CHAPTER 5
Microsoft Cybersecurity Reference Architecture and Capability Map
Introduction
Most organizations have several challenges in managing their IT environment, especially when managing a hybrid cloud environment that includes IaaS, PaaS, and SaaS services. Cybercriminals are also constantly evolving their techniques and tools and CISOs and cyber defenders are continuously deploying new security controls and technologies and adding new layers of security controls. As the number of technologies and connectivity increases, managing the integration, monitoring, and data flow becomes more complicated.
Prior to defining and designing a threat-hunting program, CISOs need to assess the existing capabilities, security controls, and tools, as well as understand the data flow and organization architecture.
This chapter focuses on the Microsoft Cybersecurity Reference Architecture (MCRA) to obtain a better understanding of the Microsoft Azure environment as well as its capabilities and security tools, dashboards, sensors, and log connectors, which help cyber defenders and threat hunters identify gaps and remediate security loopholes (configurations, patches, as well as people as the weakest link).
Microsoft Security Architecture versus the NIST Cybersecurity Framework (CSF)
The NIST Cybersecurity Framework (CSF) was originally published in February 2014 in response to Presidential Executive Order 13636, “Improving Critical Infrastructure Cybersecurity,” which called for the development of a voluntary framework to help organizations improve the cybersecurity, risk management, and resilience of their systems. NIST conferred with a broad range of partners from government, industry, and academia for over a year to build a consensus-based set of sound guidelines and practices.
While intended for adoption by the critical infrastructure sector, the foundational set of cybersecurity disciplines comprising the CSF have been supported by government and industry as a recommended baseline for use by any organization, regardless of its sector or size. Industry is increasingly referencing the CSF as a de facto cybersecurity standard.
In this chapter, we discuss how Microsoft 365 security solutions address each category within four NIST CSF core actions: Identify, Protect, Detect, and Respond. Regardless of the size of your business, this framework will guide you in deploying security solutions that are right for your organization.
This chapter will help you get started with your Microsoft 365 security solutions. It discusses how these products work together in the greater enterprise environment and provides insight into the most effective security scenarios you can enable for your organization.
In the later part of the chapter, we also discuss the overall Cybersecurity Reference Architecture from Microsoft.
The NIST Framework Core consists of five concurrent and continuous functions: Identify, Protect, Detect, Respond, and Recover. When considered together, these functions provide a high-level, strategic view of the lifecycle of an organization's management of cybersecurity risk.
Microsoft has aligned the security capabilities in Microsoft 365 to four of these core functions as shown in Figure 5.1.
Although Microsoft offers some guidance and tools to help with certain Recover functions (data backup and account recovery, for example), Microsoft 365 doesn't specifically address this function; it's covered under Azure services such as Azure Back Up and Azure Site Recovery.
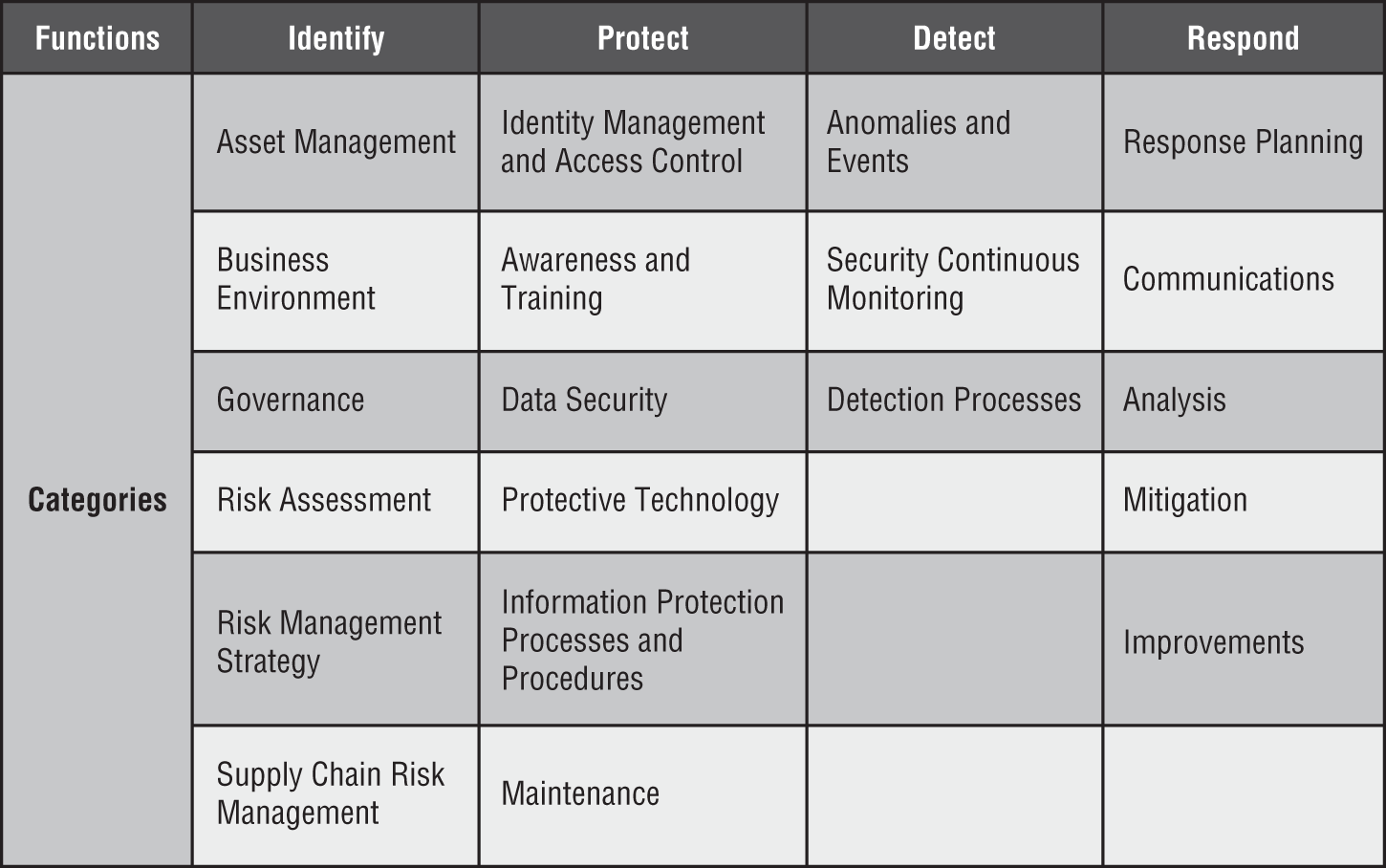
Figure 5.1: Microsoft 365 Security services aligned with NIST CSF
The Microsoft 365 security solutions philosophy is built on four pillars: Identity and Access Management, Threat Protection, Information Protection, and Security Management, as shown in Figure 5.2.
Microsoft Security Architecture
This section explores the Identify, Protect, Detect, Respond, and Recover functions attributed to Microsoft 365 Security solutions.
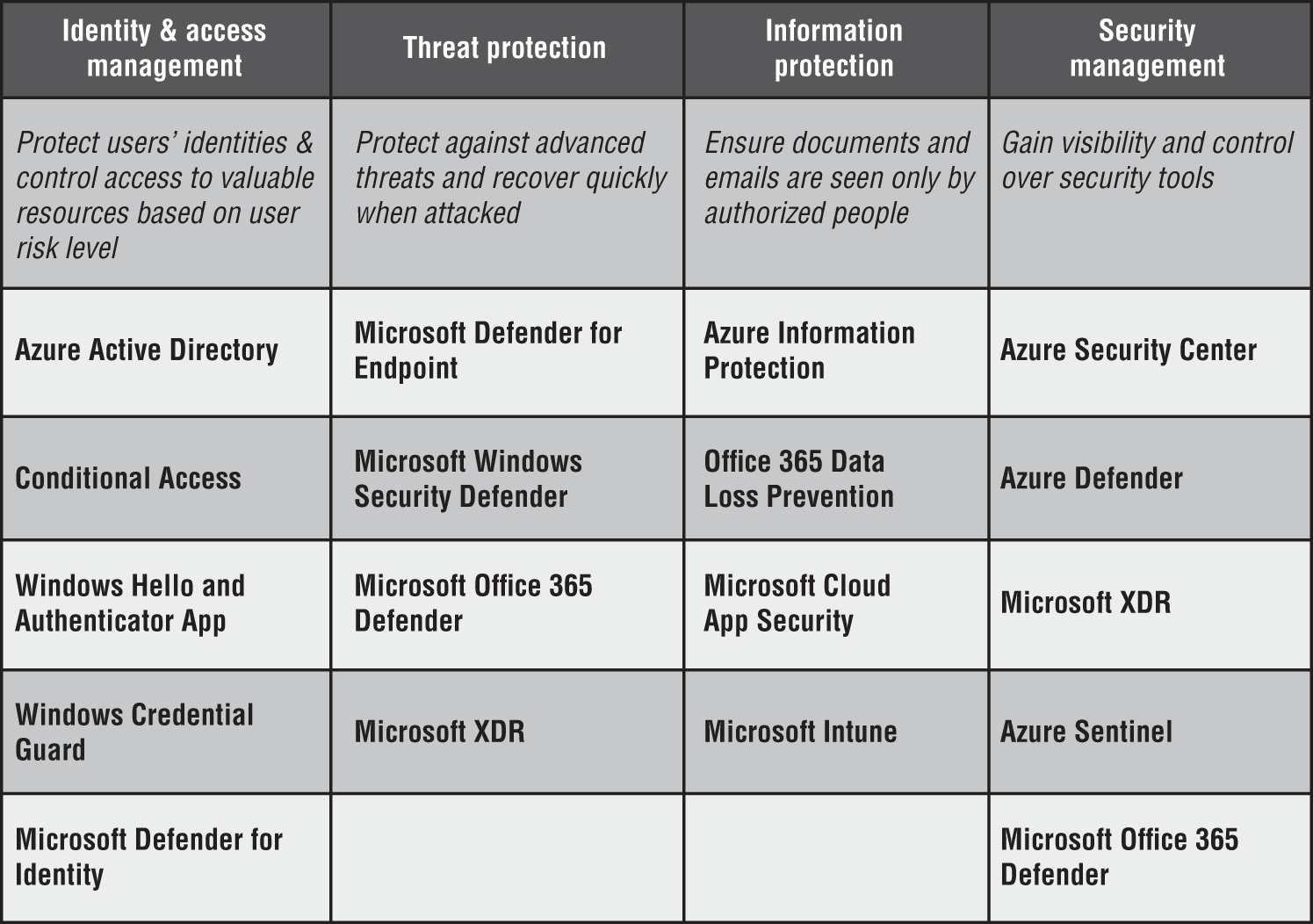
Figure 5.2: Microsoft 365 Security solutions
The Identify Function
This section addresses the six categories that comprise the Identify function: Asset Management, Business Environment, Governance, Risk Assessment, Risk Management Strategy, and Supply Chain Risk Management. They “develop an organizational understanding to manage cybersecurity risk to systems, people, assets, data, and capabilities.”
- Asset Management: Microsoft 365 security solutions help identify and manage key assets such as user identity, company data, PCs and mobile devices, and cloud apps used by company employees.
- Business Environment: Every business environment is different, and your users and organizational structure, mission, and leadership are also unique. You know best how to manage security technology within your business environment.
- Governance: Microsoft 365 security solutions include tools and resources to help you manage risk and meet regulatory, privacy, and operational (e.g., incident response) requirements.
- Risk Assessment: Capabilities in Microsoft 365 can help your organization understand cybersecurity risk related to your users, devices, apps, cloud services, and data through a variety of built-in tools and guidance. Microsoft is committed to ensuring that its customers have visibility into the risk assessments for their cloud services and provides guidance on a number of risk assessments of Microsoft cloud services.
- Risk Management Strategy: Using Microsoft 365 risk assessment capabilities can help your organization establish a risk management strategy. Microsoft can help you execute this strategy as it pertains to your priorities, constraints, risk tolerances, and assumptions. In addition, because security is an ongoing endeavor, Microsoft can help you decide on the fundamental steps that will have the most potent and lasting effect.
- Supply Chain Risk Management: The key example of supply chain risk management is Azure Active Directory business-to-business (B2B) collaboration, which enables any organization using Azure AD to work securely with users from any other organization, whether or not they use Azure AD.
The Protect Function
This section addresses the six categories that comprise the Protect function: Access Control, Awareness and Training, Data Security, Information Protection Processes and Procedures, Maintenance, and Protective Technology. The section also highlights Microsoft 365 solutions that you can leverage to align to this function.
- Identity Management, Authentication, and Access Control: The first safeguard against threats or attackers is to maintain strict, reliable, and appropriate access control. Your employees need to be able to reach the devices, apps, and data they need to be productive, balanced with the right level of access control. Microsoft 365 security solutions such as Azure AD Conditional Access can allow you to control access across devices, apps, and data.
- Awareness and Training: The organization's personnel and partners are provided cybersecurity awareness education and are trained to perform their cybersecurity-related duties and responsibilities consistent with related policies, procedures, and agreements. Microsoft's annual Digital Defense Report and Security Intelligence Reports are excellent sources of learning.
- Data Security: Microsoft 365 security solutions can help enable data protection in accordance with your organization's risk strategy. Through Microsoft 365 security solutions, data is controlled and protected at rest (e.g., in the cloud, server and workstation hard disk, shared drives, etc.), in use, and in transit. Bitlocker and Azure Information Protection (AIP) services help your organization with Data Security.
- Protective Technology: Technical security solutions are managed to ensure the security and resilience of systems and assets, consistent with related policies, procedures, and agreements. We discussed a number of protective services in the previous chapter. These services include Azure Conditional Access, MAS, Microsoft Defender, and Azure Information Protection.
- Information Protection Processes and Procedures: Security policies (that address purpose, scope, roles, responsibilities, management commitment, and coordination among organizational entities), processes, and procedures are maintained and used to manage protection of information systems and assets. Defining the security policies, processes, and procedures is an important step you will need to take to maintain the security management of your organization.
- Maintenance: To better protect an organization from threats and data breaches, attention must be paid to the vulnerabilities that may not be visible during maintenance and repairs of industrial control and information system components, such as devices and servers. Performing these maintenances and repairs securely and consistent with policies and procedures will protect organizational users, devices, apps, and data. Microsoft 365 can help you mitigate the potential threats.
The Detect Function
This section addresses the three categories that comprise the Detect function: Anomalies and Events, Security Continuous Monitoring, and Detection Processes. We summarize the key Microsoft 365 and Azure solutions that you can leverage to align to this function.
- Anomalies and Events: Many common types of threats target three key attack vectors: devices, email, and identity credentials. Microsoft 365 provides capabilities to detect attacks across these three attack areas. These solutions offer advanced threat protection, security and audit log management, and application whitelisting to ensure the security and resilience of systems and assets, consistent with related policies, procedures, and agreements.
- Security Continuous Monitoring: Microsoft 365 and Azure security solutions offer continuous monitoring, threat detection, vulnerability assessment, and event logging. Some of these services include Microsoft Defender for Endpoint, Microsoft 365 Defender, Azure Defender, MCAS, Azure Security Center, and Azure Sentinel SIEM.
- Detection Processes: The detection process is something an organization will be in charge of; Microsoft does take actions that help secure all organizations by adapting Assume Breach Strategy.
The Respond Function
This section addresses the five categories that comprise the Respond function: Response Planning, Communications, Analysis, Mitigations, and Improvements. We also summarize the key Microsoft 365 and Azure solutions that you can leverage to align to this function.
- Response Planning: Microsoft 365 security solutions can help an organization to plan a response to a threat, event, or security incident based on various visibility reports and insights. These services include Azure AD Access and usage report and Azure Defender.
- Communications: Educate your employees on security; whatever security tools you deploy to protect your company won't be effective if your employees don't use them properly or regularly. Ensure that all employees in your organization are aware of security threats and their role in protecting company assets.
- Analysis: Analysis is conducted to ensure adequate response and support recovery activities. Microsoft offers guidance and education on Windows security and forensics to allow organizations to investigate cybercriminal activity and more effectively respond and recover from malware incidents.
- Mitigation: Microsoft 365 security solutions provide tools to help with the incident response as part of an organization's risk mitigation strategy, including in-depth guides to respond to security IT incidents, whitepapers on how Microsoft responds to security incidents in Office 365, and built-in reports.
- Improvements: Using Microsoft 365 extensive reporting, logging, and insights, you'll be responsible for determining and implementing any improvements to your organization's security.
The Recover Function
This section addresses the three categories that comprise the Recover function: Recovery Planning, Improvements, and Communications. We also summarize the key Azure solutions that you can leverage to align to this function.
- Recovery Planning: Recovery processes and procedures are executed and maintained to ensure timely restoration of systems or assets affected by cybersecurity events. Azure Backup and Site Recovery are two such features that can help an organization with Recovery planning.
- Improvements: Recovery planning and processes are improved by incorporating lessons learned into future activities.
- Communications: Restoration activities are coordinated with internal and external parties, such as coordinating centers, Internet service providers, owners of attacking systems, victims, other CSIRTs, and vendors.
Using the Microsoft Reference Architecture
The Microsoft Cybersecurity Reference Architecture (MCRA) provides a single-page view of the various security solutions, which seamlessly work together in a highly integrated manner to drive simplicity and effectiveness. See Figure 5.3. The Reference Architecture can be used as a starting template for security architecture and for comparison of security capabilities. It also helps you understand the integration of different components in the Microsoft suite and their capabilities.
As organizations compete to migrate toward the cloud faster, poor architecture designs could open new loopholes and vulnerabilities. As a result, the demands of designing exhaustive architecture and integrating heterogeneous environments, especially hybrid clouds, are increasing.
MCRA describes Microsoft's cybersecurity capabilities and how they integrate with existing security architectures and capabilities.
MCRA covers M365 Security and Compliance Portal, Secure Score, MCAS (Microsoft Cloud Security Broker), Microsoft Defender and XDR, Microsoft Azure Defender, IoT and Operation Security, Security Operations, and People Security.
The entire Reference Architecture is built on some of the core foundations such as Microsoft Threat Intelligence, Microsoft Service Trust Portal (https://aka.ms/stp), Microsoft Security Development Lifecycle (SDL), GitHub Advance Security, and the Microsoft Security and Compliance Management Portal (see Figure 5.4).
Microsoft Threat Intelligence
Microsoft isn't the only company that invests in AI. However, Microsoft is in a unique position to create more powerful AI solutions. That's due in part to the massive volume and diversity of the signals they have access to, combined with their human expertise.
Like humans, intelligence requires expert guidance and data, or signals, to learn and get smarter. Microsoft analyzes trillions of signals with unparalleled diversity. These signals are collected from diversified sources and analyzed using AI and ML algorithms to get a unique insight into the various threats.
Across Microsoft platforms, billions of endpoints send anonymized telemetry from both the commercial and consumer worlds at multiple points up and down the stack. The data that Microsoft collects from the various sources passes through a strict privacy/compliance boundary to ensure that data is only being used in ways that their customers have agreed to. See Figure 5.5.
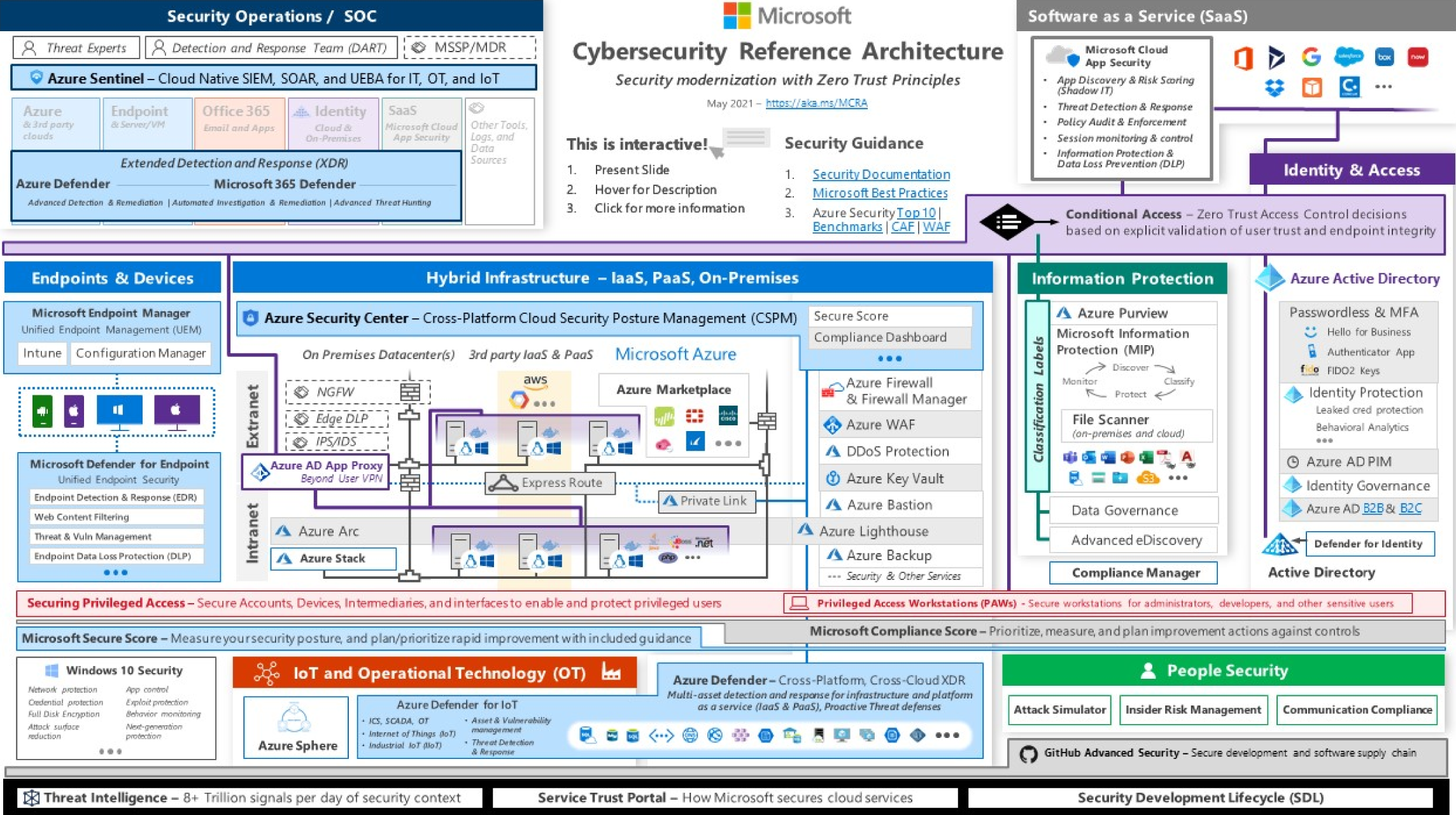
Figure 5.3: The Microsoft Cybersecurity Reference Architecture (MCRA)

Figure 5.4: Foundation of Microsoft Reference Architecture

Figure 5.5: Microsoft's Global threat activity portal
The data sources include the product noted earlier, specialized security sources, insights from dark markets (criminal forums), and learnings from incident response engagements where Microsoft helps customers with investigations and remediates incidents.
The data then goes through a collection and analysis phase to normalize it, apply various analytics to identify relevant security insights and findings, and publish to an internal API.
Each of the Microsoft products then accesses the data to provide findings, context, insight, etc., relative to that capability and then automatically feeds new detections and insights into the graph to enrich other product findings.
Additionally, human teams are constantly working with the graph to hunt for adversaries in various environments (Azure, Office 365, Microsoft IT, Windows ATP Customers, etc.) and creating, tuning, and validating new analytics to improve the overall detection.
Service Trust Portal
The Service Trust Portal contains details about Microsoft's implementation of controls and processes that protect your cloud services and the customer data therein. See Figure 5.6.
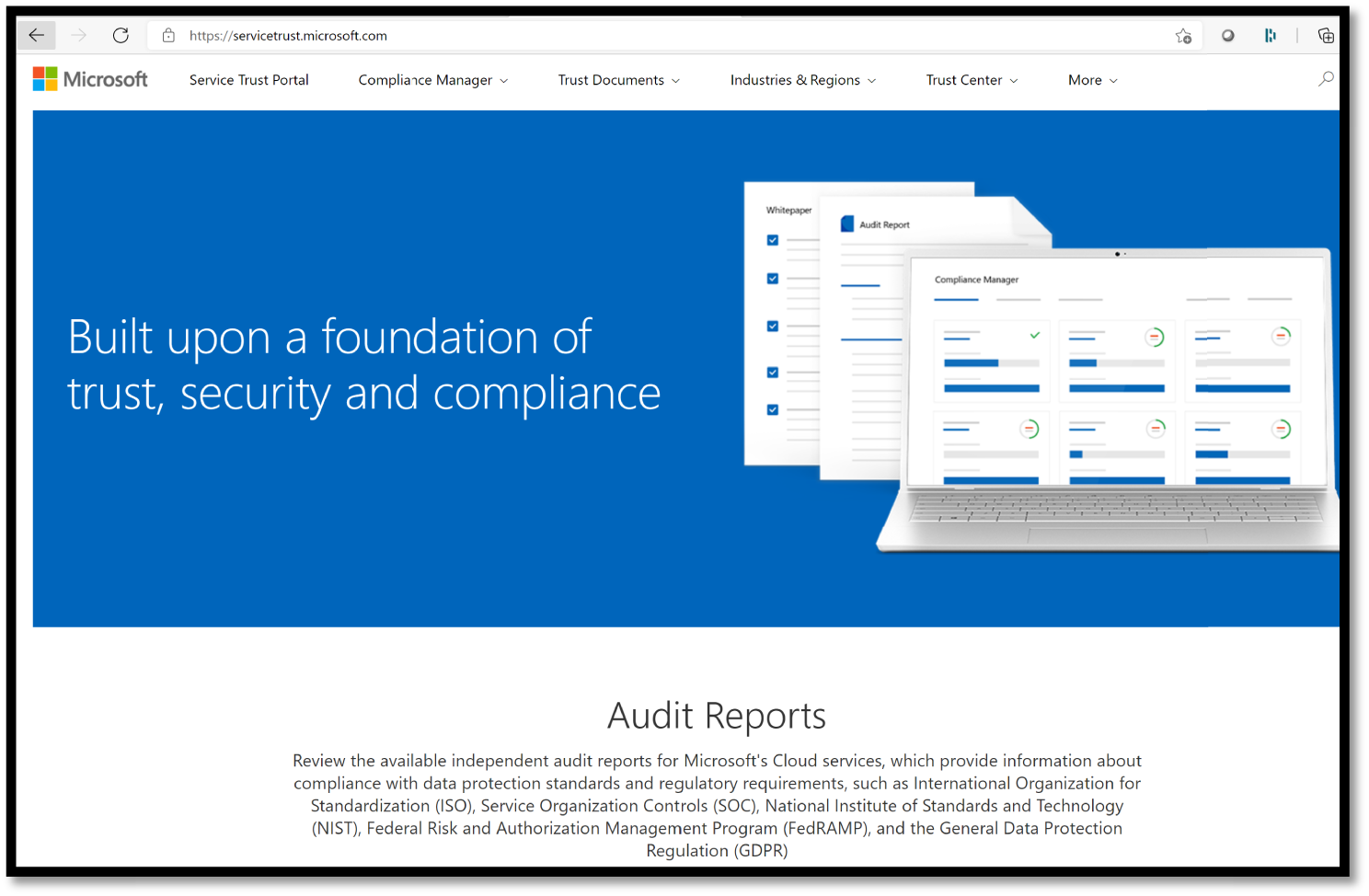
Figure 5.6: Service Trust Portal
To access some of the resources on the Service Trust Portal, you must log in as an authenticated user with your Microsoft cloud services account (either an Azure Active Directory organization account or a Microsoft Account) and review and accept the Microsoft Non-Disclosure Agreement for Compliance Materials.
Existing customers can access the Service Trust Portal at https://aka.ms/STP with one of the following online subscriptions (trial or paid): Microsoft 365, Dynamics 365, or Azure.
Security Development Lifecycle (SDL)
The Microsoft SDL introduces security and privacy considerations throughout all phases of the development process, helping developers build highly secure software, address security compliance requirements, and reduce development costs. See Figure 5.7.
The guidance, best practices, tools, and processes in the Microsoft SDL are practices that Microsoft uses internally for building more secure products and services. Microsoft has updated the SDL practices as a result of growing experience with new scenarios, like the cloud, Internet of Things (IoT), and artificial intelligence (AI). To learn more, visit https://www.microsoft.com/en-us/securityengineering/sdl/.

Figure 5.7: Microsoft SDL portal
Protecting the Hybrid Cloud Infrastructure
Microsoft invests deeply in Azure platform security. The hybrid infrastructure model and the cloud security/networking controls are new to many security professionals, and hence there are frequently inadvertent configuration errors that expose hosted resources on the cloud environment.
Today, most organizations operate a multi-platform environment with Windows and Linux servers in the datacenters, application containers, and many different generations of applications to protect. Most organizations started security with a core set of security capabilities at the network edge/egress points to protect extranet and intranet resources.
MSFT provides different controls and dashboards such as Microsoft Secure Score, Azure Security Center, aka Azure Defender, which will be briefly discussed in this section. See Figure 5.8.
Azure Marketplace
On Azure, Microsoft invested in Azure Marketplace to ensure customers have access to capabilities from popular vendors, often used by customers to extend existing on-premises controls to the cloud. Azure Marketplace integrates existing capabilities and skills, Privilege Management for protecting against high-impact attacks against the privilege accounts, Azure AD App Proxy to move beyond a user's VPN and connect users to on-premises applications from the cloud. See Figure 5.9.
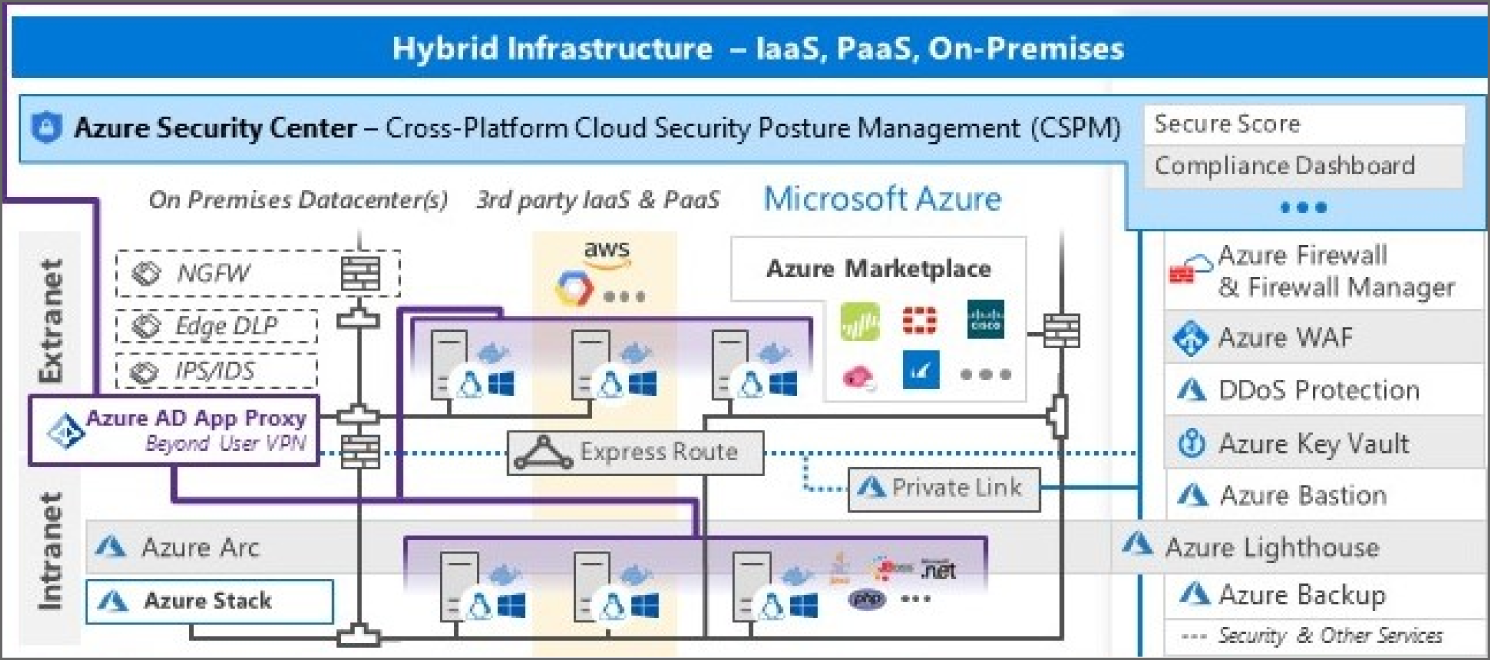
Figure 5.8: The Hybrid Infrastructure
Figure 5.9: Azure Marketplace portal
Private Link
Microsoft provides Private Link support for Azure Services to help organizations extend private networks to the PaaS services used by applications. Azure Private Link enables an organization to access Azure PaaS Services (for example, Azure Storage and SQL Database) and Azure-hosted customer-owned/partner services over a Private Endpoint in your virtual network.
Traffic between your virtual network and the service traverses over the Microsoft backbone network, eliminating exposure from the public Internet. An organization can also create their own Private Link Service within their virtual network and deliver it privately to their customers. See Figure 5.10.

Figure 5.10: Azure Private Link
While this extends current controls and practices to the cloud, private networks may not be enough to mitigate modern attacks so Microsoft recommends following Zero Trust principles (https://aka.ms/zerotrust) to modernize your access control strategy using identity, network, application, data, and other controls.
Azure Arc
Microsoft has invested in a wide range of capabilities to help secure your hybrid multi-cloud environment and the workloads in it. These are built into Azure and several extend across your hybrid infrastructure estate (on-premises, AWS, GCP, and other clouds) using Azure Arc. See Figure 5.11.
Figure 5.11: Azure Arc dashboard
Azure Arc simplifies governance and management by delivering a consistent multi-cloud and on-premises management platform. Azure Arc enables an organization to:
- Manage the entire environment, with a single pane of glass, by projecting your existing non-Azure, on-premises, or other-cloud resources into Azure Resource Manager.
- Manage virtual machines, Kubernetes clusters, and databases as if they are running in Azure.
- Use familiar Azure services and management capabilities, regardless of where they live.
- Continue using traditional ITOps, while introducing DevOps practices to support new cloud native patterns in your environment.
- Configure Custom Locations as an abstraction layer on top of Azure Arc–enabled Kubernetes cluster, cluster connect, and cluster extensions.
Azure Lighthouse
Azure Lighthouse provides cross-tenant support in Azure for services, often used by managed service providers and customers with multiple tenants. See Figure 5.12.
Figure 5.12: Azure Lighthouse portal
With Azure Lighthouse, service providers can deliver managed services using comprehensive and robust management tooling built into the Azure platform. As a result, customers maintain control over who can access their tenants, which resources they can access, and what actions can be taken. This service can also benefit enterprise IT organizations managing resources across multiple tenants. See Figure 5.13.
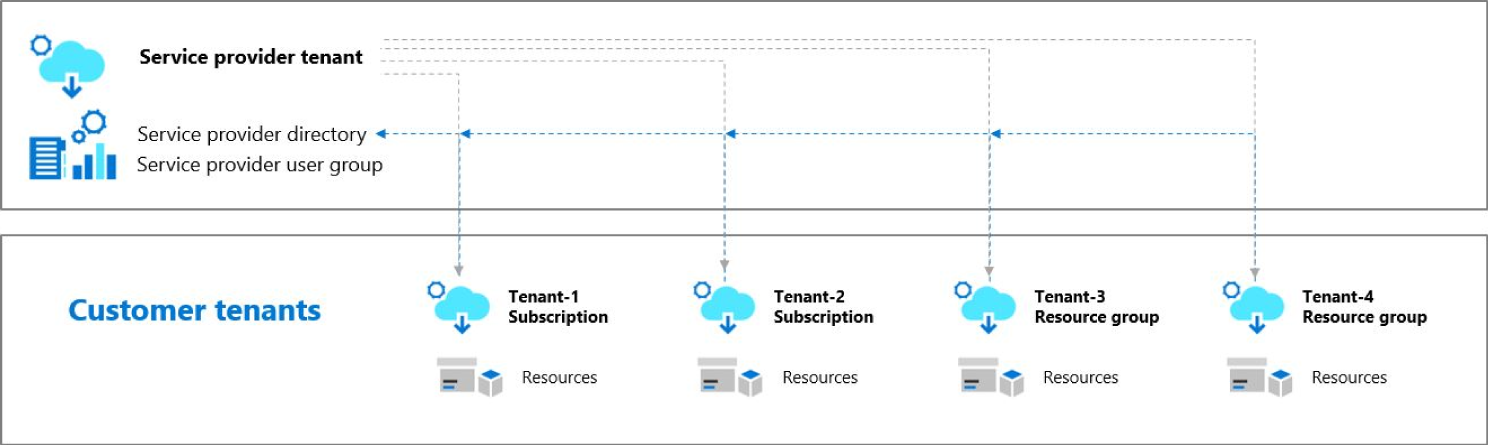
Figure 5.13: Azure Lighthouse architecture
Azure Firewall
Azure Firewall is a managed, cloud-based network security service that helps protect your Azure Virtual Network resources. See Figure 5.14.
- Azure Firewall Premium: A next-generation firewall with capabilities required for highly sensitive and regulated environments (TLS Inspection, IDPS, URL Filtering, Web Categories).
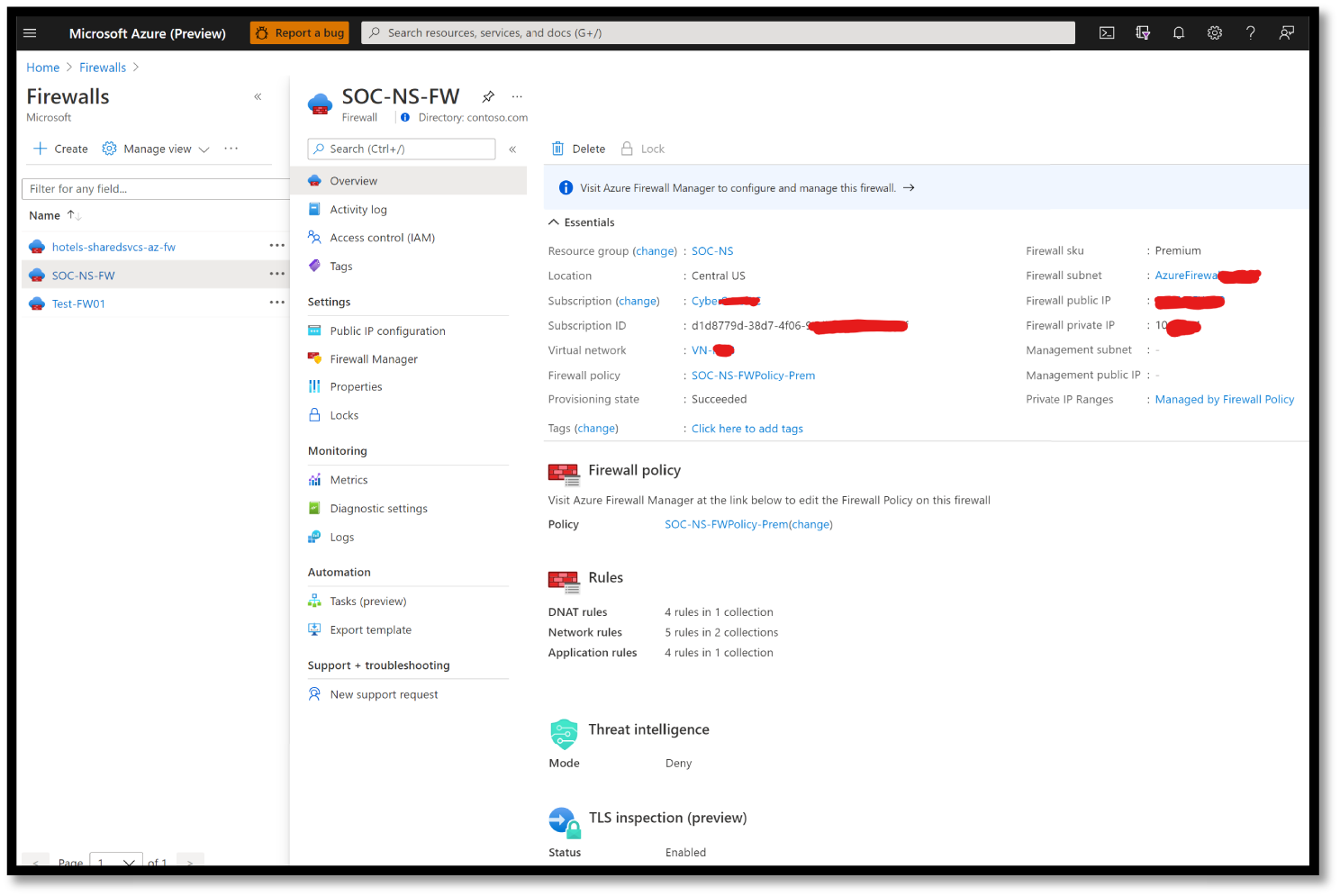
Figure 5.14: Azure Firewall
- Azure Firewall Manager: A security management service that provides central security policy and route management for cloud-based security perimeters. See Figure 5.15.
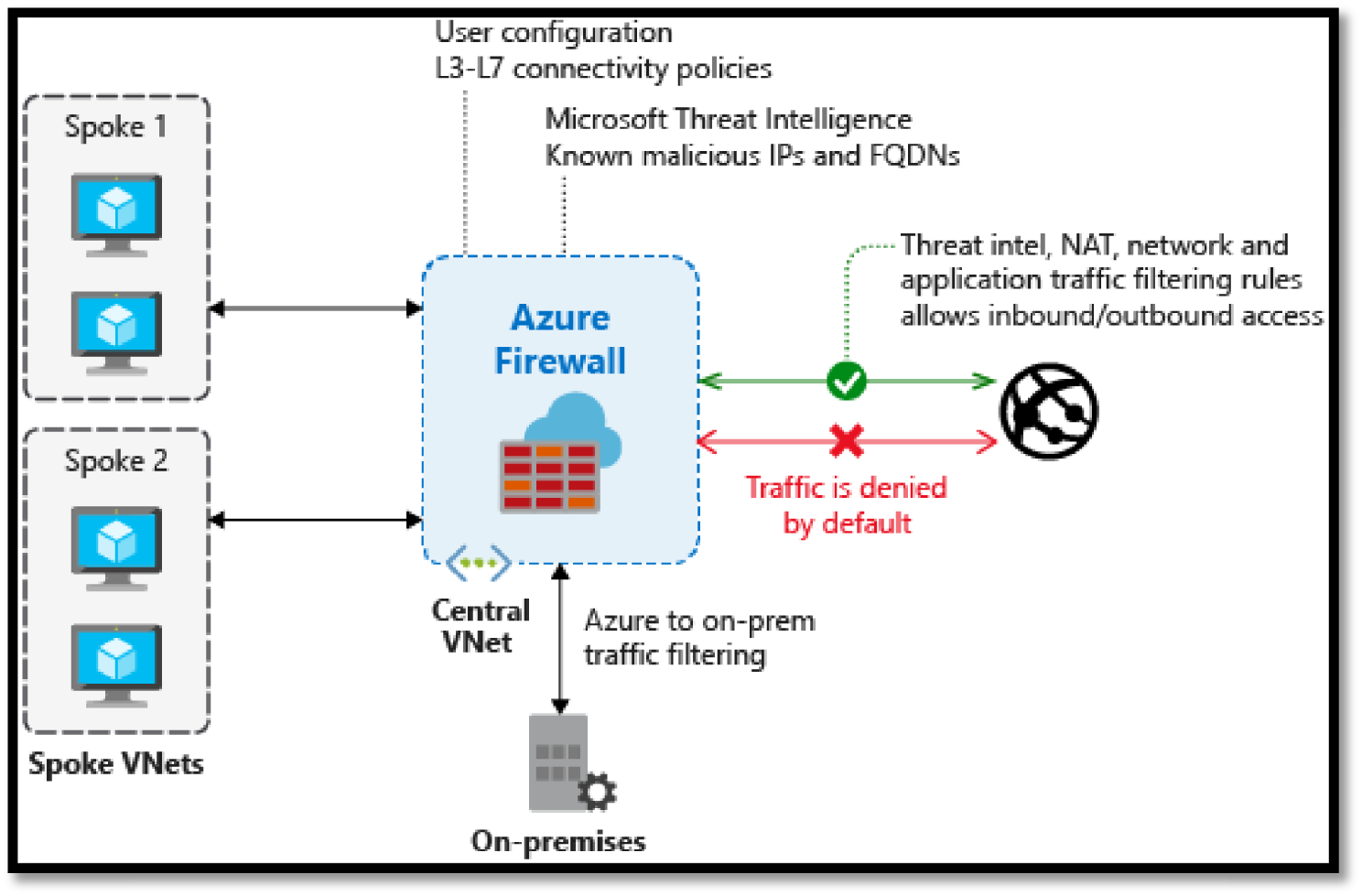
Figure 5.15: Azure Firewall architecture
Azure Web Application Firewall (WAF)
Azure WAF provides centralized protection of your web applications from common exploits and vulnerabilities. WAF on Application Gateway is based on Core Rule Set (CRS) 3.1, 3.0, or 2.2.9 from the Open Web Application Security Project (OWASP).
The WAF automatically updates to include protection against new vulnerabilities, with no additional configuration needed. WAF allows you to create separate policies for each site behind an organization's Application Gateway. See Figure 5.16.
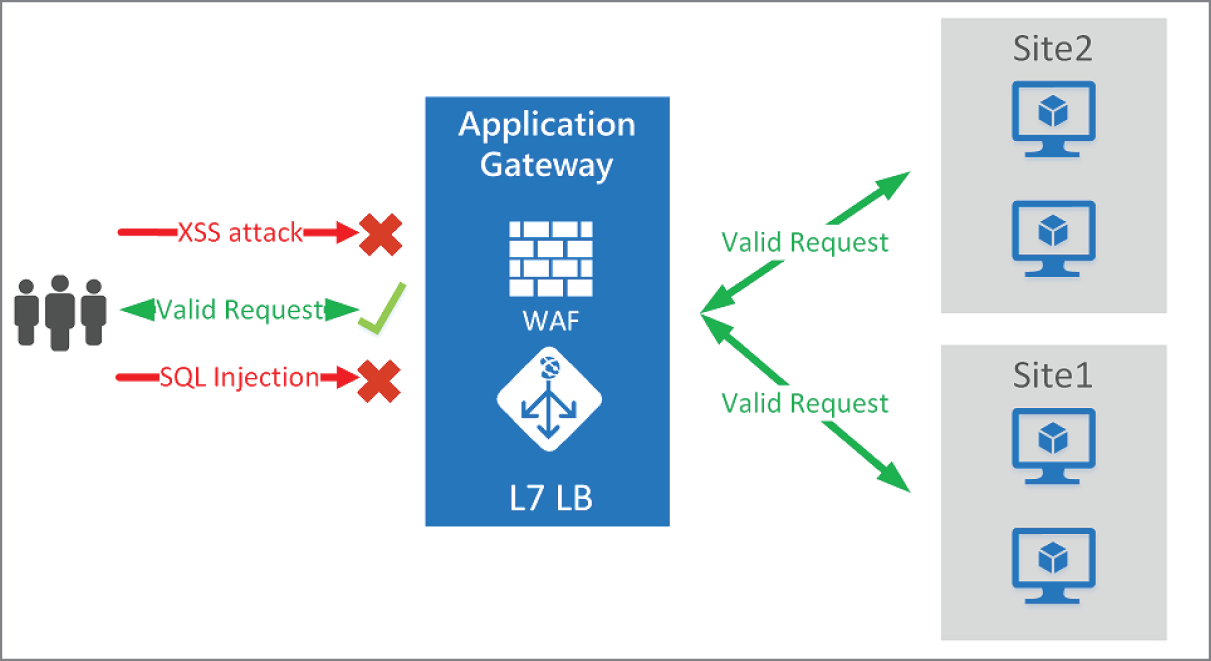
Figure 5.16: WAF design
Azure DDOS Protection
Every property in Azure is protected by Azure's infrastructure DDoS (Basic) Protection at no additional cost. The scale and capacity of the globally deployed Azure network provide defense against common network layer attacks through always-on traffic monitoring and real-time mitigation. See Figure 5.17.
DDoS Protection Basic requires no user configuration or application changes. DDoS Protection Basic helps protect all Azure services, including PaaS services like Azure DNS.
Azure DDoS Protection Standard, combined with application design best practices, provides enhanced DDoS mitigation features to defend against DDoS attacks. It is automatically tuned to help protect your specific Azure resources in a virtual network. See Figure 5.18.
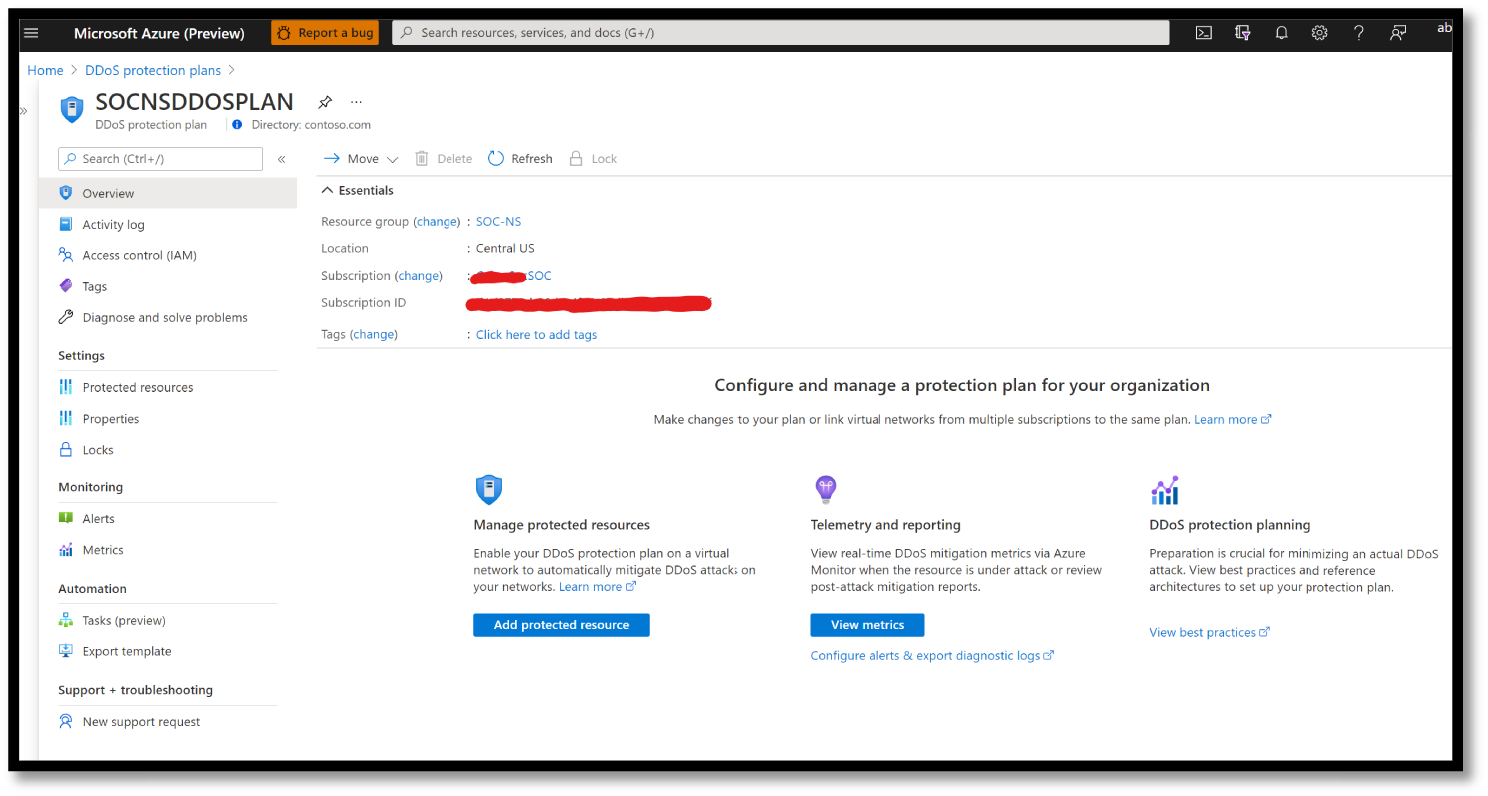
Figure 5.17: DDOS Plan dashboard
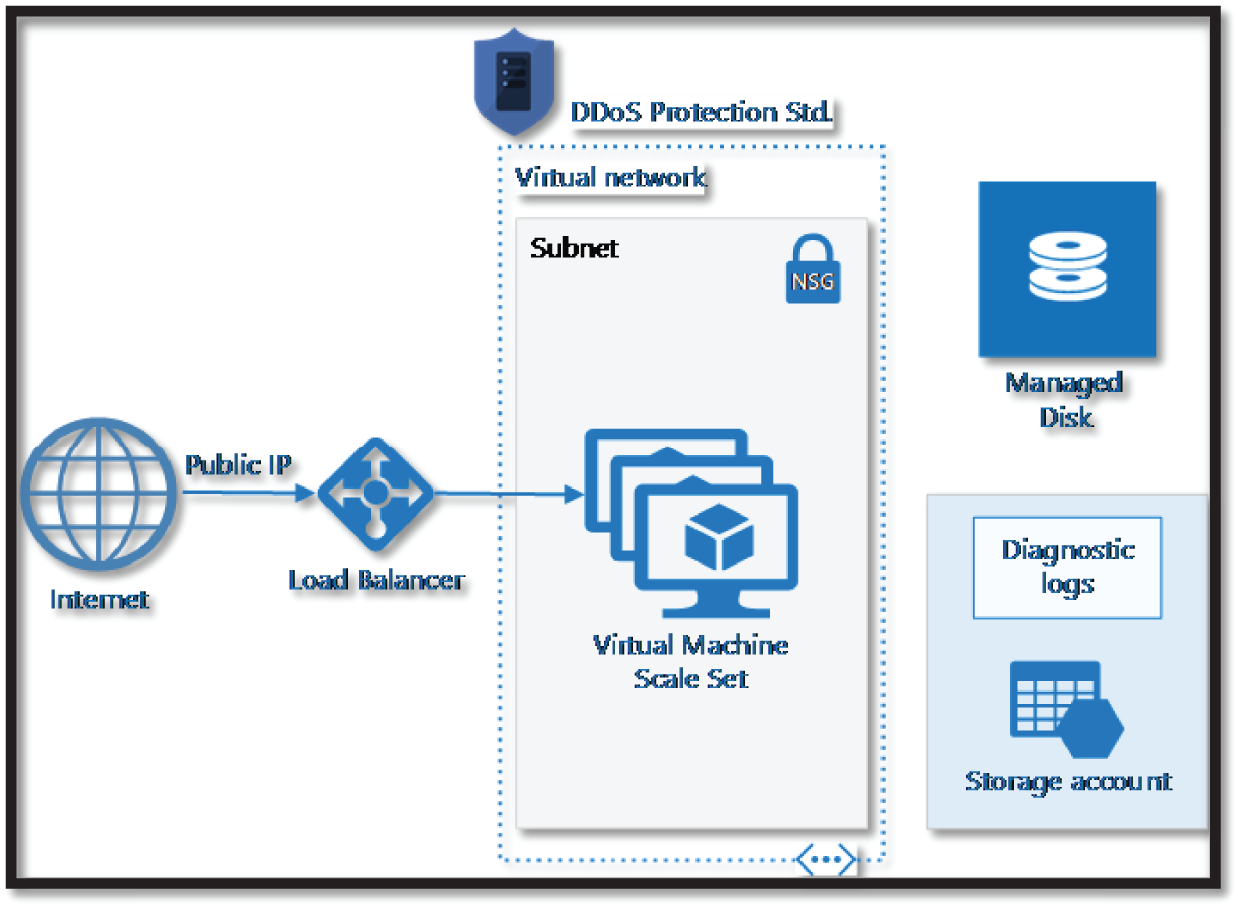
Figure 5.18: DDOS Protection Architecture
Azure Key Vault
Microsoft offers Azure Key Vault with two service tiers: Standard, which encrypts with a software key, and a Premium tier, which includes Hardware Security Module (HSM)–protected keys. See Figure 5.19.

Figure 5.19: Azure Key Vault portal
Azure Key Vault can help an organization with the following problems:
- Secrets Management: Azure Key Vault can be used to securely store and tightly control access to tokens, passwords, certificates, API keys, and other secrets.
- Key Management: Azure Key Vault can also be used as a Key Management solution. Azure Key Vault makes it easy to create and control the encryption keys used to encrypt your data.
- Certificate Management: Azure Key Vault is also a service that lets you easily enroll, manage, and deploy public and private Transport Layer Security/Secure Sockets Layer (TLS/SSL) certificates for use with Azure and your internal connected resources.
Azure Bastion
Azure Bastion is a service that an organization can deploy to let their employees or contractors connect to a virtual machine using your browser and the Azure portal. The Azure Bastion service is a fully platform-managed PaaS service that you provision inside your virtual network. See Figure 5.20.

Figure 5.20: Example of Azure Bastion for Firewall
Azure Bastion provides secure and seamless RDP/SSH connectivity to your virtual machines directly from the Azure portal over TLS. When you connect via Azure Bastion, your virtual machines do not need a public IP address, agent, or special client software. Figure 5.21 shows the architecture of an Azure Bastion deployment.

Figure 5.21: Azure Bastion architecture
The Bastion host in Figure 5.21 is deployed in the virtual network containing the AzureBastionSubnet subnet with a minimum /27 prefix.
- The user connects to the Azure portal using any HTML5 browser.
- The user selects the virtual machine to connect to.
- With a single click, the RDP/SSH session opens in the browser.
- No public IP is required on the Azure VM.
Azure Site Recovery
Using Azure Recovery, an organization can set up an Azure Site Recovery by simply replicating an Azure VM to a different Azure region directly from the Azure portal.
As a fully integrated offering, Site Recovery is automatically updated with new Azure features as they're released. An organization can minimize recovery issues by sequencing the order of multi-tier applications running on multiple virtual machines. It also ensures compliance by testing your disaster recovery plan without impacting production workloads or end users. And it keeps applications available during outages with automatic recovery from on-premises to Azure or Azure to another Azure region. See Figure 5.22.
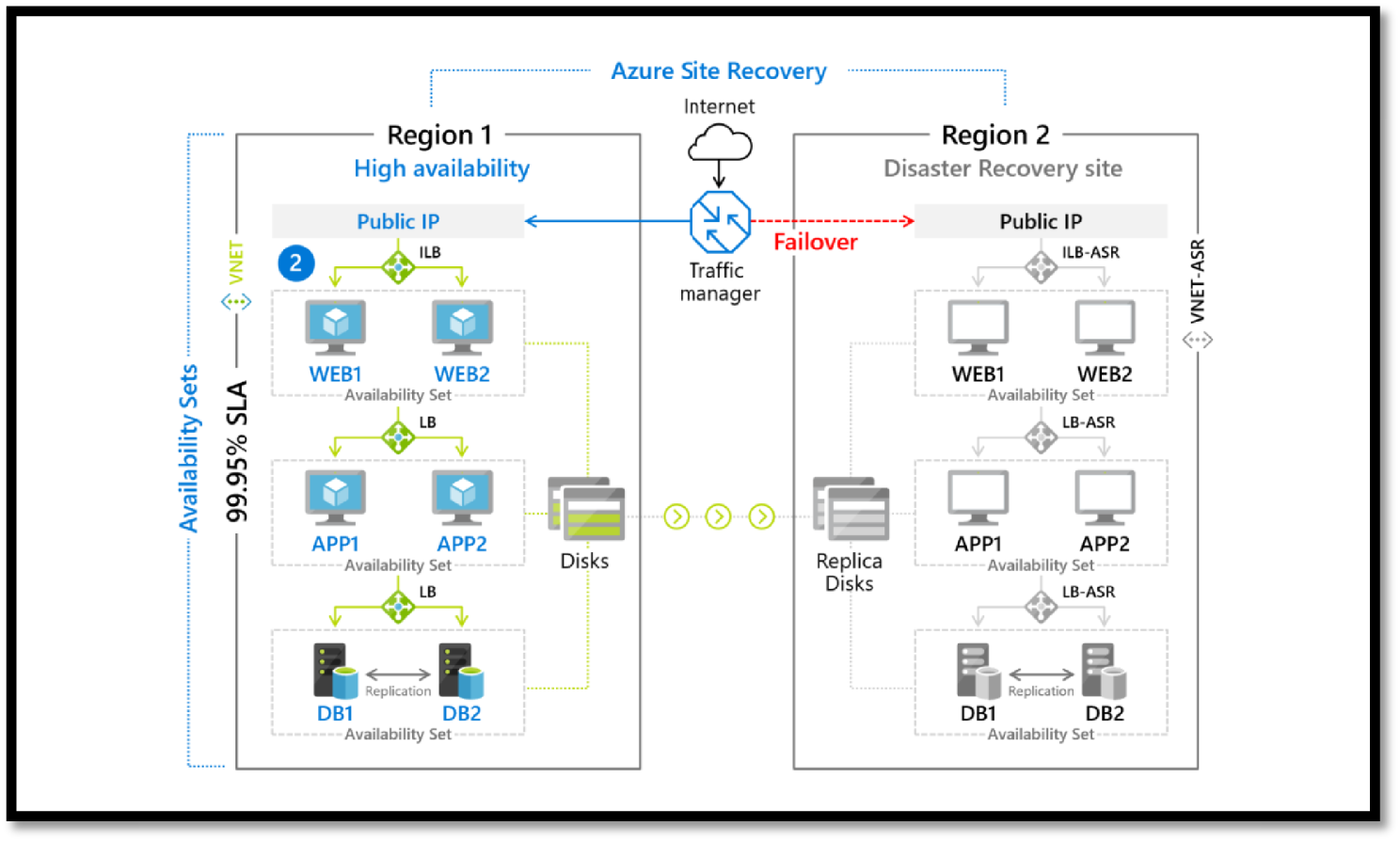
Figure 5.22: Azure Site Recovery
Azure Security Center (ASC)
ASC (see Figure 5.23) Microsoft Azure Defender (formerly known as Azure Security Center (ASC), not only helps organizations against distributed denial of service (DDoS), key management, ransomware-resistant backup archives, and confidential computing capabilities to protect data while it's being processed, but also is one of the key tools required to identify gaps and deficiencies and guide defender teams on how to remediate those issues in their cloud environment.
Azure Defender allows you to:
- Protect servers and workloads across multi-cloud (Amazon and Google Cloud) and on-premises datacenters.
- Perform vulnerability assessments.
- Detect and correct common misconfiguration issues such as
- VMs exposed directly to the Internet
- Missing Web Application Firewalls (WAFs) for web applications
- Out-of-date patches and anti-malware signatures and many others
- Leverage cutting-edge capabilities in Azure like machine learning to suggest firewall rules and application whitelists (to allow/block which files can run on servers).
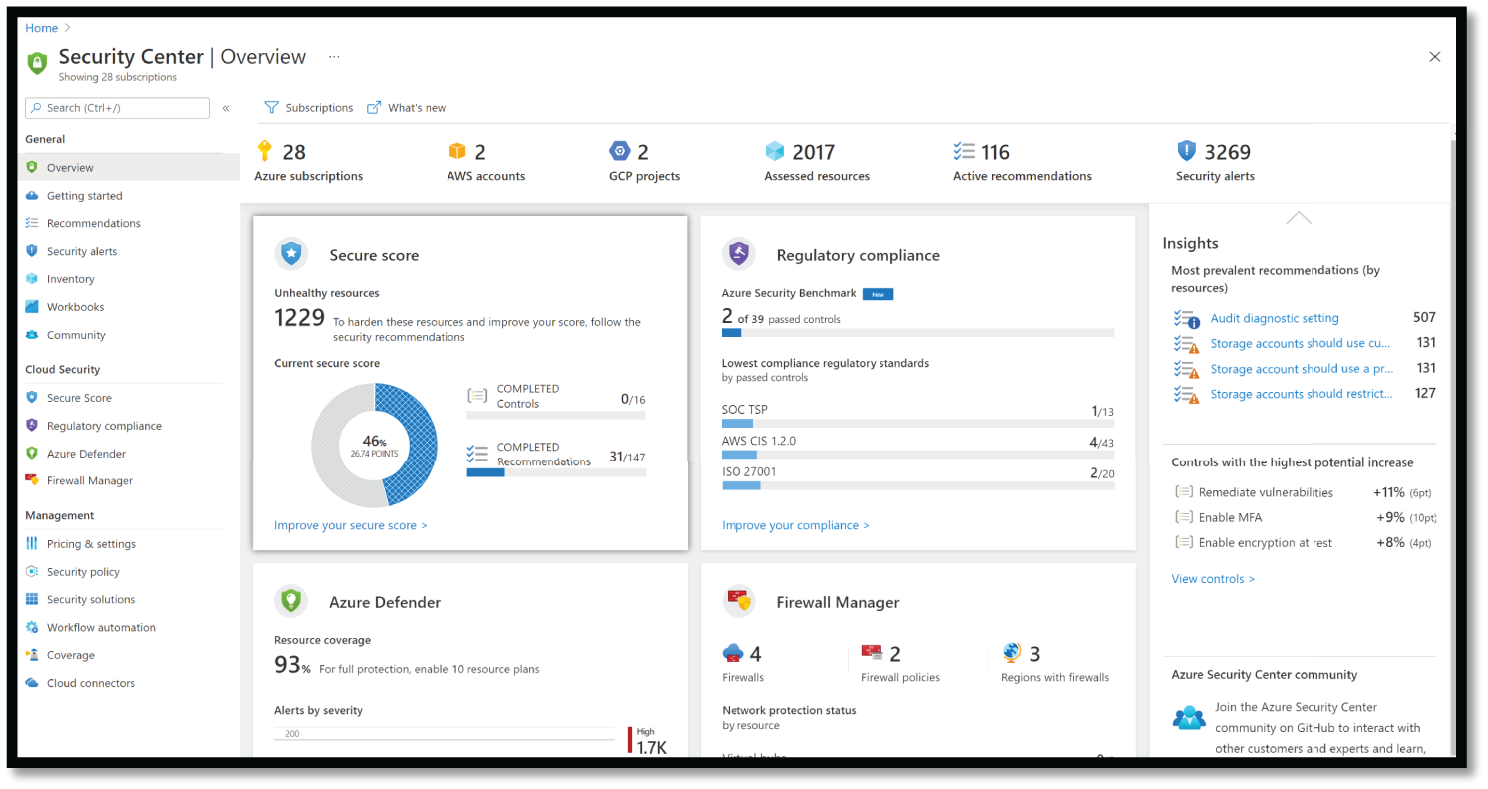
Figure 5.23: Azure Security Center (Azure Defender), view from the Azure portal
Microsoft Azure Secure Score
Microsoft Azure Secure Score (see Figure 5.24) is part of Azure Defender. It gives you reports on the deficiencies within the environment and the actions you may take to improve the environment. It also provides you with a list of tasks based on the impact and efforts needed to address the environment's gaps. It provides a granular level of information that is required for further understanding and investigation.
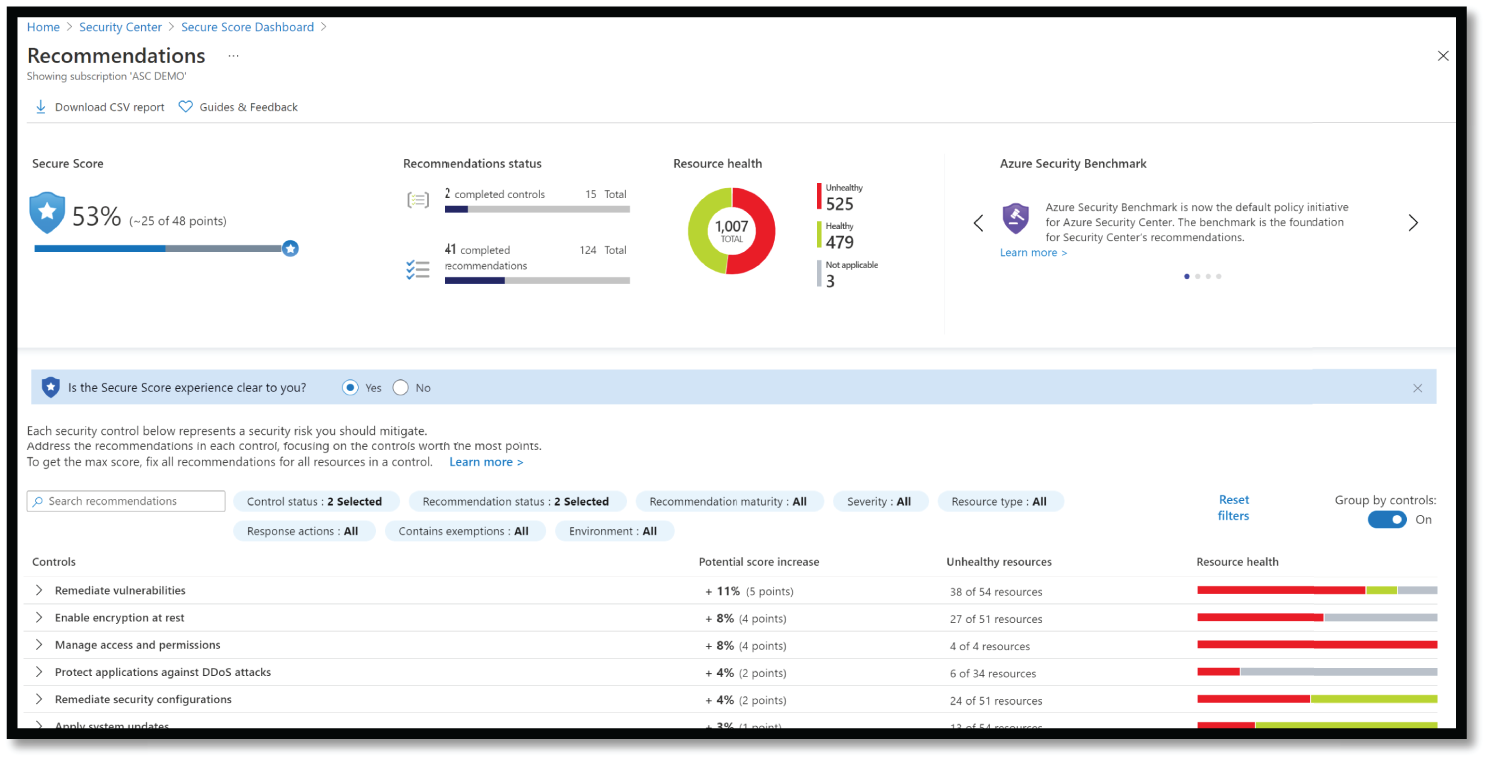
Figure 5.24: Azure Secure Score
Protecting Endpoints and Clients
Managing risk, health, and compliance across a broad spectrum of device platforms and ownership (BYODs, corporate devices, Macs, as well as unmanaged and mobile devices) is one of the most important priorities of the security and IT team (see Figure 5.25).
Many organizations take advantage of built-in Windows features and system management to provide basic security hygiene like patching and Active Directory account security and group policy.

Figure 5.25: Microsoft Endpoint Manager
Microsoft Endpoint Manager (MEM) Configuration Manager
Microsoft provides cross-platform security, multi-cloud, and management (for Windows, Linux, Mac, iOS, and Android) using a single management portal, found at https://endpoint.microsoft.com. See Figure 5.26.

Figure 5.26: Microsoft Endpoint Manager Center
For the Endpoint Protection Platform (EPP) and Endpoint Detection and Response (EDR), Microsoft uses Microsoft Defender for Endpoint (see Figure 5.27).

Figure 5.27: Microsoft Defender for Endpoint
Microsoft Defender for Endpoint is a holistic, cloud-delivered endpoint security solution that includes risk-based vulnerability management and assessment, attack surface reduction, behavioral-based and cloud-powered next-generation protection, endpoint detection and response (EDR), automatic investigation and remediation, and managed hunting services.
These capabilities are underscored with APIs that enable access and integration with the platform. Microsoft Defender for Endpoint is easily deployed, configured, and managed with a unified security management experience.
Microsoft Intune
Microsoft Intune (formerly Windows Intune) is a Microsoft cloud-based management solution for mobile device and operating system management. It aims to provide Unified Endpoint Management of both corporate and Bring Your Own Device (BYOD) devices in a way that protects corporate data.
You control how your organization's devices are used, including mobile phones, tablets, and laptops. You can also configure specific policies to manage applications. For example, you can prevent emails from being sent to people outside your organization. See Figure 5.28.

Figure 5.28: Intune architecture
Intune also allows people in your organization to use their personal devices for school or work. On personal devices, Intune helps make sure your organization's data stays protected and can isolate organization data from personal data.
Windows 10 Security includes an extensive set of platform capabilities and hardware security integrations to protect against ever-evolving attacks (see Figure 5.29).
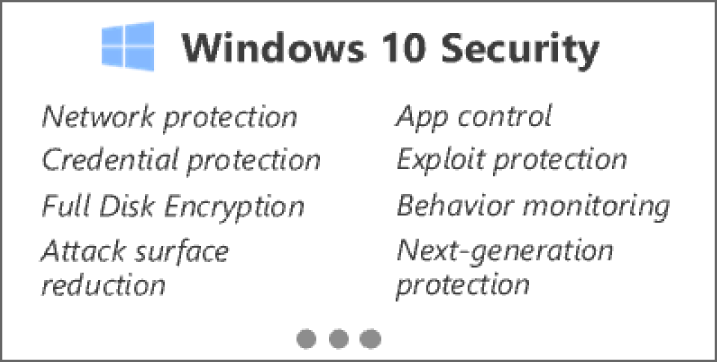
Figure 5.29: Windows 10 Security
Protecting Identities and Access
Microsoft is taking a comprehensive approach to secure identities against the full range of threats and risks (see Figure 5.30).
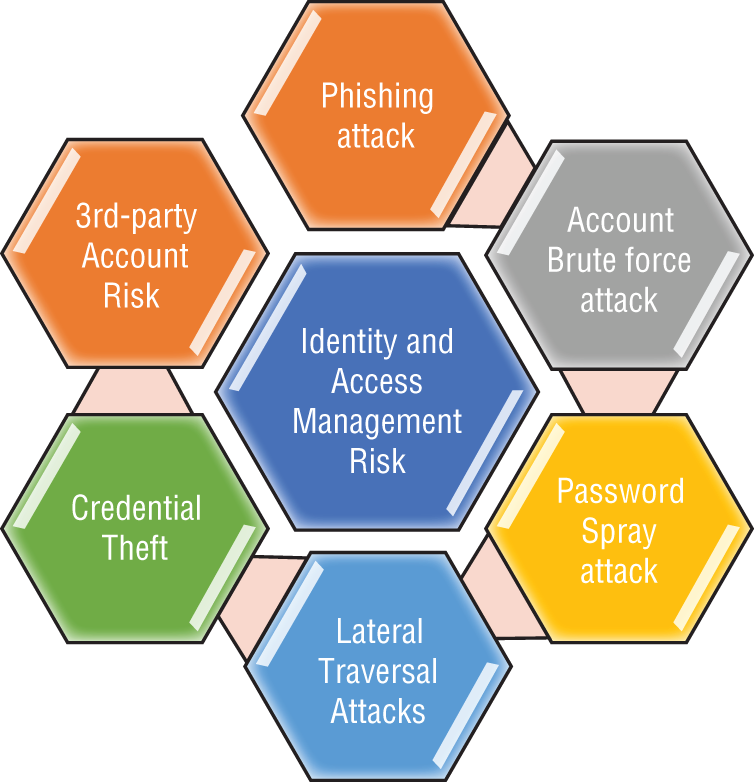
Figure 5.30: Threat and risk against identities and access
Microsoft's top services for identity protection include Azure Active Directory, Multi-Factor Authentication, Conditional Access, Azure AD Privilege Identity Management, Defender for Identity, Azure AD B2B and B2C services, and Identity Governance (see Figure 5.31).
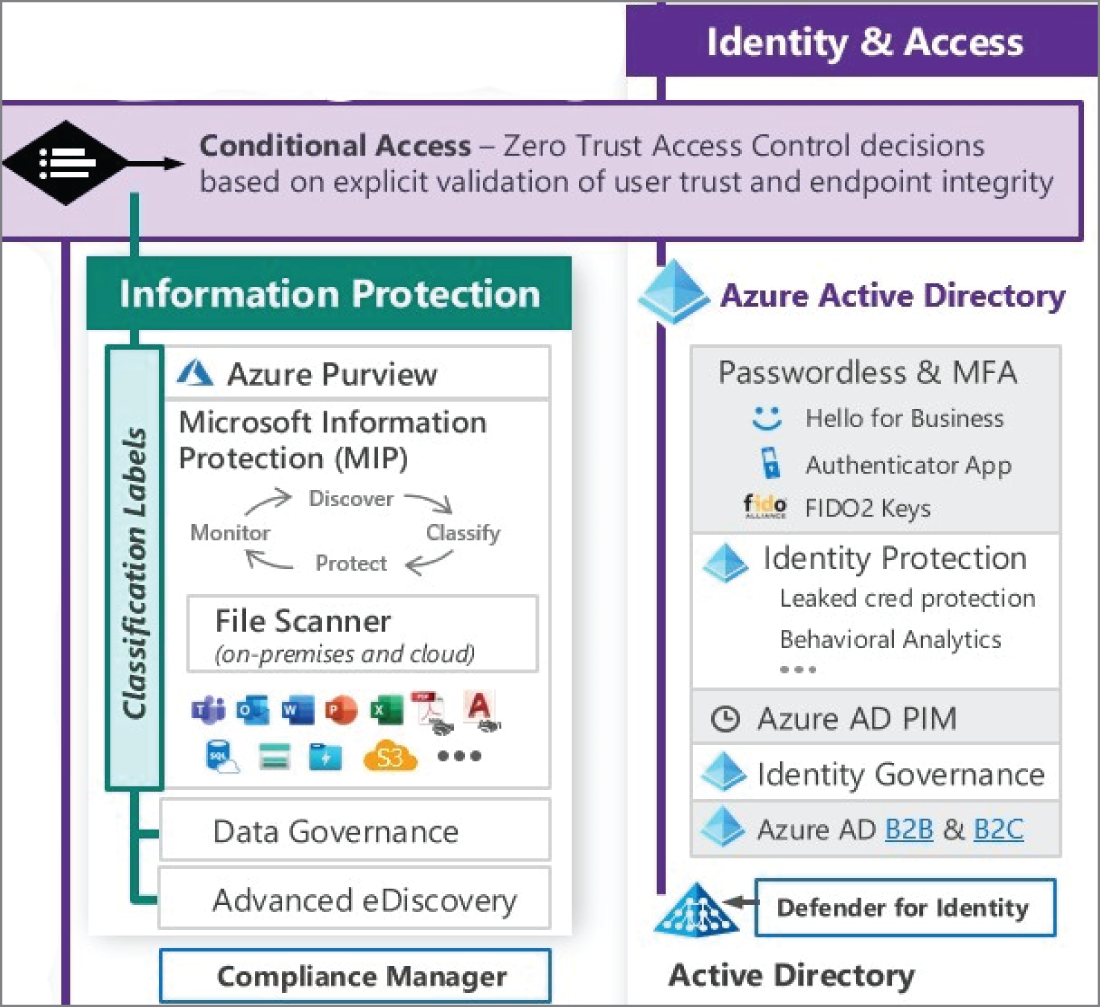
Figure 5.31: Identity and Access Management
Azure AD Conditional Access
Conditional Access applies Zero Trust principles to access control decisions by explicitly validating users’ trust and endpoints requesting access to your resources. This helps build a de facto security perimeter around these modern resources with modern controls and provides simple, consistent policy enforcement across them. See Figure 5.32.
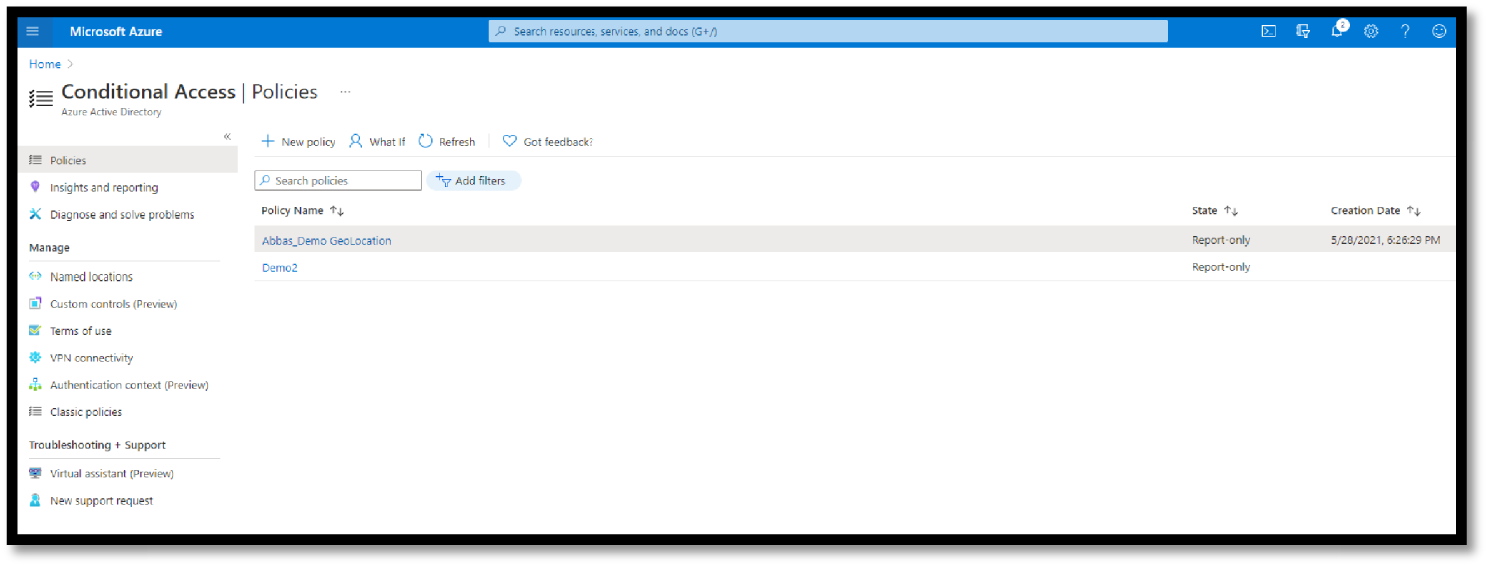
Figure 5.32: Azure Conditional Access Policies example
Policies have some of the most powerful capabilities within Azure Active. And you can scope these policies to meet just about any scenario required, including (or excluding) users/groups, apps, and other conditions such as risk, device platform and state, locations, and client application (browser, mobile, and desktop).
Passwordless for End-to-End Secure Identity
The Microsoft Authenticator app can be used to sign in to any Azure AD account without using a password. Microsoft Authenticator uses key-based authentication to enable a user credential that is tied to a device, where the device uses a PIN or biometric. Windows Hello for Business uses similar technology.
Windows Hello addresses the following problems with passwords:
- Strong passwords can be difficult to remember, and users often reuse passwords on multiple sites.
- Server breaches can expose symmetric network credentials (passwords).
- Passwords are subject to replay attacks.
- Users can inadvertently expose their passwords due to phishing attacks.
Azure Active Directory (aka Azure AD)
A fully managed multi-tenant service from Microsoft offers identity and access capabilities for applications running in Microsoft Azure and for applications running in an on-premises environment. Its name leads some to make incorrect conclusions about what Azure AD is. Therefore, to avoid any confusion with Windows Server Active Directory that you may already be familiar with in an on-premises environment, understand that Azure AD is not Windows Server Active Directory running on Virtual Machines in Microsoft Azure.
Azure AD is not a replacement for Windows Server Active Directory. If you already have an on-premises directory, it can be extended to the cloud using the directory integration capabilities of Azure AD. In these scenarios, users and groups on the on-premises directory are synced to Azure AD using a tool such as Azure Active Directory Sync (AAD Sync).
Azure MFA
Today, many organizations use on-premises multi-factor authentication systems to protect mission-critical data in their file servers and their critical Line of Business (LOB) applications. However, as these workloads (or parts of them) move to the cloud (at least in a hybrid manner), they need an effective and easy-to-use solution in the cloud for protection.
Microsoft published a whitepaper at https://www.microsoft.com/en-us/download/details.aspx?id=39052 describing in depth how these workloads (or parts of them) move to the cloud (at least in a hybrid manner) in an effective and easy-to-use solution.
Azure Active Directory Identity Protection
One of Microsoft's benefits of having numerous clients utilizing its services is that Microsoft can use this information from those clients and apply some genuine machine learning on the information that comes from Azure AD, Microsoft accounts, and even Xbox services. See Figure 5.33.
Identity Protection allows organizations to accomplish three key tasks:
- Automate the detection and remediation of identity-based risks.
- Investigate risks using data in the portal.
- Export risk detection data to third-party utilities for further analysis.

Figure 5.33: Azure AD Identity Protection portal
Identity Protection uses Microsoft's learnings from their position in organizations with Azure AD, the consumer space with Microsoft Accounts, and in gaming with Xbox to protect your users. Microsoft analyzes over 8 trillion signals per day to identify and protect customers from threats.
The signals generated by and fed to Identity Protection can be further fed into tools like Conditional Access to make access decisions, or fed back to a Security Information and Event Management (SIEM) tool for further investigation based on your organization's enforced policies.
Azure Active Directory Privilege Identity Management (PIM)
Privileged Identity Management provides time-based and approval-based role activation to mitigate the risks of excessive, unnecessary, or misused access permissions on resources that you care about. It gives limited and secure admittance to clients or gatherings to certain Azure assets or to Azure AD jobs.
PIM provides time-based, restricted, MFA enforced, approved, and auditable roles to a user or group for some Azure resource or Azure AD role. For example, if your company hires a vendor for a project to do some high-level tasks on your Azure tenant, you cannot simply provide any role to him/her. See Figure 5.34.
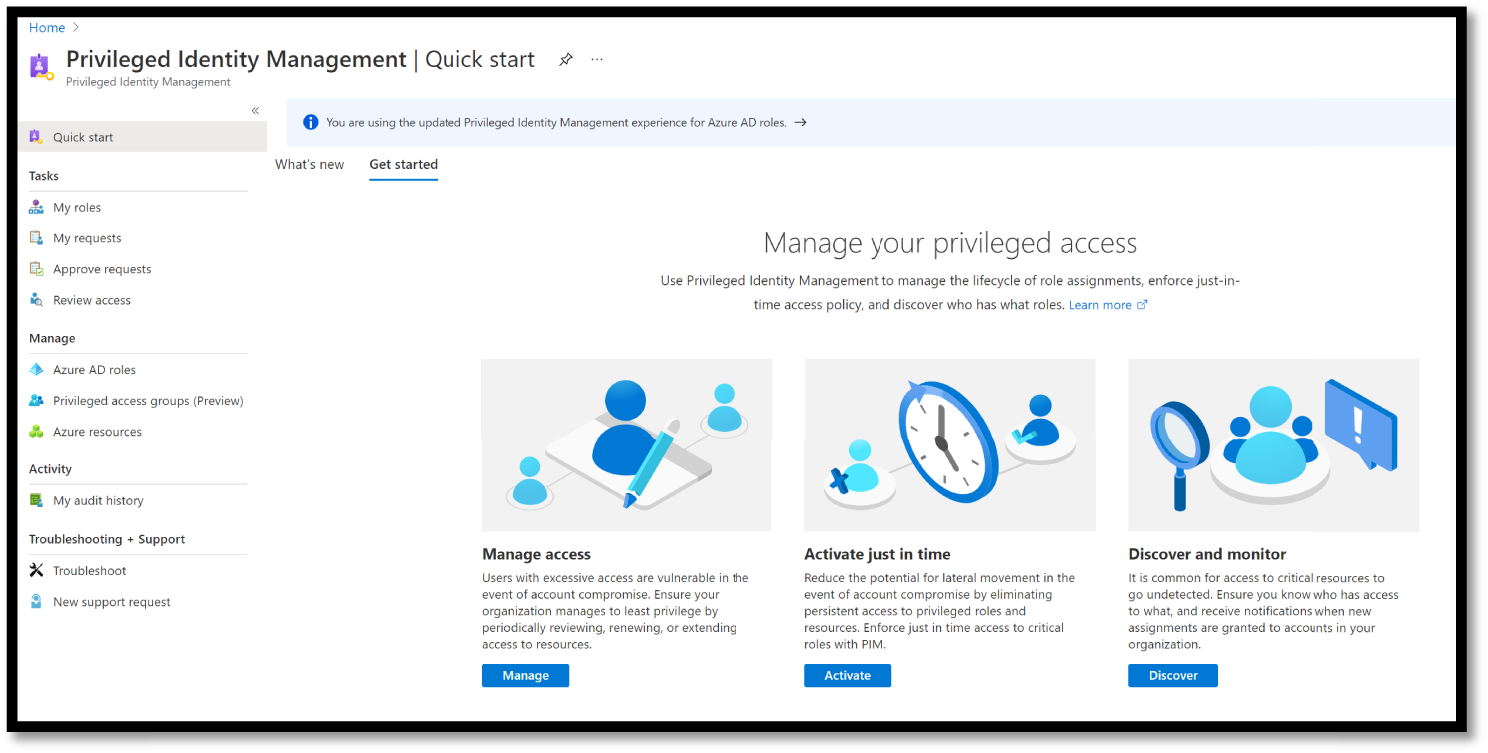
Figure 5.34: Azure PIM
Instead, you should be assessing the task first and providing a time-based access to your vendor until the project ends. When the project ends, the role is revoked, and that vendor will not have access to your Azure resource anymore. It means you are making the vendor “eligible” for doing some privileged tasks for a specific period. Here are some of the key features of Privileged Identity Management:
- Provide just-in-time privileged access to Azure AD and Azure resources
- Assign time-bound access to resources using start and end dates
- Require approval to activate privileged roles
- Enforce multi-factor authentication to activate any role
- Use justification to understand why users activate
- Get notifications when privileged roles are activated
- Conduct access reviews to ensure users still need roles
- Download audit history for internal or external audit
Microsoft Defender for Identity
Microsoft Defender for Identity (formerly Azure Advanced Threat Protection, also known as Azure ATP) is a cloud-based security solution that leverages an organization's on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
It's designed for hybrid environments, such as customers who use Office 365, but still have on-premises Active Directory infrastructure in place. It detects and alerts you to suspicious activity in your on-premises Active Directory environment. As a post-breach alerting system, the assumption is that an attacker has already gained access to your environment.
Components of Defender for Identity include Defender for Identity Portal, Identity Sensor for Domain Controls and AD FS, and Defender for Identity cloud services. See Figure 5.35.
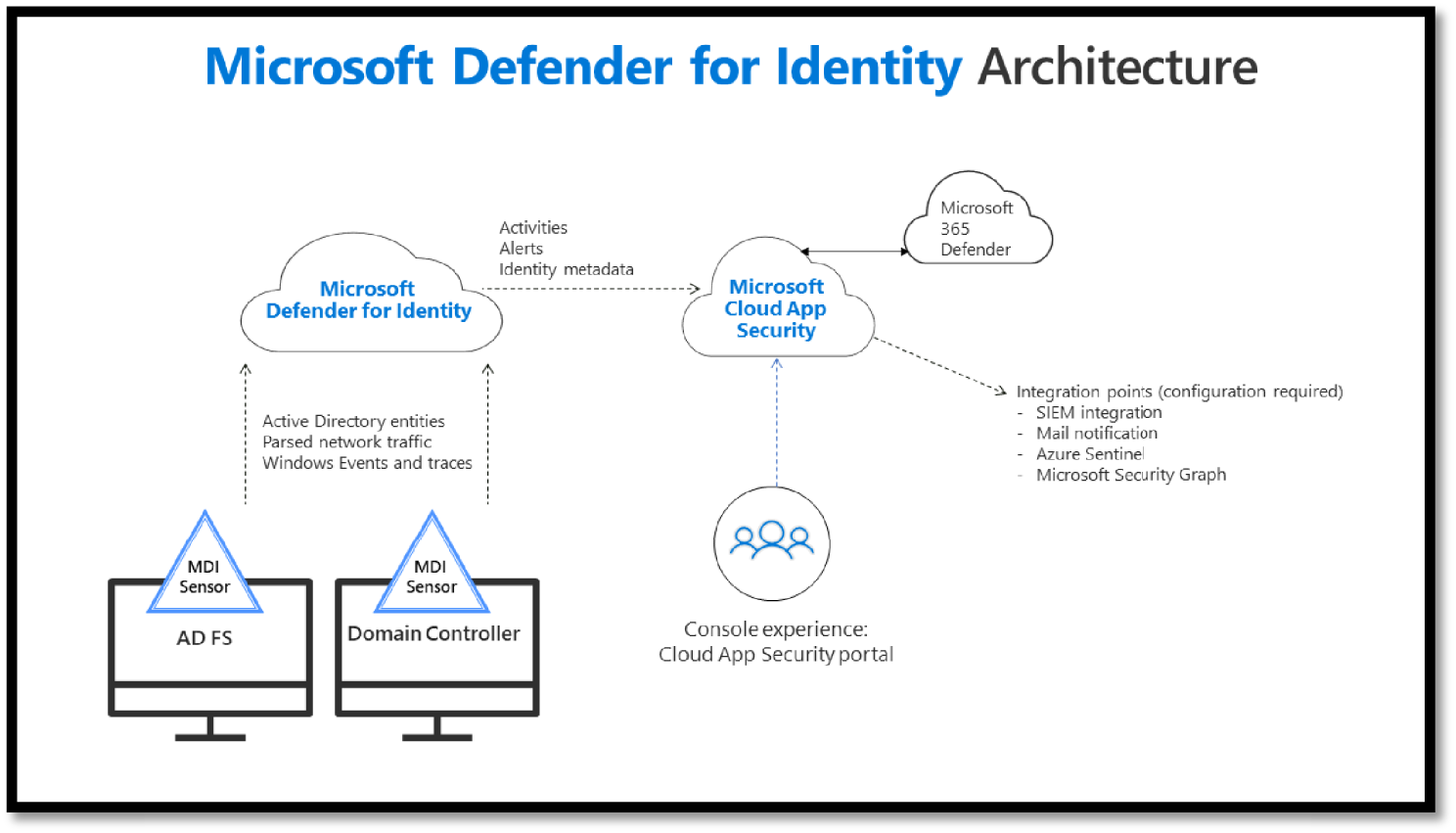
Figure 5.35: Microsoft Defender for Identity Architecture
Defender for Identity enables SecOp analysts and security professionals struggling to detect advanced attacks in hybrid environments to:
- Monitor users, entity behavior, and activities with learning-based analytics
- Protect user identities and credentials stored in Active Directory
- Identify and investigate suspicious user activities and advanced attacks throughout the kill chain
- Provide clear incident information on a simple timeline for fast triage
Azure AD B2B and B2C
Azure AD B2B collaboration can address the problem of sharing your applications with external users and is a feature of Azure AD rather than a standalone service.
These users could be suppliers, customers, partners, or any external user with whom you wish to collaborate. Again, this is more at the user level and not at the device level. See Figure 5.36.

Figure 5.36: Azure AD B2C portal
Azure AD Identity Governance
Azure Active Directory (Azure AD) Identity Governance allows you to balance your organization's need for security and employee productivity with the right processes and visibility. See Figure 5.37.

Figure 5.37: Identity Governance portal
In addition, it provides an organization with capabilities to ensure that the right people have the right access to the right resources. These and related Azure AD and Enterprise Mobility and security features allow you to mitigate access risk by protecting, monitoring, and auditing access to critical assets, while ensuring employee and business partner productivity.
Identity Governance gives organizations the ability to do the following tasks across employees, business partners, and vendors, and across services and applications, both on-premises and in clouds:
- Govern the identity lifecycle
- Govern the access lifecycle
- Secure privileged access for administration
Protecting SaaS Apps
Some of the common challenges faced with SaaS apps are concerning governance, risk, and compliance of those sprawling SaaS applications estate and unsanctioned Shadow IT applications. See Figure 5.38.
Microsoft has invested in secure and compliant SaaS services and helps its customers secure third-party Software as a Service (SaaS) with Microsoft Cloud App Security (MCAS), which provides Cloud Access Security Broker (CASB) capabilities, including XDR capabilities for SaaS applications as well as governance, threat protection, data protection, and more for these SaaS apps and the data stored within SaaS. See Figure 5.39.
Figure 5.38: SaaS challenges

Figure 5.39: MCAS Dashboard and Portal
MCAS also natively integrates with leading Microsoft solutions and is designed with security professionals to provide simple deployment, centralized management, and innovative automation capabilities.
MCAS and MDE illustrate Microsoft's philosophy of a single agent (or control point) for resources that provide many security services. This helps reduce the performance impact of installing too many security agents.
It supports various deployment modes, including log collection, API connectors, and reverse proxy. In addition, it provides rich visibility, control over data travel, and sophisticated analytics to identify and combat cyberthreats across all Microsoft and third-party cloud services (see Figure 5.40).
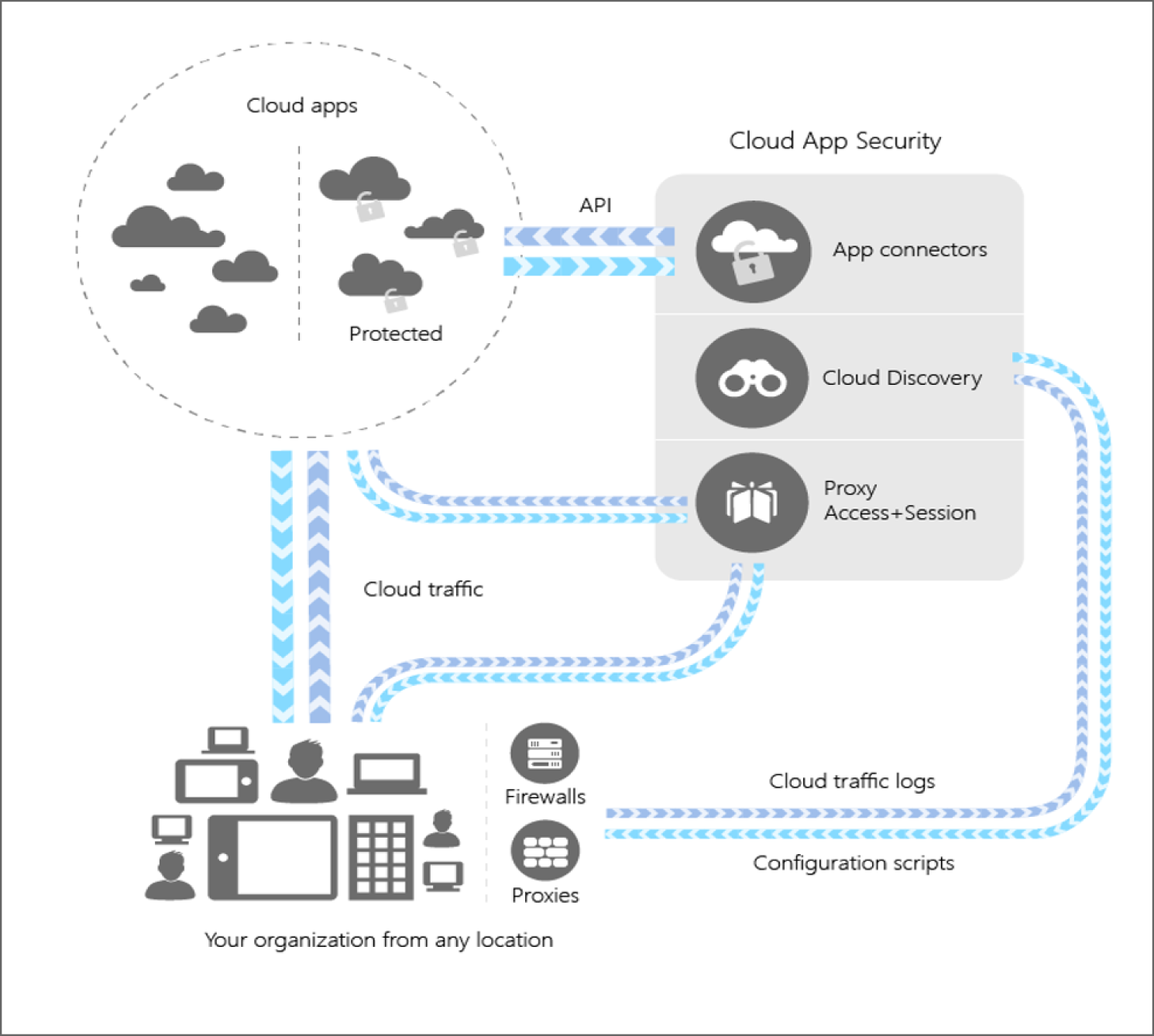
Figure 5.40: MCAS architecture
MCAS integrates and creates better visibility with your cloud by:
- Identifying cloud apps within your cloud environment using cloud discovery features.
- Helping you manage Shadow IT by sanctioning and unsanctioning apps in your cloud.
- Using easy-to-deploy app connectors that take advantage of provider APIs, for visibility and governance of apps that you connect to.
- Using Conditional Access App Control protection to get real-time visibility and control over access and activities within your cloud apps.
- Helping you have continuous control by setting, and then continually fine-tuning, policies.
Protecting Data and Information
Organizations today face a number of challenges concerning protecting and governing the data and information such as labeling, discovering, tracking information, and tracking data loss or manipulation of a file, and implementing and enforcing organization policy to protect different levels of sensitive data. For data classification, the biggest challenge is to discover and classify the data across on-premises, mobile devices, SaaS, and cloud infrastructure.
Data discovery and classification can be done through AIP scanner as an automated approach, or users can manually perform these tasks. Relying on users to identify the data and classifying them would be challenging and requires an extensive information security awareness and an educational program on how to identify the data as well as what control should be applied. Microsoft AIP could help an organization as a technology enabler to automate and manage this section. However, data classification criteria (e.g., highly confidential, confidential, restricted, public, etc.) and required security controls such as applying encryption, defining the right access of to who can access the classified documents, and others, should be defined at the data governance level and endorsed by senior management.
Microsoft is focused on providing strong data protection with an emphasis on persistently protecting the data anywhere it goes, and this contrasts with the typical industry approach, which relies solely on controls for devices/storage/networks that are unable to protect the data created/copied outside the enterprise (see Figure 5.41).
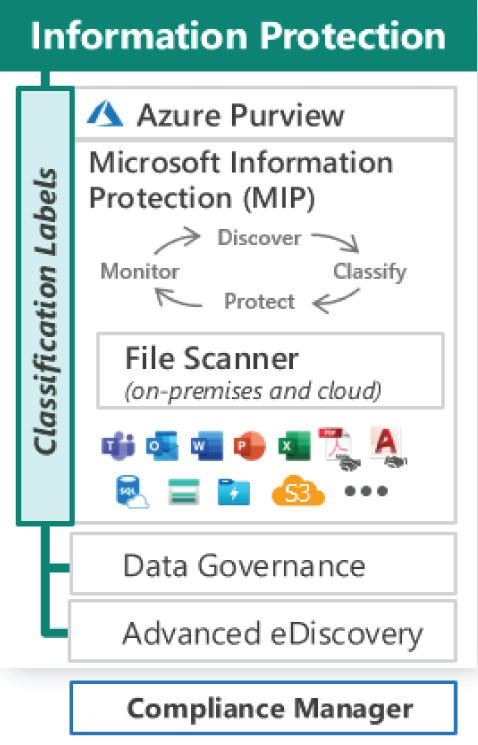
Figure 5.41: Protecting information and data
To overcome these challenges, Microsoft offers a range of services such as Azure Purview, Microsoft Information Protection (MIP), and Advanced eDiscovery.
Azure Purview
Microsoft Azure Purview is a fully managed, unified data governance service that helps you manage and govern your on-premises, multi-cloud, and SaaS data.
Purview creates a holistic, up-to-date map of your data landscape with automated data discovery, sensitive data classification, and end-to-end data lineage. As a result, Purview empowers data consumers to find valuable, trustworthy data.
It's built over Apache Atlas, an open-source project for metadata management and governance for data assets. Azure Purview also has a data share mechanism that securely shares data with external business partners without setting up extra FTP nodes or creating redundant large datasets.
Azure Purview does not move or store customer data out of the region in which it is deployed. The Purview service can be accessed from the Azure portal. See Figure 5.42.
Figure 5.42: Azure Purview dashboard
Some of the business value and advantages of Azure Purview include:
- It is designed to address the issues of annotating data sources, creating documentation of data sources, and restricting access of data sources.
- It helps enterprises get the most value from their existing information assets. In addition, the catalog creation makes data sources easily discoverable and understandable by the users who manage the data.
- Provides a cloud-based service into which you can register data sources. During registration, the data remains in its existing location, but a copy of its metadata is added to Azure Purview, along with a reference to the data source location. The metadata is also indexed to make each data source easily discoverable via search and understandable to the users who discover it.
- After you register a data source, you can then enrich its metadata. Either the user who registered the data source or another user in the enterprise adds the metadata. Any user can annotate a data source by providing descriptions, tags, or other metadata for requesting data source access. This descriptive metadata supplements the structural metadata, such as column names and data types, that's registered from the data source.
- Users can contribute to the catalog by tagging, documenting, and annotating data sources that have already been registered. They can also register new data sources, which are then discovered, understood, and consumed by the community of catalog users.
More details about this new service can be found at this link: https://azure.microsoft.com/en-us/services/purview/.
Microsoft Information Protection (MIP)
MIP helps an organization to discover, classify, and protect sensitive information wherever it lives or travels. These capabilities are included with Microsoft 365 Compliance, and it offers the tools to know your data, protect your data, and prevent data loss across the four elements of the information protection lifecycle, which are discover, classify, protect, and monitor.
MIP services can be accessed from the M365 Compliance portal at https://compliance.microsoft.com; (see Figure 5.43).
Figure 5.43: MIP service
In 2018, Microsoft introduced a unified labeling solution for Microsoft 365—Microsoft Information Protection (MIP)—that offered centralized management of labels and protection settings in the Security & Compliance Center.
Figure 5.44: Azure Information Protection portal
Azure Information Protection Unified Labeling Scanner (File Scanner)
AIP File Scanner is used to discover and assess existing data in SharePoint sites and file shares. It runs as a Windows Server service and lets you discover, classify, and protect files on UNC paths (network shares) and SharePoint document libraries and folders.
The AIP scanner can inspect any files that Windows can index. If you've configured sensitivity labels to apply automatic classification, the scanner can label discovered files to apply that classification and optionally apply or remove protection. Figure 5.45 shows the AIP scanner architecture, where the scanner discovers files across your on-premises and SharePoint servers.
The scanner uses the Azure Information Protection client, and it can classify and protect the same types of files as the client.
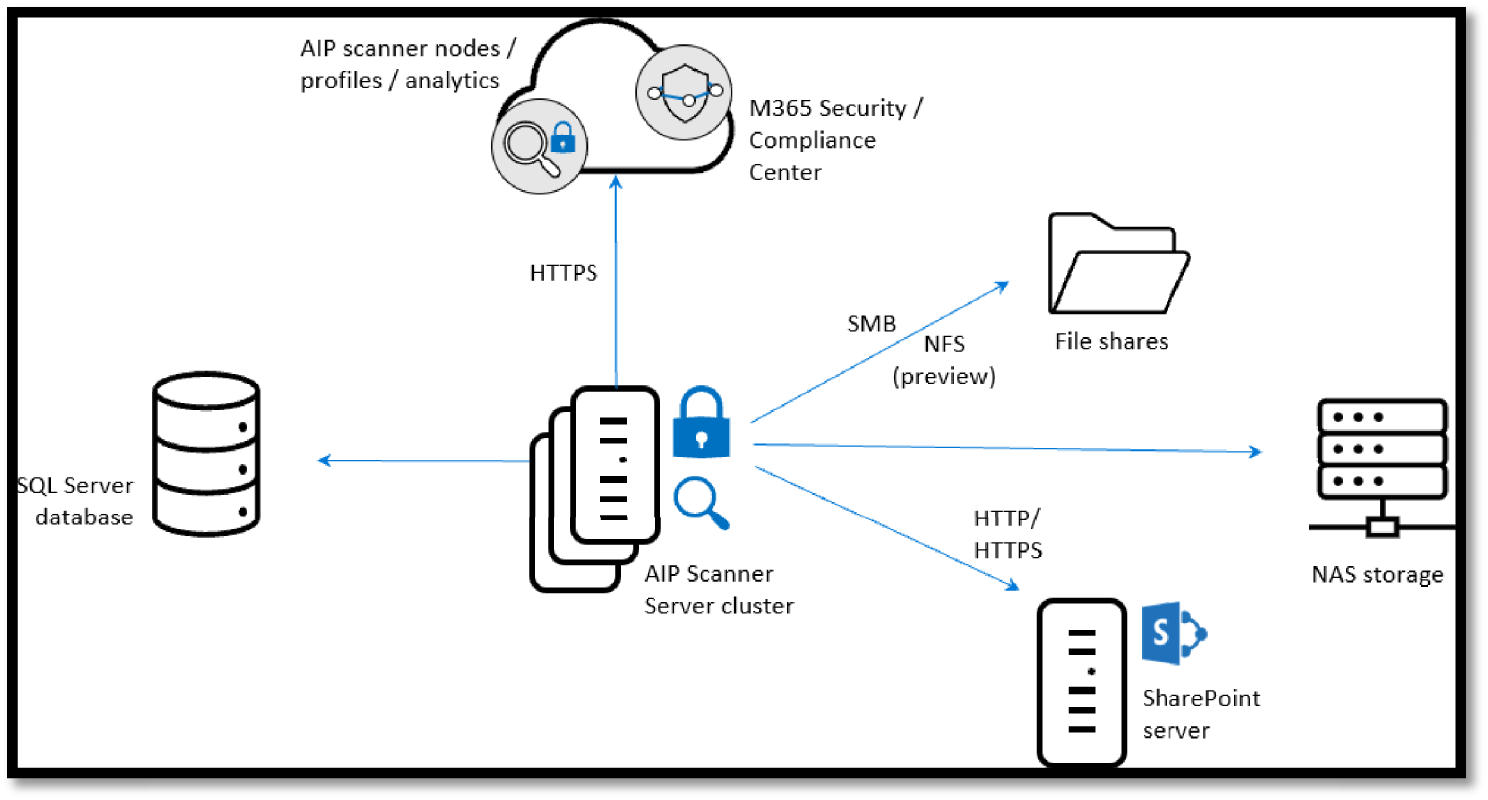
Figure 5.45: AIP File Scanner architecture
The Advanced eDiscovery Solution in Microsoft 365
Advanced eDiscovery builds on the existing Microsoft eDiscovery and analytics capabilities. Advanced eDiscovery provides an end-to-end workflow to preserve, collect,, review, analyze, and export content that's responsive to an organization's internal and external investigations. It also lets legal teams manage the entire legal hold notification workflow to communicate with custodians involved in a case.
You can use eDiscovery tools in Microsoft 365 to search for content in Exchange Online mailboxes, Microsoft 365 Groups, Microsoft Teams, SharePoint Online and OneDrive for Business sites, Skype for Business conversations, and Yammer teams. You can search mailboxes and sites in the same eDiscovery search by using the Content Search tool. And you can use Core eDiscovery cases to identify, hold, and export content found in mailboxes and sites.
If your organization has an Office 365 E5 or Microsoft 365 E5 subscription (or related E5 add-on subscriptions), you can further manage custodians and analyze content by using the Advanced eDiscovery solution in Microsoft 365. See Figure 5.46.

Figure 5.46: Core and Advanced eDiscovery portal
Compliance Manager
Microsoft Compliance Manager is a Microsoft 365 compliance center feature that helps you manage your organization's compliance requirements with greater ease and convenience. It can help you throughout your compliance journey, from taking inventory of your data protection risks to managing the complexities of implementing controls, staying current with regulations and certifications, and reporting to auditors.
With Microsoft Compliance Score, you can continuously assess and monitor data protection controls, get clear guidance on how to improve your score, reduce compliance risks, and leverage the built-in control mapping to scale your compliance effort across global, industrial, and regional standards.
- Continuous assessments: Microsoft Compliance Score can scan through your Microsoft 365 environments and detect your system settings, continuously and automatically updating your technical control status. For example, if you configured a compliance policy for Windows devices in the Azure AD portal, Microsoft Compliance Score can detect the setting and reflect that in the control details. Conversely, if you have not created the policy, Microsoft Compliance Score can flag that as a recommended action for you to take.
With the ongoing control assessment, you can now proactively maintain compliance instead of reactively fixing settings following an audit.
- Improve your score with recommended actions and solutions: Microsoft Compliance Score provides you with improvement actions in different areas, such as information protection, information governance, device management, and more. This allows you to easily understand the contribution you are making toward organizational compliance by category. Each recommended action has a different impact on your score, depending on the potential risk involved, so you can prioritize important actions accordingly.
Risk managers and compliance professionals can assess controls using the assessments view, which shows you the scores of GDPR, ISO 27001, ISO 27018, NIST CSF, NIST 800-53, HIPAA, FFIEC, and more. Microsoft Compliance Score helps make connections between each regulatory requirement and the solutions that can help you enhance your controls, thus increasing your overall score.
The Microsoft Compliance Score dashboard shows your current compliance score, helps you see what needs attention, and guides you to key improvement actions. Figure 5.47 shows an example of Compliance Manager dashboard with your compliance score.

Figure 5.47: Compliance Manager dashboard
Protecting IoT and Operation Technology
Organizations embrace the opportunity to reimagine and fundamentally transform their businesses using Internet of Things (IoT) technology.
The Internet of Things (IoT) can drive huge economic opportunities for industries and enable exciting innovations that reach across fields from childcare to eldercare, from healthcare to energy, from manufacturing to transportation. Diverse IoT in smart places—everything from remote monitoring, predictive maintenance, and smart spaces to connected products and customer-facing technologies like mobile apps—can reduce operational complexity, lower costs, and speed up time to market.
With technology pundits and analysts predicting even more expansive use of IoT devices and apps in the future, along with ever-evolving devices, services, and apps that touch the IoT space, organizations are often eager to take advantage of the business benefits. However, many companies are right to be cautious in their pursuit of the benefits of IoT solutions due to very real IoT security concerns. IoT deployments pose unique new security, privacy, and compliance challenges to businesses worldwide.
While traditional information cybersecurity revolves around software and how it is implemented, security for IoT adds an extra layer of complexity as the cyber and the physical worlds converge. A wide range of operational and maintenance scenarios in the IoT space rely on end-to-end device connectivity to enable users and services to interact, login, troubleshoot, send, or receive data from devices. Companies may want to take advantage of IoT efficiencies like predictive maintenance, for example, but knowing what IoT security standards to adhere to is essential, because operational technology (OT) is too important and valuable to risk in the event of breaches, disasters, and other threats.
Security Concerns with IoT
Although IoT devices may seem too small or too specialized to be dangerous, there is real risk in what are really network-connected, general-purpose computers that can be hijacked by attackers, resulting in problems beyond IoT security. Even the most mundane device can become dangerous when compromised over the Internet—from spying with video baby monitors to interrupted services on life-saving health care equipment. Once attackers have control, they can steal data, disrupt delivery of services, or commit any other cybercrime they'd do with a computer. Attacks that compromise IoT infrastructure inflict damage, not just with data breaches and unreliable operations, but also physical harm to the facilities, or worse—to the humans operating or relying on those facilities.
Concerns around security for IoT are also driven by:
- Device heterogeneity or fragmentation: Many companies use a large number of different devices running different software, using different chips, and may even use different methods to connect. This is what's known as device heterogeneity, and it creates a challenge to update and control all your different connected devices. For organizations with production IoT deployments, all these different devices create complexity—but software solutions do exist to simplify this process.
- Connection to valuable operational technology (OT): Many businesses would love to take advantage of the business benefits of connection, but can't risk the losses of revenue if facilities are attacked and go down, even for a few days. The good news is that there are trusted IoT cybersecurity companies that offer software solutions to help protect against attacks.
- Challenges with legacy devices: Some devices were designed before IoT existed and any connection was even possible. These devices have never been “hardened,” the process for identifying and eliminating or mitigating vulnerabilities. Many other legacy devices are inexpensive or not designed with specific IoT security in mind, so they lack IoT cybersecurity features despite good intentions of the manufacturer.
Attackers try to compromise IoT solutions by identifying security weaknesses, so building security into every part of your IoT solution is essential for minimizing risks to your data, business assets, and reputation.
Because this new IoT connectivity covers such a large and often unfamiliar attack surface and IoT devices and apps can hold massive troves of personal, operational, and corporate data, IoT security pros need to go beyond the traditional information security requirements of confidentiality, integrity, and availability.
IoT cybersecurity pros are, of course, concerned with data breaches and other cyberattacks. But, because an IoT vulnerability has the potential to cause life-threatening physical danger or shutdown of profit-making operations, they must especially concern themselves with securing connectivity, device hardening, threat monitoring, and security posture management, as well as securing data on the backend in the cloud.
Understanding That IoT Cybersecurity Starts with a Threat Model
Microsoft has long used threat models for its products and has made the company's threat modeling process publicly available. The objective of threat modeling is to understand how an attacker might be able to compromise a system and then make sure appropriate mitigations are in place. Threat modeling forces the design team to consider mitigations as the system is designed rather than after a system is deployed. This fact is critically important, because retrofitting security defenses to myriad devices in the field is infeasible, error prone, and leaves customers at risk.
Many development teams do an excellent job capturing the functional requirements for the system that benefit customers. However, identifying non-obvious ways that someone might misuse the system is more challenging. Threat modeling can help development teams understand what an attacker might do and why. Threat modeling is a structured process that creates a discussion about the security design decisions in the system, as well as changes to the design that are made along the way that impact security. While a threat model is simply a document, this documentation also represents an ideal way to ensure continuity of knowledge, retention of lessons learned, and help new teams onboard rapidly. Finally, an outcome of threat modeling is to enable you to consider other aspects of security, such as what security commitments you wish to provide to your customers. These commitments in conjunction with threat modeling inform and drive testing of your Internet of Things (IoT) solution.
An IoT Cybersecurity attack can threaten:
- Processes: Threats to processes both under your control, such as web services, and threats from external entities, such as users and satellite feeds, that interact with the system, but are not under the control of the application.
- Communication, also called data flows: Threats around the communication path between devices, devices and field gateways, and device and cloud gateways.
- Storage: Threats to temporary data queues, operating systems (OS), and image storage.
An IoT attack can be broadly categorized in five different areas: spoofing, tampering, information disclosure, denial of service, and elevation of privilege.
Spoofing and Information Disclosure:
- An attacker can manipulate the state of a device anonymously.
- An attacker may intercept or partially override the broadcast and spoof the originator (often called man-in-the-middle or MitM attacks).
- An attacker can take advantage of the vulnerability of constrained or special-purpose devices. These devices often have one-for-all security facilities like password or PIN protection, or rely on network shared key protections. When the shared secret to device or network (PIN, password, shared network key) is disclosed, it is possible to control the device or observe data emitted from the device.
Tampering:
- An attacker can tamper with any physical device—from battery drainage vulnerability or “sleep deprivation to random number generator (RNG) attacks made possible by freezing devices to reduce entropy.
- An attacker may partially or wholly replace the software running on the device, potentially allowing the replaced software to leverage the genuine identity of the device if the key material or the cryptographic facilities holding key materials were available to the illicit program.
Denial of Service:
- A device can be rendered incapable of functioning or communicating by interfering with radio frequencies or cutting wires. For example, a surveillance camera that had its power or network connection intentionally knocked out cannot report data, at all.
Information Disclosure:
- An attacker may eavesdrop on a broadcast and obtain information without authorization or may jam the broadcast signal and deny information distribution.
- An attacker may intercept or partially override the broadcast and send false information.
Elevation of Privilege:
- A device that does a specific function can be forced to do something else. For example, a valve that is programmed to open halfway can be tricked to open all the way.
Microsoft Investment in IoT Technology
Microsoft is investing in many technologies to manage and secure this ecosystem, including an end-to-end solution (called Azure Sphere) that's designed to provide highly secured, Internet-connected microcontroller (MCU) devices, and Azure Defender for IoT, which provides functionality such as asset and vulnerability management (see Figure 5.48).

Figure 5.48: IoT and Operational Technology challenges
Azure Sphere
Azure Sphere is a secured, high-level application platform with built-in communication and security features for Internet-connected devices. The platform integrates hardware built around a secured silicon chip; the Azure Sphere OS (operating system), a custom high-level Linux-based operating system; and the Azure Sphere Security Service, a cloud-based security service that provides continuous, renewable security.
Check out this URL to learn more about Azure Sphere: https://azure.microsoft.com/en-us/blog/introducing-microsoft-azure-sphere-secure-and-power-the-intelligent-edge.
Azure Defender
Defender currently covers the most highly used infrastructure services including servers/VMs, storage, databases, DNS, apps services, Kubernetes, container registries, key vault, and resource manager.
Azure Defender for IoT
For end-user organizations, Azure Defender for IoT offers agentless, network-layer security that is rapidly deployed, works with diverse industrial equipment, and interoperates with Azure Sentinel and other SOC tools that are deployed on-premises or in Azure-connected environments. For IoT device builders, Azure Defender for IoT offers lightweight agents to embed device-layer security into new IoT/OT initiatives.
Azure Defender provides threat detection for your cloud workload environments, while Azure Defender for IoT specifically helps protect IoT/OT devices from the specialized threats they face. Adversaries use different methods to target IT and IoT/OT networks. Azure Defender for IoT detects threats by analyzing the specialized protocols, devices, and machine-to-machine behaviors found in IoT/OT environments.
It also protects both managed and unmanaged IoT and operational technology (OT) devices with agentless, asset discovery, vulnerability management, and threat protection capabilities. This helps organizations to accelerate innovation with comprehensive security across all your IoT/OT devices. See Figure 5.49.

Figure 5.49: Defender for IoT
Additionally, this capability also protects IoT devices via lightweight micro agents that support standard IoT operating systems, such as Linux and RTOS. It can be deployed on-premises or in Azure-connected environments (see Figure 5.50).
Threat Modeling for the Azure IoT Reference Architecture
Microsoft uses the framework outlined previously to do threat modeling for Azure IoT. This section uses the concrete example of Azure IoT Reference Architecture to demonstrate how to think about threat modeling for IoT and how to address the threats identified. See Figure 5.51.

Figure 5.50: Azure Defender (Security Center for IoT Security)
This example identifies four main areas of focus:
- Devices and data sources
- Data transport
- Device and event processing
- Presentation

Figure 5.51: IoT Reference Architecture
Figure 5.52 provides a simplified view of Microsoft's IoT Architecture using a Data Flow Diagram model that is used by the Microsoft Threat Modeling Tool.

Figure 5.52: Threat Modeling example
It is important to note that the architecture separates the device and gateway capabilities. This approach enables the user to leverage gateway devices that are more secure: they are capable of communicating with the Cloud Gateway using secure protocols, which typically requires greater processing overhead than a native device—such as a thermostat—could provide on its own. In the Azure services zone, you can assume that the Cloud Gateway is represented by the Azure IoT Hub service.
Azure Defender for IoT Architecture (Agentless Solutions)
Defender for IoT connects both to the Azure cloud and to on-premises components. The solution is designed for scalability in large and geographically distributed environments with multiple remote locations. This solution enables a multi-layered distributed architecture by country, region, business unit, or zone. See Figure 5.53.
Azure Defender for IoT includes the following components.
Cloud connected deployments:
- Azure Defender for IoT sensor VM or appliance
- Azure portal for cloud management and integration to Azure Sentinel
- On-premises management console for local-site management
- An embedded security agent (optional)
Air-gapped (offline) deployments:
- Azure Defender for IoT sensor VM or appliance
- On-premises management console for local site management

Figure 5.53: IoT Agentless Deployment design
Azure Defender for IoT Architecture (Agent-based solutions)
Defender for IoT is enabled by default in every new IoT Hub that is created. Defender for IoT provides real-time monitoring, recommendations, and alerts, without requiring agent installation on any devices and uses advanced analytics on logged IoT Hub metadata to analyze and protect your field devices and IoT Hubs.
The Defender for IoT micro agents provides in-depth security protection and visibility into device behavior. It collects, aggregates, and analyzes raw security events from your devices. Raw security events can include IP connections, process creation, user logins, and other security-relevant information. Defender for IoT device agents also handle event aggregation to help avoid high network throughput. The agents are highly customizable, allowing you to use them for specific tasks, such as sending only important information at the fastest SLA, or for aggregating extensive security information and context into larger segments, avoiding higher service costs.
Device agents and other applications use the Azure send security message SDK to send security information into Azure IoT Hub. IoT Hub gets this information and forwards it to the Defender for IoT service.
Once the Defender for IoT service is enabled, in addition to the forwarded data, IoT Hub also sends out all of its internal data for analysis by Defender for IoT. This data includes device-cloud operation logs, device identities, and hub configuration. All of this information helps to create the Defender for IoT analytics pipeline.
Defender for IoT analytics pipeline also receives other threat intelligence streams from various sources within Microsoft and Microsoft partners. The Defender for IoT entire analytics pipeline works with every customer configuration made on the service (such as custom alerts and use of the send security message SDK).
Using the analytics pipeline, Defender for IoT combines all of the streams of information to generate actionable recommendations and alerts. The pipeline contains both custom rules created by security researchers and experts as well as machine learning models searching for deviation from standard device behavior and risk analysis.
Defender for IoT recommendations and alerts (analytics pipeline output) are written to the Log Analytics workspace of each customer. Including the raw events in the workspace and the alerts and recommendations enables deep-dive investigations and queries using the exact details of the suspicious activities detected. See Figure 5.54.
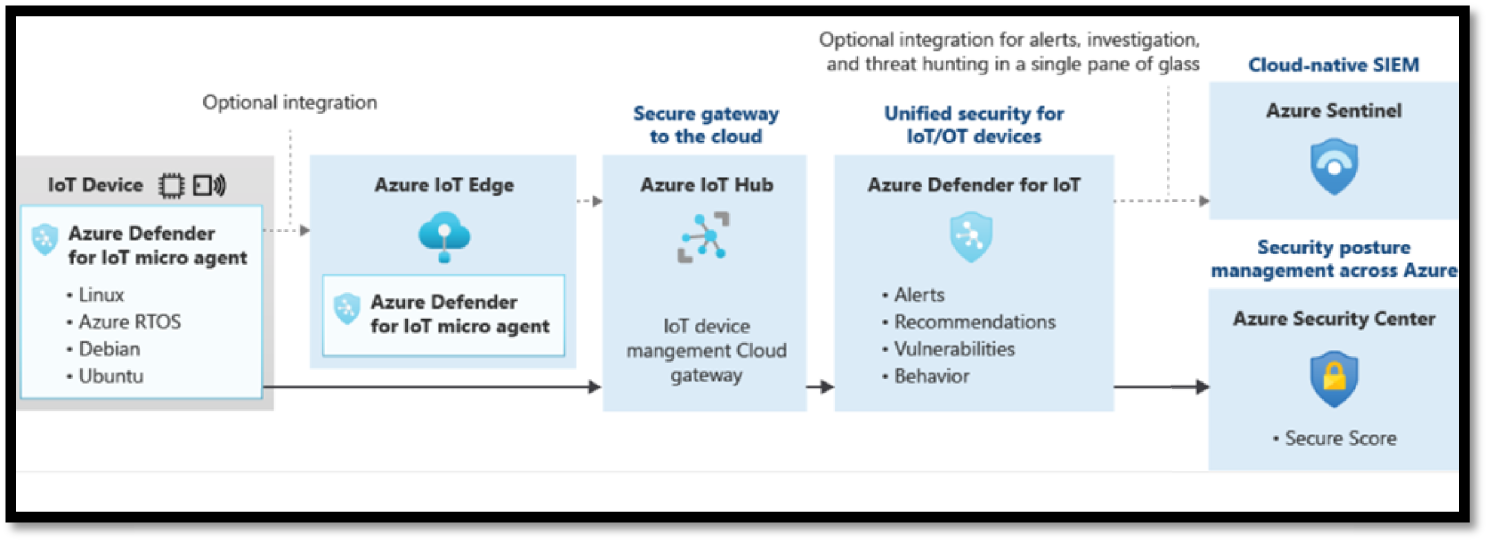
Figure 5.54: IoT Agent-based integration flow
Understanding the Security Operations Solutions
Running and operating a legacy on-premises model of security operation offers many challenges to the SecOps team. Analysts are overloaded with too many false positive signals and alerts. The investigation workflow is very siloed and poor. Integration is mostly manual. On top of that, the security tools and products are constantly evolving, which breaks the integration. Microsoft has solutions to these issues; (see Figure 5.55).

Figure 5.55: SOC solutions
Microsoft provides built-in security capabilities to enable SOCs to secure cloud and on-premises workloads using the cloud's power and its cloud-native SIEM/SOAR service, such as Azure Sentinel. Microsoft also provides other protective and detective tooling and services to manage security threats in an organization.
- Azure Sentinel, power with AI and build with ML: Azure Sentinel is Microsoft's cloud-native SIEM and SOAR service. It gives you a bird's-eye view across the enterprise. It put the cloud and large-scale intelligence from decades of Microsoft security experience to work.
- Microsoft Defender XDR: Together, Microsoft 365 Defender and Azure Defender provides an end-to-end XDR solution for threat detection and response across the Microsoft estate in the cloud, on-premises, and in other clouds. It provides advanced endpoint detection and response (EDR) capabilities, Web Content Filtering, Threat and Vulnerability Management, and Data Loss Protection (DLP). Like MCAS, Microsoft integrates this with other capabilities across their portfolio so you don't have to run multiple agents/solutions to achieve your endpoint security goals.
- Azure Defender: Delivers XDR capabilities to protect multi-cloud and hybrid workloads, including virtual machines, databases, containers, IoT, and more. Azure Defender is an evolution of the Azure Security Center threat protection capabilities and is accessed from within Azure Security Center.
- Microsoft Threat Experts: A new managed threat-hunting service in Windows Defender Advanced Threat Protection such as human adversary intrusions, hands-on keyboard attacks, and advanced attacks like cyber espionage. It provides proactive hunting, prioritization, and additional context and insights that further empower Security Operations Centers (SOCs) to identify and respond to threats quickly and accurately.
- Microsoft Detection and Response Team (DART): Provides onsite reactive incident response and remote proactive investigations. This team works with customers globally to identify risks and provide reactive incident response and proactive security investigation services to help developers manage their cyber risk, especially in today's dynamic threat environment.
- MSSP/MDR providers: Microsoft partners with top experts in the industry to build their expertise on these capabilities so that they can advise and directly support their customers.
Understanding the People Security Solutions
People security is a new domain that was added to MCRA, and it focuses on enabling, educating, and empowering the team to make good security decisions.
It's hard to keep pace with all the changes happening in the world of cybersecurity. It requires continuously learning (and unlearning) to stay ahead of the ever-evolving threat landscape. You must treat your people as valuable and powerful security assets and address security awareness, behavior, and culture in tandem.
Microsoft continues to invest in services with built-in automation, User and Entity Behavior Analytics (UEBA) so that businesses can bring about real and tangible reductions in their human cyber risk. See Figure 5.56.

Figure 5.56: People Security solutions
Attack Simulator
Simulation Training in Microsoft Defender for Office 365 is an intelligent social engineering risk management tool that empowers all employees to be defenders. It uses a real phish to emulate the employees’ attacks, and it delivers security training tailored to each employee's behavior in simulations. These simulated attacks can help you identify and find vulnerable users before an actual attack impacts your bottom line. See Figure 5.57.
Figure 5.57: Attack Simulator
It also automates the security training program's design and deployment, saving the resource-strapped security teams time and resources.
Insider Risk Management (IRM)
IRM is a compliance solution in Microsoft 365 that helps minimize internal risks by enabling you to detect, investigate, and act on malicious and inadvertent activities in an organization. Insider risk policies allow you to define the types of risks to identify and detect in the organization, including acting on cases and escalating cases to Microsoft Advanced eDiscovery if needed. See Figure 5.58.

Figure 5.58: Insider Risk Management dashboard
IRM helps the risk analysts quickly take appropriate actions to make sure users are compliant with an organization's compliance standards (see Figure 5.59).
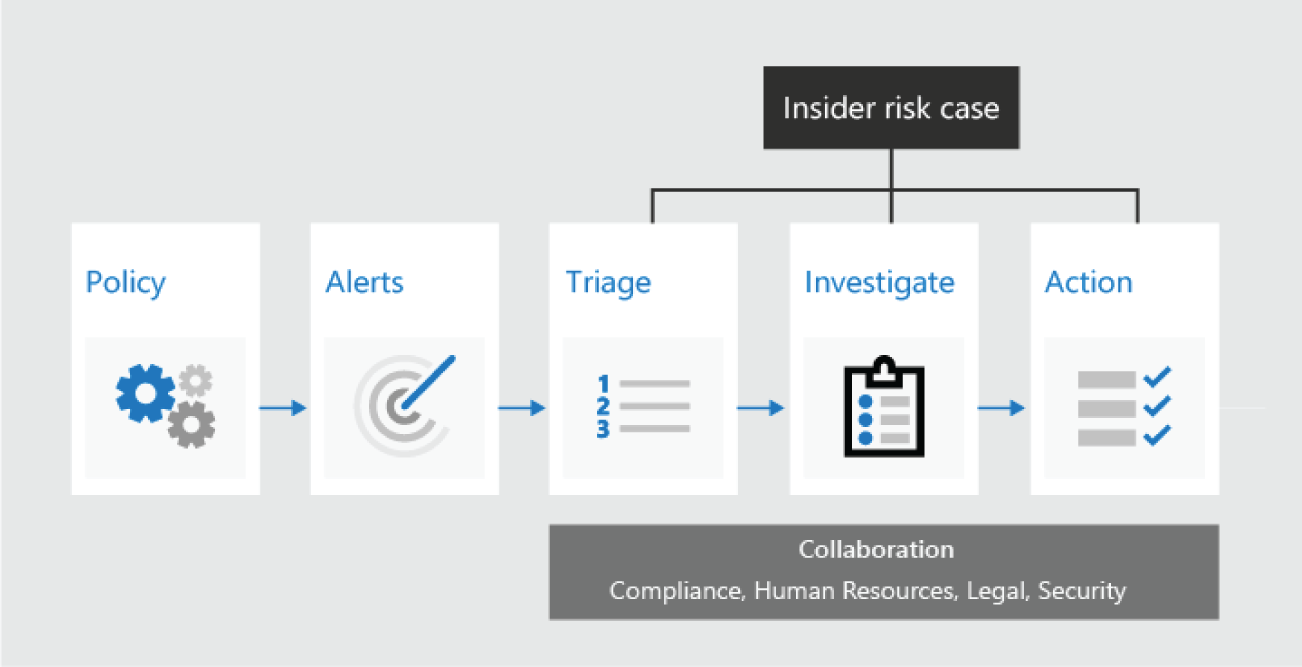
Figure 5.59: Insider Risk Management workflow
IRM is built on the following principles:
- Transparency: Allows you to balance user privacy versus organization risk with privacy-by-design architecture.
- Configurable: Easily configurable policies based on industry, geographical, and business groups.
- Integrated: Highly integrated workflow across Microsoft 365 compliance solutions.
- Actionable: Insights to enable reviewer notifications, data investigations, and user investigations.
Communication Compliance
Communication Compliance is another insider risk solution in Microsoft 365 that helps minimize communication risks to detect, capture, and act on inappropriate messages in the organization.
Communication Compliance offers built-in remediation workflows and insights that enable you to act on risks across Microsoft Teams messages, Exchange email, Skype for Business Online, or even third parties such as Instant Bloomberg. See Figure 5.60.

Figure 5.60: Communication Compliance dashboard
This also allows an organization to overcome many modern challenges associated with compliance and internal and external communications, including:
- Scanning increasing types of communication channels
- Scanning the increasing volume of message data
- Dealing with regulatory enforcement and the risk of fines
- Leveraging machine learning classifiers to quickly detect threats (to others or one's self), harassment, and profanities across company communication channels in keeping with corporate policies
- Supporting employee mental health, enabling safe remote learning, and minimizing the impact of internal risk by detecting threatening language in a timely manner.
Summary
Microsoft Cybersecurity Reference Architecture can be used for several purposes (beyond a geeky wall decoration to shock and impress your cubical neighbor), including the following:
- As a learning tool: MCRA can be leveraged as a great learning tool for those who are starting their career in cybersecurity and those who want to learn how Microsoft services integrate and work together.
- Starting template for a security architecture: The most common use case is that organizations use the document to help define a target state for cybersecurity capabilities. Organizations find this architecture useful because it covers capabilities across the modern enterprise estate that now span on-premises, mobile devices, many clouds, and IoT/Operational Technology.
- Comparison reference for security capabilities: We know of several organizations that have marked up a printed copy with what capabilities they already own from various Microsoft license suites (many customers don't know they own quite a bit of this technology), which ones they already have in place (from Microsoft or a partner/third party), and which ones are new and could fill a need.
- Microsoft's integration investments: The architecture includes visuals of key integration points with partner capabilities (e.g., SIEM/Log integration, Security Appliances in Azure, DLP integration, and more) and within its own product capabilities (e.g., Advanced Threat Protection, Conditional Access, and more).
