tone generator to identify which block is connected to which wall plate and label the punch-down block accordingly. This tool can identify a particular cable at any point between the two ends, and because the probe can detect the cable containing the tone signal through its sheath, it can help you to locate one specific cable out of a massive cable-spaghetti bundle in a ceiling conduit or other type of raceway.
Figure 18-10: A multimeter

Just connect the tone generator to one end, and touch the probe to each cable in the bundle until you hear the tone. Figure 18-11 shows a picture of my toner and the probe I use to find the tone on the other end of the cable.
Also, by testing the continuity of individual wires using alligator clips, you can use a tone generator and probe to find opens, shorts, and miswires. An open wire won’t produce a tone at the other end, a short will produce a tone on two or more wires at the other end, and an improperly connected wire will produce a tone on the wrong pin at the other end.
Sound like fun to you? Well, not so much—it takes a really long time, and it’s super tedious. Worse, the whole process is almost as prone to errors as the cable installation itself. You have to either continually travel from one end of the cable to the other to move the tone generator unit or use a partner to test each connection, keeping in close contact using radios or some other means of communication to avoid confusion. So, considering the time and effort involved, investing in a wire-map tester is just a much more practical solution unless you’re numbingly bored or really easily amused.
Figure 18-11: A toner probe

Butt Set
A butt set is essentially a portable telephone that allows you to test analog wet or dry lines and is used to monitor those lines. The most common type, shown in Figure 18-12, can both monitor and transmit.
You see these all the time with telco guys up on the telephone poles. They use their butt sets to connect to telephone lines, test them, and even make phone calls.
Another handy tool that will take the place of a butt set is a hound. This noncanine device is nothing more than an inductively coupled amplifier with a small speaker in a handheld tool. It’s used to monitor the audio on a given line to verify that you have the right pair before connecting it and typically is used with a toner probe. It will also monitor for noise.
Punch-Down Tool
Most networks today are built using twisted-pair cable of some sort. This cable is usually terminated in wiring closets using a tool known as a punch-down tool. It’s called that because that’s exactly what the tool does—punch down the wire into some kind of insulation displacement connector (IDC).
Figure 18-12: A butt set

There are different types of punch-down tools. The most common is a punch down with replaceable blades for the different types of connectors (either 66 or 110). Figure 18-13 shows an example of this type of punch-down tool.
Figure 18-13: An example of a punch-down tool
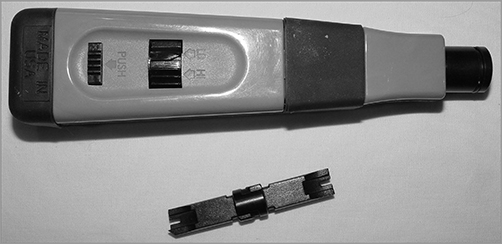
IDCs make contact by cutting through, or displacing, the insulation around a single conductor inside a twisted-pair cable.
As shown in Figure 18-14, the punch-down tool pushes a conductor between the sides of a V inside an IDC, in this example a 110 block, allowing the small metal blade inside the connector to make contact with the inner conductor deep inside the wire.
Figure 18-14: Using a punch-down tool on a small 110 block

Now let’s take a look at how to put a cable end together.
Cable Stripper/Snips
A wire crimper, often simply called a crimper, is a handy tool found in most network technicians’ tool bags. Crimpers are primarily used for attaching ends onto different types of network cables via a process known as—that’s right—crimping. Crimping involves using your hands to apply a certain amount of force to press some kind of metal teeth into the inner conductors of a cable. Before you can crimp a connector onto the end, you’ve got to strip the cable with a type of cable stripper (or snips) and then properly put the wires into the connector.
Figure 18-15 shows what a cable stripper and snip looks like (this particular tool also includes a crimper).
Often, network technicians will make patch cables with a crimper. They’ll take a small piece of Category 5e unshielded twisted-pair (UTP), strip the cable, and crimp two RJ-45 ends onto it to create the cable. Snips will create the type of cable needed to connect a host to a wall jack connection, for example. There are strippers and crimpers for the other types of cable as well—even specialized crimpers for fiber-optic ends.
Voltage Event Recorder
Alternating current (AC) is basically the food that PCs and other network devices require in specific amounts to function properly. In the United States, it’s normally 110 volts and changes polarity 60 times a second (60 hertz). These values are referred to as line voltage. Any deviation from these values can create some major problems for your PC or other electronics—like death.
Figure 18-15: A combination cable stripper, crimper, and snippers

This is why we have surge protectors. These little saviors use a special electronic circuit that monitors the incoming voltage level and trips a circuit breaker when the voltage level reaches critical mass which is known as the overvoltage threshold. Even though having a surge protector is definitely better than nothing, they too can fall victim to overvoltage events—I’m reminded of a friend whose home was struck by lightning during a thunderstorm and he found his surge protectors literally melted into the carpet! But they’re still cool because even though they’re really only somewhat protective, they are multiple-outlet strips that give us a lot more places to plug in our stuff.
By contrast, a quality voltage event recorder can troubleshoot and even provide preventative maintenance on your entire electrical system, whether it’s a home or a huge factory. Although they do big things, they’re typically small devices that just plug into a wall and record, over time, the power quality of a given circuit. You would typically use a voltage event recorder for the following applications:
Recording voltage The voltage event recorder monitors and records the supply voltage and checks whether the socket outlet is providing voltage within specifications.
Measuring distortion The device measures frequency and harmonics, and it checks whether your uninterruptible power supply (UPS) system is functioning correctly.
Measuring flicker It checks the switching loads on lighting systems.
Capturing voltage transients It can help you find intermittent, momentary events that may be affecting your equipment; the full waveform is captured with date, time stamp, and duration.
But you still have to do more to ensure the vitality of your electronic devices because they’re very sensitive to temperature as well. This means you also need a way to monitor the temperature of the place(s) where your equipment is stored.
Environmental Monitors
Environmental monitors are designed to monitor the temperate, humidity, and air flow in an area or in a device. Temperature and humidity are both critical factors in the health of computing equipment. High temperatures lead to CPU overheating and shortly thereafter systems start rebooting.
High humidity cannot be tolerated because it leads to corrosion of electrical parts followed by shorts and other failures. Low humidity sounds good on paper, but with it comes static electricity buildup in the air, which can fry computer parts if it reaches them. Both of these conditions should be monitored.
A temperature and humidity monitor can save you and your precious devices from a total meltdown. By their very nature, networks often include lots of machines placed close together in one or several location(s)—like server rooms. Clearly, these devices, all humming along at once, generate quite a bit of heat.
Just like us, electronics need to “breathe,” and they’re also pretty sensitive to becoming overheated, which is why you’ll often need a jacket in a chilly server room. It’s also why we need to set up and use temperature-monitoring devices. Twenty years ago or so, these devices didn’t send alerts or give off any kind of alarms; they were just little plastic boxes that had pieces of round graph paper to graph temperature. The paper was good for a month, and for that duration, it would just spin around in a circle being drawn on by a pen attached to the temperature coil. As the temperature moved up or down, the pen moved in or out, leaving a circle line around the paper. All of this allowed you to manually monitor the temperature modulation in the server room over time. Although intended to “alert” you when and if there were climate changes, it usually did so after the fact, and therefore, too late.
Today, these temperature/humidity systems can provide multiple sensors feeding data to a single control point—nice. Now we can much more accurately track the temperature in our server rooms dynamically in real time. The central control point is usually equipped with HTTP software that can send alerts and provide alarms via a browser should your server room experience a warming event.
Temperature/humidity monitors also come in a variety of flavors. They vary in size and cost and come in hardware and/or software varieties. The kind you need varies and is based on the size of the room and the number of devices in it. You can even get one that will just monitor your PC’s internal heat.
What type of indication or other problems will indicate you have a temperature problem in your server room? When you install new servers in a rack and you have network instability and other issues across all the servers in the rack but the power resources and bandwidth have been tested, this would be a good time to check your temperature monitor and verify that the servers are staying cool enough. Another red flag when it comes to environmental issues is a problem that occurs every day at the same time. This could be the time of day when the room temperature reaches the problematic stage.
You need network tools, and you need to know how to use them. And as I said, you can get your hands on many of them for free; so download them and use them as soon as possible to get the experience you’ll need to pass the CompTIA Network+ exam.
This chapter covered network scanners, including packet sniffers, IDS and IPS software, and port scanners. I also covered hardware tools, which are rarely free. The good news is that you don’t need many of them yourself, but the company that owns all the equipment definitely does. Even though I’ve used all of the tools I talked about in this chapter, I don’t own most of them personally—only the ones that are free or relatively inexpensive.
In the hardware tools section, I covered cable testers, analyzers, certifiers, TDR/OTDRs, and other critical tools that help you test the cables and devices in your network, monitor them, and keep them up and running smoothly.
Understand what network scanners are and how to use each one. Network scanners are described as packet sniffers, IDS/IPS software, and port scanners. These devices can help you both troubleshoot and fix your network as well as find and stop hackers in their tracks.
Remember the basic purpose of a packet sniffer. The basic purpose of packet sniffers or network analyzers is to collect and analyze each individual packet that is captured on a specific network segment to determine if problems are happening.
Remember the main purpose of IDS/IPS software. The IDS detects unwanted attempts to manipulate network systems and/or environment, and the IPS is a computer security device that monitors network and/or system activities for malicious behavior and can react in real time to stop attacks.
Understand what an OTDR is used for. An optical time-domain reflectometer (OTDR) is an optoelectronic instrument used to test fiber-optic cabling. You can learn the cable’s estimated length and attenuation (loss in db) and the location of faults.
Understand the difference between cable testers and certifiers. Cable testers simply tell you if the cable will function. Cable certifiers run much more sophisticated tests that determine if the cable performs according to specifications called for in the standard.
Understand the value of temperature and humidity monitors. These devices can monitor environmental conditions and alert you if either the temperature or the humidity in a server room or area falls below or rises above the prescribed range of safe values.
Answer the following questions about software and hardware tools:
1. True/False: An IDS box can find and fix a problem as the attack occurs.
2. True/False: A TDR is used to test fiber connections.
3. True/False: An IDS box will report an attack but not fix it.
4. True/False: An OTDR is used to test fiber connections.
5. True/False: A network analyzer will see every packet on every segment of your network at the same time.
6. What type of device determines if a cable meets standards specifications?
7. True/False: It is okay to scan the DoD network servers with a port scanner.
8. You need to monitor the temperature of your server room. What device should you use?
9. You want to monitor your UPS systems and make sure they are functioning correctly. What device should you use?
10. What type of device is used to put an RJ-45 end on a Cat 5e cable?
You can find the answers in Appendix B.
You can find the answers in Appendix A.
1. Which is a tool in the network scanner category?
A. Packet sniffers
B. IDS/IPS software
C. Port scanners
D. All of the above
2. What is the purpose of packet sniffers?
A. Discarding frames
B. Sending transmissions from one port to another port
C. Looking inside every packet on a network segment
D. Stopping malicious behavior on the network
3. You need to trace cables in multiple pair wiring. What tool will you use?
A. Toner probe
B. IDS
C. Cable tester
D. Butt set
4. What tool would you use to both find a break in a fiber-optic connection and test the fiber connectivity on the network?
A. Multimeter
B. OTDR
C. Butt set
D. Toner probe
5. You need to create a cable that will connect your host to a wall jack connection. Which of the following will you use?
A. IDS/IPS
B. Snips
C. Coax cable strippers
D. Multimeter
6. Where is the IDS/IPS software typically placed within a network?
A. Between the internal router and the firewall connected to the ISP
B. Between the printer and the router connected to the ISP
C. Between the computer and the switch configured with VLANs
D. Between the firewall and the router connected to the email server
7. What is the purpose of a port scanner?
A. Scan UDP for closed ports
B. Sweep TCP for closed ports
C. Search the network host for open ports
D. None of the above
8. What is the purpose of wire-map testers?
A. Check copper cable for crossed pairs only
B. Analyze protocols in software
C. Help find unused protocols and remove them from the network
D. Detect transposed wires, opens, and shorts in twisted-pair cables
9. Which of the following can check the speed and condition of the signal on a cable, measure the time it takes to send a signal down the wire and back, and find the exact location of a break?
A. Multimeter
B. TDR
C. Tone generator
D. Event recorder
10. Which device should be used if you need to determine whether your network meets ISO or TIA standards?
A. Angry IP
B. Certifiers
C. Nmap
D. Routing table
11. Which software tool is used to view network traffic at the frame level?
A. TDR
B. Multimeter
C. Port scanner
D. Packet sniffer
12. Which of the following options is not a function of a TDR?
A. Estimate cable lengths
B. Find splice and connector locations and their associated loss amounts
C. Display unused services
D. Determine cable-impedance characteristics
E. Send a signal down a cable and measure how long it takes to come back
13. Which device would be used to measure voltage?
A. Multimeter
B. OTDR
C. Butt set
D. Toner probe
14. Which device would most likely be used to locate a specific connection in an unlabeled punch-down block?
A. VOM
B. Certifier
C. TDR
D. Toner probe
15. Which tool would be used to connect wire between two punch-down block blades?
A. Punch-down tool
B. Crimper
C. Snips
D. Strippers
16. Which tool is used to attach an RJ-45 connector to a Cat 5 cable?
A. Punch-down tool
B. Crimper
C. Snips
D. Strippers
17. Which of the following would a technician use a punch-down tool on?
A. RJ-45 connector
B. CSU/DSU
C. 110 block
D. Fiber ST connector
18. Which device monitors incoming voltage levels and overvoltage thresholds?
A. Repeater
B. Toner probe
C. VOM
D. Surge protector
19. Which of the following tools can test a port on a device?
A. Cable certifier
B. Loopback plug
C. Butt set
D. Toner probe
20. You install new switches in your server room and are now experiencing network instability and other issues across all servers in the rack. Which device would be used to alert you of a system overheating?
A. Voltage event recorder
B. Temperature monitor
C. Surge protector
D. Probe
