|
1. |
Implementing network security is often described as a balancing act between three competing needs. Choose these needs from the following:
|
|
2. |
Fill in the blank. A disturbing recent trend has been what Cisco calls ______ threats, which focus on the application layer of the OSI model.
|
|
3. |
What are the three broad categories of security controls?
|
|
4. |
True or false. Hackers are known for thinking “inside the box” because their integral understanding of a system’s inner workings make them uniquely able to exploit weaknesses in design. |
|
5. |
Which of the following are not considered attacks against availability? (Choose all that apply.)
|
|
6. |
Fill in the blanks in the quantitative risk analysis formula with the missing variables. (Choose two; the order makes no difference.)
|
|
7. |
Network security testing is considered an important part of assessing a network’s resilience against attacks and establishing the requirement for security controls (physical, administrative, and technical). Which of the following is not a goal of network security testing?
|
|
8. |
Some of the items in the following list represent categories of disruption. Identify the three correct categories of disruption by putting them in order from least disruptive to most disruptive:
|
|
9. |
What are the three main groups of stakeholders in a security policy?
|
|
10. |
Which of the following Cisco products cannot be managed by the Cisco Security Manager?
|
|
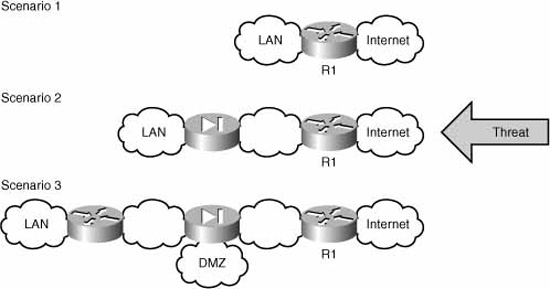
11. |
In the following figure, what do scenarios 1, 2, and 3 represent, respectively?
|
|
12. |
True or false. The service password-encryption command encrypts all the passwords on the device with the exception of the enable secret, which uses a hash. |
|
13. |
Views are very useful in creating role-based rules as to which commands are authorized for execution. Examine the sequence of commands and choose all the correct statements from the list that follows them.
|
|
14. |
With respect to AAA, access to the router is called remote ________ access and access through the router is called remote ________ access. (Pick the answer that fills in the blanks in the correct order.)
|
|
15. |
What are the three main task areas for setting up external AAA? Choose from the following list:
|
|
16. |
With respect to secure management and reporting, traffic can flow either ________, meaning that it is separate from the production network, or ________, meaning that the traffic flows across the production network. (Pick the answer that fills in the blanks in the correct order.)
|
|
17. |
For the following names of Cisco log severity levels, fill in their level:
Names:
Errors __
Informational __
Alerts __
Emergencies __
Debugging __
Warnings __
Notifications __
Critical __ |
|
18. |
Choose the statement that best describes what is being represented in the following figure.
|
|
19. |
What are the Cisco AutoSecure features that SDM Security Audit does not implement? (Choose all that apply.)
|
|
20. |
What are the two parameters that have to be configured before RSA keys can be generated to support SSH on the router?
|
|
21. |
Which of the following is Cisco’s definition of a firewall?
|
|
22. |
Match the following firewall types with the letter corresponding to the layers of the TCP/IP protocol stack at which they operate:
Firewall Types
TCP/IP Layers
A. 1 to 4
B. 1 to 5
C. 1 to 2
|
|
23. |
True or false. Assuming that the IOS router is also the VPN endpoint, encrypted packets are tested on an inbound ACL twice. |
|
24. |
Fill in the blanks. Interface ACLs are still relevant and can be used to complement Zone-Based Policy Firewall (ZPF) policies. Inbound ACLs are applied ________ ZPF policies and outbound ACLs are applied ________ ZPF policies. |
|
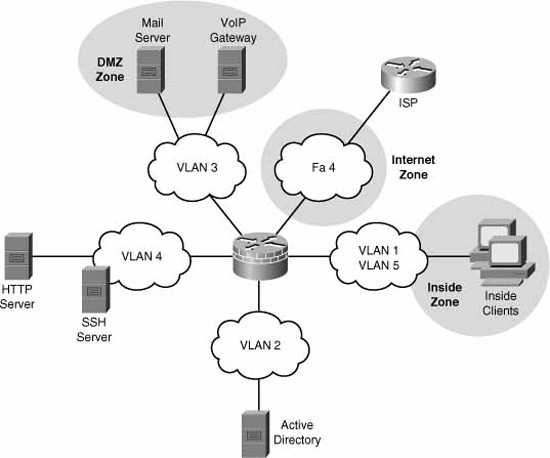
25. |
Examine the figure and answer the subsequent question.
True or false. The traffic from Vlan 2 to FastEthernet4 (Fa 4) will be forwarded. |
|
26. |
What is the area of the largest vulnerability in modern cryptosystems?
|
|
27. |
Fill in the blank. You are asked to implement a new cryptosystem that uses ciphers to provide for confidentiality of data transmitted. Researching industry data, you decide to use 3DES and not AES because 3DES ________.
|
|
28. |
True or false. Modern SSL VPNs use Transmission Level Security (TLS) instead of Secure Sockets Layer (SSL) because it is a newer, standards-based replacement for SSL. |
|
29. |
In a typical asymmetric key cryptosystem, node A will encrypt messages with the node B’s ________ and will decrypt messages from node B using node A’s own ________. Safeguarding the ________ is essential. (Pick the answers that fill in the blanks in the correct order; choices can be reused.)
|
|
30. |
Which of the following represent common Cisco applications of certificate-based authentication?
|
|
31. |
What are the two main categories of VPN?
|
|
32. |
True or false. In IPsec VPNs, Internet Key Exchange (IKE) Phase I carries data, and IKE Phase II exists only to negotiate and authenticate, but does not carry data. |
|
33. |
Fill in the blanks in the following description of IKE Phase I negotiations.
The separate elements of IKE Phase I negotiation are grouped in a ________. During IKE Phase I, either main mode or ________ may be chosen to perform negotiations. When this negotiation is complete, some vendors use their own proprietary negotiation protocol to negotiate additional parameters. Cisco’s proprietary protocol for remote-access IPsec VPNs is called ________. After Phase I is complete, ________ negotiates the IKE Phase II parameters.
Choices:
|
|
34. |
Examine the following commands:
Which statements are correct with respect to these commands? (Choose all that apply.)
|
|
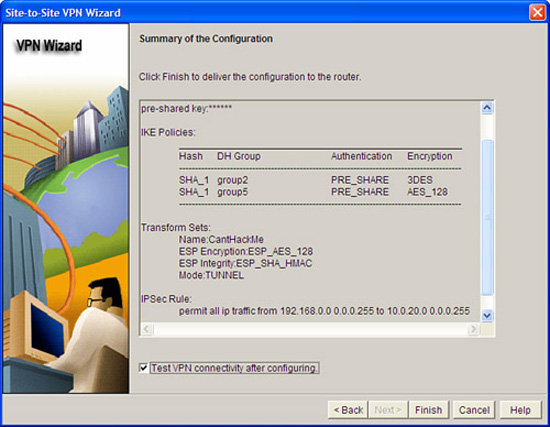
35. |
Examine the figure. It is a screenshot showing the summary of a VPN created with the Cisco SDM Site-to-Site VPN Wizard.
Which statements are correct with respect to the figure? (Choose all that apply.)
|
|
36. |
Which of the following are examples of Cisco IDS or IPS solutions? (Choose all that apply.)
|
|
37. |
Match the types of IPS alarms below with their descriptions:
IPS Alarms:
Descriptions:
|
|
38. |
What are the three main detection technologies that the Cisco IOS IPS employs?
|
|
39. |
True or false. Cisco recommends that the alert level of any signature should be set to the severity level of the signature, both for the included signature as well as for created signatures. |
|
40. |
Which CLI command verifies all Cisco IOS IPS settings?
|
|
41. |
What are the three prongs of Cisco’s Host Security Strategy?
|
|
42. |
What is Cisco’s solution for preventing a buffer overflow attack?
|
|
43. |
Match the following interceptors that CSA employs with their definitions:
Terms:
Definitions:
A. All file read/write requests are intercepted and permitted or denied based on the security policy.
B. Stymies DoS attacks by limiting the number of connections that can be made in a specified period.
C. Examines read/write requests to system configuration files.
D. Ensures that each application is only allowed write access to memory that it owns.
|
|
44. |
What is the main strategy for securing access to SANs?
|
|
45. |
Which of the following Cisco Unified Communications Manager (UCM) features can protect the VoIP network against fraud? (Choose all that apply.)
|
|
46. |
What statement best describes a VLAN hopping attack in general terms?
|
|
47. |
True or false. The best way to prevent a double-tagging VLAN hopping attack is to make sure that the native VLAN of the trunked ports is different than any of the users’ ports. |
|
48. |
Examine the following commands and answer the subsequent question.
Which of the following statements about this series of commands is correct? (Choose all that apply.)
|
|
49. |
Which commands do you use to verify that port security is configured and operational on an interface? (Choose two.)
|
|
50. |
Which of the following interface configuration commands set the native VLAN of a trunk to 10?
|