Working with Public Keys
“Sam, it seems I should have some better way to find a person’s public key. And how can I be sure a public key belongs to the person I think it belongs to?” asks Bob. “And, you said something earlier about revoking keys….”
“All excellent questions,” Sam replies. “Because you will be working with keys now, you should know more including using public keyservers, revoking keys, editing keys, and most important, deciding whether or not to trust a key. We’ll get to all those things in good time; first, let’s talk about trusting a public key.”
6.1 Trusting a Public Key
Sam says: “‘Trust but verify’ also applies to public keys. For example, consider keyservers: they are public servers hosting user-generated content. Just because a public key has been uploaded to the keyserver doesn’t mean it’s true: I can upload a key with your name and your e-mail address on it, but it doesn’t prove that key is your key. But, there are other ways to gain confidence.”
Bob asks, “What about giving me your key directly, shouldn’t I trust that?”
“That is one way to do it, but you still need to verify the key is what I say it is,” replies Sam. “The obvious way is to examine the entire public key and make sure it’s exactly correct--because a public key has to be exactly correct. Change one character of a public key, and that key is no longer usable.”
Bob asks, “Could I print out your public key and compare it to … what would I compare it to?”
“First off, keep in mind that the public key you just created seems relatively short only because it has not been signed by anyone but you; the public key block for a key that’s been signed (see web of trust) is too large for a person to verify by hand,” Sam says.
“If I give you my pubic key in person, and I’ve also posted my public key on a web site, you could compare those two keys,” replies Sam, “but you’d still have to trust that I am who I say I am; most people would check my passport or drivers license in addition to my public key.”
“You could also use a trusted third party, like if there were someone we both knew, and that person gave you a copy of my public key, you could compare the key I give you to the key that other person gives you--this is web of trust stuff again. This comes up with signing keys for open source projects: you download the signing key from the project web site, as well as from any mirror sites, and compare the keys from all those sources,” says Sam. “But there’s a better way.”
6.1.1 Using Fingerprints
“The public key block is right at the edge of manageability for a person (see the one on page 26): it’s a page or so (or more) of random-seeming text, which is a lot of random-seeming text for a person to process. But if you generate a secure hash on the entire public key, you have a fingerprint uniquely identifying the key. If I give you my public key and that key’s fingerprint, you import the public key and compare fingerprints. If they match, the public key is verified.”
“But it could still be fake, right?” asks Bob.
“Well, at some point you have to be willing to trust people you’re encrypting data with. I can claim to be Barack Obama, e-mail address [email protected], and my fingerprint checks out with a public key you found on a keyserver--but that doesn’t make me the president.” Sam continues: “What it does do is give you confidence that when you encrypt a message to me, ‘Barry’, I will be the only one who can decrypt it.”
“I could show you a passport and ID to prove my identity--but since you already know I’m a spy, you probably won’t trust my documents. You can, however, be confident that my public key is connected to me, the person sitting next to you, the person you know as ‘Sam Mallory’. It’s subtle, but it’s there and you need to deal with it.”
6.1.2 Other Ways of Verifying a Public Key
Sam continues: “In addition to the technical ways of verifying public keys, I try to use common sense to determine how much I need to worry.”
“For example, I look for multiple sources for a public key: a book, a web site, a keyserver, wherever a public key might be published. An attacker might be able to switch out the legitimate public key on my web site, but it’s harder to replace a key on a printed page in a library book. Some people even put their fingerprints on their business cards, to make things simple,” says Sam.
“How do I find the fingerprint?” asks Bob, “and what actually is it?”
6.1.3 Fingerprints
“The fingerprint for a GnuPG public key is 40 characters, usually displayed as 10 four-character ‘words’. To see a fingerprint, use the --fingerprint command”:
![]()
“Where [keyID]1 is the actual key ID or a partial/complete string of the key’s user name or e-mail address or comment. You should also know that the key ID is the last 8 bytes of the fingerprint2, so if you have the fingerprint handy, you also have the key ID. I can display the fingerprint of any key on my keyring by specifying that 8-byte key ID; here’s mine”:
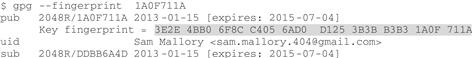
“Also, my name would work,” adds Sam, “or my e-mail address, or a string from my key comment, though usually it’s best to use the key ID, since it’s most likely to be unambiguous--I may have more than one public key, or you may have public keys from two people with the same name, but key IDs should be unique.”
Bob frowns and asks, “Should be? Are fingerprints not unique?”
“Well, key IDs and fingerprints can collide in theory, but in practice you shouldn’t have to worry about it, at least not for now3, ” answers Sam, continuing:
“You verify the public key by comparing the fingerprint GnuPG shows to the fingerprint you get from the keyholder: look at the back of my business card, and compare to what GnuPG returns. Should be the same.”
Bob taps in the command, and Sam continues: “If they don’t put their fingerprint on their business cards, people may post their fingerprint online with their public key; ideally, you want to get a fingerprint directly from the keyholder (along with photo ID), or if you know the keyholder well enough to identify them over a phone connection, that’s another way to get a fingerprint that you can trust.”
Bob asks, “What about sending a fingerprint by e-mail?” Sam replies, “That’s not a good idea because you might be tricked by a man-in-the-middle attack. That’s where someone intercepts messages intended for you, and changes them. Even if the fingerprint is sent encrypted to your public key, that proves nothing about who is sending the message. Just remember that it’s best to do verification in person.”
“What about keyservers, Sam? Can’t I get all this stuff from them?” asks Bob.
6.2 Using Keyservers
“With keyservers, as with everything on the Internet, you should trust but verify: a keyserver is no more trustworthy than the keys submitted. Remember what I said earlier? I can upload a public key in the name of Barack Obama--or anyone--to a keyserver; that still doesn’t make me the president.” Sam continues:
“A keyserver is an Internet server that stores public keys, and responds to requests relating to public keys: you can upload a key, download a key, or search for keys that match a name, e-mail address, or some other string. The preferred way to get to a good keyserver is to specify keys.gnupg.net4; it shouldn’t matter which one you use because they are designed to synchronize with other keyservers5; if you update a key on one, eventually all of them that are synchronizing properly will be updated.”
“For the casual user, or for the user who wants to maintain a low profile (that’s you, Bob), it’s not too important to worry about keyservers. They’re a convenient way to publish a key, and (usually) no need to validate the information connected to your key. Think of it like Facebook for public keys.”
Bob, clearly not satisfied, asks, “But how would I use a keyserver if I needed to?”
“I ask you to send me a secret using key ID C93138D9, but I can’t give you the whole key. Instead, I give you the fingerprint and tell you to get the key from a keyserver. The least technical way to do it is to connect to the server with my browser, use the interface to search for public keys matching that ID, and then verify the fingerprint. To search on key ID, you need to prefix the ID with the characters 0x (the numeral zero plus the lower case letter x), which identifies the rest of the value you enter as a key ID6.”
Bob frowns again, saying, “Sam, I must protest, this seems terribly complicated.”
“Or, you can use GnuPG commands to interact with keyservers; some people just like using a web interface, even if it is complicated. Keep in mind, sometimes the command line doesn’t work, though when it does, it’s great. Here’s a summary of how to use keyservers at the command line,” Sam says, handing a page to Bob:

aNote the keyserver specified: anyone can set up a keyserver and they don’t have to synchronize with the rest of the OpenPGP world. In this case, “spies.example.net” is for spies.
“The default keyserver is set to keys.gnupg.net in the GnuPG config file7,” Sam notes, “but the [server name] option is available to specify a particular keyserver to use; for example, if there is some private keyserver you want to use that isn’t included in the ‘public’ OpenPGP universe.”
“If you’re sending or receiving specific keys, you need to specify a key ID--using a string from the keyholder info won’t work,” Sam points out, “but you can use a string for searching on a keyserver, and if there are multiple hits, you’ll be prompted to specify which one you want and GnuPG retrieves that one for you.”
“A couple more things: with --refresh-keys, the search term is optional; if you leave it out, GnuPG will update your entire keyring from the keyserver. And with --send-keys, if you leave the search term out, GnuPG sends your entire keyring to the keyserver.”
“Bob, I can search for your last name in the keys.gnupg.net like this”:
![]()
“You’ve got to give --search-keys something to search on: a key ID, or a string8. If it’s a string, the keyserver returns any public key with that string in the name, e-mail address, or comment. If it’s a key ID, remember to prefix it with 0x. This will return all the keys that match the string ‘Wobble’, like this”:

“Hm, Bob, it seems you’ve exported your key to the keyserver. How did you manage to do that…” Sam, seeing Bob’s key on the list of public keys registered on a public keyserver, freaks out, but Bob sees the key and explains:
“Oh, you think that is me, but no--I told you, ‘Wobble’ is a common name in Sylvania; also, ‘Bob’. This Bob Wobble is Chairman of Sylvania Freedom Party. Also known as ‘Great Leader’. That is interesting, that our GL uses PGP. Also, different e-mail from mine,” says Bob.
“Oh, right. Bob Wobble. Of course I know who that is. But see here, look up any name: ‘George Bush’ or ‘Barack Obama’ or even ‘Adolph Hitler’ and you’ll see someone registered a public key. Means nothing--it demonstrates how little you should trust public keys you find on a keyserver, unless you have a fingerprint directly from the keyholder (or are willing to trust the signatures on the key),” says Sam. “Anyway, GnuPG lists all the matches it gets from the keyserver, and lets you choose which one you wanted to import; you enter the number, say ‘2’, and hit enter, and voila”:
![]()
“If you picked a key already on your keyring, GnuPG checks to see if the key has been updated in anyway (revocation, or additional key signings, or any other changes), and gives you a message like this if there’s no change:
![]()
“If the key has been updated, when you run --recv-keys your copy of the key will be updated from the keyserver:
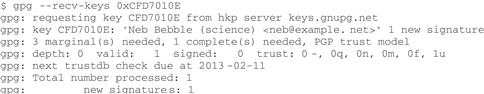
“That’s a quick rundown of working with keyservers; we may sometimes post our keys to a keyserver for convenience--we could even send messages in the name, e-mail or comment section of a public key we use to sign another key. The key thing to remember--no pun intended, eh Bob? The key thing to remember about keyservers is that once you put a key up there, it’s very difficult to delete, and it very quickly gets propagated to other keyservers all over the world.”
Bob asks, “So, how important is it that I know how to use keyservers?”
“At first, don’t worry too much about it. Look on the other side of that page I just gave you, there’s some listed there,” says Sam, as Bob looks at the sheet:
| Server Name | Notes |
| keys.gnupg.net | This is an alias for the official SKS pool (see next entry). You can see a list of IP addresses for servers currently in the pool with the command “keys.gnupg.net.” |
| pool.sks-keyservers.net | The main pool of SKS keyservers. Each pooled keyserver synchronizes with other servers, so it is only necessary to submit changes once to update the entire OpenPGP network. See http://www.sks-keyservers.net for more information about SKS pools. |
| keyserver.pgp.com | PGP Global Directory; a “verified” keyserver, meaning key holders sending keys must verify their e-mail addresses by responding to an e-mail before the key is published. |
| pgp.mit.edu | MIT Public Key Server. Do not use this keyserver. The OpenPGP community recommends against using it because the server does not reliably synchronize with other servers. |
Sam accepts a plate of tiramisu from the flight attendant and says, “Bob, let’s take a break here, and have some of this delicious dessert!”
“Yes,” replies Bob, “after cake, you can explain to me about key revocation.”
“Key revocation, coming right up--but before that, a quick general overview on how to edit a key,” says Sam.
1Key ID here is optional, if left off, GnuPG returns fingerprints for all keys on your keyring.
2The last 8 bytes of the fingerprint form the short key ID, the last 16 bytes are the long key ID.
3A collision happens when two different public keys have the same key ID; people have demonstrated methods of generating key ID collisions in OpenPGP keys, so careful users prefer the “long” 16-byte key IDs. Fingerprint collisions, while theoretically possible, have not yet been demonstrated to be practical. See http://www.asheesh.org/note/debian/short-key-ids-are-bad-news.html
4This is the default value set in the GnuPG configuration file, gpg.conf, but you may enter a particular keyserver if desired.
5The software many keyservers run is called SKS (“Synchronizing Key Server”), and GnuPG’s default keyserver, keys.gnupg.net, is an alias for pool.sks-keyservers.net which is a pool of keyservers that are active, are updated to the required minimum version of the software, and that are correctly synchronizing with the rest of the network to update keys. For more about keyservers, see http://crypto.loshin.com/?p=1025.
6Actually, it identifies the key ID you enter as a hexadecimal value, meaning it is a number in base 16 containing the numerals 0 through 9 plus the letters A through F which represent the numbers 10 through 16. Don’t worry too much about it, just don’t forget to use the prefix when searching on a keyserver.
7This file is called gpg.conf and should be located in the GnuPG installation directory.
8The string should be a complete e-mail address, or a complete name: a search on “wobbl” will fail, while “wobble” will return a selection of matches.
