Chapter 1. Reconnaissance and Scanning
This chapter covers the following CEH exam objectives:
• Reconnaissance types
• Scanning techniques
• Scanning tools
• Evasion techniques
One of the fundamental tasks with penetration testing is gathering information about the target; this is called reconnaissance. A successful penetration test depends on having information about the target site. Scanning tools and techniques are critical to conducting a successful penetration test.
Reconnaissance Types
Exam Alert
Objective The various scanning tools are critical for the Certified Ethical Hacker exam. Make certain you know these tools in detail. It is not enough to just know each tool in a general manner. Make sure you know details. For example, with command line tools, such as Nmap, you should know the various flags.
In this section we discuss various scanning techniques and tools. We also discuss specific terminology and methodology. There are alternative terms for reconnaissance. One such term that is used on the Certified Ethical Hacker (CEH) exam is footprinting.
There are many ways to conduct reconnaissance, or footprinting. There are two types of footprinting: active and passive. Passive footprinting involves gathering information about the target without any direct interaction with the target systems or network. Active footprinting requires some level of interaction with the target systems.
Passive Reconnaissance Techniques
Passive reconnaissance techniques allow you to gather a plethora of information from a website without any interaction with the website. The target doesn’t actually know you are gathering the information. This is usually the first step in the ethical hacking process: gathering as much information about the target as you can before moving ahead in the Cyber Kill Chain. There are a wide range of tools and techniques to facilitate this process, many of them free.
Google Hacking
One passive footprinting technique that is featured on the CEH v11 exam is using Google searches, sometimes called Google hacking. You can do quite a bit with a Google search. This is a list of commonly used Google hacking techniques:
• [cache:]: Displays the web pages stored in the Google cache. For example, the Google cache of my page can be retrieved with cache:chuckeasttom.com.
• [link:]: Lists web pages that have links to the specified web page.
• [related:]: Lists web pages that are similar to a specified web page.
• [info:]: Presents some information that Google has about a particular web page.
• [site:]: Presents results only for websites in the given domain. For example, to search my website for the word cryptography, you would use cryptography site:chuckeasttom.com.
• [allintitle:]: Presents results only for websites with all of the search keywords in the title.
• [intitle:]: Restricts the results to documents containing the search keyword in the title.
• [allinurl:]: Restricts the results to those with all of the search keywords in the URL.
• [inurl:]: Restricts the results to documents containing the search keyword in the URL.
• [location:]: Finds information for a specific location.
• [filetype:]: Finds results that are a specific file type. For example, if you want hacking but only PDF results, you can use hacking filetype:pdf.
Figure 1.1 shows an example in which inurl:view/index.shtml has been entered in Google. The result are links to pages with web cameras.
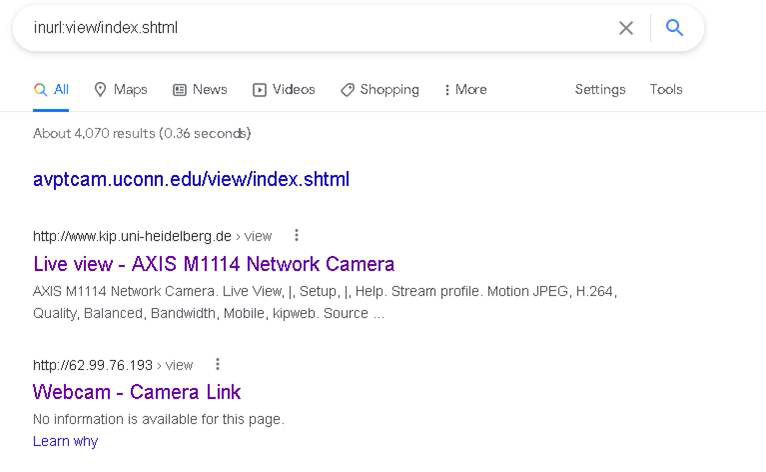
Figure 1.1 Google Search
In this example, the search string tells Google to find any web pages that have the text view/index.shtml in the URL of the website. This URL denotes a control interface for a web camera. You can use this technique to find any number of things in websites. A few examples that will be useful to you are listed in Table 1.1. Note some sources call these Google dorks.
Table 1.1 Google Hacking Examples

You can use Google Advanced Search, shown in Figure 1.2, to search using these strings and more.
Figure 1.2 Google Advanced Search
Google Advanced Image Search works much like Google Advanced Search, but it allows you to search for images rather than terms.
There is an exploit database called the Google Hacking Database at https://www.exploit-db.com/google-hacking-database. This is a good place to find vulnerabilities. You can search for specific operating systems, software, and more. This website is shown in Figure 1.3.
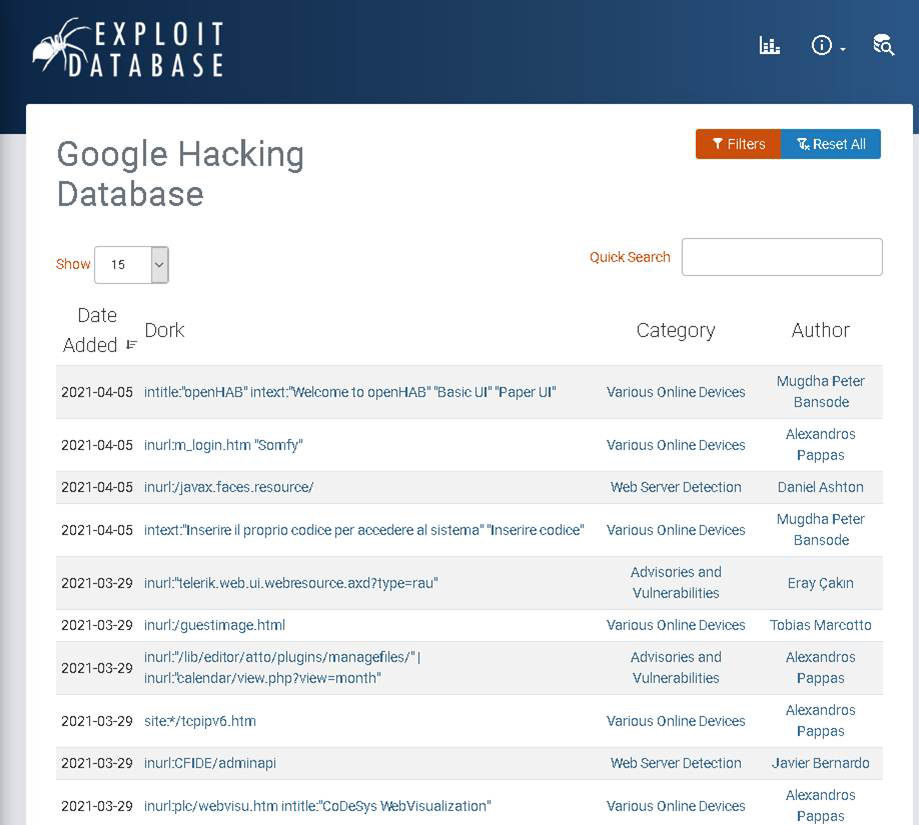
Figure 1.3 Google Hacking Database
These are a few of the internet resources that provide even more details on Google hacking:
https://resources.infosecinstitute.com/topic/google-hacking-overview/
https://www.blackhat.com/presentations/bh-europe-05/BH_EU_05-Long.pdf
https://www.sans.org/posters/google-hacking-and-defense-cheat-sheet/
Geographic Searches
Many online maps can help you find the geographic location of a given target. A few of them are listed here:
• Google Maps: https://maps.google.com
• National Geographic Maps: http://maps.nationalgeographic.com
• Bing Maps: https://www.bing.com/maps
• Wikimapia: http://www.wikimapia.org
Data Gathering
For the CEH exam you need to know that people searches as part of the passive footprinting process. For example, after you find out the name of a company’s CISO (chief information security office), you might want to try and find out more about that person through various websites and social media. Here are a few of the sites you might use:
• Intelius: https://www.intelius.com
• BeenVerified: https://www.beenverified.com
• Facebook: https://www.facebook.com
• Twitter: https://www.twitter.com
• LinkedIn: https://www.linkedin.com
There are also tools that will help you to gather information from some social media sites. The tool InSpy is a shell utility you can use with Linux. InSpy has two modes. The first mode, TechSpy, crawls LinkedIn job listings based on a target company. The second mode, EmpSpy, crawls LinkedIn for employees working at a company. This tool is a Python script that can be downloaded from https://github.com/leapsecurity/InSpy. It works on Windows and macOS as well as Linux.
For the CEH exam you also need to know how to use a wide range of websites to gather information, including financial websites and job websites. Job websites are particularly useful. If a company is looking for a web administrator who has Apache and Debian Linux experience, you can deduce that their web server is Debian Linux running Apache.
For the CEH exam you should know how to use Google groups, other forums, and blogs to gather information about a target. You may find employees discussing items in the organization that can possibly provide you valuable intel. A simple example would be a network administrator complaining in a forum that he or she is having difficulty configuring the new firewall. That would strongly indicate that the firewall is quite vulnerable, and you might also be able to gather the specs of the firewall and the vendor details.
Many sites allow you to set alerts, so that after you have conducted a search, you can be alerted when anything changes. Two examples are:
• Twitter Alerts: https://twitter.com/alerts
• Google Alerts: https://www.google.com/alerts
Useful Websites
There are a number of websites that allow you to gather information about a target without interacting with the target. The CEH exam expects you to know what these sites are and how to use them.
A website commonly used for passive footprinting is https://www.netcraft.com. This site allows you to scan websites for free and now also sells a wide range of cybersecurity services. Figure 1.4 shows a scan of my own website.

Figure 1.4 netcraft.com Scan
Another popular site for gathering information is https://www.shodan.io. This site requires you to register, but registration is free. You can then perform a wide range of searches. Figure 1.5 shows the results of a search for public-facing devices with default passwords in the city of Chicago.

Figure 1.5 Shodan Search
There are quite a few search types you can do. Some commonly used searches are given here:
• Search for default passwords
• default password country:US
• default password hostname:chuckeasttom.com
• default password city:Plano
• Find Apache servers
• apache city:“San Francisco”
• Find Webcams
• webcamxp city:Chicago
• Find OLD IIS
• “iis/6.0”
Commonly used Shodan filters are:
• Country
• City (though it does not always work)
• Hostname
• net (IP address range)
• Operating system
• Port
Shodan is a very versatile tool, and you should be quite familiar with it.
Exam Alert
Objective You should know the various filters and search methods used in Shodan.
The site https://censys.io is a paid service that provides a number of search options.
Another site that the CEH exam expects you to know about is https://archive.org. This site, which archives versions of websites, is often referred to as the Wayback Machine. The number of previous versions of a website that are archived depends on the popularity of the website. You will, for example, find a great many more past versions of Yahoo.com than you will of my own website. A search for www.yahoo.com on archive.org is shown in Figure 1.6.

Figure 1.6 Archive.org Search
Metadata Tools
It is useful to extract metadata. Whether you are working with a PDF, a Word document, or some other type of file, understanding the metadata of the file can be useful. A few metadata extraction tools are listed here:
• ExtractMetadata: http://www.extractmetadata.com
• FOCA: https://github.com/ElevenPaths/FOCA
• PhotoME: https://www.photome.de
• Meta Tag Analyzer: https://www.powermapper.com/products/sortsite/ads/website-meta-tags/
• BuzzStream: http://tools.buzzstream.com
• Exif Data Reader: https://www.dcode.fr/exif-data
• Analyse Metadata: http://www.exadium.com
• Exiftool: https://sno.phy.queensu.ca
• Exif Data Viewer: https://www.exifdata.com/
Along with these metadata extraction tools, there are sites that allow you to monitor websites, including the following:
• VisualPing: https://visualping.io
• Versionista: https://versionista.com
• WatchThatPage: http://www.watchthatpage.com
• Sken.io: https://sken.io
• Page Crawl: https://pagecrawl.io
• On Web Change: https://onwebchange.com
• Change Tower: https://changetower.com
For the CEH you will also need to understand about tracking information about emails. This involves email headers as well as email tracking applications. Email headers can provide a great deal of information. The format and content of email is actually established via the standard RFC 3864, “Header Field Registration,” which describes message header field names. Common header fields for email include:
• To: The email address and, optionally, the name of the message’s primary recipient(s).
• Subject: A brief summary of the topic of the message.
• Cc: Carbon copy, for sending a copy to secondary recipients.
• Bcc: Blind carbon copy, for adding addresses to the SMTP delivery list but making them invisible to other recipients.
• Content-Type: Information about how the message is to be displayed, usually a MIME type.
• Precedence: Used to indicate that automated vacation or out-of-office responses should not be returned for this mail (e.g., to prevent vacation notices from being sent to all other subscribers of a mailing list). Common values are “bulk,” “junk,” and “list.”
• Received: Tracking information generated by mail servers that have previously handled a message, in reverse order (i.e., last handler first).
• References: Message ID of the message that this is a reply to.
• Reply-To: Address that should be used to reply to the message.
• Sender: Address of the actual sender acting on behalf of the author listed in From.
As an ethical hacker, you might want to send an email to someone at an organization just to get a response and examine the headers. This can tell you a lot about the organization, including its email servers. There are several websites and applications for tracking emails and checking to see if an email address is valid. A few are listed here:
• PoliteMail: http://www.politemail.com
• Yesware: http://www.yesware.com
• Mail Tracker: https://hunter.io/mailtracker
• ContactMonkey: https://www.contactmonkey.com
• Zendio: http://www.zendio.com
• Rocket Reach: https://rocketreach.co
• DidTheyReadIt: http://www.didtheyreadit.com
• Trace Email: http://whatismyipaddress.com
• Email Tracker (add-on for Google Chrome): https://chrome.google.com/webstore/detail/email-tracker//
You can look up email servers for any given domain. The following are a few websites that will facilitate this process.
• Online Domain Tools http://mxlookup.online-domain-tools.com
• MX Lookup http://www.hashemian.com/tools/domain-email.php
You can also check to see if an email address exists:
Open-Source Intelligence
In general, the objectives of the CEH exam expect that you know to attempt to get information from a wide array of resources, such as company press releases, online searchers, and regulatory reports. A few helpful websites are listed here:
• EDGAR: https://www.sec.gov/edgar.shtml
• LexisNexis: https://www.lexisnexis.com
• Bloomberg: https://www.bloomberg.com
• MarketWatch: https://www.marketwatch.com
• Alexa: https://www.alexa.com
The website https://osintframework.com is a landing page for a wide range of open-source intelligence (OSINT) websites. You can see this site in Figure 1.7.
Figure 1.7 OSINT Page
At some point you might want to get information about who registered a domain name. Such a search is called a WhoIs search because the underlying protocol is called Whois. Regional internet registries that store registry information. WhoIs searches these, but you should know them for the CEH exam:
• American Registry for Internet Numbers (ARIN): https://www.arin.net
• Africa Network Information Center (AFRINIC): https://www.afrinic.net
• Réseaux IP Européens Network Coordination Centre (RIPE NCC): https://www.ripe.net
• Latin American and Caribbean Network Information Centre (LACNIC): https://www.lacnic.net
• Asia Pacific Network Information Centre (APNIC): https://www.apnic.net
Exam Alert
Objective You will be expected to know these regional registries. Many people now use Whois websites, rather than going to the registry sites, but for the CEH exam, you need to know the registries.
A number of websites can facilitate Whois lookups for you. Some of them are listed here:
• OSINT Framework https://osintframework.com
• ICANN WhoIS https://whois.icann.org
• WhoIS http://cqcounter.com/whois/
• Network Solutions WhoIS https://www.networksolutions.com/whois
• WhoIS https://www.whois.net
• WhoIS https://www.whois.com
• WhoIS https://who.is
Once you have an IP address, you can use a number of sites to get the geolocation of that IP address. Here are some of them:
• IP Location Finder: https://tools.keycdn.com/geo
• IP Geolocator: https://www.ipligence.com/geolocation
• Neustar: https://www.home.neustar/resources/tools/ip-geolocation-lookup-tool
• IP Address Geographical Location Finder: http://www.ipfingerprints.com
• IP Location: https://www.iplocation.net
• GeoIP Lookup Tool: https://www.ultratools.com
• Geo IP Tool: https://geoiptool.com
Figure 1.8 shows the use of Neustar to find the geolocation of an IP address.
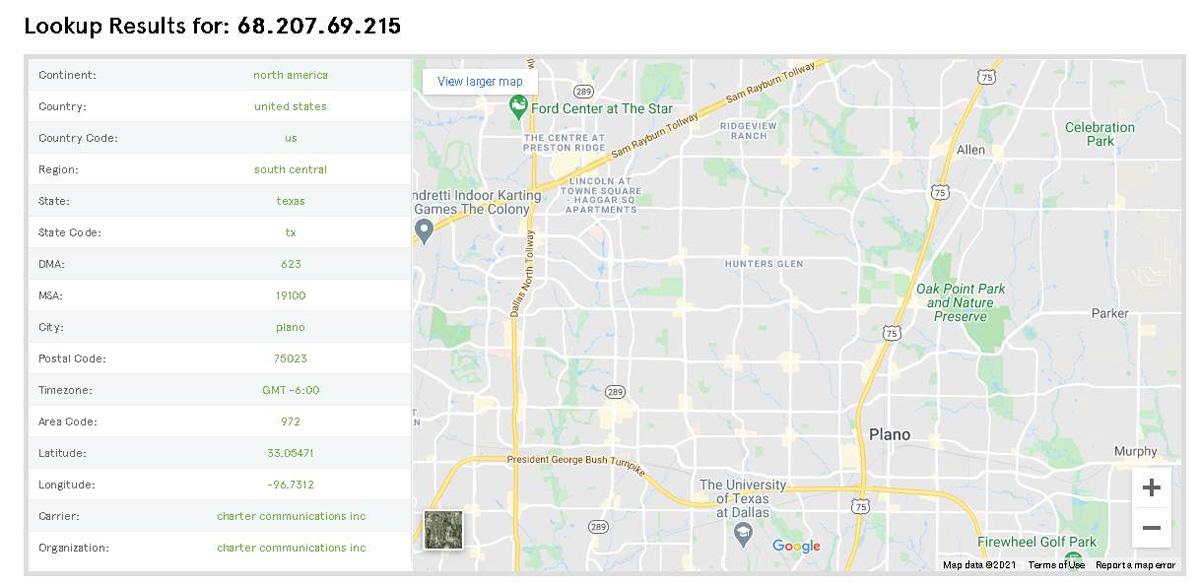
Figure 1.8 Neustar Geolocation
As you gather information about a target, DNS (Domain Name System) information is important. DNS maps IP addresses to domain names. The CEH exam expects you to know the different types of DNS records. The major types are listed here:
• A: Host (Hostname to IP address)
• PTR: Pointer (IP address to hostname)
• NS: Name Server
• SOA: Start of Authority
• SRC: Service Locator
• MX: Mail Server
• CNAME: Canonical naming (aliases for hosts)
• RP: Responsible Person
• HINFO: Information about the host, which can include OS and CPU
Fortunately, there are a number of sites that can provide DNS information about any domain name. A few of them are listed here:
• DNS Tools http://www.mydnstools.info
• DNS Lookup https://mxtoolbox.com/DNSLookup.aspx
• Online DIG https://toolbox.googleapps.com/apps/dig/
• DNS Tools https://dnschecker.org/all-tools.php
• Nirsoft Tools http://www.nirsoft.net
• DNS Watch https://www.dnswatch.info
Figure 1.9 shows the DNS results for chuckeasttom.com from https://mxtoolbox.com/DNSLookup.aspx.

Figure 1.9 https://mxtoolbox.com/DNSLookup.aspx DNS Results
Operating System Commands
There are also a number of commands you need to know for the CEH exam. traceroute is a command that traces the route from your machine to a target. The command tracert in Windows works the same way. Figure 1.10 shows the tracert (Windows) command being used from my computer to www.Pearson.com.

Figure 1.10 tracert Results
It probably will not surprise you that there are a number of tools that can help you trace the route to any address. Some of them even display results in very nice graphical interfaces. A few of those tools are listed here:
• Tialsoft Tools http://www.tialsoft.com
• OreWare http://www.oreware.com
• Ping Plotter http://www.pingplotter.com
• Visual Route http://www.visualroute.com
There are also other commands you should know. The ping command simply sends an ICMP (Internet Control Message Protocol) packet to the destination. It only tells you if the destination is reachable. The difference between ping and traceroute is often explained like this: ping tells you if you can get there, and traceroute tells you how to get there.
You can use the tool nslookup to attempt to gather information about any domain. It actually opens a new command prompt so you can try nslookup commands on the target. Usually, if the DNS server is secure, these won’t be successful.
Hacking Terminology
For the CEH exam you will need to understand basic hacking terminology. You will pick up a lot of the important terms as you go through this book. However, a few basic terms you should know are listed here:
• White hat hacker: A hacker who uses his or her skills ethically. Also known as an ethical hacker. Penetration testers are white hat hackers hired to test the security of a system.
• Black hat hacker: A hacker who uses his or her skills unethically—and often criminally.
• Gray hat hacker: Typically someone who is generally a white hat hacker but who, for some reason they believe is compelling, operates outside ethical or legal standards. (Different sources define this term differently.)
• Shoulder surfing: Literally looking over someone’s shoulder to derive information (e.g., in a coffee shop, trying to get someone’s password as they enter it).
• Dumpster diving: Looking through trash for documents that might reveal information that is valuable.
• White box testing: Penetration testing in which the tester has detailed knowledge of the target system. This is sometimes also called clear box testing or glass box testing.
• Black box testing: Penetration testing in which the tester knows only the target IP address or domain name.
Other Tools
There are many tools to aid you in all phases of ethical hacking. You should note that tools are a big part of the CEH exam. Not only should you memorize the names of tools and what they are for, but you should use as many of them as you can. Many of these tools can be downloaded for free. And some of them come with Kali Linux, which is a Linux distribution that comes with a number of hacking and forensics tools already installed and is available as a free download. For any penetration tester, having Kali Linux is a must. Kali is full of many tools, including the infamous Metasploit, which you will use in later chapters.
One popular tool in Kali is recon-ng. This Linux tool performs a number of tests at one time. Figure 1.11 shows recon-ng on a Kali Linux machine.
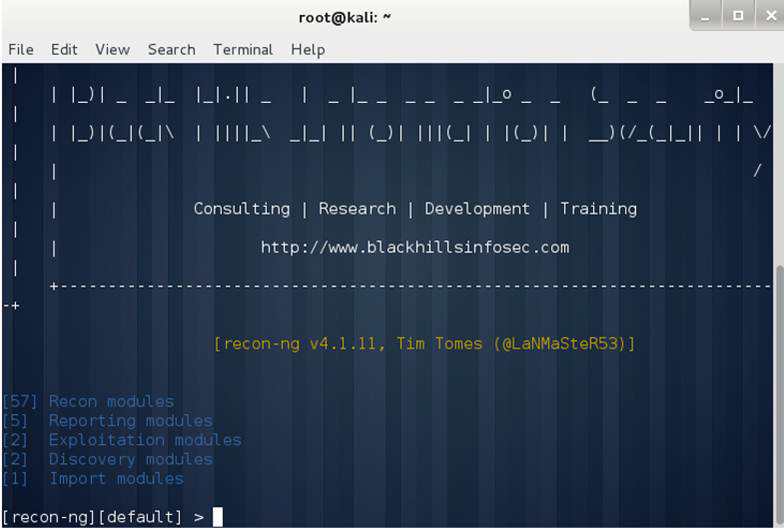
Figure 1.11 recon-ng
Active Reconnaissance Techniques
Active scanning involves actually interacting with the target network. This means there is a chance of the target network detecting your activity. There are many tools for active scanning, and the CEH exam expects you to actually know how the tools work. In other words, you need to understand TCP communications. The discussion that follows is about TCP packets, not UDP packets. UDP (User Datagram Protocol) doesn’t confirm the receipt of each packet, so these packs behave a bit differently from TCP packets.
A network packet has at least three headers: TCP (Transmission Control Protocol), IP (Internet Protocol), and Ethernet. Each of these headers contains different information that can be useful. For example, the IP header contains the source and destination IP addresses. There are also a number of flags that define how the packet should work:
• SYN = 2: Synchronized. This is a request to synchronize the sender and receiver.
• RST = 4: Reset. This is used when communication needs to be reset.
• PSH = 8: Push. This indicates to push.
• ACK = 16: Acknowledgement. All packets after the initial SYN packet sent by the client should have this flag set.
• URG = 32: Urgent. This marks the packet as urgent.
• ECE = 64: ECN-Echo. This indicates things about the sender. If the SYN flag is set, the TCP peer is ECN capable.
• CWR = 128: Congestion Window Reduced (CWR). This flag is set by the sending host to indicate that it received a TCP segment with the ECE flag set and had responded in the congestion control mechanism.
A typical connection begins with the machine requesting a connection sending a packet with the SYN flag set. The target machine responds with the SYN and ACK flags set. Then the sender sends back the ACK flag. This is called a three-way handshake. When communication is over, the side ending the communication sends a packet with the FIN flag, the other side sends an ACK and then a FIN, and the machine that requested the termination sends an ACK flag.
Many scanning tools work by sending an unexpected flag. For example, a tool may send the FIN flag when there is no connection. Different systems respond to this flag in different ways. The FIN flag allows the scanning tool to make guesses about the target system and gain information about the target. Another technique is called the Xmas scan because several flags are turned on—like lights on a Christmas tree. The null scan has all flags turned off. Again, the goal is to send unexpected packets to the destination and see what sort of response comes back.
Another type of scan that is sometimes used is the IDLE scan, sometimes called the IPID header scan. An IP packet has an IPID (IP identification) number. Operating systems increase the IPID number for each packet sent. The IDLE scan uses an idle machine (thus the name), also called a zombie machine, to help scan the target. The IDLE scan works like this:
1. You send a SYN + ACK packet to the zombie machine to probe its IPID number.
2. That machine is not expecting a SYN + ACK packet, as there was no preceding SYN, so it sends an RST packet. That RST packet contains the current IPID number.
3. You send a SYN packet to the target machine, spoofing the IP address of the zombie machine.
4. If the port is open, the target sends a SYN+ACK packet to the zombie machine. In response, the zombie sends an RST to the target.
5. If the port is closed, the target sends an RST to the zombie, but the zombie does not send anything back.
6. You probe the zombie IPID number again. An IPID increased by 2 indicates an open port, whereas an IPID increased by 1 indicates a closed port.
The idea is to perform a port scan of the target, but the target’s logs will contain only the IP address of the zombie machine.
Exam Alert
Objective The CEH exam may test you on all of the flags. However, the FIN, SYN, ACK, and RST flags are most often used by scanning tools, so you should ensure that you understand these flags. Also make certain you understand the three-way handshake.
For the CEH, you to have at least basic networking knowledge. If you don’t have a working knowledge of networking, you won’t be able to fully understand the information provided by many tools. We cover a few basic facts here. However, if you feel you need more help with networking concepts and terminology, you might want to read CompTIA Network+ N10-007 Exam Cram, 6th edition, by Emmett Dulaney.
IP version 4 (IPv4) addresses are being replaced by IP version 6 (IPv6) address, but IPv4 addresses are still quite common. An IPv4 address appears as a series of four decimal numbers, called octets, separated by periods (for example, 162.31.44.125). Each octet must be between 0 and 255; therefore, the address 162.31.44.466 would not be valid. An IPv4 address is actually four binary numbers; it is displayed in decimal format so that humans can readily read them.
Given that an IPv4 address is 32 bits long (in binary), there are 232 possible IPv4 addresses; that is a total of over 4.2 billion possible IP addresses. This might seem like a lot of addresses, but we have already run out of new IP addresses. A number of measures have been used to expand the number of IP addresses, including private and public IP address space. Also, we now have IPv6 to address this issue.
IPv6 utilizes a 128-bit address (instead of a 32-bit address), so there is no chance of running out of IP addresses in the foreseeable future. IPv6 also utilizes a hex numbering method in order to avoid long addresses such as 132.64.34.26.64.156.143.57.1.3.7.44.122.111.201.5. An example of a hex address is 3FFE:B00:800:2::C.
SSDP Scan
SSDP (Simple Service Discovery Protocol) enables one machine to discover the services on another machine. It allows a computer to find out which machines are running DHCP, DNS, or other services. The UPnP SSDP M-SEARCH information discovery tool is a part of Metasploit that can be used to find services on other machines (see Figure 1.12). We will explore Metasploit in detail in later chapters.
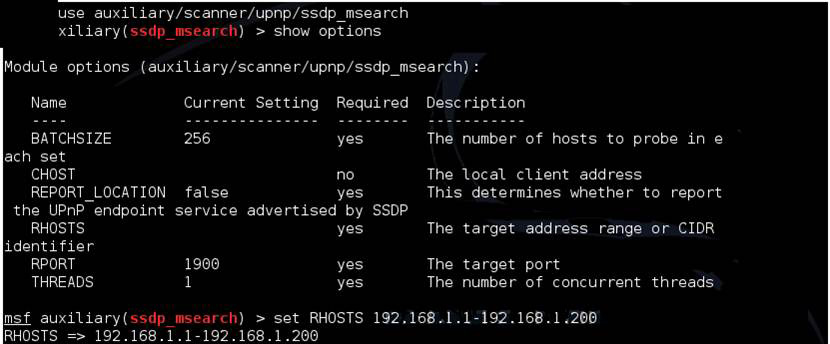
Figure 1.12 UPnP SSDP M-SEARCH
Nmap
Nmap is a popular port scanner, and you can expect the CEH exam to ask you details about it. Nmap allows you to set a number of flags to customize a scan. The allowed flags are listed here:
• -O: Operating system detection
• -sP: Ping scan
• -sT: TCP connect scan
• -sS: SYN scan
• -sF: FIN scan
• -sX: Xmas scan
• -sN: NULL scan
• -sU: UDP scan
• -sO: Protocol scan
• -sA: ACK scan
• -sW: Windows scan
• -sR: RPC scan
• -sL: List/DNS scan
• -sI: Idle scan
• -Po: Don’t ping
• -PT: TCP ping
• -PS: SYN ping
• -PI: ICMP ping
• -PB: TCP and ICMP ping
• -PM: ICMP netmask
• -oN: Normal output
• -oX: XML output
• -oG: Greppable output
• -oA: All output
• -T: Timing
• -T 0: Paranoid
• -T 1: Sneaking
• -T 2: Polite
• -T 3: Normal
• -T 4: Aggressive
• -T 5: Insane
A scan that leaves the target half open is often called a stealth scan. In such a scan, you send a SYN packet, the server responds with SYN/ACK, and the client sends an RST before the connection is complete. This is often not noted by defensive systems. The most reliable scan is a full open scan. This means simply completing the three-way handshake and getting a full connection. The data from a full open scan is quite reliable, but it is guaranteed that your scan is at least in the logs of the target system. Scans can be done with any of the flags set, all of them set, or none of them set. There is a graphic version of Nmap called Zenmap, as shown in Figure 1.13.
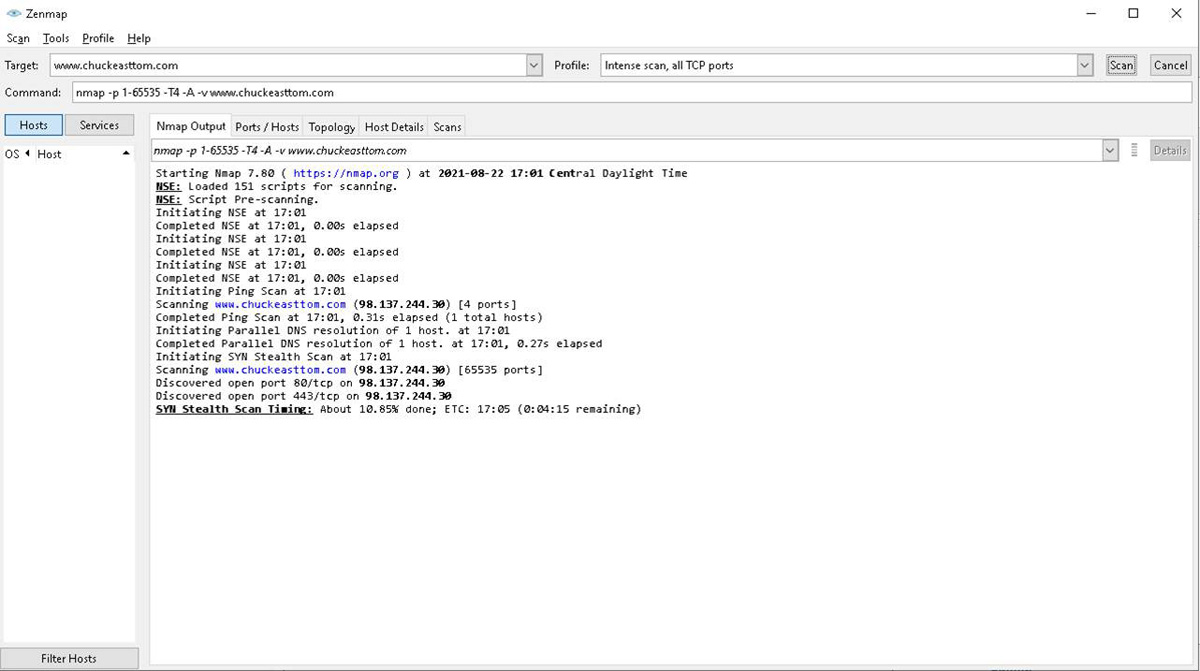
Figure 1.13 Zenmap Tool
While Nmap is the most commonly used scanning tool, there are other tools that the CEH exam may ask you about. A few of them are listed here:
• NetScanTools: https://www.netscantools.com
• hping: http://www.hping.org
• Ping Scanner Pro: https://ping-scanner-pro.soft112.com
• SuperScan: https://sectools.org/tool/superscan/
• Fing: https://www.fing.io (for mobile devices)
• IP Scanner: http://10base-t.com (for mobile devices)
• Visual Ping Tester: http://www.pingtester.net
• NetScanTools Pro: https://www.netscantools.com
• SolarWinds: http://www.solarwinds.com
hping
hping is a versatile tool that allows you to perform a number of different scans from the command line. A few examples of hping scans are shown here:
• hping3 -1 192.168.1.25 (ICMP ping)
• hping3 -2 192.168.1.25 -p 80 (UDP scan on port 80)
• hping3 -1 192.168.1.x--rand-dest -I eth0 (scan of a subnet for live hosts)
• hping3 -8 80-200 -S 192.168.1.25 -V (SYN scan of ports 80 to 200)
Commonly used hping flags include the following:
• -v --version: Show version
• -q -- quite: Quiet
• -I - Interface: Interface name
• --beep beep: For each matching packet
• -a --spoof: Spoof source address
• -t --ttl: Sets the Time to Live value, which by default is 64
• -f --frag: Splits packets into fragments
• -p --destpot: Destination port
• -F: FIN flag
• -S: SYN flag
• -A: ACK flag
• -R: Reset flag
• -U: Urgent flag
• -X: Xmas tree
hping also lets you spoof the source IP address. For example, hping3 www.chuckeasttom.com -a 182.10.10.10 uses the spoofed IP address 182.10.10.10 to scan www.chuckeasttom.com.
Banner Grabbing
Banner grabbing involves attempting to grab a banner, usually from a web server, to learn about that server. Active banner grabbing techniques open a TCP (or similar) connection between an origin host and a remote host. Passive banner grabbing involves trying to derive information from error messages, network traffic, web page extensions, and similar data. One simple way to try active banner grabbing is to use Telnet:
1. Enter telnet <IP Address> <Port 80> (for example, telnet 127.0.0.1 80) and then press Enter.
2. Enter HEAD /HTTP/1.0 and then press Enter twice.
Banner Grabbing Countermeasures
There are also several countermeasures to banner grabbing. Here are a few:
• If you are using Apache 2.x with the mod_headers module, you can use a directive in the httpd.conf file to change banner information. For example, in the header, you can set the server to a new server name.
• With Apache, you can change the ServerSignature line to ServerSignature Off in the httpd.conf file.
• You can display false banners to mislead or deceive attackers.
• You can use ServerMask (https://www.iis.net/downloads/community/2009/01/servermask) tools to disable or change banner information.
• You can turn off unnecessary services on the server to limit the information disclosure.
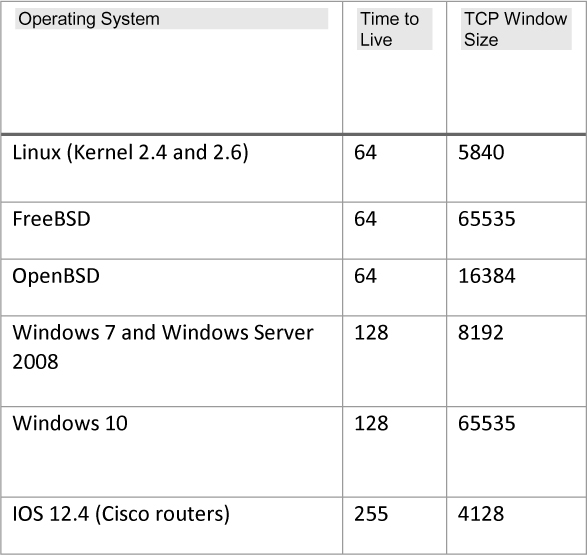
TTL and TCP Scanning
It is possible to identify the target operating system by examining the TTL and TCP window size in packets coming from a target. Some common TTL and TCP window size values are shown in Table 1.2.
Table 1.2 TTL Values and TCP Window Sizes for Different Operating Systems
TTL and TCP Countermeasures
The CEH exam expects you to know the general countermeasures to stop TTL and TCP probes. Some basic countermeasures are listed here:
• Filter all inbound ICMP messages at the firewalls and routers.
• Configure firewall and IDS rules to detect and block probes.
• Ensure that all router, IDS, and firewall firmware is updated to the latest release/version.
• Close all unused TCP/UDP ports.
• Check logs for signs that you have been under reconnaissance (e.g., logs from a security information and event management system).
Remember that the role of an ethical hacker is to make the target organization more secure. So, understanding countermeasures is an important part of being an ethical hacker.
Evading IDS/Firewall
One of the skills that is critical for an ethical hacker is the ability to evade firewalls and IDS. Testing evasion techniques is an important part of a penetration test.
Exam Alert
The CEH exam expect you to have general knowledge of firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS). This is part of the general basic networking knowledge that is considered prerequisite for the CEH exam.
One way to evade firewalls and IDS/IPS is to spoof an IP address. Many scans don’t work with IP spoofing because you are looking for a response from the target. If you spoof another IP address, the response to your scan will go to the spoofed IP address.
Fragmenting packets and having them reassembled after all fragments arrive can also obfuscate what is in the packets. This can be useful in evading firewalls and IDS/IPS. The Nmap tool allows you to fragment packets. Here is an example:
nmap -sS -T2 -A -f 192.168.1.51
This command does a SYN scan, with polite timing, in an attempt to detect services (-A) and fragment the packet.
Nmap also allows you to use a decoy address with the -D flag. You can either generate a random number of decoy addresses or specify them. The following example shows the generation of a random number of decoy addresses:
nmap -D RND:192.168.1.51
Another evasion technique is to connect via a proxy server. A proxy server is essentially an intermediary that your connections go through. There are many such tools available. Some are free, others have a minimal cost:
• Proxy Switcher: https://www.proxyswitcher.com
• Proxifier: https://www.proxifier.com
• HMA: https://www.hidemyass.com/en-us/index
Another option is to use Tor Browser. Tor is an acronym for The Onion Router. Onion routing essentially routes packets all around the world, bouncing them through proxy servers. Each packet is encrypted with multiple layers of encryption. Each proxy can decrypt only one layer and sends the packet to the next proxy. Someone who intercepts a packet in transit between two proxies can only determine the previous proxy and the next proxy—and not the origin or destination.
Tor was originally designed, implemented, and deployed as an onion routing project of the U.S. Naval Research Laboratory, for the primary purpose of protecting government communications. Tor Browser is a free tool that allows people to use the internet anonymously. It is actually a modified Firefox browser. Tor anonymizes the origin of your traffic.
What Next?
If you want more practice on this chapter's exam objectives before you move on, remember that you can access all of the Cram Quiz questions on the book web page. The next chapter covers enumeration and vulnerability scanning techniques in detail.
