Chapter 2
Domain 2.0: Software and Systems Security
EXAM OBJECTIVES COVERED IN THIS CHAPTER:
- 2.1 Given a scenario, apply security solutions for infrastructure management.
- Cloud vs. on-premises
- Asset management
- Segmentation
- Network architecture
- Change management
- Virtualization
- Containerization
- Identity and access management
- Cloud access security broker (CASB)
- Honeypot
- Monitoring and logging
- Encryption
- Certificate management
- Active defense
- 2.2 Explain software assurance best practices.
- Platforms
- Software development lifecycle (SDLC) integration
- DevSecOps
- Software assessment methods
- Secure coding best practices
- Static analysis tools
- Dynamic analysis tools
- Formal methods for verification of critical software
- Service-oriented architecture
- 2.3 Explain hardware assurance best practices.
- Hardware root of trust
- eFuse
- Unified Extensible Firmware Interface (UEFI)
- Trusted Foundry
- Secure processing
- Anti-tamper
- Self-encrypting drive
- Trusted firmware updates
- Measured boot and attestation
- Bus encryption
- What purpose does a honeypot system serve when placed on a network as shown in the following diagram?

- It prevents attackers from targeting production servers.
- It provides information about the techniques attackers are using.
- It slows down attackers like sticky honey.
- It provides real-time input to IDSs and IPSs.
- A tarpit, or a system that looks vulnerable but actually is intended to slow down attackers, is an example of what type of technique?
- A passive defense
- A sticky defense
- An active defense
- A reaction-based defense
- As part of a government acquisitions program for the U.S. Department of Defense, Sean is required to ensure that the chips and other hardware level components used in the switches, routers, and servers that he purchases do not include malware or other potential attack vectors. What type of supplier should Sean seek out?
- A TPM
- An OEM provider
- A trusted foundry
- A gray-market provider
- Susan needs to test thousands of submitted binaries. She needs to ensure that the applications do not contain malicious code. What technique is best suited to this need?
- Sandboxing
- Implementing a honeypot
- Decompiling and analyzing the application code
- Fagan testing
- Manesh downloads a new security tool and checks its MD5. What does she know about the software she downloaded if she receives the following message:
root@demo:~# md5sum -c demo.md5demo.txt: FAILEDmd5sum: WARNING: 1 computed checksum did NOT match- The file has been corrupted.
- Attackers have modified the file.
- The files do not match.
- The test failed and provided no answer.
- Tracy is designing a cloud infrastructure for her company and wants to generate and store encryption keys in a secure way. What type of technology should she look for as part of her infrastructure as a service vendor's portfolio?
- TPM
- HSM
- UEFI
- VPC
- Aziz needs to provide SSH access to systems behind his datacenter firewall. If Aziz's organization uses the system architecture shown here, what is the system at point A called?

- A firewall-hopper
- An isolated system
- A moat-protected host
- A jump box
- Charles wants to provide additional security for his web application, which currently stores passwords in plaintext in a database. Which of the following options will best prevent theft of the database resulting in exposed passwords?
- Encrypt the database of plaintext passwords
- Use MD5 and a salt
- Use SHA-1 and a salt
- Use
bcrypt
- What type of protected boot process is illustrated in the following diagram?

- Measured boot
- TPM
- Remote attestation
- Signed BIOS
- An access control system that relies on the operating system to constrain the ability of a subject to perform operations is an example of what type of access control system?
- A discretionary access control system
- A role-based access control system
- A mandatory access control system
- A level-based access control system
- During his analysis of a malware sample, Sahib reviews the malware files and binaries without running them. What type of analysis is this?
- Automated analysis
- Dynamic analysis
- Static analysis
- Heuristic analysis
- Carol wants to analyze a malware sample that she has discovered. She wants to run the sample safely while capturing information about its behavior and impact on the system it infects. What type of tool should she use?
- A static code analysis tool
- A dynamic analysis sandbox tool
- A Fagan sandbox
- A decompiler running on an isolated VM
Use the following scenario for questions 13–15.
Mike is in charge of the software testing process for his company. They perform a complete set of tests for each product throughout its lifespan. Use your knowledge of software assessment methods to answer the following questions.
- A new web application has been written by the development team in Mike's company. They used an Agile process and have built a tool that fits all of the user stories that the participants from the division that asked for the application outlined. If they want to ensure that the functionality is appropriate for all users in the division, what type of testing should Mike perform?
- Stress testing
- Regression testing
- Static testing
- User acceptance testing
- Mike's development team wants to expand the use of the software to the whole company, but they are concerned about its performance. What type of testing should they conduct to ensure that the software will not fail under load?
- Stress testing
- Regression testing
- Static testing
- User acceptance testing
- Two years after deployment, Mike's team is ready to roll out a major upgrade to their web application. They have pulled code from the repository that it was checked into but are worried that old bugs may have been reintroduced because they restored additional functionality based on older code that had been removed in a release a year ago. What type of testing does Mike's team need to perform?
- Stress testing
- Regression testing
- Static testing
- User acceptance testing
- Susan is reviewing files on a Windows workstation and believes that
cmd.exehas been replaced with a malware package. Which of the following is the best way to validate her theory?- Submit
cmd.exeto VirusTotal. - Compare the hash of
cmd.exeto a known good version. - Check the file using the National Software Reference Library.
- Run
cmd.exeto make sure its behavior is normal.
- Submit
- As part of her malware analysis process, Caitlyn diagrams the high-level functions and processes that the malware uses to accomplish its goals. What is this process known as?
- Static analysis
- Composition
- Dynamic analysis
- Decomposition
- As a U.S. government employee, Michael is required to ensure that the network devices that he procures have a verified chain of custody for every chip and component that goes into them. What is this program known as?
- Gray-market procurement
- Trusted foundry
- White-market procurement
- Chain of procurement
- Padma is evaluating the security of an application developed within her organization. She would like to assess the application's security by supplying it with invalid inputs. What technique is Padma planning to use?
- Fault injection
- Stress testing
- Mutation testing
- Fuzz testing
- Nishi is deploying a new application that will process sensitive health information about her organization's clients. In order to protect this information, the organization is building a new network that does not share any hardware or logical access credentials with the organization's existing network. What approach is Nishi adopting?
- Network interconnection
- Network segmentation
- Virtual LAN (VLAN) isolation
- Virtual private network (VPN)
- Bobbi is deploying a single system that will be used to manage a very sensitive industrial control process. This system will operate in a standalone fashion and not have any connection to other networks. What strategy is Bobbi deploying to protect this SCADA system?
- Network segmentation
- VLAN isolation
- Airgapping
- Logical isolation
- Which software development life cycle model is illustrated in the image?

- Waterfall
- Spiral
- Agile
- RAD
- Geoff has been asked to identify a technical solution that will reduce the risk of captured or stolen passwords being used to allow access to his organization's systems. Which of the following technologies should he recommend?
- Captive portals
- Multifactor authentication
- VPNs
- OAuth
- The company that Amanda works for is making significant investments in infrastructure as a service hosting to replace their traditional datacenter. Members of her organization's management have expressed concerns about data remanence when Amanda's team moves from one virtual host to another in their cloud service provider's environment. What should she instruct her team to do to avoid this concern?
- Zero-wipe drives before moving systems.
- Use full-disk encryption.
- Use data masking.
- Span multiple virtual disks to fragment data.
- Huan is hiring a third-party consultant who will have remote access to the organization's datacenter, but he would like to approve that access each time it occurs. Which one of the following solutions would meet Huan's needs in a practical manner?
- Huan should keep the consultant's password himself and provide it to the consultant when needed, and then immediately change the password after each use.
- Huan should provide the consultant with the password but configure his own device to approve logins via multifactor authentication.
- Huan should provide the consultant with the password but advise the consultant that she must advise him before using the account and then audit those attempts against access logs.
- Huan should create a new account for the consultant each time she needs to access the datacenter.
- Ian is reviewing the security architecture shown here. This architecture is designed to connect his local datacenter with an IaaS service provider that his company is using to provide overflow services. What component can be used at the points marked by the question marks (?s) to provide a secure encrypted network connection?

- Firewall
- VPN
- IPS
- DLP
- Which one of the following technologies is not typically used to implement network segmentation?
- Host firewall
- Network firewall
- VLAN tagging
- Routers and switches
- Which one of the following approaches is an example of a formal code review process?
- Pair programming
- Over-the-shoulder
- Fagan inspection
- Pass-around code review
- The Open Web Application Security Project (OWASP) maintains an application called Orizon. This application reviews Java classes and identifies potential security flaws. What type of tool is Orizon?
- Fuzzer
- Static code analyzer
- Web application assessor
- Fault injector
- Barney's organization mandates fuzz testing for all applications before deploying them into production. Which one of the following issues is this testing methodology most likely to detect?
- Incorrect firewall rules
- Unvalidated input
- Missing operating system patches
- Unencrypted data transmission
- Kobe wants to provide access to a jump box in a secured network. What technology should he deploy to allow a secure connection to the system through untrusted intermediary networks?
- VPC
- An air gap
- A VPN
- Physical segmentation
- Mia would like to ensure that her organization's cybersecurity team reviews the architecture of a new ERP application that is under development. During which SDLC phase should Mia expect the security architecture to be completed?
- Analysis and Requirements Definition
- Design
- Development
- Testing and Integration
- Which one of the following security activities is not normally a component of the Operations and Maintenance phase of the SDLC?
- Vulnerability scans
- Disposition
- Patching
- Regression testing
- Which hardware device is used on endpoint devices to store RSA encryption keys specific to that device to allow hardware authentication?
- A SSD
- A hard drive
- A MFA token
- A TPM
- Which one of the following testing techniques is typically the final testing done before code is released to production?
- Unit testing
- Integration testing
- User acceptance testing
- Security testing
Use the following scenario for questions 36–38.
Olivia has been put in charge of performing code reviews for her organization and needs to determine which code analysis models make the most sense based on specific needs her organization has. Use your knowledge of code analysis techniques to answer the following questions.
- Olivia's security team has identified potential malicious code that has been uploaded to a webserver. If she wants to review the code without running it, what technique should she use?
- Dynamic analysis
- Fagan analysis
- Regression analysis
- Static analysis
- Olivia's next task is to test the code for a new mobile application. She needs to test it by executing the code and intends to provide the application with input based on testing scenarios created by the development team as part of their design work. What type of testing will Olivia conduct?
- Dynamic analysis
- Fagan analysis
- Regression analysis
- Static analysis
- After completing the first round of tests for her organization's mobile application, Olivia has discovered indications that the application may not handle unexpected data well. What type of testing should she conduct if she wants to test it using an automated tool that will check for this issue?
- Fault injection
- Fagan testing
- Fuzzing
- Failure injection
- Which one of the following characters would not signal a potential security issue during the validation of user input to a web application?
<`>$
- The Open Web Application Security Project (OWASP) maintains a listing of the most important web application security controls. Which one of these items is least likely to appear on that list?
- Implement identity and authentication controls
- Implement appropriate access controls
- Obscure web interface locations
- Leverage security frameworks and libraries
- Kyle is developing a web application that uses a database backend. He is concerned about the possibility of an SQL injection attack against his application and is consulting the OWASP proactive security controls list to identify appropriate controls. Which one of the following OWASP controls is least likely to prevent a SQL injection attack?
- Parameterize queries
- Validate all input
- Encode data
- Implement logging and intrusion detection
- Jill's organization has adopted an asset management tool. If she wants to identify systems on the network based on a unique identifier per machine that will not normally change over time, which of the following options can she use for network-based discovery?
- IP address
- Hostname
- MAC address
- None of the above
- Barcodes and RFID tags are both frequently used for what asset management practice?
- Asset disposition
- Asset tagging
- Asset acquisition
- Asset lifespan estimation
- What type of secure boot process is shown in the following image?

- Remote attestation
- Measured boot
- Logged loader
- UEFI
- Ian has been asked to deploy a secure wireless network in parallel with a public wireless network inside his organization's buildings. What type of segmentation should he implement to do so without adding additional costs and complexity?
- SSID segmentation
- Logical segmentation
- Physical segmentation
- WPA segmentation
- Barbara has segmented her virtualized servers using VMware to ensure that the networks remain secure and isolated. What type of attack could defeat her security design?
- VLAN hopping
- 802.1q trunking vulnerabilities
- Compromise of the underlying VMware host
- BGP route spoofing
- What major issue would Charles face if he relied on hashing malware packages to identify malware packages?
- Hashing can be spoofed.
- Collisions can result in false positives.
- Hashing cannot identify unknown malware.
- Hashing relies on unencrypted malware samples.
- Noriko wants to ensure that attackers cannot access his organization's building automation control network. Which of the following segmentation options provides the strongest level of assurance that this will not happen?
- Air gap
- VLANs
- Network firewalls
- Host firewalls
- What type of network device is most commonly used to connect two or more networks to forward traffic between them?
- A switch
- A firewall
- A router
- An IPS
Use the following scenario for questions 50–53.
Angela is a security practitioner at a mid-sized company that recently experienced a serious breach due to a successful phishing attack. The company has committed to changing their security practices across the organization and has assigned Angela to determine the best strategy to make major changes that will have a significant impact right away.
- Angela's company has relied on passwords as their authentication factor for years. The current organizational standard is to require an eight-character, complex password, and to require a password change every 12 months. What recommendation should Angela make to significantly decrease the likelihood of a similar phishing attack and breach in the future?
- Increase the password length.
- Shorten the password lifespan.
- Deploy multifactor authentication.
- Add a PIN to all logins.
- Angela has decided to roll out a multifactor authentication system. What are the two most common factors used in MFA systems?
- Location and knowledge
- Knowledge and possession
- Knowledge and biometric
- Knowledge and location
- As part of the investigation after the breach, Angela's team noticed that some staff were using organizational resources after hours when they weren't supposed to be logged in. What type of authentication model could she deploy to use information about an employee's role and work hours to manage when they can be logged in?
- Location factors
- Biometric factors
- Context based authentication
- Multifactor authentication
- Angela's multifactor deployment includes the ability to use text (SMS) messages to send the second factor for authentication. What issues should she point to?
- VoIP hacks and SIM swapping
- SMS messages are logged on the recipient's phones
- PIN hacks and SIM swapping
- VoIP hacks and PIN hacks
- Keith needs to manage digital keys, and he wants to implement a hardware security module in his organization. What U.S. government standard are hardware security modules often certified against?
- PCI-DSS
- HSM-2015
- FIPS 140-2
- CA-Check
- What purpose does the OpenFlow protocol serve in software-defined networks?
- It captures flow logs from devices.
- It allows software-defined network controllers to push changes to devices to manage the network.
- It sends flow logs to flow controllers.
- It allows devices to push changes to SDN controllers to manage the network.
- What type of access control system relies on the operating system to control the ability of subjects to perform actions on objects through a set of policies controlled by a policy administrator?
- RBAC
- MAC
- DAC
- ABAC
- What term is used to describe an isolated pool of cloud resources for a specific organization or user allocated inside of a public cloud environment?
- VPN
- VPC
- CDA
- CCA
- Rick's security research company wants to gather data about current attacks and sets up a number of intentionally vulnerable systems that allow his team to log and analyze exploits and attack tools. What type of environment has Rick set up?
- A tarpit
- A honeypot
- A honeynet
- A blackhole
- Kalea wants to prevent DoS attacks against her serverless application from driving up her costs when using a cloud service. What technique is not an appropriate solution for her need?
- Horizontal scaling
- API keys
- Setting a cap on API invocations for a given timeframe
- Using timeouts
- What is the purpose of change management in an organization?
- Ensuring changes are scheduled
- Ensuring changes are documented
- Ensuring that only approved changes are made
- All of the above
- What is the key difference between virtualization and containerization?
- Virtualization gives operating systems direct access to the hardware, whereas containerization does not allow applications to directly access the hardware.
- Virtualization lets you run multiple operating systems on a single physical system, whereas containerization lets you run multiple applications on the same system.
- Virtualization is necessary for containerization, but containerization is not necessary for virtualization.
- There is not a key difference; they are elements of the same technology.
- Which software development methodology is illustrated in the diagram?

- Spiral
- RAD
- Agile
- Waterfall
- What advantage does a virtual desktop infrastructure have when addressing data theft?
- No data is stored locally on the endpoint device
- Built-in DLP
- All data is encrypted at rest
- All data is stored locally on the endpoint device
- Brandon is designing the hosting environment for containerized applications. Application group A has personally identifiable information, Application group B has health information with different legal requirements for handling, and Application group C has business sensitive data handling requirements. What is the most secure design for his container orchestration environment given the information he has?
- Run a single, highly secured container host with encryption for data at rest.
- Run a container host for each application group and secure them based on the data they contain.
- Run a container host for groups A and B, and a lower-security container host for group C.
- Run a container host for groups A and C, and a health information–specific container host for group B due to the health information it contains.
- Local and domain administrator accounts, root accounts, and service accounts are all examples of what type of account?
- Monitored accounts
- Privileged accounts
- Root accounts
- Unprivileged accounts
- Ned has discovered a key logger plugged into one of his workstations, and he believes that an attacker may have acquired usernames and passwords for all of the users of a shared workstation. Since he does not know how long the keylogger was in use or if it was used on multiple workstations, what is his best security option to prevent this and similar attacks from causing issues in the future?
- Multifactor authentication
- Password complexity rules
- Password lifespan rules
- Prevent the use of USB devices
- Facebook Connect, CAS, Shibboleth, and ADFS are all examples of what type of technology?
- Kerberos implementations
- Single sign-on implementations
- Federation technologies
- OAuth providers
- Which of the following is not a common identity protocol for federation?
- SAML
- OpenID
- OAuth
- Kerberos
- Mei is designing her organization's datacenter network and wants to establish a secure zone and a DMZ. If Mei wants to ensure that user accounts and traffic that manage systems in the DMZ are easily auditable, and that all access can be logged while helping prevent negative impacts from compromised or infected workstations, which of the following solutions is Mei's best design option?
- Administrative virtual machines run on administrator workstations
- A jump host
- A bastion host
- SSH or RDP from administrative workstations
- The identity management system used by Greg's new employer provides rights based on his job as a system administrator. What type of access control system is this?
- RBAC
- MAC
- DAC
- ABAC
- During a periodic audit of account privileges, Rhonda reviews the account rights in an Active Directory domain for every administrative user and removes any rights to directories or systems that should no longer be available to the administrative users. What type of review is this?
- Manual review
- IAM assessment
- Mandatory audit review
- Discretional audit review
- Naomi wants to enforce her organization's security policies on cloud service users. What technology is best suited to this?
- OAuth
- CASB
- OpenID
- DMARC
- Lucca wants to ensure that his Windows logs capture events for one month. What setting should he change in the settings to ensure this?

- Increase the size of the log file to 40480.
- Leave the log file as is.
- Change the setting to archive the log when full.
- Clear the log to start clean.
- Elliott wants to encrypt data sent between his servers. What protocol is most commonly used for secure web communications over a network?
- TLS
- SSL
- IPSec
- PPTP
- What occurs when a website's certificate expires?
- Web browsers will report an expired certificate to users.
- The website will no longer be accessible.
- The certificate will be revoked.
- All of the above.
- What term is used to describe defenses that obfuscate the attack surface of an organization by deploying decoys and attractive targets to slow down or distract an attacker?
- An active defense
- A honeyjar
- A bear trap
- An interactive defense
- The OWASP mobile application security checklist's cryptography requirements include a requirement that the application uses “proven implementations of cryptographic primitives.” What does this requirement mean, and why is it in the checklist?
- Only use basic cryptographic techniques to ensure that developers can understand them
- Only use proven versions of cryptographic algorithms so that they will be secure
- Only use in-house developed and tested cryptographic algorithms to avoid known vulnerabilities
- Only use open source cryptographic techniques to ensure that their source code can be reviewed
- Claire knows that a web application that her organization needs to have in production has vulnerabilities due to a recent scan using a web application security scanner. What is her best protection option if she knows that the vulnerability is a known SQL injection flaw?
- A firewall
- An IDS
- A WAF
- DLP
Use the following scenario to answer questions 79–81.
Donna has been assigned as the security lead for a DevSecOps team building a new web application. As part of the effort, she has to oversee the security practices that the team will use to protect the application. Use your knowledge of secure coding practices to help Donna guide her team through this process.
- A member of Donna's team recommends building a blacklist to avoid dangerous characters like
‘and<script>tags. How could attackers bypass a blacklist that individually identified those characters?- They can use a binary attack.
- They can use alternate encodings.
- They can use different characters with the same meaning.
- The characters could be used together to avoid the blacklist.
- The design of the application calls for client-side validation of input. What type of tool could an attacker use to bypass this?
- An XSS injector
- A web proxy
- A JSON interpreter
- A SQL injector
- A member of Donna's security team suggests that output encoding should also be considered. What type of attack is the team member most likely attempting to prevent?
- Cross-site scripting
- SQL injection
- Cross-site request forgery
- All of the above
- What type of access control system uses information like age, title, organization ID, or security clearance to grant privileges?
- RBAC
- MAC
- DAC
- ABAC
- Alex has deployed a new model of network connected Internet of Things (IoT) devices throughout his organization's facilities to track environmental data. The devices use a system on a chip (SOC) and Alex is concerned about potential attacks. What is the most likely exploit channel for SOCs in this environment?
- Physical attacks
- Attacks via an untrusted foundry
- Attacks against the operating system and software
- Side channel attacks
- Nathan downloads a BIOS update from Dell's website, and when he attempts to install it on the PC, he receives an error that the hash of the BIOS does not match the hash stored on Dell's servers. What type of protection is this?
- Full-disk encryption
- Firmware protection
- Operating system protection
- None of the above
- What practice is typical in a DevSecOps organization as part of a CI/CD pipeline?
- Automating some security gates
- Programmatic implementation of zero-day vulnerabilities
- Using security practitioners to control the flow of the CI/CD pipeline
- Removing security features from the IDE
- Naomi wants to validate files that are uploaded as part of her web application. Which of the following is not a common technique to help prevent malicious file uploads or denial of service attacks?
- Using input validation to ensure only allowed file extensions
- Uploading all files to a third-party virus scanning platform like VirusTotal
- Checking the size of uploaded files against a maximum allowed file size
- Checking zip files for their structure and path before unzipping them
- Valerie wants to prevent potential cross-site scripting attacks from being executed when previously entered information is displayed in user's browsers. What technique should she use to prevent this?
- A firewall
- A HIDS
- Output encoding
- String randomization
- While developing a web application, Chris sets his session ID length to 128 bits based on OWASP's recommended session management standards. What reason would he have for needing such a long session ID?
- To avoid duplication
- To allow for a large group of users
- To prevent brute-forcing
- All of the above
- Robert is reviewing a web application and the developers have offered four different responses to incorrect logins. Which of the following four responses is the most secure option?
- Login failed for user; invalid password
- Login failed; invalid user ID or password
- Login failed; invalid user ID
- Login failed; account does not exist
- What technology is most commonly used to protect data in transit for modern web applications?
- VPN
- TLS
- SSL
- IPSec
- Nathan is reviewing PHP code for his organization and finds the following code in the application he is assessing. What technique is the developer using?
$stmt = $dbh->prepare("INSERT INTO REGISTRY (var1, var2) VALUES (:var1, :var2)");$stmt->bindParam(':var1', $var1);$stmt->bindParam(':var2', $var2);- Dynamic binding
- Parameterized queries
- Variable limitation
- None of the above
- Which of the following components is not typically part of a service-oriented architecture?
- Service provider
- Service guardian
- Service broker
- Service consumer
- Which role in a SAML authentication flow validates the identity of the user?
- The SP
- The IDP
- The principal
- The RP
- Anja is assessing the security of a SOAP-based web service implementation. Which of the following web service security requirements should she recommend to reduce the likelihood of a successful man-in-the-middle attack?
- Use TLS.
- Use XML input validation.
- Use XML output validation.
- Virus-scan files received by web service.
- Which of the following components are not part of a typical SOAP message?
- The envelope
- The header
- The stamp
- The body
- Alice wants to ensure proper access control for a public REST service. What option is best suited to help ensure that the service will not suffer from excessive use?
- Restricting HTTP methods
- Using JSON web tokens
- Using API keys
- Using HTTPS
- How are requests in REST-based web services typically structured?
- As XML
- As a URL
- As a SQL query
- As a SOAP statement
- While reviewing the code for a Docker-based microservice, Erik discovers the following code:
echo "pidfile = /run/example.pid">> /etc/example.conf &&echo "logfile = /data/logs/example.log">> /etc/example.conf &&echo "loglevel = debug">> /etc/example.conf &&echo "port = : 5159">> /etc/example.conf &&echo "username = svc">> /etc/example.conf &&echo "password = secure">> /etc/example.conf &&What has he found?
- A misconfigured microservice
- Hard-coded credentials
- Improperly configured log files
- A prohibited port
- What type of access is typically required to compromise a physically isolated and air-gapped system?
- Wired network access
- Physical access
- Wireless network access
- None of the above, because an isolated, air-gapped system cannot be accessed
- The organization that Allan works for wants to securely store digital keys for their enterprise security certificates. What type of device should they select to help manage and protect their keys?
- A hardware token
- A HSM
- A PEBKAC
- A cigar box CA
- Charlene wants to provide an encrypted network connection for her users. She knows her users require a full network connection rather than application specific uses. What VPN technology should she choose?
- SSL
- TLS
- IPSec
- WPA2
- How are eFuses used to prevent firmware downgrades?
- If they are burned, the firmware cannot be changed.
- The number of fuses burned indicates the current firmware level, preventing old versions from being installed.
- eFuses must be reset before firmware can be downgraded, requiring administrative access.
- eFuses cannot be used to prevent firmware downgrades.
- Dev wants to use Secure Boot on a workstation. What technology must his workstation use to support Secure Boot?
- BIOS
- ROM
- UEFI
- TPM
- What requirements must be met for a trusted execution environment to exist?
- All trusted execution environment assets must have been installed and started securely.
- The trusted execution environment must be verified and certified by a third party.
- The trusted execution environment must be verified and approved by the end user.
- Only trusted components built into the operating system can be run in a trusted execution environment.
- What hardware feature do Apple devices use to manage keys in a secure way outside of the processor?
- A cryptographic bastion
- A Secure Enclave
- A HSM
- A cryptolocker
- Which of the following is not a typical capability of processor security extensions?
- Data and instruction path integrity checks
- Error detection for memory and registers
- Stack bounds checking
- Secure register wiping capabilities
- What concept describes a security process that ensures that another process or device cannot perform read or write operations on memory while an operation is occurring?
- Nonblocking memory
- Memory coherence
- Atomic execution
- Trusted execution
Use the following scenario to answer questions 108–111.
Tom connects to a website using the Chrome web browser. The site uses TLS encryption and presents the digital certificate shown here.

- Who created the digital signature shown in the last line of this digital certificate?
- Starfield Services
- Amazon
- nd.edu
- RSA
- Which one of the following websites would not be covered by this certificate?
nd.eduwww.nd.eduwww.business.nd.edu- All of these sites would be covered by the certificate.
- What encryption key does the certificate contain?
- The website's public key
- The website's private key
- Tom's public key
- Tom's private key
- After Tom initiates a connection to the website, what key is used to encrypt future communications from the web server to Tom?
- The website's public key
- The website's private key
- Tom's public key
- The session key
- Holographic stickers are a common tool used for what type of security practice?
- Anti-tamper
- Anti-theft
- Asset management
- Asset tracking
- Olivia has been tasked with identifying a solution that will prevent the exposure of data on a drive if the drive itself is stolen. What type of technology should she recommend?
- MFA
- SED
- P2PE
- eSATA
- Amanda's organization wants to ensure that user awareness, documentation, and other tasks are accomplished and tracked as new infrastructure is added and modified. What type of tool should they acquire?
- A project management tool
- An IDE
- A change management tool
- A ticketing tool
- Christina wants to check the firmware she has been provided to ensure that it is the same firmware that the manufacturer provides. What process should she follow to validate that the firmware is trusted firmware?
- Download the same file from the manufacturer and compare file size.
- Compare a hash of the file to a hash provided by the manufacturer.
- Run strings against the firmware to find any evidence of tempering.
- Submit the firmware to a malware scanning site to verify that it does not contain malware.
- Amanda's organization uses an air-gap design to protect the HSM device that stores their root encryption certificate. How will Amanda need to access the device if she wants to generate a new certificate?

- Wirelessly from her laptop
- Over the wired network from her PC
- From a system on the air-gapped network
- Amanda cannot access the device without physical access to it
- What is the key difference between a secured boot chain and a measured boot chain?
- A secured boot chain depends on a root of trust.
- A measured boot chain computes the hash of the next object in the chain and stores it securely.
- A secured boot chain computes the hash of the next object in the chain and stores it securely.
- A measured boot chain depends on a root of trust.
- Encrypted data transmission from a CPU to a GPU is an example of what type of technology?
- Secure Enclave
- Bus encryption
- Hardware security module
- Software security module
- Which of the following parties directly communicate with the end user during a SAML transaction?
- The relying party
- The SAML identity provider
- Both the relying party and the identity provider
- Neither the relying party nor the identity provider
- What type of dedicated device is used in organizations that can generate keys, create and validate digital signatures, and provide cryptoprocessing to both encrypt and decrypt data?
- HSMs
- BGPs
- SSMs
- None of the above
- Saeed wants to ensure that devices procured by his company are captured in inventory and tracked throughout their lifespan via physical inventory tracking methods. What can he do to make sure that the assets are easier to quickly identify against an asset inventory?
- Record them in a database
- Record them via paper forms
- Use asset tagging
- Use hardware address-based tagging
- Isaac is developing a mobile application and is following the OWASP Mobile Application Security Checklist. Which of the following is a practice he should not follow?
- The application will use symmetric cryptography with hard-coded keys as its sole method of encryption.
- Data for the application will be encoded on the network using TLS any time data is sent or received.
- The application will use the Secure Enclave on iOS devices to store cryptographic keys.
- The application invalidates sessions after a predetermined period of inactivity and session tokens expire.
- Micro-probing, applying unexpected or out of specification voltages or clock signals, and freezing a device are all examples of types of attacks prevented by what type of technique?
- DRM
- Anti-theft
- Anti-tamper
- Fault tolerance
- Patricia wants to protect updated firmware for her organization's proprietary hardware when it is installed and is concerned about third parties capturing the information as it is transferred between the host system and the hardware device. What type of solution should she use to protect the data in transit if the device is a PCIe internal card?
- Bus encryption
- CPU encryption
- Full-disk encryption
- DRM
- Piper wants to delete the contents of a self-encrypting drive (SED). What is the fastest way to securely do so?
- Use a full-drive wipe following DoD standards.
- Delete the encryption key for the drive.
- Use a degausser.
- Format the drive.
- What type of module is required to enable Secure Boot and remote attestation?
- A TPM module
- A HSM
- A GPM
- An MX module
- Although both Secure Boot and Measured Boot processes rely on a chain of trust, only one validates the objects in the chain. Which technology does this and what process does it follow?
- A Secured Boot chain validates the boot objects using private keys to check against public keys already in the BIOS.
- A Measured Boot chain computes the hash of the next object in the chain and compares it to the hash of the previous object.
- A Secured Boot chain computes the hash of the next object in the chain and compares it to the hash of the previous object.
- A Measured Boot chain validates the boot objects using private keys to check against public keys already in the BIOS.
- What type of operation occurs in a way that prevents another processor or I/O device from reading or writing to a memory location that is in use by the operation until the operation is complete?
- A complete operation
- A fractional operation
- Atomic execution
- Perpendicular execution
- Adil is attempting to boot a system that uses UEFI and has Secure Boot enabled. During the boot process, the system will not start because of a recognized key error. What has occurred?
- The user has not entered their passphrase.
- The drive token needs updated.
- A USB token is not plugged in.
- The operating system may not be secure.
- Support for AES, 3DES, ECC, and SHA-256 are all examples of what?
- Encryption algorithms
- Hashing algorithms
- Processor security extensions
- Bus encryption modules
- Bernie sets up a VPC for his organization and connects to it through a VPN. What has he created and where?
- A private segment of a public cloud
- A private segment of a local virtualization environment
- A public segment of a private cloud
- A public segment of a local virtualization environment
- What types of attacks can API keys help prevent when used to limit access to a REST-based service?
- Brute-force attacks
- Time-of-access/time-of-use attacks
- Man-in-the-middle attacks
- Denial-of-service attacks
- Which of the following is not a benefit of physical segmentation?
- Easier visibility into traffic
- Improved network security
- Reduced cost
- Increased performance
Use the following diagram to answer the next three questions.
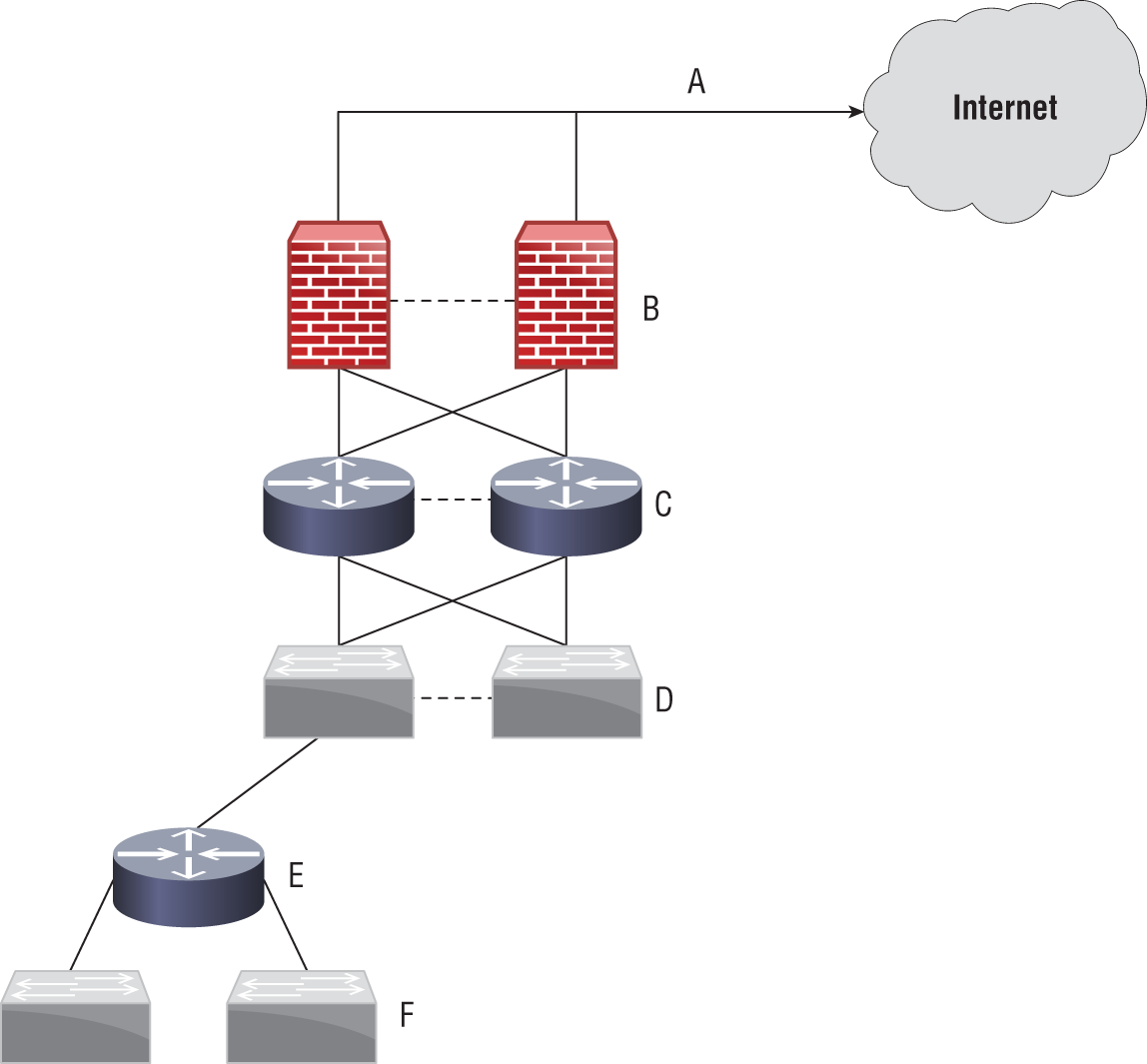
- Scott has designed a redundant infrastructure, but his design still has single points of failure. Which of the single points of failure is most likely to cause an organizationwide Internet outage?
- Point A
- Point C
- Point E
- Point F
- After identifying the single point of failure for his connectivity, Scott wants to fix the issue. What would be the best solution for the issue he identified?
- A second connection from the same ISP on the same fiber path
- A second connection from a different ISP on the same fiber path
- A second connection from the same ISP on a different fiber path
- A second connection from a different ISP on a different fiber path
- Scott has been asked to review his infrastructure for any other critical points of failure. If point E is an edge router and individual workstations are not considered mission critical, what issue should he identify?
- Point D
- Point E
- Point F
- None of the above
- Which of the following options is most effective in preventing known password attacks against a web application?
- Account lockouts
- Password complexity settings
- CAPTCHAs
- Multifactor authentication
- Ben adds a unique, randomly generated string to each password before it is hashed as part of his web application's password storage process. What is this process called?
- Mashing
- Hashing
- Salting
- Peppering
- Which of the following is not a common use case for network segmentation?
- Creating a VoIP network
- Creating a shared network
- Creating a guest wireless network
- Creating trust zones
- Kwame discovers that secrets for a microservice have been set as environment variables on the Linux host that he is reviewing using the following command:
docker run -it -e "DBUSER= appsrv" -e DBPASSWD=secure11" dbappsrvWhich processes can read the environment variables?
- The dbuser
- The Docker user
- All processes on the system
- Root and other administrative users
- What three layers make up a software defined network?
- Application, Datagram, and Physical layers
- Application, Control, and Infrastructure layers
- Control, Infrastructure, and Session layers
- Data link, Presentation, and Transport layers
- Which of the following is not a security advantage of VDI?
- No data is stored locally on the endpoint device.
- Patch management is easier due to use of a single central image.
- VDI systems cannot be infected with malware.
- There is isolation of business tools and files even when using personally owned devices.
- Micah is designing a containerized application security environment and wants to ensure that the container images he is deploying do not introduce security issues due to vulnerable applications. What can he integrate into the CI/CD pipeline to help prevent this?
- Automated checking of application hashes against known good versions
- Automated vulnerability scanning
- Automated fuzz testing
- Automated updates
- Susan wants to optimize the DevOps workflow as part of a DevSecOps initiative. What optimization method should she recommend to continuously integrate security without slowing work down?
- Automate some security gates.
- Perform security testing before development.
- Perform security testing only after all code is fully operational.
- None of the above.
- Camille wants to integrate with a federation. What will she need to authenticate her users to the federation?
- An IDP
- A SP
- An API gateway
- A SSO server
Answer the next three questions based on your knowledge of container security and the following scenario.
Brandon has been tasked with designing the security model for container use in his organization. He is working from the NIST SP 800-190 document and wants to follow NIST recommendations wherever possible.
- What can Brandon do to create a hardware-based basis for trusted computing?
- Only use in-house computing rather than cloud computing.
- Use a hardware root of trust like a TPM module and Secure Boot methods.
- Manually inspect hardware periodically to ensure that no keyloggers or other unexpected hardware is in place.
- Only use signed drivers.
- Brandon needs to deploy containers with different purposes, data sensitivity levels, and threat postures to his container environment. How should he group them?
- Segment containers by purpose
- Segment containers by data sensitivity
- Segment containers by threat model
- All of the above
- What issues should Brandon consider before choosing to use the vulnerability management tools he has in his non-container-based security environment?
- Vulnerability management tools may make assumptions about host durability.
- Vulnerability management tools may make assumptions about update mechanisms and frequencies.
- Both A and B
- Neither A nor B
- Timing information, power consumption monitoring, electromagnetic emanation monitoring, and acoustic monitoring are all examples of what types of attacks against SOCs, embedded systems, and other platforms?
- Trusted foundry attacks
- Side-channel attacks
- Primary channel attacks
- Untrusted foundry attacks
- What key functionality do enterprise privileged account management tools provide?
- Password creation
- Access control to individual systems
- Entitlement management across multiple systems
- Account expiration tools
- Amira wants to deploy an open standard–based single sign-on (SSO) tool that supports both authentication and authorization. What open standard should she look for if she wants to federate with a broad variety of identity providers and service providers?
- LDAP
- SAML
- OAuth
- OpenID Connect
- Nathaniel wants to use an access control system that takes into account information about resources like the resource owner, filename, and data sensitivity. What type of access control system should he use?
- ABAC
- DAC
- MAC
- RBAC
- What secure processing technique requires an operation to be complete before the memory locations it is accessing or writing to can be used by another process?
- Trusted execution
- Atomic execution
- Anti-tamper
- Bus encryption
- Betty wants to review the security logs on her Windows workstation. What tool should she use to do this?
Secpol.msc- Event Viewer
- Log Viewer
Logview.msc
- What type of attack is the use of query parameterization intended to prevent?
- Buffer overflows
- Cross-site scripting
- SQL injection
- Denial-of-service attacks
- Isaac is configuring syslog on a Linux system and wants to send the logs in a way that will ensure that they are received. What protocol should he specify to do so?
- UDP
- HTTP
- HTTPS
- TCP
- Bob wants to deploy a VPN technology with granular access controls for applications that are enforced at the gateway. Which VPN technology is best suited to this requirement?
- IKE VPNs
- TLS VPNs
- X.509 VPNs
- IPsec VPNs
- What type of attack is output encoding typically used against?
- DoS
- XSS
- XML
- DDoS
- Alaina wants to identify only severe kernel issues on a Linux system, and she knows that log levels for the kernel range from level 0 to level 7. Which of the following levels is the most severe?
- Level 1,
KERN_ALERT - Level 2,
KERN_CRIT - Level 4,
KERN_WARNING - Level 7,
KERN_DEBUG
Use the following scenario for questions 160–162.
Scott has been asked to select a software development model for his organization and knows that there are a number of models that may make sense for what he has been asked to accomplish. Use your knowledge of SDLC models to identify an appropriate model for each of the following requirements.
- Level 1,
- Scott's organization needs basic functionality of the effort to become available as soon as possible and wants to involve the teams that will use it heavily to ensure that their needs are met. What model should Scott recommend?
- Waterfall
- Spiral
- Agile
- Rapid Application Development
- A parallel coding effort needs to occur; however, this effort involves a very complex system and errors could endanger human lives. The system involves medical records and drug dosages, and the organization values stability and accuracy over speed. Scott knows the organization often adds design constraints throughout the process and that the model he selects must also deal with that need. What model should he choose?
- Waterfall
- Spiral
- Agile
- Rapid Application Development
- At the end of his development cycle, what SDLC phase will Scott enter as the new application is installed and replaces the old code?
- User acceptance testing
- Testing and integration
- Disposition
- Redesign
- Sofía wants to ensure that the ICs in the new device that her commercial consumer products company is releasing cannot be easily reverse engineered. Which technique is not an appropriate means of meeting her requirement?
- Use a trusted foundry.
- Encase the IC in epoxy.
- Design the chip to zeroize sensitive data if its security encapsulation fails.
- Design the chip to handle out of spec voltages and clock signals.
- Charles is reviewing the certificate properties for the certificate for
www.comptia.organd notices that the DNS name readsDNS name = *.comptia.orgDNS name = comptia.orgWhat type of certificate is in use?
- A multidomain certificate
- A wildcard certificate
- A mismatched certificate
- An invalid certificate
- Alaina wants to implement a modern service-oriented architecture (SOA) that relies on HTTP-based commands, works well in limited bandwidth environments, and can handle multiple data formats beyond XML. What should she build her SOA in?
- SOAP
- Waterfall
- REST
- CAVE
- The OWASP Session Management Cheatsheet advises that session IDs are meaningless and recommends that they should be used only as an identifier on the client side. Why should a session ID not have additional information encoded in it like the IP address of the client, their username, or other information?
- Processing complex session IDs will slow down the service.
- Session IDs cannot contain this information for legal reasons.
- Session IDs are sent to multiple different users, which would result in a data breach.
- Session IDs could be decoded, resulting in data leakage.
- Nia's honeynet shown here is configured to use a segment of unused network space that has no legitimate servers in it. What type of threats is this design particularly useful for detection?

- Zero-day attacks
- SQL injection
- Network scans
- DDoS attacks
- Bounds checking, removing special characters, and forcing strings to match a limited set of options are all examples of what web application security technique?
- SQL injection prevention
- Input validation
- XSS prevention
- Fuzzing
- Abigail is performing input validation against an input field and uses the following regular expression:
^(AA|AE|AP|AL|AK|AS|AZ|AR|CA|CO|CT|DE|DC|FM|FL|GA|GU|HI|ID|IL|IN|IA|KS|KY|LA|ME|MH|MD|MA|MI|MN|MS|MO|MT|NE|NV|NH|NJ|NM|NY|NC|ND|MP|OH|OK|OR|PW|PA|PR|RI|SC|SD|TN|TX|UT|VT|VI|VA|WA|WV|WI|WY)$What is she checking with the regular expression?
- She is removing all typical special characters found in SQL injection.
- She is checking for all U.S. state names.
- She is removing all typical special characters for cross-site scripting attacks.
- She is checking for all U.S. state name abbreviations.
- Adam is testing code written for a client-server application that handles financial information and notes that traffic is sent between the client and server via TCP port 80. What should he check next?
- If the server stores data in unencrypted form
- If the traffic is unencrypted
- If the systems are on the same network
- If usernames and passwords are sent as part of the traffic
- Nick wants to prevent unauthorized firmware from being installed on devices that his organization manufacturers. What technique should he use to provide an effective security layer?
- Encrypted firmware
- Signed firmware
- Binary firmware
- None of the above
- A web server and a web browser are examples of what type of platform?
- Embedded
- Firmware
- Client-server
- SOC
- Lara has been assigned to assess likely issues with an embedded system used for building automation and control. Which of the following software assurance issues is least likely to be of concern for her organization?
- Lack of updates and difficulty deploying them
- Long life cycle for the embedded devices
- Assumptions of network security where deployed
- Use of proprietary protocols
- Lucca wants to prevent brute-force attacks from succeeding against a web application. Which of the following is not a commonly implemented solution to help reduce the effectiveness of brute-force attacks?
- Multifactor authentication
- Account lockouts
- Password reuse
- CAPTCHAs
- Noam wants to ensure that he would know if the operating system, boot loader, and boot drivers of his PC were infected with malware. What type of boot process should he use to have it checked using a cryptographic hash?
- Manual boot hash comparison
- Secure Boot
- TPM
bootsec
- Jennifer uses an application to send randomized data to her application to determine how it responds to unexpected input. What type of tool is she using?
- A UAT tool
- A stress testing tool
- A fuzzer
- A regression testing tool
- Isaac wants to securely handle passwords for his web application. Which of the following is not a common best practice for password storage?
- Use a dedicated password hash like
bcrypt. - Use a salt.
- Store passwords in an encrypted form.
- Set a reasonable work factor for your system.
- Use a dedicated password hash like
- Kristen wants to securely store passwords and knows that a modern password hashing algorithm is her best option. Which of the following should she choose?
- SHA-256
bcrypt- MD5
- SHA-512
- Liam wants to protect data at rest in an SaaS service. He knows that he needs to consider his requirements differently in his cloud environment than an on-premises environment. What option can he use to ensure that the data is encrypted when it is stored?
- Install a full-disk encryption tool.
- Install a column-level encryption.
- Select an SaaS service that supports encryption at rest.
- Hire an independent auditor to validate the encryption.
- Faraj wants to use statistics gained from live analysis of his network to programmatically change its performance, routing, and optimization. Which of the following technologies is best suited to his needs?
- Serverless
- Software-defined networking
- Physical networking
- Virtual private networks (VPNs)
- Elaine's team has deployed an application to a cloud-hosted serverless environment. Which of the following security tools can she use in that environment?
- Endpoint antivirus
- Endpoint DLP
- IDS for the serverless environment
- None of the above
- Valerie is leading an effort that will use a formal Fagan inspection of code. Which phase in the Fagan inspection process includes finding actual defects?

- Overview
- Preparation
- Inspection
- Rework
- Greg wants to prevent SQL injection in a web application he is responsible for. Which of the following is not a common defense against SQL injection?
- Prepared statements with parameterized queries
- Output validation
- Stored procedures
- Escaping all user-supplied input
- While reviewing code that generates a SQL query, Aarav notices that the “address” field is appended to the query without input validation or other techniques applied. What type of attack is most likely to be successful against code like this?
- DoS
- XSS
- SQL injection
- Teardrop
- What type of assertion is made to an SP in a SAML authentication process?
- The user's password
- Who the user is
- Who the SP is
- What rights the user has
- Megan wants to downgrade the firmware for a device she is working with, but when she attempts to do so, the device will not accept the older firmware. What type of hardware technology has she most likely encountered?
- A TPM
- A HSM
- eFuse
- A trusted foundry
- Security screws are an example of what type of control?
- Anti-tamper
- Detective
- Anti-theft
- Corrective
- What U.S. government program focuses on ensuring that integrated circuits have an assured chain of custody, a supply chain that can avoid disruption, and processes in place to protect chips from being modified or tampered with?
- Secure Forge
- DMEA
- Trusted foundry
- IC Protect
- Michelle wants to acquire data from a self-encrypting drive. When is the data on the drive unencrypted and accessible?
- Data is unencrypted before the system boots.
- Data is unencrypted after the OS boots.
- Data is unencrypted only when it is read from the drive.
- Data is never unencrypted.
- What term describes hardware security features built into a CPU?
- Atomic execution
- Processor security extensions
- Processor control architecture
- Trusted execution
- Angela wants to provide her users with a VPN service and does not want them to need to use client software. What type of VPN should she set up?
- IPsec
- Air gap
- VPC
- SSL/TLS
- Lucca needs to explain the benefits of network segmentation to the leadership of his organization. Which of the following is not a common benefit of segmentation?
- Decreasing the attack surface
- Increasing the number of systems in a network segment
- Limiting the scope of regulatory compliance efforts
- Increasing availability in the case of an issue or attack
- Kubernetes and Docker are examples of what type of technology?
- Encryption
- Software-defined networking
- Containerization
- Serverless
- Nathan is designing the logging infrastructure for his company and wants to ensure that a compromise of a system will not result in the loss of that system's logs. What should he do to protect the logs?
- Limit log access to administrators.
- Encrypt the logs.
- Rename the log files from their common name.
- Send the logs to a remote server.
- After creating a new set of encryption keys for an SSH key, Allan inadvertently uploads them to GitHub as part the check-in process for software he is writing. What options does he have to fix this issue?
- He can modify the private key to fix the issue and then needs to re-upload it to GitHub.
- He needs to generate a keypair and replace it wherever it is in use.
- He needs to change the password for the keypair.
- He needs to modify the public key to fix the issue and then needs to re-upload it to GitHub.
- What type of software testing most frequently happens during the development phase?
- Unit testing
- User acceptance testing
- Fuzzing
- Stress testing
- What are the four phases found in the spiral SDLC model?
- Design, User Story Identification, Build, and Analysis
- Identification, Design, Build, and Evaluation
- Requirement Gathering, Analysis, Design, and Build
- User Story Identification, User Story Design, User Co-Creation, and User Acceptance Testing
- What is the primary concept behind DevSecOps versus DevOps?
- Development should occur before security operations.
- Device security is part of operations.
- Security should be part of the integrated application life cycle.
- Operations security requires developers to play the primary security role.
Use the following diagram and scenario for questions 199–201.
Amanda has been assigned to lead the development of a new web application for her organization. She is following a standard SDLC model as shown here. Use the model and your knowledge of the software development life cycle to answer the following questions.

- Amanda's first task is to determine if there are alternative solutions that are more cost effective than in-house development. What phase is she in?
- Design
- Operations and maintenance
- Feasibility
- Analysis and requirements definition
- What phase of the SDLC typically includes the first code analysis and unit testing in the process?
- Analysis and requirements definition
- Design
- Coding
- Testing and integration
- After making it through most of the SDLC process, Amanda has reached point E on the diagram. What occurs at point E?
- Disposition
- Training and transition
- Unit testing
- Testing and integration
- Ansel knows he wants to use federated identities in a project he is working on. Which of the following should not be among his choices for a federated identity protocol?
- OpenID
- SAML
- OAuth
- Authman
