Chapter 2. Computer Systems Security
This chapter covers the following subjects:
Computer Systems Security Threats—This portion of Chapter 2 can help you to differentiate between the various computer security threats you should be aware of for the exam including malware in all of its forms, spam, privilege escalation, and more. Then we discuss how to defend against those threats in a proactive way, and how to fix problems that do occur in the case that threats have already manifested themselves. By far, this is the most important section of this chapter; study it carefully!
Implementing Security Applications—In this section, you learn how to select, install, and configure security applications such as personal firewalls, antivirus programs, and host-based intrusion detection systems. You’ll be able to distinguish between the various tools and decide which is best for the different situations you’ll see in the field.
Securing Computer Hardware and Peripherals—Here we delve into the physical; how to protect a computer’s hardware, BIOS, and peripherals. We also discuss how to protect cell phones and USB devices.
This chapter covers the CompTIA Security+ SY0-201 objectives 1.1, 1.2, and 1.5.
Simply stated, the most important part of a computer is the data. The data must be available, yet secured in such a way so that it can’t be tampered with. Computer systems security is all about the security threats that can compromise an operating system and the data held within. Threats such as viruses, Trojans, and spyware are extremely prevalent in today’s society. They are a big part of this chapter, and this chapter is an important part of the book. But it doesn’t stop there, your computer can be accessed in other ways including via the BIOS and by external devices. And “computer” doesn’t just mean that desktop computer at a user’s desk. It also means laptops, PDAs, and cell phones—actually any other devices that have processing power and an operating system. These threats can be eliminated by implementing security applications on every one of your client computers on the network. Applications that can help to secure your computers against malware threats include antivirus programs, antispyware applications, personal firewalls, and host-based intrusion detection systems.
By implementing these security applications and ensuring that they are updated on a regular basis, you can stave off the majority of malicious attacks that can target a computer system.
Foundation Topics: Computer Systems Security Threats
To combat the various security threats that can occur on a computer system, we first need to classify them. Then we need to define how these threats can be delivered to the target computer. Afterward we can discuss how to prevent security threats from happening and troubleshoot them if they do occur. Let’s start with the most common computer threat and probably the most deadly—malicious software.
Malicious Software
Malicious software, or malware, is software designed to infiltrate a computer system and possibly damage it without the user’s knowledge or consent. Malware is a broad term used by computer professionals to include viruses, worms, Trojan horses, spyware, rootkits, adware, and other types of undesirable software.
Of course, we don’t want malware to infect our computer system, but to defend against it we first need to define it and categorize it. Then we can put preventative measures into place. It’s also important to locate and remove/quarantine malware from a computer system in the case that it does manifest itself.
For the exam, you need to know about several types of malware. For the past several years, an emphasis shift from viruses to spyware has occurred. Most people know about viruses and have some kind of antivirus software running. However, many people are still confused about exactly what spyware is, how it occurs, and how to protect against it. Because of this, computer professionals spend a lot of time fixing spyware issues and training users on how to protect against them in the future. However, viruses are still a valid foe; let’s start by discussing them.
Viruses
A virus is code that runs on a computer without the user’s knowledge; it infects the computer when the code is accessed and executed. For viruses to do their dirty work, they first need to be executed by the user in some way. A virus also has reproductive capability and can spread copies of itself throughout the computer if it is first executed by the user. By infecting files accessed by other computers, the virus can spread to those other systems as well. The problem is that computers can’t call in sick on Monday; they need to be up and running as much as possible, more than your average human.
One well-known example of a virus is the Love Bug. Originating in 2000, this virus would arrive by an e-mail titled “I love you” with an attachment named love-letter-for-you.txt.vbs, or one of several other permutations of this fictitious love. Some users would be tricked into thinking this was a text file, but the extension was actually .vbs, short for Visual Basic script. This virus deleted files, sent usernames and passwords to its creator, infected 15 million computers, and supposedly caused $5 billion in damage. Educate your users on how to screen their e-mail!
You might encounter several different types of viruses:
![]()
• Boot sector—Initially loads into the first sector of the hard drive; when the computer boots, the virus then loads into memory.
• Macro—Usually placed in documents and e-mailed to users in the hopes that the user will open the document, thus executing the virus.
• Program—Infects executable files.
• Polymorphic—Can change every time is it executed in an attempt to avoid antivirus detection.
• Stealth—Uses various techniques to go unnoticed by antivirus programs.
• Armored—These protect themselves from antivirus programs by tricking the program into thinking that it is located in a different place from where it actually resides. Essentially, it has a layer of protection that it can use against the person who tries to analyze it; it will thwart attempts by analysts to examine its code.
• Multipartite—A hybrid of boot and program viruses that attacks the boot sector or system files first and then attacks the other.
Worms
Worms are much like viruses except they self-replicate whereas a virus does not. Worms take advantage of backdoors and security holes in operating systems and applications. They look for other systems on the network or through the Internet that are running the same applications and replicate to those other systems. With worms, the user doesn’t need to access and execute the malware. A virus needs some sort of carrier to get it where it wants to go and needs explicit instructions to be executed, or it must be executed by the user. The worm does not need this carrier or explicit instructions to be executed.
A well-known example of a worm is Nimda (admin backward), which propagated automatically through the Internet in 22 minutes in 2001, causing widespread damage. It propagated through network shares, mass e-mailing, and operating system vulnerabilities.
Trojan Horses
Trojan horses, or simply Trojans, appear to perform wanted functions but are actually performing malicious functions behind the scenes. These are not technically viruses and can easily be downloaded without noticing them. Remote access Trojans (RATs) are the most common type of Trojan, for example Back Orifice or NetBus; their capability to allow an attacker higher administration privileges than the owner of the system makes them dangerous as well. Another example of a remote access Trojan (also known as a backdoor Trojan) is SubSeven, as shown in Figure 2-1. As you can see in the figure, this program has the capability to scan for unprotected hosts and make all kinds of changes to a host when connected. A program like this was not designed to be used maliciously, but programs like these are easy for an average person to download and use. When a target computer is controlled by an attacker, it could easily become a robot (or simply a bot), carrying out the plans of the attackers at their command.
Figure 2-1. Example of a Remote Access Trojan Program

Note
It should go without mentioning, but I’ll mention it anyway. Take extreme care when dealing with applications such as SubSeven; they are dangerous! During the writing of this book, I set up a test computer on a segregated network as my guinea pig, so to speak. This computer is where I run tests on viruses, spyware, Trojans, and malicious applications. I call it a “clean computer.” This computer never sees any of my other live networks, does not connect to the Internet, and is wiped when tests are complete. Please be careful and use test systems and test networks when assessing malware and antimalware applications.
Spyware
Spyware is a type of malicious software either downloaded unwittingly from a website or installed along with some other third-party software. Usually, this malware collects information about the user without the user’s consent. It could be as simple as a piece of code that logs what websites you access, or go as far as a program that records your keystrokes. Spyware is also associated with advertising (those pop-ups that just won’t go away!) and could possibly change the computer configuration without any user interaction; for example, redirecting a browser to access websites other than those wanted. Adware usually falls into the realm of spyware because it pops up advertisements based on what it has learned from spying on the user. Grayware is another general term that describes applications that are behaving improperly but without serious consequences. It is associated with spyware, adware, and joke programs. Very funny...not. One example (of many) of spyware is the Internet Optimizer, which redirects IE error pages out to other website’s advertising pages.
Rootkits
A rootkit is a type of software designed to gain administrator-level control over a computer system without being detected. The term is a combination of the words “root” (meaning the root user in a UNIX/Linux system or administrator in a Windows system) and “kit” (meaning software kit). Usually, the purpose is to perform malicious operations on a target computer at a later date without the knowledge of the administrators or users of that computer. Rootkits can target the BIOS, boot loader, kernel, and more. An example of a boot loader rootkit is the Evil Maid Attack; this attack can extract the encryption keys of a full disk encryption system, which we discuss more later. Rootkits are difficult to detect because they are activated before the operating system has fully booted. A rootkit might install hidden files, processes, and hidden user accounts. Because rootkits can be installed in hardware or software, they can intercept data from network connections, keyboards, and so on.
Spam
Spam is the abuse of electronic messaging systems such as e-mail, broadcast media, instant messaging, and so on. Spammers send unsolicited bulk messages indiscriminately, usually without benefit to the actual spammer, because the majority of spam is either deflected or ignored. Companies with questionable ethics condone this type of marketing (usually set up as a pyramid scheme) so that the people at the top of the marketing chain can benefit; however, it’s usually not worthwhile for the actual person that sends out spam.
The most common form of spam is e-mail spam, which is one of the worst banes of network administrators. Spam can clog up resources and possibly cause a type of denial of service to an e-mail server if there is enough of it. It can also mislead users, in an attempt at social engineering. And the bulk of network-based viruses are transferred through spam e-mails. Yikes! The worst type of spamming is when a person uses another organization’s e-mail server to send the spam. Obviously illegal, it could also create legal issues for the organization that owns the e-mail server. Just about everyone has seen a spam e-mail, and in the rare case that you haven’t, check out this link for some pretty horrific examples:
www.antespam.co.uk/spam-resource/
Summary of Malware Threats
Table 2-1 summarizes the malware threats discussed up to this point.
Table 2-1. Summary of Malware Threats

![]()
Ways to Deliver Malicious Software
Malware is not sentient (...not yet) and can’t just appear out of thin air; it needs to be transported and delivered to a computer or installed on a computer system in some manner. This can be done in several ways. The simplest way would be for attackers to gain physical access to an unprotected computer and perform their malicious work locally. But because it can be difficult to obtain physical access, this can be done in several other ways, as shown in the upcoming sections. Some of the methods listed next can also be used by an attacker to simply gain access to a computer, make modifications, and so on, in addition to delivering the malware.
Via Software, Messaging, and Media
Malware can be delivered via software in a lot of different ways. A person who e-mails a zipped file might not even know that malware also exists in that file. The recipients of the e-mail will have no idea that the extra malware exists unless they have software to scan their e-mail attachments for it. Malware could also be delivered via FTP. Because FTP servers are inherently insecure, it’s easier than you might think to upload insidious files and other software. Malware is often found among P2P networks and bit torrents. Great care should be taken by users who use these technologies. Malware can also be embedded within, and distributed by, websites through the use of corrupting code or bad downloads. Malware can even be distributed by advertisements. And of course, removable media can victimize a computer as well. CD-ROMs, DVDs, and USB flash drives can easily be manipulated to automatically run malware when they are inserted into the computer. This is when AutoRun is not your friend! The removable media could also have hidden viruses or worms and possibly logic bombs configured to set that malware off at specific times.
Active Interception
Active interception (also known as active inception) normally includes a computer placed between the sender and the receiver in an effort to capture and possibly modify information. If a person can eavesdrop on your computer’s data session, then that data can be stolen, modified, or exploited in other ways. Examples of this include session theft and man-in-the-middle attacks. For more information on these attacks, see the section titled “Ports, Protocols, and Malicious Attacks” in Chapter 5, “Network Design Elements and Threats.”
Privilege Escalation
Privilege escalation is the act of exploiting a bug or design flaw in a software or firmware application to gain access to resources that normally would’ve been protected from an application or user. This results in a user gaining additional privileges, more than were originally intended by the developer of the application; for example, if a regular user gains administrative control, or if a particular user can read another user’s e-mail without authorization.
Backdoors
Backdoors are used in computer programs to bypass normal authentication and other security mechanisms in place. Originally, backdoors were used by developers as a legitimate way of accessing an application, but soon after they were implemented by attackers who would use backdoors to make changes to operating systems, websites, and network devices. Or the attacker would create a completely new application that would act as a backdoor, for example Back Orifice, which enables a user to control a Windows computer from a remote location. Quite often, it is installed via a Trojan horse; this particular one is known as a remote access Trojan or RAT. Some worms install backdoors on computers so that remote spammers can send junk e-mail from the infected computers, or so an attacker can attempt privilege escalation. Unfortunately, there isn’t much that can be done about backdoors aside from updating or patching the system infected and keeping on top of updates. However, if network administrators were to find out about a new backdoor, they should inform the manufacturer of the device or the application as soon as possible. Backdoors are less common nowadays, because their practice is usually discouraged by software manufacturers and by makers of network devices.
Logic Bombs
Logic bombs are code that has, in some way, been inserted into software; it is meant to initiate one of many types of malicious functions when specific criteria are met. Logic bombs blur the line between malware and a malware delivery system. They are indeed unwanted software but are intended to activate viruses, worms, or Trojans at a specific time. Trojans set off on a certain date are also referred to as time bombs. The logic bomb ticks away until the correct time, date, and other parameters have been met. So, some of the worst bombs do not incorporate an explosion whatsoever. The logic bomb could be contained within a virus or loaded separately. Logic bombs are more common in the movies than they are in real life, but they do happen, and with grave consequences; but more often than not, they are detected before they are set off. If you, as a systems administrator, suspect that you have found a logic bomb, or a portion of the code of a logic bomb, you should notify your superior immediately and check your organization’s policies to see if you should take any other actions. Action could include placing network disaster recovery processes on stand-by; notifying the software vendor; and closely managing usage of the software including, perhaps, withdrawing it from service until the threat is mitigated. Logic bombs are the evil cousin of the Easter egg.
Easter eggs historically have been a platonic extra that was added to an OS or application as a sort of joke; quite often, it was missed by quality control and subsequently released by the manufacturer of the software. An example of an Easter egg is the capability to force a win in Windows XP’s Solitaire by pressing the ALT+Shift+2 keys simultaneously. Easter eggs are not normally documented (being tossed in last minute by humorous programmers) and are meant to be harmless, but nowadays they are not allowed by responsible software companies and are thoroughly scanned for. Because an Easter egg (and who knows what else) can possibly slip past quality control, and the growing concerns about malware in general, many companies have adopted the idea of Trustworthy Computing, which is a newer concept that sets standards for how software is designed, coded, and checked for quality control. Sadly, as far as software goes, the Easter egg’s day has passed.
Botnets and Zombies
I know what you are thinking—the names of these attacks and delivery methods are getting a bit ridiculous. But bear with me; they make sense and are deadly serious. Allow me to explain—malware can be distributed throughout the Internet by a group of compromised computers, known as a botnet, and controlled by a master computer (where the attacker resides). The individual compromised computers in the botnet are called zombies. This is because they are unaware of the malware that has been installed on them. This can occur in several ways, including automated distribution of the malware from one zombie computer to another. Now imagine if all the zombie computers had a specific virus or other attack loaded, and a logic bomb was also installed, ready to set off the malware at a specific time. If this were done to hundreds or thousands of computers, a synchronized attack of great proportions could be enacted on just about any target. Often, this is known as a distributed denial of service, or DDoS, attack, and is usually perpetuated on a particularly popular server, one that serves many requests.
Preventing and Troubleshooting Malware
Now that we know the types of malware, and the ways that they can be delivered to a computer, let’s talk about how to stop them before they happen, and how to troubleshoot them if they do happen. Unfortunately, given the amount of computers you will work on, they will happen.
If a system is affected by malware, it might be sluggish in its response time or display unwanted pop-ups and incorrect home pages; or applications (and maybe even the whole system) could lock up or shut down unexpectedly. Quite often, malware uses CPU and memory resources directly or behind the scenes, causing the system to run slower than usual. In general, a technician should look for erratic behavior from the computer, as if it had a mind of its own! Let’s go over viruses and spyware, and show how to prevent them, and finally how to troubleshoot them if they do occur.
Preventing and Troubleshooting Viruses
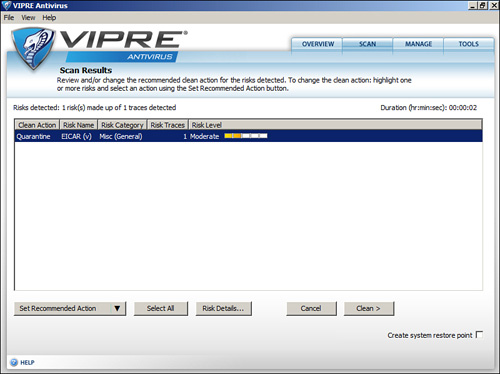
We can do several things to protect a computer system from viruses. First, every computer should have antivirus software running on it. McAfee, Norton, and Vipre are examples of manufacturers of AV software, but there are many others. Second, the AV software should be updated, which means that the software will require a current license; this is renewed yearly with most providers. When updating, be sure to update the AV engine and the definitions if you are doing it manually. Otherwise, set the AV software to automatically update at periodic intervals, for example, every day or every week. It’s a good idea to schedule regular full scans of the system within the AV software. Figure 2-2 shows an example of a scan that has detected a virus. It recommends that the virus be quarantined; this is the cleaning action that will be taken if you click the Clean button. This is actually one of many test viruses that can be created on a system; it doesn’t do any particular damage, but it verifies that your AV software can live up to its name.
Figure 2-2. Example of Detected Virus
Note
For a quick video of the Vipre AV software quarantining some malware, see the following link:
Next, we want to make sure that the computer has the latest service packs and updates available. This goes for the operating system and applications such as Microsoft Office. Backdoors into operating systems and other applications are not uncommon, and the OS manufacturers often release fixes for these breaches of security. In Windows XP, Automatic Updates can be configured by going to Start > Control Panel > Automatic Updates. In Windows Vista go to Start > Control Panel > System Maintenance > Windows Update. Then click the Change settings link.
Configure Automatic Updates according to your company’s policy. You can also check if your computer is up to date by going to Start > All Programs > Windows Update. In Windows XP, it directs you to a website that prompts you to install a Windows Update component and then checks if the computer has the latest security (and other) patches. In Windows Vista you can check for updates directly within the Automatic Updates program.
It’s also important to make sure that a firewall is available, enabled, and updated. A firewall closes all the inbound ports to your computer (or network) in an attempt to block intruders. The Windows Firewall is a built-in feature of Windows XP/Vista, and you might also have a SOHO router with a built-in firewall. By using both, you have two layers of protection from viruses and other attacks. You can access the Windows Firewall by navigating to Start > Control Panel > Windows Firewall. Keep in mind that you might need to set exceptions for programs that need to access the Internet. This can be done by the program, or the port used by the protocol, and can be configured in the Exceptions tab, enabling specific applications to communicate through the firewall while keeping the rest of the ports closed.
Another way to help prevent viruses is to use what I call “separation of OS and data” (similar to the term “separation of church and state” in concept but not in content!). This method calls for two hard drives. The operating system is installed to the C: drive, and the data is stored on the D: drive (or whatever letter you use for the second drive). This compartmentalizes the system and data, making it more difficult for viruses to spread and easier to isolate them when scanning. It also enables for easy reinstallation without having to back up data! You can accomplish a similar scenario by using two partitions on the same drive.
Note
There are other viruses that can affect other types of computers. PDAs, micro computers, Mac, and Linux are all susceptible, although not as commonly targeted as Windows operating systems. For example, the Phage virus can infect Palm PDA applications. Although this virus occurs rarely, Palm released an update to its operating system for the virus. It might seem to be a hassle to update a PC, Mac, or PDA, but quite often it is necessary, especially if your computer or mobile device is promiscuous; meaning that it has contact with foreign removable media, questionable websites, and unknown networks.
Finally, educate users as to how viruses can infect a system. Instruct them on how to screen their e-mails and tell them not to open unknown attachments. Show them how to scan removable media before copying files to their computer, or set up the computer to scan removable media automatically. Sometimes user education works; sometimes it doesn’t. One way to make user education more effective is to have a technical trainer educate your users, instead of doing it yourself. This can provide for a more engaging learning environment.
By using these methods, virus infection can be severely reduced. However, if a computer is infected by a virus, you want to know what to look for so that you can “cure” the computer.
Here are some typical symptoms of viruses:
• Computer runs slower than usual.
• Computer locks up frequently or stops responding altogether.
• Computer restarts on its own or crashes frequently.
• Disk drives and applications are not accessible or don’t work properly.
• Strange sounds occur.
• You receive unusual error messages.
• Display or print distortion occurs.
• New icons appear or old icons (and applications) disappear.
• There is a double extension on a file attached to an e-mail that was opened, for example: .txt.vbs or .txt.exe.
• Antivirus programs will not run or can’t be installed.
• Files have been corrupted or folders are created automatically.
Before making any changes to the computer, make sure that you back up critical data and verify that the latest updates have been installed to the OS and the AV software. Then, perform a thorough scan of the system using the AV software’s scan utility; if allowed by the software, run the scan in Safe Mode. Another option is to move the affected drive to a “clean machine,” a computer that is used solely for the purpose of scanning for malware, that does not connect to the Internet. This can be done by slaving the affected drive to an IDE, SATA, or eSATA port of the other computer and running the AV software on the clean machine to scan that drive. PC repair shops have this kind of isolated clean machine.
Hopefully, the AV software will find and quarantine the virus on the system. In the case that the AV software’s scan does not find the issue, or if the AV software has been infected and won’t run, you can try using an online scanner such as Trend Micro’s HouseCall: http://housecall.trendmicro.com/ or download Microsoft’s Malicious Software Removal Tool: www.microsoft.com/security/malwareremove/default.mspx.
In rare cases, you might need to delete individual files and remove Registry entries. This might be the only solution when a new virus has infected a system and there is no antivirus definition released. Instructions on how to remove viruses in this manner can be found on AV software manufacturers’ websites.
When it comes to boot sector viruses, your AV software is still the best bet. The AV software might use a boot disk to accomplish scanning of the boot sector, or it might have boot shielding built in. Some BIOS programs have the capability to scan the boot sector of the hard drive at startup; this might need to be enabled in the BIOS setup first. It is also possible to use the DOS SYS command to restore the first sector or the FDISK/MBR command to repair the master boot record within the boot sector, but a DOS-based boot disk is necessary to do this; it needs to be created on a DOS-based computer or downloaded from the Internet. Windows 2000 and XP offer the FIXMBR command available from the Recovery Console. Windows Vista offers the bootrec /fixmbr command from within the System Recovery Options Command Prompt. Keep in mind that the DOS, Recovery Console, and System Recovery Options Command Prompt methods might not fix the problem; they might render the hard drive inoperable depending on the type of virus. It is best to use the AV software’s various utilities that you have purchased for the system.
Preventing and Troubleshooting Worms and Trojans
Worms and Trojans can be prevented and troubleshot in the same manner as viruses. There are scanners for Trojans as well, for example: www.windowsecurity.com/trojanscan/. In some cases, AV software scans for worms and Trojans in addition to viruses. The application at this link and most AV software can easily detect RATs such as SubSeven, which was mentioned previously in the chapter, regardless of whether it is the actual attacker’s application or any .exe files that are part of the application and are used at the victim computer.
Preventing and Troubleshooting Spyware
Preventing spyware works in much the same manner as preventing viruses when it comes to updating the operating system and using a firewall. Also, because spyware has become much more common, antivirus companies have begun adding antispyware components to their software. Here are a few more things you can do to protect your computer in the hopes of preventing spyware:
• Download and install antispyware protection software. For example, Windows Defender, available at the following link: www.microsoft.com/windows/products/winfamily/defender/default.mspx. Other options include Spyware Doctor with Antivirus, SpyBot S&D (free), or one of the antivirus programs previously mentioned if it includes spyware protection. Be sure to keep the antispyware software updated.
• Adjust Internet Explorer security settings. This can be done by clicking Tools on the menu bar, selecting Internet Options, and accessing the Security tab. From there, the security level can be increased, and trusted and restricted sites can be established. (It’s a good thing.) Internet Explorer 7 and higher also have a phishing filter that you can turn on by going to Tools > Phishing Filter and clicking Turn on Automatic Website Checking. This attempts to filter out fraudulent online requests for usernames, passwords, and credit card information, which is also known as web-page spoofing. Higher security settings can also help to fend off session hijacking that is the act of taking control of a user session after obtaining or generating an authentication ID. Similar security settings are available on most of today’s web browsers.
• Uninstall unnecessary applications and turn off superfluous services (for example, Telnet and FTP if they are not used).
• Educate users on how to surf the web safely. User education is actually the number one method of preventing malware! Access only sites believed to be safe, and download only programs from reputable websites. Don’t click OK or Agree to close a window; instead press Alt+F4 on the keyboard to close that window. Be wary of file-sharing websites and the content stored on those sites. Be careful of e-mails with links to downloadable software that could be malicious.
• Consider technologies that discourage spyware. For example, use a browser that is less susceptible to spyware. Consider running a browser within a virtual machine, or take it to the next level and use a thin-client computer!
Here are some common symptoms of spyware:
• The web browser’s default home page has been modified.
• A particular website comes up every time you perform a search.
• Excessive pop-up windows appear.
• The network adapter’s activity LED blinks frequently when the computer shouldn’t be transmitting data.
• The firewall and antivirus programs turn off automatically.
• New programs, icons, and favorites appear.
• Odd problems occur within windows (slow system, applications behaving strangely, and such).
• The Java console appears randomly.
To troubleshoot and repair systems infected with spyware, first disconnect the system from the Internet. Then, try uninstalling the program from Add/Remove Programs in Windows XP, or Programs and Features in Windows Vista. Some of the less malicious spyware programs can be fully uninstalled without any residual damage. Be sure to reboot the computer afterward and verify that the spyware was actually uninstalled! Next, scan your system with the AV software to remove any viruses that might have infested the system, which might get in the way of a successful spyware removal. Again, do this in Safe Mode if the AV software offers that option.
Note
In some cases, Safe Mode is not enough, and you need to boot off of a CD (Knoppix or BartPE, for example) and then rerun the scans.
Next, scan the computer with the antispyware software of your choice in an attempt to quarantine and remove the spyware. You can use other programs, such as HijackThis, in an attempt to remove malware, but be careful with these programs because you will probably need to modify the Registry. Remove only that which is part of the infection.
Finally, you need to make sure that the malware will not reemerge on your system. To do this, check your home page setting in your browser, verify that your host’s file hasn’t been hijacked (located in C:WINDOWSsystem32driversetc), and make sure that unwanted websites haven’t been added to the Trusted Sites within the browser.
Preventing and Troubleshooting Rootkits
A successfully installed rootkit enables unauthorized users to gain access to a system acting as the root or administrator user. Rootkits are copied to a computer as a binary file; this binary file can be detected by signature-based and heuristic-based antivirus programs, which we speak more to later in this chapter in the “Host-Based Intrusion Detection Systems” section. However, after the rootkit is executed, it can be difficult to detect. This is because most rootkits are collections of programs working together that can make many modifications to the system. When subversion of the operating system takes place, that OS can’t be trusted, and it is difficult to tell if your antivirus programs run properly, or if any of your other efforts have any effect. Although security software manufacturers are attempting to detect running rootkits, it is doubtful that they will be successful. The best way to identify a rootkit is to use removable media (USB flash drive, or a special rescue CD-ROM) to boot the computer. This way, the operating system is not running, and therefore, the rootkit is not running, making it much easier to detect by the external media. Programs that can be used to detect rootkits include the following:
• Microsoft Sysinternals Rootkit Revealer: http://technet.microsoft.com/en-us/sysinternals/bb897445.aspx (for Windows systems)
• chkrootkit: www.chkrootkit.org/ (for UNIX-based systems)
Unfortunately, because of the difficulty involved in removing a rootkit, the best way to combat rootkits is to reinstall all software. Generally, a PC technician, upon detecting a rootkit, will do just this, because it usually takes less time than attempting to fix all the rootkit issues, plus it can verify that the rootkit has been removed completely.
Preventing and Troubleshooting Spam
The Internet needs to be conserved, just like our environment. Might sound crazy, but it’s true. There is only so much space to store information, and only so much bandwidth that can be used to transfer data. It is estimated that spam causes billions of dollars in fraud, damage, lost productivity and so on every year; it’s the single biggest gobbler of Internet resources. The worst part is that most spammers do not bear the burden of the costs involved; someone else usually does. So the key is to block as much spam as possible, report those who do it, and train your users. Here are several ways that spam can be reduced:
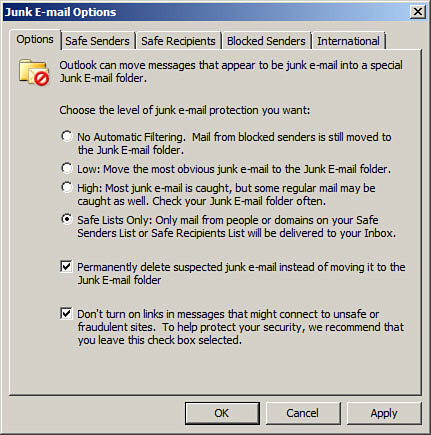
• Use a spam filter—This can be purchased for the server-side as software or as an appliance. One example of an appliance is the Barracuda Networks Spam Firewall (www.barracudanetworks.com). Barracuda monitors spam activity and creates and updates whitelists and blacklists, all of which can be downloaded to the appliance automatically. Network administrators should also block any e-mails that include attachments that do not comply with company rules. For example, some companies enable only .zip, .txt, and .doc to go through their e-mail attachment filter. If your company uses a web-hosting company for its website and for e-mail, that company often has many spam filtering options. And on the client-side, you can configure Outlook and other mail programs to a higher level of security against spam; this is usually in the Junk E-mail Options area, as shown in Figure 2-3. Spam filters can also be installed on individual clients. Many popular antivirus suites have built-in spam filtering. Make sure it is enabled! Just as an example, my personal e-mail account (which I try to keep private) has a filter at the web hosting company, plus my antivirus software package filters the e-mails, and Outlook is set to High in the Junk E-mail Options page, and of course, I still get at least 30 or 40 spams to my inbox every single day.
Figure 2-3. Outlook 2003 Junk E-mail Options Set at Highest Level of Security
• Close open mail relays—SMTP servers can be configured as open mail relays, this enables anyone on the Internet to send e-mail through the SMTP server. Although this is desirable to customers of the company who runs the SMTP server, it is not desirable to the company to have a completely open mail relay. So, open mail relays should either be closed or configured in such a way that only customers and properly authenticated users can use them. Open mail relays are also known as SMTP open relays.
• Remove e-mail address links from the company website—Replace these with online forms (secure PHP or CGI forms) that enable a person to contact the company but not enable them to see any company e-mail addresses. Use a separate advertising e-mail address for any literature or ads. Consider changing this often; marketing people might already do this as a form of tracking leads.
• Use whitelists and blacklists—Whitelists are lists of e-mail addresses or entire e-mail domains that are trusted, whereas blacklists are not trusted. These can be set up on e-mail servers, e-mail appliances, and within mail client programs such as Outlook.
• Train your users—Have them create and use a free e-mail address whenever they post to forums and newsgroups, and not to use their company e-mail for anything except company-related purposes. Make sure that they screen their e-mail carefully; this is also known as e-mail vetting. E-mail with attachments should be considered volatile unless the user knows exactly where it comes from. Train your employees never to make a purchase from an unsolicited e-mail. Also, explain the reasoning behind using BCC when sending an e-mail to multiple users. Let’s not beat around the bush; we all know that this is the most difficult thing to ask of a company and its employees who have more important things to do. However, some companies enforce this as policy and monitor users’ e-mail habits. Some companies have a policy in place in which users must create a “safe” list. This means that only the addresses on that list can send e-mail to the user and have it show up in the inbox.
You Can’t Save Every Computer from Malware!
On a final and sad note, sometimes computers become so infected with malware that they cannot be saved. In this case, the data should be backed up (if necessary by removing the hard drive and slaving it to another system), and the operating system and applications reinstalled. The BIOS of the computer should also be flashed. After the reinstall, the system should be thoroughly checked to make sure that there were no residual effects and that the system’s hard drive performs properly.
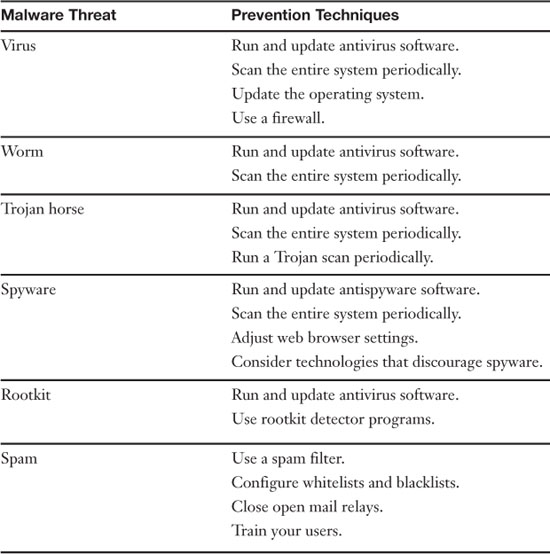
Summary of Malware Prevention Techniques
Table 2-2 summarizes the malware prevention techniques we have discussed up to this point.
Table 2-2. Summary of Malware Prevention Techniques
![]()
Implementing Security Applications
In the preceding section, we discussed antivirus suites such as McAfee, Norton, and so on. These application suites usually have antivirus, antispyware, and antispam components. Quite often, they also have a built-in firewall as well, known as a personal firewall. And perhaps the application suite also has a built-in intrusion detection system (IDS); a piece of software that monitors and analyzes the system in an attempt to detect malicious activities. The type of IDS that a client computer would have is a host-based intrusion detection systems (HIDS). But there are other types of standalone software firewalls and HIDS; we cover these in just a bit. Another type of built-in security is the pop-up blocker. Integrated into web browsers and web browser add-ons, pop-up blockers help users to avoid websites that could be malicious. Let’s discuss these security applications in a little more depth, starting with personal firewalls.
Personal Software Firewalls
Personal firewalls are applications that protect an individual computer from unwanted Internet traffic. They do so by way of a set of rules and policies. Some personal firewalls prompt the user for permission to enable particular applications to access the Internet. In addition, some personal firewalls now also have the capability to detect intrusions to a computer and block that intrusion; this is a basic form of a HIDS that we talk more about in the next section.
Examples of software-based personal firewalls include the following:
• Windows Firewall—Built in to Windows, the basic version is accessible from the Control Panel in Windows Vista and later and from the network adapter’s Properties window in older versions of Windows (XP and 2000). The advanced version, the Windows Firewall with Advanced Security, can be accessed (for example in Windows Vista) by navigating to Start > Administrative Tools > Windows Firewall with Advanced Security. This advanced version enables a user to complete more in-depth configurations such as custom rules.
Note
For a quick tutorial on using the Windows Firewall with Advanced Security, see the following link:
• ZoneAlarm—Originally a free product that is still available (see the following link), this was purchased by Check Point and is now also offered as part of a suite of security applications. Go to www.zonealarm.com/security/en-us/zonealarm-pc-security-free-firewall.htm.
• ipfirewall—Built in to Mac OS and some versions of FreeBSD.
Antivirus application suites, such as Norton 360, McAfee Total Protection, Kaspersky Internet Security, and so on, include personal firewalls as well. This has become a common trend over the past few years, and you can expect to see personal firewall applications built in to most antivirus application suites in the future.
Because they are software, and because of the ever-increasing level of Internet attacks, personal firewalls should be updated often, and in many cases it is preferable to have them auto-update, although this depends on your organization’s policies.
A personal firewall is software, and as such, it can utilize some of the computer’s resources. In the late ’90s and early 2000s, there were some complaints that particular antivirus suites used too much CPU power and RAM, sometimes to the point of crashing the computer; in some cases this was because of the resources used by the firewall. So a smart systems administrator will select an application suite that has a small footprint. Some organizations opt not to use personal firewalls on client computers and instead focus more on the network-based firewalls and other security precautions. This can vary but should be carefully analyzed before a decision is made.
Personal firewalls (like any software application) can also be the victim of attack. If worms or other malware compromise a system, the firewall could be affected. This just reinforces the concept that antivirus suites should be updated often; daily updates would be the optimal solution.
A common scenario for security in small offices and home offices is to have a 4-port SOHO router/firewall protecting the network and updated personal firewalls on every client computer. This combination provides two levels of protection for the average user, which is usually adequate. But larger networks usually concentrate more on the network firewall (or firewalls) and network-based IDSs than on personal firewalls; although, it is common to see both levels of firewall security in larger network as well.
Host-Based Intrusion Detection Systems
Let’s start by talking about intrusion detection systems (IDS) in general. An IDS is used to monitor an individual computer system or a network, or portion of a network and analyze data that passes through to identify incidents, attacks, and so forth. You should be aware of two types of IDSs for the exam:
• Host-based intrusion detection system (HIDS)—Loaded on an individual computer; it analyzes and monitors what happens inside that computer, for example, if any changes have been made to file integrity. A HIDS is installed directly within an operating system, so it is not considered to be an “inline” device, unlike other network-based IDS solutions. One of the advantages of using a HIDS is that it can interpret encrypted traffic. Disadvantages include price and resource-intensive, and by default the HIDS object database is stored locally; if something happens to the computer the database will be unavailable.
• Network intrusion detection system (NIDS)—Can be loaded on the computer, or can be a standalone appliance, but it checks all the packets that pass through the network interfaces, enabling it to “see” more than just one computer; because of this, a NIDS is considered to be an “inline” device. Advantages include the fact that it is less expensive and less resource intensive, and an entire network can be scanned for malicious activity as opposed to just one computer. Of course, the disadvantage is that a NIDS cannot monitor for things that happen within an operating system. For more information about NIDS, see the section “NIDS Versus NIPS” in Chapter 6, “Network Perimeter Security.”
Following are two main types of monitoring that an IDS can carry out:
• Statistical anomaly—Establishes a performance baseline based on normal network traffic evaluations. It then compares current network traffic activity with the baseline to detect whether it is within baseline parameters. If the sampled traffic is outside baseline parameters, an alarm is triggered and sent to the administrator.
• Signature-based—Network traffic is analyzed for predetermined attack patterns, which are known as signatures. These signatures are stored in a database that must be updated regularly to have effect. Many attacks today have their own distinct signatures. However, only the specific attack that matches the signature will be detected. Malicious activity with a slightly different signature might be missed.
For more information about the various types of on a monitoring methodologies, see the section “Monitoring Methodologies” in Chapter 11, “Monitoring and Auditing.”
IDS solutions need to be accurate and updated often to avoid the misidentification of legitimate traffic or, worse, the misidentification of attacks. Following are two main types of misidentification you need to know for the exam:
• False positive—If the IPS identifies legitimate activity as something malicious, it would be known as a false positive.
• False negative—If the IPS does not have a particular attack’s signature in its database, and lets that attack run its course thinking it is legitimate, it is known as a false negative. More information about false positives, false negatives, and other IDS terminology can be found in Chapter 8, “Physical Security and Authentication Models.”
Some antivirus application suites have basic HIDS functionality, but true HIDS solutions are individual and separate applications that monitor log files, check for file integrity, monitor policies, detect rootkits, and alert the administrator in real-time of any changes to the host. This is all done in the hopes to detect malicious activity such as spamming, zombie/botnet activity, identify theft, keystroke logging, and so on. A few examples of HIDS applications include the following:
• Trend Micro OSSEC (www.ossec.net)—A free solution with versions for Windows, Mac, Linux and UNIX
• Osiris (http://osiris.shmoo.com)—Another free download for Windows or Linux
• Verisys (www.ionx.co.uk/products/verisys)—A commercial HIDS solution for Windows
It is important to protect the HIDS database because this can be a target for attackers. It should either be encrypted, stored on some sort of read-only memory, or stored outside the system.
If an IDS observes an incident, it notifies the systems or network administrator so that she might quarantine and fix the problem. However, over time, the need for prevention has become more desirable, and so intrusion prevention systems (IPS) and intrusion detection and prevention systems (IDPS) were developed. These not only detect incidents and attacks, but also attempt to prevent them from doing any real damage to the computer or to the network.
Pop-Up Blockers
For a website to generate revenue, a webmaster quite often advertises other products and services, charging fees to the organization that creates these products and services. The only way that an organization can continually advertise on the website is if it is positive it will get a certain amount of click-through response for its ads. However, web users quickly learn to define which windows are advertisements and which aren’t. So advertisers need to constantly create new and exciting ways to advertise their products. The traditional JavaScript-based pop-up window doesn’t do as good of a job as it used to because many web browsers have built-in pop-up blockers, but you still see tons of them on the Internet, and they can take their toll on user productivity—and can be detrimental to the user’s computer. For example, some pop-up ads, if clicked, force the user to go to one or more separate websites that could have harmful code. Or worse yet, the pop-up itself could have malicious code built in; perhaps the Close button within the ad launches some other process altogether. Some attackers create entire websites with malicious pop-ups just to infect as many computers as they can. As mentioned in Chapter 1, “Introduction to Security,”: “Why take advantage of users? Because they are there to be taken advantage of!” Not that I condone this behavior, but this mentality is infectious, making pop-ups and all their cousins common; so systems administrators should try their best to block pop-ups. One way to do this is with a pop-up blocker. Following are some examples of web browsers that have built-in pop-up blocking functionality, and web browser add-on pop-up blocking tools:
• Internet Explorer
• Mozilla Firefox
• Google Toolbar (add-on) http://toolbar.google.com
• Adblock Plus (add-on) http://adblockplus.org/en/
• IE7Pro (add-on) www.ie7pro.com/
One of the problems with pop-up blocking is that it might block content that is not an advertisement but instead is integral to the actual website. For example, on my website www.davidlprowse.com, I run a bulletin board system that has the capability to enable users to know that they have new private messages from other users; one of the options is for this alert to show up as a pop-up window. Because so many users do not see this alert, and instead get a message from the browser that says “Pop-up blocked” or something similar, which can look sort of suspicious to the user, I decided to turn that functionality off and instead let the main login page of the website (and e-mails) notify the user of new messages. This type of philosophy should be taken into account by webmasters when they define what the purpose of their website will be. Proper website functionality should be integrated directly into the actual web page, because most users ignore pop-ups or consider them malicious and attempt to close them, or block them, if they weren’t otherwise blocked automatically by their browser.
When dealing with the previously listed applications and add-ons, pop-up blocking is known as ad filtering; but this can be taken to another level, known as content filtering. Content filters block external files that use JavaScript or images from loading into the browser. Content filtering continues to become more and more important as advertisers become more and more clever. Internet Explorer version 8 has built-in content filtering, and Adblock Plus can provide the same functionality for Mozilla Firefox, plus there are proxy-based programs such as Squid that can filter content (among other things) for multiple computers. For more about proxy servers, see the section “Firewalls and Network Security” in Chapter 6.
Of course, advertisers have some new tricks in an attempt to get past the pop-up blockers and content filters: flash-based pop-ups, pop-under ads, DHTML hover ads, and so on. Advertisers continue to battle for ad space with smart new ad types, so systems administrators should be prepared to update their clients’ web browsers and browser add-ons on a regular basis.
Securing Computer Hardware and Peripherals
Now that the operating system is better secured, let’s talk about securing other types of computer hardware, external peripheral devices, and the BIOS.
Although it’s important to secure PCs, Macs, the servers, and other hosts on the network, we can’t forget about wireless devices such as laptops, PDAs, and cell phones. And also a plethora of devices can be connected to a computer system, for example, USB flash drives, external SATA hard drives, and removable media such as CD-ROMs and DVDs.
Then of course, there’s the underlying firmware without which our computer could not run; I’m speaking of the BIOS.
Securing the BIOS
The BIOS can be the victim of malicious attacks; for mischievous persons it can also act as the gateway to the rest of the system. Protect it! Or your computer just might not boot. Following are a few ways to do so:
• Use a BIOS password—The password that blocks unwanted persons from gaining access to the BIOS is the supervisor password. Don’t confuse it with the user password (or power-on password) employed so that the BIOS can verify a user’s identity before accessing the operating system. Both of these are shown in Figure 2-4. Because BIOS passwords are relatively weak compared to other types of passwords, organizations often use one password for the BIOS on every computer in the network; in this scenario, there is all the more reason to change the password at regular intervals. Because most computers’ BIOS password can be cleared by opening the computer (and either removing the battery or changing the BIOS jumper), some organizations opt to use locking cables or a similar locking device that deters a person from opening the computer.
Figure 2-4. BIOS and Drive Lock Passwords

![]()
On a semi-related note, many laptops come equipped with drive lock technology; this might simply be referred to as an HDD password. If enabled, it prompts the user to enter a password for the hard drive when the computer is first booted. If the user of the computer doesn’t know the password for the hard drive, the drive locks and the OS does not boot. An 8-digit, or like, hard drive ID usually associates the laptop with the hard drive installed (refer to Figure 2-4). On most systems this password is clear by default, but if the password is set and forgotten, it can usually be reset within the BIOS. Some laptops come with documentation clearly stating the BIOS and drive lock passwords.
• Flash the BIOS—Flashing describes the updating of the BIOS. By updating the BIOS to the latest version, you can avoid possible exploits and BIOS errors that might occur. All new motherboards issue at least one new BIOS version within the first 6 months of the motherboard’s release.
• Configure the BIOS—Set up the BIOS to reduce the risk of infiltration. For example, change the BIOS boot order (boot device priority) so that it looks for a hard disk first and not any type of removable media. Also, if a company policy requires it, disable removable media including the floppy drives and eSATA and USB ports.
Securing Storage Devices
Removable Storage
Removable storage, or removable media, includes CD-ROMs, DVDs, USB devices, eSATA devices, and even floppy disks in some cases. A network administrator can prevent access to removable media from within the BIOS and within the operating system policies. In many companies, all removable media is blocked except for specifically necessary devices, which are approved on a case-by-case basis. Users should be trained on the proper usage of removable media and should not be allowed to take any data home with them. Users who sometimes work from home should do so via a VPN connection to keep the data confidential, yet accessible.
USB devices must be carefully considered. They are small but can transport a lot of data. These devices can be the victim of attacks and the delivery mechanism for attacks to a computer. For example, a USB flash drive might have data files or entire virtual operating systems that can be exploited by viruses and worms. Also, an attacker can attempt to install a special type of virus or worm onto the flash drive executed when the flash drive connects to the computer; in this scenario the computer is the target for the malware. Organizations must decide whether to allow USB devices to be used. Operating system group policies can be implemented to enforce what users are allowed to use USB devices. As mentioned earlier, the BIOS can also disable the use of USB devices on a local computer. Finally, the data on a USB device can be encrypted with various programs, for example, TrueCrypt (www.truecrypt.org/), or you might opt to purchase a secure USB flash drive, for example, a flash drive by Ironkey (https://www.ironkey.com/).
Network Attached Storage
Network attached storage (NAS) is a storage device that connects directly to your Ethernet network. Examples of NAS include simple devices such as the D-Link DNS 323. This device contains two hard drives enabling you to set up RAID 1 mirroring, which protects your data if one drive fails. A more advanced example of NAS would be a device that looks more like a computer and might house up to 32 drives and contain terabytes of data. Possibly hot-swappable, these drives can be physically replaced, and the data can be rebuilt in a short amount of time. A NAS device might be part of a larger storage area network (SAN); therefore, network security should also be considered when implementing any type of NAS. For more information on network security, see Chapters 5 through 7. To protect a single NAS device consider data encryption, authentication, and constant secure logging of the device.
Whole Disk Encryption
Encryption is a huge component of today’s computer security. By encrypting information, the data is rearranged in such a way in which only the persons with proper authentication can read it. To encrypt an entire hard disk, you need some kind of full disk encryption software. Several are currently available on the market; one developed by Microsoft is called BitLocker—available only on Vista Ultimate and Vista Enterprise. This software can encrypt the entire disk which, after complete, is transparent to the user. Following are some requirements for this:
• Trusted Platform Module (TPM)—A chip residing on the motherboard that actually stores the encrypted keys.
or
• An external USB key to store the encrypted keys.
and
• A hard drive with two volumes, preferably created during the installation of Windows. One volume is for the operating system (most likely C:) that will be encrypted; the other is the active volume that remains unencrypted so that the computer can boot. If a second volume needs to be created, the BitLocker Drive Preparation Tool can be of assistance and can be downloaded from Windows Update.
BitLocker software is based on the Advanced Encryption Standard (AES) and uses a 128-bit key. Keep in mind that a drive encrypted with BitLocker usually suffers in performance compared to a nonencrypted drive and could have a shorter shelf life as well.
BitLocker can be accessed via the following steps:
Step 1. Navigate to Start > Accessories > Run.
Step 2. Type gpedit.msc and press Enter.
Step 3. In the Group Policy window, navigate to Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption.
Figure 2-5 shows a screen capture of the BitLocker configuration screen.
Figure 2-5. BitLocker Configuration Screen

Note
For more information about BitLocker and how to use it, see the following link: http://technet.microsoft.com/en-us/library/cc766295(WS.10).aspx.
Securing Cell Phones and PDAs
Unfortunately, cell phones and PDAs can be the victims of attack as well. Attackers might choose to abuse your service or use your cell phone as part of a larger scale attack, and possibly to gain access to your account information.
Users of cell phones and PDAs should be careful who they give their cell phone number to, and to try not to list their cell phone on any websites, especially when purchasing products. Train your users not to follow any links sent by e-mail or by text messages if these are unsolicited. Explain the issues with much of the downloadable software, such as games and ringtones, to your users. Use a locking code/password that’s hard to guess; this will lock the phone after a specific amount of time has lapsed, and use complex passwords when necessary.
Cell phones and PDA software must be updated just like computer software; keep these devices up to date, and there will be less of a chance that they will be affected by viruses and other malware. You can encrypt data in several ways, and some organizations have policies that specify how data will be encrypted. More good tips are available at the following National Cyber Alert System website links:
• www.us-cert.gov/cas/tips/ST05-017.html
• www.us-cert.gov/cas/tips/ST04-020.html
Any time a cell phone or PDA connects, it uses some type of wireless service. Whether it’s GSM, Wi-Fi, infrared, RFID or Bluetooth, security implications exist. The best solution is to turn off the particular service when not in use, or simply turn the phone/PDA off altogether. Bluetooth is especially vulnerable to virus attacks including bluejacking and bluesnarfing.
Bluejacking is the sending of unsolicited messages to Bluetooth-enabled devices such as mobile phones and PDAs. Bluejacking can be stopped by setting the affected Bluetooth device to “undiscoverable” or by turning off Bluetooth altogether.
Bluesnarfing is the unauthorized access of information from a wireless device through a Bluetooth connection. Generally, Bluesnarfing is the theft of data (calendar information, phonebook contacts, and so on). Ways of discouraging Bluesnarfing include using a pairing key that is not easy to guess; for example, stay away from 0000 or similar default Bluetooth pairing keys! Otherwise, Bluetooth devices should be set to “undiscoverable” (only after legitimate Bluetooth devices have been set up, of course), or Bluetooth can be turned off altogether.
For more information about Bluetooth vulnerabilities see the section “Securing Wireless Networks” in Chapter 7, “Securing Network Media and Devices.”
Exam Preparation Tasks: Review Key Topics
Review the most important topics in the chapter, noted with the Key Topics icon in the outer margin of the page. Table 2-3 lists a reference of these key topics and the page numbers on which each is found.
![]()
Table 2-3. Key Topics for Chapter 2

Complete Tables and Lists from Memory
Print a copy of Appendix A, “Memory Tables,” (found on the DVD), or at least the section for this chapter, and complete the tables and lists from memory. Appendix B, “Memory Tables Answer Key,” also on the DVD, includes completed tables and lists to check your work.
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
worm,
spam,
host-based intrusion detection system (HIDS),
Hands-On Labs
Complete the following written step-by-step scenarios. After you finish (or if you do not have adequate equipment to complete the scenario), watch the corresponding video solutions on the DVD.
If you have additional questions, feel free to post them at my website: www.davidlprowse.com in the Ask Dave forum. (Free registration is required to post on the website.)
Equipment Needed
• A computer with Internet access. A test computer or virtual machine is strongly recommended for these labs and not your every-day computer.
• Web browser: Internet Explorer version 6 and higher or Firefox are recommended.
• Microsoft Virtual PC 2007. Freely downloaded from the following link: www.microsoft.com/downloads/details.aspx?FamilyId=04D26402-3199-48A3-AFA2-2DC0B40A73B6&displaylang=en, or simply do a search for Microsoft Virtual PC.
Lab 2-1: Using Free Malware Scanning Programs
In this lab, you download and install free Trend Micro programs and use them to scan your computer for malware. You should use a test computer or virtual machine for this lab. The steps are as follows:
Step 1. Download Trend Micro’s HouseCall software from http://housecall.trendmicro.com/.
Step 2. When it finishes downloading, install the program.
Step 3. The program should run automatically; use it to scan your computer for malware. You can click settings to select different partitions or folders. If you find any malware, quarantine it!
Step 4. Consider downloading and utilizing other tools in the Free Tools list such as HijackThis, Rootkit Buster, and so on.
Step 5. When you finish working with the free malware scanning programs, uninstall each of them from the computer.
Watch the solution video in the Hands-On Scenarios section of the DVD.
Lab 2-2: How to Secure the BIOS
In this lab, you use the virtual BIOS in Microsoft Virtual PC to make some configuration changes, thus securing the BIOS. The steps are as follows:
Step 1. Download and install Microsoft Virtual PC 2007.
Step 2. Run the Virtual PC program; this should display the Virtual PC console.
Step 3. Create a new virtual machine:
A. In the Virtual PC Console, click the New button.
B. In the New Virtual Machine window, click Next.
C. Click the Create a virtual machine radio button and click Next.
D. Name the virtual machine Bios Test. If you want to save the virtual machine (VM) somewhere else, do so now. Then click Next.
E. Leave the Operating system drop-down menu selection as Other and click Next.
F. Leave the default settings for RAM and click Next.
G. Select the A new virtual hard disk radio button and click Next.
H. Leave the settings as the default, or select a new location for the virtual hard disk if you want; then click Next.
I. Click Finish; your VM is now created. For a more detailed lab about how to create a virtual machine in Virtual PC, see Lab 3-2 in Chapter 3, “OS Hardening and Virtualization.”
Step 4. Access the VM BIOS:
A. Make sure the VM is highlighted in the Virtual PC Console window.
B. Either double-click the new VM, or click the Start button.
C. Immediately press the Del key to access the virtual BIOS. You get only a second or two to do so. If you miss the timeout, simply restart the VM by clicking Action on the menu bar and select Reset.
D. This should display the BIOS Setup Utility window. At this point, you need to use the keyboard (especially the arrow keys) to navigate through the VM’s BIOS; the mouse will not function.
Step 5. Change the Boot device priority order:
A. Arrow over to the Boot menu.
B. Verify that Boot Device Priority is highlighted and press Enter.
C. Press the + sign until the Hard Drive option is listed first. Adjust the rest of the boot devices as you see fit.
Step 6. Disable the floppy drive:
A. Press the Esc key to return to the main menu.
B. Arrow over to the Advanced menu.
C. Arrow down to Floppy Configuration and press Enter.
D. Highlight Floppy A and press Enter.
E. Arrow up to Disabled and press Enter.
F. Press Esc; this should display the Floppy Configuration screen, and Floppy A should be set to Disabled.
Step 7. Configure a complex supervisor password:
A. Press the Esc key to return to the main menu.
B. Arrow over to the Security menu.
C. Highlight Change Supervisor Password and press Enter.
D. Type a complex password, for example ABc123 and press Enter.
E. Confirm the password by typing it again.
F. In the Supervisor Password field, it should now say Installed.
Step 8. Return the virtual BIOS settings to normal. To return the BIOS password, you need to type the old password, and then simply press Enter to configure a blank password. If you choose to secure the virtual BIOS in the future, you need to save the virtual machine settings by selecting Action > Close > Save State (in the drop-down menu).
Watch the solution video in the “Hands-On Scenarios” section of the DVD.
View Recommended Resources
For readers who want to brush up on their CompTIA A+ topics:
• Prowse, David L. CompTIA A+ Exam Cram, Fourth Edition. Que. 2010.
Links to antimalware companies:
• McAfee Total Protection: www.mcafee.com
• Norton Internet Security 2010: http://antivirus.norton.com
• Vipre Antivirus: www.vipreantivirus.com/
Windows Defender:
www.microsoft.com/windows/products/winfamily/defender/default.mspx.
Barracuda Networks:
Microsoft Sysinternals Rootkit Revealer:
http://technet.microsoft.com/en-us/sysinternals/bb897445.aspx (for Windows systems)
chkrootkit:
www.chkrootkit.org/ (for UNIX-based systems)
Windows BitLocker Drive Encryption Step-by-Step Guide:
http://technet.microsoft.com/en-us/library/cc766295(WS.10).aspx
National Cyber Alert System links:
www.us-cert.gov/cas/tips/ST05-017.html
www.us-cert.gov/cas/tips/ST04-020.html
Answer Review Questions
Answer the following review questions. You can find the answers at the end of this chapter.
1. A group of compromised computers that have software installed by a worm is known as which of the following?
A. Botnet
B. Virus
C. Honeypot
D. Zombie
2. What are some of the drawbacks to using HIDS instead of NIDS on a server?
A. A HIDS may use a lot of resources that can slow server performance.
B. A HIDS cannot detect operating system attacks.
C. A HIDS has a low level of detection of operating system attacks.
D. A HIDS cannot detect network attacks.
3. Which of the following computer security threats can be updated automatically and remotely? (Select the best answer.)
A. Virus
B. Worm
C. Zombie
D. Malware
4. Which of the following is the best mode to use when scanning for viruses?
A. Safe Mode
B. Last Known Good Configuration
C. Command Prompt only
D. Boot into Windows normally
5. Which of the following is a common symptom of spyware?
A. Infected files
B. Computer shuts down
C. Applications freeze
D. Pop-up windows
6. What are two ways to secure the computer within the BIOS? (Select the two best answers.)
A. Configure a supervisor password.
B. Turn on BIOS shadowing.
C. Flash the BIOS.
D. Set the hard drive first in the boot order.
7. Dan is a network administrator. One day he notices that his DHCP server is flooded with information. He analyzes it and finds that the information is coming from more than 50 computers on the network. Which of the following is the most likely reason?
A. Virus
B. Worm
C. Zombie
D. PHP script
8. Which of the following is not an example of malicious software?
A. Rootkits
B. Spyware
C. Viruses
D. Browser
9. Which type of attack uses more than one computer?
A. Virus
B. DoS
C. Worm
D. DDoS
10. What are the two ways that you can stop employees from using USB flash drives? (Select the two best answers.)
A. Utilize RBAC.
B. Disable USB devices in the BIOS.
C. Disable the USB root hub.
D. Enable MAC filtering.
11. Which of the following does not need updating?
A. HIDS
B. Antivirus software
D. Antispyware
12. Which of the following are Bluetooth threats? (Select the two best answers.)
A. Bluesnarfing
B. Blue bearding
C. Bluejacking
D. Distributed denial of service
13. What is a malicious attack that executes at the same time every week?
A. Virus
B. Worm
C. Bluejacking
D. Logic bomb
14. Which of these is true for active inception?
A. When a computer is put between a sender and receiver
B. When a person overhears a conversation
C. When a person looks through files
D. When a person hardens an operating system
15. Tim believes that his computer has a worm. What is the best tool to use to remove that worm?
A. Antivirus software
B. Antispyware software
C. HIDS
D. NIDS
16. Which of the following types of scanners can locate a rootkit on a computer?
A. Image scanner
B. Barcode scanner
C. Malware scanner
D. Adware scanner
17. Which type of malware does not require a user to execute a program to distribute the software?
A. Worm
B. Virus
D. Stealth
18. Which of these is not considered to be an inline device?
A. Firewall
B. Router
C. CSU/DSU
D. HIDS
19. Whitelisting, blacklisting, and closing open relays are all mitigation techniques addressing what kind of threat?
A. Spyware
B. Spam
C. Viruses
D. Botnets
20. How do most network-based viruses spread?
A. By CD and DVD
B. Through e-mail
C. By USB flash drive
D. By floppy disk
21. Which of the following defines the difference between a Trojan horse and a worm? (Select the best answer.)
A. Worms self-replicate but Trojan horses do not.
B. The two are the same.
C. Worms are sent via e-mail; Trojan horses or not.
D. Trojan horses are malicious attacks; worms are not.
22. Which of the following types of viruses hides its code to mask itself?
A. Stealth virus
B. Polymorphic virus
C. Worm
D. Armored virus
23. Which of the following types of malware appears to the user as legitimate but actually enables unauthorized access to the user’s computer?
A. Worm
B. Virus
D. Spam
24. Which of the following would be considered detrimental effects of a virus hoax? (Select the two best answers.)
A. Technical support resources are consumed by increased user calls.
B. Users are at risk for identity theft.
C. Users are tricked into changing the system configuration.
D. The e-mail server capacity is consumed by message traffic.
25. To mitigate risks when users accesses company e-mail with their cell phone, what security policy should be implemented on the cell phone?
A. Data connection capabilities should be disabled.
B. A password should be set on the phone.
C. Cell phone data should be encrypted.
D. Cell phone should be only for company use.
26. Your manager wants you to implement a type of intrusion detection system (IDS) that can be matched to certain types of traffic patterns. What kind of IDS is this?
A. Anomaly based IDS
B. Signature-based IDS
C. Behavior-based IDS
D. Heuristic-based IDS
Answers and Explanations
1. A. A botnet is a group of compromised computers, usually working together, with malware that was installed by a worm or a Trojan horse.
2. A and D. Host-based intrusion detection systems (HIDS) run within the operating system of a computer. Because of this, they can slow a computer’s performance. Most HIDS do not detect network attacks well (if at all). However, a HIDS can detect operating system attack, and will usually have a high-level of detection for those attacks.
3. C. Zombies (also known as zombie computers) are systems that have been compromised without the knowledge of the owner. A prerequisite is the computer must be connected to the Internet so that the hacker or malicious attack can make its way to the computer and be controlled remotely. Multiple zombies working in concert often form a botnet. See the section “Computer Systems Security Threats” in Chapter 2, “Computer Systems Security,” for more information.
4. A. Safe Mode should be used (if your AV software supports it) when scanning for viruses.
5. D. Pop-up windows are common to spyware. The rest of the answers are more common symptoms of viruses.
6. A and D. Configuring a supervisor password in the BIOS disallows any other user to enter the BIOS and make changes. Setting the hard drive first in the BIOS boot order disables any other devices from being booted off, including floppy drives, optical drives, and USB flash drives. BIOS shadowing doesn’t have anything to do with computer security, and although flashing the BIOS may include some security updates, it’s not the best answer.
7. B. A worm is most likely the reason that the server is being bombarded with information by the clients; perhaps it is perpetuated by a botnet. Because worms self-replicate, the damage can quickly become critical.
8. D. A web browser (for example, Internet Explorer) is the only one listed that is not an example of malicious software. Although a browser can be compromised in a variety of ways by malicious software, the application itself is not the malware.
9. D. A DDoS, or distributed denial of service, attack uses multiple computers to make its attack, usually perpetuated on a server. None of the other answers use multiple computers.
10. B and C. By disabling all USB devices in the BIOS, a user cannot use their flash drive. Also, the user cannot use the device if you disable the USB root hub within the operating system.
11. C. Pop-up blockers do not require updating to be accurate. However, host-based intrusion detection systems, antivirus software, and antispyware all need to be updated to be accurate.
12. A and C. Bluesnarfing and bluejacking are the names of a couple Bluetooth threats. Another attack could be aimed at a Bluetooth device’s discovery mode. To date there is no such thing as blue bearding, and a distributed denial of service attack uses multiple computers attacking one host.
13. D. A logic bomb is a malicious attack that executes at a specific time. Viruses normally execute when a user inadvertently runs them. Worms can self-replicate at will. And bluejacking deals with Bluetooth devices.
14. A. Active inception (aka active interception) normally includes a computer placed between the sender and the receiver to capture information.
15. A. Antivirus software is the best option when removing a worm. It may be necessary to boot into safe mode to remove this worm when using antivirus software.
16. C. Malware scanners can locate rootkits and other types of malware. These types of scanners are often found in antimalware software from manufacturers such as McAfee, Norton, Viper, and so on. Adware scanners (quite often free) can scan for only adware. Always have some kind of antimalware software running on live client computers!
17. A. Worms self-replicate and do not require a user to execute a program to distribute the software across networks. All the other answers do require user intervention. Stealth refers to a type of virus.
18. D. HIDS or host-based intrusion detection systems are not considered to be an inline device. This is because they run on an individual computer. Firewalls, routers, and CSU/DSUs are inline devices.
19. B. Closing open relays, whitelisting, and blacklisting bar all mitigation techniques that address spam. Spam e-mail is a serious problem for all companies and must be filtered as much is possible.
20. B. E-mail is the number one reason why network-based viruses spread. All a person needs to do is double-click the attachment within the e-mail, and the virus will do its thing, which is most likely to spread through the user’s address book. Removable media such as CDs, DVDs, USB flash drives, and floppy disks can spread viruses but are not nearly as common as e-mail.
21. A. The primary difference between a Trojan horse and a worm is that worms will self-replicate without any user intervention; Trojan horses do not self-replicate.
22. D. An armored virus attempts to make disassembly difficult for an antivirus software program. It thwarts attempts at code examination. Stealth viruses attempt to avoid detection by antivirus software altogether. Polymorphic viruses change every time they run. Worms are not viruses.
23. C. A Trojan, or a Trojan horse, will appear to be legitimate and will look like it’ll perform desirable functions, but in reality it is designed to enable unauthorized access to the user’s computer.
24. A and C. Because a virus can affect many users, technical support resources can be consumed by an increase in user phone calls and e-mails. This can be detrimental to the company because all companies have a limited amount of technical support personnel. Another detrimental effect is that unwitting users may be tricked into changing some of their computer system configurations. The key term in the question is “virus hoax.” If the e-mail server is consumed by message traffic, that would be a detrimental effect caused by the person who sent the virus and by the virus itself but not necessarily by the hoax. Although users may be at risk for identity theft, it is not one of the most detrimental effects of the virus hoax.
25. B. A password should be set on the phone, and the phone should lock after a set period of time. When the user wants to use the phone again, the user should be prompted for a password. Disabling the data connection altogether would make access to e-mail impossible on the cell phone. Cell phone encryption of data is possible, but it could use a lot of processing power that may make it unfeasible. Whether the cell phone is used only for company use is up to the policies of the company.
26. B. When using an IDS, particular types of traffic patterns refers to signature-based IDS.
