Toni emerged from her hairdressing appointment to find her ex-boyfriend, Frank, a violent young man who once put her in the emergency room with a broken rib, sitting across the street on a bench. Walking quickly to her car, Toni, hands shaking, fumbled to find the release lock. Once inside, she locked all the doors and sped off. This was the fourth time in the last week that Frank had found out where she was going. She headed toward her friend Claire’s house, checking in the rearview mirror the whole way to see if she spotted Frank’s car. She deliberately made several wrong turns and circled the block three times to ensure no one was following her. Two hours later and feeling much better from her visit with her friend, Toni stepped out of Claire’s house only to find Frank sitting across the street again.
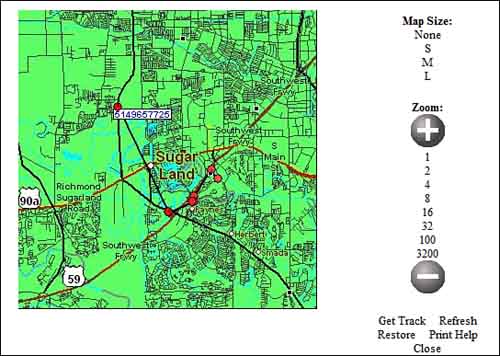
How did Frank always know where Toni was? Just prior to their breakup, Frank had installed a small receiver inside Toni’s car that he had purchased on the Internet for $500 (see Figure 1.1). This GPS Snitch device is no bigger than a set of keys and can be hidden in just about anything—a bag, a car—to give a stalker instantaneous knowledge of someone’s whereabouts. It runs on batteries but can be hard-wired into a vehicle to eliminate the need for batteries. It was hidden behind the dashboard. The receiver, which was hard-wired into the vehicle, was feeding Toni’s whereabouts to Frank 24 hours a day, 7 days a week. All Frank had to do was dial up his cell phone or access a computer to find out exactly where Toni’s car was (see Figure 1.2). The map overlay shows the path of a vehicle equipped with GPS Snitch. The path and location can be retrieved via an Internet browser or a web-enabled cell phone. If the cell phone is not web-enabled (meaning it cannot display an Internet page), the location can be sent via text message (“123 Main Street @ 10:05AM”) at regular intervals.
High-Tech Stalkers
Many people are familiar with the term stalking, but few understand the concept of cyber stalking, which is stalking with a technology component to it. Whether someone is stalking via the Internet or stalking using the many tech tools available for purchase for tracking and snooping on another person, it is cyber stalking.
Many stalkers consider finding and tracking someone a personal challenge, a way of proving that they are smarter than their target. Other times, stalkers’ efforts are aimed at trying to upset and provoke their victims by constantly reminding them of their presence. Combine that warped mentality with a little technical knowledge, and it’s like leaving a car unlocked with the keys in the ignition. Unfortunately, many people (both men and women) lack the knowledge to understand how someone is tracking them.
In this book, we provide numerous examples of cases from both the media and our own experiences in law enforcement with one goal in mind—to make you aware of all the dangers of cyber crime. The more you know, the better your chances are of never becoming a victim.
We not only want to share the tools of cyber criminals, but in the case of cyber stalkers, we explain how they think. We’ll put you inside the head of someone who derives devious pleasure in proving he is smarter than his victim and controlling his victim.
In his February 1, 2006 blog, “How I Stalked My Girlfriend,” appearing in The Guardian (London), columnist Ben Goldacre writes about how easy it was to set up GPS tracking on his girlfriend’s cell phone. He did so with her permission, of course, but even so, he was astounded at how quick and easy it was to do:
I unplugged her phone and took it upstairs to register it on a website I had been told about…. I ticked the website’s terms and conditions without reading them, put in my debit card details, and bought 25 GPS Credits for £5.
Almost immediately, my girlfriend’s phone vibrated with a new text message. “Ben Goldacre has requested to add you to their Buddy List! To accept, simply reply to this message with ‘LOCATE.’” I sent the requested reply. The phone vibrated again. A second text arrived: “WARNING: [this service] allows other people to know where you are. For your own safety make sure that you know who is locating you”. I deleted both these text messages.
On the website, I see the familiar number in my list of “GPS devices” and I click “locate”. A map appears of the area in which we live, with a person-shaped blob in the middle, roughly 100 yards from our home. The phone doesn’t go off at all. There is no trace of what I’m doing on her phone. I can’t quite believe my eyes: I knew that the police could do this, and telecommunications companies, but not any old random person with five minutes access to someone else’s phone. I can’t find anything in her mobile that could possibly let her know that I’m checking her location. As devious systems go, it’s foolproof. I set up the website to track her at regular intervals, take a snapshot of her whereabouts automatically, every half hour, and plot her path on the map, so that I can view it at my leisure. It felt, I have to say, exceedingly wrong.” (Source: http://www.guardian.co.uk/technology/2006/feb/01/news.g2)
The Victim’s Side
It is important for victims to work with law enforcement and advocacy groups to develop a safety plan and then methodically build a case. Keeping the victim safe and obtaining the best evidence to prosecute the criminal are priorities. A stalker’s behavior is obsessive and can escalate suddenly at any time, making deterrence and criminal apprehension difficult. Often the most dangerous time for a victim is when he or she tries to leave to get help, because a stalker feels threatened by the notion of the victim being inaccessible and this can trigger an escalation in violent behavior.
The good news is that law enforcement agencies are more sensitive these days to victim needs and the dynamics of these dangerous relationships. Laws are changing to reflect the seriousness of these violent crimes. Responding officers and investigators are better trained to build these cases from a behavioral approach as well as a technological approach.
Prosecutors are on board as well, but the reality is that these types of cases are still difficult to prosecute. Typically, these infractions occur over time and in various jurisdictions. Each single incident can initially appear to be benign. A single occurrence of behavior does not often constitute a crime, and even when a pattern of behavior is established, the crime is often a lower-level misdemeanor, which results in very little jail time, if any at all. It is not uncommon for these cases to take months and sometimes years to prosecute, and when a conviction is won, the jail time is not necessarily significant given what terror the victim has endured.
One of our goals in writing Cyber Crime Fighters: Tales from the Trenches is that by detailing cases, we help readers recognize specific behavior patterns and steer clear of the person exhibiting them before the situation escalates into a dangerous one. We want you to understand that other educated, level-headed, intelligent people have fallen victim to cyber stalkers and predators because they did not recognize those patterns. History, as the saying goes, repeats itself. By sharing all these stories, it is our sincere hope that you will never become part of the history of victimization.
Identity Assumption
Unlike identity theft, which is usually focused on perpetrating fraud, identity assumption is more commonly used to destroy someone’s reputation.
Falsely posting comments in a public forum that specifically digresses from someone’s known beliefs is identity assumption in its mildest form. Imagine someone’s picture getting uploaded to the tens of thousands of pornography websites. Imagine having a pornographic website created in your own name along with compromising pictures of yourself. And by the way, those pictures can easily be created using image-editing programs such as Photoshop. This is the same software used by magazine and print editors to make teeth whiter, remove an inch or two from waistlines, and so on. A face from one photo can easily be placed on another or edited using commonly available software.
The Wild, Wild Web
Much of the Internet is still the “Wild, Wild Web” and remains largely unregulated. There is very little authentication of email accounts, websites, and blogs. Anyone can establish them. In an effort to lure pedophiles, law enforcement routinely establishes false identities as young adolescents. There is no validation of age, gender, sex, or location on most free email programs; hence, it is very easy for anyone to create a false identity.
Websites are easy to create with just a bit of technical knowledge. Remember all the phony websites established to accept donations in the wake of Hurricane Katrina? Imagine if a website was created using your name and image with links to such nefarious activities as pornography or even worse, child pornography. This is the modern day equivalent of scrawling “For a good time, call Jane Doe” on the bathroom wall. Someone with an axe to grind can do much damage in little time.
With no regulations whatsoever, people can put together a website for just about anything. Websites can be used for professional reasons. They can be used to sell cars, share recipes, or list team stats. They can provide critical medical information or archive history that would otherwise be lost, but they can also be built to completely damage a person’s reputation, promote child sexual exploitation, or to perpetuate a dangerous infatuation.
Sticks and Stones
Cyber stalking is a unique form of cyber crime because it has the potential to move from a web address to a real address—from the virtual to the actual. Our experience has proven that, too often, cyber stalking is not taken seriously by authorities because it may not involve physical contact or because the victim and stalker do not live in close proximity to each other. This needs to change.
When a victim in New Hampshire complains of being cyber stalked by someone from California, her complaint needs to be taken just as seriously as if the offender lived in the same town and posed a physical threat. It is not acceptable to tell a victim to “turn off your computer” or “change your email address” if she needs that email address for professional purposes.
Even if the cyber stalking never crosses over to a physical threat (and we sincerely hope it doesn’t), it is still as frightening, real, and distressing as in-person threats. Words will hurt you—being terrified has both psychological and physical manifestations.
The retail giant Wal-Mart was recently taken to task for selling t-shirts that read, “Some call it Stalking. I call it Love” (see a similar t-shirt in Figure 1.6). Women’s groups and victim advocacy groups across the country were outraged. Wal-Mart quickly pulled the t-shirts off their shelves and stated, “It is not our desire to encourage or make light of such a serious issue through the sale of any products we carry”.
The “Stalker” E-Card
Imagine you are checking your email and receive notification that you have received an electronic greeting, or “e-card”. You click the link and are taken to a site with a black background upon which the following letters appear, one by one, as if they are being typed to you in real time:
Does it bother you to know that I am thinking of your beautiful green eyes and soft brown hair? You can turn this off, you know, and I’ll be gone. Or will I? Maybe I’m nearby. Where is that again? That’s right, Washington Road. I’m watching you.
How frightening this would be to anyone, but especially to a victim of a stalker, cyber stalker, or domestic violence. And yet the example we’ve given here is very similar to the eerie stalker e-card message created by a well-known, major greeting card company just a few years ago. The card’s design centered around allowing the sender to “customize” it with very specific details, such as hair and eyes, location, and so on.
Just like websites, electronic cards can be created by anyone. There is no validation of who created them or where they came from without a detailed forensic investigation, and that is not likely to occur unless the e-card was somehow connected to a major crime.
Needless to say, this e-card was pulled from the site and is no longer accessible, but we mention it to point out that cyber stalking can come from many technologies. Even major corporations with millions of customers and big public relations departments sometimes lack oversight of their products or the insight that stalking is not a joke. Just ask anyone who has ever been a victim.
The anonymity of the Internet lends itself to people expressing themselves in ways they might not ordinarily express during face-to-face communications. As a result, people may say things that offend or outrage others.
Bestselling author Patricia Cornwell recently appealed to her readers to counter negative reviews of her novel Book of the Dead. It wasn’t just one bad review, but a sudden onslaught of hundreds of negative reviews appearing on sites such as Amazon and eBay. Cornwell suspected an organized group was behind the effort and appealed to her readers to counter these negative reviews with positive ones. The negative reviews did not stop the book from becoming a bestseller, but it points out just how easy it is to use a very public and largely unregulated medium to wreak havoc on someone’s reputation. Just like the female realtor who became a victim of identity assumption, a person’s reputation can very quickly plummet using the power of the Internet.
Cyber Stalking and the Law
The general legal definition of stalking includes five parts (or elements) that are necessary to prosecute the crime in most states:
1. A “willful course of conduct”…
2. … of repeated or continued harassment, without permission,…
3. … of another individual…
4. … that would cause a reasonable person to feel terrorized, frightened, intimidated, threatened, or harassed…
5. … and that actually causes the victim to feel terrorized, frightened, intimidated, threatened, or harassed.
The term reasonable person refers to the average, everyday person and how he or she might respond to a situation where they are exposed to repeated harassment or other stalking behavior. The response to such a situation would be based upon all of the information available to the person at the time. Essentially, we can simplify the concept by generalizing that a “reasonable person” would respond to a situation in a manner similar to the response of a majority of people exposed to the same set of circumstances. For instance, if a message is left on an answering machine by an ex-spouse stating that he or she is going to come smash all your car windows, and that ex-spouse has damaged your property before, it is likely that if 10 people hear that message, the majority will respond that the threat should be taken seriously. It is reasonable to believe that the ex-spouse will follow through on the threat.
Acts that qualify as stalking include following or appearing within the sight of someone; approaching or confronting someone in a public or private place; appearing at the workplace or home of another; entering the person’s property (trespassing); contacting someone repeatedly via phone, mail, or email; getting other friends or family to harass a person on the stalker’s behalf; leaving notes, presents, or other items for the victim.
Although stalking is a crime in and of itself, it is important to remember that stalking often occurs along with other crimes, such as trespassing, assault, criminal threatening, sexual assault, vandalism, criminal mischief, and prowling. Although stalking does not require that a person know his or her stalker, more often than not, the stalker is someone the victim knows or has been involved with.
Most states have stalking statutes with corresponding requirements and sentences. Many states also offer the protection of a stalking order, an order very similar to the civil domestic violence petition or order. The requirements can vary, but essentially a course of conduct, including two or more behaviors, must occur that makes the victim afraid for his or her personal safety. Your local law-enforcement agency or family court can guide you as to the steps that can be taken to obtain a stalking order.
The Violence Against Women Act of 2000 made cyber stalking a part of the Federal Interstate Stalking Statute, but federal legislation is still lacking. Therefore, the bulk of legislation still falls at the state level.
In 2006, President Bush signed federal anti-cyber stalking legislation. At the time of this writing, 45 states currently have cyber stalking-related laws. Several states have pending laws, and the four remaining states (Idaho, New Jersey, Utah, and Nebraska) have no legislation. It should be noted that in some states, laws that are aimed at preventing cyber stalking are really meant to protect victims under the age of 18.
Cyber Stalking Facts
The following statistics shed some light on who the stalker is and who the stalker targets:
• Sixty-six percent of stalkers pursue their victim at least once per week.
• Seventy-eight percent of stalkers use more than one approach.
• Eighty-one percent of victims stalked by an intimate partner reported that they had previously been assaulted.
• Eighty-seven percent of stalkers are men.
• Ninety-four percent of female victims are stalked by men.
• Sixty percent of male victims are stalked by other men.
• Just over 13% of college students reported being stalked.
• Sixty-two percent of cyber stalking victims are female, primarily ages 18–24.
(Source: www.wiredsafety.org/resources/powerpoint/cyberstalking_study.ppt)
Just like domestic violence, stalking and cyber stalking at the hands of a former intimate partner can escalate and result in danger to a victim. Factors used in threat assessment include looking at the stalker’s level of motive, means, ability, intent, and experience. A rise in these things, in combination with one another, can determine the level of threat facing a victim. The danger potential is often seen in “dramatic moments” such as the arrest of the perpetrator, the issuance of a restraining or stalking order, court hearings, custody hearings, anniversary dates, and any family-oriented holiday. The threat level is greater to a victim during these times.
Lethality Assessment Tools
Many law-enforcement agencies are now using lethality assessment tools, including the model used by most agencies in the State of Maryland. The Maryland Lethality Assessment Program for First Responders was instituted in the State of Maryland through the Maryland Network Against Domestic Violence and was recently recognized as one of the Harvard Kennedy School’s Ash Institute’s “Top 50 Programs” of the 2008 Innovations in American Government competition. The Lethality Assessment Program (LAP) is based on 25 years of research by Dr. Jacquelyn Campbell, of the John Hopkins University School of Nursing, and is a result of the following bodies of research:
• Only 4% of domestic violence–related homicide victims ever take advantage of domestic violence program services.
• In 50% of domestic-related homicides, officers had previously responded to a call at the scene.
• The re-assault of a high-danger victim is reduced by 60% if a domestic violence shelter is utilized.
The goal of the LAP is to prevent serious injury, re-assault, and domestic-related homicides by encouraging victims to seek out support and services provided by domestic violence programs. It includes a screening tool for first-responding law-enforcement officers and a protocol referral so that officers can initiate appropriate resources, with the goal of facilitating a conversation between the victim and a domestic violence hotline counselor.
These assessment tools primarily ask questions of victims in the form of checklists and look at factors such as prior victimization and abuse, any prior drug or alcohol abuse on behalf of the perpetrator, the perpetrator’s threats toward the victim or her children, the perpetrator’s access and degree of interest in weapons, violence outside the home, stalking behavior, history of suicide attempts, history of the relationship including prior breakups, the perpetrator’s physical access to the victim and her family and/or relatives, and violence against family pets.
At this time, the Maryland Lethality Assessment Program may be the only system in the country that utilizes a research-based screening tool and an accompanying referral protocol that facilitates a cooperative effort between law enforcement and domestic violence programs in helping high-risk victims seek support services and domestic violence intervention programs.
The lethality assessment tool results in a score that assists law enforcement in understanding the potential threat toward a victim. It’s a valuable tool from a law-enforcement perspective, but one that victims don’t have available to them. Therefore, we’ll add perhaps the most important tool you always have with you—your gut instinct. Listen to it. We’ve seen hundreds of cases where victims said they heard “a tiny voice” or had a “funny feeling” telling them not to respond to that email or that someone seems to violating their personal space or is overly friendly, and so on. Your gut instinct is there. Listen to it!
If You Think You Are Being Cyber Stalked
If you find that you have caught the eye of a cyber stalker, these are some valuable suggestions to stop the unwanted intrusion of the stalker:
• Make it clear to the other person you do not want any further contact with him or her through one message and save that message. If you send it by email, use the Blind Copy (BC:) feature of your email program and send a copy to yourself for your records.
• Save everything! Do not delete any emails or text messages. If you can, print out any emails and save them. Do not alter them in anyway. Save the original emails online because they may contain important routing information that can help law enforcement determine the sender.
• Once you advise the person you want no further contact, do not reply to him or her! Better yet, do not even open the emails or attachments from a suspected stalker. Stalkers often derive pleasure out of provoking someone. If you continue to reply, you continue to provoke.
• Have your own personal safety network of friends, family, and resources. Always let someone know where you will be and when you are expected to return.
• Take security measures at home, in your vehicle, and at work in conjunction with your cyber safety measures. Memorize emergency numbers and have them on speed dial on your cell phone. Keep your cell phone charged and with you at all times. Block outgoing Caller ID and do not accept private calls.
• Do not be afraid to seek counseling if necessary for your well-being.
• Contact your local law-enforcement agency. Oftentimes, the laws regarding cyber crime and cyber stalking are murky. Only a professional police officer can advise you about the law. Follow the advice and direction you are given. Unfortunately, many victims do not follow through with law-enforcement advice.
• If it is determined that no law has been broken and the person persists in contacting you, consider notifying his or her Internet service provider and advising them. They may take action depending on their internal policies.
• Make certain that if the abuser/stalker is an “ex,” there is no chance he or she had the opportunity to download any programs that aid in monitoring your online activity. Be aware of spyware and how it can give a stalker the ability to monitor all of your computer use.
• Seek information on obtaining a stalking order or restraining order. Laws and procedures vary from state to state. However, your local law-enforcement agency can guide you toward the process that best meets your needs.
• If you find a website that is focused on harassing you, it may violate local harassment laws. Furthermore, becoming familiar with search engines such as www.whois.net can assist you in determining the owner of any malicious website. Again, assistance can be found with your local police department or victim advocacy group.
• If you can, create a new email account or an additional email account using a free web-based email site. Do not provide detailed information about yourself in the profile.
• Change your passwords and PIN numbers because email addresses are often used by abusers and stalkers to impersonate their victims or cause them harm. Change your passwords frequently.
• Search for your name on the Internet on major search engines such as Google and Yahoo!. You will be amazed at what you may find about yourself online. This may show that your contact information is easily accessible. Be sure to search for your full name in quotation marks, as this will give search engine results for your name in its entirety and condense results. If you do not use quotes around your full name, you will likely end up with many results that include your first name and last name somewhere in an article or blog, but not together or even referring to you. For example, searching for Jane Smith (without quotes) could result in an article where Jane Doe and Charlie Smith are mentioned together. Also check out sites that specialize in telephone number, address, or name searches to see what is out there. (See Chapter 2, “Two Bedrooms Up, One Bedroom Down—What Someone Can Find Out About You on the Internet,” for more information.)
Teen/Tech Stalking
Anyone with teenagers knows how comfortable teens are with technology, but this has led to a new form of cyber stalking dubbed “teen/tech stalking” in which cell phones and text messages—the staples of many teens nowadays—are used to harass, dominate, and/or humiliate young people, in most cases teen girls.
Teen Study
Teenage Research Unlimited recently conducted a nationwide survey of 615 teens between the ages of 13 and 18. The results are alarming:
• Thirty percent admit they’ve been text-messaged or emailed up to 30 times an hour by a boyfriend or girlfriend checking up on them.
• Eighteen percent said their partner has used a social-networking site to harass them.
• Seventeen percent said their partner made them “afraid not to respond to a cell phone call, email, IM, or text message”.
• Ten percent said they had been threatened in calls or messages.
• Fifty-eight percent of parents whose teens were physically assaulted by their partner did not know it had happened.
Online Games—The New Stalker’s Ground
We’re seeing an alarming trend in cases connected to online games being used as a playground for cyber stalkers, pedophiles, and other forms of cyber crime. Here are a few interesting cases:
• A 31-year-old Australian woman was arrested when she traveled to North Carolina to lure a 16-year-old boy she encountered playing World of Warcraft.
• A 26-year-old Florida resident is under investigation for allegedly coaxing a 15-year-old girl he played World of Warcraft with to run away with him.
• In China, a Legend of Mir 3 player is spending the rest of his life behind bars for fatally stabbing another for the “theft” of a virtual sword.
Online gaming has evolved considerably in the last few years, from static games where a player competed against the computer, to “virtual communities” in which one player is virtually pitted against another.
Popular online games such as World of Warcraft, Second Life, and Halo are known as massively multiplayer online games, or MMOGs. They allow players to interact and chat with each other in real time.
Players adopt virtual personas in the form of characters or “avatars” when playing. Unlike social networking sites where participants might try to be polite, these gaming sites pit player against player in a highly competitive, and often “virtually violent” atmosphere. Because they include socialization opportunities via web chats and instant messaging, they also provide fertile ground for pedophiles.
Just recently, a 20-year-old man from Saratoga Springs, New York, was arrested for allegedly stalking a 15-year-old girl he met while playing the online game Halo. This man drove 40 hours from New York to Spokane, Washington, a trip of almost 2,600 miles, to meet her and then sent her a threatening text message when she rejected him. The girl’s parents watched the man drive by their house, noted his license plate, and called the police. His case is pending.
Online Gaming and Malware
Of the 137 million computer users, it is estimated that a quarter of them play some form of online game. In addition to the opportunities this opens up for cyber stalkers, it also creates a fertile ground for malware—malicious software that can do nasty things to your computer, including stealing your account information. We will discuss malware in greater depth in Chapter 11, “Phishing, Pharming, Spam, and Scams,” but it is interesting that the majority of malware is found in China, where passwords are stolen surreptitiously to aid in identity theft and fraud. China has become a breeding ground for skilled programmers and code writers who cross the line from “hackers” to “crackers” (criminal hackers). The more sophisticated online gaming becomes, the more opportunities it presents for cyber crime to be committed.
Would You Say It to My Face?
The Internet can be a very safe place to travel if you know how to protect yourself online. The most important line of defense to your online personal safety arsenal is to ask yourself one thing: Would I tell a stranger who looks suspicious to me, someone I have just met for the very first time in person, what I’m about to say online?
It is easy—due to the supposed “anonymity” of the Internet—to say things you would never dream of saying to a stranger you’ve just met on a bus or in a bar. The Internet is not anonymous, not by any means. The perception that what you say online to a stranger 3,000 miles away won’t come back to haunt you is a dangerous one to have. Always act under the premise that the person you’re communicating with online is sitting next to you just a few feet away before sending that email or posting that blog. We’re not trying to limit anyone’s freedom of speech; we’re just suggesting that you think about what the potential reaction of what you say online could be before you post—for your own personal safety.
National School Board Survey
A recent National School Boards Association survey reports that more than 25% of the educators polled report they are aware of false websites and/or pages being created for the purposes of exacting revenge on an educator.
Interestingly and disturbingly enough, this practice is fairly common, and teens often find it humorous to set up MySpace pages for a principal or teacher they are not particularly fond of. We have seen this with at least two local educators who had been targeted for this type of degradation. The MySpace pages contained their photos, address info, and even phone numbers. The fake profiles were mean and humiliating. Ironically, we stumbled upon one of the pages in the course of an investigation. The other was discovered because the kids were bragging about it at the local high school. For one of the victims, we found three separate prank pages.
Women as Perpetrators
In February of 2008, a 50-year-old Oregon tax attorney was arrested and charged with trying to frame her ex-boyfriend by sending explicit pictures of him to his boss. What we find interesting about this case—in addition to the fact that a woman was doing the cyber stalking—was the elaborate methods she used to try and cover her trail, including the use of prepaid cell phones to make harassing phone calls and phony email accounts, as well as regular mail to stalk and harass. This was also the first case to invoke Washington State’s cyber stalking law from 2004, the state where the offense was alleged to have occurred.