Chapter 2. The Mobile Money Ecosystem
When a new startup sets out to build some revolutionary mobile payment app, the possibilities appear to be endless, prompting visions of happy users gliding through checkout lines with nothing but a wave of the phone and a jaunty tip of the hat. No paper receipt for me, thank you! Users will surely toss their plastic debit cards into a lake. A paradigm shift!
Yet the reality is that a mobile payment experience lives and breathes by the technological ecosystem that it is built upon. As with any digital experience, the ever dark and mysterious “backend system” can make or break your app, regardless of how usable and slick your UI might be or how many user personas you research and compose. If the cashier at the store can’t see your customers check in on their point-of-sale (POS) app, or the register’s near-field communication (NFC) reader doesn’t “beep,” then your users may be left red-faced and fumbling for that plastic card you’ve worked so hard to advance them away from.
End users could not possibly understand (or care) how payments technologies work behind the scenes; they expect only that this app will make their lives easier by expediting payments or helping them save money. They want to be assured that the app is maintaining their financial privacy and allowing them to keep track of their spending. Mobile apps in the financial space are rarely known for elegant interfaces, and this is often attributed to technical architecture challenges and lack of institutional agility. It is in your best interest as a product designer to understand the technology underlying any digital experience, so that you can anticipate any limitations or UX pain points that may occur. Unexpected latencies or loss in network connectivity to the phone, if not handled with appropriate messaging and alternate flows, can mar an otherwise gracefully designed app. In this chapter, we’ll take a look at the most common technology approaches, with particular attention to the UX benefits and shortcomings of each (see Table 2-1).
Benefits | Challenges | Examples | |
NFC | Transaction speed, secure storage of card data, no need for data network, can be wiped remotely | Complex ecosystem, lack of merchant acceptance in some markets | Isis, Google Wallet |
Cloud | Works on most devices and OSes, variety of redemption methods (QR/barcode, geolocation) | Dependence on data networks, lack of security standards, higher processing costs for merchants means less acceptance | PayPal, LevelUp |
Closed loop | Works on most devices and OSes, less risk for consumers, uses existing merchant POS accessories, often tied to rewards programs | Accepted only by sponsoring merchant; if linked to a debit/credit card as funding source, can be a security risk | Starbucks, Dunkin Donuts |
Payment Framework Types
As Table 2-1 outlines, there are generally three types of payment frameworks that a mobile wallet or payment app may be built upon: NFC, cloud, or closed loop systems. The chosen route often depends on who is building it, and how she envisions her POS experience playing out. NFC is favored by issuers and mobile networks due to its high grade of security and risk management processes. Independent startups favor cloud-based wallets and usually go with linking their users’ cards with a cloud-based service and using data connectivity, geolocation, or QR (quick response) codes/barcodes to transact. Merchants tend to choose closed loop systems so as to favor their own stored-value or reloadable gift card systems as the primary funding source.
These three ecosystems—NFC, cloud wallets, and closed loop—can even work together in the same wallet, enabling a versatile mobile wallet that is easier to distribute to different device platforms (for examples of the interplay of the three methods, please see Chapter 7). Each ecosystem may have its own benefits and drawbacks, so developers must weigh the cost of each approach and choose the one that would be best for them.
NFC Payment Apps
NFC (Figure 2-1) is like many other wireless communication standards, such as Bluetooth or RFID (radio frequency identification), allowing two objects to exchange tiny packets of data. While Bluetooth or RFID can work when objects are several feet away from each other, NFC is more intimate—with a range usually around a centimeter. It can be used for all sorts of mobile use cases: sharing photos between friends, tapping a poster to get promotional media downloads, or reading a transit card to get the current balance.
An NFC payment at the register typically relies on three key components: the NFC antenna of a mobile phone, a tamper-resistant secure element (a smart chip where the user’s card data is protected according to EMV[33] standards) somewhere inside that phone,[34] and a contactless NFC reader accessory at the store’s point of sale. A consumer with an NFC-enabled device can walk into any store that supports contactless payments and tap his phone on the reader to pay. To the merchant, it appears as if the user had swiped his card as usual (or entered a chip and PIN card, as customary outside the US).
NFC is now present in over 125 million mobile devices around the world.[35] It allows two devices (in this case, a phone and a POS reader), within an inch or so from each other, to exchange data. This electromagnetic conversation between the reader and the phone lasts half a second, during which time the POS reader retrieves data from the secure chip inside the phone. It’s the same encrypted data that is written onto the magnetic stripe of your old plastic card, but with extra data and cryptograms added to the end of it that can have a lifecycle of validity.
The user experience of an NFC payment works like this: when the consumer approaches a payment terminal to check out, she opens up her app, enters a PIN, and, when she is ready to pay, taps a Pay button or just holds her phone over the reader. Alternately, she could just hold her phone over the POS reader without opening the app. These tapping interactions vary depending on the mobile contactless specification being used—that is, functional requirements dictated by Visa payWave, MasterCard PayPass, American Express ExpressPay, and Discover Zip—as well as how the issuing bank has mandated that its card product be presented at the point of sale. The POS reader alerts the consumer and the merchant with a loud beep, the consumer’s phone vibrates or shows a confirmation message of some sort, and the transaction’s done!
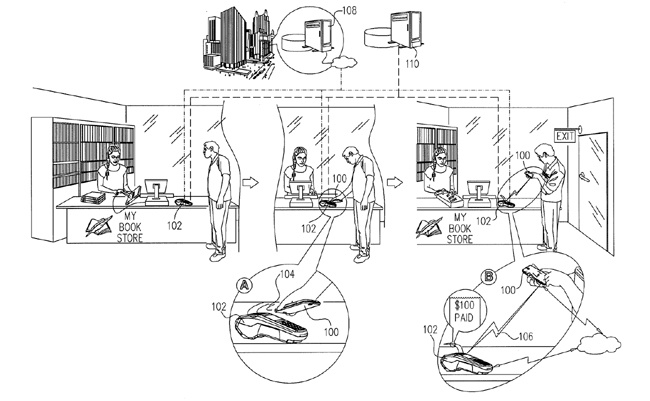
In Figure 2-2 you can see an illustration of a typical mobile NFC transaction and the communication back and forth from the ecosystem, taken from a contactless reader patent for Verifone, a manufacturer of retail checkout systems.[36] At point A, the user has tapped the phone on the reader to complete a purchase at a bookstore. At point B, the reader shows that the purchase was successful, and the amount. Further data from the purchase (name of the merchant, time and date, anything you might see on a paper receipt) can be sent to the user’s phone once the transaction travels through the traditional payment networks.
Although NFC (sometimes called mobile contactless) is well regulated and widely used in places like South Korea on public transit and vending machines, it has struggled to take off in other markets like the US and the UK.[37] This can be attributed to several factors, such as device availability and merchant acceptance, but it is primarily due to the complex and fragmented NFC infrastructure that makes these types of transactions possible.
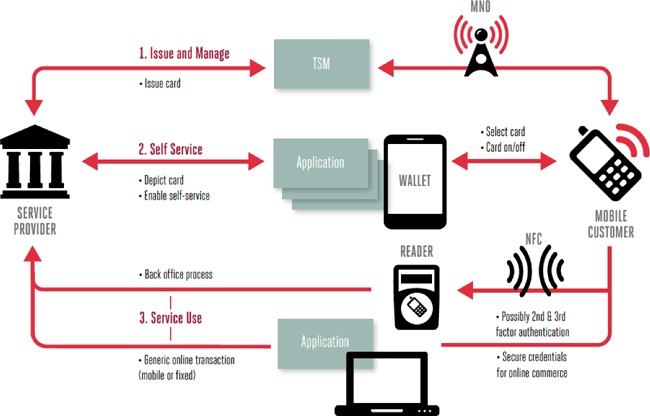
In Figure 2-3, you can see three parties working in concert to enable NFC payments on a phone. The essential players include the mobile network operator (MNO), a trusted service manager (TSM), and a service provider (could be a bank, merchant, or transit authority). In wallets like Isis, where multiple banks are involved, this ecosystem gets a bit more complex, with multiple TSMs and service providers.
- MNO
Grants over-the-air access of its SIM card to the TSM so that it can install (and later remove) the bank customer’s card data, which is usually contained in a small Java applet that only one wallet app can use.
- TSM
Works on behalf of the bank to securely install and manage the card data on the device via the mobile data network.
- Bank or issuer
Issues the card to the customer, and dictates how that card data can be used in the mobile context.
- Service provider
Controls the user experience and facilitates communication between the bank, the MNO, and the customer. In some cases, the service provider and the bank are one and the same, as banks are beginning to incorporate NFC payments as part of their mobile banking apps.
In the last two years, there have been a handful of successful NFC pilots in various countries, prompted by collaborations between device manufacturers, banks, and telcos...and supported by the major payment networks such as Visa and MasterCard.
At the London 2012 Olympics Village, only Visa cards or cash could be used to make a purchase, and every terminal was enabled for contactless payments. In all, 726 Visa staff, partners, Visa-sponsored athletes, and journalists were issued Samsung Galaxy SIII NFC phones equipped with a Visa payWave mobile app (Figure 2-4). They processed an average of 15 transactions each using their phones. After the event, Visa confirmed that 150,000 payments at games venues were made using the technology. That’s 15% of all card payments, and most were at a value of £20 and under.
Here in the United States, U.S. Bank conducted two rounds of pilots (one in 2010 and 2013), providing pilot participants with iPhones equipped with a special case (between $20 and $50) that had an NFC antenna built in, plus a microSD to store their card data. Though the users enjoyed the speed of transactions and the futuristic “coolness” of tapping a phone to buy something, they balked at the unwieldy case accessory that was used in the pilot to power the iPhones with NFC. Our phones are very personal objects, and it can be a real showstopper if any newfangled gadget negatively affects how we use them for other purposes, like decreased battery life or unwanted bulk.
In Austin and Salt Lake City in late 2013, a consortium of US carriers called Isis operated an NFC pilot where users could tap phones to make payments and redeem local offers. Isis launched to the rest of the country in November 2013. Though initially mired by delayed release dates and an awkward user interface, Isis is certainly an unprecedented alignment between competing carriers in a concerted effort to advance the NFC ecosystem in the US. We’ll take a closer look at the user experience of Google Wallet and Isis in Chapter 3.
Benefits
The primary benefit of the NFC ecosystem is consumer peace of mind, in terms of security. NFC payments are the most secure form of mobile transacting, requiring users to hold their phones very close to the reader in order to make a payment (see Figure 2-5). It uses powerful bank-grade security constructs, such as the smart chip on the device (which is nearly impossible for hackers to crack compared with apps that store the consumer’s card data at the OS level or in a cloud service) plus secure over-the-air data connections, multifactor authentication,[39] and PIN codes to bar any malicious use of the app. If a user loses her phone, one call to the bank or the service provider sets the ecosystem in motion to either block a stolen phone from making unauthorized payments, or remove the payment functionality entirely.
Likewise, studies have shown that consumers are more likely to trust a mobile payment application if it is associated with their financial institution. In the chart shown in Figure 2-6, you can see that financial institutions like card networks and banks clearly win out over tech companies like Google or Apple and mobile network operators like Verizon or AT&T.
Secondly, the speed of an NFC transaction itself makes dealing with cash look resolutely Stone Age; some apps allow you tap and pay without opening the app at all (usually for low-value transactions or intransit scenarios). The act of tapping an NFC device feels more natural to some users, as opposed to trying to properly align a barcode or a QR code to a scanner (which has to be an optical scanner, as the lasers of more common scanners will just bounce off the phone’s glass screen). While it is true that adoption lags in the US compared with Canada and Brazil (which have higher penetration of NFC POS readers in retail), NFC can certainly be faster than credit cards and cash. An NFC transaction from start to finish is about a third faster than other forms of payment, as you can see in Table 2-2. The overall time it takes to pull out a leather wallet to remove a credit card, swipe it, type in a PIN, and collect a receipt from the cashier can be around 45 seconds, give or take (go ahead—time yourself!). An NFC payment, if you already have your phone out (which you probably did while you were bored and waiting in line) generally takes around 12 seconds. The additional second or two for the cashier to give you a receipt is also stripped away, as the app can now give you a fairly complete transaction record.
Payment method | Time (seconds) |
Checks | 64 |
Credit/debit | 48.5 |
PIN debit | 44.4 |
Cash | 28.5 |
NFC | 12.5 |
[a] Nick Holland, “Contactless Payments and NFC in the United States: Beyond Science Fiction,” Aite Group, LLC, January 30, 2008 (http://bit.ly/1oetF1s). | |
Other benefits are the ability to pay even when there is no data network (like inside a big-box retail store where phone signals are diminished) because the system is built upon existing settlement and processing rails that we use every day with plastic cards. The system’s interoperability with loyalty cards, transit ticketing, government identification, and building access/keyed entry makes it the primary contender for replacing all the uses of the old leather wallet.
Challenges
Critics of NFC question whether the technology will ever reach wide use, citing the lack of merchant acceptance, and that it doesn’t truly save time at the register when compared with using a debit card or cash. Unfortunately, all the planets of the NFC ecosystem must align before the consumer can download the app and find a shop with a compatible reader. An initiative like Isis[40]—a rare joint venture of the three largest mobile carriers in the US (AT&T, Verizon, and T-Mobile) whose participants include card issuers like Wells Fargo and American Express—takes an immense amount of coordination and relationship building, which can be a lengthy investment of time. Countries like South Korea and Japan have had success with this system, because it was generally lorded over by individual mobile networks or device manufacturers. Consortiums like these were a key element to getting this form of payment into the hands of consumers. The nuanced interplay of these parties has a noticeable influence on consumer experience, especially during the first use, when the user is setting up his phone for payments and downloading his card data.
For example, with some NFC apps, after the user downloads the app and registers, it may take anywhere from 30 seconds to 12 hours until the bank authorizes the TSM to install the user’s card on the device. Designers would have to consider how to communicate to users that they must wait for a significant amount of time until their phones are ready to tap. Communication during the activation process must be transparent and reassuring, without overwhelming users with technical jargon. Any ambiguity during the onboarding process tends to make a bad first impression.
Another challenge is feedback in the form of information that can be shown to the user after the transaction is complete—essentially taking the place of a receipt. In some markets, the contactless readers at the register may not provide the app with complete transaction data when users tap their phones, such as the purchase amount or currency; they may send back only a vague “transaction data received” response, which can be somewhat confusing to consumers, causing them to rely on more traditional stimuli: a nod from the cashier and a beep from the POS to tell them the transaction was approved.
Merchant acceptance is always a challenge for mobile payment apps, and NFC is no exception (though it is the most widely accepted). The number of NFC-enabled points of sale varies from region to region. Places like Canada, France, Brazil, and Poland have contactless readers in every corner shop and taxi, whereas as of June 2013 there were only 500,000+ readers in the US. This number may grow within the next few years, thanks to the payment networks (Visa, MasterCard, American Express, etc.) adjusting their risk liability policies to place more responsibility on the merchants for fraudulent purchases, which would be reduced by EMV cards like the ones used for NFC. The burden will soon be on merchants to make sure their POS systems are upgraded with the latest accessories. But for now, just over 7% of the 7 million retail stores in the US accept NFC.
Another frustrating challenge to implementing an NFC payment app, and one that designers and developers typically have little to no influence over, is overall awareness. This does not apply just to potential users being aware of the service and its benefits (which is why we hire marketing folks). Consumer awareness is relatively easy to get a handle on, as more NFC-enabled devices are released into the market and users become more accustomed to using NFC to share pictures or check in at their favorite venues. A clear, strong marketing campaign combined with a successful user experience will help uneasy users feel more comfortable using their phones in this way.
But once the reader is up and running, a store may or may not have properly trained its staff in how it all works, prompting blank looks from the cashier if the customer has any trouble tapping her phone. Sometimes this kind of training is just not a priority, given how few NFC users are out there relative to people paying with cash or cards. More than a few times, I’ve pulled out my Google Wallet or Isis Wallet on my NFC-enabled Android phone at my local Whole Foods, only to find the employees had helpfully covered up their contactless reader pads with a placard plugging the weekly sales promotion or marketing (see Figure 2-7). Even if your favorite coffee shop does have a compatible reader, it must be correctly configured and in good working condition to accept a tap (from any contactless form factor, be it a phone or a card or a keyfob).
Cloud
Storage “in the cloud” is a technology buzz phrase that has found its way into the payments world. Our documents and personal content are now readily available from any web-connected device, to use when and where we need them. Along these lines, in Chapter 1 we saw money become less tangible, and now thanks to mobile devices we can access our money from anywhere.
Considered by some to be the most efficient ecosystem, cloud-based payments require much less infrastructural heavy lifting than the NFC ecosystem does. A customer enrolls his card with a secure web service, and any payments made using a mobile device are charged back to that funding source. Sensitive card data is (hopefully) never stored on the phone. Instead, transactions are facilitated by the scanning of barcodes and QR codes in store (LevelUp), prepaying for a purchase from the consumer’s device and picking it up (Square Order), or using geolocation to verify that an eligible consumer is present (PayPal Here).
The pioneer of this system as it began on the Web is PayPal, so it has the most users (15% of all mobile users as of this writing[41]), but scores of startups have now entered the fray. According to the Payments category on Angel List, there’s around 1,100 and counting! In the case of the LevelUp app (shown in Figure 2-8), users present a tokenized QR code at a participating merchant, which then charges their linked funding source. The merchant simply scans the QR code with its proprietary LevelUp scanner, attached to a point of sale (LevelUp also has apps for merchants). The reader beeps, and a few seconds later, the user gets an electronic receipt. LevelUp also ties in rewards for frequent shoppers, so they can rack up discounts.
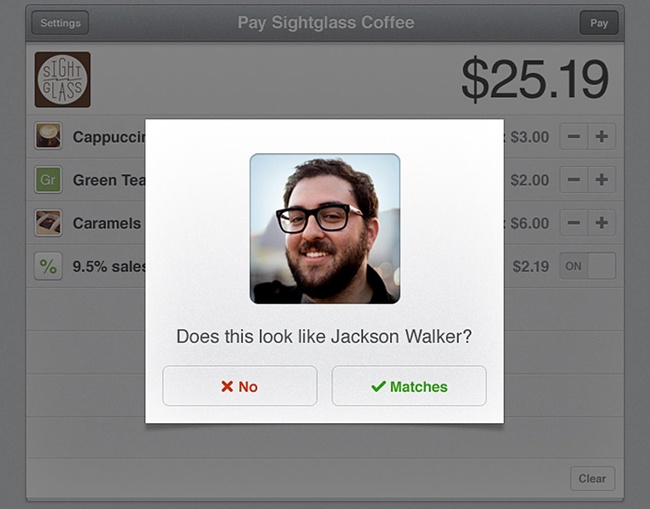
Rather than be tied to any single payment interaction, PayPal tries more of a “Swiss Army knife” approach in an effort to maximize the number of compatible merchants available to the user. PayPal incorporates as many payment methods as possible, including remote ordering, entering a phone number and PIN at the point of sale, using geolocation- triggered check-in, and even using Bluetooth Low Energy beacons (see Figure 2-9). The geolocation payment is especially forward-thinking. When a user is within several feet of a store, she can “check in,” and her name and face pops up on the merchant’s point-of-sale app. The customer only needs to say, “I’m paying with PayPal; I’m Lucy,” and then she can grab her double latte and go.
Square is another proponent of cardless transactions via the cloud. The service was founded to rejuvenate the conventional POS and inventory system. It all started with using an elegant plastic card swiper that plugs into a phone’s audio jack. The company recently retired one of its payment products, Square Wallet, a companion to its Register app where the user could link a credit or debit card, then simply check in to his favorite merchants and give his name at checkout, where his face and name would pop up on the merchant’s Register app (Figure 2-10). It was a precursor to PayPal’s geo-check-in payment feature. Shifting gears, Square launched a new product called Square Order (shown in Figure 2-11) that allows users to place orders at nearby restaurants with an elegant ordering process and one-tap checkout. All they have to do is walk or drive down to the merchant and pick up their order.
Square and PayPal have oriented their products mostly toward making payment acceptance easier for merchants, by giving them lower processing fees and allowing them to take card payments with a card swiper accessory, and in the process upgrading the traditional “cash register”–style UI that plagues most point-of-sale systems. Ever watched a checkout cashier hunt and peck for that item you ordered? Companies like Intuit, LevelUp, and Revel are changing all of that, and passing the saved time to the store’s customers. This paradigm is especially ideal for very small businesses, like those in the world of gourmet food trucks, where being able to accept all payment types on the go equals a boost in revenue.
Benefits
Cloud wallets are an agile alternative to the complex infrastructure of NFC, with much lower barriers to entry for both users and developers. A new startup looking to enter this space need only comply with cardholder privacy rules set by the Payment Card Industry Data Security Standard (PCI DSS), established by Visa, MasterCard, American Express, JCB, and Discover to provide multiple layers of protection for handling cardholder data and conducting digital transactions. After PCI compliance and the establishment of a settlement API to process payments, it’s simply a matter of creating a user experience that will authenticate that the user: a) is who he says he is, b) has a valid card, and c) intends to initiate a payment. Registration for a new user is fairly pain-free (once he gets past the dreaded credit card form), and he can be up and running in less time than with NFC apps.
These kinds of apps are also hardware agnostic. There’s no need for users to upgrade their devices to one that is NFC ready, for example, so this approach tends to work on all the major mobile platforms (unless it involves the use of Bluetooth Low Energy beacons, which require phones to meet the latest Bluetooth specifications).
Challenges
This approach still faces the same distribution and adoption challenges that NFC wallets do, in that both rely on the merchant having compatible hardware at the register—whether it’s a laser scanner for barcodes, or a point-of-sale app that recognizes when registered customers are nearby. When it comes to revenue, merchants tend to stick with what works and aren’t often prone to experimenting with register hardware—especially if they just dropped $5,000 on a point-of-sale system.
Another hit to cloud payments is that they’re not as favorable to merchants who must work with an acquirer to process their transactions, because these acquirers typically charge higher processing fees for transactions perceived as being higher risk. Usually cloud-based payments are considered “card-not-present transactions” for which the store will incur higher fees.[42] This is in contrast to NFC payments, which act as “card-present transactions,” meaning the cardholder and the card were present at the sale, so they carry a low settlement risk.
Cloud payment apps expose the user to the most security risk, once her card data has been transported and stored on the server. Though most apps like PayPal’s allow the user to set a PIN or passcode to lock her app, the app is only as secure as the cloud server, the encryption strength of the app’s communication, and the user’s PIN selections. In a recent survey, nearly 9,000 iPhone users admitted that their screen lock code is 1234.[43] The second most popular lock code was 0000! Should a hacker eavesdrop on a user’s mobile data traffic, using methods like Wi-Fi network spoofing—that is, setting up an innocuous-looking public Wi-Fi network called “attwifi-free” or “free public Wi-Fi”—then any phone that hops onto this network (either by user choice or because the network resembles one the phone already trusts) provides a window for that hacker to see passwords and cardholder information being passed between the app and the cloud. That double latte might cost more than the user bargained for!
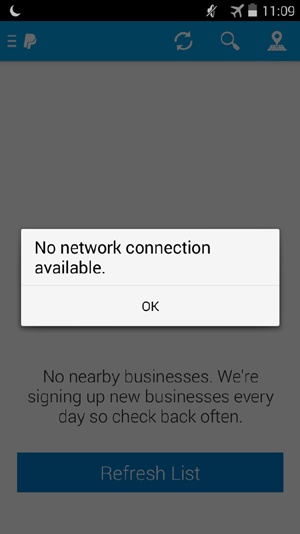
Another practical challenge here is that transactions aren’t possible when the cellular network is unreliable or Wi-Fi is unavailable (see Figure 2-12). Even when data connectivity is not an issue, there is often a perceived latency while the user waits for confirmation of the transaction in the form of a push notification, SMS, or some other form of digital receipt. Even in today’s world of lightning-fast 4G LTE networks and public Wi-Fi hotspots, just a short connectivity drop of a few bars is enough to slow or halt a cloud-based payment.
Closed Loop
Closed loop payment systems are like little jars inside a retail shop where the consumer can set aside her money for later use. They are based on stored-value cards that can be redeemed at only one merchant (like that $25 gift card for Best Buy your brother gave you for Christmas, and you forgot about it until Easter). A companion mobile app allows customers to redeem that stored value, usually by presenting a QR or barcode at the point of sale. Users can reload the card indefinitely, putting in only as much money as they intend to spend with that particular merchant, limiting the exposure of their financial details and bank accounts. This is also a great way for users to budget how much they spend on particular types of purchases, like groceries or restaurants. Merchants usually weave loyalty schemes and offers into their closed loop cards to keep their customers coming back.
The most successful examples of this system are the Starbucks and Dunkin Donuts apps (the latter is shown in Figure 2-13). Starbucks, notably, has processed 4 million payments a week since its app launched in 2011.[44] These apps also allow users to redeem loyalty points for free drinks, which keeps customers coming back in a caffeinated cycle of savings, and they are much easier than carrying around (and reloading) a clumsy plastic card. We’ll take a long look at the Starbucks app as a case study in the next two chapters.
Benefits
Closed loop apps are inherently easy to implement from an acceptance perspective, as they are usually sponsored by the merchant itself. They are especially quick to release, thanks to the use of barcodes and QR codes, which can be read by most laser scanners already attached to modern points of sale (though it’s unlikely that you’ll find them at the corner grocery store). All the checkout cashier needs to do to accept the payment is to indicate that the customer is paying with a gift card.
The user’s risk can be very low, depending on how much money he loads onto the card. These low stakes make this system a good entry point for users who want to try out mobile payments for the first time. As these cards are often tied to rewards programs, the user can also be shown a points tracker, which encourages him to earn enough points to get free items and save money on future purchases. Because it’s on a mobile device, a closed loop app that can track the balance of a store’s card is a huge improvement over the plastic version; the user won’t have to ask the merchant to swipe the card to look up the balance, or be surprised when the balance is lower than he expected. These apps are entirely device agnostic, and can be deployed on any mobile device...or even smartwatches (Figure 2-14)! They can be used even when there isn’t a data signal—a leg up on cloud-based payments.
Challenges
These experiences do need wireless connectivity to an extent, so that the user can see her current balance before she attempts to scan it at the register (lest she incur angry stares from her fellow shoppers for slowing down the checkout line). Otherwise, she is going into the purchase without knowing if she has enough funds.
Closed loops systems are just that, closed: they can be used only at one associated retailer. This clutters the user’s mobile home screen with icons of her favorite shops, as opposed to offering her “one wallet to pay them all.” There are gift card wallets, like Gyft and GoWallet, that can store cards from multiple merchants, but they won’t include rewards points and may not have balance tracking.
A minor UX challenge here is the brightness of the user’s screen and ambient light reflection. Barcode scanners can be fickle creatures, needing just the right light conditions and laser alignment for a good read. Starbucks has utilized the mobile OS to reduce scanning issues by overriding the device’s brightness setting so that the screen shines at the brightest level when the barcode is displayed.
QR codes are not standardized, so they’re vulnerable to malicious redirection or copying by scammers. 1D barcodes are standardized but are limited to 10–20 characters, which doesn’t allow them to store much data, like randomized tokens. They are both easily duplicated. If the user leaves her phone unattended while the code is displaying, someone could (in theory) grab the phone, take a screenshot, and email it to himself.
Summary
Each of these systems has its own benefits and drawbacks, and so a payments developer—whether a financial institution, mobile carrier, or startup—must choose the system that is most appropriate. Though businesses often make decisions like this by weighing revenue models, time to market, or customer ownership, in the end it is ease of use, security, and added value that drive consumer adoption.
In the next chapter, we’ll take a close look at the user experience of mobile wallets and payment apps that utilize NFC, cloud, and closed loop systems to see how these underlying technologies play out when they are implemented.
[33] Acronym for Europay, MasterCard, and Visa; they wrote the specifications for how chip cards can be used.
[34] Note that there is now the concept of tokenized locally hosted EMV card applets, which can be stored temporarily on the phone for NFC payments and periodically refreshed by the issuing bank. As of this writing, this method is available only on Android or BlackBerry devices thanks to host-card emulation. It is currently being tested by a handful of banks while awaiting certification by the payment networks (Visa, MasterCard, etc.). This method would eliminate reliance on mobile network operators for provisioning (getting the card onto the phone).
[35] ABI Research, “Mobile and Mega Trends Report, Q2 2013” (http://bit.ly/1oetkMe).
[36] Verifone. Payment facilitating system for use with a mobile communicator utilizing a near field communication link. US Patent 20130030933, filed July 27, 2011, and issued January 31, 2013.
[37] This could quickly change should Apple decide to incorporate NFC into the iPhone. That would mean significant changes to the phone’s innards, so the jury is still out on whether this would ever happen. Find more about Apple in Chapter 7.
[38] Groupe Speciale Mobile Association, “The Role of the Trusted Service Manager in Commerce,” December 2013 (http://bit.ly/1oetuD7).
[39] Multifactor authentication involves verifying something the user knows (a login and password) and something the user has (card details), and can even include fingerprint verification thanks to the iPhone 5S and some Android devices.
[40] Note that in July 2014, the Isis consortium announced that it would rebrand to a new name, yet to be announced as of this writing. The intent was to avoid association with the militant group known as ISIS.
[41] Yankee Group report, “US Mobile Wallet Roundup: Gauging the Future Potential of Today’s Solutions,” February 27, 2014.
[42] This is the purpose of the Card Verification Value, or CVV, also known as “the three-digit code from the back of your card.” It confirms that a physical card was present at the time of payment.
[43] Daniel Amitay, “Most Common iPhone Passcodes,” Big Brother Camera Security, June 14, 2011 (http://bit.ly/1oetJ1f).
[44] “Starbucks Mobile Payment App Nears 4M Transactions Per Week,” Mobile Payments Today, April 29, 2013 (http://bit.ly/1oetUtb).