Chapter 12
Cyber Terrorism and Information Warfare
Chapter Objectives
After reading this chapter and completing the exercises, you will be able to do the following:
 Explain what cyber terrorism is and how it has been used in some actual cases
Explain what cyber terrorism is and how it has been used in some actual cases Understand the basics of information warfare
Understand the basics of information warfare Have a working knowledge of some plausible cyber terrorism scenarios
Have a working knowledge of some plausible cyber terrorism scenarios Have an appreciation for the dangers posed by cyber terrorism
Have an appreciation for the dangers posed by cyber terrorism Explain future trends in cyber warfare
Explain future trends in cyber warfare
Introduction
This book has looked at various ways a person might use a computer to commit a crime. This book has also looked into specific methods to make a system more secure. One issue that has not been addressed is cyber terrorism. People in countries around the world have grown accustomed to the ever-present threat of terrorist attacks, which can come in the form of bombs, hijacking, release of a biological agent, or other means. However, in our modern world, we have to consider cyber attacks as well.
The first question might be this: What is cyber terrorism? According to the FBI, cyber terrorism is a premeditated, politically motivated attack against information, computer systems, computer programs, and data that results in violence against noncombatant targets by subnational groups or clandestine agents. Cyber terrorism is simply the use of computers and the Internet connectivity between them in order to launch a terrorist attack. In short, cyber terrorism is just like other forms of terrorism—it is only the milieu of the attack that has changed. Clearly, the loss of life due to a cyber attack would be much less than that of a bombing. In fact, it is highly likely that there would be no loss of life at all. However, significant economic damage, disruptions in communications, disruptions in supply lines, and general degradation of the national infrastructure are all quite possible via the Internet.
The real question might be: What is the difference between cyber espionage and cyber terrorism? First and foremost, the goal of espionage is simply to gather information. It is preferable to the spy if no one is even aware that anything occurred. This is true for both corporate and international espionage. Cyber terrorism, on the other hand, seeks to cause damage, and it needs to be as public as possible. The idea is to strike fear into people. While some might find the topics related, they are actually quite different.
Leading up to the 2022 Russian invasion of Ukraine, Russia made coordinated cyber strikes against Ukraine. This sort of two-pronged operation—cyber attacks coupled with kinetic warfare—is expected to be more common in coming years. First disrupting the target’s infrastructure through a cyber attack improves the chance that the kinetic attacks will succeed. This is not meant as a comment on the morality of the Russian invasion of Ukraine but rather an observation about the role cyber attacks play and will continue to play in traditional conflict scenarios.
It is a strong possibility that, in time, someone or some group will try to use computer methods to launch a military or terrorist attack against our nation. Some experts make the case that the MyDoom virus was an example of domestic economic terrorism. However, an attack such as that may be only the tip of the iceberg. Sometime in the near future, our nation may be the target of a serious cyber terrorism attack. This chapter will examine some possible cyber terrorism scenarios, with the purpose of giving you a realistic assessment of just how serious a threat this is. In the exercises at the end of the chapter, you will have the opportunity to examine current acts of cyber terrorism, as well as potential threats, and the actions you can take to help prevent them.
The first edition of this book discussed cyber terrorism as well. That was in 2004. At that time, some may have thought that the coverage of that topic was almost fiction, that there was no real threat from cyber terrorism. That has proven to not be the case. One of the first indications that cyber terrorism is a real threat was that in November 2006 the secretary of the Air Force announced the creation of the Air Force Cyber Command (AFCC), whose primary function is to monitor and defend American interests in cyberspace. The AFCC draws upon the personnel resources of the 67th Network Warfare Wing as well as other resources. It seems that the U.S. Air Force takes the threat of cyber terrorism and cyber warfare seriously, given that it has created an entire command to counter that threat.
Actual Cases of Cyber Terrorism
Because some readers may wonder whether this is just fear mongering, let’s look at some actual cases of cyber terrorism before we delve into the various aspects of it. How likely is a genuine cyber terrorist attack? Well, let’s look at some real-world cases of cyber terrorism before we delve into the various aspects of it. We will begin with older cases and work our way forward to modern cases to provide a timeline of cyber warfare, espionage, and terrorism.
CENTCOM, or Central Command, is the U.S. military command responsible for operations in the Middle East and Near East. In 2008 CENTCOM was infected with spyware. A USB drive was left in the parking lot of a DoD facility in the Middle East. A soldier picked it up and plugged it into his workstation, thus introducing the spyware to the CENTCOM network. The worm was known as Agent.btz, a variant of the SillyFDC worm. This was a significant security breach, and we will probably never know how much data was lost or how much damage was caused.
The year 2009 brought a number of Internet-based attacks, specifically against U.S. government websites, such as the websites of the Pentagon and the White House (in the United States) and various government agencies in South Korea. These attacks coincided with increased tensions with North Korea. Clearly, these where examples of cyber terrorism, albeit relatively minor.
In December 2009 a far more disturbing story came out. Hackers broke into computer systems and stole secret defense plans of the United States and South Korea. Authorities speculated that North Korea was responsible. The information stolen included a summary of plans for military operations by South Korean and U.S. troops in case of war with North Korea, and the attacks traced back to a Chinese IP address. This case is clearly an example of cyber espionage and a very serious one at that.
In December 2010 a group calling itself the Pakistan Cyber Army hacked the website of India’s top investigating agency, the Central Bureau of Investigation (CBI). This sort of cyber espionage is far more common than what is revealed to the public.
In 2015 Chinese hackers were deemed responsible for breaking into U.S. government computers and accessing the data of 4 million current and former federal employees. This was a breach of the Office of Personnel Management.
Also in 2015, half of Turkey experienced a 12-hour power outage after an attack carried out by advanced persistent threat (APT) group MuddyWater, which has ties to Iran’s Ministry of Intelligence and Security. The group used malicious PDFs and Office documents as their main attack vector.1
1. https://www.zdnet.com/article/state-sponsored-iranian-hackers-attack-turkish-govt-organizations/
In 2017 Russian-backed hackers targeted at least 10,000 U.S. Defense Department (DoD) employees via Twitter.
In 2019 Russia accused the United States of planting malware on Russia’s power grid.2 The Russian government claims that U.S. probing of the Russian power grid goes back as far as 2012. There is, however, no evidence that any of the malware had actually been used.
2. https://www.securityweek.com/us-planted-powerful-malware-russias-power-grid-report
In 2022 the United States claimed to have removed malware around the world to prevent Russian cyber attacks. The malware in question was meant to allow GRU (Russian military intelligence) to create and control botnets.3
3. https://www.justice.gov/opa/pr/justice-department-announces-court-authorized-disruption-botnet-controlled-russian-federation
These incidents show a steady progression in the use of cyber weapons by nation-states. Clearly, this issue is not hypothetical but rather actual and increasing. Later in this chapter, detailed examinations of specific incidents will be provided.
China’s Advanced Persistent Threat
An advanced persistent threat (APT), as the name suggests, is a series of advanced cyber attacks that are sustained over a period of time—hence the term persistent. The security firm Mandiant tracked several APTs over a period of 7 years,4 all originating in China, specifically Shanghai and the Pudong region. These APTs were simply named APT1, APT2, and so on.
4. https://www.mandiant.com/resources/apt1-exposing-one-of-chinas-cyber-espionage-unit
The attacks were linked to UNIT 61398 of China’s military. The Chinese government regards this unit’s activities as classified, but it appears that offensive cyber warfare is one of its tasks. A single one of the APTs from this group compromised 141 companies in 20 different industries. APT1 was able to maintain access to victim networks for an average of 365 days—and in one case for 1764 days. APT1 is responsible for stealing 6.5 terabytes of information from a single organization over a 10-month time frame.
India and Pakistan
India and Pakistan have had deep enmity for each other for quite some time. It should be no surprise that, in recent years, this has involved cyber operations.
One India published an article in August 2015 titled “Pakistan Wants to Launch Cyber War on India,” which stated, “The cyber wing of the Intelligence Bureau has warned that government websites could be hacked by the Pakistan Cyber Army in this ongoing proxy war against India.”5 As per the latest alert, Pakistan’s ISI has directed its cyber army to declare an Internet war on India.
5. https://www.oneindia.com/india/pakistan-wants-to-launch-cyber-war-on-india-1831947.html
This has continued. In 2022, there was an article discussing the various ways India and Pakistan have utilized cyber attacks in their ongoing dispute over Kashmir.6 Both sides have employed cyber attacks against the other. Furthermore, both sides have used third parties as part of their cyber conflict.
6. https://nationalinterest.org/blog/techland-when-great-power-competition-meets-digital-world/how-pakistan-brought-cyberwar-kashmir
Russian Hackers
According to ISight Partners, a cyber intelligence firm, in 2014 hackers from Russia were spying on computers used in NATO and the European Union.7 The spying was accomplished by exploiting bugs in Microsoft Windows. The hackers were also reported to have been targeting sites in Ukraine for spying.
7. https://www.nytimes.com/2014/10/15/business/international/russian-hackers-used-bug-in-microsoft-windows-for-spying-report-says.html
Iran–Saudi Tension
The tension between Iran and Saudi Arabia has gone on for decades. The civil war in Yemen has been a proxy war between Iran and Saudi Arabia. Each side has accused the other of cyber attacks. In addition, there have been numerous accusations of outside influence. The Houthi have been accused of being proxies for Iran, as both the Houthi and Iran are Shia. The United States and Saudi Arabia have both accused Iran of arming the Houthi. Iran and the Houthi deny any affiliation. African nations such as Eritrea have also been accused of supporting the Houthi. The Yemeni government has actually received support from the United States and Saudi Arabia.
The Shamoon virus was first discovered in 2012, and a variant was found circulating in 2017. Shamoon acts as spyware but deletes files after it has uploaded them to the attacker. The virus attacked Saudi Aramco workstations, and a group named Cutting Sword of Justice claimed responsibility for the attack. A number of security officials within Saudi Aramco have blamed Iran for this attack. And, like Stuxnet (described shortly), this virus infected systems other than the intended target.
Weapons of Cyber Warfare
In cyber warfare and cyber terrorism, malware is still the primary weapon. Whether it is spyware, a virus, a Trojan horse, a logic bomb, or some other sort of malware, it is still the malware that is the essential vehicle for conducting a cyber conflict. In this section, we will look at some well-known malware that has been used in conflicts.
Stuxnet
Stuxnet is a classic example of weaponized malware. Stuxnet first spread via infected USB drives; however, once it was on an infected machine, it would spread over the entire network and even over the Internet. The Stuxnet virus then searched for a connection to a specific type of programmable logic controller (PLC), specifically the Siemens Step7 software. If that particular PLC was discovered, Stuxnet would load its own copy of a specific DLL for the PLC in order to monitor the PLC and then alter the PLC’s functionality.
Stuxnet was designed to target centrifuge controllers involved in Iran’s uranium enrichment. But the virus spread beyond its intended target and thus became publicly known. While many users reported no significant damage from Stuxnet, outside the Iranian reactors, it was detected on numerous machines.
Stuxnet employed a classic virus design. Stuxnet has three modules: a worm that executes routines related to the attack; a link file that executes the propagated copies of the worm; and a rootkit responsible for hiding files and processes, with the goal of making it more difficult to detect the presence of Stuxnet. It is not the purpose of this discussion to explore the intricacies of Stuxnet. Rather, Stuxnet is introduced as both an example of state-sponsored malware attacks and at least an attempt to target such attacks.
Flame
No modern discussion of cyber warfare and espionage would be complete without a discussion of Flame. This virus first appeared in 2012 and was targeting Windows operating systems. The first item that makes this virus notable is that it was specifically designed for espionage. It was first discovered in May 2012 at several locations, including Iranian government sites. Flame is spyware that can monitor network traffic and take screenshots of the infected system.
It was spyware that recorded keyboard activity and network traffic, took screenshots, and is even reported to have recorded Skype conversations. It also would turn the infected computer into a Bluetooth beacon attempting to download information from nearby Bluetooth-enabled devices.
Kaspersky Lab reported that the Flame file contained an MD5 hash that only appeared on machines in the Middle East. This indicates the possibility that the virus authors intended to target the malware attack to a specific geographical region. The Flame virus also appears to have had a kill function allowing someone controlling it to send a signal directing it to delete all traces of itself. These two items indicate an attempt to target the malware, though the outcome of that targeting seems to have been a failure, or we would not be aware of its existence.
StopGeorgia.ru Malware
A number of hacking incidents played a role in the conflict between Russia and Georgia. The StopGeorgia.ru forum was an online forum designed to facilitate attacks against key network targets within Georgia. The online forum would advertise specific targets, give tutorials (and in some cases tools) for helping even low-skilled attackers engage the targets, and even provided links to proxy servers to help facilitate the attack by hiding the attacker’s true IP address and location.
As an example of what the website StopGeorgia.ru offered, there was a tool named DoSHTTP that automated DoS attacks and a list of websites and IP addresses within Georgia that would be good targets. This encouraged anyone sympathetic to Russia’s position in this conflict, who had even minimal computer skills, to embark on cyber attacks against Georgia.
FinFisher
FinFisher spyware was designed for law enforcement agencies with a warrant, to collect evidence on suspects. However, the software was released by WikiLeaks. It is now available on the Internet for anyone who wishes to use it.
BlackEnergy
BlackEnergy theoretically manipulates water and power systems, including causing blackouts and water supply disruptions. The BlackEnergy software has been traced to the Russian group SandWorm. In January 2016, a blackout at the Kiev airport was linked to the BlackEnergy malware.
The BlackEnergy malware specifically affects power plants. The malware is a 32-bit Windows executable. BlackEnergy is versatile malware, able to initiate several different attack modalities. It can launch distributed denial of service (DDoS) attacks. It also can deliver KillDisk, a feature that renders a system unusable.
Regin
Regin—also known as QWERTY and Prax—is a malware and hacking toolkit alleged to have been created by the U.S. National Security Agency in cooperation with the British GCHQ. The malware was first published by Kaspersky Lab and Symantec in 2014. This malware, which targets specific Windows computers, is quite stealthy due to its encrypted virtual file system.
NSA ANT Catalog
NSA ANT is reported to be a catalog that NSA makes available to agencies within the U.S. government that have clearance. It is a catalog of malware, including spyware, that has been developed by the National Security Agencies Tailored Access Operations group. A number of sources purport to have lists of items in the catalog as well as screenshots from the catalog. Given the classified nature of this catalog, if it actually exists, any website claiming to have details of the catalog should be treated with some skepticism.
Economic Attacks
There are a variety of ways that a cyber attack can cause economic damage. Lost files and lost records are one way. Chapter 9, “Computer Security Technology,” discussed cyber espionage and mentioned the inherent value of data. In addition to stealing that data, it could simply be destroyed, in which case the data is gone and the resources used to accumulate and analyze the data are wasted. To use an analogy, consider that a malicious person could choose to simply destroy your car rather than steal it. In either case, you are without the car and will have to spend additional resources acquiring transportation.
In addition to simply destroying economically valuable data (remember that there is very little data that does not have some intrinsic value), there are other ways to cause economic disruption. Some of those ways include stealing credit cards, transferring money from accounts, and committing fraud. But it is a fact that anytime IT staff is involved with cleaning up a virus rather than developing applications or administering networks and databases, there is economic loss. The mere fact that companies now need to purchase antivirus software and intrusion detection software and hire computer security professionals means that computer crime has already caused economic damage to companies and governments around the world. However, the general damage caused by random virus outbreaks, lone hacking attacks, and online fraud is not the type of economic damage that is the focus of this chapter. This chapter is concerned with a concerted and deliberate attack against a particular target or targets for the exclusive purpose of causing direct damage.
A good way to get a firm grasp on the impact of this type of attack is to walk through a scenario. Group X (which could be an aggressive nation, a terrorist group, an activist group, or literally any group with the motivation to damage a particular nation) decides to make a concerted attack on our country. It finds a small group of individuals (in this case, six) who are well versed in computer security, networking, and programming. These individuals, motivated either by ideology or monetary needs, are organized to create a coordinated attack. There are many possible scenarios under which they could execute such an attack and cause significant economic harm. The example outlined next is just one of those possible attack modalities. In this case, each individual has an assignment, and all assignments are designed to be activated on the same specific date:
 Team member one sets up several fake e-commerce sites. Each of these sites is up for only 72 hours and pretends to be a major stock brokerage site. During the brief time it is up, the site’s real purpose is only to collect credit card numbers, bank account numbers, and so forth. On the predetermined date, all of those credit card and bank numbers will be automatically, anonymously, and simultaneously posted to various bulletin boards/websites and newsgroups, making them available for any unscrupulous individual who wishes to use them.
Team member one sets up several fake e-commerce sites. Each of these sites is up for only 72 hours and pretends to be a major stock brokerage site. During the brief time it is up, the site’s real purpose is only to collect credit card numbers, bank account numbers, and so forth. On the predetermined date, all of those credit card and bank numbers will be automatically, anonymously, and simultaneously posted to various bulletin boards/websites and newsgroups, making them available for any unscrupulous individual who wishes to use them. Team member two creates a virus that is contained in a Trojan horse. Its function is to delete key system files on the predetermined date. In the meantime, it shows a series of business tips or motivational slogans, making it a popular download with people in business.
Team member two creates a virus that is contained in a Trojan horse. Its function is to delete key system files on the predetermined date. In the meantime, it shows a series of business tips or motivational slogans, making it a popular download with people in business. Team member three creates another virus. It is designed to create distributed denial of service (DDoS) attacks on key economic sites, such as those for stock exchanges or brokerage houses. The virus spreads harmlessly and is set to begin its DDoS attack on the predetermined date.
Team member three creates another virus. It is designed to create distributed denial of service (DDoS) attacks on key economic sites, such as those for stock exchanges or brokerage houses. The virus spreads harmlessly and is set to begin its DDoS attack on the predetermined date. Team members four and five begin the process of footprinting major banking systems, preparing to crack them on the predetermined date. Footprinting is the process of gathering information—some from public sources, others by scanning the target system/network.
Team members four and five begin the process of footprinting major banking systems, preparing to crack them on the predetermined date. Footprinting is the process of gathering information—some from public sources, others by scanning the target system/network. Team member six prepares a series of false stock tips to flood the Internet on the predetermined date.
Team member six prepares a series of false stock tips to flood the Internet on the predetermined date.
If each of these individuals is successful in his mission, on the predetermined date several major brokerages and perhaps government economic sites are taken down, viruses flood networks, and files are deleted from the machines of thousands of businesspeople, economists, and stockbrokers. Thousands of credit cards and bank numbers are released on the Internet, guaranteeing that many will be misused. It is also highly likely that the cracking team members four and five will have some success—meaning that possibly one or more banking systems are compromised. It does not take an economist to realize that this would easily cost hundreds of millions of dollars, perhaps even billions of dollars. A concerted attack of this nature could easily cause more economic damage to our country than most traditional terrorists attacks (bombings) have ever done. This is illustrated in Figure 12.1.

Figure 12.1 A team member of Group X?
You could extrapolate on this scenario and imagine not just one group of six cyber terrorists, but five groups of six—each group with a different mission and each mission designed to be committed approximately 2 weeks apart. In this scenario, the nation’s economy would literally be under siege for 2.5 months.
This scenario is not particularly far-fetched when you consider that, in past decades, nuclear scientists were sought after by various nations and terrorist groups. More recently, experts in biological weapons have been sought by these same groups. It seems extremely likely that these groups will see the possibilities of this form of terrorism and seek out computer security/hacking experts. Given that there are thousands of people with the requisite skills, it seems likely that a motivated organization could find a few dozen people willing to commit these acts.
Military Operations Attacks
When computer security and national defense are mentioned together, the obvious thought that comes to mind is the possibility of some hacker breaking into ultra-secure systems at the U.S. Department of Defense, Central Intelligence Agency (CIA), or National Security Agency (NSA). However, such an intrusion into one of the most secure systems in the world is very unlikely—not impossible, but very unlikely. The most likely outcome of such an attack would be for the attacker to be promptly captured. Such systems are hyper-secure, and intruding upon them is not as easy as some movies might suggest. However, there are a number of scenarios in which breaking into less secure systems could jeopardize our national defense or put military plans at risk.
Consider less sensitive military systems for a moment—systems that are responsible for basic logistical operations (such as food, mail, and fuel). Someone who cracks one or more of these systems could perhaps obtain information that several C-141s (aircraft often used for troop transports and parachute operations) are being routed to a base that is within flight distance of some city—a city that has been the focal point of political tensions. This same cracker (or team of crackers) might also find that a large amount of ammunition and food supplies—enough for perhaps 5000 troops for 2 weeks—is simultaneously being routed to that base. Then, on yet another low-security system, the cracker (or team of crackers) may note that a given unit, such as two brigades of the 82nd Airborne Division, has had all military leaves canceled. It does not take a military genius to conclude that these two brigades are preparing to drop in on the target city and secure that target. Therefore, the fact that a deployment is going to occur, the size of the deployment, and the approximate time of that deployment can all be deduced without ever attempting to break into a high-security system.
Taking the previous scenario to the next level, assume the hacker gets deep into the low-security logistical systems. Then assume that he does nothing to change the routing of the members of the brigades or the transport planes—actions that might draw attention. However, he does alter the records for the shipment of supplies so that the supplies are delivered 2 days late and to the wrong base. So there would be two brigades potentially in harm’s way, without a resupply of ammunition or food en route. Of course, the situation could be rectified, but the units in question may go for some time without resupply—enough time, perhaps, to prevent them from successfully completing their mission.
These are just two scenarios in which compromising low-security/low-priority systems can lead to very significant military problems. This further illustrates the serious need for high security on all systems. Given the interconnectivity of so many components of both business and military computer systems, there are no truly “low-priority” security systems.
General Attacks
The previously outlined scenarios involve specific targets with specific strategies. However, once a specific target is attacked, defenses can be readied for it. There are many security professionals who work constantly to thwart these specific attacks. What may be more threatening is a general and unfocused attack with no specific target. Consider the various virus attacks of late 2003 and early 2004. With the exception of MyDoom, which was clearly aimed at the Santa Cruz Organization, these attacks were not aimed at a specific target. However, the sheer volume of virus attacks and network traffic did cause significant economic damage. IT personnel across the globe dropped their normal projects to clean infected systems and shore up the defenses of systems. While these attacks are several years old, they are typical and thus worthy of study.
This leads to another possible scenario in which various cyber terrorists continuously release new and varied viruses, perform denial of service attacks, and work to make the Internet in general, and e-commerce in particular, virtually unusable for a period of time. Such a scenario would actually be more difficult to combat, as there would not be a specific target to defend or a clear ideological motive to use as a clue to the identity of the perpetrators.
Supervisory Control and Data Acquisitions (SCADA)
SCADA systems are industrial systems used to operate and monitor large-scale equipment (for example, power generators, civil defense alarms, water treatment plants). These systems are very attractive targets for cyber terrorism. In 2009 60 Minutes did a report on the vulnerability of power systems. It showed that penetration testers working for the Department of Energy were able to take over a power generator and potentially overload it, causing permanent damage and taking it offline. The famous Stuxnet virus that infected Iranian nuclear facilities was exploiting a vulnerability in SCADA systems.
These systems are of particular concern because damage to them is not simply an economic attack. It is entirely possible for lives to be lost as a result of cyber attacks on SCADA systems.
The components of a SCADA system include:
 Remote terminal units (RTUs) connected to sensors to send and receive data, often with embedded control capabilities
Remote terminal units (RTUs) connected to sensors to send and receive data, often with embedded control capabilities Programmable logic controllers (PLCs)
Programmable logic controllers (PLCs) A telemetry system, typically used to connect PLCs and RTUs with control centers
A telemetry system, typically used to connect PLCs and RTUs with control centers A data acquisition server, which is a software service that uses industrial protocols to connect software services, via telemetry, with field devices such as RTUs and PLCs
A data acquisition server, which is a software service that uses industrial protocols to connect software services, via telemetry, with field devices such as RTUs and PLCs A human–machine interface (HMI) to present processed data to a human operator
A human–machine interface (HMI) to present processed data to a human operator A historian, which is a software service that accumulates time-stamped data, Boolean events, and Boolean alarms in a database
A historian, which is a software service that accumulates time-stamped data, Boolean events, and Boolean alarms in a database A supervisory (computer) system
A supervisory (computer) system
There are standards for SCADA security. Special Publication 800-82, Revision 2, “Guide to Industrial Control System (ICS) Security,” is specific to industrial control systems, including SCADA systems and PLCs (programmable logic controllers). This document begins by examining the threats to these systems in detail. It also discusses how to develop a comprehensive security plan for such a system.
Information Warfare
Information warfare certainly predates the advent of the modern computer and, in fact, may be as old as conventional warfare. In essence, information warfare is any attempt to manipulate information in pursuit of a military or political goal. When you attempt to use any process to gather information on an opponent or when you use propaganda to influence opinions in a conflict, these are both examples of information warfare. Chapter 7, “Industrial Espionage in Cyberspace,” discussed the role of the computer in corporate espionage. The same techniques can be applied to a military conflict in which the computer can be used as a tool in espionage. Although information gathering will not be reexamined in this chapter, it is only one part of information warfare. Propaganda is another aspect of information warfare. The flow of information impacts troop morale, citizens’ outlooks on a conflict, the political support for a conflict, and the involvement of peripheral nations and international organizations.
Propaganda
Computers and the Internet are very effective tools that can be used in the dissemination of propaganda. Many people now use the Internet as a secondary news source, and some even use it as their primary news source. This means that a government, terrorist group, political party, or any activist group could use what appears to be an Internet news website as a front to put its own political spin on any conflict. Such a website does not need to be directly connected to the political organization whose views are being disseminated; in fact, it is better if it is not directly connected. The Irish Republican Army (IRA), for example, has always operated with two distinct and separate divisions: one that takes paramilitary/terrorist action and another that is purely political. This allows the political/information wing, called Sinn Féin, to operate independently of any military or terrorist activities. In fact, Sinn Féin now has its own website (www.sinnfein.org), shown in Figure 12.2, where it disseminates news with its own perspective. In this situation, however, it is fairly clear to whomever is reading the information that it is biased toward the perspective of the party sponsoring the site. A better scenario (for the party concerned) occurs when there is an Internet news source that is favorably disposed to a political group’s position without having any actual connection. This makes it easier for the group to spread information without being accused of obvious bias. The political group (be it a nation, rebel group, or terrorist organization) can then “leak” stories to that news agency.

Figure 12.2 The Sinn Féin website.
Information Control
Since World War II, control of information has been an important part of political and military conflicts. Following are just a few examples:
 Throughout the Cold War, Western democracies invested time and money in radio broadcasts into communist nations. This well-known campaign was referred to as Radio Free Europe. The goal was to create dissatisfaction among citizens of those nations, hopefully encouraging defection, dissent, and general discontent. Most historians and political analysts agree that this was a success.
Throughout the Cold War, Western democracies invested time and money in radio broadcasts into communist nations. This well-known campaign was referred to as Radio Free Europe. The goal was to create dissatisfaction among citizens of those nations, hopefully encouraging defection, dissent, and general discontent. Most historians and political analysts agree that this was a success. The Vietnam War was the first modern war to which there was strong and widespread domestic opposition. Many analysts believe that opposition was due to the graphic images being brought home via television.
The Vietnam War was the first modern war to which there was strong and widespread domestic opposition. Many analysts believe that opposition was due to the graphic images being brought home via television. Today, the government and military of every nation are aware of how the phrases they use to describe activities can affect public perception. They do not say that innocent civilians were killed in a bombing raid. Rather, they state that there was “some collateral damage.” Governments do not speak of being the aggressor or starting a conflict. They speak of “preemptive action.” Dissenters in any nation are almost always painted as traitors or cowards.
Today, the government and military of every nation are aware of how the phrases they use to describe activities can affect public perception. They do not say that innocent civilians were killed in a bombing raid. Rather, they state that there was “some collateral damage.” Governments do not speak of being the aggressor or starting a conflict. They speak of “preemptive action.” Dissenters in any nation are almost always painted as traitors or cowards.
Public perception is a very important part of any conflict. Each nation wants its own citizens to be totally in support of what it does and to maintain very high morale. High morale and strong support lead to volunteering for military service, public support for funding the conflict, and political success for the nation’s leader. At the same time, you want the enemy to have low morale—to doubt not only their ability to be successful in the conflict but also their moral position relative to the conflict. You want them to doubt their leadership and to be as opposed to the conflict as possible. The Internet provides a very inexpensive vehicle for swaying public opinion.
Web pages are just one facet of disseminating information. Having people post to various discussion groups can also be effective. One full-time propaganda agent could easily manage 25 or more distinct online personalities, each spending time in different bulletin boards and discussion groups, espousing the views that his political entity wants to espouse. These can reinforce what certain Internet news outlets are posting, or they could undermine those postings. They can also start rumors. Rumors can be very effective even when probably false. People often recall hearing something with only a vague recollection of where they heard it and whether it was supported by data.
Such an agent could have one personality that purports to be a military member (it would take very little research to make this credible) and could post information “not seen in newscasts” that would cast the conflict in either a positive or a negative light. She could then have other online personas that entered the discussion who would agree with and support the original position. This would give the initial rumor more credibility. Some people suspect this is already occurring in Usenet newsgroups and Yahoo! discussion boards. Obviously, Usenet and Yahoo! are just two examples. The Internet is replete with various blogs, community sites, boards, and more.
Fyi: Cyber Information Warfare Now
Anyone familiar with Yahoo! news boards (this is just one example; there are certainly many more) has probably noticed an odd phenomenon. At certain times, there will be a flood of posts from anonymous users, all saying essentially the same things—even using the same grammar, punctuation, and phrasing—and all in support of some ideological perspective. These flurries often happen in times when influence of public opinion is important, such as when an election is nearing. Whether or not these postings are coordinated by a well-known or official organization is debatable. However, they are an example of information warfare. One person or group of people attempts to sway opinion by flooding one particular media (Internet groups) with various items advocating one view. If they are lucky, some individuals will copy the text and email it to friends who do not participate in the newsgroups, thus crossing over to another media and spreading opinions (in some cases entirely unfounded) far and wide.
Fyi: Disinformation—A Historical Perspective
While disinformation campaigns are certainly easier to conduct since the advent of mass communication, particularly the Internet, such activities did exist prior to the Internet, or even television. For example, in the weeks leading up the famous D-Day invasion of World War II, the Allied forces used a number of disinformation techniques:
 They created documents and communiqués listing fictitious military units that would invade from an entirely different location than the real invasion was planned.
They created documents and communiqués listing fictitious military units that would invade from an entirely different location than the real invasion was planned. They used Allied double agents to spread similar disinformation to the Germans.
They used Allied double agents to spread similar disinformation to the Germans. A few small groups simulated a large-scale invasion to distract the German army.
A few small groups simulated a large-scale invasion to distract the German army.
Disinformation
Another category of information warfare that is closely related to propaganda is disinformation. It is a given that a military opponent is attempting to gather information about troop movements, military strength, supplies, and so forth. A prudent move would be to set up systems that had incorrect information and were just secure enough to be credible but not secure enough to be unbreakable. An example would be to send an encrypted coded message such that, when the message is decrypted, seems to say one thing, but to those who can complete the code it has a different message. The actual message is “padded” with “noise.” That noise is a weakly encrypted false message, whereas the real message is more strongly encrypted. In this way, if the message is decrypted, there exists a high likelihood that the fake message will be decrypted and not the real one. General Gray, USMC, put it best when he said, “Communications without intelligence is noise; intelligence without communications is irrelevant.”8
8. https://www.powerquotations.com/quote/communications-without-intelligence-is-noise
The goal of any military or intelligence agency is to make certain our communications are clear and that the enemy can only receive noise.
Actual Cases of Cyber Terrorism
Several cases of cyber terrorism have already been mentioned in this chapter. In this section we will briefly look at additional cases. We will examine incidents that occurred between 1996 and 2022. It should be noted that there are voices in the computer security industry that think cyber terrorism or cyber war are simply not realistic scenarios. Marcus Ranum of Information Security magazine states as much in the April 2004 issue. He and others claim that there is no danger from cyber terrorism and that, in fact, “The whole notion of cyberwarfare is a scam.”9 That quotation is quite old, but it illustrates that this is not a new perspective. Unfortunately, actual case studies have shown that this view is simply wrong. However, computer warfare and cyber terrorism have already been used on a small scale. It seems quite plausible that, in a matter of time, it will be seen on a much larger scale.
9. https://taosecurity.blogspot.com/2008/11/response-to-marcus-ranum-hitb-cyberwar.html
Even if you believe that the scenarios outlined in the earlier sections of this chapter are merely the product of an overactive imagination, you should consider that there have already been a few actual incidents of cyber terrorism, although much less severe than the theoretical scenarios. This section examines some of these cases to show you how such attacks have been carried out in the past.
Some of the incidents listed next were reported in testimony before the Special Oversight Panel on Terrorism, Committee on Armed Services, U.S. House of Representatives. Earlier in this chapter, we listed more recent attacks, but these older attacks are important to illustrate just how long this problem has been going on. Some of these cases are quite old, but we move from historical cases to current cases.
 In 1996, a computer hacker allegedly associated with the white supremacist movement temporarily disabled a Massachusetts ISP and damaged part of the ISP’s record-keeping system. The ISP had attempted to stop the hacker from sending out worldwide racist messages under the ISP’s name. The hacker signed off with the threat, “You have yet to see true electronic terrorism. This is a promise.”
In 1996, a computer hacker allegedly associated with the white supremacist movement temporarily disabled a Massachusetts ISP and damaged part of the ISP’s record-keeping system. The ISP had attempted to stop the hacker from sending out worldwide racist messages under the ISP’s name. The hacker signed off with the threat, “You have yet to see true electronic terrorism. This is a promise.” In 1998 ethnic Tamil guerrillas swamped Sri Lankan embassies with 800 emails a day over a 2-week period. The messages read, “We are the Internet Black Tigers and we’re doing this to disrupt your communications.” Intelligence authorities characterized it as the first known attack by terrorists against a country’s computer systems. This is obviously a very old case, but it illustrates how long this sort of thing has been occurring.
In 1998 ethnic Tamil guerrillas swamped Sri Lankan embassies with 800 emails a day over a 2-week period. The messages read, “We are the Internet Black Tigers and we’re doing this to disrupt your communications.” Intelligence authorities characterized it as the first known attack by terrorists against a country’s computer systems. This is obviously a very old case, but it illustrates how long this sort of thing has been occurring. During the Kosovo conflict in 1999, NATO computers were blasted with email bombs and hit with DoS attacks by hacktivists (the name applied to individuals who work for their causes using cyber terrorism) protesting the NATO bombings. In addition, according to reports, businesses, public organizations, and academic institutes received highly politicized virus-laden emails from a range of Eastern European countries. Web defacements were also common. After the Chinese embassy was accidentally bombed in Belgrade, Chinese hacktivists posted messages such as, “We won’t stop attacking until the war stops!” on U.S. government websites.
During the Kosovo conflict in 1999, NATO computers were blasted with email bombs and hit with DoS attacks by hacktivists (the name applied to individuals who work for their causes using cyber terrorism) protesting the NATO bombings. In addition, according to reports, businesses, public organizations, and academic institutes received highly politicized virus-laden emails from a range of Eastern European countries. Web defacements were also common. After the Chinese embassy was accidentally bombed in Belgrade, Chinese hacktivists posted messages such as, “We won’t stop attacking until the war stops!” on U.S. government websites. In August 2010 the United States publicly warned that the Chinese military was targeting American companies as well as government agencies. The United States further warned that the Chinese government was utilizing civilian experts in these attacks. In this report a Chinese computer spying network named GhostNet was revealed.
In August 2010 the United States publicly warned that the Chinese military was targeting American companies as well as government agencies. The United States further warned that the Chinese government was utilizing civilian experts in these attacks. In this report a Chinese computer spying network named GhostNet was revealed. The Shamoon virus was first discovered in 2012, and a variant circulated in 2017. Shamoon acts as spyware but deletes files after it has uploaded them to the attacker. The virus attacked Saudi Aramco workstations, and a group named Cutting Sword of Justice claimed responsibility for the attack. A number of security officials within Saudi Aramco have blamed Iran for this attack. And, like Stuxnet, this virus infected systems other than the intended target.
The Shamoon virus was first discovered in 2012, and a variant circulated in 2017. Shamoon acts as spyware but deletes files after it has uploaded them to the attacker. The virus attacked Saudi Aramco workstations, and a group named Cutting Sword of Justice claimed responsibility for the attack. A number of security officials within Saudi Aramco have blamed Iran for this attack. And, like Stuxnet, this virus infected systems other than the intended target. In 2013 the New York Times reported multiple cyber attacks, all targeting financial institutions within the United States. All appear to have been instigated from Iran.
In 2013 the New York Times reported multiple cyber attacks, all targeting financial institutions within the United States. All appear to have been instigated from Iran. In December 2015 a significant portion of the Ivano-Frankivsk region in Ukraine had no power for approximately 6 hours due to the BlackEnergy malware. The attacks have been attributed to a Russian cyber espionage group named Sandworm.
In December 2015 a significant portion of the Ivano-Frankivsk region in Ukraine had no power for approximately 6 hours due to the BlackEnergy malware. The attacks have been attributed to a Russian cyber espionage group named Sandworm. In 2017 the United States accused Russia of hacking into U.S. systems using the antivirus product Kaspersky. Then in the fall of 2017, Israel claimed that it had hacked Russian spy agencies, and found evidence that the Russians were indeed using Kaspersky as a vehicle for cyber espionage. This is a classic case of everyone seeming to be hacking into everyone else.
In 2017 the United States accused Russia of hacking into U.S. systems using the antivirus product Kaspersky. Then in the fall of 2017, Israel claimed that it had hacked Russian spy agencies, and found evidence that the Russians were indeed using Kaspersky as a vehicle for cyber espionage. This is a classic case of everyone seeming to be hacking into everyone else. It has been alleged that in October 2018, the United States launched an operation named Synthetic Theology to identify Russian agents who were interfering in the Macedonian and Ukrainian elections. The entire operation is said to have been a cyber operation.
It has been alleged that in October 2018, the United States launched an operation named Synthetic Theology to identify Russian agents who were interfering in the Macedonian and Ukrainian elections. The entire operation is said to have been a cyber operation. In November 2018 German security officials announced that a Russia-linked group had targeted the email accounts of several members of the German parliament, as well as the German military and several embassies.
In November 2018 German security officials announced that a Russia-linked group had targeted the email accounts of several members of the German parliament, as well as the German military and several embassies. In December 2018 the United States, in coordination with Australia, Canada, the UK, and New Zealand, accused China of conducting a 12-year campaign of cyber espionage targeting the intellectual property and trade secrets of companies across 12 countries. The announcement was tied to the indictment of two Chinese hackers associated with the campaign.
In December 2018 the United States, in coordination with Australia, Canada, the UK, and New Zealand, accused China of conducting a 12-year campaign of cyber espionage targeting the intellectual property and trade secrets of companies across 12 countries. The announcement was tied to the indictment of two Chinese hackers associated with the campaign. In January 2019 hackers associated with Russian intelligence services were found to have targeted the Center for Strategic and International Studies.
In January 2019 hackers associated with Russian intelligence services were found to have targeted the Center for Strategic and International Studies. In February 2019 European aerospace company Airbus revealed that it had been targeted by Chinese hackers who stole the personal and IT identification information of some of its European employees.
In February 2019 European aerospace company Airbus revealed that it had been targeted by Chinese hackers who stole the personal and IT identification information of some of its European employees. Beginning in March 2019, it was reported that the United States began persistent cyber operations against Russia’s power grid.
Beginning in March 2019, it was reported that the United States began persistent cyber operations against Russia’s power grid.
In March 2021 it was reported that Russian hackers targeted Lithuanian government officials with spyware. The group, named APT29, is alleged to have carried out a variety of attacks related to cyber espionage.
The now infamous Colonial Pipeline attack of May 2021 is an important one in the history of cyber warfare and terrorism. This pipeline controls approximately 45% of the oil that services the East Coast of the United States. The attack forced the company to turn off the pipeline and eventually to pay the $5 million ransom. This would be characterized as cyber terrorism.
In the buildup to the 2022 Russian invasion of Ukraine, there were multiple cyber attacks on Ukraine. This is an example of cyber warfare being used to augment kinetic warfare.
The good news is that most of these attacks caused little damage and were clearly the work of amateurs. However, it may only be a matter of time before more damaging attacks are perpetrated by far more skilled cyber terrorists. Yet it is clear that cyber terrorism, at least on a low-intensity scale, is already beginning. These warnings can be heeded and the issues taken seriously, or they can simply be ignored until disaster strikes. In addition, there are other items of concern, such as the recruiting of terrorists via the Internet, which we will look at later in this chapter. Here are some additional actual cases of spying.
 In June 2000, Russian authorities arrested a man they accused of being a CIA-backed hacker. As shown in Figure 12.3, this man allegedly hacked into systems of the Russian Domestic Security Service (FSB) and gathered secrets that he then passed on to the CIA. This example illustrates the potential for a skilled hacker using knowledge to conduct espionage operations. This type of espionage is likely occurring much more often than is reported in the media, and many such incidents may never come to light.
In June 2000, Russian authorities arrested a man they accused of being a CIA-backed hacker. As shown in Figure 12.3, this man allegedly hacked into systems of the Russian Domestic Security Service (FSB) and gathered secrets that he then passed on to the CIA. This example illustrates the potential for a skilled hacker using knowledge to conduct espionage operations. This type of espionage is likely occurring much more often than is reported in the media, and many such incidents may never come to light.

Figure 12.3 BBC report on an arrested hacker.
 Operation Ababil was a 2012 hacktivist-led effort that executed DoS attacks on the New York Stock Exchange and various banks. The hacktivist group Qassam Cyber Fighters claimed credit.
Operation Ababil was a 2012 hacktivist-led effort that executed DoS attacks on the New York Stock Exchange and various banks. The hacktivist group Qassam Cyber Fighters claimed credit. Perhaps most disconcerting was the 2015 breach of the U.S. Office of Personnel Management. It is estimated that over 21 million records were stolen, including detailed background checks of persons with security clearances.
Perhaps most disconcerting was the 2015 breach of the U.S. Office of Personnel Management. It is estimated that over 21 million records were stolen, including detailed background checks of persons with security clearances.
It is also frightening to consider reports that our satellites, used for communication, weather, and military operations, could be vulnerable to hacking. Such vulnerabilities seem rather unlikely to be exploited simply because of the skill level required to execute such an attack. As previously mentioned, hacking/cracking is like any other human endeavor in that, based on the law of averages, most people are mediocre. The level of skill required to compromise security on a satellite system is far greater than that required to compromise the security of a website. Of course, that does not mean that such an attack is impossible, but simply that it is less likely.
Future Trends
By carefully analyzing what is occurring presently in cybercrime and cyber terrorism along with the recent history of that field, we can extrapolate and make reasonably accurate estimates about what trends will dominate in the near future. This section considers machine learning/artificial intelligence and then both positive and negative trends.
Machine Learning/Artificial Intelligence
With the growth of machine learning (ML) and artificial intelligence (AI), it should come as no surprise that ML/AI will also impact cyber warfare. Machine learning is already having an effect on hacking. And cyber warfare is simply the coordinated use of hacking attacks by a nation-state or an international threat actor to achieve political goals. As one example of machine learning improving hacking attacks, an article published in August 2021 demonstrated that AI wrote better, more believable phishing emails than did humans.10
10. https://www.wired.com/story/ai-phishing-emails/
A 2019 article published in ZDNet, “Adversarial AI: Cybersecurity Battles Are Coming,” outlines the coming use of AI and ML in offensive operations, with the possibility of attacks completely executed by AI.11
11. https://www.zdnet.com/article/adversarial-ai-cybersecurity-battles-are-coming
Given that malware is the weapon of choice in cyber warfare and that cyber warfare is a part of nation-state national security policy, a natural next step is the application of machine learning to offensive cyber capabilities. One significant focus is on the use of machine learning in the development and deployment of weaponized malware.
Implementing machine learning directly in malware would cause the malware to consume substantial resources on the target and be more likely to be discovered. Machine learning algorithms could be offloaded to a command and control server. The various instances of a given type of malware would communicate data to the command and control center. That data would be subjected to machine learning in order to improve the efficacy of the currently deployed malware. This would function in much the same way as botnet communications with the command and control center.
In addition, machine learning algorithms could be used in the development and testing of weaponized malware. This would make the malware more efficient and more effective. Machine learning could also be used to enhance vulnerability discovery to improve the efficacy of attacks.
Positive Trends
It does seem that various governments are beginning to take notice of the problem of cyber terrorism and are taking some steps to ameliorate the dangers. For example, then Senator John Edwards (D-NC) proposed two bills in 2002 aimed at allocating $400 million for cybersecurity efforts. The first measure, called the Cyberterrorism Preparedness Act of 2002, a portion of which is shown in Figure 12.4, allocated $350 million over 5 years for improving network security, first for federal systems and then for the private sector. It also created a group assigned to gather and distribute information about the best security practices. The Cybersecurity Research and Education Act of 2002, a portion of which is shown in Figure 12.5, provided $50 million over 4 years for fellowships that were used to train IT specialists in cybersecurity. It also called for the creation of a web-based university where administrators could get updated training. The Cybersecurity Research and Education Act was passed and became Public Law 107-305. The Cyberterrorism Preparedness Act of 2002 was not passed. However, many of its goals were addressed by the PATRIOT Act.

Figure 12.4 The Cyberterrorism Preparedness Act of 2002.

Figure 12.5 The Cybersecurity Research and Education Act of 2002.
Title VIII of the U.S. PATRIOT Act specifically deals with cyber terrorism. The number of cyber attacks included in its definition of cyber terrorism is expansive, including attempts to damage or alter medical records and releasing a virus in a target system. Penalties are also clearly set out.
In 2010 the U.S. Department of Defense established the U.S. Cyber Command (USCYBERCOM). This unit, based in Ft. Meade, Maryland, is a joint task force representing components of all portions of the U.S. Armed Forces.
In 2011 the Dutch Ministry of Defense formulated and published a cyber strategy that included a joint cyber defense military unit. It also established an offensive and defensive cyber force named Defence Cyber Command (DCC).
In 2013 Germany revealed that it had a Computer Network Operations unit. Some public reports suggested that the unit was rather small, with about 60 members, but the nature of the unit makes it difficult to get accurate numbers. It was reported that the German intelligence agency (Federal Intelligence Service in English, Bundesnachrichtendienst in German, commonly known as simply BND) began in 2013 to hire a number of hackers.
More and more nations are treating cyber defense like any other area of defense and establishing the appropriate military and intelligence organizations to deal with it.
In the second edition of this book, I stated, “It is unreasonable to ask every police department to have a computer-crime specialist on staff. However, state-level investigative agencies should be able to hire such personnel.” I am thrilled to report that many positive trends in this area have exceeded my expectations. First, many law enforcement agencies, even small local agencies, do indeed now have cyber forensic detectives. There are also a number of cybercrime task forces that bring together state, local, and federal resources. For example, the U.S. Secret Service had established Electronic Crimes Task Forces around the country that bring together state, local, and federal resources to combat cybercrime and terrorism. The Department of Homeland Security has set up regional Fusion Centers to assist in coordinating the sharing of information between intelligence agencies and law enforcement agencies, at all levels.
Negative Trends
Unfortunately, as legislative bodies become aware of the problem of cyber terrorism and focus resources on the issue, the threats continue to grow. A paper commissioned by the Rand Corporation noted that even groups such as Al-Qaeda—which have not used cyber terrorism as one of their attack modalities as of this writing—have used Internet and computer technology resources to plan their various activities and coordinate training.
As early as 2000, the U.S. General Accounting Office warned of several possible cyber terrorism scenarios. As shown in Figure 12.6, these concerns focused on lethal attackers and possible attack scenarios in which the computer-controlled machinery in a chemical plant was altered in order to cause a release of toxic chemicals into the environment. This could be done in a variety of ways, including simply causing the machinery to drastically overproduce, overheat, or perhaps prematurely shut down equipment. The panel also contemplated scenarios in which water and power supplies were interrupted or compromised via computer systems. In essence, the focus was on the potential for massive casualties as a direct result of a cyber-based attack rather than the economic damage on which this chapter’s scenarios tend to focus.
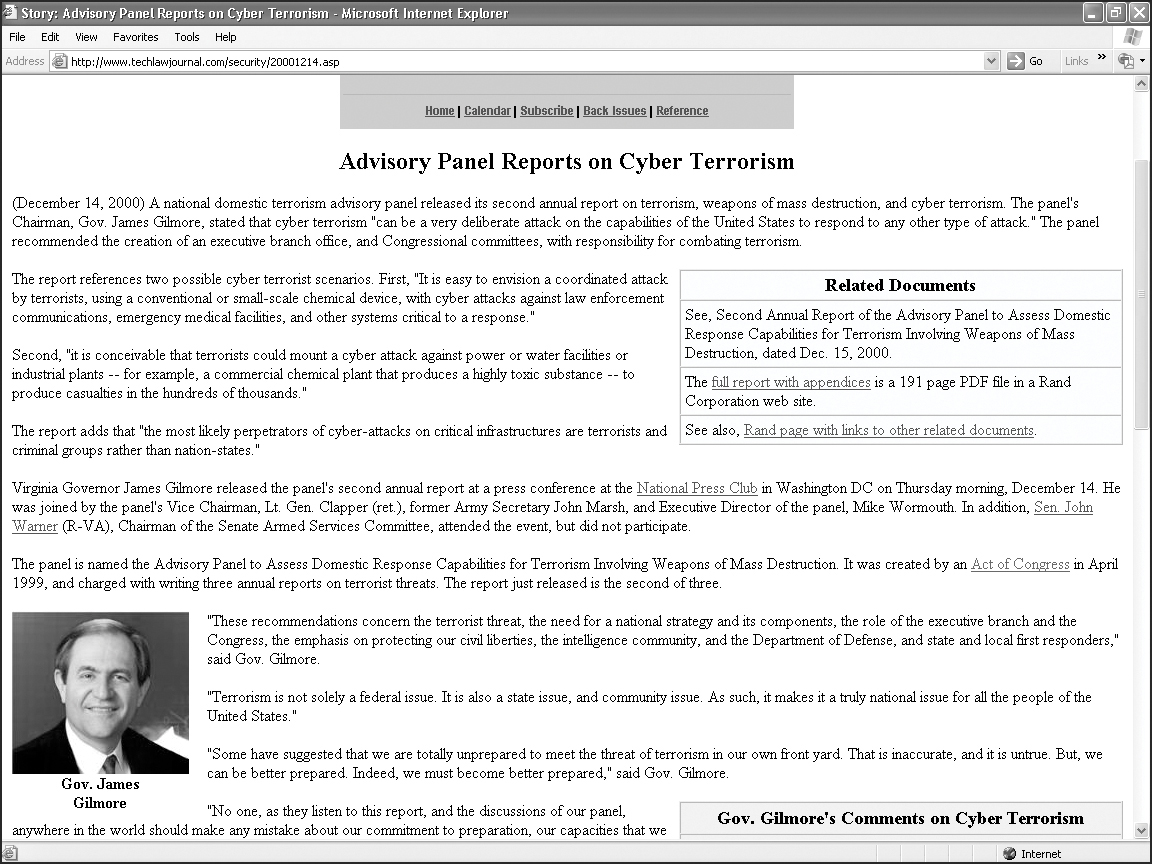
Figure 12.6 Rand report on cyber terrorism.
Defense Against Cyber Terrorism
As the world becomes more dependent on computer systems, the danger of cyber terrorism will grow. Clearly, there must be a much stronger emphasis on computer security. In addition to the basic security measures already recommended in this book, these are some recommendations for preparing for and protecting systems against cyber terrorism:
 Major academic institutions must begin dedicated research and academic programs that are devoted solely to computer security. Fortunately, since earlier editions of this book, that has changed. We now have a wide spectrum of cybersecurity related degrees.
Major academic institutions must begin dedicated research and academic programs that are devoted solely to computer security. Fortunately, since earlier editions of this book, that has changed. We now have a wide spectrum of cybersecurity related degrees. Computer crime must be treated far more seriously, with stronger punishments and more active investigation of suspected crimes. This has also improved since the earlier editions of this book.
Computer crime must be treated far more seriously, with stronger punishments and more active investigation of suspected crimes. This has also improved since the earlier editions of this book. Rather than train law enforcement officers in basic computer crime, I have always recommended that it is more appropriate to train highly skilled computer professionals in law enforcement. To adequately combat cyber terrorism, one absolutely must first and foremost be a highly qualified computer expert.
Rather than train law enforcement officers in basic computer crime, I have always recommended that it is more appropriate to train highly skilled computer professionals in law enforcement. To adequately combat cyber terrorism, one absolutely must first and foremost be a highly qualified computer expert. An emergency reporting system may need to be implemented so that security professionals from various industries have a single source where they can report attacks on their systems and can view the issues with which other security professionals are dealing. This could enable security professionals as a group to more quickly recognize when a coordinated attack is occurring. There are currently many diverse reporting and communications platforms.
An emergency reporting system may need to be implemented so that security professionals from various industries have a single source where they can report attacks on their systems and can view the issues with which other security professionals are dealing. This could enable security professionals as a group to more quickly recognize when a coordinated attack is occurring. There are currently many diverse reporting and communications platforms.
In addition, you can make some additions to and variations on your existing security measures. For example, you should have a recovery process in place so that data can be quickly recovered should someone delete important files. You should also, as recommended in Chapter 9, assess what data is of most value and focus your attention on that data. But, as this chapter points out, you must consider how data that might at first appear to be of little value may actually reveal more information about you personally or your company than is prudent.
Terrorist Recruiting and Communication
The Internet is an incredible communication tool, and it serves as a communications and recruiting tool for terrorist groups. Terrorists use Internet chat rooms for communication and planning. It is easy to set up a private chat room or bulletin board. Members of a terrorist group can then use public terminals to log in to that chat room or bulletin board and discuss plans. The terror network in the Netherlands that was responsible for the killing of filmmaker Theo van Gogh met regularly on Yahoo! to devise and discuss its plans. This is just one example of a terrorist group using the Internet to plan attacks.
The Internet’s ubiquitous nature enables terrorists who are geographically separated to communicate and coordinate. Websites allow terrorist groups to spread propaganda, raise funds, and recruit new members. And, as discussed, the Internet will even enable extremist groups to inspire lone individuals to act on their own but in the interests of the group.
It is also a fact that various terrorist groups have been using social media for recruiting purposes. Social media can be used to locate and entice those likely to be sympathetic to a terrorist organization. Then a grooming process can occur (not unlike that used by pedophiles). If needed, the terrorist group can even provide the new terrorist with training on topics like bomb making via the Internet. The advantage to the terrorist organization is that if the fledgling terrorist is caught, he has no knowledge of the terrorist organization. He has never even met any of the members, so he cannot give any information.
TOR and the Dark Web
TOR was mentioned in Chapter 6, “Techniques Used by Hackers,” and is discussed again here due to its connection to the topics of this chapter. TOR, or The Onion Router, may not seem like a military application of cryptography; however, it is appropriate to cover this topic in this chapter for two reasons:
 The TOR project is based on an earlier Onion Routing protocol developed by the U.S. Navy specifically for military applications. So TOR is an example of military technology being adapted to civilian purposes.
The TOR project is based on an earlier Onion Routing protocol developed by the U.S. Navy specifically for military applications. So TOR is an example of military technology being adapted to civilian purposes. TOR is used by privacy advocates every day. But it is also used by terrorist groups and organized criminals.
TOR is used by privacy advocates every day. But it is also used by terrorist groups and organized criminals.
TOR consists of thousands of volunteer relays spread around the world. Each relay uses encryption to conceal the origin and even final destination of the traffic passing through it. Each relay is only able to decrypt one layer of the encryption, revealing the next stop in the path. Only the final relay is aware of the destination, and only the first relay is aware of the origin. This makes tracing network traffic practically impossible.
The basic concepts of onion routing were developed at the U.S. Naval Research Laboratory in the mid-1990s and later refined by the Defense Advanced Research Projects Agency (DARPA). The goal was to provide secure intelligence communication online.
Onion routers communicate using TLS (covered in depth in Chapter 13, “Cyber Detective”) and ephemeral keys. Ephemeral keys are so called because they are created for one specific use and then destroyed immediately after that use. Onion routers often use 128-bit AES as the symmetric key.
While the TOR network is a very effective tool for maintaining privacy, it has also become a tool for hiding criminal activity. Markets on the TOR network are used expressly to sell and distribute illegal products and services. Stolen credit card numbers and other financial data are common products on TOR markets. The images in Figures 12.7 and 12.8 give you some insight into what is on the Dark Web. These are actual screenshots. It must be noted that neither I nor the publisher endorses these sites. In fact, I work with law enforcement regularly and am opposed to what is done on these websites. However, if you are going to learn cybersecurity, you should know what is out there.
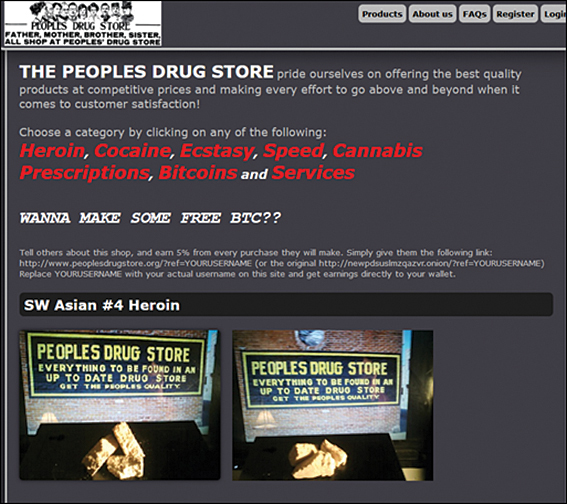
Figure 12.7 Drugs on the Dark Web.
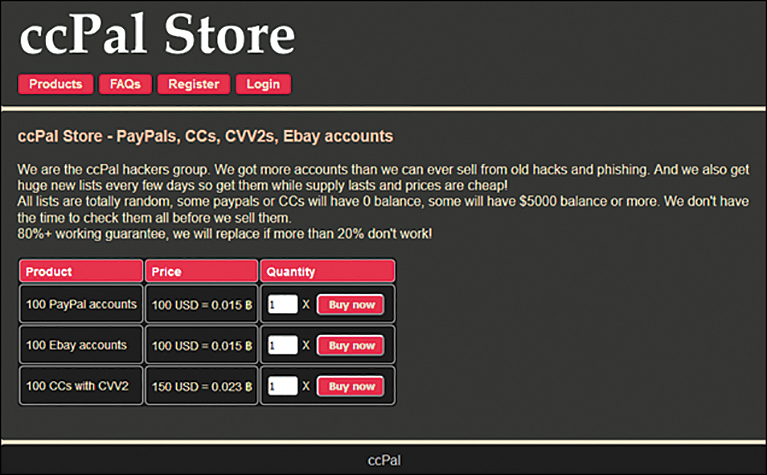
Figure 12.8 Accounts for sale.
Are some sites on the Dark Web fake? Of course. Some are simply scamming people out of their money and not delivering the nefarious service or money. But many are real—particularly those selling stolen credit cards, drugs, and child pornography.
In 2015 the founder of Silk Road, Ross Ulbricht, the most well-known of the TOR markets, was sentenced to life in prison. Many people on various news outlets have claimed that this sentence is draconian. And one can certainly argue the merits of any sentence. But allow me to give you food for thought. Silk Road was not simply a venue for privacy or even for marijuana exchanges. It became a hub for massive drug dealing, including heroin, cocaine, and meth. It was also used to traffic in arms, stolen credit cards, child pornography, and even murder for hire. The venue Mr. Ulbricht created was a hub for thousands of very serious felonies.
Summary
It is clear that there are a variety of ways in which cyber terrorist attacks could be used against any industrialized nation. Many experts, including various government panels, senators, and terrorism experts, believe that cyber terrorism is a very real threat. It is more important than ever before to be extremely vigilant in securing your computer systems. You must also look beyond the obvious uses of data and consider how someone with an intent to harm or cause economic hardship could use seemingly unimportant information. In the exercises at the end of this chapter, you will have a chance to explore various cyber terrorism and information warfare threats.
Test Your Skills
Multiple Choice Questions
1. What is the most likely damage from an act of cyber terrorism?
A. Loss of life
B. Compromised military strategy
C. Economic loss
D. Disrupted communications
2. Which of the following is not an example of financial loss due to cyber terrorism?
A. Lost data
B. Transfer of money from accounts
C. Damage to facilities including computers
D. Computer fraud
3. Which of the following military/government systems would most likely be the target of a successful computer hack?
A. The most sensitive systems of the CIA
B. Nuclear systems at NORAD
C. Low-security logistical systems
D. Military satellite control systems
4. Which of the following might be an example of domestic cyber terrorism?
A. Sasser virus
B. Mimail virus
C. Sobig virus
D. MyDoom virus
5. What differentiates cyber terrorism from other computer crimes?
A. It is organized.
B. It is politically or ideologically motivated.
C. It is conducted by experts.
D. It is often more successful.
6. Which of the following is a political group that has already used the Internet for political intimidation?
A. Internet Black Tigers
B. Al-Qaeda
C. Mafia
D. IRA
7. What is information warfare?
A. Spreading disinformation
B. Spreading disinformation or gathering information
C. Gathering information
D. Spreading disinformation or secure communications
8. Which of the following would most likely be considered an example of information warfare?
A. Radio Free Europe during the Cold War
B. Radio political talk show
C. Normal news reports
D. Military press releases
9. Which of the following is a likely use of Internet newsgroups in information warfare?
A. To spread propaganda
B. To monitor dissident groups
C. To send encoded messages
D. To recruit supporters
10. Sending a false message with weak encryption, intending it to be intercepted and deciphered, is an example of what?
A. Poor communications
B. Need for better encryption
C. Disinformation
D. Propaganda
11. Which of the following best describes the communication goal of any intelligence agency?
A. To send clear communications to allies and noise to all other parties
B. To send clear communications to allies and noise only to the enemy
C. To send disinformation to the enemy
D. To send clear communications to allied forces
12. Which of the following conflicts had a cyber warfare component?
A. 1989 invasion of Panama
B. 1990 Kosovo crisis
C. 1990 Somalia crisis
D. Vietnam War
13. Which of the following agencies has allegedly had one of its cyber spies actually caught?
A. NSA
B. KGB
C. FBI
D. CIA
14. Which of the following is a cyber attack that would likely cause loss of life?
A. Disruption of banking system
B. Disruption of water supply systems
C. Disruption of security systems
D. Disruption of chemical plant control systems
Exercises
EXERCISE 12.1: Finding Information Warfare
Pick a current political topic.
Track that topic on multiple bulletin boards, Yahoo! newsgroups, or blogs.
Look for signs that might indicate an organized effort to sway opinion or information warfare. This might include posts allegedly made by separate individuals that have highly similar points, grammar, and syntax.
Write a brief essay discussing what you found and why you think it constitutes information warfare.
EXERCISE 12.2: Cyber Terrorism Threat Assessment
Pick some activist group (political or ideological) that you find intriguing.
Using only the Web, gather as much information about that organization as you can.
Write a brief dossier on that group, including what you think is the likelihood that such a group would engage in information warfare or cyber terrorism and why.
EXERCISE 12.3: Finding Information Policies
Using the Web or other resources, locate several examples of organizational policies regarding information dissemination.
Find points common to all such policies.
Write a brief essay explaining why these policies might be related to either propagating or preventing information warfare.
EXERCISE 12.4: How Companies Defend Against Cyber Terrorism
Interview the IT staff of a company to find out whether they take information warfare or cyber terrorism directly into account when they are securing their systems.
Find out what steps they take to protect their company’s systems from these threats.
Write a brief essay explaining what you have found out.
EXERCISE 12.5: Pulling It All Together
Pulling together what you have learned from previous chapters, what information can you apply to the protection of a system against cyber terrorism or information warfare? Write a brief outline of the steps you would take to secure a system against these threats.
Projects
PROJECT 12.1: Computer Security and Cyber Terrorism
Consider the various security measures you have examined thus far in this book. Given the threat of cyber terrorism, write an essay discussing how those methods might relate to cyber terrorism. Also discuss whether or not the threat of computer-based terrorism warrants a higher security standard than you might have otherwise used and explain why or why not.
PROJECT 12.2: The Law and Cyber Terrorism
Note: This is meant as a group project.
Using the Web or other resources, find and examine laws that you feel relate to cyber terrorism. Then write an essay describing legislation you believe needs to be written regarding cyber terrorism. Essentially, your group should act as if it were technical advisors to a congressional committee drafting new legislation.
PROJECT 12.3: Cyber Terrorism Scenario
Considering any of the theoretical cyber terrorism scenarios presented in this chapter, write a security and response plan that you feel addresses that scenario and protects against that specific threat.
Case Study
Jane Doe is the network administrator responsible for security for a small defense contractor. Her company handles some low-level classified material. She has implemented a strong security approach that includes the following:
 A firewall has all unneeded ports closed.
A firewall has all unneeded ports closed. Virus scanners are placed on all machines.
Virus scanners are placed on all machines. Routers between network segments are secured.
Routers between network segments are secured. All machines have the operating systems patched monthly.
All machines have the operating systems patched monthly. Passwords are long and complex, and they are required to be changed every 90 days.
Passwords are long and complex, and they are required to be changed every 90 days.
What other recommendations would you make to Jane Doe? Explain the reasons for each of your recommendations.
