Risk Assessment
Rachel Derr
Abstract
In Chapter 2 we discussed “What is risk?” The discussion here continues that chapter and assists in the process of determining the consequences of any incident. The potential for an adverse outcome is assessed as a function of threats, vulnerabilities, and consequences associated with an incident, event, or occurrence. In previous chapters, we have discussed risk, threats, and vulnerabilities; now we cover the consequences of an incident. This chapter walks readers through the process of putting all of the process together.
Keywords
consequence; asset; threat; vulnerabilities; human impact; economic impact; public confidence
Introduction
Chapter 2 discusses the question “What is risk?” This chapter continues that discussion and explores how to determine the consequences of an incident. The potential, or risk (R), for an adverse outcome is assessed as a function of threats (T), vulnerabilities (V), and consequences (C) associated with an incident, event, or occurrence.
The product or process that collects information and assigns values to risks for the purpose of informing priorities, developing or comparing course of action, and informing decision making is considered a risk assessment.
If previous chapters, we have discussed risk, threats, and vulnerabilities. Now we will cover the consequences of an incident.
Considering the Consequences
Although we are discussing it last, the potential consequences of an incident, such as a terrorist attack or a natural or man-made disaster, are the first factors to be considered in risk assessment.
In the context of the National Infrastructure Protection Plan (NIPP), consequence is measured as the range of loss or damage that can be expected.
Let’s take a look at the formula that has shown up in this text and evaluate how we consider risk. Aspects of this process are:
1. Where will the incident occur? (Asset)
2. Who or what will cause the incident? (Threat)
4. Are we down wind from a chemical plant?
5. What are the crime stats in this area? Are there a number of break-ins to businesses?
What is the risk assessment process? This part of a threat analysis will assist you in identifying real risks to your organization. It will assist your team with taking a look as actual probability of an occurrence to your organization and the actual result of impact to your organization.
Consequences are based on criteria in Homeland Security Presidential Directive 7 (see Chapters 1 and 6). Consequence criteria can be broken into four categories:
Human Impact
Human impact consists of the effect on human life and physical well-being (e.g., fatalities, injuries, illnesses). Psychological impact is indirect and is not included in this category.
Economic Impact
Economic impact consists of the direct and indirect effects on the economy, including the cost to rebuild the organization, the cost to respond to and recover from an attack, indirect costs resulting from disruption of product or service, and long-term costs from environmental damage.
A prime example of this type of impact is the BP oil spill also known as the Deepwater Horizon oil spill in the Gulf of Mexico in April 2010 (Fig. 9.1). The spill had a strong EI to BP and on the Gulf Coast’s economy sectors such as offshore drilling, fishing, and tourism. BP’s expenditures on the spill included the cost of the spill response, containment, relief well drilling, grants to the Gulf States, claims paid, and federal costs (including fines and penalties). As of March 2012, BP estimated that the company’s total spill-related expenses were approximately $37.2 billion.1

Impact on Public Confidence
This impact is the effect on public morale and confidence in national economic and political institutions. The public will question their belief in an organization after any incident. Psychological impact falls into this category. The public will also question the safety of the organization both physically and financially.
Impact on Government Capability
This impact is the effect on the government’s ability to maintain order, deliver minimum essential public services, ensure public health and safety, and carry out national security–related missions.
A perfect example of this is the shooting of a young African American, Michael Brown, in Ferguson, Missouri. As a result of the incident, there is very little confidence in the city’s government, especially the local police department. The words racism and fear are common when we read about the situation in Ferguson. This situation has both a social and Economic Impact (EI) on the city of Ferguson. When the verdict was released, looting and destruction of businesses occurred. Social unrest can have a lasting negative impact on a local economy in a way that’s much more persistent than even a natural disaster.
A full consequence assessment takes into consideration public health and safety, economic, psychological, and government impacts; however, estimating potential indirect impacts requires the use of assumptions and other complex variables. The local, city, and state government probably did not assume such destruction would occur in Ferguson.
An assessment of all categories of consequence may be beyond the capabilities available for a given risk analysis. At a minimum, assessments should focus on the two most fundamental impacts: the human and the most relevant direct EI.
Determining Consequences
When determining consequences, what does a full consequence assessment consider? It considers:
Can we accurately estimate the consequences? The consequence assessment worksheet (Table 9.1) can be used to assign a numerical value to the potential consequences of a threat or hazard incident.
Table 9.1
Human Impact and Economic Impact Worksheets
| Asset: City Hall |
| Scenario: (describe in detail) |
| Tornado hit City Hall |
| Human Impact (Relative to Total Asset Population) | |
| Number of people affected | 0 |
| <6% of personnel affected | 1 |
| 6%–12% | 2 |
| 12%–25% | 3 |
| 25%–50% | 4 |
| ≥50% personnel affected | 5 |
| HI value for this scenario | 1 |
| Economic Impact (Relative to Total Asset Value) | |
| <6% | 1 |
| 6%–12% | 2 |
| 12%–25% | 3 |
| 25%–50% | 4 |
| ≥50% value lost | 5 |
| EI value for this scenario | 3 |
| Total consequence score (C = HI +EI) | 4 |




The Human Impact (HI) value is based on the estimate of the percentage of personnel in the vicinity of the asset that will be killed or sustain severe illness or injury. Psychological impact is not included in HI, only physical impact. The EI value is based on an estimate of the percentage of the total value of the asset that is lost as a result of the incident. The worksheet does not allow a “zero” value for EI for any incident.
In an incident such as a poison gas attack, the majority of the consequences are deaths and illnesses, but there will also be EI because of facility decontamination, lost operating time, and other factors. In any incident in which injury or death occurs, some EI must be estimated.
The total consequence score is the sum of the HI and EI values. These estimates do not consider all the many variables involved, but they serve as a simple model to rank HI and EI on a scale of 1 to 10, where 10 indicates maximum severity. You will need to complete the HI and EI worksheet for each of the scenarios: (1) a terrorist attack (2) a natural disaster, and (3) a man-made disaster
A list of potential consequences of an incident is listed below. Note that items in this list are not independent. In fact, one can lead to another. For example, release of hazardous material can lead to injury or death.
![]() Impact on national security: facilitating an act of terrorism
Impact on national security: facilitating an act of terrorism
![]() Reduction or loss of production at one site or multiple sites simultaneously
Reduction or loss of production at one site or multiple sites simultaneously
![]() Injury or death of persons in the community
Injury or death of persons in the community
![]() Release, diversion, or theft of hazardous materials
Release, diversion, or theft of hazardous materials
![]() Violation of regulatory requirements
Violation of regulatory requirements
![]() Criminal or civil legal liabilities
Criminal or civil legal liabilities
Undesirable incidents of any sort detract from the value of an enterprise, but safety and security incidents can have longer term negative impacts than other types of incidents on all stakeholders, employees, shareholders, customers, and the communities where an organization operates.
Risk Assessment: The Applied Approach
Prioritizing vulnerabilities must include consideration of the consequences of an attack that exploits the specific vulnerability. What happens if someone gets through? What’s the worst thing that can happen? Based on threat knowledge, what’s the most likely thing that could happen? After the scenarios are defined, the consequences can be predicted.
T is threat (or hazard) from the jurisdictional threat (hazard) worksheet (value 1–10), V is vulnerability from the vulnerability assessment worksheet (score 1–12), and C is consequence value from the consequence assessment worksheet (value 1–10).
Various methodologies are available to facilitate risk assessment. Many owners and operators use a risk assessment methodology as a component of their business continuity and disaster mitigation planning.
A common approach based on a robust understanding of existing methodologies is needed to enable the setting of protection priorities across sectors.
The first element of this approach is to establish a common definition and process for analysis of the basic factors of risk Critical Infrastructure and Key Resources (CIKR) protection. In the context of homeland security, the NIPP framework assesses risk as a function of consequence, vulnerability, and threat:
![]() Threat: The likelihood that a particular asset, system, or network will sustain an attack or an incident. In the context of risk from terrorist attack, the estimate of this is based on the analysis of the intent and capability of an adversary; in the context of natural disaster or accident, the likelihood is based on the probability of occurrence. Numerical values for threats are determined using the jurisdictional threat worksheet.
Threat: The likelihood that a particular asset, system, or network will sustain an attack or an incident. In the context of risk from terrorist attack, the estimate of this is based on the analysis of the intent and capability of an adversary; in the context of natural disaster or accident, the likelihood is based on the probability of occurrence. Numerical values for threats are determined using the jurisdictional threat worksheet.
![]() Vulnerability: The likelihood that a characteristic of or flaw in an asset, system, or network’s design, location, security posture, process, or operation renders it susceptible to destruction, incapacitation, or exploitation by terrorist or other intentional acts, mechanical failures, and natural hazards. Numerical values for vulnerabilities are determined using the vulnerability assessment worksheet.
Vulnerability: The likelihood that a characteristic of or flaw in an asset, system, or network’s design, location, security posture, process, or operation renders it susceptible to destruction, incapacitation, or exploitation by terrorist or other intentional acts, mechanical failures, and natural hazards. Numerical values for vulnerabilities are determined using the vulnerability assessment worksheet.
![]() Consequence: The negative effects on public health and safety, the economy, public confidence in institutions, and the functioning of government, both direct and indirect, that can be expected if an asset, system, or network is damaged, destroyed, or disrupted by a terrorist attack, natural disaster, or other incident. Numerical values for consequences are determined using the consequence assessment worksheet.
Consequence: The negative effects on public health and safety, the economy, public confidence in institutions, and the functioning of government, both direct and indirect, that can be expected if an asset, system, or network is damaged, destroyed, or disrupted by a terrorist attack, natural disaster, or other incident. Numerical values for consequences are determined using the consequence assessment worksheet.
Risk assessments for CIKR protection consider all three components of risk and are conducted on an asset, system, network, or function basis, depending on the fundamental characteristics of the infrastructure being examined.
For some sectors, particularly those with specifically identifiable facilities that might be exploited, an asset-based approach is typically used; for others, particularly those with virtual or information based core processes, assessing system or network risk and resiliency is more appropriate.
Risk assessment combines the probability of an incident occurring with the severity (consequence) of an incident to “prioritize” vulnerabilities. The risk assessment diagram combines threat and vulnerability (T×V) into a probability that the event could occur and plots that probability against the severity (consequence, C) (Fig. 9.2).
Risk Definitions
| Risk Level | Value | Description |
| High Risk | R >601 | Unacceptable risk, highly likely to occur |
| Moderate Risk | 101 <R <600 | Serious Risk, likely to occur |
| Low Risk | <100 | Minimal risk, highly unlikely to occur |
Numerical values can be assigned to each of the factors. The total risk values are calculated by using a variety of formulas and a sample of this approach is show below:
![]() Threat: A scale from 1 (low) to 10 (high) is being used in this example. This is based on the Jurisdiction Threat Worksheet from the Threat and Risk Assessment and the Jurisdictional and Hazard Worksheet.
Threat: A scale from 1 (low) to 10 (high) is being used in this example. This is based on the Jurisdiction Threat Worksheet from the Threat and Risk Assessment and the Jurisdictional and Hazard Worksheet.
![]() Vulnerability: A scale from 1–12 was used and is based on the results from the Vulnerability Assessment Worksheet.
Vulnerability: A scale from 1–12 was used and is based on the results from the Vulnerability Assessment Worksheet.
![]() Consequence: A scale from 1–10 was used; the Consequence Assessment Worksheet assigns these values.
Consequence: A scale from 1–10 was used; the Consequence Assessment Worksheet assigns these values.
| Site Assessed: ABC County Courthouse | |
| TERRORIST ATTACK | |
| Threat Value (Jurisdictional Worksheet) | T = 10 |
| Vulnerability Value (Vulnerability Assessment Worksheet) | V = 9 |
| Consequence Value (Condequence Assessment Worksheet) | C = 5 |
| Probability Value (T×V) | P = T×V = 90 |
| Risk Value (T×V×C) | R = T×V×C = 450 |
| MAN-MADE DISASTER | |
| Threat Value (Jurisdictional Worksheet) | T = 1 |
| Vulnerability Value (Vulnerability Assessment Worksheet) | V = 8 |
| Consequence Value (Condequence Assessment Worksheet) | C = 9 |
| Probability Value (T×V) | P = T×V = 8 |
| Risk Value (T×V×C) | R = T×V×C = 72 |
| NATURAL DISASTER | |
| Threat Value (Jurisdictional Worksheet) | T = 1 |
| Vulnerability Value (Vulnerability Assessment Worksheet) | V = 8 |
| Consequence Value (Condequence Assessment Worksheet) | C = 5 |
| Probability Value (T×V) | P = T×V = 8 |
| Risk Value (T×V×C) | R = T×V×C = 40 |
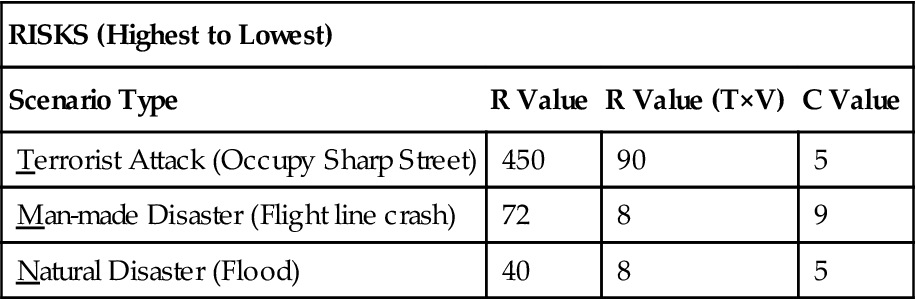
| RISKS (Highest to Lowest) | |||
| Scenario Type | R Value | R Value (T×V) | C Value |
| Terrorist Attack (Occupy Sharp Street) | 450 | 90 | 5 |
| Man-made Disaster (Flight line crash) | 72 | 8 | 9 |
| Natural Disaster (Flood) | 40 | 8 | 5 |

Overall, the Department of Homeland Security Risk Lexicon defines part of risk, as a hypothetical situation comprised of a hazard; an entity impacted by that hazard, and associated conditions including consequences when appropriate.
What has been covered in this chapter is the expected magnitude of loss due to a terrorist attack, natural disaster, or other incident, along with the likelihood of such an event occurring and causing that loss. The DHS Risk Lexicon defines Risk Assessment as a process bycollecting information and assigning the values to certain risks for the purpose of informing priorities, the ability to prepare action plans and assist in the decision making process.
The consequences that are considered for the nation-level comparative risk assessment are based on the criteria set forth in HSPD-7 which we discussed in the beginning of the text. This chapter discussed the following four categories:
Various practices are available to complete a risk assessment. A common approach based a the understanding of existing practices is needed to enable the setting of protection across sectors. The basic element of this approach is to establish a common definition and process for analyzing the basic factors of risk for CI/KR protection.
In the context of homeland security, the National Infrastructure Protection Plan framework assesses risk as a function of consequence, vulnerability, and threat. These values can be assigned and a total risk value is calculated. Once the values have been assigned you can then prioritize the values.
Risk assessments consider all three components of risk and are conducted on functional basis depending on the fundamental characteristic of the actual infrastructure being assessed.

