Chapter 11
Troubleshooting Connectivity Issues
COMPTIA SERVER+ EXAM OBJECTIVES COVERED IN THIS CHAPTER:
- ✓ 7.4 Given a scenario, effectively diagnose network problems, selecting the appropriate tools and methods
- Common problems (Internet connectivity failure, email failure, resource unavailable, DHCP server misconfigured, nonfunctional or unreachable, destination host unreachable, unknown host, default gateway misconfigured, failure of service provider, cannot reach by host name/FQDN)
- Causes of common problems (improper IP configuration, VLAN configuration, port security, improper subnetting, component failure, incorrect OS route tables, bad cables, firewall [misconfiguration, hardware failure, software failure], misconfigured NIC, routing/switch issues, DNS and/or DHCP failure, misconfigured hosts file, IPv4 vs. IPv6 misconfigurations)
- Networking tools (ping, tracert/traceroute, ipconfig/ifconfig, nslookup, net use/mount, route, nbtstat, netstat)
- ✓ 7.6 Given a scenario, effectively diagnose security issues, selecting the appropriate tools and methods
- Common problems (file integrity issue, privilege escalation, applications will not load, can’t access network file/shares, unable to open files, excessive access, excessive memory utilization)
- Causes of common problems (open ports, active services, inactive services, intrusion detection configurations, antimalware configurations, local/group policies, firewall rules, misconfigured permissions, virus infection, rogue processes/services)
- Security tools (port scanners, sniffers, cipher, checksums, telnet client, antimalware)
 When users are unable to connect to the resources they need, they can’t do their job. There are two main sources of connectivity problems. Network issues mean that a misconfigured or malfunctioning device exists somewhere between users and their resources. Security issues mean that a security feature is either correctly or incorrectly denying the user access to the resources. In this chapter, we’ll discuss the diagnosis of both of these issues.
When users are unable to connect to the resources they need, they can’t do their job. There are two main sources of connectivity problems. Network issues mean that a misconfigured or malfunctioning device exists somewhere between users and their resources. Security issues mean that a security feature is either correctly or incorrectly denying the user access to the resources. In this chapter, we’ll discuss the diagnosis of both of these issues.
Diagnosing Network Problems
Users cannot access a resource if a clear and valid path in the network does not exist between their device and the device holding the resource. This means that any network connectivity issue could exist in a number of places between the two. It could be that one of the two end devices is misconfigured, or the problem could be related to one of the infrastructure devices between them (switches and routers). In this section we’re going to first look at common network issues and error messages and then follow that discussion up with possible solutions. Finally, we’ll look at tools that can aid you in identifying these issues.
Common Problems
As you address networking issues, you’ll find a number of common problems seem to appear frequently. The users may not always describe the issues in these terms, but you will learn over time which of these issues are possible causes of their dilemma.
Resource Unavailable
Network problems, usually manifesting themselves as an inability to connect to resources, can arise from many different sources. This section discusses some common symptoms of networking issues. For many of the issues we will cover, you may find that the user simply has no connectivity. This is as good a time as any to talk about general network troubleshooting for a single device.
No Connectivity
When no connectivity can be established with the network, your troubleshooting approach should begin at the Physical layer and then proceed up the OSI model. As components at each layer are eliminated as the source of the problem, proceed to the next higher layer. A simple yet effective set of steps might be as follows:
- Check the network cable to ensure it is the correct cable type (crossover or straight-through) and that it is functional. If in doubt, try a different cable.
- Ensure that the NIC is functional and the TCP/IP protocol is installed and functional by pinging the loopback address (127.0.0.1 in IPv4 or ::1 in IPv6). If required, install or reinstall TCP/IP and/or replace or repair the NIC.
- Check the local IP configuration and ensure that the IP address, subnet mask, and gateway are correct. If the default gateway can be pinged, the computer is configured correctly for its local network and the problem lies beyond the router or with the destination device. If pings to the gateway are unsuccessful, ensure that the IP configurations of the router interface and the computer are compatible and in the same subnet.
When dealing with a wireless network, ensure that the wireless card is functional. The wireless card is easily disabled with a keystroke on a laptop and should be the first thing to check. If the network uses a hidden SSID, ensure that the station in question is configured with the correct SSID.
APIPA/Link Local Addresses
Automatic Private IP Addressing (APIPA) is a TCP/IP feature Microsoft added to its operating systems. If a DHCP server cannot be found, the clients automatically assign themselves an IP address, somewhat randomly, in the 169.254.x.x range with a subnet mask of 255.255.0.0. This allows them to communicate with other hosts that have similarly configured themselves, but they will be unable to connect to the Internet or to any machines or resources that have DHCP-issued IP addresses.
If the network uses DHCP for IP configuration and the computer with the connectivity issue has an APIPA address, the problem is one of these three things:
- The DHCP server is out of IP addresses.
- The DHCP server is on the other side of a router and there is no functional DHCP relay present or no IP helper address configured on the router—all of which is to say the DHCP request is not reaching the DHCP server.
- The computer has a basic connectivity issue preventing it from connecting to the network (see the sections, “Limited connectivity, Local connectivity and Intermittent connectivity” later in this chapter.)
In Chapter 2, “Installing and Configuring Servers,” you learned about a type of IPv6 address called a link local address that in many ways is like an APIPA address in that the device will generate one of these addresses for each interface with no intervention from a human, as is done with APIPA. The scope of the address is also the same; it is not routable and is good only on the segment where the device is located.
However, as is the case with APIPA addresses, if two devices that are connected to the same segment generate these addresses, they will be in the same network, and the two devices will be able to communicate. This is because the devices always generate the address using the same IPv6 prefix (the equivalent of a network ID in IPv4), which is fe80::/64. The reminder of the address is created by spreading the 48-bit MAC address across the last 64 bits, yielding an IPv6 address that looks like the following one:
FE80::2237:06FF:FECF:67E4/64Limited Connectivity
In some cases, the computer has connectivity to some but not all resources. When this is the case, issues that may reside on other layers of the OSI model should come under consideration. These include the following:
Authentication Issues Does the user have the permission to access the resource?
DNS Issues You may be able to ping the entire network using IP addresses, but most access is done by name, not IP address. If you can’t ping resources by name, DNS is not functional, meaning either the DNS server is down or the local machine is not configured with the correct IP address of the DNS server. If recent changes have occurred in the DNS mappings or if your connection to the destination device has recently failed because of a temporary network issue that has been solved, you may need to clear the local DNS cache using the ipconfig/flushdns command.
Remote Problem Don’t forget that establishing a connection is a two-way street, and if the remote device has an issue, communication cannot occur. Always check the remote device as well. Any interconnecting device between the computer and resource, such as a switch or router, should also be checked for functionality.
Local Connectivity
When a computer can communicate only on its local network or subnet, the problem is usually one of the following:
Incorrect Subnet Mask Sometimes an incorrect mask will prevent all communication, but in some cases it results in successful connections locally but not remotely (outside the local subnet). The subnet mask value should be the same mask used on the router interface connecting to the local network.
Incorrect Default Gateway Address If the computer cannot connect to the default gateway, it will be confined to communicating with devices on the local network. This IP address should be that of the router interface connecting to the local network.
Router Problem If all users on the network are having connectivity problems, you likely have a routing issue that should be escalated to the proper administrators.
Intermittent Connectivity
When a connectivity issue comes and goes, it can be a hardware issue or a software issue. Check the following hardware components for functionality:
Network Cable A damaged cable can cause intermittent connectivity.
Network Interface Card If the NIC is not properly seated or has worked its way partially out of its slot, it can cause connections that come and go.
Interference On a wireless network, cordless phones, microwave ovens, and other wireless networks can interfere with transmissions. Also, users who stray too far from the access point can experience a signal that comes and goes.
The following are software issues that can cause intermittent connectivity:
DHCP Issues When the DHCP server is down or out of IP addresses, the problem will not manifest itself to those users who already have an IP address until their lease expires and they need a new address. In this case, some users will be fine and others will not, and then users who were fine earlier in the day may have problems later when their IP address lease expires.
DNS Problems If the DNS server is down or malfunctioning, it will cause problems for DNS clients who need name resolution requests answered. For users who have already connected to resources in the last hour before the outage, connectivity to those resources will still be possible until the name-to–IP address mapping is removed from the client DNS resolver cache.
IP Conflict
IP address conflicts are somewhat rare when DHCP is in use, but they can still happen. DHCP servers and clients both check for IP duplication when the DHCP client receives an IP address, but the process doesn’t always work. Moreover, if someone with a statically configured IP address connects to the network with the same address as another machine, a conflict will exist.
Regardless of how the conflict occurs, it must be resolved because until it is, one or possibly both computers with the same address will not be able to network. You can determine the MAC address of the computer with which you are experiencing the conflict by using the ping command followed by the arp -a command. In Exercise 11.1 you will identify an IP address conflict.
Slow Transfer Speeds
Slow transmission on the network can be caused by hardware and software issues. Some of the physical issues that can cause slow performance are as follows:
Interference Both wireless and wired networks can be affected by interference from electromagnetic interference (EMI) and radio frequency interference (RFI). EMI will degrade network performance. This can be identified by the poor performance present. Be sure to run cables around (not over) ballasts and other items that can cause EMI. RFI is a similar issue introduced by radio waves. Wireless networks suffer even more from both of these issues.
Incorrect Cabling The network can go only as fast as its weakest link. Using CAT3 cabling, for example, will only allow the device using that cable to operate at 10 Mbps even if its network cards are capable of 10 Gbps.
Malfunctioning NIC Network interface cards (NICs) can malfunction and cause a broadcast storm. These broadcast packets fill the network with traffic that slows performance for all. Use a protocol analyzer to determine the MAC address of the offending computer.
From a software standpoint, the following issues can result in less-than-ideal performance:
Router Misconfiguration If the router is not configured correctly, it can cause slow performance because of less-than-optimal routing paths. Escalate the issue to the appropriate administrators.
Switch Misconfiguration An improperly implemented redundant switch network can result in switching loops that cause slow performance. Escalate the issue to the appropriate administrators.
Low RF Signal
In a wireless network, the signal coming from the access point has a distance limit. With some variation by standard, this is about 300 feet. However, this distance is impacted by obstructions and interference in the area. The WLAN design should include a site survey that identifies these issues and locates access points (APs) and antenna types in such a way as to mitigate these effects.
It is also useful to know that APs and some client radios have a setting to control signal strength. It is not a normal practice to change the setting in a laptop wireless card, but it may be necessary to change the transmit level on an AP. In many cases, it is actually beneficial to reduce the transmit level of an AP in situations where it is interfering with other APs in your network or you want to limit the range of the signal to prevent it from leaving the building. This is especially true in high-density areas where several APs are collocated in the same area for increased throughput.
SSID Not Found
In an 802.11 WLAN, the service set identifier (SSID) is used as a both a network name and in some cases the magic word that allows access to the network. One of the ways you can increase the security of a WLAN (not sufficient in and of itself but a good addition to a layered approach to WLAN security) is to “hide” the SSID. This is also referred to as disabling SSID broadcast. This is done by setting the access point to not list the SSID in the beacon frames. These frames contain the information that is used to populate the list of available wireless networks when you “scan” for wireless networks on your wireless device.
The reason this doesn’t constitute real security is that the SSID is only removed from the beacon frames, which are used by stations to locate available networks. The SSID is not removed from many other frame types, and a hacker can use a wireless sniffer to capture those frames and learn the SSID.
When the SSID is hidden, the only way a device can connect to the WLAN is to be configured with a profile that includes the SSID of the WLAN. While every operating system is slightly different, to do this in Windows 8.1, you follow these steps:
- Open the Network and Sharing Center, as shown in Figure 11.3.
- Select Set Up A New Connection Or Network, opening the page shown in Figure 11.4.
- Select the option Manually Connect To A Wireless Network and click Next, opening the page shown in Figure 11.5.
- Complete the network name, security type, encryption type, and security key; check the box Connect Even If The Network Is Not Broadcasting; and click Next. Now the profile is complete, and you should be able to connect to the “hidden” network. To make it easier for the user, you may also want to check the box Start This Connection Automatically.

Figure 11.3 Network and Sharing Center

Figure 11.4 Set Up A New Connection Or Network

Figure 11.5 Manually connecting to a wireless network
Internet Connectivity Failure
When users cannot connect to the Internet, you will hear about it and soon. This issue can have a number of sources, such as the following:
- The IP configuration of the user’s computer
- The IP configuration of the user’s default gateway or router
- The IP configuration of any routers that stand between the gateway and the Internet
- The DNS server
- The ISP
- The DHCP server
Each of these potential sources will yield specific clues that may indicate their involvement. Some of these clues will be covered in the sections that follow. It is always helpful to first determine the scope of the issue as that may eliminate some possibilities. If the user is the only one having the issue, then it is probably the IP configuration of that user’s device (or malfunctioning hardware on the device). In that case, check for the correct IP address, subnet mask, default gateway, and DNS server address on the user’s device. Don’t forget to ask the user about any changes they may have made recently. Recently made changes are frequently found to be the cause of issues.
If multiple users are having this issue, it is probably an infrastructure device that stands between the users and the Internet. If you know where the affected users are located, it may help you to determine what network path these devices share to the Internet. Then you can trace your way from them to the Internet, checking the configuration and functionality of each until you locate the problem.
Email Failure
Often users will complain that the email server is down. As a technician you should learn to filter user’s descriptions of issues through your deeper understanding of the network. You know that if the user can’t connect to email it may be the email server, but it could also be a host of other issues as well. As always you should determine the scope of the issue first. If multiple users are having this issue, it is probably an infrastructure device that stands between the users and the email server or the email server itself. If only one user is affected, check the IP configuration of the user’s device and the functionality of their email client.
Just as when addressing Internet issues, trace your way from the affected user to the email server, checking the configuration and functionality of each until you locate the problem. Keep in mind this includes both the DNS server and the DHCP server as well as the routers and switches in the path. Finally, if the path is clear it is time to check the functionality of the email server.
DHCP Server Misconfigured
As you learned earlier, if the DHCP server has an issue many users may be affected. Always ensure it has a sufficient number of IP addresses to service each scope. Also make sure that any default gateway and DNS server addresses it is issuing are correct; if they aren’t, it will cause the users to be unable to leave their local subnet or perform name resolution.
Nonfunctional or Unreachable
Always keep in mind that the destination device may not be functional or it may not be reachable even though it is functioning. We’ll be looking at the meaning of certain ICMP messages in a moment; they can tell you a lot, but know that although you may be able to ping the destination by both IP address and name, that doesn’t mean that the service the destination is providing is working. You can determine this by attempting a Telnet connection to the IP address of the device and adding the port number of the service as shown here. In this example, the test is meant to test the functionality of HTTP:
telnet 192.168.5.5 80If the port is open, you will see a blank screen. This will mean that the connection is successful. If it is not open, you will see this:
telnet 192.168.5.5 80
Connecting to 192.168.5.5 ..... could not open connection to the host on port 80: connect failedKeep in mind that this only tests connectivity to the service and does not guarantee the service is configured or functioning correctly.
Destination Host Unreachable
This is an error message you may receive when attempting to ping the destination device. This means that one of the routers along the path to destination does not have a route to the network where the device resides. It does not mean that the device is not on or is unavailable. That is a different message.
It will appear as a destination unreachable message (this is a group of message types that all have code numbers) with a code number of 1.
Code numbers do not appear in a destination unreachable message. However, you can use a protocol analyzer to capture one of the packets and view the code number by viewing the packet in the tool. You will do this in Exercise 11.2.
If the message comes with no source IP address, that means the message is coming from the local router (the default gateway of the sender). If it has the source IP address of the sender, then it is another router in the path. If this is the message you are getting, it’s time to start looking at the routing tables of the routers or to escalate the issue if that is outside your realm.
Unknown Host
This message tells you that the host specified is not known. This message is usually generated by a router local to the destination host and usually means a bad IP address. It will appear as a destination unreachable message (this is a group of message types that all have code numbers) with a code number of 7.
Default Gateway Misconfigured
Earlier you learned that if the computer cannot connect to the default gateway, it will be confined to communicating with devices on the local network. This IP address should be that of the router interface connected to the local network. You should also ensure that the IP address of the computer is in the same network with the gateway, which means they must share the same network ID. They cannot share the same network ID unless they have the same subnet mask as well. When troubleshooting gateway issues, consider all of these factors. At the end of the day, the device must be able to ping its gateway.
Failure of Service Provider
While it is typically not the cause of Internet issues, always keep in mind that it is possible that the ISP is suffering a failure. If the entire location is suffering an inability to get to the Internet, it is time to consider this possibility. This is simple enough to verify by calling the ISP, but if you want to verify it yourself, execute a traceroute to an Internet address and then you can determine where the traffic is stopping. traceroute is a command that will be covered in “Networking Tools” later in this section, but for now, it allows you to identify the last router that was able to route the packet, thus telling you where the path ends.
Cannot Reach by Host Name/FQDN
When attempting to connect to resources by name, which is the method users employ, the connection is made to a fully qualified domain name (FQDN) in the form of hostname.domain.com. As you learned earlier, if this is not possible, it is a name resolution issue or a DNS issue. This means that the problem could be located in several places. Always consider those possibilities:
- The DHCP server may be issuing an incorrect DNS server address.
- The computer may be configured manually with an incorrect DNS server IP address.
- There may be a network issues preventing access to the DNS server.
- The DNS server is malfunctioning.
Causes of Common Problems
While coverage of many of the common causes of these issues is provided in each section as it applies to that issue, we’ll go over them again in more detail in this section.
Improper IP Configuration
As you know already, no networking will be possible unless the IP configurations of the computers on both ends of a connection attempt are correct. This includes the following:
- IP address
- Default gateway
- Subnet mask
- DNS server
VLAN Configuration
By default, all ports in a switch are in the same Layer 2 network or the same LAN. It is possible to subdivide the switch into separate Layer 2 networks called virtual LANs, or VLANs. When we do this, we also place the devices that are in different VLANs in different Layer 3 networks as well. However, even if we assign devices in different VLANs with IP addresses in the same subnet, they will not be able to communicate because they are also separated at Layer 2.
VLANs can also span switches, meaning that devices connected to different switches can be in the same VLAN. When this is done, you must create special links called trunk links that permit the traffic of multiple VLANs between these switches.
This means that misconfiguration of VLANs can cause communication issues. The types of mistakes that can cause this include
- Ports assigned to an incorrect VLAN
- Devices in the same VLAN with IP addresses in different IP subnets
- VLANs that have been mistakenly disallowed from crossing a trunk link
When VLANs are in use, always consider these possible misconfigurations on the switch and escalate the problem if that is not your area of expertise.
Port Security
Another feature that is available on switches can cause connectivity issues. It is possible to use a feature called port security to prevent the attachment of unauthorized devices to the switch. The port security features allows you to
- Specify the only MAC address or addresses allowed to send traffic in the port.
- Specify the total number of MAC addresses that can transmit on the port.
- Specify an action to be taken when a violation occurs (either shut the port down or prevent transmissions by the guilty MAC address).
As you can imagine, this creates a scenario ripe for connectivity issues. Even if the port security configuration is correct, the connection of an unauthorized device to a port might shut down the port, causing an issue for a legitimate device when it is reconnected to the port. If you suspect port security, check the following:
- Is the port listed as err-disabled in the output of the
show portcommand? If so, it must be enabled manually. - Is the port allowing all required legitimate MAC addresses (don’t forget the IP phone to which the computer may be connected)?
- Is the port allowing the required number of MAC addresses—for example, if it is only allowing one and there are two attached (IP phone and computer)?
When port security is in use, always consider these possible misconfigurations on the switch and escalate if that is not your area of expertise.
Improper Subnetting
Subnetting was covered in Chapter 8, “Networking,” in the section “CIDR Notation and Subnetting,” but let’s cover a few key points again.
Devices that are in the same IP subnet must have an IP address and subnet mask combination that places them in the same subnet. Regardless of whether you are using default subnet masks or you are implementing CIDR (which allows nondefault mask lengths), for two devices to be in the same subnet they must share the same network portion of the IP address. This means that their IP addresses must agree in the bits covered by the mask. For example, consider these two addresses:
192.168.6.5/16
192.168.5.6/16For these two addresses to be in the same subnet, they must agree in the first 16 bits (the number of bits in the mask). In this case, they both have 192.168 in the first two octets or 16 bits so they are in the same subnet. However, consider these changes:
192.168.6.5/24
192.168.5.6/24Now they must agree in the first 24 bits, which they do not (192.168.5 and 192.168.6) so they are now not in the same subnet. Regardless of whether CIDR is in use, always consider these possible misconfigurations on the devices.
Component Failure
Yes, it’s true, the network problem may not be your fault—at least it might not be a misconfiguration. Sometime components fail. If any router, switch, or firewall in the network fails or one of its components fails, there will be network issues. When this occurs, typically the effect is widespread. It will usually affect an entire subnet or an entire section of the network. These issues should be escalated as soon as they are discovered due to the scope of the issue.
Incorrect OS Route Tables
Routers route packets by consulting a routing table that the router creates by placing all directly connected (or local) networks in the table and then adding remote networks as they become known to the router. The router can learn remote networks in one of two ways: by administrators adding them manually or by learning them from other routers via a common routing protocol. As both of these methods involve human beings making configuration settings, there are always opportunities for misconfigurations.
When you have discovered that the path between two devices ends at a specific router (remember, you can determine this with the traceroute command), it is time to suspect the routing table of that router. The show ip route command can be used to identify the routes of which the router is aware. If the router is missing the route, it will never be able to forward packets to the destination network. While configuring routers is beyond the scope of this book, consider this possibility when you have identified a router where a path between two devices ends and then escalate as necessary.
Bad Cables
While technicians learn at the beginning of their careers to always check the Physical layer first, hours are sometime devoted to troubleshooting upper-layer issues to no avail when a bad cable is the culprit. Keep in mind as well that performance issues also sometimes have their roots in a damaged cable.
In some cases, a cable may function but not well. If the cable has a nick in the outside covering it allows EMI and RFI to more easily enter the cable. This “noise” damages packets and cause them to fail the integrity check when they arrive at their destination. This causes the packet to be lost for good in the case of UDP traffic, and it causes it to be retransmitted in the case of TCP traffic. The time spent sending the packet again could have been used to send new packets, so this results in a lower data rate. Always consider a damaged cable first when a server is suffering poor performance.
While it is beyond the scope of this book, if you examine the performance information on the switch port to which the server is connected you can identify when packets are being dropped due to CRC errors.
Firewall
As with other infrastructure devices such as routers and switches, when a firewall has issues, multiple users are typically affected. These issues usually are caused by one of three things.
Misconfiguration
Firewalls use rule sets that must be constructed carefully or they will not achieve their goal. In most cases, but not all, access control lists (ACLs) are used to control traffic through an interface. The list of rules is created and then applied either inbound or outbound to an interface. When a packet arrives at an interface on the firewall, the firewall starts at the top of the list of rules and starts comparing the traffic type in the packet to each rule in order. When it finds the first rule that matches the traffic type in the packet, it takes the action (either allow or deny) specified in the rule and stops reading the list. This means the order is very important.
For example, let’s say our intent is to prevent a computer at 192.168.5.5/24 from sending traffic through an interface while allowing everyone else in the subnet to send traffic. We create these two rules in this order:
- Permit 192.168.5.0/24
- Deny 192.168.5.5/24
Can you guess what will happen? Since the devices at 192.168.5.5/24 matches both rules and the permit rule is first, the rule that we created designed to deny this traffic will never be denied. So as you can see, incorrect rule order is a common mistake.
Another common characteristic of ACLs is that (in most systems but not all) there is an implied deny all rule at the end of every ACL. You don’t see it; it’s automatic. This means that if the firewall goes all the way through the list and none of the rules allow the traffic, the traffic is denied. Failing to explicitly allow traffic that should be allowed is another common mistake.
Finally, you can create ACLs until you are blue in the face and if you never apply them to an interface, they never enforce anything. So failure to apply the ACL is another common mistake.
While most systems use the logic just explained, there are some systems that, rather than applying the first rule that matches, go all the way through the list and select the rule that is the best match. So a system that uses that logic would have been able to select the proper rule in our previous example because the second rule in the list is a better match of the sender’s IP address than the first rule in the list. You must understand the logic of each system.
Hardware Failure
It is also possible that the firewall may suffer a hardware failure. This can happen regardless of whether the firewall is implemented as an appliance or as software running on a server. Any hardware issue that affects the server on which the software is installed will affect the firewall function. Likewise, any hardware issues with interfaces, memory, or CPU on an appliance will affect the hardware appliance as well.
Software Failure
Software failures can also occur either in the firewall software running on a server or with the firmware or operating system running in an appliance. In many cases, these failures can be avoided by maintaining all patches to the firewall software and firmware as it becomes available. Although these failures are always possible, a more likely threat is a misconfiguration of the software, as discussed earlier.
Misconfigured NIC
Most technicians don’t think much about the settings on a NIC; they just plug it in and if it works they are satisfied. A misconfigured NIC, like a damaged cable, may work but not work well if its duplex and speed settings do not match those of the switch port to which it is connected. Although most network cards supposedly “autosense” the setting on the other end and set themselves to match, this function requires a negotiation process that can fail, and when it does the two ends may default to a mismatch.
Just as a damaged cable causes damaged packets that fail the integrity check and must be transmitted again, a speed or duplex mismatch causes packet collisions, which also cause packets to be re-sent and lower throughput. This is another behavior you can detect by reviewing errors occurring on the switchport.
Routing/Switch Issues
Routing and switch issues like firewall issues will typically affect multiple users. This is not a book on routers and switches, but you should be able to connect certain errors with certain devices. You’ve already learned that if a router has no route in its table to a destination network, it will be unable to send traffic to that network. That will result in a destination unreachable message when you attempt to ping that destination. Here are several messages that indicate a lack of a route or a security issue:
- Destination unreachable with a source address (and a code number of 0): A router in the path other than the local route has no route to that network.
- Destination unreachable with no source address (with a code number of 0): The local router has no route to the network.
- Destination unreachable (with a code number of 9 or 10); The source device is not permitted to send to that network (code 9) or to that device (code 10). This message indicates an ACL is prohibiting the traffic.
Switch issues will only affect those devices attached to the switch unless there are VLANs spanning switches; then the effect may be more widespread. Most issues with switches concern switch port security misconfigurations or speed and duplex mismatches, but problems can also occur when trunk links are misconfigured between switches. While the default setting is to allow the traffic of all VLANs across a trunk link, it is possible to disallow certain VLANs. Obviously a mistake when configuring that setting could cause issues. Always consider that possibility when intra-VLAN issues are occurring.
DNS and/or DHCP Failure
DNS and DHCP failures will affect multiple users and the damage will depend on several factors. Let’s start with DHCP.
Most issues with DHCP result in computers being unable to obtain an IP configuration. That manifests itself to the user as an inability to connect to anything, which may result in all sorts of misdiagnoses by the user (the email server is down, the web server is down…). This can be caused by
- The DHCP server is out of IP addresses.
- The computer is unable to reach the DHCP server.
- The DHCP server is down.
The first problem is simple enough to solve: add more IP addresses. The second can occur if the computer is located in a different subnet from the DHCP server and relay agents are not in use. Since DHCP clients locate the DHCP server with a broadcast packet, they must be in the same subnet or the server will never hear the broadcast. Relay agents can be applied to the router interfaces, and then the router interface can relay these packets to the server. In their absence, an inability to connect will occur. One of the symptoms of this condition is that the device will have a self-generated IP address. If the device is Windows and it is running IPv4, the address will have 169 in the first octet.
DNS issues will also be widespread. Users will be unable to locate resources by name. To them, this issue will appear to be the same as an issue with DHCP in that they can’t connect to anything. So you may get some of the same user misdiagnoses. You can easily determine which it is by pinging the destination by name and by IP address. If you can ping by IP address but not by name, the issue is DNS.
Misconfigured Hosts File
Most systems rely on DNS for name resolution, but it is not the only method a system can use. Windows and Linux systems have a file called Hosts that can be populated manually with IP address–to-name mappings. The downside to this is the static nature of the file—that is, any changes have to be made manually. This file is always located at C:WindowsSystem32driversetchosts. If this file is misconfigured, it will result in an inability to connect to the destination. To make matters worse, this file is the first place the device looks before it attempts DNS, so if there is an entry in the file for the name, it never uses DNS!
Finally, some forms of malware edit the Hosts file and add entries. So even if you are not aware that anyone has ever edited this file, it is still something to check since malware can add entries.
IPv4 vs. IPv6 Misconfigurations
IPv6 is the new version of IP that uses 128-bit IP addresses rather than 32-bit, as in IPv4. Many technicians are still learning IPv6, and it is an area ripe for misconfiguration.
IPv6 offers a number of improvements, the most notable of which is its ability to handle growth in public networks. IPv6’s 128-bit addressing scheme allows for a huge number of possible addresses: 340,282,366,920,938,463,463,374,607,431,768,211,456.
Table 11.1 compares IPv4 to IPv6.
Table 11.1 IPv4 vs. IPv6
| Feature | IPv4 | IPv6 |
| Loopback address | 127.0.0.1 | 0:0:0:0:0:0:0:1 (::1) |
| Private ranges | 10.0.0.0/8 172.16.0.0/12 192.168.0.0/24 |
FC00:/7 |
| Autoconfigured addresses | 169.254.0.0/16 | FE80:: |
One common mistake is to configure two ends of a link such that they are not in the same subnet. In IPv6, the number of bits in the prefix is given after the address, as shown here:
- aaaa.bbbb.cccc.dddd.0000.0000.0000.0000 /64
This means that the prefix is 64 bits long, or aaaaa.bbbbb.ccccc.ddddd. Therefore, for two IP addresses to be in the same network, the address must be the same across the first 64 bits.
Networking Tools
A number of command-line tools are available to help you diagnose network issues, some of which we have already referred to. You should understand how these tools work and in which situations they may help you gather useful diagnostic data.
ping
The ping command makes use of the ICMP protocol to test connectivity between two devices. ping is one of the most useful commands in the TCP/IP protocol. It sends a series of packets to another system, which in turn sends a response. The ping command can be extremely useful for troubleshooting problems with remote hosts.
The ping command indicates whether the host can be reached and how long it took for the host to send a return packet. On a LAN, the time is indicated as less than 10 milliseconds. Across WAN links, however, this value can be much greater. When the -a parameter is included, the command will also attempt to resolve the hostname associated with the IP address. Figure 11.9 shows an example of a successful ping.

Figure 11.9 The ping command
tracert/traceroute
The tracert command (called traceroute in Linux and Unix) is used to trace the path of a packet through the network. Its best use is in determining exactly where in the network the packet is being dropped. It will show each hop (router) the packet crosses and how long it takes to do so. Figure 11.10 shows a partial display of a traced route to www.msn.com.

Figure 11.10 Using tracert
ipconfig/ifconfig
The ipconfig command is used to view the IP configuration of a device and, when combined with certain switches or parameters, can be used to release and renew the lease of an IP address obtained from a DHCP server and to flush the DNS resolver cache. Its most common use is to view the current configuration. Figure 11.11 shows its execution with the /all switch, which results in a display of a wealth of information about the IP configuration.

Figure 11.11 Using ipconfig
ipconfig can be used to release and renew a configuration obtained from a DHCP server by issuing first the ipconfig/release command, followed by the ipconfig/renew command.
It is also helpful to know that when you have just corrected a configuration error (such as an IP address) on a destination device, you should ensure that the device registers its new IP address with the DNS server by executing the ipconfig/registerdns command.
It may also be necessary to clear incorrect IP address–to-hostname mappings that may still exist on the devices that were attempting to access the destination device. This can be done by executing the ipconfig/flushdns command.
If you are using a Linux or Unix system, the command is not ipconfig but ifconfig. Figure 11.12 shows an example of the command and its output. The ifconfig command with the -a option shows all network interface information, even if the network interface is down.

Figure 11.12 ifconfig
nslookup
The nslookup command is a command-line administrative tool for testing and troubleshooting DNS servers. It can be run in two modes: interactive and noninteractive. Noninteractive mode is useful when only a single piece of data needs to be returned; interactive allows you to query for either an IP address for a name or a name for an IP address without leaving nslookup mode. The command syntax is as follows:
nslookup [-option] [hostname] [server]To enter interactive mode, simply type nslookup. When you do, by default it will identify the IP address and name of the DNS server that the local machine is configured to use, if any, and then will go to the > prompt. At this prompt, you can type either an IP address or a name, and the system will attempt to resolve the IP address to a name or the name to an IP address.
C:> nslookup
Default Server: nameserver1.domain.com
Address: 10.0.0.1
>The following are other queries that can be run that may prove helpful when you are troubleshooting name resolution issues:
- Looking up different data types in the database (such as Microsoft records)
- Querying directly from another name server (different from the one the local device is configured to use)
- Performing a zone transfer
net use/mount
The net command is one of the most powerful on the Windows-based network, as illustrated by net use. The options that can be used with the command differ slightly based on the Windows operating system you are using; you can view a full list by typing net /?.
The net use command is used on Windows-based clients to connect or disconnect from shared resources. You can see what is currently shared by typing net use without any other parameters, as shown in Figure 11.13.

Figure 11.13 Typing net use lets you see what is currently shared.
The mount command serves to attach the filesystem found on some device to the filesystem in Linux and Unix. The standard form of the mount command is
mount -t type device destination_dirwhere type represents the type of device, device represents the device, and destination_dir represents the directory you want to mount. In the following example, a CD-ROM is mounted and the -o ro parameter indicates it should be mounted with read-only access. The iso9660 identifies the device as a CD-ROM.
# mount -t iso9660 -o ro /dev/cdrom /mntroute
The route command can be used in both Linux and Windows to view and edit the routing table on computers. To view the routing table in Linux, use the route command like this:
$ route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.1.0 * 255.255.255.0 U 0 0 0 eth0The output shows that the device is aware of one network (the one to which it is connected).
In Windows, the command requires the print keyword, as shown here:
C:WINDOWSsystem32>route print
===========================================================================
Interface List
18...9c 4e 36 7e 04 6d ......Microsoft Wi-Fi Direct Virtual Adapter
6...0a 00 27 00 00 00 ......VirtualBox Host-Only Ethernet Adapter
10...08 9e 01 36 53 73 ......Realtek PCIe FE Family Controller
14...9c 4e 36 7e 04 6c ......Intel(R) Centrino(R) Wireless-N 2200
12...e0 06 e6 be cc 7b ......Bluetooth Device (Personal Area Network)
1...........................Software Loopback Interface 1
7...00 00 00 00 00 00 00 e0 Microsoft ISATAP Adapter
17...00 00 00 00 00 00 00 e0 Teredo Tunneling Pseudo-Interface
5...00 00 00 00 00 00 00 e0 Microsoft ISATAP Adapter #9
===========================================================================
IPv4 Route Table
===========================================================================
Active Routes:
Network Destination Netmask Gateway Interface Metric
0.0.0.0 0.0.0.0 192.168.0.1 192.168.0.6 20
127.0.0.0 255.0.0.0 On-link 127.0.0.1 306
127.0.0.1 255.255.255.255 On-link 127.0.0.1 306
127.255.255.255 255.255.255.255 On-link 127.0.0.1 306
192.168.0.0 255.255.255.0 On-link 192.168.0.6 276
192.168.0.6 255.255.255.255 On-link 192.168.0.6 276
192.168.0.255 255.255.255.255 On-link 192.168.0.6 276
192.168.56.0 255.255.255.0 On-link 192.168.56.1 266
192.168.56.1 255.255.255.255 On-link 192.168.56.1 266
192.168.56.255 255.255.255.255 On-link 192.168.56.1 266
224.0.0.0 240.0.0.0 On-link 127.0.0.1 306
224.0.0.0 240.0.0.0 On-link 192.168.56.1 266
224.0.0.0 240.0.0.0 On-link 192.168.0.6 276
255.255.255.255 255.255.255.255 On-link 127.0.0.1 306
255.255.255.255 255.255.255.255 On-link 192.168.56.1 266
255.255.255.255 255.255.255.255 On-link 192.168.0.6 276
===========================================================================
Persistent Routes:
None
IPv6 Route Table
===========================================================================
Active Routes:
If Metric Network Destination Gateway
17 306 ::/0 On-link
1 306 ::1/128 On-link
17 306 2001::/32 On-link
17 306 2001:0:5ef5:79fb:30be:34ca:cd75:ec40/128
On-link
6 266 fe80::/64 On-link
10 276 fe80::/64 On-link
17 306 fe80::/64 On-link
17 306 fe80::30be:34ca:cd75:ec40/128
On-link
6 266 fe80::a1f4:3886:392:d218/128
On-link
10 276 fe80::f098:57fb:c0d7:5e65/128
On-link
1 306 ff00::/8 On-link
6 266 ff00::/8 On-link
17 306 ff00::/8 On-link
10 276 ff00::/8 On-link
===========================================================================
Persistent Routes:
None
This output lists both the IPv4 and IPv6 routing tables as well as a list of the interfaces. Use the route and route print commands to determine if a device has a route to its default gateway. A route of this type is called the default route, and in Windows it’s listed as a destination network of 0.0.0.0 with a mask of 0.0.0.0.
nbtstat
Microsoft networks use an interface called Network Basic Input/Output System (NetBIOS) to resolve workstation names with IP addresses. The nbtstat command can be used to view NetBIOS information. In Figure 11.14 it has been executed with the -n switch, which will display the NetBIOS names that are currently known to the local machine. In this case, this local machine is aware only of its own NetBIOS names.

Figure 11.14 Using nbtstat
netstat
The netstat (network status) command is used to see what ports are listening on the TCP/IP-based system. The -a option is used to show all ports, and /? is used to show what other options are available (the options differ based on the operating system you are using). When executed with no switches, the command displays the current connections, as shown in Figure 11.15.

Figure 11.15 Using netstat
Diagnosing Security Issues
While many connectivity problems are rooted in network issues, others are caused by security features and functions. The end result is the same—the user cannot connect to a resource—but the symptoms are somewhat different. Next, we’ll look at diagnosing security issues that cause connectivity issues and other more general security concerns.
Common Problems
Just as certain hardware and software issues seem to happen more often than others, there will be some security issues that are commonplace as well. Many of these are the result of human error in configuration, and others are the result of poorly configured or poorly written applications. In this section, we’ll look at some common security issues.
File Integrity Issue
When files become altered either through corruption or unauthorized access, we say that the integrity of the file has been compromised. When system files are altered (sometimes through the actions of malware), it can cause operating system errors and crashes. In the “Security Tools” section, we’ll look at some ways to maintain the integrity of both system files and other critical files that need protection.
Privilege Escalation
When any user is able to attain additional rights and permissions, we say that privilege escalation has occurred. In most cases, this occurs as a result of the user obtaining the login information for a privileged account, logging in as that user, and making use of those additional rights and permissions. If the compromised action is an administrator or root account, the situation becomes worse because then the user may be able to clear the security log and hide their tracks. In the “Causes of Common Problems” section, we’ll talk about how this occurs and what can be done to minimize the likelihood of this happening.
Applications Will Not Load
Another possible symptom of a malware infection is the crashing of applications. While this will occur from time to time for other reasons, when it is occurring repeatedly you should suspect malware. When the application that is crashing is your antivirus software, this is an even stronger indication of malware, as disabling or damaging your antivirus protection is the first thing that some types of malware attempt to do.
It is also a possibility that if your organization makes use of software restriction policies, the user may be trying to run a disallowed application. In that case, you should ensure that the software restriction policies that are controlling the user are correct.
Finally, it is always possible that the application is simply corrupted. In that case, try removing and reinstalling the application.
Can’t Access Network File/Shares
Although network issues should be ruled out first, in some cases network file and share permissions may be preventing a user from accessing a share or file. In Windows, you must always consider the effects of multiple permissions users may have as a result of permissions applied to their account and those applied to any groups they may be in. You should have a clear understanding of how these permissions work together. In the “Causes of Common Problems” section, we’ll review how Windows permissions work.
Unable to Open Files
When files will not open on a machine, there is always the possibility that the file permissions are the cause, but there can be other reasons. If the user lacks the application required to open the file, it will not open. This often occurs when users receive an email attachment in a file format for which they do have the proper application. They may or may not know how to locate and install the application, even if the application is free. If a software restriction policy is preventing the installation of the proper application, the user may have to get assistance and permission to read the document.
Excessive Access
Over time as users change jobs, get promoted, and move from one department to another, something called permission creep occurs. This means that while they have attained new permissions as the result of the new job, the old permission that applied to the previous position are not removed as they should be. This can be prevented by performing a formal permission review at the time of the application of the new permissions and also at regular intervals thereafter.
Excessive Memory Utilization
When memory utilization goes up without a corresponding known increase in workload, it is usually an indication of malware. It makes complete sense if you think about it. The memory is being used by something and in this case it is the malware. Any instance of excessive memory utilization should be investigated to see if malware is the issue. Otherwise, you could have a faulty application that needs to be patched or replaced.
Causes of Common Problems
It may be hard to determine, but every issue has a cause. Although it is sometimes tempting to adopt a quick workaround to get things moving (and in some cases that may be the best approach), you should always attempt to determine the root cause. Otherwise, the issue could keep returning. In this section, we’ll look at some causes that are worthy of consideration because they are common. We’ll also cover common security weaknesses that you should be aware of.
Open Ports
One of the guiding principles of security is to disable all services that are not needed and to close the port of any services not in use. Hackers know common attacks that utilize common port numbers. In most cases, maintaining patches and updates prevents hackers from taking advantage of open ports, but not always. In the “Security Tools” section, we’ll talk about how you can use the same tools the hackers do to discover these open ports.
Active Services
While on the surface the presence of active services might appear to be a good thing, in some cases it is not. Following the same principle we followed with respect to open ports, any services or applications that are not required on a device should be disabled. The reason for this is that most services and applications have been compromised at some point. If all patches are applied, these compromises are usually addressed, but any that are not required should be disabled to be safe.
Inactive Services
When required services are inactive, it’s a problem. Sometimes when the system is started you receive a message that tells you a service failed to start. When that occurs, use the event log to determine the service that failed. Then, to interact with the service, access the Administrative Tools section of Control Panel and choose Services. This starts up the Services console. You can right-click any service and choose to start, stop, pause, resume, or restart it. You can also double-click the service to access its properties and configure such things as the startup type, dependencies, and other variables.
If the service refuses to start, it could be that a service on which it depends will not start. To determine what services must be running for the problem service to start, select the Dependencies tab of the service’s Properties dialog box, as shown in Figure 11.16.

Figure 11.16 Service dependencies
In the figure you can see that the Remote Desktop service depends on both the RPC and the Terminal Device Driver services to function. Try starting these services first. In some cases, you may need to trace the dependencies up several levels to get things going.
Intrusion Detection Configurations
An intrusion detection system (IDS) is a system responsible for detecting unauthorized access or attacks. It can verify, itemize, and characterize threats from outside and inside the network. Most IDSs are programmed to react in certain ways in specific situations. Event notification and alerts are crucial to IDSs as these devices do not respond to or prevent attacks. These notifications and alerts inform administrators and security professionals when and where attacks are detected. The most common way to classify an IDS is based on its information source: network based or host based.
The most common IDS, a network-based IDS (NIDS), monitors network traffic on a local network segment. To monitor traffic on the network segment, the network interface card (NIC) must be operating in promiscuous mode. An NIDS can monitor only the network traffic. It cannot monitor any internal activity that occurs within a system, such as an attack against a system that is carried out by logging on to the system’s local terminal. An NIDS is affected by a switched network because generally an NIDS monitors only a single network segment.
When these devices are misconfigured, the result will not be what you desire. Anyone supporting these should be trained in configuring and supporting them. Even when they are configured correctly, there can be errors. A false positive occurs when an event is identified as a threat when it is not. A false negative is even worse; it occurs when a threatening event is not identified. As you see, configuring these can be tricky and requires expert knowledge.
Antimalware Configurations
Most issues that occur with antimalware configurations result in an inability to update either the malware definitions or the malware engine. Both should be updated regularly, preferable on an automatic basis, which almost all enterprise products support. Missing updates are one of the biggest causes of malware outbreaks in a network. Although some threats (called zero-day threats) will occur before the vendor has developed a solution, outbreaks that occur due to missing updates should be viewed as a failure of your processes. You should develop procedures to ensure that updates occur.
Local/Group Policies
When Group Policies are used to control security in an enterprise, an incomplete understanding of how Group Policies operate can result in actions being allowed that should not be allowed and actions being prevented that should not be prevented. Active Directory, the directory service used in Windows, has a hierarchal structure and policy settings are inherited from one level to another in a specific way. When a machine starts up and is applying Group Policies, it applies them in this order:
- Domain
- OU
- Local
This means that policies on the local machine will overrule any at the OU level and any at the OU level will overrule any from the domain level. Further complicating this is the fact the user may have one set of policies applied while their computer may have another. So the system is ripe for misconfiguration by someone with an incomplete understanding of the inheritance process.
Fortunately, there is a tool that can help identity why a particular policy is not being applied to a device or user. The gpresult command is used to show the Resultant Set of Policy (RSoP) report/values for a remote user and computer. Bear in mind that configuration settings occur at any number of places. Often one of the big unknowns is which set of configuration settings takes precedence and which is overridden. With gpresult, it is possible to ascertain which settings apply. An example of the output is shown in Figure 11.17.
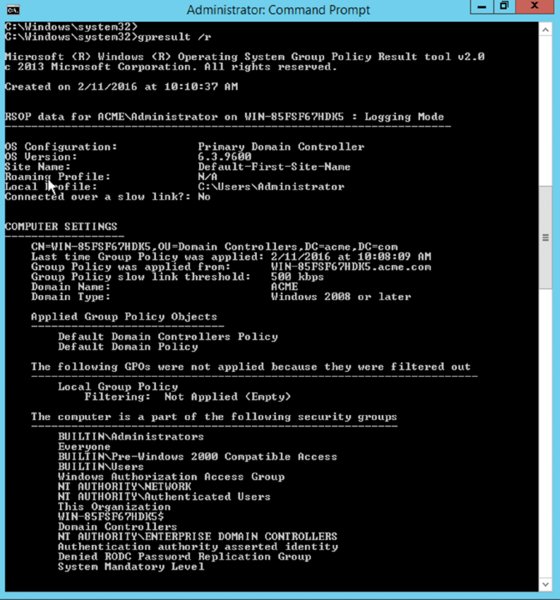
Figure 11.17 gpresult
Firewall Rules
When firewall rules are misconfigured, not only can it cause network connectivity issues, it can also create serious security issues. You learned earlier that the order of the rules in an ACL are sometimes critical to the proper operation of the ACL. This is another area where an incomplete understanding of the logic used by a particular firewall product can have disastrous and far-reaching results. Only technicians who have been trained in that product should be allowed to manage these ACLs.
Misconfigured Permissions
Earlier you learned that incomplete understanding of the inheritance of Group Policies can result in the policies either not being applied or being applied incorrectly. Because filesystem permissions also use inheritance, an opportunity also exists for issues with permissions. Most of the confusion when it comes to permissions involves the inheritance process, the interaction of various permissions that a user may have as a result of being a member of groups that may also have permissions, and the fact that there are two systems at work—the NTFS security system and the Share security system. NTFS and share permissions were covered in the section “Permissions” in Chapter 7, “Securing Server Data and Network Access.”
Allow vs. Deny
By default, the determination of NTFS permissions is based on the cumulative NTFS permissions for a user. Rights can be assigned to users based on group membership and individually; the only time permissions do not accumulate is when the Deny permission is invoked.
When NTFS permissions and share permissions come in conflict, the system will compare the combined NTFS permissions to the combined share permissions. The system will apply the most restrictive of these two.
Virus Infection
Sometimes despite all efforts a virus outbreak may occur. Even if you maintain all updates, the system will not be able to recognize or mitigate a zero-day attack. When this does occur, you should take certain steps to contain and eliminate the issue.
Recognize Learn to recognize how a system reacts to malware.
Quarantine Prevent malware from propagating.
Search and Destroy Remove malware from infected systems.
Remediate Return the system to normal after the malware is gone.
Educate Train users to prevent malware outbreaks.
Rogue Processes/Services
Earlier you learned how a runaway process or service can consume all of the resources of a device, causing it to “lock up” or operate slowly. You can use the Task Manager tool to identify the guilty process and the taskkill command to end it.
Task Manager lets you shut down nonresponsive applications selectively in all Windows versions. In current versions of Windows, it can do so much more: Task Manager allows you to see which processes and applications are using the most system resources, view network usage, see connected users, and so on. To display Task Manager, press Ctrl+Alt+Del and click the Task Manager button to display it. You can also right-click on an empty spot in the Taskbar and choose it from the pop-up menu that appears.
The Task Manager tool in Windows Server 2012 R2 is shown in Figure 11.18. If you find that you cannot locate the process, it could be caused by malware which frequently “hides” from Task Manager. Always consider this as a possibility and scan for malware.

Figure 11.18 Task Manager
Security Tools
Just as you have many networking tools available to troubleshoot network connectivity issues, you also have an impressive set available to you for security issues. These tools allow you to gain the same visibility a hacker might have so you can make any required changes to maintain a secure network. In this section, we’ll survey the most common of these tools.
Port Scanners
Internet Control Message Protocol (ICMP) messages can be used to scan a network for open ports. Open ports indicate services that may be running and listening on a device that may be susceptible to attack. An ICMP, or port scanning, attack basically pings every address and port number combination and keeps track of which ports are open on each device as the pings are answered by open ports with listening services and not answered by closed ports. One of the most widely used port scanners is Network Mapper (Nmap), a free and open source utility for network discovery and security auditing. Figure 11.19 shows the output of a scan using Zenmap, an Nmap security scanner GUI. Starting in line 12 of the output shown in this figure, you can see that the device at 10.68.26.11 has seven ports open:

Figure 11.19 Zenmap
Discovered open port 139/tcp on 10.68.26.11Figure 11.20 shows output from the command-line version of Nmap. You can see in this figure that a ping scan of an entire network just completed. From it you can see that the computer at 172.16.153.242 has three ports open: 23, 443, and 8443. However, the computer at 172.16.153.253 has no open ports. The term filtered in the output means that the ports are not open. To obtain this output, the command Nmap 172.16.153.0/23 was executed, instructing the scan to include all computers in the 172.16.153.0/23 network.

Figure 11.20 Nmap command line
In a scenario where you need to determine what applications and services are running on the devices in your network, a port scanner would be appropriate. It also allows you to identify any open ports that should not be open.
Sniffers
Sniffing is the process of capturing packets for analysis; sniffing used maliciously is referred to as eavesdropping. Sniffing occurs when an attacker attaches or inserts a device or software into the communication medium to collect all the information transmitted over the medium. Sniffers, called protocol analyzers, collect raw packets from the network; both legitimate security professionals and attackers use them. The fact that a sniffer does what it does without transmitting any data to the network is an advantage when the tool is being used legitimately and a disadvantage when it is being used against you (because you cannot tell you are being sniffed). Organizations should monitor and limit the use of sniffers. To protect against their use, encrypt all traffic on the network.
One of the most widely used sniffers is Wireshark. It captures raw packets off the interface on which it is configured and allows you to examine each packet. If the data is unencrypted, you will be able to read the data. Figure 11.21 shows an example of Wireshark in use.

Figure 11.21 Wireshark
In the output shown in Figure 11.21, each line represents a packet captured on the network. You can see the source IP address, the destination IP address, the protocol in use, and the information in the packet. For example, line 511 shows a packet from 10.68.26.15 to 10.68.16.127, which is a NetBIOS name resolution query. Line 521 shows an HTTP packet from 10.68.26.46 to a server at 108.160.163.97. Just after that, you can see that the server sending an acknowledgment back. To try to read the packet, you would click on the single packet. If the data were clear text, you would be able to read and analyze it. So you can see how an attacker could acquire credentials and other sensitive information.
Protocol analyzers can be of help whenever you need to see what is really happening on your network. For example, say you have a security policy that says certain types of traffic should be encrypted. But you are not sure that everyone is complying with this policy. By capturing and viewing the raw packets on the network, you would be able to determine whether they are.
Cipher
Cipher is a Windows command-line utility that can be used to view and alter the encryption of files on an NTFS partition. Run with no parameters, it will display the encryption state of the current folder and any file contained within it. That allows you to verify that sensitive files are encrypted as they should be. It is a very powerful tool, however, that can do many more things. Among the tasks you can perform with this tool and the parameters required are
/e Encrypts the specified folders and marks them so that files that are added to the folder later are encrypted too.
/d Decrypts the specified folders and marks them so that files that are added to the folder later are decrypted too.
For more information, on these command options, see https://technet.microsoft.com/en-us/library/bb490878.aspx.
Checksums
Checksums are values that can be calculated based on the contents of a file that can be used later to verify that the file has not changed. There are a number of tools that can do this, such as the Microsoft File Checksum Integrity Verifier. Many third-party tools can be used to create checksums that can be verified at a later time.
Telnet Client
Although a Telnet client comes on every Windows machine, the client is not installed by default. It is a handy tool to have because it allows you to connect to a device at the command line and work at the command line. You should know, however, that Telnet transmits in clear text so you would not want to use it to perform any sensitive operations (like changing a password). In Exercise 11.3 you will install the Telnet client in a Windows 10 computer.
Antimalware
The primary method of preventing the propagation of malicious code involves the use of antimalware software. This category includes antivirus, antispyware, and antispam software.
Antivirus software is an application that is installed on a system to protect it and to scan for viruses as well as worms and Trojan horses. Most viruses have characteristics that are common to families of virus. Antivirus software looks for these characteristics, or fingerprints, to identify and neutralize viruses before they affect you.
More than 200,000 known viruses, worms, bombs, and other malware have been defined. New ones are added all the time. Your antivirus software manufacturer will usually work hard to keep the definition database files current. The definition database file contains all the known viruses and countermeasures for a particular antivirus software product. You probably won’t receive a virus that hasn’t been seen by one of these companies. If you keep the virus definition database files in your software up-to-date, you probably won’t be overly vulnerable to attacks.
Summary
In this chapter you learned about some of the common issues that prevent network connectivity, among them email failures, Internet failures, and DNS failures. You also learned many of the causes of these issues, such as misconfigured VLANs, improper subnetting, and DHCP failures. You were also exposed to some of the tools that you can use to troubleshoot these issues.
Security misconfigurations can also cause connectivity issues. You learned that this can lead to an inability to open files, applications that will not load, and privilege escalations. We also discussed the causes of these issues, such as misconfigured policies and permission, firewall rules, and rogue processes. Finally, we covered the tools you can use to troubleshoot security-related issues, such as port scanners, sniffers, and checksum tools.
Exam Essentials
Identify common connectivity issues. This includes Internet connectivity failures, email failures, a misconfigured DHCP server, destination host unreachable messages, unknown host messages, a misconfigured default gateway, failure of the service provider, and inability to reach a host by name/FQDN.
Identify common causes of connectivity issues. Describe common causes such as improper IP configuration, VLAN configuration, port security, improper subnetting, component failure, incorrect OS route tables, bad cables, firewall misconfiguration hardware failure, software failure, misconfigured NICs, routing/switch issues, DNS and/or DHCP failure, misconfigured Hosts file, and IPv4 vs. IPv6 misconfigurations.
List common tools. Tools include ping, tracert/traceroute, ipconfig/ifconfig, nslookup, net use/mount, route, nbtstat, and netstat.
Identify common security issues. These include file integrity issues, privilege escalation, applications that will not load, inability to access network file/shares, inability to open files, excessive access, and excessive memory utilization.
Identify common causes of security issues. Causes include open ports, active services, inactive services, intrusion detection configurations, antimalware configurations, local/Group Policies, firewall rules, misconfigured permissions, virus infections, and rogue processes/services.
List common tools. Among these are port scanners, sniffers, cipher, checksums, Telnet clients, and antimalware.
Review Questions
You can find the answers in the Appendix.
-
Which of the following addresses is used to test the functionality of the NIC?
- 0.0.0.0
- 127.0.0.1
- 255.255.255.255
- 0.0.0.1
-
Which of the following features will assign a host with an address in the 169.254.x.x range with a subnet mask of 255.255.0.0?
- NAT
- DHCP
- APIPA
- SSID
-
Which of the following is the IPv6 prefix of a link local address?
- FE20: :/64
- 2001: :/64
- FFEE: :/64
- FE80: :/64
-
Which of the following commands clears the local DNS cache?
ipconfig/flushdnsflushdnscache/flushdnsipconfig/flush
-
Which of the following should be the same on all devices in the same subnet?
- IP address
- Subnet mask
- Hostname
- FQDN
-
Which of the following behaviors affects a WLAN but not a wired LAN?
- Collisions
- CRC failures
- Interference
- DNS issues
-
What command allows you to determine the MAC address of the computer with which you are experiencing a conflict after pinging the IP address?
ipconfig/idping -iarp -dmac-id
-
What are you hiding when you disable SSID broadcast?
- The MAC address of the AP
- The IP address of the AP
- The hostname of the AP
- The network name
-
Which of the following would not be a cause of an inability to connect to the Internet?
- The IP address of the computer
- The MAC address of the computer
- The default gateway address of the computer
- The DNS server address of the computer
-
Which of the following commands could be used to see if HTTP is working on a server?
telnet 192.168.5.5ping 192.168.5.5 :80telnet 192.168.5.65 80Pathping 192.168.5.5
-
What is the code number of a destination unreachable message when it indicates the destination host is unreachable?
- 0
- 1
- 2
- 3
-
You receive a destination unreachable message with no source IP address. Where is it coming from?
- A remote router
- A remote DNS server
- A local DNS server
- The local router
-
When the default gateway address is incorrect on the router, which connections will succeed?
- From a local device to a remote device
- From a remote device to a local device
- From a local device to the Internet
- From a local device to a local device
-
Which server could be the source of an inability to connect to a local host by name?
- NAT server
- SQL server
- DNS server
- Web server
-
At what layer of the OSI model are devices in different VLANs separated?
- Layer 1
- Layer 2
- Layer 4
- Layer 7
-
Which of the following features can be used to prevent unauthorized devices from connecting to a switch?
- NAT
- Port security
- Portfast
- Cipher
-
Which of these is the default mask of a Class B network?
- 255.0.0.0
- 255.255.0.0
- 255.255.255.0
- 255.255.255.255
-
Which of the following features can administrators use to create smaller networks called subnets by manipulating the subnet mask of a larger classless or major network?
- NAT
- CIDR
- DHCP
- DNS
-
What command is used on a router to identify the routes of which the router is aware?
ip routeshow routeroute printshow ip route
-
Which commands are used on a router to identify the path taken to a destination network? (Choose two.)
traceroutetracertipconfig/tracetrace
