Chapter 9
Access Control Management
Chapter Objectives
After reading this chapter and completing the exercises, you will be able to do the following:
Explain access control fundamentals.
Apply the concepts of default deny, need-to-know, and least privilege.
Understand secure authentication.
Protect systems from risks associated with Internet connectivity, remote access, and telework environments.
Manage and monitor user and administrator access.
Develop policies to support access control management.
What could be more essential to security than managing access to information and information systems? The primary objective of access controls is to protect information and information systems from unauthorized access (confidentiality), modification (integrity), or disruption (availability). The access control management domain incorporates the most fundamental precepts in information security: default deny, least privilege, and need-to-know.
We begin this chapter with a broad discussion of access control concepts and security models with a focus on authentication and authorization. We examine the factors of authentication with an emphasis on the importance of multifactor authentication. We look at the mandatory and discretionary authorization options for granting access rights and permission. We consider the risks associated with administrative and privileged accounts. Reaching past the boundaries of the internal network, we apply these concepts to the infrastructure, including border security, Internet access, remote access, and the teleworking environment. We will be mindful of the need to audit and monitor entry and exit points and to be prepared to respond to security violations. Throughout the chapter, we develop policies designed to support user access and productivity while simultaneously mitigating the risk of unauthorized access.
FYI: ISO/IEC 27002:2013 and NIST Guidance
Section 9 of ISO 27002:2013 is dedicated to access control, with the objective of managing authorized access and preventing unauthorized access to information systems. This domain extends to remote locations, home offices, and mobile access.
Corresponding NIST guidance is provided in the following documents:
SP 800-94: “Guide to Intrusion Detection and Prevention Systems”
SP 800-41, R1: “Guidelines on Firewalls and Firewall Policy”
SP 800-46, R1: “Guide to Enterprise Telework and Remote Access Security”
SP 800-77: “Guide to IPsec VPNs”
SP 800-114: “User’s Guide to Securing External Devices for Telework and Remote Access”
SP 800-113: “Guide to SSL VPNs”
SP 800-225: “Guidelines for Securing Wireless Local Area Networks (WLANs)”
SG 800-46, R2: “Guide to Enterprise Telework, Remote Access and Bring Your Own Device Security”
SG 800-114: “User’s Guide to Telework and Bring Your Own Device (BYOD) Security”
Access Control Fundamentals
Access controls are security features that govern how users and processes communicate and interact with systems and resources. The primary objective of access controls is to protect information and information systems from unauthorized access (confidentiality), modification (integrity), or disruption (availability). When we’re discussing access controls, the active entity (that is, the user or system) that requests access to a resource or data is referred to as the subject, and the passive entity being accessed or being acted upon is referred to as the object.
An identification scheme, an authentication method, and an authorization model are the three common attributes of all access controls. An identification scheme is used to identify unique records in a set, such as a username. Identification is the process of the subject supplying an identifier to the object. The authentication method is how identification is proven to be genuine. Authentication is the process of the subject supplying verifiable credentials to the object. The authorization model defines how access rights and permission are granted. Authorization is the process of assigning authenticated subjects the permission to carry out a specific operation.
The process for identifying, authenticating and authorizing users or groups of users to have access to applications, systems or networks is referred to as identity management. This is done by associating user permissions with established identities. These managed identities can also refer to systems and applications that need access to organizational systems. Identity management is focused on authentication, whereas access management is aimed at authorization. The purpose of having a good identity management solution is to enforce that only authenticated and authorized users are granted access to the specific applications, systems, or networks within your organization. Identity management is certainly an important part of cybersecurity and it also provides benefits for the overall productivity of the organization.
The security posture of an organization determines the default settings for access controls. Access controls can be technical (such as firewalls or passwords), administrative (such as separation of duties or dual controls), or physical (such as locks, bollards, or turnstiles).
What Is a Security Posture?
A security posture is an organization’s approach to access controls based on information about an object, such as a host (end system) or network. There is a concept called network access control (NAC) in which networking devices such as switches, firewalls, wireless access points, and others can enforce policy based on the security posture of a subject, in this case a device trying to join the network. NAC can provide the following:
Identity and trust
Visibility
Correlation
Instrumentation and management
Isolation and segmentation
Policy enforcement
The two fundamental postures are open and secure. Open, also referred to as default allow, means that access not explicitly forbidden is permitted. Secure, also referred to as default deny, means that access not explicitly permitted is forbidden. In practical application, default deny means that access is unavailable until a rule, access control list (ACL), or setting is modified to allow access.
The challenge for organizations that adopt a secure posture is that a number of devices on the market today, including tablets and smartphones as well as software applications, come with an out-of-the-box setting of default allow. Why? Interoperability, ease of use, and productivity are the three reasons cited. The explosive growth in the use of technology, coupled with increasing awareness of vulnerabilities, is creating a shift in the industry. Organizations have become more security conscious and are beginning to demand more secure products from their vendors. Microsoft is an example of a company that has responded to market requirements. Early Windows server operating systems were configured as default allow. Current Windows server operating systems are configured as default deny.
There is also the concept of threat-centric network access control (TC-NAC), which enables identity systems to collect threat and vulnerability data from many third-party threat and vulnerability scanners and software. This gives the identity management system a threat and risk view into the hosts it is controlling access rights for. TC-NAC enables you to have visibility into any vulnerable hosts on your network and to take dynamic network quarantine actions when required. The identity management system can create authorization policies based on vulnerability attributes, such as Common Vulnerability Scoring System (CVSS) scores received from your third-party threat and vulnerability assessment software. Threat severity levels and vulnerability assessment results can be used to dynamically control the access level of an endpoint or a user.
You can configure the external vulnerability and threat software to send high-fidelity Indications of Compromise (IoC), Threat Detected events, and CVSS scores to a central identity management system. This data can then be used in authorization policies to dynamically or manually change an endpoint’s network access privileges accordingly. The following are examples of threat software and vulnerability scanners:
Cisco Advanced Malware Protection (AMP) for Endpoints
Cisco Cognitive Threat Analytics (CTA)
Qualys
Rapid7 Nexpose
Tenable Security Center
Principle of Least Privilege and Separation of Duties
The principle of least privilege states that all users—whether they are individual contributors, managers, directors, or executives—should be granted only the level of privilege they need to do their jobs, and no more. For example, a sales account manager really has no business having administrator privileges over the network, or a call center staff member over critical corporate financial data.
The same concept of principle of least privilege can be applied to software. For example, programs or processes running on a system should have the capabilities they need to get their job done, but no root access to the system. If a vulnerability is exploited on a system that runs everything as root, the damage could extend to a complete compromise of the system. This is why you should always limit users, applications, and processes to access and run as the least privilege they need.
Somewhat related to the principle of least privilege is the concept of need-to-know, which means that users should get access only to data and systems that they need to do their job, and no other.
Separation of duties is an administrative control that dictates that a single individual should not perform all critical- or privileged-level duties. Additionally, important duties must be separated or divided among several individuals within the organization. The goal is to safeguard against a single individual performing sufficiently critical or privileged actions that could seriously damage a system or the organization as a whole. For instance, security auditors responsible for reviewing security logs should not necessarily have administrative rights over the systems. Another example is that a network administrator should not have the ability to alter logs on the system. This is to prevent such individuals from carrying out unauthorized actions and then deleting evidence of such action from the logs (in other words, covering their tracks).
Think about two software developers in the same organization ultimately working toward a common goal, but one is tasked with developing a portion of a critical application and the other is tasked with creating an application programming interface (API) for other critical applications. Each developer has the same seniority and working grade level; however, they do not know or have access to each other’s work or systems.
How Is Identity Verified?
Identification is the process of providing the identity of a subject or user. This is the first step in the authentication, authorization, and accounting process. Providing a username, a passport, an IP address, or even pronouncing your name is a form of identification. A secure identity should be unique in the sense that two users should be able to identify themselves unambiguously. This is particularly important in the context of account monitoring. Duplication of identity is possible if the authentication systems are not connected. For example, a user can use the same user ID for his corporate account and for his personal email account. A secure identity should also be nondescriptive, so that information about the user’s identity cannot be inferred. For example, using “Administrator” as the user ID is generally not recommended. An identity should also be issued in a secure way. This includes all processes and steps in requesting and approving an identity request. This property is usually referred to as secure issuance.
The list that follows highlights the key concepts of identification.
Identities should be unique. Two users with the same identity should not be allowed.
Identities should be nondescriptive. It should not be possible to infer the role or function of the user. For example, a user called “Admin” represents a descriptive identity, whereas a user called “o1337ms1” represents a nondescriptive identity.
Identities should be securely issued. A secure process for issuing an identity to a user needs to be established.
Identities can be location-based. A process for authenticating someone based on his or her location.
There are three categories of factors: knowledge (something the user knows), possession (something a user has), and inherence or characteristics (something the user is).
Authentication by Knowledge
Authentication by knowledge is where the user provides a secret that is only known by him or her. An example of authentication by knowledge would be a user providing a password, a personal identification number (PIN) code, or answering security questions.
The disadvantage of using this method is that once the information is lost or stolen (for example, if a user’s password is stolen), an attacker would be able to successfully authenticate. Nowadays, a day does not pass without hearing about a new breach in retailers, service providers, cloud services, and social media companies. If you look at the VERIS community database, you will see thousands of breach cases where users’ passwords were exposed (https://github.com/vz-risk/VCDB). Websites like “Have I been pwned” (https://haveibeenpwned.com) include a database of billions of usernames and passwords from past breaches and even allow you to search for your email address to see if your account or information has potentially been exposed.
Something you know is knowledge-based authentication. It could be a string of characters, referred to as a password or PIN, or it could be an answer to a question. Passwords are the most commonly used single-factor network authentication method. The authentication strength of a password is a function of its length, complexity, and unpredictability. If it is easy to guess or deconstruct, it is vulnerable to attack. Once known, it is no longer useful as a verification tool. The challenge is to get users to create, keep secret, and remember secure passwords. Weak passwords can be discovered within minutes or even seconds using any number of publicly available password crackers or social engineering techniques. Best practices dictate that passwords be a minimum of eight characters in length (preferably longer), include a combination of at least three upper and/or lowercase letters, punctuation, symbols, and numerals (referred to as complexity), be changed frequently, and be unique. Using the same password to log in to multiple applications and sites significantly increases the risk of exposure.
NIST Special Publication 800-63B, “Digital Identity Guidelines: Authentication and Lifecycle Management” provides guidelines for authentication and password strengths. NIST confirms that the length of a password has been found to be a primary factor in characterizing password strength. The longer the password the better. Passwords that are too short are very susceptible to brute force and dictionary attacks using words and commonly chosen passwords.
NIST suggests that “the minimum password length that should be required depends to a large extent on the threat model being addressed. Online attacks where the attacker attempts to log in by guessing the password can be mitigated by limiting the rate of login attempts permitted.”
Generally, when users are granted initial access to an information system, they are given a temporary password. Most systems have a technical control that will force the user to change his or her password at first login. A password should be changed immediately if there is any suspicion that it has been compromised.
As any help desk person will tell you, users forget their passwords with amazing regularity. If a user forgets his password, there needs to be a process for reissuing passwords that includes verification that the requester is indeed who he says he is. Often cognitive passwords are used as secondary verification. A cognitive password is a form of knowledge-based authentication that requires a user to answer a question based on something familiar to them. Common examples are mother’s maiden name and favorite color. The problem, of course, is that this information is very often publicly available. This weakness can be addressed using sophisticated questions that are derived from subscription databases such as credit reports. These questions are commonly referred to as out-of-wallet challenge questions. The term was coined to indicate that the answers are not easily available to someone other than the user, and that the user is not likely to carry such information in his or her wallet. Out-of-wallet question systems usually require that the user correctly answer more than one question and often include a “red herring” question that is designed to trick an imposter but which the legitimate user will recognize as nonsensical.
It may seem very convenient when a website or application offers to remember a user’s log on credentials or provide an automatic logon to a system, but this practice should be strictly prohibited. If a user allows websites or software applications to automate the authentication process, unattended devices can be used by unauthorized people to gain access to information resources.
FYI: Yahoo! Password Compromise
In October 2017, Yahoo confirmed that more than 3 billion accounts were compromised in its websites, including email, Tumblr, Fantasy, and Flickr. Prior to that, in July of 2012, the hacker group D33ds Company claimed responsibility for attacking Yahoo! Voice and exposing 453,492 plain text login credentials. The full data dump was made available on Pastebin and the passwords are well-known and weak. The top 10 most used passwords in order of popularity are listed here. Additional information is available at http://pastebin.com/2D6bHGTa.
123456 (38%)
password (18%)
welcome (10%)
ninja (8%)
abc123 (6%)
123456789 (5%)
12345678 (5%)
sunshine (5%)
princess (5%)
qwerty (4%)
Authentication by Ownership or Possession
With this type of authentication, the user is asked to provide proof that he owns something specific—for example, a system might require an employee to use a badge to access a facility. Another example of authentication by ownership is the use of a token or smart card. Similar to the previous method, if an attacker is able to steal the object used for authentication, he will be able to successfully access the system.
Examples include a one-time passcode, memory cards, smartcard, and out-of-band communication. The most common of the four is the one-time passcode sent to a device in the user’s possession. A one-time passcode (OTP) is a set of characteristics that can be used to prove a subject’s identity one time and one time only. Because the OTP is valid for only one access, if captured, additional access would be automatically denied. OTPs are generally delivered through a hardware or software token device. The token displays the code, which must then be typed in at the authentication screen. Alternatively, the OTP may be delivered via email, text message, or phone call to a predetermined address or phone number.
A memory card is an authentication mechanism that holds user information within a magnetic strip and relies on a reader to process the information. The user inserts the card into the reader and enters a personal identification number (PIN). Generally, the PIN is hashed and stored on the magnetic strip. The reader hashes the inputted PIN and compares it to the value on the card itself. A familiar example of this is a bank ATM card. A smartcard works in a similar fashion. Instead of a magnetic strip, it has a microprocessor and integrated circuits. The user inserts the card into a reader, which has electrical contacts that interface with the card and power the processor. The user enters a PIN that unlocks the information. The card can hold the user’s private key, generate an OTP, or respond to a challenge-response.
Out-of-band authentication requires communication over a channel that is distinct from the first factor. A cellular network is commonly used for out-of-band authentication. For example, a user enters her name and password at an application logon prompt (factor 1). The user then receives a call on her mobile phone; the user answers and provides a predetermined code (factor 2). For the authentication to be compromised, the attacker would have to have access to both the computer and the phone.
FYI: The Multifactor Authentication Gold Rush
In response to password insecurity, many organizations, such as Google, Facebook, Twitter, Valve, and Apple have deployed multifactor authentication options to their users. With multifactor authentication, accounts are protected by something you know (password) and something you have (one-time verification code provided to you). Google offers a variety of ways to get the code, including text message, phone call, Google authenticator app for Android and iOS devices, and a printable list of one-time codes.
Even gamers have been protecting their accounts using services and applications such as the Steam Guard Mobile Authenticator app. Millions of users have made their accounts stronger with multifactor verification. Have you?
Authentication by Characteristic
A system that uses authentication by characteristic authenticates the user based on some physical or behavioral characteristic, sometimes referred to as a biometric attribute. Here are the most used physical or physiological characteristics:
Fingerprints
Face recognition
Retina and iris
Palm and hand geometry
Blood and vascular information
Voice recognition
Here are examples of behavioral characteristics:
Signature dynamic
Keystroke dynamic/pattern
The drawback of a system based on this type of authentication is that it’s prone to accuracy errors. For example, a signature-dynamic-based system would authenticate a user by requesting that the user write his signature and then comparing the signature pattern to a record in the system. Given that the way a person signs his name differs slightly every time, the system should be designed so that the user can still authenticate even if the signature and pattern is not exactly the one in the system. However, it should also not be too loose and thus authenticate an unauthorized user attempting to mimic the pattern.
Two types of errors are associated with the accuracy of a biometric system:
A Type I error, also called false rejection, happens when the system rejects a valid user who should have been authenticated.
A Type II error, also called false acceptance, happens when the system accepts a user who should have been rejected (for example, an attacker trying to impersonate a valid user).
The crossover error rate (CER), also called the equal error rate (EER), is the point where the rate of false rejection errors (FRR) and the rate of false acceptance error (FAR) are equal. This is generally accepted as an indicator of the accuracy (and hence the quality) of a biometric system.
Multi-Factor Authentication
The process of authentication requires the subject to supply verifiable credentials. The credentials are often referred to as factors.
Single-factor authentication is when only one factor is presented. The most common method of single-factor authentication is the password. Multifactor authentication is when two or more factors are presented. Multilayer authentication is when two or more of the same type of factors are presented. Data classification, regulatory requirements, the impact of unauthorized access, and the likelihood of a threat being exercised should all be considered when you’re deciding on the level of authentication required. The more factors, the more robust the authentication process.
Identification and authentication are often performed together; however, it is important to understand that they are two different operations. Identification is about establishing who you are, whereas authentication is about proving you are the entity you claim to be.
What Is Authorization?
Once authenticated, a subject must be authorized. Authorization is the process of assigning authenticated subjects permission to carry out a specific operation. The authorization model defines how access rights and permission are granted. The three primary authorization models are object capability, security labels, and ACLs. Object capability is used programmatically and is based on a combination of an unforgeable reference and an operational message. Security labels are mandatory access controls embedded in object and subject properties. Examples of security labels (based on its classification) are “confidential”, “secret”, and “top secret.” Access control lists (ACLs) are used to determine access based on some combination of specific criteria, such as a user ID, group membership, classification, location, address, and date.
Additionally, when granting access, the authorization process would check the permissions associated with the subject/object pair so that the correct access right is provided. The object owner and management usually decide (or give input on) the permission and authorization policy that governs the authorization process.
The authorization policy and rule should take various attributes into consideration, such as the identity of the subject, the location from where the subject is requesting access, the subject’s role within the organization, and so on. Access control models, which are described in more detail later in this chapter, provide the framework for the authorization policy implementation.
An authorization policy should implement two concepts:
Implicit deny: If no rule is specified for the transaction of the subject/object, the authorization policy should deny the transaction.
Need-to-know: A subject should be granted access to an object only if the access is needed to carry out the job of the subject.
The three categories of ACLs are discretionary access controls, role-based access controls, and rule-based access controls.
Mandatory Access Control (MAC)
Mandatory access controls (MACs) are defined by policy and cannot be modified by the information owner. MACs are primarily used in secure military and government systems that require a high degree of confidentiality. In a MAC environment, objects are assigned a security label that indicates the classification and category of the resource. Subjects are assigned a security label that indicates a clearance level and assigned categories (based on need-to-know). The operating system compares the object’s security label with the subject’s security label. The subject’s clearance must be equal to or greater than the object’s classification. The category must match. For example, for a user to access a document classified as “Secret” and categorized as “Flight Plans,” the user must have either Secret or Top Secret clearance and have been tagged to the Flight Plan category.
Discretionary Access Control (DAC)
Discretionary access controls (DACs) are defined by the owner of the object. DACs are used in commercial operating systems. The object owner builds an ACL that allows or denies access to the object based on the user’s unique identity. The ACL can reference a user ID or a group (or groups) that the user is a member of. Permissions can be cumulative. For example, John belongs to the Accounting Group. The Accounting Group is assigned read permissions to the Income Tax folder and the files in the folder. John’s user account is assigned write permissions to the Income Tax folder and the files in the folder. Because DAC permissions are cumulative, John can access, read, and write to the files in the tax folder.
Role-Based Access Control (RBAC)
Role-based access controls (RBACs) (also called “nondiscretionary controls”) are access permissions based on a specific role or function. Administrators grant access rights and permissions to roles. Users are then associated with a single role. There is no provision for assigning rights to a user or group account.
Let’s take a look at the example illustrated in Figure 9-1.

FIGURE 9-1 RBAC Example
Omar is associated with the role of “Engineer” and inherits all the permissions assigned to the Engineer role. Omar cannot be assigned any additional permissions. Jeannette is associated with the role of “Sales” and inherits all the permissions assigned to the Sales role and cannot access engineering resources. Users can belong to multiple groups. RBAC enables you to control what users can do at both broad and granular levels.
Rule-Based Access Control
In a rule-based access controls environment, access is based on criteria that are independent of the user or group account. The rules are determined by the resource owner. Commonly used criteria include source or destination address, geographic location, and time of day. For example, the ACL on an application requires that it be accessed from a specific workstation. Rule-based access controls can be combined with DACs and RBACs.
In Practice
Access Control Authorization Policy
Synopsis: To state the access control authorization principles of the organization.
Policy Statement:
Default access privileges will be set to default deny (deny all).
Access to information and information systems must be limited to personnel and processes with a need-to-know to effectively fulfill their duties.
Access permissions must be based on the minimum required to perform the job or program function.
Information and information system owners are responsible for determining access rights and permissions.
The Office of Information Security is responsible for enforcing an authorization process.
Permissions must not be granted until the authorization process is complete.
Attribute-Based Access Control
Attribute-based access control (ABAC) is a logical access control model that controls access to objects by evaluating rules against the attributes of entities (both subject and object), operations, and the environment relevant to a request.
ABAC supports a complex Boolean rule set that can evaluate many different attributes.
The policies that can be implemented in an ABAC model are limited only to the degree imposed by the computational language and the richness of the available attributes.
An example of an access control framework that is consistent with ABAC is the Extensible Access Control Markup Language (XACML).
Accounting
Accounting is the process of auditing and monitoring what a user does once a specific resource is accessed. This process is sometimes overlooked; however, as a security professional, it is important to be aware of accounting and to advocate that it be implemented because of the great help it provides during detection and investigation of cybersecurity breaches.
When accounting is implemented, an audit trail log is created and stored that details when the user has accessed the resource, what the user did with that resource, and when the user stopped using the resource. Given the potential sensitive information included in the auditing logs, special care should be taken in protecting them from unauthorized access.
In Practice
Authentication Policy
Synopsis: To require the positive identification of the person or system seeking access to secured information, information systems, or devices.
Policy Statement:
Access to and use of information technology (IT) systems must require an individual to uniquely identify and authenticate him/herself to the resource.
Multiuser or shared accounts are allowed only when there is a documented and justified reason that has been approved by the Office of Information Security.
The Office of Information Security is responsible for managing an annual user account audit of network accounts, local application accounts, and web application accounts.
Data classification, regulatory requirements, the impact of unauthorized access, and the likelihood of a threat being exercised must all be considered when deciding upon the level of authentication required. The Office of Information Security will make this determination in conjunction with the information system owner.
Operating systems and applications will at a minimum be configured to require single-factor complex password authentication:
The inability to technically enforce this standard does not negate the requirement.
Password length, complexity, and expiration will be defined in the company password standard.
The password standard will be published, distributed, and included in the acceptable use agreement.
Web applications that transmit, store, or process “protected” or “confidential” information must at a minimum be configured to require single-factor complex password authentication:
The inability to technically enforce this standard does not negate the requirement.
Password length, complexity, and expiration will be defined in the company password standard.
If available, multifactor authentication must be implemented.
Passwords and PINs must be unique to the application.
Exceptions to this policy must be approved by the Office of Information Security.
All passwords must be encrypted during transmission and storage. Applications that do not conform to this requirement may not be used.
Any mechanism used for storing passwords must be approved by the Office of Information Security.
If any authentication mechanism has been compromised or is suspected of being compromised, users must immediately contact the Office of Information Security and follow the instructions given.
Infrastructure Access Controls
A network infrastructure is defined as an interconnected group of hosts and devices. The infrastructure can be confined to one location or, as often is the case, widely distributed, including branch locations and home offices. Access to the infrastructure enables the use of its resources. Infrastructure access controls include physical and logical network design, border devices, communication mechanisms, and host security settings. Because no system is foolproof, access must be continually monitored; if suspicious activity is detected, a response must be initiated.
Why Segment a Network?
Network segmentation is the process of logically grouping network assets, resources, and applications. Segmentation provides the flexibility to implement a variety of services, authentication requirements, and security controls. Working from the inside out, network segments include the following types:
Enclave network: A segment of an internal network that requires a higher degree of protection. Internal accessibility is further restricted through the use of firewalls, VPNs, VLANs, and network access control (NAC) devices.
Trusted network (wired or wireless): The internal network that is accessible to authorized users. External accessibility is restricted through the use of firewalls, VPNs, and IDS/IPS devices. Internal accessibility may be restricted through the use of VLANs and NAC devices.
Semi-trusted network, perimeter network, or DMZ: A network that is designed to be Internet accessible. Hosts such as web servers and email gateways are generally located in the DMZ. Internal and external accessibility is restricted through the use of firewalls, VPNs, and IDS/IPS devices.
Guest network (wired or wireless): A network that is specifically designed for use by visitors to connect to the Internet. There is no access from the Guest network to the internal trusted network.
Untrusted network: A network outside your security controls. The Internet is an untrusted network.
Figure 9-2 shows the topology of a network that has not been properly segmented.

FIGURE 9-2 Network Without Segmentation
The network topology in Figure 9-2 shows an enterprise that has a call center, a branch office, a warehouse, and a data center. The branch is a retail office where customers purchase their goods and the enterprise accepts credit cards. Users in the call center and the warehouse have access to the resources in the Branch office and vice versa. They also have access to resources in the data center. If any device is compromised, an attacker can pivot (or move laterally) in the network.
The topology in Figure 9-3 shows the same enterprise network topology, except that firewalls were installed to segment the network and to allow the traffic from the credit card readers to communicate only with specific servers in the data center.
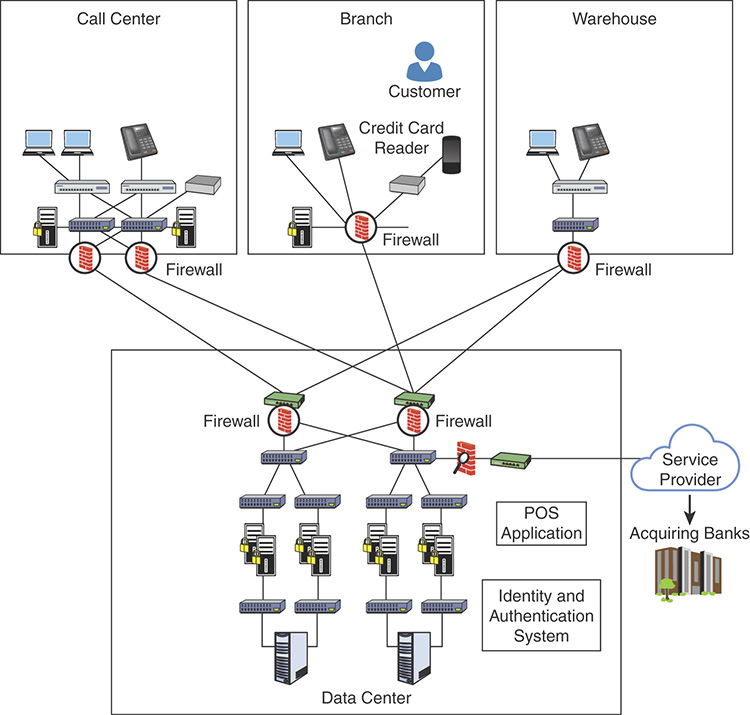
FIGURE 9-3 Network with Segmentation
Several other technologies can be used to segment a network:
Virtual LANs (VLANs)
Security Group Tagging (SGT)
VPN Routing and Forwarding (VRF)
vMicro-segmentation at the virtual machine level
Micro-segmentation for containers
In Practice
Network Segmentation Policy
Synopsis: Directive to logically group network assets, resources, and applications for the purpose of applying security controls.
Policy Statement:
The network infrastructure will be segregated into distinct segments according to security requirements and service function.
The Office of Information Security and the Office of Information Technology are jointly responsible for conducting annual network segment risk assessments. The results of the assessments will be provided to the Chief Operating Officer (COO).
Complete documentation of the network topology and architecture will be maintained by the Office of Information Technology, including an up-to-date network diagram showing all internal (wired and wireless) connections, external connections, and end points, including the Internet.
What Is Layered Border Security?
Layered security is the term applied to having different types of security measures designed to work in tandem with a single focus. The focus of layered border security is protecting the internal network from external threats. Layered border security access controls include firewall devices, intrusion detection systems (IDSs), and intrusion prevention systems (IPSs). To be effective, these devices must be properly configured and expertly managed. Due to the complexity of and resource requirements associated with maintaining and monitoring border security devices, many organizations have chosen to outsource the function to managed security service providers (referred to as MSSPs). Oversight of in-house administration or of the MSSP is a critical risk management safeguard.
So, What Are Firewalls?
Firewalls are devices or software that control the flow of traffic between networks. They are responsible for examining network entry and exit requests and enforcing organizational policy. Firewalls are a mandatory security control for any network connected to an untrusted network such as the Internet. Without a properly configured firewall, a network is completely exposed and could potentially be compromised within minutes, if not seconds. A firewall policy defines how the firewall should handle inbound and outbound network traffic for specific IP addresses and address ranges, protocols, ports, applications, and content types. The policy is codified in the rule set. The rule set is used by the firewall to evaluate ingress (incoming) and egress (outgoing) network traffic. In keeping with access control best practices, rule sets should be initially set to default deny (deny all) and then strict rules implemented that allow connectivity based on business need.
NIST SP-41, R1: Guidelines on Firewalls and Firewall Policy, provides an overview of firewall technologies and discusses their security capabilities and relative advantages and disadvantages in detail. It also provides examples of where firewalls can be placed within networks, and the implications of deploying firewalls in particular locations. The document also makes recommendations for establishing firewall policies and for selecting, configuring, testing, deploying, and managing firewall solutions.
FYI: IP Address, Ports, and Protocols Simplified
IP addresses, ports, and protocols form the basis of Internet communications:
An IP address is how a specific network host or device is identified.
A port is how an application or service is identified.
A protocol is a standardized way for hosts and network devices to exchange information.
Let’s compare IP addresses, ports, and protocols to mailing a letter.
If you want to mail a letter, you must follow the postal protocol, including how to address the letter to the recipient, the return address requirements, and where a letter can be mailed (such as the post office or mailbox).
The address must include the city (network), the street (network segment), and house number (host or device).
To be delivered to the right person (application or service), the address must include a unique name (port).
Network-based firewalls provide key features used for perimeter security. The primary task of a network firewall is to deny or permit traffic that attempts to enter or leave the network based on explicit preconfigured policies and rules. Firewalls are often deployed in several other parts of the network to provide network segmentation within the corporate infrastructure and also in data centers. The processes used to allow or block traffic may include the following:
Simple packet-filtering techniques
Application proxies
Network address translation
Stateful inspection firewalls
Next-generation context-aware firewalls
The purpose of packet filters is simply to control access to specific network segments by defining which traffic can pass through them. They usually inspect incoming traffic at the transport layer of the Open System Interconnection (OSI) model. For example, packet filters can analyze Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) packets and judge them against a set of predetermined rules called access control lists (ACLs). They inspect the following elements within a packet:
Source IP address
Destination IP address
Source port
Destination port
Protocol
Packet filters do not commonly inspect additional Layer 3 and Layer 4 fields such as sequence numbers, TCP control flags, and TCP acknowledgment (ACK) fields. Various packet-filtering firewalls can also inspect packet header information to find out whether the packet is from a new or an existing connection. Simple packet-filtering firewalls have several limitations and weaknesses:
Their ACLs or rules can be relatively large and difficult to manage.
They can be deceived into permitting unauthorized access of spoofed packets. Attackers can orchestrate a packet with an IP address that is authorized by the ACL.
Numerous applications can build multiple connections on arbitrarily negotiated ports. This makes it difficult to determine which ports are selected and used until after the connection is completed. Examples of this type of application are multimedia applications such as streaming audio and video applications. Packet filters do not understand the underlying upper-layer protocols used by this type of application, and providing support for this type of application is difficult because the ACLs need to be manually configured in packet-filtering firewalls.
Application proxies, or proxy servers, are devices that operate as intermediary agents on behalf of clients that are on a private or protected network. Clients on the protected network send connection requests to the application proxy to transfer data to the unprotected network or the Internet. Consequently, the application proxy sends the request on behalf of the internal client. The majority of proxy firewalls work at the application layer of the OSI model. Most proxy firewalls can cache information to accelerate their transactions. This is a great tool for networks that have numerous servers that experience high usage. Additionally, proxy firewalls can protect against some web-server-specific attacks; however, in most cases, they do not provide any protection against the web application itself.
Several Layer 3 devices can supply network address translation (NAT) services. The Layer 3 device translates the internal host’s private (or real) IP addresses to a publicly routable (or mapped) address.
NAT is often used by firewalls; however, other devices, such as routers and wireless access points, provide support for NAT. By using NAT, the firewall hides the internal private addresses from the unprotected network, and exposes only its own address or public range. This enables a network professional to use any IP address space as the internal network. A best practice is to use the address spaces that are reserved for private use (see RFC 1918, “Address Allocation for Private Internets”).
The white paper titled “A Security-Oriented Approach to IP Addressing” provides numerous tips on planning and preparing your network IP address scheme. This white paper is posted at the following link: www.cisco.com/web/about/security/intelligence/security-for-ip-addr.html.
Normally, firewalls perform a technique called port address translation (PAT). This feature is a subset of the NAT feature that allows many devices on the internal protected network to share one IP address by inspecting the Layer 4 information on the packet. This shared address is usually the firewall’s public address; however, it can be configured to any other available public IP address.
Intrusion Detection Systems and Intrusion Prevention Systems
It is possible for malicious activity to masquerade as legitimate traffic. Intrusion detection systems (IDSs) are passive devices designed to analyze network traffic to detect unauthorized access or malevolent activity. Most IDSs use multiple methods to detect threats, including signature-based detection, anomaly-based detection, and stateful protocol analysis. If suspicious activity is detected, IDSs generate an onscreen, email, and/or text alert. Intrusion prevention systems (IPSs) are active devices that sit inline with traffic flow and can respond to identified threats by disabling the connection, dropping the packet, or deleting the malicious content.
There are four types of IDS/IPS technologies:
Network-based IDS/IPS: Monitors network traffic for particular network segments or devices and analyzes the network and application protocol activity to identify suspicious activity.
Wireless IDS/IPS: Monitors wireless network traffic and analyzes it to identify suspicious activity involving the wireless networking protocols themselves.
Network behavior analysis IDS/IPS: Examines network traffic to identify threats that generate unusual traffic flows, such as distributed denial of service (DDoS) attacks, certain forms of malware, and policy violations (for example, a client system providing network services to other systems).
Host-based IDS/IPS: Monitors the characteristics of a single host and the events occurring within that host for suspicious activity.
IDS/IPS has four decision states. True positive occurs when the IDS/IPS correctly identifies an issue. True negative occurs when the IDS/IPS correctly identifies normal traffic. False positive occurs when the IDS/IPS incorrectly identifies normal activity as an issue. False negative occurs when the IDS/ISP incorrectly identifies an issue as normal activity.
Network-based IDS and IPS use several detection methodologies, such as the following:
Pattern-matching and stateful pattern-matching recognition
Protocol analysis
Heuristic-based analysis
Anomaly-based analysis
Correlation protection capabilities based on threat intelligence
NIST SP-94: “Guide to Intrusion Detection and Prevention Systems” describes the characteristics of IDS and IPS technologies and provides recommendations for designing, implementing, configuring, securing, monitoring, and maintaining them. The types of IDS/IPS technologies are differentiated primarily by the types of events they monitor and the ways in which they are deployed.
Content Filtering and Whitelisting/Blacklisting
Controls are required to protect the internal network from insider requests that could result in malware distribution, data exfiltration, participation in peer-to-peer (P2P) networks, and viewing of inappropriate or illegal content. The insider request could come from authenticated authorized users or could be a response to a malicious command or instruction. As discussed earlier, border device egress filters can and should be used to restrict outbound traffic by source and destination address, port, and protocol. The filters can be supplemented by self-generated, open source, or subscription-based IP whitelists and/or blacklists. Whitelists are addresses (IP and/or Internet domain names) of known “good” sites to which access should be allowed. Conversely, blacklists are addresses (IP and/or Internet domain names) of known “bad” sites to which access should be denied. It is common practice to block entire ranges of IP addresses specific to geographic regions. Content-filtering applications can be used to restrict access by content category (such as violence, gaming, shopping, or pornography), time factors, application type, bandwidth use, and media.
Border Device Administration and Management
Border device administration and management is a 24/7/365 responsibility. On a daily basis, performance needs to be monitored to enable potential resource issues to be identified and addressed before components become overwhelmed. Logs and alerts must be monitored and analyzed to identify threats—both successful and unsuccessful. Administrators need to be on the watch for security patches and apply them expediently. Border device policies, configurations, and rule sets must be backed up or replicated.
Policy rules and rule sets need to be updated as the organization’s requirements change or when new threats are identified. Changes should be closely monitored because unauthorized or incorrect modifications to the rule set can put the organization at risk. Modifications should be subject to the organization’s change management process. This includes a separation of approval and implementation duties. Configuration and rule set reviews as well as testing should be performed periodically to ensure continued compliance with the organization’s policies. Internal reviews can uncover configuration settings and rules that are outdated, redundant, or harmful. The review should include a detailed examination of all changes since the last regular review, particularly who made the changes and under what circumstances. External penetration testing can be used to verify that the devices are performing as intended.
FYI: Blue, Red, and Purple Teams
The defenders of the corporate network are typically referred to as blue teams. These blue teams include analysts in a security operation center (SOC), computer security incident response teams (CSIRTs), and other information security (InfoSec) teams. Offensive security teams such as ethical hackers or penetration testers are often referred to as the red team. The objective of red teams is to identify vulnerabilities as well as an organization’s attack detection and response capabilities. There is another concept called purple teaming. Purple teaming is when both the red and blue teams align forces to completely defend the organization and collaborate closely. In the past, most of these teams did not collaborate with each other.
In Practice
Border Device Security Access Control Policy
Synopsis: Requirements for the secure design, configuration, management, administration, and oversight of border devices.
Policy Statement:
Border security access control devices will be implemented and securely maintained to restrict access between networks that are trusted to varying degrees.
The default policy for handling inbound and outbound traffic should be to default deny (deny all).
If any situation renders the Internet-facing border security devices inoperable, Internet service must be disabled.
The Office of Information Security is responsible for approving border security access control architecture, configuration, and rule sets.
The Office of Information Technology is responsible for designing, maintaining, and managing border security access control devices.
At the discretion of the COO, this function or part of it may be outsourced to an MSSP.
Oversight of internal or MSSP border security device administrators is assigned to the Office of Information Security.
The types of network traffic that must always be denied without exception will be documented in the border device security standards.
Rule sets must be as specific and simple as possible. Rule set documentation will include the business justification for allowed traffic.
All configuration and rule set changes are subject to the organizational change management process.
All rule set modifications must be approved by the Office of Information Security.
All border security access control devices must be physically located in a controlled environment, with access limited to authorized personnel.
To support recovery after failure or natural disaster, the border security device configuration, policy, and rules must be backed up or replicated on a scheduled basis, as well as before and after every configuration change.
Border devices must be configured to log successful and failed activity as well as configuration changes.
Border device logs must be reviewed daily by the Office of Information Technology or MSSP, and an activity report must be submitted to the Office of Information Security.
Configuration and rule set reviews must be conducted annually:
The review is to be conducted by an external, independent entity.
Selection of the vendor is the responsibility of the Audit Committee.
Testing results are to be submitted to the COO.
External penetration testing must, at a minimum, be performed semi-annually:
The testing is to be conducted by an external, independent entity.
Selection of the vendor is the responsibility of the Audit Committee.
Testing results are to be submitted to the COO.
Remote Access Security
The need to access internal corporate network resources from external locations has become increasingly common. In fact, for companies with a remote or mobile workforce, remote access has become the norm. The nature of remote access technologies—permitting access to protected resources from external networks and often external hosts as well—is fraught with risk. Companies should start with the assumption that external facilities, networks, and devices contain hostile threats that will, if given the opportunity, attempt to gain access to the organization’s data and resources. Controls, including authentication, must be carefully evaluated and chosen based on the network segment’s information systems and the classification of information that will be accessible. Consideration must be given to ensuring that the remote access communication and stored user data cannot be accessed or read by unauthorized parties (confidentiality), detecting intentional or unintentional modifications to data in transit (integrity), and ensuring that users can access the resources as required (availability). Remote access security controls that must be considered include the physical security of the client devices, the use of cryptography in transit, the method of authentication and authorization, and the risks associated with local storage.
NIST SP 800-46, R2 “Guide to Enterprise Telework, Remote Access and Bring Your Own Device Security,” provides information on security considerations for several types of remote access solutions, and it makes recommendations for securing a variety of telework and remote access technologies. The publication also provides recommendations for creating telework-related policies and for selecting, implementing, and maintaining the necessary security controls for remote access servers and clients.
Remote Access Technologies
The two most common remote access technologies are virtual private networks (VPNs) and remote access portals. VPNs are generally used to extend the resources of a network to a remote location. Portals are generally used to provide access to specific applications.
A virtual private network (VPN) provides a secure tunnel for transmitting data through an unsecured network such as the Internet. This is achieved using tunneling and encryption in combination to provide high security remote access without the high cost of dedicated private lines. IPsec (short for IP security) is a set of protocols developed by the Internet Engineering Task Force (IETF) to support secure exchange of packets at the IP layer. IPsec is most commonly associated with VPNs as the protocol providing tunneling and encryption for VPN connections between physical sites or between a site and a remote user. The tunnel can be thought of as a virtual pathway between systems within the larger pathway of the Internet. The popularity of VPN deployments is a result of worldwide low-cost accessibility to the Internet, in contrast to private circuits that are expensive, require long-term contracts, and must be implemented between specific locations. More information on IPsec VPNs is available from NIST SP 800-77, “Guide to IPsec VPNs,” and more information on SSL tunnel VPNs is available from NIST SP 800-113, “Guide to SSL VPNs.”
A remote access portal offers access to one or more applications through a single centralized interface. A portal server transfers data to the client device as rendered desktop screen images or web pages, but data is typically stored on the client device temporarily. Portals limit remote access to specific portal-based applications. Another type of portal solution is terminal server access, which gives each remote user access to a separate standardized virtual desktop. The terminal server simulates the look and feel of a desktop operating system and provides access to applications. Terminal server access requires the remote user either to install a special terminal server client application or to use a web-based interface, often with a browser plug-in or other additional software provided by the organization. What’s more, applications such as Teamview and Joinme are specifically designed to create remote desktop sessions.
Remote Access Authentication and Authorization
Whenever feasible, organizations should implement mutual authentication so that a remote access user can verify the legitimacy of a remote access server before providing authentication credentials to it. The presentation of a preselected picture is an example of server-side authentication. Best practices dictate that multifactor authentication be required for remote access authentication. For an attacker to gain unauthorized access, he would have to compromise two authentication factors—one of which would either be something the user has or something the user is. Significantly increasing the work factor is a powerful deterrent! Additionally, users should be required to reauthenticate periodically during long remote access sessions or after a period of inactivity.
In addition to authenticating the user, remote access devices such as workstations and tablets should be evaluated to ensure they meet the baseline standards required for internal systems. Network access control (NAC) systems can be used to check a remote access device based on defined criteria, such as operating system version, security patches, antivirus software version, and wireless and firewall configurations, before it is allowed to connect to the infrastructure. If the device does not meet the predefined criteria, the device is denied access.
In Practice
Remote Access Security
Synopsis: To assign responsibility and set the requirements for remote access connections to the internal network.
Policy Statement:
The Office of Information Security is responsible for approving remote access connections and security controls.
The Office of Information Technology is responsible for managing and monitoring remote access connection.
Remote access connections must use 128-bit or greater encryption to protect data in transit (such as VPN, SSL, or SSH).
Multifactor authentication must be used for remote access. Whenever technically feasible, one factor must be out-of-band.
Remote equipment must be company-owned and configured in accordance with company workstation security standards.
Business partners and vendors wanting to obtain approval for remote access to computing resources must have access approved by the COO. Their company sponsor is required to provide a valid business reason for the remote access to be authorized.
Employees, business partners, and vendors approved for remote access must be presented with and sign a Remote Access Agreement that acknowledges their responsibilities prior to being granted access.
Remote access devices must be configured to log successful and failed activity as well as configuration changes.
Remote access logs must be reviewed daily by the Office of Information Technology or designee, and an activity report must be submitted to the Office of Information Security.
Remote access user lists must be reviewed quarterly by the Office of Human Resources.
The result of the review must be reported to both the Office of Information Security and the Office of Information Technology.
External penetration testing must, at a minimum, be performed semi-annually:
The testing is to be conducted by an external independent entity.
Selection of the vendor is the responsibility of the Audit Committee.
Testing results are to be submitted to the COO.
Teleworking Access Controls
The Telework Enhancement Act of 2010, Public Law 111-292, defines teleworking as “a work flexibility arrangement under which an employee performs the duties and responsibilities of such employee’s position, and other authorized activities, from an approved worksite other than the location from which the employee would otherwise work.” In plain language, teleworking allows employees to work offsite, often from their home. The Telework Coalition (TelCoa) list of teleworking benefits includes “increased employee productivity and motivation, reduced vehicular pollution, traffic reduction, improved work-life balance, a reduced dependency on imported oil, providing new employment opportunities for the disabled, rural, and older worker, as well as spouses of those in the military and a means to efficiently and effectively establish a decentralized and distributed work force that is necessary as a critical component in business continuity and disaster recovery planning.”1
1. Our Vision and Mission, © 2011, The Telework Coalition
Remote locations must be thought of as logical and physical extensions of the internal network and secured appropriately. Controls to ensure the confidentiality, integrity, and availability (CIA) of the information assets and information systems, including monitoring, must be commensurate with the on-premise environment.
NIST SP 800-114, “User’s Guide to Telework and Bring Your Own Device (BYOD) Security,” provides practical, real-world recommendations for securing telework computers’ operating systems (OS) and applications, as well as the home networks that the computers use. It presents basic recommendations for securing consumer devices used for telework. The document also presents advice on protecting the information stored on telework computers and removable media. In addition, it provides tips on considering the security of a device owned by a third party before deciding whether it should be used for telework.
In Practice
Teleworking Policy
Synopsis: To assign responsibility and set the requirements for teleworking.
Policy Statement:
Teleworking schedules must be requested in writing by management and authorized by the Office of Human Resources.
The Office of Human Resources is responsible for notifying the Office of Information Security and Office of Information Technology when a user is granted or denied teleworking privileges.
Teleworking equipment, including connectivity devices, must be company-owned and configured in accordance with company security standards.
The Office of Information Technology is responsible for managing, maintaining, and monitoring the configuration of and the connection to the teleworking location.
Remote access will be granted in accordance with the remote access policy and standards.
The teleworker is responsible for the physical security of the telecommuting location.
Local storage of information classified as “protected” or “confidential” must be authorized by the Office of Information Security.
Monitoring the teleworker is the responsibility of his or her immediate supervisor.
User Access Controls
The objective of user access controls is to ensure that authorized users are able to access information and resources while unauthorized users are prevented from access to the same. User access control and management is an enterprise-wide security task. NIST recommends that organizations manage information system accounts, including the following:
Identifying account types (individual, group, system, application, guest, and temporary)
Establishing conditions for group membership
Identifying authorized users of the information system and specifying access privileges
Requiring appropriate approvals for requests to establish accounts
Establishing, activating, modifying, disabling, and removing accounts
Specifically authorizing and monitoring the use of guest/anonymous and temporary accounts
Notifying account managers when temporary accounts are no longer required and when information system users are terminated, transferred, or information system usage or need-to-know/need-to-share changes
Deactivate temporary accounts that are no longer required and accounts of terminated or transferred users
Granting access to the system based on
A valid access authorization
Intended system usage
Other attributes as required by the organization or associated business functions
Reviewing accounts periodically
Why Manage User Access?
User access must be managed to maintain confidentiality and data integrity. In keeping with the least privilege and need-to-know security precepts, users should be provided access to the information and systems needed to do their job and no more. Humans are naturally curious beings. Given unfettered access, we will peek at that which we know we should not. Moreover, user accounts are the first target of a hacker who has gained access to an organization’s network. Diligent care must be used when designing procedures for creating accounts and granting access to information.
As discussed in Chapter 6, “Human Resources Security,” user provisioning is the process of creating user accounts and group membership, providing company identification and authentication mechanisms, and assigning access rights and permissions. Regardless of the department tasked with the user provisioning process, the information owner is ultimately responsible for authorization and oversight of access. The information owner or designee should review application, folder, or file access controls on a periodic basis. Factors that influence how often reviews should be conducted include the classification of the information being accessed, regulatory requirements, and rate of turnover and/or reorganization of duties. The review should be documented. Issues or inaccuracies should be responded to expediently.
In Practice
User Access Control and Authorization Policy
Synopsis: To define user access control and authorization parameters and responsibilities.
Policy Statement:
Default user access permissions will be set to default deny (deny all) prior to the appropriation of specific permissions based on role and/or job function.
Access to company information and systems will be authorized only for workforce personnel with a need-to-know to perform their job function(s).
Access will be restricted to the minimal amount required to carry out the business requirement of the access.
An authorization process must be maintained. Permissions must not be granted until the authorization process is complete.
Information owners are responsible for annually reviewing and reauthorizing user access permissions to data classified as “protected” or “confidential”:
The Office of Information Security is responsible for managing the review and reauthorization process.
An annual report of completion will be provided to the Audit Committee.
Administrative Account Controls
Networks and information systems must be implemented, configured, managed, and monitored. Doing so requires accounts with elevated privileges. Common privileged accounts include network administrators, system administrators, database administrators, firewall administrators, and webmasters. This concentration of power can be dangerous. Mitigating controls include segregation of duties and dual controls. Segregation of duties requires that tasks be assigned to individuals in such a manner that no one individual can control a process from start to finish. Dual control requires that two individuals must both complete their half of a specific task. An example of segregation of duties is allowing a security engineer to modify a firewall configuration file but not upload the configuration into the production environment. An example of dual control is requiring two separate keys to unlock a door. Each key is assigned to an individual user. The theory of both controls is that in order to act maliciously, two or more individuals would need to work together. All administrative or privileged account activity should be logged and reviewed.
Administrative accounts should be used only when the activity being performed requires elevated rights and permissions. There is no need to use this type of account to perform routine activities such as checking email, writing reports, performing research on the Internet, and other activities for which a basic user account will suffice. This is important because viruses, worms, and other malicious code will run in the security context of the logged-in user. If a user is logged in as a system administrator and her computer is infected with malicious code, the criminal that controls the malware has administrative privilege as well. To address this very real risk, every person with a special privilege account should also have a basic user account with which to perform duties that do not require administrative access.
FYI: User Account Controls in Windows, MAC OS X, and Linux
Microsoft Windows User Account Control (UAC) can be configured so that applications and tasks always run in the security context of a non-administrator account, unless an administrator specifically authorizes administrator-level access to the system. Microsoft takes this to the next level since Windows 10. The UAC privilege elevation prompts are color-coded to be app-specific. This is done to allow you to quickly identify an application’s potential security risk. Detailed information about Windows UAC can be obtained at
Linux-based systems and MAC OS X have implemented a similar approach since the early 1980s. There are two ways to run administrative applications in Linux and MAC OS X. You can either switch to the super user (root) with the su command, or you can take advantage of sudo. For example, to be able to install an application in Debian or Ubuntu you can run the sudo apt-get install command followed by the application or package name that you would like to install. If you are not familiar with Linux, you can learn additional details about Linux users and groups at https://linode.com/docs/tools-reference/linux-users-and-groups/.
In Practice
Administrative and Privileged Account Policy
Synopsis: To ensure the proper assignment, use, management, and oversight of accounts with administrative or elevated privileges.
Policy Statement:
Request for assignment of administrator-level accounts or changes to privileged group membership must be submitted to the Office of Information Security and approved by the COO.
The Office of Information Security is responsible for determining the appropriate use of administrator segregation of duties and dual controls.
Administrative and privileged user accounts will be used only when performing duties requiring administrative or privileged access.
All administrative and privileged account holders will have a second user account for performing any function where administrative or privileged access is not required.
User accounts assigned to contractors, consultants, or service providers who require administrative or privileged access will be enabled according to documented schedule and/or formal request, and be disabled at all other times.
Administrative and privileged account activity will be logged daily and reviewed by the Office of Information Security.
Administrative and privileged account assignments will be reviewed quarterly by the Office of Information Security.
What Types of Access Should Be Monitored?
Monitoring access and use is a critical component of information security. What is most unfortunate is that many organizations deploy elaborate systems to gather data from many sources and then never look at the data. Mining log data results in a wealth of information that can be used to protect your organization. Log data offers clues about activities that have unexpected and possibly harmful consequences, including the following:
At-risk events, such as unauthorized access, malware, data leakage, and suspicious activity
Oversight events, such as reporting on administrative activity, user management, policy changes, remote desktop sessions, configuration changes, and unexpected access
Security-related operational events, such as reporting on patch installation, software installation, service management, system reboots, bandwidth utilization, and DNS/DHCP traffic
At a minimum, three categories of user access should be logged and analyzed: successful access, failed access, and privileged operations. Successful access is a record of user activity. Reporting should include date, time, and action (for example, authenticate, read, delete, or modify). Failed access is indicative of either unauthorized attempts or authorized user issues. In the first instance, it is important to know whether an intruder is “testing” the system or has launched an attack. In the second, from an operational standpoint, it is important to know if users are having problems logging in, accessing information, or doing their jobs. Oversight of administrative or privileged accounts is critical. Administrators hold the keys to the kingdom. In many organizations, they have unfettered access. Compromise or misuse of administrator accounts can have disastrous consequences.
Is Monitoring Legal?
As we discussed in Chapter 6, employees should have no expectation of privacy in respect to actions taken on company time or with company resources. The United States judiciary system has favored employers’ right to monitor to protect their interests. Among the reasons given in the Defense Counsel Journal are the following:
The work is done at the employer’s place of business.
The employer owns the equipment.
The employer has an interest in monitoring employee activity to ensure the quality of work.
The employer has the right to protect property from theft and fraud.
Court rulings suggest that reasonableness is a standard applying to surveillance and monitoring activities. Electronic monitoring is reasonable when there is a business purpose, policies exist to set the privacy expectations of employees, and employees are informed of organizational rules regarding network activities and understand the means used to monitor the workplace.
Acceptable use agreements should include a clause informing users that the company will and does monitor system activity. A commonly accepted practice is to present this statement to system users as a legal warning during the authentication process. Users must agree to company monitoring as a condition of logging on.
In Practice
Monitoring System Access and Use Policy
Synopsis: Monitoring of network activity is necessary to detect unauthorized, suspicious, or at-risk activity.
Policy Statement:
The Office of Information Technology, the Office of Information Security, and the Office of Human Resources are jointly responsible for determining the extent of logging and analysis required for information systems storing, processing, transmitting, or providing access to information classified as “confidential” or “protected.” However, at a minimum the following must be logged:
Successful and failed network authentication
Successful and failed authentication to any application that stores or processes information classified as “protected”
Network and application administrative or privileged account activity
Exceptions to this list must be authorized by the COO.
Access logs must be reviewed daily by the Office of Information Technology or designee, and an activity report must be submitted to the Office of Information Security.
FYI: Small Business Note
One of the most significant information security challenges that small businesses face is not having dedicated IT or information security personnel. Very often, someone in the organization with “IT skills” is tapped to install and support critical devices, such as firewalls, wireless access points, and networking components. The result is that these devices are often left in their default mode and are not properly configured. Of particular concern is when the administrative account password is not changed. Attackers can easily obtain default passwords and take over the device. Passwords can be found in product documentation, and compiled lists are available on the Internet from sites such as www.defaultpassword.com/ and www.routerpasswords.com/.
Summary
Access controls are security features that govern how users and processes communicate and interact with systems and resources. The objective of implementing access controls is to ensure that authorized users and processes are able to access information and resources while unauthorized users and processes are prevented from access to the same. Access control models refer to the active entity that requests access to an object or data as the subject and the passive entity being accessed or being acted upon as the object.
An organization’s approach to access controls is referred to as its security posture. There are two fundamental approaches—open and secure. Open, also referred to as default allow, means that access not explicitly forbidden is permitted. Secure, also referred to as default deny, means that access not explicitly permitted is forbidden. Access decisions should consider the security principles of need-to-know and least privilege. Need-to-know means having a demonstrated and authorized reason for being granted access to information. Least privilege means granting subjects the minimum level of access required to perform their job or function.
Gaining access is a three-step process. The first step is for the object to recognize the subject. Identification is the process of the subject supplying an identifier such as a username to the object. The next step is to prove that the subjects are who they say they are. Authentication is the process of the subject supplying verifiable credentials to the object. The last step is determining the actions a subject can take. Authorization is the process of assigning authenticated subjects the rights and permissions needed to carry out a specific operation.
Authentication credentials are called factors. There are three categories of factors: knowledge (something the user knows), possession (something a user has), and inherence (something the user is). Single-factor authentication is when only one factor is presented. Multifactor authentication is when two or more factors are presented. Multilayer authentication is when two or more of the same type of factor are presented. Out-of-band authentication requires communication over a channel that is distinct from the first factor. Data classification, regulatory requirement, the impact of unauthorized access, and the likelihood of a threat being exercised must all be considered when deciding on the level of authentication required.
Once authentication is complete, an authorization model defines how subjects access objects. Mandatory access controls (MACs) are defined by policy and cannot be modified by the information owner. Discretionary access controls (DACs) are defined by the owner of the object. Role-based access controls (RBACs) (also called nondiscretionary) are access permissions based on a specific role or function. In a rule-based access controls environment, access is based on criteria that are independent of the user or group account, such as time of day or location.
A network infrastructure is defined as an interconnected group of hosts and devices. The infrastructure can be confined to one location or, as often is the case, widely distributed, including branch locations and home offices. Network segmentation is the process of logically grouping network assets, resources, and applications to stratify authentication requirements and security controls. Segments include enclaves, trusted networks, guest networks, perimeter networks (also referred to as DMZs), and untrusted networks (including the Internet).
Layered security is the term applied to having different types of security measures designed to work in tandem with a single focus. The focus of layered border security is protecting the internal network from external threats. Firewalls are devices or software that control the flow of traffic between networks using ingress and egress filters. Egress filters can be supplemented by self-generated, open source, or subscription-based IP whitelists or blacklists. Whitelists are addresses (IP and/or Internet domain names) of known “good” sites. Conversely, blacklists are addresses (IP and/or Internet domain names) of known “bad” sites. Content-filtering applications can be used to restrict access by content category (such as violence, gaming, shopping, or pornography), time factors, application type, bandwidth use, and media. Intrusion detection systems (IDSs) are passive devices designed to analyze network traffic to detect unauthorized access or malevolent activity. Intrusion prevention systems (IPSs) are active devices that sit inline with traffic flow and can respond to identified threats by disabling the connection, dropping the packet, or deleting the malicious content.
The need to access internal corporate network resources from remote locations has become increasingly common. Users who work remotely (often from home) on a scheduled basis are referred to as teleworkers. VPNs and remote access portals can be used to provide secure remote access for authorized users. A virtual private network (VPN) provides a secure tunnel for transmitting data through an unsecured network such as the Internet. IPsec (short for IP security) is a set of protocols developed by the Internet Engineering Task Force (IETF) to support secure exchange of packets at the IP layer and is used by VPN devices.
A remote access portal offers access to one or more applications through a single centralized interface. Both mechanisms authenticate and authorize subjects. Best practices dictate that multifactor authentication be used for remote access connections. Network access control (NAC) systems can be used to check a remote access device based on defined criteria, such as operating system version, security patches, antivirus software and DAT files, and wireless and firewall configurations, before it is allowed to connect to the infrastructure.
Organizations are dynamic. New employees are hired, others change roles, some leave under friendly conditions, and others are involuntarily terminated. The objective of user access controls is to ensure that authorized users are able to access information and resources while unauthorized users are prevented from access to the same. Information owners are responsible for the authorization of access and ongoing oversight. Access control reviews should be conducted periodically, commensurate with the classification of the information being accessed, regulatory requirements, and the rate of turnover and/or reorganization of duties.
Access controls are configured and managed by users with administrative or elevated privileges. Although this is necessary, the concentration of power can be dangerous. Mitigating controls include segregation of duties and dual controls. Segregation of duties requires that tasks be assigned to individuals in such a manner that no one individual can control a process from start to finish. Dual control requires that two individuals must both complete their half of a specific task.
Oversight of user and administrator access reflects best practices and, in many cases, a regulatory requirement. At a minimum, three categories of user access should be logged and analyzed: successful access, failed access, and privileged operations. It is incumbent on the organization to institute a log review process as well as incident-responsive procedures for at-risk or suspicious activity.
Access control management policies include Authentication Policy, Access Control Authorization Policy, Network Segmentation Policy, Border Device Security Policy, Remote Access Security Policy, Teleworking Policy, User Access Control and Authorization Policy, Administrative and Privileged Account Policy, and Monitoring System Access and Use Policy.
Test Your Skills
Multiple Choice Questions
1. Which of the following terms best describes access controls that are security features that govern how users and processes interact?
A. Objects
B. Resources
C. Processes
D. All of the above
2. Which of the following terms best describes the process of verifying the identity of a subject?
A. Accountability
B. Authorization
C. Access model
D. Authentication
3. Which of the following terms best describes the process of assigning authenticated subjects permission to carry out a specific operation?
A. Accountability
B. Authorization
C. Access model
D. Authentication
4. Which of the following terms best describes the active entity that requests access to an object or data?
A. Subject
B. Object
C. Resource
D. Factor
5. Which of the following security principles is best described as giving users the minimum access required to do their jobs?
A. Least access
B. Less protocol
C. Least privilege
D. Least process
6. Which of the following security principles is best described as prohibiting access to information not required for one’s work?
A. Access need security principle
B. Need-to-monitor security principle
C. Need-to-know security principle
D. Required information process security principle
7. Which type of access is allowed by the security principle of default deny?
A. Basic access is allowed.
B. Access that is not explicitly forbidden is permitted.
C. Access that is not explicitly permitted is forbidden.
D. None of the above.
8. Which of the following statements best describes security posture?
A. An organization’s approach to access controls based on information about an object, such as a host (end system) or network
B. An organization’s approach to access controls based on information about a network switch or router
C. An organization’s approach to access controls based on information about a router
D. An organization’s approach to access controls based on information about a firewall
9. Who is responsible for defining discretionary access controls (DACs)?
A. Data owners
B. Data administrators
C. Data custodians
D. Data users
10. Which of the following terms best describes the control that is used when the SOP for user provisioning requires the actions of two systems administrators—one who can create and delete accounts and the other who assigns access permissions?
A. Least privilege
B. Segregation of duties
C. Need-to-know
D. Default deny
11. Which of the following types of network, operating system, or application access controls is user-agnostic and relies on specific criteria, such as source IP address, time of day, and geographic location?
A. Mandatory
B. Role-based
C. Rule-based
D. Discretionary
12. Which of the following is not considered an authentication factor?
A. Knowledge
B. Inheritance
C. Possession
D. Biometric
13. Which of the following terms best describes authentication that requires two or more factors?
A. Dual control
B. Multifactor
C. Multilabel
D. Multilayer
14. Which of the following statements provides examples of good password management?
A. Passwords should be changed to increase the complexity and the length of the password.
B. Passwords should be changed when there is a suspicion that the password has been compromised.
C. Passwords should be changed to create a unique password after a user initially logs on to a system using a default or basic password.
D. All of the above.
15. Which of the following terms best describes a type of password that is a form of knowledge-based authentication that requires users to answer a question based on something familiar to them?
A. Categorical
B. Cognitive
C. Complex
D. Credential
16. Which of the following types of authentication requires two distinct and separate channels to authenticate?
A. In-band authentication
B. Mobile authentication
C. Out-of-band authentication
D. Out-of-wallet authentication
17. Which of the following terms best describes the internal network that is accessible to authorized users?
A. Trusted network
B. DMZ
C. The Internet
D. Semi-trusted network
18. Rules related to source and destination IP address, port, and protocol are used by a(n) _____ to determine access.
A. Firewall
B. IPS
C. IDS
D. VPN
19. Which of the following statements is true of an intrusion detection system (IDS)?
A. An IDS can disable a connection.
B. An IDS can respond to identified threats.
C. An IDS uses signature-based detection and/or anomaly-based detection techniques.
D. An IDS can delete malicious content.
20. Which of the following terms best describes a VPN?
A. A VPN provides an encrypted tunnel for transmitting data through an untrusted network.
B. A VPN is a cost-effective solution for securing remote access.
C. Both A and B.
D. Neither A nor B.
Exercises
Exercise 9.1: Understanding Access Control Concepts
Define the following access control management terminology:
Term
Definition
1.1
Access control
1.2
Authentication
1.3
Authorization
1.4
Default deny
1.5
Default allow
1.6
Least privilege
1.7
Need-to-know
1.8
Mandatory access control (MAC)
1.9
Discretionary access control (DAC)
1.10
Network access control (NAC)
Provide an example of an authentication control that affects you.
Provide an example of an authorization control that affects you.
Exercise 9.2: Managing User Accounts and Passwords
How many authentication factors does the email program you use require?
What are the required password characteristics for the email program you use? Include length, complexity, expiration, and banned words or phrases.
In your opinion, are the requirements adequate?
Exercise 9.3: Understanding Multifactor and Mutual Authentication
Find an image of or take a picture of a possession or inherence authentication device.
Find and describe an example of mutual authentication.
Explain how one of the preceding works.
Exercise 9.4: Analyzing Firewall Rule Sets
Firewall rule sets use source IP addresses, destination addresses, ports, and protocols.
Describe the function of each.
What is the purpose of the following rule?
Allow Src=10.1.23.54 dest=85.75.32.200 Proto=tcp 21
What is the purpose of the following rule?
Deny Src=ANY dest=ANY Proto=tcp 23
Exercise 9.5: Granting Administrative Access
Do you have administrative rights on your laptop, workstation, or tablet?
If yes, do you have the option to also have a normal user account? If no, who does?
Explain what is meant by the phrase “security context of the currently logged-in user.”
Projects
Project 9.1: Creating an RFP for Penetration Testing
You have been asked to send out a red team penetration testing Request for Proposal (RFP) document.
Explain what is often referred to as a “red team.”
What is the difference between a red team and a blue team?
Find three companies to send the RFP to. Explain why you chose them.
The selected vendor will potentially have access to your network. What due diligence criteria should be included in the vendor selection process? Select one of the companies from the previous step and find out as much as you can about them (for example, reputation, history, credentials).
Project 9.2: Reviewing User Access Permissions
Reviewing user access permissions can be a time-consuming and resource-intensive process and is generally reserved for applications or systems that have information classified as “protected” or “confidential.”
Should the student portal at your school be subject to an annual user access permission audit? If yes, why? If no, why not?
Automating review processes contributes to efficiency and accuracy. Research options for automating the user access review process and make a recommendation.
Project 9.3: Developing Telecommuting Best Practices
Your organization has decided to allow users the option of working from home.
Make a list of six security issues that must be considered.
Note your recommendations for each issue and detail any associated security control.
Assume that your recommendations have been accepted. You have now been tasked with training teleworkers. Create a presentation that explains “work from home” security best practices.
Case Study
Assessing a Current Security Breach
It often feels like every week there is a major breach. In early 2018 Facebook suffered from a privacy breach. Research this incident and answer the following questions:
How did the Facebook breach happen? How did it impact its reputation?
Research another breach that is more current. How does it compare to the Facebook breach?
Why was the attack successful? What controls were missing that may have prevented or detected the attack?
How much did the breach cost each company?
References
Regulations Cited
“Supplement to Authentication in an Internet Banking Environment,” issued by the Federal Institutions Examination Council, 6/28/2011.
“The Telework Enhancement Act of 2010, Public Law 111-292,” official website of the Government Printing Office, accessed 11/2017, https://www.gpo.gov/fdsys/pkg/BILLS-111hr1722enr/pdf/BILLS-111hr1722enr.pdf.
Other References
Kampanakis, Panos, Omar Santos, and Aaron Woland, Cisco Next-Generation Security Solutions: All-in-One Cisco ASA Firepower Services, NGIPS, and AMP, Indianapolis: Cisco Press, 2016.
Santos, Omar, Joseph Muniz, and Stefano De Crescenzo, CCNA Cyber Ops SECFND 210-250 Official Cert Guide, First Edition, Indianapolis: Cisco Press, 2017.
“Statistics of 450,000 Leaked Yahoo Accounts,” Pastebin, accessed 04/2018, http://pastebin.com/2D6bHGTa.
Larson, Selena, “Every Single Yahoo Account Was Hacked—3 Billion in All,” CNN, October 4, 2017, accessed 04/2018, http://money.cnn.com/2017/10/03/technology/business/yahoo-breach-3-billion-accounts/index.html.
Saltzer, J. H., and M. D. Schroeder, “The Protection of Information in Computer Systems.” Proceedings of the IEEE, vol. 63, no. 9 (Sept. 1975).
“The Telecommuter Infographic, An Analysis of the World’s Remote Workforce,” MySammy LLC, accessed 04/2018, https://www.mysammy.com/infographics-telecommuter.
“What Is Telecommuting?” Emory University WorkLife Resource Center, accessed 04/2018, www.worklife.emory.edu/workplaceflexibility/telecommuting/whatis.html.
