Chapter 3. Fundamentals of Intrusion Analysis
This chapter covers the following topics:
![]() Common artifact elements and sources of security events
Common artifact elements and sources of security events
![]() Understanding regular expressions
Understanding regular expressions
![]() Protocols, protocol headers, and intrusion analysis
Protocols, protocol headers, and intrusion analysis
![]() Using packet captures for intrusion analysis
Using packet captures for intrusion analysis
This chapter covers the common artifact elements and sources of security events and how you can use regular expressions to analyze security event data. You will learn the details about different protocols, protocol headers, and how they relate to intrusion analysis. You will also learn how to use packet captures for intrusion analysis.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz helps you identify your strengths and deficiencies in this chapter’s topics. The seven-question quiz, derived from the major sections in the “Foundation Topics” portion of the chapter, helps you determine how to spend your limited study time. Table 3-1 outlines the major topics discussed in this chapter and the “Do I Know This Already?” quiz questions that correspond to those topics.
1. Source and destination IP addresses are usually shown in NetFlow records and security events. What other artifacts are part of NetFlow records? (Select all that apply.)
a. Destination ports
b. Usernames
c. Signature IDs
d. Source ports
2. Which of the following are artifacts that are usually shown in IDS and IPS events? (Select all that apply.)
a. Signature IDs
b. Passwords
c. PII
d. Source and destination IP addresses
3. Which of the following regular expressions will match the word cat, bat, or rat?
a. [bcr]at
b. ^at
c. brc(at)
d. brc[at]
4. Which of the following regular expressions will match any IP address on the 10.1.2.0/24 network?
a. %10.1.2.$
b. 10.1.2..*
c. ^10.1.2.0
d. 10.[1..2].0
5. Which of the following is true about protocol header analysis?
a. Protocol header analysis has several drawbacks over IDS systems because it has less detection capabilities for both known and unknown attacks. This is because protocol header analysis tools cannot match traffic using signatures of security vulnerability exploits.
b. Protocol header analysis has several benefits over more primitive security techniques because it has better detection of both known and unknown attacks. This is done by matching traffic on signatures of security vulnerability exploits.
c. Protocol header analysis has several benefits over more primitive security techniques because it has better detection of both known and unknown attacks. This is done by alerting and blocking traffic on anomalies within the protocol transactions, instead of just simply matching traffic on signatures of security vulnerability exploits.
d. Protocol header analysis is a primitive security technique that does not allow an IDS or IPS device to match traffic using signatures of security vulnerability exploits.
6. Which of the following is an example of a packet capture program?
a. Wireshark
b. Packetshark
c. PacketReal
d. NetFlow
7. Refer to the following output of tcpdump. Which of the following statements are true of this packet capture? (Select all that apply.)
23:52:36.664771 IP omar.cisco.com.33498 > www1.cisco.com.http: Flags [S], seq 2841244609, win 29200,
options [mss 1460,sackOK,TS val 1193036826 ecr 0,nop,wscale 7], length 0
23:52:36.694193 IP www1.cisco.com.http > omar.cisco.com.33498: Flags [S.], seq 1686130907,
ack 2841244610, win 32768, options [mss 1380], length 0
23:52:36.694255 IP omar.cisco.com.33498 > www1.cisco.com.http: Flags [.], ack 1, win 29200, length 0
23:52:36.694350 IP omar.cisco.com.33498 > www1.cisco.com.http: Flags [P.], seq 1:74, ack 1, win 29200,
length 73: HTTP: GET / HTTP/1.1
23:52:36.723736 IP www1.cisco.com.http > omar.cisco.com.33498: Flags [.], ack 74, win 32695, length 0
23:52:36.724590 IP www1.cisco.com.http > omar.cisco.com.33498: Flags [P.], seq 1:505, ack 74,
win 32768, length 504: HTTP: HTTP/1.1 301 Moved Permanently
23:52:36.724631 IP omar.cisco.com.33498 > www1.cisco.com.http: Flags [.], ack 505, win 30016, length 0
23:52:36.724871 IP omar.cisco.com.33498 > www1.cisco.com.http: Flags [F.], seq 74, ack 505, win 30016,
length 0
23:52:36.754313 IP www1.cisco.com.http > omar.cisco.com.33498: Flags [F.], seq 505, ack 75, win 15544,
length 0
23:52:36.754364 IP omar.cisco.com.33498 > www1.cisco.com.http: Flags [.], ack 506, win 30016, length 0
a. The source host is omar.cisco.com and the destination is www1.cisco.com.
b. These are UDP transactions.
c. These are TCP transactions.
d. This is SIP redirect via HTTP.
Foundation Topics
Common Artifact Elements and Sources of Security Events
There are numerous artifact elements and sources of security event information. Figure 3-1 lists the common artifact elements found in security events.
Source and destination IP addresses are usually shown in network security events. Figure 3-2 shows the Intrusion Events panel of the summary dashboard of the Cisco Firepower Management Center (FMC). In Figure 3-2, you can see the top attackers’ and top targets’ IP addresses.
Figure 3-3 shows a more detailed list of events in the Cisco FMC displaying the source and destination IP addresses of each system involved in each event.
Figure 3-4 shows the Cisco ASA logs in the Cisco Adaptive Security Device Manager (ASDM). You can see that all of the logs are mostly around the 5-tuple (source and destination IP addresses, source and destination ports, and protocols).
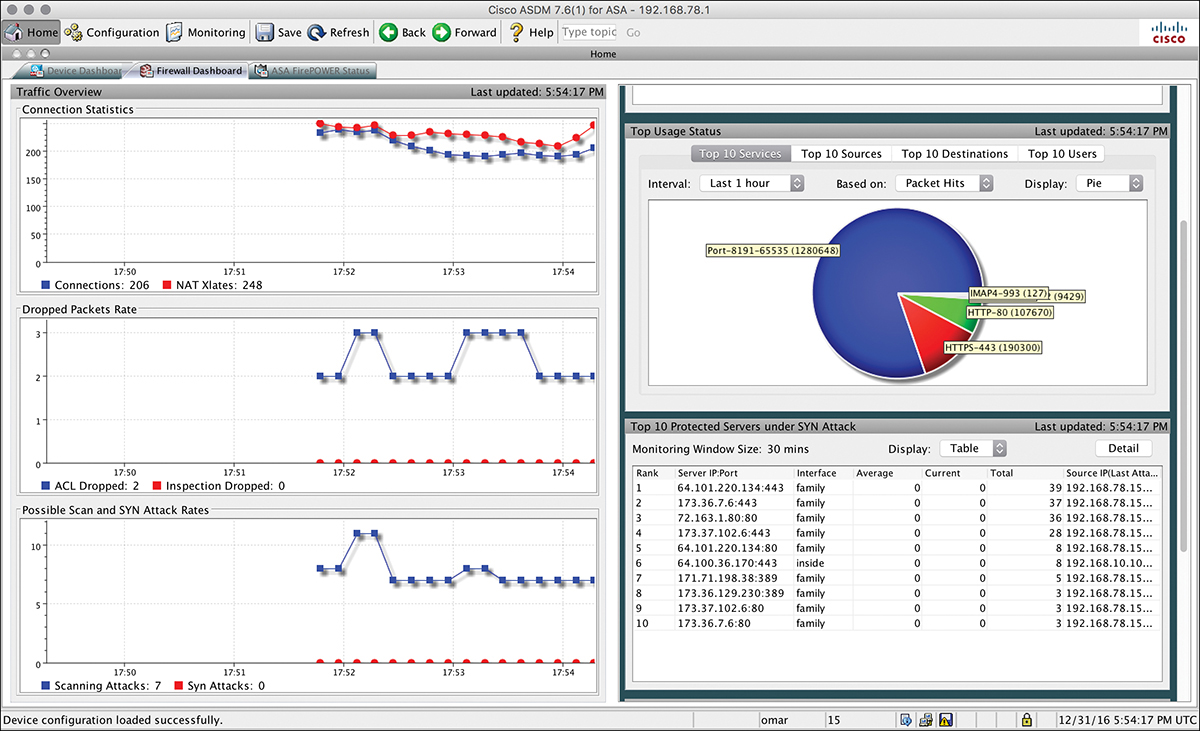
Services are also part of many security event logs. Figure 3-5 shows the Cisco ASDM firewall dashboard, where you can see statistics about the top services and top destinations under attack.
Security threat intelligence is extremely useful for correlating events and to gain an insight of what known threats are in your network. Figure 3-6 shows different security threat intelligence events in the Cisco FMC.
DNS intelligence and URL reputation are also used in many security solutions, such as the Firepower appliances, Firepower Threat Defense (FTD), the Cisco Web and Email security appliances, and many more. Figure 3-7 shows many security events in the Cisco FMC that list several communications to known-malicious command-and-control (CnC) servers based on DNS intelligence.
File hashes are also part of many security event logs. For example, the Cisco Advanced Malware Protection (AMP) for Networks (A4N) and Cisco AMP for Endpoints (A4E) examine, record, track, and send files to the cloud. The Cisco AMP for Networks creates an SHA-256 hash of the file and compares it to the local file cache. If the hash is not in the local cache, it queries the Cisco FMC. The Cisco FMC has its own cache of all the hashes it has seen before, and if it hasn’t previously seen this hash, the Cisco FMC queries the cloud. Unlike with AMP for Endpoints, when a file is new, it can be analyzed locally and doesn’t have to be sent to the cloud for an analysis. Also, the file is examined and stopped in transit, as it is traversing the appliance.
It’s very important to note that only the SHA-256 hash is sent unless you configure the policy to send files for further analysis in Threat Grid.
Figure 3-8 shows the Cisco AMP for Endpoints console. In Figure 3-8, you can see a file (iodnxvg.exe) that was determined to be malware. There you can see the SHA-256 hash (fingerprint) of the file.
Cisco AMP can also provide retrospective analysis. The Cisco AMP for Networks appliance keeps data from what occurred in the past. When a file’s disposition is changed, Cisco AMP provides a historical analysis of what happened, tracing the incident/infection. With the help of Cisco AMP for Endpoints, retrospection can reach out to that host and remediate the bad file, even though that file was permitted in the past. Figure 3-9 shows the retrospective analysis capabilities of the Cisco FMC.
Figure 3-9 shows the network file trajectory in the Cisco FMC. To view this screen, you can navigate to Analysis, Files, Network File Trajectory. You can also access a file’s trajectory from the Context Explorer, dashboard, or event views with file information.
You can also search SHA-256 hash values, host IP addresses, or the name of a file you want to track.
On the trajectory map, you can locate the first time a file event occurred involving an IP address. This highlights a path to that data point, as well as any intervening file events and IP addresses related to the first file event. The corresponding event in the Events table is also highlighted. The map scrolls to that data point if not currently visible.
You can also click any data point to highlight a path that includes all data points related to the selected data point, tracking a file’s progress through the network. You can click the arrow icon to view all events not displayed in the File Summary event view. If you hover your mouse over the event icon, you can view summary information for the event. If you click any event summary information link, the first page of the File Events default workflow appears in a new window, with all the extra events constrained based on the file type.
False Positives, False Negatives, True Positives, and True Negatives
The term false positive is a broad term that describes a situation in which a security device triggers an alarm but there is no malicious activity or an actual attack taking place. In other words, false positives are “false alarms,” and they are also called “benign triggers.” False positives are problematic because by triggering unjustified alerts, they diminish the value and urgency of real alerts. If you have too many false positives to investigate, it becomes an operational nightmare and you most definitely will overlook real security events.
There are also false negatives, which is the term used to describe a network intrusion device’s inability to detect true security events under certain circumstances—in other words, a malicious activity that is not detected by the security device.
A true positive is a successful identification of a security attack or a malicious event. A true negative is when the intrusion detection device identifies an activity as acceptable behavior and the activity is actually acceptable.
Traditional IDS and IPS devices need to be tuned to avoid false positives and false negatives. Next-generation IPSs do not need the same level of tuning compared to traditional IPS. Also, you can obtain much deeper reports and functionality, including advanced malware protection and retrospective analysis to see what happened after an attack took place.
Traditional IDS and IPS devices also suffer from many evasion attacks. The following are some of the most common evasion techniques against traditional IDS and IPS devices:
![]() Fragmentation: When the attacker evades the IPS box by sending fragmented packets.
Fragmentation: When the attacker evades the IPS box by sending fragmented packets.
![]() Using low-bandwidth attacks: When the attacker uses techniques that use low-bandwidth or a very small amount of packets in order to evade the system.
Using low-bandwidth attacks: When the attacker uses techniques that use low-bandwidth or a very small amount of packets in order to evade the system.
![]() Address spoofing/proxying: Using spoofed IP addresses or sources, as well as using intermediary systems such as proxies to evade inspection.
Address spoofing/proxying: Using spoofed IP addresses or sources, as well as using intermediary systems such as proxies to evade inspection.
![]() Pattern change evasion: Attackers may use polymorphic techniques to create unique attack patterns.
Pattern change evasion: Attackers may use polymorphic techniques to create unique attack patterns.
![]() Encryption: Attackers can use encryption to hide their communication and information.
Encryption: Attackers can use encryption to hide their communication and information.
Understanding Regular Expressions
If you are a security professional, network engineer, or software developer, you are most definitely familiar with regular expressions because they are considered “a Swiss army knife” for many uses. A regular expression (sometimes referred to as “regex”) is a text string for describing a search pattern. Regular expressions go beyond regular wildcards (such as *.mp3 to find all .mp3 files in a folder). Regular expressions can do a lot more. They are used in programming languages such as Perl, Python, PHP, Java, .NET, and several others. They are also commonly used to create intrusion detection signatures and search patterns in security tools.
Let’s take a look at a few quick basic examples. Example 3-1 shows a list of files on a Linux system.
Example 3-1 List of Several Text Files
omar@odin:~/cyberOps$ />ls -1/>
apple.txt
banana.txt
grape.txt
omar.txt
orange.txt
pear.txt
In Example 3-2, the grep command is used with the regular expression ^o to list all files that start with the letter o. In this case, the files that start with an o are omar.txt and orange.txt.
Example 3-2 Files Starting with an o
omar@odin:~/cyberOps$ />ls -1 | grep ^o/>
omar.txt
orange.txt
Let’s take a look at a more practical example. In Example 3-3, we have a file called packets.txt that has hundreds of transactions between hosts in the network (the complete output was omitted for brevity).
Example 3-3 The Contents of packets.txt
omar@odin:~/cyberOps$ cat packets.txt
15:46:15.551728 IP 192.168.78.8.ssh > 192.168.10.100.59657: Flags [P.], seq
3299992344:3299992544,
ack 4159081141, win 389, length 200
15:46:15.602341 IP 192.168.10.100.59657 > 192.168.78.8.ssh: Flags [.], ack 200, win
2065, length 0
15:46:15.700150 01:80:c2:00:00:01 (oui Unknown) > Broadcast, ethertype Unknown
(0x8874), length 60:
0x0000: e100 676a 11f5 e211 d51f e040 0000 0000 ..gj.......@....
0x0010: 0000 0000 0000 0000 0000 0000 0000 0000 ................
0x0020: 0000 0000 0000 0000 0000 0000 0000 ..............
15:46:15.942336 ARP, Request who-has 192.168.78.24 tell 192.168.78.7, length 46
15:46:16.540072 IP 192.168.78.8.51800 > resolver1.opendns.com.domain: 50883+ PTR? 100.10.168.192.in-addr.arpa. (45)
15:46:16.554415 IP resolver1.opendns.com.domain > 192.168.78.8.51800: 50883* 0/1/0 (104)
15:46:16.554631 IP 192.168.78.8.43662 > resolver1.opendns.com.domain: 18373+ PTR? 8.78.168.192.in-addr.arpa. (43)
15:46:16.569193 IP resolver1.opendns.com.domain > 192.168.78.8.43662: 18373* 0/1/0 (102)
15:46:16.569373 IP 192.168.78.8.35694 > resolver1.opendns.com.domain: 53427+ PTR? 24.78.168.192.in-addr.arpa. (44)
15:46:16.583627 IP resolver1.opendns.com.domain > 192.168.78.8.35694: 53427* 0/1/0 (103)
15:46:16.583735 IP 192.168.78.8.53838 > resolver1.opendns.com.domain: 39294+ PTR? 7.78.168.192.in-addr.arpa. (43)
15:46:16.598422 IP resolver1.opendns.com.domain > 192.168.78.8.53838: 39294* 0/1/0 (102)
15:46:16.598528 IP 192.168.78.8.35167 > resolver1.opendns.com.domain: 6469+ PTR? 22.78.168.192.in-addr.arpa. (44)
15:46:16.612963 IP resolver1.opendns.com.domain > 192.168.78.8.35167: 6469* 0/1/0 (103)
15:46:16.617261 IP 192.168.78.8.58139 > resolver1.opendns.com.domain: 45553+ PTR? 23.78.168.192.in-addr.arpa. (44)
15:46:16.631734 IP resolver1.opendns.com.domain > 192.168.78.8.58139: 45553* 0/1/0 (103)
15:46:16.942294 ARP, Request who-has 192.168.78.24 tell 192.168.78.7, length 46
15:46:16.962249 ARP, Request who-has 192.168.78.22 tell 192.168.78.7, length 46
15:46:17.065729 IP 192.168.78.122.3451 > 255.255.255.255.5246: UDP, length 181
15:46:17.066197 IP 192.168.78.122.3451 > 255.255.255.255.5246: UDP, length 181
15:46:17.336147 IP 192.168.10.100.59657 > 192.168.78.8.ssh: Flags [P.], seq 1:41, ack 200, win 2065, length 40
15:46:17.336356 IP 192.168.78.8.ssh > 192.168.10.100.59657: Flags [P.], seq 200:240, ack 41, win 389, length 40
15:46:17.387069 IP 192.168.10.100.59657 > 192.168.78.8.ssh: Flags [.], ack 240, win 2065, length 0
15:46:17.462246 ARP, Request who-has 192.168.78.23 tell 192.168.78.7, length 46
15:46:17.577756 IP 192.168.10.100.59657 > 192.168.78.8.ssh: Flags [.], ack 280, win 2065, length 0
15:46:17.581627 IP resolver1.opendns.com.domain > 192.168.78.8.33813: 54875* 0/1/0 (104)
***output omitted for brevity***
Let’s say that we want to display any transactions of the host with IP address 192.168.78.8 that took place at 15:46:15. We can use the grep command with a regular expressions like cat packets.txt | grep ^15:46:15.*78.8, as shown in Example 3-4. Of course, there are numerous other ways you can use regular expressions to display the same contents and manipulate that file.
Example 3-4 Searching Using grep and Regular Expressions for Contents in packets.txt
omar@odin:~/cyberOps$ />cat packets.txt | grep ^15:46:15.*78.8/>
15:46:15.551728 IP 192.168.78.8.ssh > 192.168.10.100.59657: Flags [P.], seq
3299992344:3299992544,
ack 4159081141, win 389, length 200
15:46:15.602341 IP 192.168.10.100.59657 > 192.168.78.8.ssh: Flags [.], ack 200, win
2065, length 0
You must be familiar with regular expressions for the exam. If you are not familiar with the basic concepts of regular expressions, the following are several great resources:
![]() MIT’s regex Cheat Sheet: http://web.mit.edu/hackl/www/lab/turkshop/slides/regex-cheatsheet.pdf
MIT’s regex Cheat Sheet: http://web.mit.edu/hackl/www/lab/turkshop/slides/regex-cheatsheet.pdf
![]() Regexp Security Cheat Sheet: https://github.com/attackercan/regexp-security-cheatsheet
Regexp Security Cheat Sheet: https://github.com/attackercan/regexp-security-cheatsheet
![]() Regular Expressions Info: http://www.regular-expressions.info
Regular Expressions Info: http://www.regular-expressions.info
![]() Fun regular expression exercises: https://regexcrossword.com
Fun regular expression exercises: https://regexcrossword.com
Protocols, Protocol Headers, and Intrusion Analysis
Traditional IDS and IPS, as well as next-generation IPS, can perform protocol analysis. The security device understands how various protocols, such as TCP, HTTP, TLS, Ethernet Frames, and many more, are supposed to work. They also ensure that the traffic that is inspected is compliant with the expected behavior for that protocol. In order to be able to inspect and enforce protocol compliance, the security device must look at the protocol headers. Traditional and next-generation firewalls also provide protocol inspection capabilities to make sure that such protocols are compliant. Protocol header analysis has several benefits over more primitive security techniques because it has better detection of both known and unknown attacks. This is done by alerting and blocking traffic on anomalies within the protocol transactions, instead of just simply matching traffic on signatures of security vulnerability exploits. Additionally, protocol analysis–based signatures are more difficult for threat actors to evade.
For example, if you search on the Internet for IPSec-based vulnerabilities, you will find dozens of results and examples. Traditional IDS and IPS systems leverage signatures based on the technical aspects of each vulnerability. On the other hand, by also having protocol analysis capabilities, the security device can alert on any misuse or anomaly of IPSec transactions.
Using Packet Captures for Intrusion Analysis
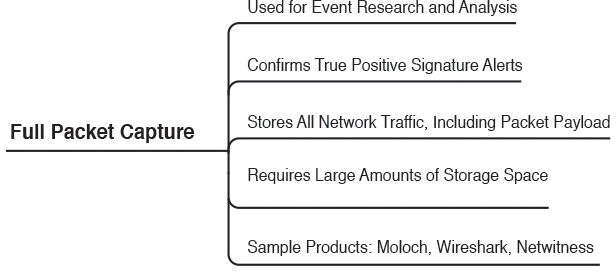
In the previous section, you learned about protocol analysis. One of the best ways to understand protocols and become familiar with the ins and outs of the packets traversing your network is to use sniffers, also called packet capture utilities. Packet captures can be used for security event research and analysis. They also confirm false positives and true positives. You can store all network traffic, including packet payload. On the other hand, one of the major disadvantages of full packet capture is that it requires large amounts of storage space and resources to analyze such data.
One of the most popular packet capture programs (or sniffers) is Wireshark. Figure 3-10 shows the Wireshark software displaying the details about a packet between source IP address 192.168.10.100 and the destination host with the IP address of 192.168.78.8.
In Figure 3-10, you can also see that this packet is an encrypted SSH packet that’s 40 bytes long. Under the Ethernet header section that’s highlighted both in the middle panel and in the lower hexadecimal dump of the packet, you can see Layer 2 details such as the MAC address of the network interface card of the source host (1c:1b:0d:6a:fb:a5) and the device in between that host and the final destination. In this case, that device is a Cisco ASA firewall with the MAC address 18:8b:9d:ad:79:c3.
Figure 3-11 shows the details about the TCP session highlighted in the middle panel and in the hexadecimal representation below it. You can see that the source port is 59657 and the destination port is the default SSH port (port 22). You can see details about the TCP header, which is 40 bytes long, as well as the TCP sequence number, acknowledge (ACK) number, TCP flags, Window size value, and much more.
In Figure 3-11, you can also see the SSH protocol information. As you can see there, the payload of the packet is encrypted.
Packet capture tools such as Wireshark come with tons of protocol decoding capabilities and also allow you to filter packets to better analyze the ones you capture. Another great feature is the ability to follow a TCP stream in the way the application layer sees it. For example, you may not want to see just the low-level details about one packet but rather all the packets in that stream or session. In order to do this, you can select a TCP packet in the packet list of the stream you want to analyze and then select the Follow TCP Stream menu item from the Wireshark Analyze menu, as illustrated in Figure 3-12. Alternatively, you can right-click the packet and click Follow, TCP Stream.
After you select to follow the TCP stream, the screen shown in Figure 3-13 is displayed. There, you can see the details about the transactions of that stream and all the associated packets. In Figure 3-13, you can see that the session is an HTTP session. You can see the HTTP GET being sent to the HTTP server (192.168.78.8). You can even see that the server is running the NGINX web server.
Wireshark even provides capabilities that allow you to create command-line ACL rules for many different firewall products, including Cisco IOS, Linux Netfilter (iptables), OpenBSD PF, and Windows Firewall (via netsh), as shown in Figure 3-14.
Other, more scalable packet capture utilities are available. For example, Moloch is an open source full packet capture utility that provides indexing and a database in which you can store your packet captures. You can download and obtain more information about Moloch at https://github.com/aol/moloch.
Examples of commercial packet capture software are Symantec Blue Coat Security Analytics and Packet Capture (https://www.bluecoat.com/products-and-solutions/security-analytics-and-incident-response) and RSA NetWitness (https://www.rsa.com/en-us/products/threat-detection-and-response/network-monitoring-and-forensics).
Mapping Security Event Types to Source Technologies
You learned while preparing for the CCNA Cyber Ops SECFND exam that many different security technologies and products can be used in the security operations center (SOC) and in many organizations. It is really important to understand what products and technologies are used for what types of security events and how to analyze these events. Let’s start with intrusion detection and prevention. Figure 3-15 shows the different types of analysis and features provided by intrusion detection and prevention systems as well as some sample products.
Figure 3-16 shows the different types of analysis and features provided by anomaly detection systems as well as some sample products.
Figure 3-17 shows the different types of analysis and features provided by malware analysis technologies as well as some sample products.
Figure 3-18 shows the different types of analysis and features provided by full packet capture solutions as well as some sample products.
Figure 3-19 shows the different types of analysis and features provided by protocol and packet metadata solutions as well as some sample products.
Depending on the technology and products used, you may need to analyze thousands upon thousands of logs and events. Some tools provide capabilities to see the overall health of your network, but also allow you to dive deeply into the details about each security event and potential intrusion. For instance, the Cisco Firepower Management Center (FMC) has drill-down views and a table view of events that share some common characteristics you can use to narrow a list of events. You can then concentrate your analysis on a group of related events, as shown in Figure 3-20.
In Figure 3-20, you can see two different message types related to SNMP and the number of times these events were encountered in the network. To access an intrusion event workflow in the FMC, you can navigate to Analysis, Intrusions, Events.
You can optionally limit the number of intrusion events that appear on the event views, as described in Intrusion Event Drill-Down Page Constraints or Intrusion Event Table View Constraints.
Figure 3-21 shows all the different events that matched the first message type or threat illustrated in Figure 3-20. In Figure 3-21 you can see detailed information about the source and destination IP addresses, geo-location information, source and destination ports, and many other types of information.
You can click each of the items shown in Figure 3-21 and either download the packets to your local system or view the packet details, as shown in Figure 3-22.
Exam Preparation Tasks
Review All Key Topics
Review the most important topics in the chapter, noted with the Key Topic icon in the outer margin of the page. Table 3-2 lists a reference of these key topics and the page numbers on which each is found.
Complete Tables and Lists from Memory
Print a copy of Appendix B, “Memory Tables,” (found on the book website), or at least the section for this chapter, and complete the tables and lists from memory. Appendix C, “Memory Tables Answer Key,” also on the website, includes completed tables and lists to check your work.
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
Q&A
The answers to these questions appear in Appendix A, “Answers to the ‘Do I Know This Already’ Quizzes and Q&A.” For more practice with exam format questions, use the exam engine on the website.
1. Refer to the following packet capture. Which of the following statements is true about this packet capture?
00:00:04.549138 IP omar.cisco.com.34548 > 93.184.216.34.telnet: Flags [S], seq
3152949738, win 29200,
options [mss 1460,sackOK,TS val 1193148797 ecr 0,nop,wscale 7], length 0
00:00:05.547084 IP omar.cisco.com.34548 > 93.184.216.34.telnet: Flags [S], seq
3152949738, win 29200,
options [mss 1460,sackOK,TS val 1193149047 ecr 0,nop,wscale 7], length 0
00:00:07.551078 IP omar.cisco.com.34548 > 93.184.216.34.telnet: Flags [S], seq
3152949738, win 29200,
options [mss 1460,sackOK,TS val 1193149548 ecr 0,nop,wscale 7], length 0
00:00:11.559081 IP omar.cisco.com.34548 > 93.184.216.34.telnet: Flags [S], seq
3152949738, win 29200,
options [mss 1460,sackOK,TS val 1193150550 ecr 0,nop,wscale 7], length 0
a. The host with the IP address 93.184.216.34 is the source.
b. The host omar.cisco.com is the destination.
c. This is a Telnet transaction that is timing out and the server is not responding.
d. The server omar.cisco.com is responding to 93.184.216.34 with four data packets.
2. Which of the following is a successful identification of a security attack or a malicious event?
a. True positive
b. True negative
c. False positive
d. False negative
3. Which of the following is when the intrusion detection device identifies an activity as acceptable behavior and the activity is actually acceptable?
a. True positive
b. True negative
c. False positive
d. False negative
4. Which of the following terms describes a situation in which a security device triggers an alarm but there is no malicious activity or an actual attack taking place?
a. True positive
b. True negative
c. False positive
d. False negative
5. Which of the following has been used to evade IDS and IPS devices?
a. SNMP
b. HTTP
c. TNP
d. Fragmentation
6. Which of the following is not an example of an element in an IDS alert or event?
a. Signature ID
b. Protocol ID or number
c. Flow record
d. Source and destination ports
7. Which of the following are not components of the 5-tuple of a flow in NetFlow? (Select all that apply.)
a. Source IP address
b. Flow record ID
c. Gateway
d. Source port
e. Destination port