Editing and Revoking a Public Key
“Why would I want to edit my key? What is there to edit? And what about revoking a key?” asks Bob. “You had a lot to say about key revocation earlier, but I still don’t really understand what that means, and how it works. Can you explain?”
Sam responds: “Your public key pair is more than just the raw bits of the public and private keys used for encrypting and digital signing. There are other pieces of data that get bound up with your key pair: the name and e-mail address you enter when you generate the key, the time/date the key was created, the time/date the key expires, even the passphrase you use to protect the key.”
“Some of those things cannot be changed, obviously, like the time/date the key was created; some can be changed but probably shouldn’t until you’re more experienced with GnuPG, like name and e-mail address; and there are some things where it makes a certain amount of sense to know how to change them, like the passphrase protecting the key, signing someone else’s key, setting an expiration date or revoking a key entirely,” Sam explains. “So it’s good to know how to edit a key.”
7.1 Editing Keys
“There are a lot of ways to edit keys: for example, there are four different ways to sign a key1, and there’s a way you can direct others to a particular keyserver to retrieve your key2. All key editing starts with the basic GnuPG --edit-key command. The syntax is like this”:
![]()
“You have to specify which key to edit, whether it’s by the user ID, name, or e-mail address. GnuPG returns an error message with command syntax summary if you don’t specify a user. You can also include a command (e.g., passwd to change a passphrase), otherwise GnuPG returns a special key-editing command prompt after it lists some key information.” Sam says, nodding at the screen. “Like this”:
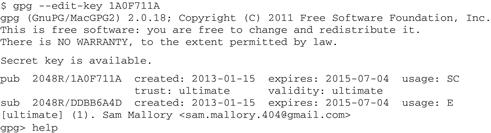
“With the command gpg --edit-key 1A0F711A, I tell GnuPG I want to edit my key. GnuPG tells me about the key (so I can make sure it’s the one I want to edit), and gives me this new prompt, gpg>. If I type the word ‘help’ here, GnuPG lists a few dozen key-editing commands.” Sam pauses and says, “But I won’t do that. I just wanted to show you how it works, so you know how to change a key expiration date3 or revoke a signature on someone’s key4. Also, you need to save changes before you exit this key-editing mode5.”
“As long as you read the prompts, you should be OK. Also, you exit from the gpg> prompt by typing quit and hitting Enter; if you’ve made changes, GnuPG prompts you to save them before quitting. Next, we’ll revoke a key,” says Sam.
7.2 Revoking a Key
“You’ve got to be able to revoke any key you’ve created, especially if it doesn’t have an expiration date6.” Sam says, glancing at Bob for confirmation.
“If you’re revoking a key by choice, you have the advantage of being able to plan how you do it. So if you are changing jobs or want to migrate to a stronger key, give a warning to the people who use it. More importantly, when you generate your new key, sign it with your old key before you revoke the old key. That makes it easier for your associates to accept your new key as yours and not an attempt by someone else to steal your identity.” Sam goes on: “But if your key has been compromised, issue the revocation immediately and notify your associates: you may need to distribute your new key in person, as we’ve already discussed.”
“But Sam, please explain how I revoke a key? You talk about revoking, and you talk about a revocation certificate--how does it all work?” asks Bob.
7.2.1 The Revocation Process
“Ideally,” begins Sam, “when you create a new key you also generate a revocation certificate for it. This ‘certificate’ is basically a signed message from yourself (the keyholder) announcing your key is invalid and should not be used. You store this certificate somewhere safe--a safe deposit box or anywhere it won’t be easily found or associated with the computer you use with that public key. If you lose control over your key (someone stole your computer or cracked your passphrase), you can use the revocation certificate to revoke the key.”
“So there are two steps in revoking a key: generating the certificate and keeping it safe, and publishing the certificate when you need to revoke the key.” Sam, seeing Bob is still looking confused, says, “I’ll show you.”
7.2.2 Creating the Revocation Certificate
“The command to generate a revocation certificate is this”:
![]()
“Doing it this way, the certificate is echoed to the screen (GnuPG produces this output using ASCII-armoring), or you can use the --output option to specify a file in which the certificate is saved. Here’s what it looks like,” Sam says as he enters the command:
![]()
“I’ve entered my own key ID, and GnuPG returns information about the key: it’s a secret key, 2048 bits, the date I created it and my name and e-mail,” says Sam.
“Do I have to use the key ID?” asks Bob, “What about name or e-mail?”
Sam answers, “Yes, you could use those, but it’s better to get the key ID, in case you have more than one key with the same name or e-mail; the key ID is unique.”
“If it’s the correct key, answer yes to the first prompt, and then indicate why you’re revoking the key. I prefer not to advertise that I’ve had my key compromised--it reflects poorly on my security habits--so I’d just say the key has been superseded or is no longer used, or perhaps not specify any reason at all”:

“The next prompt is for a ‘description’; again, my inclination is to not give away too much information, though you can enter a general message (‘Contact me for details’) or anything you like--or nothing,” Sam says as he continues typing:

“Next, enter the passphrase for that key. Without the passphrase, you can’t do anything--another reason to generate the revocation certificate right away after generating the key, so if you do forget the key, at least you can revoke it.” Sam enters his passphrase and GnuPG returns a message along with the certificate:

Sam explains, “That PGP block is the revocation certificate; I can cut and paste that block to use it, but it’s easier (if I’m careful) to send the output directly to a file. I’d use this command to save the revocation certificate to revkey.asc”:
![]()
Bob scans the GnuPG message above the PGP block and asks, pointedly, “Why does it say that about Mallory accessing the certificate, is that bad for you?”
“Oh, that’s just a coincidence: ‘Mallory’ is a name used in the ‘cryptographic cast of characters’. It’s a name--like Bob or Alice or Eve--that stands in for a role. It’s a placeholder, and just a coincidence, the same as we use the names ‘Bob’ and ‘Alice’ when talking about two people communicating with each other. Also, ‘Eve’ is an eavesdropper, and ‘Mallory’ (or ‘Mallet’, sometimes) is a ‘malicious attacker’. Nothing at all like myself, of course.”
“I see,” says Bob, “of course. But as we’ve already determined that you are using a pseudonym, it was an interesting choice on your part, no? Please, do continue.”
Sam, flustered, says, “Yes, where were we? Oh yes, revoking the key.”
7.2.3 Revoking a Key
“There are two steps to issuing the revocation: first, revoke the key on your own keyring--when you are ready to stop using--and second, publish the revocation to a public keyserver, if you’ve published it to a keyserver,” Sam explains, “So, first, load the certificate into your keyring like this”:
![]()
“Once I import the revocation certificate I can no longer use the key to sign anything but I can still decrypt any ciphertexts encrypted with it.” explains Sam. “Next, I publish the revocation to any keyservers I posted my key to, like this”:
![]()
“And that’s all; if you want to see that your revocation was accepted by the keyserver, you’ll have to go check the keyserver directly and look up the key ID.”
Sam adds, “And don’t forget, if you’re doing a routine revocation, use the old key to sign your new key before you revoke the old one. That way your associates can trust the new key without too much trouble if they refresh their keyrings from a keyserver periodically. Just be sure to warn them the key is changing.”
7.2.4 A Different Way to Revoke
“If you don’t want to generate a revocation certificate, you can use the --edit-key command--as long as you’ve got your key passphrase,” answers Sam. “You still need to update a keyserver to publish the revocation. Here’s how”:
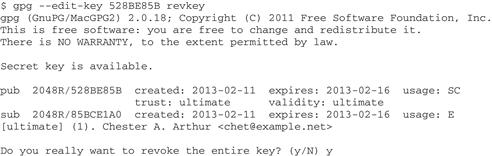
“From this point, it’s almost exactly the same process as before; the big difference is that when you’re finished, you go back to the gpg> prompt. From there, quit and you’re prompted to save changes. Then, publish the revocation to a keyserver, same as before,” finishes Sam.
“Thank you, Sam, everything is very clear,” replies Bob, “or should I call you Mallet?” Bob pauses just a moment and then says, “It seems as though we’ve covered most of my questions about GnuPG, but I’m sure there must be more I should know about. Do you mind if I check my e-mail and take some notes, that should take about half an hour--maybe we can wrap things up then?”
7.3 Command Summary and Review
| Command | Description and Notes |
| gpg --edit-key user-id [commands] | Edit key identified by user-id (name or e-mail is also allowed); commands are optional, if left out, GnuPG prompts for interactive editing. |
| gpg --gen-revoke key-id | Generate a revocation certificate for key-id (user ID, name or e-mail). Resulting certificate will be echoed to the screen; use --output option to output to a file. |
| gpg -o revkey.asc --gen-revoke key-id | Generate revocation certificate for key-id and save as revkey.asc. |
| gpg --import revkey.asc | Import the revocation certificate (revkey.asc) and revoke the key locally. |
| gpg --keyserver keyserver --send-keys key-id | Publish revocation to keyserver. |
| gpg --edit-key user-id revkey | Revoke a key using the GnuPG key editor. |
7.4 Review Questions
1. Who are some of the other “players” in the cryptographic cast of characters? (Hint: use your favorite search engine for more information.) Why is it helpful to use these placeholder names?
2. If you lost your passphrase for an old key that’s been published on a keyserver, is there anything you can do about it? (Hint: you can’t revoke that key, but you can sign it with some other key--remember that keys can have comments.)
3. Change the expiration date on your public key. How would you add (or edit) the user name with --edit-key? How? (hint: it’s not obvious or easy.)
4. What’s the difference between revoking a key and disabling a key?
1They are sign (make a signature on the key), lsign (sign for local purposes but never export the signature), nrsign (sign nonrevocably, meaning the signature cannot be revoked) and tsign (make a “trust” signature, similar to the --edit-key trust command but used within groups rather than globally). These special types of signature can be combined (e.g., a key can be signed nonrevocably, for local use only).
2The command --edit-key keyID keyserver will prompt for a URL of the preferred keyserver to refresh the key from, when needed. This is a preference that users may override.
3Enter the command gpg --edit-key key-id expire and you’ll be prompted for a new expiration date for key-id (see Chapter 3).
4Enter the command gpg --edit-key key-id revsig and you’ll be prompted regarding which signatures to revoke. Novices should use this with caution, if at all.
5After entering change information, at the gpg> prompt enter save and GnuPG saves the change(s) and exits to the OS command line. Enter quit and, if you’ve made changes that haven’t been saved, GnuPG may prompt you to save before exiting.
