Chapter 5. Malware
Chapter Objectives
After reading this chapter and completing the exercises, you will be able to do the following:
Understand viruses (worms) and how they propagate, including famous viruses like WannaCry, Rombertik, and Petya
Have a working knowledge of several specific virus outbreaks
Understand how virus scanners operate
Understand what a Trojan horse is and how it operates
Have a working knowledge of several specific Trojan horse attacks
Grasp the concept behind the buffer-overflow attack
Have a better understanding of spyware and how it enters a system
Defend against each of these attacks through sound practices, antivirus software, and antispyware software
Introduction
In Chapter 4, “Denial of Service Attacks,” we examined the denial of service (DoS) attack, which is a very common attack and one that can easily be perpetrated. In this chapter, we will continue our examination of security threats by looking at several other types of attacks. First, you will learn about virus outbreaks. Our discussion will focus on information about how and why virus attacks work, including their deployment through Trojan horses. This chapter is not a “how to create your own virus” tutorial but rather an introduction to the concepts underlying these attacks as well as an examination of some specific case studies.
This chapter will also explore viruses, worms, buffer-overflow attacks, spyware, and several other forms of malware. Each of these brings a unique approach to an attack, and each needs to be considered when defending a system. Your ability to defend against such attacks will be enhanced by expanding your knowledge of how they work. In the exercises at the end of the chapter, you will have the opportunity to research preventive methods for viruses and to try out antivirus methods from McAfee, Norton, AVG, Bitdefender, Kaspersky, Malwarebytes, and other antivirus vendors.
Before proceeding, there are two important facts to keep in mind. The first is that the categories described in this chapter are not always clear in real-world malware. For example, a single piece of malware might combine virus functionality and spyware capabilities and might also be used to launch a DoS attack. It is still important to learn and understand the categories of malware, but you also need to be aware that many real-world malware examples overlap several categories. The second fact to keep in mind is that the world of malware is very dynamic. Things are changing fast. We will look at specific examples that are worthy of study due to their prominence in the history of malware, but it is a good idea to always stay current and constantly review the most recent malware outbreaks.
Viruses
By definition, a computer virus is a program that self-replicates. Some sources define a virus as a file that must attach to another file, such as an executable, in order to run. However, that is not accurate. Generally, a virus will also have some other unpleasant function, but the self-replication and rapid spread are the hallmarks of a virus. Often this growth, in and of itself, can be a problem for an infected network. Any rapidly spreading virus can reduce the functionality and responsiveness of a network. Simply by exceeding the traffic load that a network was designed to carry, the network may be rendered temporarily nonfunctional. The infamous ILOVEYOU virus actually had no negative payload, but the sheer volume of emails it generated bogged down many networks.
How a Virus Spreads
A virus usually spreads primarily in one of just a few ways. The first is to simply email itself out to everyone in your email address book. Another method is to scan your computer for connections to a network and then copy itself to other machines on the network to which your computer has access. Viruses can also reside on portable media such as USB devices, CDs, or DVDs. It is also possible to mask a virus with a legitimate file; in this case, it is called a Trojan horse. Sometimes a website is infected with a virus, and when someone visits the website, that person’s computer becomes infected.
The email method is, by far, the most common method for virus propagation, and Microsoft Outlook may be the one email program most often hit with such virus attacks. The reason is not so much a security flaw in Outlook as it is the ease of working with Outlook. All Microsoft Office products are made so that a legitimate programmer who is writing software for a business can access many of the application’s internal objects and thereby easily create applications that integrate with the applications within the Microsoft Office suite. For example, a programmer could write an application that would access a Word document, import an Excel spreadsheet, and then use Outlook to automatically email the resulting document to interested parties. Microsoft has done a good job of making this process very easy, and it usually takes a minimum amount of programming to accomplish these tasks. Using Outlook, it takes less than five lines of code to reference Outlook and send out an email. This means a program can cause Outlook itself to send emails, unbeknownst to the user. There are numerous code examples on the Internet that show exactly how to do this, free for the taking. For this reason, it does not take a very skilled programmer to be able to access your Outlook address book and automatically send emails. Essentially, the ease of programming Outlook is why there are so many virus attacks that target Outlook.
While the overwhelming majority of virus attacks spread by exploiting the victim’s existing email software, some virus outbreaks have used other methods for propagation, such as their own internal email engine. Another virus propagation method is for a virus to simply copy itself across a network. Virus outbreaks that spread via multiple routes are becoming more common.
The method of delivering a payload can be rather simplistic and rely more on end-user negligence than on the skill of the virus writer. Enticing users to go to websites or open files they should not visit or open is a common method for delivering a virus and one that requires no programming skill at all. Regardless of the way a virus arrives at your doorstep, once it is on your system, it will attempt to spread and, in many cases, will also attempt to cause some harm to your system. Once a virus is on your system, it can do anything that any legitimate program can do—so it could potentially delete files, change system settings, or cause other harm.
Types of Viruses
There are many different types of viruses. In this section we will briefly look at some of the major virus types. Viruses can be classified by either their method for propagation or their activities on the target computers.
Macro: Macro viruses infect the macros in office documents. Many office products, including Microsoft Office, allow users to write mini-programs called macros. These macros can also be written as a virus. A macro virus is written into a macro in some business application. For example, Microsoft Office allows users to write macros to automate some tasks. Microsoft Outlook is designed so that a programmer can write scripts using a subset of the Visual Basic programming language, called Visual Basic for Applications (VBA). This scripting language is, in fact, built into all Microsoft Office products. Programmers can also use the closely related VBScript language. Both languages are quite easy to learn. If such a script is attached to an email and the recipient is using Outlook, then the script can execute. That execution can do any number of things, including scan the address book, look for addresses, send out email, delete email, and more.
Multi-partite: Multi-partite viruses attack the computer in multiple ways, for example, infecting the boot sector of the hard disk and one or more files.
Memory resident: A memory-resident virus installs itself and then remains in RAM from the time the computer is booted up to when it is shut down.
Armored: An armored virus uses techniques that make it hard to analyze. Code confusion is one such method. The code is written such that if the virus is disassembled, the code won’t be easily followed. Compressed code is another method for armoring a virus.
Sparse infector: A sparse infector virus attempts to elude detection by performing its malicious activities only sporadically. With a sparse infector virus, the user will see symptoms for a short period, then no symptoms for a time. In some cases the sparse infector targets a specific program but the virus executes only every 10th time or 20th time that target program executes. Or a sparse infector may have a burst of activity and then lie dormant for a period of time. There are a number of variations on the theme, but the basic principle is the same: to reduce the frequency of attack and thus reduce the chances for detection.
Polymorphic: A polymorphic virus literally changes its form from time to time to avoid detection by antivirus software.
Metamorphic: A metamorphic virus is a special case of the polymorphic virus that completely rewrites itself periodically. Such viruses are very rare.
Boot sector: As the name suggests, this type of virus infects the boot sector of the drive. Such viruses can be difficult for antivirus software to find because most antivirus software runs within the operating system, not in the boot sector.
Virus Examples
The threat from virus attacks cannot be overstated. While there are many web pages that give information on viruses, in my opinion, there are only a handful of web pages that consistently give the latest, most reliable, most detailed information on virus outbreaks. Any security professional will want to consult these sites on a regular basis. You can read more about any virus, past or current, at the following websites:
https://us.norton.com/internetsecurity-malware-virus-faq.html?
http://www.techrepublic.com/pictures/the-18-scariest-computer-viruses-of-all-time/
The following sections will look at a number of real-world virus outbreaks. We will examine very recent viruses as well as some examples from 10 or more years in the past. This should give you a fairly complete overview of how viruses behave in the real world.
WannaCry
This was the big news of 2017. In March 2017, WannaCry hit the world in a storm of activity. However, this virus will be studied for many years to come. There are several reasons for this. The first reason this virus is noteworthy, is that there was a patch for the vulnerability it exploited, and that patch had been available for weeks. This illustrates why patch management is such an important part of cybersecurity.
The WannaCry virus had an odd feature: It had a built-in kill switch. If a particular URL was registered, that would kill WannaCry. A man named Marcus Hutchins accidentally discovered the kill switch and stopped WannaCry. Hutchins was initially hailed as a hero, but he was later arrested by the FBI (not in connection with WannaCry) for developing and selling banking Trojan malware.
Petya
Petya was first discovered in 2016 but continued to spread all the way into 2018. It targeted Windows machines, infecting the boot sector and encrypting the hard drive’s file system. It then demanded payment in bitcoin. This is an excellent example of a virus combining multiple features. The virus’s name comes from the 1995 James Bond movie Golden Eye, in which Petya is one of the Soviet weapons satellites.
Shamoon
The Shamoon virus was first discovered in 2012, and a variant resurged in 2017. Shamoon acts as spyware but deletes files after it has uploaded them to the attacker. The virus attacked Saudi Aramco workstations, and a group named Cutting Sword of Justice claimed responsibility for the attack.
Rombertik
Rombertik wreaked havoc in 2015. This malware uses the browser to read user credentials to websites. It is most often sent as an attachment to an email. Perhaps even worse, in some situations Rombertik will either overwrite the master boot record on the hard drive, making the machine unbootable, or begin encrypting files in the user’s home directory.
Gameover ZeuS
Gameover ZeuS is a virus that creates a peer-to-peer botnet. Essentially, it establishes encrypted communication between infected computers and the command and control computer, allowing the attacker to control the various infected computers. (A command and control computer is the computer used in a botnet to control the other computers. These are the central nodes from which a botnet will be managed.) In 2014 the U.S. Department of Justice was able to temporarily shut down communication with the command and control computers; then in 2015 the FBI announced a reward of $3 million for information leading to the capture of Evgeniy Bogachev for his alleged involvement with Gameover ZeuS.
CryptoLocker and CryptoWall
One of the most widely known examples of ransomware is the infamous CryptoLocker, first discovered in 2013. CryptoLocker utilized asymmetric encryption to lock the user’s files. Several varieties of CryptoLocker have been detected.
CryptoWall is a variant of CryptoLocker first found in August 2014. It looked and behaved much like CryptoLocker. In addition to encrypting sensitive files, however, it would communicate with a command and control server and even take a screenshot of the infected machine. By March 2015 a variation of CryptoWall had been discovered bundled with the spyware TSPY_FAREIT.YOI; this variant actually steals credentials from the infected system in addition to holding files for ransom.
Atlanta’s Ransomware Attack
The city of Atlanta, Georgia, was hit with ransomware in March 2018. Many of the city’s systems were impacted, including utilities, courts, and other essential systems. Two Iranian hackers, Faramarz Savandi and Mohammed Mansouri, were indicted for the attack. This attack is noteworthy for several reasons. The first is that it used the SamSam ransomware, which gets access to systems not through phishing but rather via brute-force password guessing. The second issue is that Atlanta had previously been criticized for failing to spend adequately on security. An audit just 2 months before the attack had found 1500 to 2000 vulnerabilities.
FakeAV
While the FakeAV virus has been around for several years, it is well worth studying. This virus, which first appeared in July 2012, affected Windows systems ranging from Windows 95 to Windows 10 and Windows Server 2016. It was a fake antivirus (thus the name FakeAV) that would pop up fake virus warnings. This was not the first such fake antivirus malware, but it is a successful example of the type.
MacDefender
The MacDefender virus is very interesting for multiple reasons. First, it specifically targets Mac computers. Most experts for a long time agreed that Apple products remained relatively virus free simply because their products did not have enough market share to attract the attention of virus writers. Many suspected that if Apple garnered a greater market share, it would also begin to experience more virus attacks, and this has proven to be true.
The MacDefender virus was first seen in the early months of 2011, and variations are still seen today. It is embedded in some web pages, and when a user visits those web pages, she is given a fake virus scan that tells her she has a virus, and it needs to be fixed. The “fix” is actually downloading a virus. The point of the virus is to get end users to purchase the MacDefender “antivirus” product. This is the second reason this case is noteworthy. Fake antivirus attacks, also known as scareware, have been becoming increasingly common.
Kedi RAT
In September 2017 the Kedi RAT (Remote Access Trojan) virus was spreading through phishing emails. Once on an infected system, it would steal data, and then it would exfiltrate that data by emailing it via a Gmail account. It specifically attempted to identify personal and/or financial data on the infected system to sell.
The Sobig Virus
Sobig, which was first found in 2003, is not a recent virus, but it is an excellent virus to study because it received a lot of media attention and caused a lot of harm when it hit. This virus used a multimodal approach to spreading—that is, it used more than one mechanism to spread and infect new machines. It would copy itself to any shared drives on your network and would email itself out to everyone in your address book. Sobig was therefore particularly virulent, which is also why it is important to study.
FYI: Virulent Virus
The term virulent means essentially the same thing in reference to a computer virus as it does in relationship to a biological virus: It is a measure of how rapidly the infection spreads and how easily it infects new targets.
In the case of Sobig, if one person on a network was unfortunate enough to open an email containing the virus, not only would his machine be infected, but so would every shared drive on that network to which this person had access. However, Sobig, like most other email-distributed virus attacks, had telltale signs in the email subject or title that could be used to identify the email as one infected by a virus. The email would have some enticing title such as “here is the sample” or “the document” to encourage you to be curious enough to open the attached file. The virus would then copy itself into the Windows System directory.
This particular virus spread so far and infected so many networks that the multiple copying of the virus alone was enough to bring some networks to a standstill. This virus did not destroy files or damage the system, but it generated a great deal of traffic that bogged down the networks it infected. The virus itself was of moderate sophistication. Once it was out, however, many variants began to spring up, further complicating the situation. One of the effects of some variants of Sobig was to download a file from the Internet that would then cause printing problems. Some network printers would just start printing junk. The Sobig.E variant would even write to the Windows Registry, causing itself to be in the computer startup. These complex characteristics indicate that the creator knew how to access the Windows Registry, access shared drives, alter the Windows startup, and access Outlook.
This brings up the issue of virus variants and how they occur. In the case of a biological virus, mutations in the genetic code cause new virus strains to appear, and the pressures of natural selection allow some of these strains to evolve into entirely new species of viruses. Obviously, the biological method is not what occurs with a computer virus. With a computer virus, some intrepid programmer with malicious intent gets a copy of a virus (perhaps her own machine becomes infected) and then reverse-engineers it. Since many virus attacks are in the form of a script attached to an email, unlike with traditionally compiled programs, the source code of these attacks is readily readable and alterable. The programmer in question then simply takes the original virus code, introduces some change, and rereleases the variant. Frequently, the people who are caught for virus creation are actually the developers of the variants who lacked the skill of the original virus writer and therefore were easily caught.
The Mimail Virus
Mimail is another older virus that is still worth studying. The Mimail virus did not receive as much media attention as Sobig, but it had some intriguing characteristics. This virus collected email addresses not only from your address book but also from other documents on your machine. Thus, if you had a Word document on your hard drive and an email address was in that document, Mimail would find it. This strategy meant that Mimail would spread further than many other viruses. Mimail had its own built-in email engine, so it did not have to “piggyback” off your email client. It could spread regardless of what email software you used.
These two differences from most viruses make Mimail interesting to people who study computer viruses. There are a variety of techniques that allow you to programmatically open and process files on your computer; however, most virus attacks do not employ them. The scanning of the document for email addresses indicates a certain level of skill and creativity on the part of the virus writer. In this author’s opinion, Mimail was not the work of an amateur but rather a person with professional-level programming skill.
The Bagle Virus
Bagle is another historical virus. It is not an issue today but is noteworthy in the history of malware because it combined email attachments with a fake virus warning. The Bagle virus began to spread rapidly in the fourth quarter of 2003. The email it sent claimed to be from your system administrator. It would tell you that your email account had been infected by a virus and that you should open the attached file to get instructions. Once you opened the attached file, your system was infected. This virus was particularly interesting for several reasons. To begin with, it spread both through email and by copying itself to shared folders. Second, it could scan files on your PC, looking for email addresses. Finally, it would disable processes used by antivirus scanners. In biological terms, this virus took out your computer’s “immune system.” The disabling of virus scanners was a new twist that indicated at least moderate programming skills on the part of the virus creator.
A Nonvirus Virus
Another new type of virus has been gaining popularity in the past few years, and that is the “nonvirus virus” or, put simply, a hoax. Rather than actually writing a virus, a hacker sends an email to every address he has. The email claims to be from some well-known antivirus center and warns of a new virus that is circulating. The email instructs people to delete some file from their computer to get rid of the virus. The file, however, is not really a virus but part of a computer’s system. The jdbgmgr.exe virus hoax used this scheme. It encouraged the reader to delete a file that was actually needed by the system. Surprisingly, a number of people followed this advice and not only deleted the file but promptly emailed their friends and colleagues to warn them to delete the file from their machines.
FYI: The Morris Internet Worm
The Morris worm was one of the first computer worms ever to be distributed over the Internet—and it was certainly the first to gain any significant media attention.
Robert Tappan Morris, Jr., then a student at Cornell University, wrote this worm and launched it from an MIT system on November 2, 1988. Morris did not actually intend to cause damage with the worm. Instead, he wanted the worm to reveal bugs in the programs it exploited in order to spread. However, bugs in the code allowed an individual computer to be infected multiple times, and the worm became a menace. Each additional “infection” spawned a new process on the infected computer. At a certain point, the large number of processes running on an infected machine slowed down the computer to the point of being unusable. At least 6000 UNIX machines were infected with this worm.
Morris was convicted of violating the 1986 Computer Fraud and Abuse Act and was sentenced to a $10,000 fine, 3 years’ probation, and 400 hours of community service. But perhaps the greatest impact of this worm was that it led to the creation of the Computer Emergency Response Team (CERT). CERT (www.cert.org) is an organization hosted at Carnegie Mellon University that is a repository for security bulletins, information, and guidelines. CERT is a source that any security professional should be familiar with.
Flame
No modern discussion of viruses would be complete without a discussion of Flame. This virus, which first appeared in 2012, targeted Windows operating systems. The first item that makes this virus notable is that it was specifically designed by the U.S. government for espionage. It was discovered in May 2012 at several locations, including Iranian government sites. Flame is spyware that can monitor network traffic and take screenshots of the infected system.
The Earliest Viruses
It is instructive to consider the very first viruses every found. In 1971, Bob Thomas created what is widely believed to be the first computer virus, named Creeper. It spread through the ARPANET (the precursor to the Internet) and displayed a message “I’m the creeper, catch me if you can!” Another program, named Reaper, was created to delete Creeper.
Wabbit, which was found in 1974, made multiple copies of itself, thus adversely affecting the performance of the infected computer.
Apple Viruses 1, 2, and 3 are some of the first viruses “in the wild” or public domain. These viruses, which were found on the Apple II operating system in 1981, spread through Texas A&M via pirated computer games.
The Impact of Viruses
In early 2018, Taiwan Semiconductor Manufacturing Company, one of the largest chipmakers and a supplier for Apple, said it had been hit by a computer virus that had affected computer systems and fabrication tools. Estimates placed the damages over $170 million. The specific virus was not described in the news reports, but a single company being hit with a single virus causing so much havoc illustrates the dangers of computer viruses.
Rules for Avoiding Viruses
You should notice a common theme with all virus attacks (except the hoax): They want you to open some type of attachment. The most common way for a virus to spread is as an email attachment. Knowing this, you can follow a few simple rules to drastically reduce the odds of becoming infected with a virus:
Use a virus scanner. McAfee and Norton (explored in the exercises at the end of this chapter) are the two most widely accepted and used virus scanners. However, Kaspersky and AVG are also good, reputable choices. Each costs about $30 per year to keep your virus scanner updated. Do it. Each antivirus product has proponents and detractors, and I won’t delve into the opinions on which is better. For most users, any of the four major antivirus programs would be effective. I rotate which one I use periodically just so I can stay familiar with all of them.
If you are not sure about an attachment, do not open it.
You might even exchange a code word with friends and colleagues. Tell them that if they wish to send you an attachment, they should put the code word in the title of the message. Without seeing the code word, you will not open any attachment.
Do not believe “security alerts” that are sent to you. Microsoft does not send out alerts in this manner. Check the Microsoft website regularly, as well as one of the antivirus websites previously mentioned.
These rules will not make your system 100% virus proof, but they will go a long way toward protecting your system.
Trojan Horses
Recall from earlier chapters that Trojan horse is a term for a program that looks benign but actually has a malicious purpose. We have already seen viruses that are delivered via a Trojan horse. You might receive or download a program that appears to be a harmless business utility or game. More likely, the Trojan horse is just a script attached to a benign-looking email. When you run the program or open the attachment, it does something else other than or in addition to what you thought it would. It might do any of the following:
Download harmful software from a website.
Install a key logger or other spyware on your machine.
Delete files.
Open a backdoor for a hacker to use.
It is common to find combination virus/Trojan horse attacks. In those scenarios, the Trojan horse spreads like a virus. The MyDoom virus opened a port on your machine that a later virus, doomjuice, would exploit, thus making MyDoom a combination of a virus and a Trojan horse.
A Trojan horse can also be crafted especially for an individual. If a hacker wished to spy on a certain individual, such as the company accountant, he could craft a program specifically to attract that person’s attention. For example, if he knew the accountant was an avid golfer, he could write a program that computed handicap and listed best golf courses. He would post that program on a free web server. He would then email a number of people, including the accountant, telling them about the free software. The software, once installed, could check the name of the currently logged-on person. If the logged-on name matched the accountant’s name, the software could then go out, unknown to the user, and download a key logger or other monitoring application. If the software did not damage files or replicate itself, then it would probably go undetected for quite a long time. There have been a number of Trojan horses through the years. One of the earliest and most widely known was Back Orifice.
FYI: Virus or Worm?
As noted in Chapter 4, there is disagreement among the experts about the distinction between a virus and a worm. Some experts would call MyDoom (as well as Sasser, which will be discussed later) a worm because it spread without human intervention. However, I would define a virus as any file that can self-replicate and a worm as any program that can propagate without human interference. This is also the most common definition you will find among security experts.
Such a program could be within the skill set of virtually any moderately competent programmer. This is one reason that many organizations have rules against downloading any software onto company machines. I am unaware of any actual incident of a Trojan horse being custom tailored in this fashion. However, it is important to remember that those creating virus attacks tend to be innovative people.
It is also important to note that creating a Trojan horse does not require programming skill. There are free tools on the Internet, such as EliteWrapper, that allow someone to combine two programs—one hidden and one not. So one could easily take a virus and combine it with, for example, a poker game. The end user would see only the poker game, but when it was run, it would launch the virus.
Another scenario to consider is one that would be quite devastating. Without divulging programming details, the basic premise will be outlined here to illustrate the grave dangers of Trojan horses. Imagine a small application that displays a series of unflattering pictures of Osama Bin Laden. This application would probably be popular with many people in the United States, particularly people in the military, intelligence community, or defense-related industries. Now assume that this application simply sits dormant on the machine for a period of time. It need not replicate like a virus because the computer user will probably send it to many of his associates. On a certain date and time, the software connects to any drive it can, including network drives, and begins deleting all files. If such a Trojan horse were released “in the wild,” within 30 days it would probably be shipped to thousands, perhaps millions, of people. Those thousands or millions of computers would then begin deleting files and folders. Imagine the devastation.
This scenario is mentioned precisely to frighten you a little. Computer users, including professionals who should know better, routinely download all sorts of things from the Internet, such as amusing flash videos and cute games. Every time an employee downloads something of this nature, there is a chance of downloading a Trojan horse. One need not be a statistician to realize that if employees continue that practice long enough, they will eventually download a Trojan horse onto a company machine. If they do, hopefully the virus will not be as vicious as the theoretical one just outlined here.
Because Trojan horses are usually installed by users themselves, the security countermeasure for this attack is to prevent downloads and installations by end users. From a law enforcement perspective, the investigation of a crime involving a Trojan horse would involve a forensic scan of the computer hard drive, looking for the Trojan horse itself.
There are a number of tools, some free for download, that will help a person create a Trojan horse. One that I use in my penetration testing classes is eLiTeWrap. It is easy to use. Essentially, it can bind any two programs together. Using a tool such as this one, anyone can bind a virus or spyware to an innocuous program such as a shareware poker game. This would lead to a large number of people downloading what they believe is a free game and unknowingly installing malware on their own system.
The eLiTeWrap tool is a command line tool, but it is very easy to use. Just follow these steps:
Enter the file you want to run that is visible.
Enter the operation:
1—Pack only
2—Pack and execute, visible, asynchronously
3—Pack and execute, hidden, asynchronously
4—Pack and execute, visible, synchronously
5—Pack and execute, hidden, synchronously
6—Execute only, visible, asynchronously
7—Execute only, hidden, asynchronously
8—Execute only, visible, synchronously
9—Execute only, hidden, synchronously
Enter the command line.
Enter the second file (the item you are surreptitiously installing).
Enter the operation.
When done with files, press Enter.
In Figure 5.1 you can see a demonstration that is appropriate for a classroom laboratory. In this example, two innocuous programs are combined into one Trojan horse. The programs chosen are simple Windows utilities that won’t harm the computer. However, it illustrates how easy it would be to combine legitimate programs with malware, for delivery to a target computer.

This illustration is meant to show how easy it is to create a Trojan horse, not to encourage you to do so. It is important to understand just how easy this process is so you can understand the prevalence of malware. Any attachment or download should be treated with significant suspicion.
The Buffer-Overflow Attack
You have become knowledgeable about a number of ways to attack a target system: denial of service, virus, and Trojan horse. While these attacks are probably the most common, they are not the only methods. Another method of attacking a system is called a buffer-overflow (or buffer-overrun) attack. A buffer-overflow attack happens when someone tries to put more data in a buffer than it was designed to hold. Any program that communicates with the Internet or a private network must take in some data. This data is stored, at least temporarily, in a space in memory called a buffer. If the programmer who wrote the application was careful, when you try to place too much information into a buffer, that information is then either simply truncated or outright rejected. Given the number of applications that might be running on a target system and the number of buffers in each application, the chances of having at least one buffer that was not written properly are significant enough to cause any prudent person some concern.
Someone who is moderately skilled in programming can write a program that purposefully writes more into the buffer than it can hold. For example, if the buffer can hold 1024 bytes of data and you try to fill it with 2048 bytes, the computer simply loads the extra 1024 bytes into memory. If that extra data is actually a malicious program, then it has just been loaded into memory and is thus now running on the target system. Or, perhaps the perpetrator simply wants to flood the target machine’s memory, thus overwriting other items that are currently in memory and causing them to crash. Either way, the buffer overflow is a very serious attack.
Fortunately, buffer-overflow attacks are a bit harder to execute than DoS attacks or simple Microsoft Outlook script viruses. To create a buffer-overflow attack, you must have a good working knowledge of some programming language (C or C++ is often chosen) and understand the target operating system/application well enough to know whether it has a buffer overflow weakness and how that weakness might be exploited.
It must be noted that modern operating systems and web servers are not generally susceptible to common buffer overflow attacks. Windows 95 was quite susceptible, but it has been many years since a Windows operating system was susceptible. Certainly Windows 7, 8, or 10 cannot be compromised with this type of attack. However, the same cannot be necessarily said for all the custom applications developed to run on various systems. It is always possible that an Internet-enabled application, including but not limited to web applications, might be susceptible to this kind of attack.
Essentially, this vulnerability exists only if programmers fail to program correctly. If all programs truncate extra data, then a buffer overflow cannot be executed on that system. However, if the program does not check the boundaries of variables and arrays and allows excess data to be loaded, then that system is vulnerable to a buffer overflow.
The Sasser Virus/Buffer Overflow
Sasser is an older attack but one that demonstrates the use of a buffer-overflow attack. Sasser is a combination attack in that the virus (or worm) spreads by exploiting a buffer overrun.
The Sasser virus spreads by exploiting a known flaw in a Windows system program. Sasser copies itself to the Windows directory as avserve.exe and creates a Registry key to load itself at startup. Therefore, once your machine is infected, you will start the virus every time you start the machine. This virus scans random IP addresses, listening on successive TCP ports starting at 1068 for exploitable systems—that is, systems that have not been patched to fix this flaw. When one is found, the worm exploits the vulnerable system by overflowing a buffer in LSASS.EXE, which is a file that is part of the Windows operating system. That executable is a built-in system file and is part of Windows. Sasser also acts as an FTP server on TCP port 5554, and it creates a remote shell on TCP port 9996. Next, Sasser creates an FTP script named cmd.ftp on the remote host and executes it. This FTP script instructs the target victim to download and execute the worm from the infected host. The infected host accepts this FTP traffic on TCP port 5554. The computer also creates a file named win.log on the C: drive. This file contains the IP address of the localhost. Copies of the virus are created in the Windows System directory as #_up.exe. Examples are shown here:
c:WINDOWSsystem3212553_up.exe
c:WINDOWSsystem3217923_up.exe
c:WINDOWSsystem3229679_up.exe
A side effect of this virus is that it causes your machine to reboot. A machine that is repeatedly rebooting without any other known cause may well be infected with the Sasser virus.
This is another case in which the infection can easily be prevented by several means. First, if you update your systems on a regular basis, those systems should not be vulnerable to this flaw. Second, if you ensure that your network’s routers or firewall block traffic on the ports involved (9996 and 5554), you will prevent most of Sasser’s damage. Your firewall should only allow traffic on specified ports; all other ports should be shut down. In short, if you as the network administrator are aware of security issues and are taking prudent steps to protect the network, your network will be safe. Many networks have been affected by this virus, however, indicating that not enough administrators are properly trained in computer security.
Spyware
In Chapter 1, “Introduction to Computer Security,” spyware was mentioned as one of the threats to computer security. Using spyware, however, requires a great deal more technical knowledge on the part of the perpetrator than do some other forms of malware. The perpetrator must be able to develop spyware for the particular situation or customize existing spyware for his needs. He must then be able to get the spyware on the target machine.
Spyware can be as simple as a cookie used by a website to record a few brief facts about your visit to that website, or it could be of a more insidious type, such as a key logger. Recall from Chapter 1 that a key logger is a program that records every keystroke you make on your keyboard; this spyware then logs your keystrokes to the spy’s file. The most common use of a key logger is to capture usernames and passwords. However, this method can capture every username and password you enter and every document you type, as well as anything else you might type. This data can be stored in a small file hidden on your machine for later extraction or sent out in TCP packets to some predetermined address. In some cases, the software is even set to wait until after hours to upload this data to some server or to use your own email software to send the data to an anonymous email address. There are also some key loggers that take periodic screenshots from your machine, revealing anything that is open on your computer. Whatever the specific mode of operation, spyware is software that literally spies on your activities on a particular computer.
Legal Uses of Spyware
There are some perfectly legal uses for spyware. Some employers have embraced spyware as a means of monitoring employee use of company technology. Many companies have elected to monitor phone, email, or web traffic within the organization. Keep in mind that the computer, network, and phone systems are the property of the company or organization, not of the employee. These technologies are typically supposed to be used only for work purposes; therefore, company monitoring might not constitute an invasion of privacy. While courts have upheld this monitoring as a company’s right, it is critical to consult an attorney before initiating this level of employee monitoring as well as to consider the potential negative impact on employee morale.
Parents can also elect to use this type of software on their home computer to monitor the activities of their children on the Internet. The goal is usually a laudable application—protecting their children from online predators. Yet, as with employees in a company, the practice may illicit a strong negative reaction from the parties being spied upon (namely, their children). Parents have to weigh the risk to their children versus what might be viewed as a breach of trust.
How Is Spyware Delivered to a Target System?
Clearly, spyware programs can track all activity on a computer, and that information can be retrieved by another party via a number of different methods. The real question is this: How does spyware get onto a computer system in the first place? The most common method is through a Trojan horse. It is also possible that when you visit a certain website, spyware may download in the background while you are simply perusing the website. Of course, if an employer (or parent) is installing the spyware, it can then be installed openly in the same way that an organization would install any other application.
Obtaining Spyware Software
Given the many other utilities and tools that have been mentioned as being available from the Internet, you probably will not be surprised to learn that you can obtain many spyware products for free, or at very low cost, on the Internet. You can check the Counterexploitation website (www.cexx.org), shown in Figure 5.2, for a lengthy list of known spyware products circulating on the Internet and for information about methods you can use to remove them. The SpywareGuide website (www.spywareguide.com) lists spyware that you can get right off the Internet should you feel some compelling reason to spy on someone’s computer activities. Figure 5.3 shows the categories of malware that are available from this site. Several key logger applications are listed on this site, as shown in Figure 5.4. These applications include well-known key loggers such as Absolute Keylogger, Tiny Keylogger, and TypO. Most can be downloaded for free or for a nominal charge.



Some well-known Trojan horses are also listed at this site (as shown in Figure 5.5), such as the 2nd Thought application, which downloads to a person’s PC and then blasts it with advertisements. This particular piece of spyware is one that downloads to your PC when you visit certain websites. It is benign in that it causes no direct harm to your system or files; it also does not gather sensitive information from your PC. However, it is incredibly annoying as it inundates your machine with unwanted ads. This sort of software is often referred to as adware. Frequently, these ads cannot be stopped by normal protective pop-up blockers because the pop-up windows are not generated by a website that you visit but rather by rogue software running on your machine. Pop-up blockers only work to stop sites you visit from opening new windows. Websites use well-known scripting techniques to cause your browser to open a window, and pop-up blockers recognize these techniques and prevent the ad windows from opening. However, adware that launches a new browser instance bypasses the pop-up blocker’s function.

Other Forms of Malware
In this and preceding chapters, the most prominent forms of malware have been discussed. There are, however, many other forms of attack. It is beyond the scope of this book to explore all of them, but you should be aware of the existence of some of the other forms of malware. Simply being aware can go a long way toward enabling you to defend your system efficiently. This section will touch upon just a few other forms of malware. You should reference the websites discussed in the end-of-chapter exercises and projects often so that you can stay up-to-date with all current forms of attack and defenses.
Rootkits
A rootkit is a collection of tools that a hacker uses to mask her intrusion and obtain administrator-level access to a computer or computer network. The intruder installs a rootkit on a computer after first obtaining user-level access, either by exploiting a known vulnerability or cracking a password. The rootkit then collects user IDs and passwords to other machines on the network, thus giving the hacker root or privileged access.
A rootkit may consist of utilities that also do the following:
Monitor traffic and keystrokes
Create a backdoor into the system for the hacker’s use
Alter log files
Attack other machines on the network
Alter existing system tools to circumvent detection
The presence of a rootkit on a network was first documented in the early 1990s. At that time, the Sun and Linux operating systems were the primary targets for hackers looking to install rootkits. Today, rootkits are available for a number of operating systems and are increasingly difficult to detect on any network.
Malicious Web-Based Code
Malicious web-based code, also known as web-based mobile code, simply refers to code that is portable to all operating systems or platforms, such as HTTP, Java, and so on. The “malicious” part implies that it is a virus, worm, Trojan horse, or some other form of malware. Simply put, the malicious code does not care what the operating system may be or what browser is in use. It infects them all blindly.
Where does this code come from, and how it is spread? The first generation of the Internet was mostly indexed text files. However, as the Internet has grown into a graphical, multimedia user experience, programmers have created scripting languages and new application technologies to enable a more interactive experience. Programs written with scripting languages run the gamut from useful to poorly crafted to outright dangerous.
Technologies such as Java and ActiveX enable buggy or untrustworthy programs to move to and execute on user workstations. (Other technologies that can enable malicious code are executables, JavaScript, VBScript, and plug-ins.) The Web increases the mobility of code without differentiating between program quality, integrity, or reliability. Using available tools, it is quite simple to “drag and drop” code into documents that are subsequently placed on web servers and made available to employees throughout the organization or individuals across the Internet. If this code is maliciously programmed or just improperly tested, it can cause serious damage.
Not surprisingly, hackers have used these very useful tools to steal, alter, and erase data files as well as gain unauthorized access to corporate networks. A malicious code attack can penetrate corporate networks and systems from a variety of access points, including websites, HTML content in email messages, or corporate intranets.
Today, with billions of Internet users, new malicious code attacks can spread through corporations almost instantly. The majority of damage caused by malicious code happens in the first hours after a first-strike attack occurs—before there is time for countermeasures. The costs of network downtime or theft of IP make malicious code a top priority.
Logic Bombs
A logic bomb is a type of malware that executes its malicious purpose when a specific criterion is met. The most common factor is date/time. For example, a logic bomb might delete files on a certain date/time. For example, in June 2006, Roger Duronio, a system administrator for UBS, was charged with using a logic bomb to damage the company’s computer network. His plan was to drive the company stock down due to damage from the logic bomb, so he was charged with securities fraud. Duronio was later convicted and sentenced to 8 years and 1 month in prison and ordered to pay $3.1 million restitution to UBS. This case illustrates this problem is not new.
In 2017 Mittesh Das of Atlanta Georgia was found guilty of transmitting malicious code with the intent of causing damage to a U.S. Army computer. Mr. Das created a logic bomb that would delete files in U.S. Army Reserve payroll systems after his company lost the contract. The incident actually occurred in 2014. He was sentenced to 2 years in prison followed by 3 years of probation.
Nimesh Patel is alleged to have created a logic bomb to attack his former employer’s servers in 2016. He is alleged to have logged on to the network after his employment ended, and uploaded malware. The software was designed to delete financial data from the Oracle database.
Another example occurred at the mortgage company Fannie Mae. On October 29, 2008, a logic bomb was discovered in the company’s systems. While this is an older example, it is an important one in the history of logic bombs. This logic bomb had been planted by a former contractor, Rajendrainh Makwana, who had been terminated. The bomb was set to activate on January 31, 2009, and completely wipe all of the company’s servers. Makwana was indicted in a Maryland court on January 27, 2009, for unauthorized computer access. On December 17, 2010, he was convicted and sentenced to 41 months in prison, followed by 3 years of probation. Makwana planted the logic bomb between the time he was terminated and the time the network administrators cancelled his network access. This illustrates the importance of ensuring that the accounts of former employees are deactivated immediately when their employment is terminated—whether it is an involuntary termination, a retirement, or a voluntary quit.
Spam
Spam, which most people are familiar with, is unwanted and unsolicited email that is sent out to multiple parties. Often it is used for marketing purposes, but it can be used for much more malicious goals. For example, spam is a common vehicle for spreading viruses and worms. Spam is also used to send emails enticing recipients to visit phishing websites in order to steal their identities. At best, spam is an annoyance, and at worst, it is a vehicle for spyware, viruses, worms, and phishing attacks.
Advanced Persistent Threats
Advanced persistent threats (APTs) is a relatively new term for a continuous process of attacking. It can involve hacking, social engineering, malware, or combinations of attacks. The issue is that the attack must be relatively sophisticated, thus the term advanced, and it must be ongoing, thus the term persistent.
The security firm Mandiant tracked several APTs over a period of 7 years, all originating in China—specifically, Shanghai and the Pudong region. These APTs were simply named APT1, APT2, and so on.
The attacks were linked to the UNIT 61398 of China’s military. The Chinese government regards this unit’s activities as classified, but it appears that offensive cyber warfare is one of its tasks. Just one of the APTs from this group compromised 141 companies in 20 different industries. APT1 was able to maintain access to victim networks for an average of 365 days, and in one case for 1764 days. APT1 is responsible for stealing 6.5TB of information from a single organization over a 10-month time frame. We will discuss the Chinese attack in more detail in Chapter 12, “Cyber Terrorism and Information Warfare.”
Detecting and Eliminating Viruses and Spyware
Once you understand the nature of malware, and just how devastating it can be, the next logical topic is to detect and remove malware.
Antivirus Software
In this chapter and throughout this book, we have discussed the need for running virus-scanning software. This section provides some details on how virus scanners work and information on the major virus-scanning software packages. This information should help you better understand how a virus scanner might protect your system and help you make intelligent decisions regarding the purchase and deployment of an antivirus solution.
A virus scanner can work in one of two ways. The first is to look for a signature (or pattern) that matches a known virus. It is therefore important to keep your virus software updated so that you have the most recent list of signatures with which to work.
The other way in which a virus scanner might check a given PC is to look at the behavior of an executable. If a program behaves in a way consistent with virus activity, the virus scanner may flag it as a virus. Such activity could include the following:
Attempting to copy itself
Attempting to access the address book of the system’s email program
Attempting to change Registry settings in Windows
Figure 5.6 shows the Norton Security antivirus software in action. You can see that the virus definitions are up-to-date, virus scanning is enabled, auto-protection is enabled, and Internet worm protection is enabled as well. The other popular virus scanners have many of the same features.
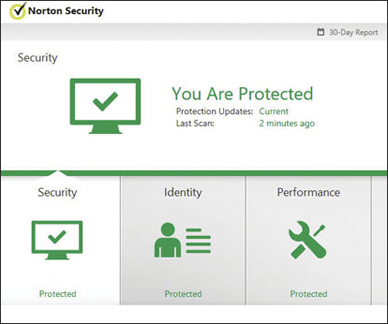
Most antivirus software today offers additional features, such as the ability to warn the user of known phishing websites, detect spyware as well as viruses, and even detect likely phishing attempts. Any modern antivirus product should be a comprehensive package, protecting against a variety of attacks, rather than just stopping viruses.
As mentioned earlier, there are many antivirus vendors. McAfee, Bitdefender, Kaspersky, AVG, and Malwarebytes are some of the most widely known.
McAfee offers solutions for the home user and large organizations. All of McAfee’s products have some common features, including email scanning and file scanning. They also scan instant messaging traffic. Figure 5.7 displays a screenshot of McAfee.

Avast (see Figure 5.8) is another widely used antivirus product. This product is offered for free for home, noncommercial uses. You can download the product from the vendor’s website: www.avast.com. You can also find professional versions, versions for UNIX or Linux, and versions specifically for servers. In addition, Avast is available in multiple languages, including English, Dutch, Finnish, French, German, Spanish, Italian, and Hungarian.

AVG antivirus (see Figure 5.9), which has become quite popular, is available in a free version as well as in a commercial version.

Malwarebytes is another widely used antivirus product. This product, available from https://www.malwarebytes.com, is available as both free version and paid premium versions. Figure 5.10 shows the Malwarebytes interface.

Windows Defender was first released as part of Windows Vista and Windows 7. It has grown and increased its features with each version of Windows. It is a free part of the Windows operating system. Figure 5.11 shows the main screen of Windows Defender for Windows 10.

Remediation Steps
Obviously, a crucial step in mitigating the risk from malware is running up-to-date antivirus software. I don’t endorse any particular antivirus program. McAfee, Norton, AVG, Kaspersky, and Malwarebytes are all reputable products. I do, however, recommend that if you are using both host-based antivirus and network antivirus, you should use products from two different vendors. This way, what one misses, the other is likely to catch.
In addition to running antimalware software, there are specific steps security professionals can take to mitigate the risk from malware. Note that the goal is to mitigate the threat of malware. It is impossible to completely eliminate such threats, but you can reduce both the frequency of attacks and the severity of damage.
It is important to educate end users. End users must be made aware of the prevalence of malware. The goal is for all users on your network to be suspicious of attachments and of downloads. Certainly, there are business needs that require the use of attached documents. But you can educate users on considering a few simple questions before opening any attachment:
Was this attachment expected? Attachments from people you do not know or from whom you did not expect any attachment must always be treated as potential malware.
Is the email specific, such as “These are the third-quarter sales reports we discussed in our meeting yesterday”? Such specifics tend to indicate real email with real documents attached. But generic-sounding emails such as “Here is your document” or emails that try to convince the user that he must urgently open the attachment should be suspected of being malware.
Do you have significant doubts about the authenticity of an email attachment? When in doubt, ask technical support.
Taking these simple measures would eliminate many malware outbreaks.
You can take a more complicated route to render your computers virtually immune to malware: First, set up a virtual machine on your computer. There are a variety of virtual machine applications, such as VMware and Oracle Box (which is free). Then install into that virtual machine (VM) some operating system other than what the host computer runs. So if your host is Windows 10, then the VM could run Linux. If your host is Mac, the VM could run Windows. Now if you surf the Internet inside the VM, it is almost impossible for you to get a virus on the host machine. To date, no virus has jumped the VM/host barrier, and no virus infects multiple operating systems. It should be noted that Java viruses and certain web page malware can infect browsers on different systems. However, as a general rule, a virus written for Windows won’t affect a Mac computer and vice versa.
Summary
Clearly, there are a number of ways to attack a target system: by using DoS attacks, viruses/worms, Trojan horses, buffer-overflow attacks, and spyware. Each type of attack comes in many distinct variations. There are so many ways for a hacker to attack a system that securing your system can be a rather complex task. However, it should be obvious by this point that securing your system is absolutely critical. In the upcoming exercises, you will try out antivirus programs by Norton and McAfee.
Another theme that is driven home throughout this chapter is that many, if not most, attacks are preventable. The exercises ahead will give you practice in figuring out how to prevent the Sasser and Sobig viruses. In most cases, prompt and regular patching of the system, use of antivirus tools, and blocking of unneeded ports would prevent such attacks. The fact that so many systems do get infected is an indication of the very real problem of network professionals not being skilled in computer security.
Test Your Skills
Multiple Choice Questions
1. John is a network security administrator for a midsized college. He is trying to explain to a new hire what a virus is. Which of the following is the best definition of virus?
A. A program that causes harm on your computer
B. A program used in a DoS attack
C. A program that slows down networks
D. A program that self-replicates
2. Isabelle is responsible for cybersecurity at her company. She is concerned that a virus would cause damage to the IT systems. What is the most common damage caused by virus attacks?
A. Slowing down networks by the virus traffic
B. Deleting files
C. Changing the Windows Registry
D. Corrupting the operating system
3. You are trying to form policies for your organization to mitigate the threat of viruses. You want to ensure that you address the most common way for a virus to spread. What is the most common way for a virus to spread?
A. By copying to shared folders
B. By email attachment
C. By FTP
D. By download from a website
4. Which of the following is the primary reason that Microsoft Outlook is so often a target for virus attacks?
A. Many hackers dislike Microsoft.
B. Outlook copies virus files faster.
C. It is easy to write programs that access Outlook’s inner mechanisms.
D. Outlook is more commonly used than other email systems.
5. Which of the following virus attacks used a multimodal approach?
A. Slammer virus
B. Mimail virus
C. Sobig virus
D. Bagle virus
6. What factor about the WannaCry virus is especially interesting to security practitioners?
A. It could have been prevented with good patch management.
B. It deleted critical system files.
C. It was difficult to protect against.
D. It was very sophisticated and likely an example of nation-state weaponized malware.
7. What is the name of the very first virus ever detected?
A. Creeper
B. Wabbit
C. Mimail
D. Unnamed
8. Which of the following reasons most likely enabled the Bagle virus to spread so rapidly?
A. The email containing it claimed to be from the system administrator.
B. It copied itself across the network.
C. It was a sophisticated virus.
D. It was particularly virulent.
9. What made the Bagle virus so dangerous?
A. It changed Windows Registry settings.
B. It disabled antivirus software.
C. It deleted key system files.
D. It corrupted the operating system.
10. Which of the following is a method that any person can use to protect against virus attacks?
A. Set up a firewall.
B. Use encrypted transmissions.
C. Use secure email software.
D. Never open unknown email attachments.
11. You are trying to develop methods to mitigate the threat of viruses in your company. Which of the following is the safest way to send and receive attachments?
A. Use a code word indicating that an attachment is legitimate.
B. Send only spreadsheet attachments.
C. Use encryption.
D. Use virus scanners before opening attachments.
12. Shelly is trying to teach new employees how to handle emailed security alerts. Which of the following is true regarding emailed security alerts?
A. You must follow them.
B. Most companies do not send alerts via email.
C. You can trust attachments on security alerts.
D. Most companies send alerts via email.
13. Which of the following is something a Trojan horse might do?
A. Open a backdoor for malicious software.
B. Change your memory configuration.
C. Change ports on your computer.
D. Alter your IP address.
14. Jared is explaining various attacks to students in an introduction to cybersecurity class. He wants to make certain they fully understand the different attacks. What does a buffer-overflow attack do?
A. It overflows a port with too many packets.
B. It puts more email in an email system than it can hold.
C. It overflows the system.
D. It puts more data in a buffer than it can hold.
15. What virus exploited buffer overflows?
A. Sobig virus
B. Mimail virus
C. Sasser virus
D. Bagle virus
16. What can you do with a firewall to help protect against virus attacks?
A. There is nothing you can do on a firewall to stop virus attacks.
B. Shut down all unneeded ports.
C. Close all incoming ports.
D. None of the above are correct.
17. Malek is explaining various malware types to new technical support personnel. He is explaining to them the various types of malware so that they can recognized them. What type of malware is a key logger?
A. Virus
B. Buffer overflow
C. Trojan horse
D. Spyware
18. Which of the following is a step that all computer users should take to protect against virus attacks?
A. Purchase and configure a firewall.
B. Shut down all incoming ports.
C. Use nonstandard email clients.
D. Install and use antivirus software.
19. What is the primary way a virus scanner works?
A. By comparing files against a list of known virus profiles
B. By blocking files that copy themselves
C. By blocking all unknown files
D. By looking at files for virus-like behavior
20. What other way can a virus scanner work?
A. By comparing files against a list of known virus profiles
B. By blocking files that copy themselves
C. By blocking all unknown files
D. By looking at files for virus-like behavior
Exercises
Exercise 5.1: Using Norton Antivirus
Go to the Norton AntiVirus website (www.symantec.com/downloads) and download the trial version of its software.
Install and run the software.
Carefully study the application, noting features that you like and dislike.
Exercise 5.2: Using McAfee Antivirus
Go to the McAfee antivirus website (http://www.mcafeee.com) and download the trial version of its software.
Install and run the software.
Carefully study the application, noting features you like and dislike.
Exercise 5.3: Preventing Sasser
Using resources on the Web or in journals, carefully research the Sasser virus. You may find that www.f-secure.com and the Symantec Security Center at https://www.symantec.com/security-center are helpful in this exercise.
Write a brief essay about how Sasser spread, what damage it caused, and what steps could be taken to prevent it.
Exercise 5.4: Preventing Sobig
Using resources on the Web or in journals, carefully research the Sobig virus. You may find that www.f-secure.com and the Symantec Security Center at https://www.symantec.com/security-center are helpful in this exercise.
Write a brief essay about how Sobig spread, what damage it caused, and what steps could be taken to prevent it.
Exercise 5.5: Learning About Current Virus Attacks
Using resources on the Web or in journals, find a virus that has been spreading in the past 90 days. You may find that www.f-secure.com and the Symantec Security Center at https://www.symantec.com/security-center are helpful in this exercise.
Write a brief essay about how the virus spread, what damage it caused, and what steps could be taken to prevent it.
Projects
Project 5.1: Antivirus Policies
This activity can also work as a group project.
Considering what you have learned in this chapter and in previous chapters, as well as using outside resources, write an antivirus policy for a small business or school. Your policy should include technical recommendations as well as procedural guidelines. You may choose to consult existing antivirus policy guidelines that you find on the Web to get some ideas. However, you should not simply copy these antivirus policies. Rather, you should come up with your own.
Project 5.2: The Worst Virus Attacks
Using resources on the Web, books, or journals, find a virus outbreak that you consider to have been the worst in history. Write a brief paper describing this attack and explain why you think it is the worst. Was it widely spread? How quickly did it spread? What damage did it do?
Project 5.3: Why Write a Virus?
A number of hypotheses have been formed regarding why people write viruses. These hypotheses range from the frankly conspiratorial to the academically psychological. Taking whatever position you feel is most likely, write a paper explaining why you think people take the time and effort to write a virus.
