Using Gnu Privacy Guard
Bob lives in Sylvania, a tiny nation ruled by a dictator who forbids all printed dissent and criticism. However, emboldened on a visit to the United States, Bob wrote his own brief editorial, on a cocktail napkin while sitting at the airport bar, waiting to board his plane home. It begins:
Free Sylvania!
Those two words alone could send Bob to the Sylvanian gulag if discovered back home. As the exhilaration of creation wears off, Bob downloads and installs Gnu Privacy Guard1 to encrypt his work. He’s been told it’s good for encryption, and it’s free, so why not?
Bob’s plane leaves Logan in 15 minutes, and when he starts reading the tutorial for GnuPG, he panics: it goes on at great length about public key encryption and key pairs and generating key pairs and generating revocation certificates, and even when he gets to the part about encrypting a file, it says he’ll need someone else’s public key to encrypt to. Bob quietly starts to freak out.
Fortunately for Bob, he’s sitting next to a man who picks up on Bob’s anxiety and offers to help. This good Samaritan is actually named Sam, and he just happens to know all about GnuPG. After they introduce themselves, Sam says, “Listen Bob, I can help you get it all sorted out, don’t worry. We’ve even got time for a drink before they board your flight.”
1.1 Keeping Data Secret, for a Novice GnuPG User
After seating themselves in the lounge, Sam says, “You’re in a hurry and need to encrypt a file. You’ve just installed GnuPG but don’t know much about encryption, so your best bet is to use single-key encryption with a strong passphrase. It’s easy: all you need is GnuPG, no need to set anything up.”
Sam explains, “Using symmetric (secret) key encryption I can make sure no one can see the contents but me (and whoever I share the passphrase with). That’s how I’d do it if I was in a hurry and didn’t have time to study tutorials or books.”
Bob looks pointedly at his watch, then the departure board, but Sam continues, “Symmetric encryption is easy with GnuPG because I don’t need to generate my own public key pair or get anyone else’s key: I just enter an encryption command and enter a strong passphrase for my encrypted file. Are you ready?”
1.2 The Simplest Example: GnuPG Symmetric Encrypting Text
Sam opens his laptop and a terminal window, and explains to Bob: “I think of GnuPG commands as if they’re sentences; every GnuPG sentence starts with ‘gpg’, and there are grammar rules in this sentence like ‘options first, then files’ and ‘options before commands’. You have to be careful to follow the grammar, but it’s usually easy. Here’s how I encrypt a file called example.txt2,” and he types:
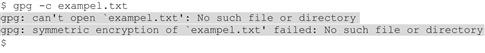
“Oh crud, what the…” Sam, reading the GnuPG error messages onscreen after he hit <Enter>, realizes he misspelled the filename. “Oops, that’s what you get when the filename doesn’t exist in the current directory; it happens all the time and isn’t a big deal. And if you get an error message that doesn’t make sense, you can usually get help by searching for that message on your favorite web search engine.” Sam retypes the command and is prompted for a passphrase3 (twice):
![]()
“OK, I entered a passphrase, but now, nothing. Or is it?” Sam says as he shows Bob a directory listing4 that includes a new file called example.txt.gpg. “When GnuPG creates new files, it names them by adding the .gpg extension.”
Sam continued: “Here’s my thinking when I enter that command. First, gpg=’run GnuPG’. Then, -c, an abbreviation for the command --symmetric, for single-key encryption. If I used the -e option (--encrypt) that would be for doing public key encryption; I’ll show you public key encryption later, if you like.” Sam sipped his drink.
“So that’s my command: ‘GnuPG, encrypt something!’. ‘Something’ is whatever comes after the command, in this case a file called example.txt in the current directory5. I hit <Enter> and I’m prompted to enter a passphrase, and it should be something hard to crack. Good passphrases are hard to come up with, but they should be longer than 8–10 characters at the very least, and should appear as random as possible, including upper and lower case letters, symbols and numbers. It will be hard to remember, but it will also be hard for someone to guess. Just remember that if you forget it, you won’t be able to decrypt your file either.”
Bob asks, “How do I decrypt this file? Do I need GnuPG to decrypt?”
1.3 Decrypting a File (Symmetric Key)
Sam said: “It’s easy to decrypt a file, but you do need GnuPG (or compatible software6) to do it. Here’s how,” Sam says as he types the command and hits <Enter>, entering a passphrase when prompted:
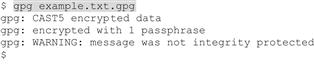
“Sam, what does that WARNING mean?” Bob asks. “Oh, don’t worry about that: GnuPG can be a chatty little program, and not always completely clear. The first two lines mean the file was encrypted with the CAST5 algorithm--the default for GnuPG single-key encryption, with one passphrase. The last line means the file wasn’t digitally signed.”
Sam continues: “The messages tell you the file was encrypted successfully. GnuPG stored the decrypted file, named example.txt, to disk; now both files are in my directory. I didn’t have to explicitly say I’m decrypting (though I could have used the --decrypt option for clarity). Often you can just enter gpg <file_name> and GnuPG ‘does the right thing’ with the file--if it’s GnuPG compatible7, like if it’s an encrypted file and you enter a valid passphrase. If you enter a file that’s not GnuPG compatible, you’ll get an error, GnuPG won’t assume you want to encrypt unless you tell it explicitly, with -c for symmetric encryption, or -e for public key.”
Bob spoke up: “Hang on, Sam, do I have to save it to a file? I’m not sure I want to save my secrets as plaintext on my hard drive.”
Sam answers, “That’s a good point. You’d probably rather just use the --decrypt or -d command, because GnuPG sends its output directly to the standard output (that’s a fancy name for the terminal window, or console).” He types a few lines, and says, “here’s what it looks like, I’m really just telling the computer: ‘run GnuPG and decrypt (some file)’ ”:

Sam went on: “After I enter the passphrase, GnuPG prints the decrypted file out to the console--it’s highlighted here, a 3-line text file. This is a simple way to decrypt files with GnuPG: just enter gpg -d <filename> (whatever the filename actually is); if the file can be decrypted GnuPG just splashes it out to the screen, no worries about having incriminating evidence saved on your disk, either.”
As Bob peers at the screen, Sam goes on: “Bob, you should know that when I have a plaintext file and I encrypt it, GnuPG creates a new file for the encrypted version (that’s what we call ciphertext) but nothing happens to the original plaintext file. It’s still sitting there, so you should securely erase8 the plaintext file, not just delete it, if you’re worried about someone finding it. Otherwise it could get you in trouble.”
Bob says, “But I’d rather not save a dangerous secret on my disk at all, ever; even if I delete it, it can still be recovered--can’t it?” Sam answers, “Yes, it often can be recovered, but there are ways to make it harder…” when Bob interrupts: “Is there any way I can encrypt something without saving plaintext to the disk at all?”
As the flight attendant announces “All passengers attention. Now please board Sylvania Air Flight 789,” over the intercom, the men finish their drinks and start packing up. “Listen Bob,” Sam says, “here’s my card: give me a call if you want to talk more about this. I’ll be in Sylvania for a couple of weeks on business, so let’s meet for another drink and I’ll answer all your encryption questions then.”
Bob examines the card: “Sam Mallory, Consultant”, a phone number, an email address ([email protected]) and a string of what seems to be nonsense letters and numbers; then looks up to see Sam lining up for Bob’s own flight. Bob hurries after Sam; he wants an answer to his last question before their paths diverge.
1.4 Encrypting Interactively
“Hey, Sam--looks like we’re on the same flight! Where are you sitting?” Bob asks as he catches up to Sam. “Please, can you explain how to encrypt interactively?”
Sam, ignoring Bob’s first question, replies, “Sure, interactive encrypting. It’s not hard, just a bit strange for people who are used to working in a GUI all the time.”
Sam clears his throat. “Remember how the GnuPG command looked? First it said gpg, then it said what to do, like --encrypt, and then we typed in a filename to encrypt. I said if you leave off the command but give a filename, GnuPG can figure out what to do with the file if it’s an OpenPGP-compliant file.” Bob nods as the line inches forward.
Sam says, “The last part of the command, where you put the thing you want to encrypt or decrypt or digitally sign is (often) optional. If you leave that part blank, GnuPG assumes that you’ve got something to enter interactively. Instead of doing anything after you hit <Enter>, GnuPG will wait for you to enter something to encrypt or decrypt.”
Bob thinks about it for a moment as the line inches forward and asks, “How does that work, though? What gets output? How do you enter something to encrypt?”
“Good questions,” says Sam. “This is where it gets a little more complicated, because you have to use an option, in this case the --armor or -a option. ‘Armor’ is short for ‘ASCII-armored’.”
“Huh? What does that mean?” Bob goggles as Sam inches forward in line.
1.5 ASCII Armor
Bob catches up as Sam says: “You want your ciphertext to look as random as possible. That means random bits, which when you try to print it out as text it looks like crazy gibberish, lots of weird symbols. It looks like your computer’s barfing at the command line.” Sam opens his laptop to demonstrate. “Like this”:9

“That’s called binary output. Computers can read it, but people can’t make sense of it, at all.” Bob nods, and Sam continues:
“Sometimes we want GnuPG to produce encrypted output that uses letters and numbers that humans can accurately decode--something we can print out to the terminal window or stick in an email message. It looks like letters and numbers, but it’s random-looking letters and numbers that don’t seem to mean anything.”
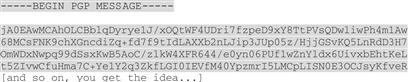
“ASCII armor is a way to get that kind of human-readable output; it means, ‘encrypt this data but output only standard alphanumeric characters’. It makes more sense when you can look at it.” Sam types a bit more and shows Bob an ASCII-armored file:
Sam tucks his laptop under his arm as the flight attendant takes his boarding pass and ushers him toward the plane; Sam turns to Bob and says, “Maybe I can show you more on the plane. See you later!” and walks off--as the other attendant turns to Bob and, looking at his boarding pass, says, “Sir, we’ve overbooked this flight today, would you please wait a moment?”
Accustomed to long lines and dodgy supply back home in Sylvania, Bob waits, outwardly placid and smiling neutrally--and is rewarded almost immediately as the flight attendant looks up from his terminal to say, “Mr. Wobble, we have a seat in first class for you today, would that be acceptable?” Without waiting for an answer, the attendant ushers Bob toward the front of the plane and seats him next to his new friend, in the nearly empty first-class compartment.
“Oh, hey, congratulations! Coach on this flight is always a sardine tin. Get comfortable and I’ll show you interactive encryption and ASCII armoring,” says Sam as he opens his laptop again. “Look:”
![]()
“I’ve just started GnuPG with the option, -a, to generate output in ASCII armor, and a command, -c, to do symmetric encryption. Notice I don’t have to give each option its own hyphen--but I could, if I wanted10.”
“Since I haven’t specified an input file, GnuPG gives me a completely empty line, and I can start typing my message. When I’m done, I have to enter an ‘end-of-file’ sequence)11. GnuPG prompts for a passphrase (twice); here’s the result:”
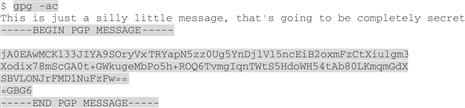
Sam says: “The plaintext is that line of text I typed in after the command; the ciphertext output is under that line. See the lines with hyphens that say BEGIN PGP MESSAGE and END PGP MESSAGE? Those are the part of the ASCII armor that shows where ciphertext begins and ends.”
Bob, staring at the lines, asks “What is this ‘PGP’? Is it part of GnuPG?”
Sam says, “It’s a long story. ‘PGP’ stands for ‘Pretty Good Privacy’, the first real end user encryption software, written by Philip Zimmermann back in 1991. It was a big deal because the US government considered strong encryption munitions, so it was illegal to ‘export’. With software, that just means downloading it over the Internet, and Zimmerman could have gone to federal prison for it. He stuck his neck out, and he’s a hero to many. It eventually got sorted out, but with the genie out of the bottle the feds backed down and now almost everyone has, or can get, strong encryption12. If it weren’t for Zimmermann, we might not be sitting here talking about encryption.”
As the flight attendant serves Bob and Sam flutes of champagne and moist warm towels, Sam continues: “PGP fascinated Internet pioneers back then, and as the only practical, accessible, program for encryption, PGP was eventually written into Internet standards, and used widely enough that an Internet standard called ‘OpenPGP’ was created.”
“Anyone can write programs conforming to the OpenPGP standard, so anyone else’s OpenPGP-compliant programs can be used to exchange encrypted and/or digitally signed data. You don’t, strictly speaking, need to decrypt a GnuPG-encrypted with GnuPG, you could use a commercial program--like PGP Software from Zimmermann’s old company, or an open source one if you want. However, many people now use the open source project Gnu Privacy Guard, a.k.a. GnuPG.”
Bob sips his own drink and settles luxuriously in his seat as he listens, and asks, “Why doesn’t everyone use PGP then? Wouldn’t it be better to buy software from a company instead of this open source stuff? Couldn’t someone hack GnuPG by sticking in some kind of back door? Also, why should I use the command line--isn’t there a Windows program I can use? And what about public key encryption?”
“Bob, those are some great questions, but I’ve had a long day. We’re not going to get to Sylvania for another 12 hours, so if you’ll excuse me, I’m going to take a nap, and you can look over my notes about using GnuPG and how to use the command line. When I wake up we can talk about public keys. OK?” Sam says as he hands Bob a folder.
“Sure, Sam, I can do that. Thanks!” Bob opens the file and starts to flip through several dozen pages of laser-printed manuscript. “What a nice coincidence that I bump into someone with so much encryption knowledge, just when I need it!” he says, to himself as Sam has already shut his eyes and reclined his seat for a nap.
1Go to www.gnupg.org/download for the official downloads; http://gpg4win.org/ for GnuPG for Windows and https://www.gpgtools.org/ for GPGTools (OS X).
2Files in these examples will always be read from or written to the current working directory in the terminal/console session (unless otherwise specified).
3Depending on the OS, you’ll get a different kind of prompt; usually it’s in a small GUI window that pops up specifically for secure passphrase entry.
4dir on Windows, ls on Mac OS X or Linux.
5A directory is the text-only version of a folder; folder is the icon for the directory.
6Any program that supports the OpenPGP standard for encryption should work. OpenPGP is discussed later in the chapter.
7GnuPG creates files that conform to the OpenPGP format. Any programmer that knows the format can (theoretically) write a program to recognize and work with GnuPG files.
8For more about secure deletion, see EFF “Secure Deletion (Surveillance Self-Defense project)” at https://ssd.eff.org/tech/deletion.
9Sam uses the UNIX/Linux/OS X command cat, for “reading files sequentially, writing them to the standard output.” In Windows, use the command more filename.txt to list the file filename.txt.
10Sometimes is the operative word; other times, you’ve got to keep options separate.
11On Windows: press <Enter> then <ctrl-z> then <Enter>. On OS X/Linux, press <Enter> then <ctrl-d>. That is, the <Control> key plus the letter “z” (or “d”). Pressing <ctrl-c> (“abort”) quits GnuPG without executing any command.
12Encryption software can be difficult to come by in some countries where Internet access and access to computers may be limited by the government.

