Selected FAQs on Using GnuPG
Bob reads from Sam Mallory’s FAQ on using GnuPG:
2.1 Why Use GnuPG
GnuPG is Free software with a capital “F”, which means not only is the program free to download and share, but the source code is also free to download, use and modify. Free software licenses basically say “Do whatever you like with this program--use it, share it, modify it, add to it and fix it, even publish your modifications--as long as you don’t change the license agreement.” In other words, feel free to add new features to GnuPG and publish them, but you’ve got to use the same license and allow others to add new features to your version of GnuPG and publish them too.
The original PGP was freeware: that meant it was free to download the program but the source code was not published. By 1996 Philip Zimmermann founded PGP Inc. to sell a commercial version of PGP; by 2010 a PGP product line was being marketed by Symantec, and other vendors offer encryption software as well. If you get what you pay for, why do so many people prefer to use a Free program?
The answer is that for encryption, free/open--meaning the source code is freely available and can be reviewed, modified and used without restriction--is best. I feel confident that GnuPG is secure not just because I can review the code, but because I know that over the years since its first release, many knowledgeable and skillful programmers and security experts have reviewed the code--and fixed the bugs and errors they’ve found.
I use software that conforms to the OpenPGP standard because that way I’ll always have access to my data. With proprietary data formats, I’m handcuffed to the vendor who controls those formats; I can only access my data as long as I pay the vendor for current software.
Finally, with closed source programs there is concern about vendors including back doors that give law enforcement agencies easy access to encrypted data. Though the intention (to defeat criminals) is admirable, the reality is back doors let in anyone who knows about them: not just legitimate law enforcement agents, but also any random hackers, corrupt sheriffs or disgruntled employees who find out about and use the back door, all of which would be bad. Free and open source software is better because no one can secretly add anything to the code base.
Plus, free/open source software doesn’t cost anything!
2.2 Why Start with the Command Line
I’m not saying graphical user interface (GUI) encryption software is bad, I’m just saying that it’s best to start out doing encryption at the command line for a number of reasons:
It’s the simplest way to get started. Just one thing to download and install (or nothing to install for Linux systems, where GnuPG is already installed).
It works the same, everywhere. If you can use GnuPG at the command line on a Mac, it works almost exactly the same on Linux or Windows.
It mostly works the same as it used to (and as it will in 5 years). No guarantees here, but the GnuPG interface is pretty stable. No need to relearn a new interface when the latest version is released or when it’s ported to run under the newest version of Windows or OS X.
GnuPG at the command line is a standard. Much easier to work with a program that is widely available and familiar to anyone who knows about encryption.
Once you understand the basics, it would be counter-productive to stick with the command line, especially if you use encryption regularly. For example, an e-mail reader plug-in to sign and authenticate digital signatures on messages, or a plug-in for a word processor if you frequently encrypt messages you compose.
2.3 Why Use the Command Line
GUIs are the default for modern end-user operating systems, but I prefer using a command line interface (CLI).
The command line is exact; there is no uncertainty about which icon was clicked on (or how many times you clicked), and there’s an audit trail that can be used to see what commands were issued1. The results of each command can also be viewed easily by scrolling through terminal session window.
There are many programs that act as GUI front-ends to GnuPG, but trying to learn encryption by using them can be as confusing as using the command line version of GnuPG. Also, a GUI front-end adds another point of failure: one more piece of software that can have security flaws or be subverted by an attacker.
Using GnuPG at the command line means stepping through each cryptographic process, which means you can be more aware of what is going on and thus can avoid security pitfalls more easily.
If you find it impossible to use the command line, using an “official” GUI (that is, a GUI program packaged with GnuPG) is acceptable. However, in line with the precept “keep it as simple as possible, but no simpler,” using the command line may be preferable where circumstances call for the greatest caution.
2.4 Getting to the Command Line
On OS X and Linux systems, use the Terminal application to open a CLI. This is the default terminal program for *nix systems; there are other programs that give access to a system shell, which are also acceptable.
The Command Prompt window lets Microsoft Windows users enter commands directly to the system. Command Prompt works similarly to Terminal on OS X/*nix systems.
Getting to the command line:
Windows: from the Start icon, choose “All Programs,” then “Accessories,” then “Command Prompt.”
OS X: the Terminal application is found in the Applications/Utilities folder.
Linux: the Terminal application can be started by pressing the Ctrl-Alt-T key combination, or from the Applications menu.
Many shell commands that make life easier on those systems are unavailable in Windows. I recommend using an OS X/*nix system for cryptography; Windows users can use a live-boot version of Linux to get the same functionality, with improved overall security.
2.5 Is GnuPG Even Installed?
Checking whether GnuPG is installed is a good introduction to using GnuPG: it calls for entering a GnuPG command and checking the result. To see whether GnuPG is installed, open a terminal or command line window and issue the command (type the command and press <Enter>):
![]()
The command prompt is the dollar sign ($). The prompt is what tells you the computer is ready to accept a command; the exact prompt you see will almost certainly look different. On Windows, it looks like C:UsersSam>; on OS X, Linux, and other UNIX-like systems the default prompt usually includes hostname (name of the computer you’re using), the path (current working directory, as with Windows), and your user ID on the system, ending with the $ symbol. Like this:
![]()
This prompt tells me that I’m logged into a *nix/OS X system as “sam,” on “sams-laptop,” in the “myDocs” directory.
To execute a command, type the command and press the Enter key.
The output from the command gpg --version will look something like this:

GnuPG reports back what version it’s running, in this case GnuPG version 2.0.19/GnuPG for Windows (Gpg4win) version 2.1.1-34299-beta. GnuPG reports more than version about itself in response to this command: where the GnuPG home directory2 is and which cryptographic algorithms are supported: listed after Pubkey are the public key algorithms being used, listed next under Cipher are the single key algorithms, under Hash for secure hashing and under Compression for compression algorithms3.
GnuPG comes in two flavors: version 1 (currently at release 1.4.12) is the “portable standalone version,” and version 2 (currently at 2.0.19) is “enhanced.” Both versions give essentially the same user experience and both are current and supported, so whichever version is installed should be acceptable.
To see which is the most current version of GnuPG, check the GnuPG web site, http://www.gnupg.org/.
2.6 GnuPG Commands and Options
One enters GnuPG commands at the system command line (Linux or Mac OS X terminal or Windows command prompt). They can be tricky to get right, but using the command line makes it easier to understand what GnuPG is doing, and makes it easier to do the “right” thing (where “right”=“what I want it to do”).
Checking for the software version is a simple method I can use to check whether GnuPG is installed; the next command I want to know is how to get help:
![]()
The gpg --help (or gpg -h) command summarizes commonly used GnuPG commands and options, and returns the same information as gpg --version, followed by a summary of GnuPG commands and options, starting with basic syntax rules for using it at the command line:
![]()
In other words, to invoke GnuPG, enter one or more options (or none), give it one or more files (or none) as needed; if an action (command) is not specified, GnuPG will choose a default action depending on the options and files that are specified.
NOTE: Using explicit commands and options will produce the best results with GnuPG, as it allows me to specify exactly what I want GnuPG to do. However, explicit commands are not always necessary.
GnuPG commands issued with a filename but without a specific command are interpreted in context of the file contents. If the file contains GnuPG data (e.g., if the file is encrypted or digitally signed), then GnuPG will do the “right thing” with the file: decrypt the file or verify the signature.
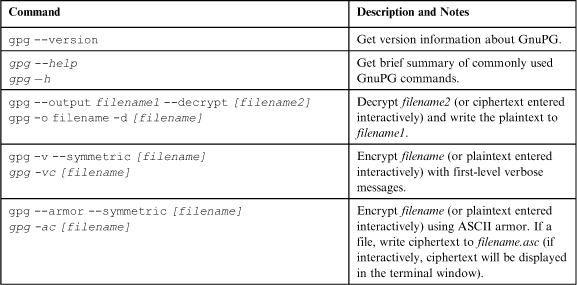
The rest of the help file contains a list of GnuPG commands (actions that the program can perform for me). This is the actual list that gpg --help displays; don’t worry if they seem confusing, I only really use a half dozen or so commands on a regular basis, and a few more less frequently:

Every command has a long-form name like: --encrypt, --verify, or --list-keys. These long command names are prefixed with the double-dash and are relatively easy to understand. Some commands also have a short-form name; for example, -e for “encrypt,” -s for “sign,” or -k for “list keys.”
I can have GnuPG sign and encrypt at the same time, but all other GnuPG actions are strictly one action at a time (e.g., list keys, decrypt data, export a key, etc.).
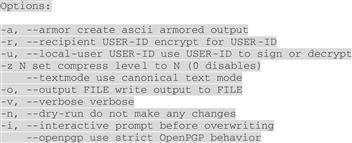
After listing the commands themselves, help lists all GnuPG options. As with commands, most users can get away with knowing only three or four of these:
Followed by a handful of examples:
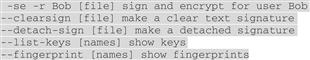
It’s easier to understand if you look at examples.
2.7 Simple Examples
To encrypt (single key) a file:
![]()
Other than the prompts to enter a passphrase, GnuPG returns no additional information, and writes the ciphertext to a file called essay.txt.gpg. The original plaintext file (essay.txt) remains on disk.
To decrypt a symmetric key-encrypted file and save the plaintext to a file:
![]()
The command entered above can be read as “decrypt file example.docx.gpg and write the plaintext into file example.docx.” When executed, the plaintext file example.docx is created after the user successfully enters the passphrase. The WARNING message indicates that although the file was encrypted, it was not digitally signed.
2.8 Options: Getting More Information
GnuPG messages can be terse, and even though the program reads or writes a file, it may not “report back” with any messages (e.g., what actually happened). To get GnuPG to return more information about results, use the verbose option (-v):
![]()
This tells me GnuPG encrypted the file with the CAST5 algorithm (the default for symmetric encryption) and wrote an encrypted file as foo.bar.gpg.
Verbose mode does not affect the function of the program, just the amount of information returned by GnuPG when it executes a command.
“Doubling” the verbose mode option increases the amount of information returned. If I specify the -vv option for this command, I get no more information—there isn’t any. Increasing amounts of information is often available for other GnuPG commands, and can be accessed by using more v’s at the command line (e.g., gpg -vvvv -c foo.bar).
2.9 Options: Text or Binary
When GnuPG creates cryptographic output (e.g., when it encrypts a file, exports a public key, generates a digital signature), the default behavior is to save the output to a binary file with the extension .gpg. As noted above, it is also possible to output to a differently named file relatively easily, but it will still be saved as a binary file.
Binary files are fine, but it’s often better to produce human-readable output. For example, when a digital signature is appended to an e-mail or other text message, the signature must consist only of characters that can be displayed correctly by the e-mail or other application software. This is why there is an option in GnuPG to generate output that encodes all the cryptographic data in a form that can be displayed in readable form.
The --armor (-a) option directs GnuPG to “create ASCII-armored output.” Armored output simplifies matters when sending encrypted data in an e-mail message, or when publishing public keys4.
To encrypt symmetrically to an ASCII-armored file, I use this command:
![]()
The default output file is foo.bar.asc (.asc indicates that the file contains ASCII data). That file can be viewed with any text editor—or listed at the command line with shell commands like cat, less or more:
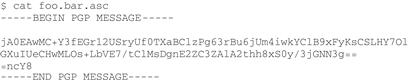
ASCII-armored results can be saved to a file, cut and pasted into a message, or printed out and manually re-entered to a computer for decryption later. You could even take a photo of the output; this kind of screenshot might be enough to fly under the radar of an attacker looking for suspicious files.
ASCII armor is particularly useful when experimenting with GnuPG.
2.11 Review Questions
1. Practice some of the command line commands introduced in this chapter, including one to get a listing of all files in a directory, and to list a file’s contents on screen. Look up how to copy a file at the command line of your OS, how to delete a file, and how to use wildcards to do things to multiple files with a single command.
2. What is a FAQ? What is a Howto document? Why do you think Sam is compiling a FAQ on how to use GnuPG?
1You can scroll old commands with the up and down arrow keys, and view all previous commands via the “history” command (on Windows, doskey/history). This can be a risk since anyone looking at your commands can see which files you’ve been encrypting and decrypting, if you don’t clear your history manually. See Chapter 8 for more information.
2The directory C:UsersSamAppDataRoaminggnupg is the GnuPG home directory on a Windows system; it would be ~/.gnupg (a hidden directory in the user’s home directory) under OS X or Linux.
3By default, GnuPG compresses files before encrypting; according to the specification in RFC 4880, “compression has the added side effect that some types of attacks can be thwarted by the fact that slightly altered, compressed data rarely uncompresses without severe errors.”
4For more about ASCII armoring, see http://tools.ietf.org/html/rfc4880#section-6.2.