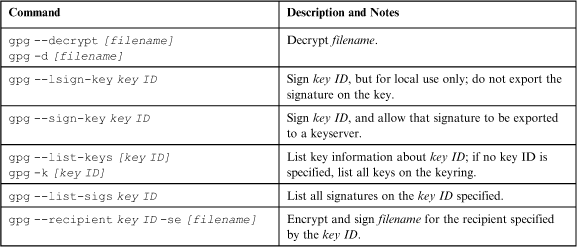
Public Key Functions
Sam, allowing Bob some time to ponder the implications of his new situation, expects Bob not just to understand how much trouble he’s in, but also to accept that he is no longer the master of his own fate. But mostly, Sam wants Bob to allow himself the possibility of a happy ending--if he can follow instructions. To imagine that there may be a carrot hidden somewhere in this new scenario, something--anything--to motivate beyond the stick that Sam believes he now holds over Bob’s head.
Sam waits for 10 minutes before returning to his seat.
“Relax, Mr. Wobble. To be sure we all understand what’s going on here, why don’t you tell me what you’ve figured out, and I’ll correct you when you’re wrong. OK?”
“Yes, of course.” Bob responds, the image of reason. He’d realized what was happening even before Sam had stood up. “It’s about using GnuPG. You sniffed me, a Sylvanian physicist in Boston for a conference, downloading software ordinarily forbidden in Sylvania. You know my wife Eve is director of Computer Technology Division for Sylvanian Security Service (SSS). Also of course, you know about my acquaintance with young girl of name Alice.”
Sam nods, and asks, “And?”
“And, you are a spy. CIA, perhaps?” Bob asks, and Sam nods again as Bob wonders whether it even matters for whom Sam works.
Bob continues, “You want me to work for you, as a spy. I’m a scientist, I have information, I can get more from wife if I snoop on her. If I do not, you turn me over to SSS with proof I’ve written a protest essay and used cryptography, which could put me in Sylvanian prison for 20 years. As a rational person, I would not like to go to prison.”
“You tricked me into turning thought crimes into actual crimes: by downloading and using GnuPG, and by writing a protest essay. I’ve taken risks, so, you believe it is my great good fortune to be caught by CIA, not SSS.” Bob continues: “What is going on now, I think, is you are teaching me to protect myself with GnuPG while I conduct my treasonous acts.”
Sam nods once more, and Bob says, “OK, Sam, let us continue please. I’m ready.”
4.1 Decrypting and Verifying
“Check your e-mail, Bob, and you’ll find that message from me I mentioned earlier; it’s been encrypted with your public key, and I’ve signed it with my public key. Your task now is to decrypt the message and verify the signature. What do you do, and why?”
Bob opens his Gmail account and finds the new message from Sam. In it is an ASCII-armored block of text. Bob says: “First, I highlight and copy the message block, and,” a pause, and with less certainty, “then, I decrypt, and then I verify?”
“Close,” says Sam, “but it’s easier than that. If a ciphertext is encrypted and signed, GnuPG decrypts and automatically verifies the signature without any extra commands. Try it; just gpg --decrypt and paste the message.” Bob starts typing, pasting in the PGP block after entering the command:

Sam taps on Bob’s laptop. “Now it might get a little messy, because you may get a dialog box prompting for a passphrase before you finish entering the ciphertext, which you’ve got to do by entering the ‘end-of-file’ sequence. So, enter the passphrase, then <Enter> and <Ctrl-d>,” says Sam. “That’s for OS X/Linux; on Windows it’s <Enter>, then <Ctrl-z>, then <Enter> again.”
“Sam, this is very annoying and complicated. Is there not an easier way?”
Sam thinks it over. “Actually, there are a couple of things you can do. You could get a plug-in for your browser or e-mail client, it will let you highlight ASCII-armored text and use a dropdown menu to decrypt or validate it. Best to look for a good one that meets your needs after you learn more about GnuPG at the command line.”
Sam pauses, “The other solution it to dump the ciphertext into a file. GnuPG handles files very nicely at the command line. If you use a thumb drive and you can hide it well when you’re not using it, you should be OK. But remember to securely erase anything incriminating on that drive.”
“I see,” said Bob, “but explain to me why this stupid dialog box keeps popping up? Why not just prompt me at the command line. It’s so confusing.”
4.1.1 Pinentry Dialog Box and RAM Caching
“Good question, Bob. Pinentry is a collection of GUI dialog programs that GnuPG uses to accept input of passphrases (and PINs, thus the name). Pinentry makes entering passphrases more secure because it is more difficult to run a brute-force attack, and you can use some versions of Pinentry to manage how long a passphrase is kept in memory.”
Sam continues: “When you enter a passphrase, it has to go into the system’s working memory1--there’s no other way to get it from you to GnuPG. The big question is, how long will that passphrase stay in memory? For greater security, I want it to be forgotten immediately--but that can be annoying and inconvenient, especially if I have several tasks to complete that require my passphrase, like encrypting or signing a bunch of different files.”
“Some versions of Pinentry give me the option of specifying how long to cache a passphrase (my Linux version does this; Mac and Windows versions aren’t as nice). Also, there are variables I can set in my GnuPG configuration file to change the time-to-live of the cache2.”
“If my passphrase is cached in memory I must never walk away from a logged-in terminal session: anyone could walk up and decrypt all of my ciphertexts without entering a passphrase; if they’ve got software that can copy the contents of the system memory, they could even actually discover my passphrase!” Sam waits to see if Bob is getting this; then goes on, “For now, remember to close all GnuPG terminal sessions, quit out of the terminal program, and shut your computer down when you’re not using it.”
Bob asks, “Shut down? Power off, or can I go to hibernate or sleep mode?”
“No! Even if you lock your screen, there are ways to grab keys and passphrases out of RAM. Shut it down!” Sam says. “Bob, here’s my advice”:
Clear your system memory by powering down after GnuPG sessions. Unlike disk storage, system RAM is cleared out when the system is powered down. And if you use sleep mode, your system is just writing what’s in RAM to a file on your disk--pretty easy to break you passphrases that way.
Use Linux. I know, Linux is supposedly more complicated, but it’s also more predictable for command line issues than OS X or Windows. Also, GnuPG and related software usually works best on Linux.
Run GnuPG from a LiveBoot version of Linux. Using a “LiveBoot” version of Linux--one that boots directly from a DVD or a thumb drive3--and you can do what you want without leaving any trace on your system drives.
“Let’s get back to work. I’ll show you how to work with files.”
4.1.2 Storing ASCII-Armored Text in a File
Sam points to Bob’s computer and says, “Let’s work with that ciphertext block in a file. Open a text editor4--not a word processor--paste the ciphertext into a new file and save it with an.asc extension, try using bob.txt.asc. Then try decrypting it as a file.” Bob opens TextEdit (he uses OS X) and does as Sam says, then enters the command (and passphrase when prompted):
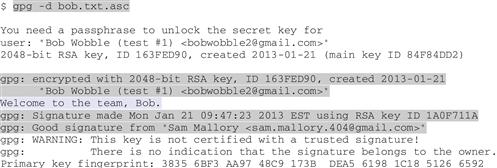
Sam says, “Look what happens: first GnuPG prompts you for your passphrase to unlock your secret key (actually, private key of the public key pair); then it decrypts and outputs the message to the screen (‘Welcome to the team, Bob’); then it reports a good signature from me,” says Sam. “This is fine for plaintext that is actual plain text (that is, letters and numbers), but if the original file was a binary file--an image or video--you would need to write the decrypted output into a file.”
Before Bob can get his question out, Sam adds, “Oh, about that warning? It’s one of the coolest things about the OpenPGP protocol.” Sam says as he sips amber liquid from a tumbler that has recently appeared on his tray table. Scotch, probably, thinks Bob.
4.2 Web of Trust
“Back in the early days of the Internet, people did amazing things by turning traditional models upside down. Instead of using servers to host information for dumb clients, the Internet let computers interact as peers. Instead of storing databases centrally, people started using the Internet to distribute database functions.” Bob sips and continues:
“Think of each OpenPGP key pair as a record in a distributed database. Each ‘record’, stored on the key holder’s computer, includes the public key, name and e-mail address, key ID, key creation and expiration dates, and so on. With no central authority to dispense certainty about key registrants (let’s call it ‘trust’), how do you trust a key holder unless you’ve met in person and have checked each other’s picture ID?” Bob starts to think about it, but Sam goes on:
“It’s one of the biggest problems with public key encryption: how do you trust the public key you’re looking at belongs to the person who claims it. Am I who I say I am? Anyone can generate a key that says their name is Sam Mallory--so how can you trust me when I claim to be Sam Mallory?”
“Sam, you are getting very philosophical. What does this mean?” asks Bob.
“What it means is that instead of requiring a central certification authority of some kind, for people to register their names and public keys with, Phil Zimmermann figured back in 1992 that it would be a good idea to have individuals sign each other’s keys when they have some proof of the person’s identity.” Sam points to the laptop again and says:
![]()
“Did you see those last three lines there? The digital signature checked out, and it says that Sam Mallory, me, signed it--but these three lines tell you that GnuPG thinks you have no reason to believe that the ‘signature belongs to the owner’.”
Slamming down his drink, Sam turns to Bob and says, “Listen, right now I’m here to tell you that that is my public key; the fact we’re sitting here having this conversation should be enough for you to trust me. So you will sign off on my key (which I’ll show you in a minute). But for anyone else, you’re going to need to check credentials like passport or drivers license, at least, before you trust the signature. Got that?”
“Sure. If you sign someone’s public key, I should trust that key, too?” asks Bob.
“You trust it if I tell you to trust it--and don’t trust any key that hasn’t been signed by me,” replies Sam. “Listen, the web of trust idea is pretty cool, it’s just not really taken off in the same way that, say, Facebook has taken off with users. It’s kind of like LinkedIn5 in how it gives you access to other people’s networks. But with web of trust, you’re certifying how trustworthy you judge someone to be. If it’s a stranger whose passport you’ve checked, that’s one thing--but if it’s your cousin or lifelong friend or long-time work buddy and you check their passport, you might give that person’s key a higher level of certification; if you’re confident they are serious about security, you might even trust other people who they trust.”
“But, as cool as the web of trust is, some people never bother with it. You can still use GnuPG without thinking about web of trust--it’s easy if you don’t have many keys and get them mostly in person. Or else if you keep in mind that using a key you pulled off some web site may or may not be the key for the person it purports to be.” Sam pauses, then says, “Just remember to be careful about who you trust, and whose keys you trust.”
4.2.1 Signing a Key
Sam says, “Time to sign my key.” Bob starts with gpg -h to see if he can figure it out. “Should I use gpg --lsign-key or gpg --sign-key?” he asks.
Sam says, “Excellent question. GnuPG help isn’t very helpful here. It says --lsign-key is to ‘sign a key locally’ and --sign-key is ‘sign a key’. The difference is that signing a key is a big deal: it means that you’re announcing that you’ve determined the key holder is who she says she is. You’re announcing, ‘I trust this person’s key’.”
“If you weren’t doing spying for us, Bob, I’d say, don’t worry about it. But since you are spying for us, I’m going to suggest you stay away from making public announcements about anyone’s keys. OK?” Sam continues:
“So, you use the --lsign-key command when you want to note that you trust a key, you just don’t want to allow your signature to be exported off the local computer. Regular users use that option when they have someone’s key, and they think it’s probably fine but they just haven’t gotten around to verifying it yet. Otherwise, the --sign-key option is for when you’re ready to take a position on someone’s public key, and don’t mind having your opinion propagate around the Internet.”
“So, sign my key locally. There’s no need for you to start emitting information about who your friends are or who you know. I know I talked about that web of trust, but in this situation you probably don’t want to leave too many digital footprints.”
Bob signs Sam’s public key, locally. “First, I need to find your key ID, so I command GnuPG to list all my keys, and then I copy the key ID for your key”:
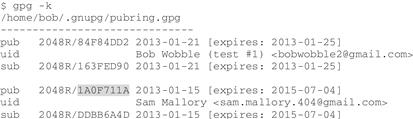
Sam points to the short list and says, “You’ve only got two keys in your keyring, so it’s not a big deal, but you could also command GnuPG to list keys that match ‘Sam’, by using the command gpg -k Sam.” Bob tries it, and says, “That’s good to know. Does that trick work for other commands?”
“GnuPG is pretty good about letting you specify what you want. So if you want to list out keys or fingerprints, you can specify a string that should be in the name or e-mail address. For instance, if you want to see all keys that have ‘gmail’ in them, you can do that,” says Sam. “You can also specify more than one key ID in a single command. So what next?”
Bob says, “I have your key ID, now I want to sign it, locally, so:”
![]()
“And GnuPG lists out all this information about the key I want to sign, to make sure”:
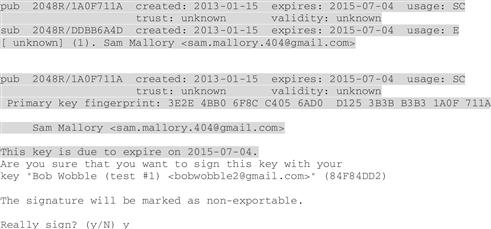
“I enter y to ‘really’ sign the key,” says Bob, “and, voila”:
![]()
“So I enter my passphrase, and…” Bob enters his passphrase in the pinentry dialog box, “…and, I’m back to the command prompt. Do I have to list my keys to see what happened and check that the signature is there?”
“No, actually, listing the keys won’t show you the signatures on the keys.” Sam says, “There’s a different command to list key signatures…”
Bob, scanning the GnuPG help listing again, finds it: “--list-sigs, right?”
Sam says, “Right. And that’s one of the commands that gives you the option to specify a particular key you want, or that will give you information on all your keys if you leave the key ID out. For one key, enter the command with the key ID you want to see.”
“Do I need to use that prefix for the key ID? You know, the 0x before the key ID number?”Bob asks.
“No, you don’t need to do that; you can also use a user name or e-mail address,” answers Sam, as Bob complies:
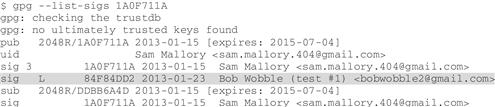
“Your signature shows up on my key now,” says Sam. “See that letter L there? That’s to remind you that your signature on my key is local. The number 3 on the line above it is part of my own signature on my own key, 3 means fully trusted6. By default, GnuPG signs your own key when you create it, for security: if you didn’t sign your own key, someone else could put a signature that looks like yours but is actually their own, and that’s how someone could hijack your key. But that shouldn’t ever happen these days, as GnuPG automatically signs your key for you when you generate it.”
4.3 Encrypt and Sign
Sam asks, “Bob, how about you encrypt and sign a binary file to send to me? Do you have any pictures from your trip you’d like to share?” asks Sam.
“How about a photo of the secret biology lab I was shown when I visited Menotomy University? I tell GnuPG to encrypt and sign file bio_lab.jpg, for recipient ‘Sam Mallory’. Do I need to specify an output file?” Bob asks.
“You can specify an output filename if you like, but by default the encrypted file will be the plaintext file plus the extension.gpg; that’s for binary files. For ASCII-armored ones, the default extension is.asc,” says Sam. He adds, “Oh, and you’ll probably forget this, but if you encrypt files in other directories and you want to specify an output file, you’ve got to specify the entire filename plus directory path. If you don’t, the output file gets written to whatever directory you’re currently working in--not the same directory where the plaintext file is. So using the default file naming option might be a good thing, most of the time.”
Bob starts typing:
![]()
Sam stops Bob before he hits <Enter>: “That will work fine, also using the key ID would be a good idea, just in case you had more than one key for me. Like this”:
![]()
“They’re both ways to tell GnuPG to sign and encrypt the file bio_lab.jpg for recipient ‘Sam Mallory’ (key ID ddbb6a4d); then, when it finishes, you can check the directory (use ls -l bio_lab.* command to get a listing in OS X or Linux, dir bio_lab.* for Windows) to see listings for plaintext and ciphertext versions of that file.”
Bob says, “I can encrypt and decrypt, even sign things. I understand how to use the options. If an option needs a value, like the --recipient option, I need a key ID or other identifier; if --output option, I need a filename.”
Sam, nodding, says, “Now, send me the file, and I’ll decrypt and verify it, and we can talk about what digital signatures are good for.”
4.4 Benefits of Digital Signatures
Sam says, “We expect you to exercise extreme caution when communicating: authenticating our messages, and making sure your messages are verifiable.”
“But why? Isn’t it enough to get a message encrypted with your own key, which you gave to me personally?” asks Bob. “What does signing it do?”
“Digital signature does three things: first, it identifies you as the person who signed the message: that’s authentication. Second, it guarantees that the message I receive is the same message you signed, unmodified in transit: that’s integrity. Third, having signed a plaintext, that signature is an undeniable proof: you cannot deny you signed it. That’s non-repudiation.” Sam recites. “When we send you instructions, you’ll probably be interested to know whether we sent them or someone less agreeable. Likewise, you’ll want to know the instructions you’ve received are complete and unchanged in any way from what we sent.”
“So, how am I going to use signatures, then?” asks Bob.
Sam answers, slowly: “When you send me a message, encrypt and sign it. When you send me a file, encrypt and sign it. When I send you a file or message, decrypt it and verify the signature. Verify it means being certain to read the messages that GnuPG returns after it decrypts.”
“OK,” says Bob, with a hint of uncertainty. “That seems simple?”
Sam, noting Bob’s uncertainty, says, “Yes, it seems simple, and it is simple, if you follow the rules. We’re going to set up a cover story for you, in case you are discovered passing encrypted messages back and forth between the United States and Sylvania, so you won’t automatically be considered a traitor, especially by your wife. We’ll also set up some duress codes for you, so if you’re detected you can signal me without tipping off the SSS--or your wife.”
“Cover story?” asks Bob.
“Yes,” Sam says: “Yours will be that you’re carrying on with Alice, that sweet graduate student at Menotomy University. It doesn’t matter that you feel only innocent, paternal feelings toward her. Would you rather your wife suspect you of being an old fool and committing adultery or that you’re a traitor?”
Bob nods, unhappily. He’d rather not be suspected of anything, but that train has left the station. Sam continues:
“A duress code is something you say or do that isn’t obvious, but that signals you can no longer trust that your message is secure. It might be as simple as including a certain word in every message, and omitting that word when security has been breached. For instance, you might start normal messages with ‘Dear Alice’, but use something else, like, ‘Hi cupcake!’ if your activities are exposed. It could be even more subtle, like using different punctuation or a misspelled word. We’ll work out the details before we land, don’t worry about that. Meanwhile, let’s take a little break--it’s time for lunch!” With that, a flight attendant arrives to ask the two whether they would prefer steak or lobster--or both.
Bob sips his drink and clicks a link to a cat video his wife “Liked” on Facebook. “Oh what a silly kitty, that’s your own tail!” Bob thinks to himself, “And perhaps there is a way out of this situation that doesn’t end with bread and water and a cell for me.” Bob opens a message window, and begins composing to his wife:
Dearest cupcakes: Am having great flight, all praise to the Leader. What an adorable kitty! You know how much I love cats! Cannot wait to see our kitty Walter--if only you could bring him to the airport when you come to get me.
“I wonder if Sam knows I’m allergic to cats,” Bob ponders, as he clicks “Send.”
4.6 Review Questions
1. What proof of identity has Sam Mallory offered to Bob? Should Bob trust him?
2. Make a list of all the GnuPG commands and options that Bob has learned so far.
3. Web of trust is one way to distribute trust in public keys; see how it differs from the other option, certificate authority. Which is more commonly used? Why?
4. In what ways could Bob’s message be modified to contain impromptu duress codes?
1That is, the system’s Random Access Memory (RAM).
2See “Managing shell command history in OS X/Linux” (http://crypto.loshin.com/?p=1013).
3See http://www.ubuntu.com/download/help/try-ubuntu-before-you-install for an example.
4Good open source text editors include Gedit, Emacs, and Vim; versions are available for most OSes. Notepad is included with Windows; TextEdit with OS X.
5See http://linkedin.com for more about how LinkedIn works.
6See “GnuPG Signature Flags” at http://crypto.loshin.com/?p=987 for more details.