5. Broadband Network Services
In this chapter:
Introduction
Today’s broadband networks are increasingly made up of high-speed fiber-optic links with the augmented capacity required by the growing reliance on applications located on the Internet and in the cloud. Current workplaces cannot come close to functioning without the reliable, high-capacity broadband links now available. Older broadband technologies have capacity and flexibility limitations have that make them unsuitable for most of today’s requirements.
Carrier Gigabit Ethernet and dedicated wavelengths are largely replacing older, inflexible, limited-in-speed, broadband services wherever fiber cabling is available. Gigabit Ethernet is now commonly deployed on fiber cabling at enterprise locations. These links support speeds of up 100Gbps. But large social network companies are deploying 400 Gigabit connections at their data centers. Moreover, telephone companies’ core networks that carry traffic between cities, states, and across the country are achieving terabit (thousand gigabit per second) data rates.
Dedicated wavelengths on fiber-optic cabling are a high-capacity alternative to Carrier Gigabit Ethernet. Dedicated wavelengths refer to a portion of the fiber-optic cabling capacity, an individual wavelength, dedicated to a single customer. These often link customers’ branch offices, warehouses, and headquarters together.
While increasing capacity on fiberoptic cables is important, it doesn’t solve the issues of managing traffic, prioritizing applications and automating functions in broadband networks. Wide Area Software Defined Networks (WA SDNs) are able to prioritize applications and automate routing on broadband networks. They can be programmed to automatically route traffic away from congested routes and parts of networks that are completely out of service.
This flexibility and automation is due to the defining aspect of WA SDN: it is controlled by software. This contrasts with earlier network protocols, which used hardware (routers, switches, and other adjuncts) to control traffic in packet networks. WA SDNs are a layer of software that runs on top of dedicated wavelengths and Gigabit Ethernet.
Multiprotocol Label Service (MPLS), which does prioritize voice and video, is still used by enterprises. However, the routing is rigid and the capacity is limited. It’s not uncommon for MPLS and WA SDN to be present in the same enterprise networks with MPLS under the control of WA SDN.
Telephone companies, particularly in urban and suburban areas, are often dropping support for older, slower, inflexible services wherever fiber-optic cabling is available. The older services, mainly T1, T3, and DSL have severely limited capacity and less-flexible configurations than newer broadband. Moreover, it is more costly for telephone companies to support them than the more flexible Carrier Gigabit Ethernet and Dedicated Wavelength services. For these reasons, and because customers are demanding higher capacities, telephone companies are phasing out T1, T3, and DSL wherever fiber cabling is available.
As it’s difficult for organizations to accomplish their day-to-day functions when their broadband networks are unavailable, reliability and availability are critical concerns. Many customers take it for granted that because there are few network outages, their broadband networks will be available 7 days a week, 24 hours a day. However, for large financial services companies and medical institutions, this is not adequate. Most of these large institutions have duplicate, backup fiber-optic lines connecting their buildings to broadband links if their primary links fail. Fiber-optic lines cut by a backhoe or a failure in the telephone company’s equipment can cause failures.
Managed services are one way that carriers differentiate themselves from regional and smaller competitors, who sell discounted broadband services. Examples of managed services are managing Wi-Fi networks and consulting on data centers. In addition, large carriers distinguish themselves from smaller carriers by promoting their international presence. This is important for enterprises with a global infrastructure. A discount on mobile services is another distinguishing factor that large carriers offer major enterprise customers to lure them away from smaller telephone companies that may offer discounts in smaller regions of the country.
Note
Disagreement within the FCC over the Definition of Broadband
The Telecommunications Act of 1996 requires that the Federal Communications Commission annually:
 Review the definition of broadband
Review the definition of broadband Determine if advanced telecommunications (broadband) capability is being deployed to all Americans
Determine if advanced telecommunications (broadband) capability is being deployed to all Americans Analyze whether advanced telecommunications is deployed in a reasonable and timely fashion
Analyze whether advanced telecommunications is deployed in a reasonable and timely fashion Define advanced telecommunications capability (data rates)
Define advanced telecommunications capability (data rates)
Defining advanced telecommunications capability means setting the minimum speed that fixed line network operators need to offer subscribers in order for the service to be considered broadband. In 2015 the FCC defined broadband as 25Mbps downstream and 3Mbps upstream. In 2017, the FCC affirmed the 25/3Mbps speeds, and also asked for comments on whether this capacity is adequate for today’s needs.
Not everyone agrees with the FCC’s definition of broadband. On August 8, 2017, FCC Commissioner Mignon L. Clyburn issued the following statement in response to the FCC’s majority opinion keeping the definition of broadband as 25Mbps downstream and 3Mbps upstream. The following are excerpts from Clyburn’s statement:
We sell consumers short by proposing a speed benchmark that is way too low. The statute defines ... broadband as ...‘capable of originating and receiving high-quality voice, data, graphics and video telecommunications’... the 25/3Mbps standard we propose would not even allow for a single stream of 1080p video conferencing....
The designation 1080p (1080 pixels) refers to the resolution (number of pixels) on televisions and video conferencing. A pixel can be thought of as a dot or picture element. 1080p is the resolution generally found in high-definition transmissions to televisions.
Broadband Worldwide
A report commissioned by the Broadband Forum and conducted by the market analyst firm Point Topic revealed that there were a total of 871.1 million fixed-broadband subscribers worldwide at the end of the first quarter of 2017. The report covers only broadband access over cabling and fixed, point-to-point wireless services. According to China Money’s April 27, 2017, article “China’s Fixed-Line Broadband Penetration Rate To Hit 63% This Year” by Pan Yue, China had 310 million broadband subscribers. This is the highest number of broadband subscribers in a single country worldwide. According to statistics company Statista, as of the end of the first quarter of 2017, the United States had 93.9 million broadband subscribers. This is the second-highest number of broadband subscribers worldwide according to Point Topic.
Many people in less-developed parts of the world access the Internet primarily over mobile services. This is because dedicated Internet access over landline networks is frequently either not available or more costly than mobile services in these areas. In addition, electricity is often expensive. In the Philippines, both ISP-delivered dedicated Internet access and electricity are too costly for most citizens. Thus, mobile services are attractive as electricity is only required for charging laptops, tablet computers, and other devices that are equipped with mobile capabilities. Moreover, a single device can be used to make calls and to access sites such as Facebook.
While current mobile networks support broadband services, they’re slower than those over most wireline networks. However, new technologies and upgrades to existing standards are vastly improving Internet access on mobile networks and spurring adoption of mobile broadband. See Chapter 7 for information on 5G mobile protocols.
Wired Internet speeds for the premium plan (100, 200, and 300 Mbps) were up to 70 percent slower than promised.
Voip Calling Services over Broadband
When voice is transmitted on broadband networks using Voice over Internet Protocol (VoIP), voice is digitized and bundled into packets to make it compatible with the data packets on broadband networks. Packets are similar to envelopes in that they include headers that specify addressee and sender information (one of the ways that they differ, of course, is that they also provide error correction). Because headers are carried along with data packets, they interface more easily with computer services such as e-mail. Standard computer platforms are used to manage VoIP services.
Residential vs. Enterprise Services
When VoIP services such as Skype were first available, residential customers adopted them before the more cautious enterprises saw their value and began adopting them in large numbers. Additionally, small businesses used VoIP and its related services before large enterprise customers, who were concerned with quality and security lapses. As capacity in broadband networks increased and delays decreased, larger enterprises began using VoIP and its features. Non-profits, businesses, and commercial firms commonly use conference calling, unified communications, and other features available at low costs from VoIP providers over broadband networks. Large telephone and cable TV companies now commonly offer these features as well.
Lower-Priced, Flexible Consumer VoIP Services Adopted by Enterprises
Many consumers and organizations use VoIP for their phone calls. These calls are often carried over their broadband links. Large telephone companies are transitioning their calling services to low-cost VoIP where voice is just another piece of data on the network. VoIP services include features such as voicemail, audio conferences, video conferencing, and unified communications. See Figure 5-1 for transmission of voice on carriers’ networks. Because this results in the need to maintain only one type of network—a data network—increasing numbers of enterprise and residential customers’ calls are now carried as packets along with video and data traffic. Without VoIP, carriers are required to support both voice and data networks.
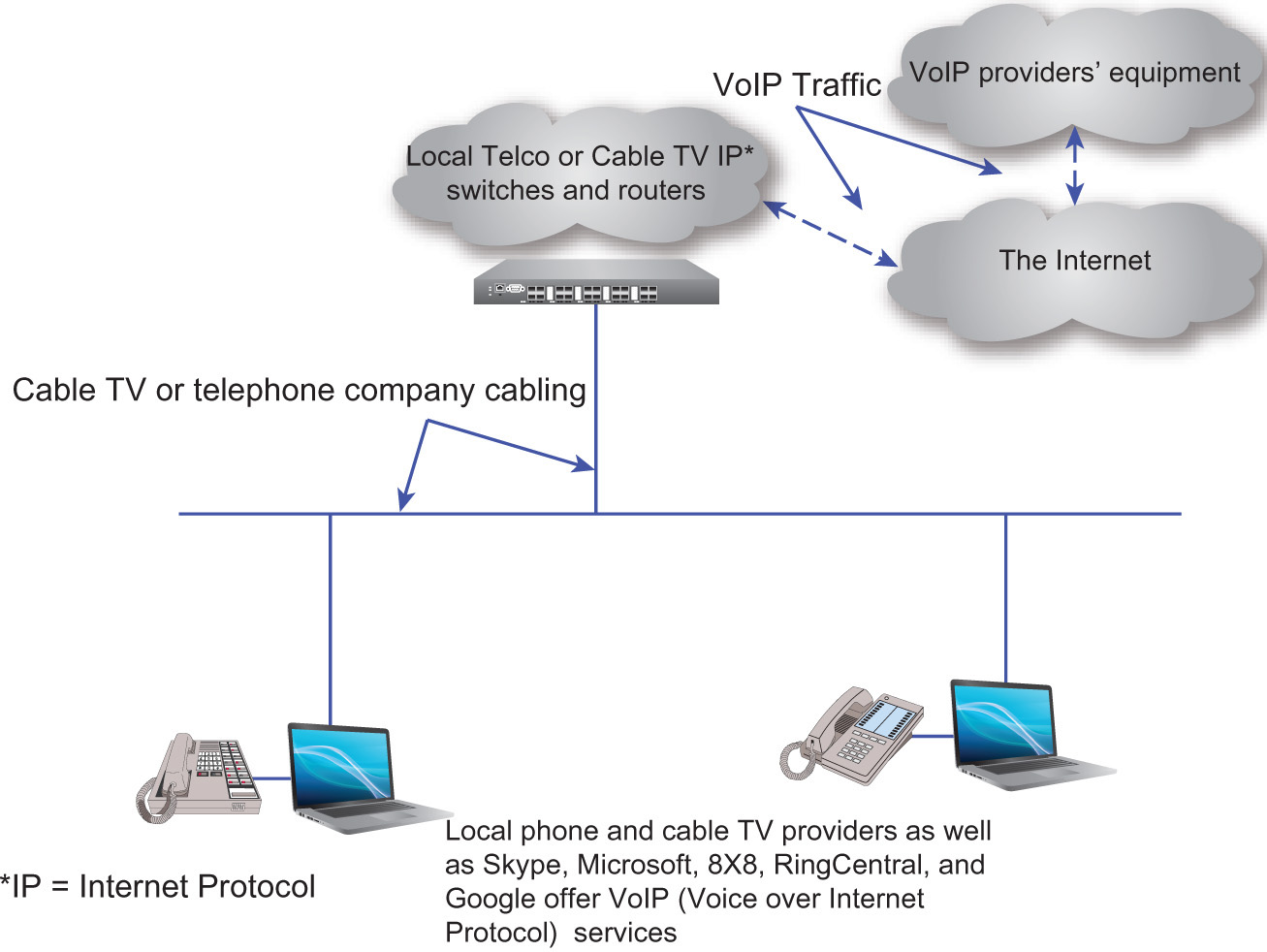
Figure 5-1 Transmitting Voice over IP traffic (VoIP) on carriers’ infrastructure.
VoIP for Very Small Organizations
Very small organizations and start-ups with fewer than 25 employees often use services from companies such as Google, Skype, and Vonage that have been adapted for business to replace traditional, on-site telephone systems. For example, features might include the ability to transfer calls to another employee in the same facility or in a remote office. The features provided also include a fixed, single phone number for mobile devices, work phones, and home phones, with a single voicemail box for messages from these three types of devices. It can also include audio and video conferencing. Some of these features were previously only available for large organizations with complex, onsite phone systems.
These VoIP services enable organizations to develop a new business or service without purchasing hardware for a telephone system. In addition, the services can be used for businesses in which all or many of their staff members work at home or in remote offices.
Even midsize and large organizations with their own onsite telephone systems often use these network-based VoIP services for certain functions. One of the most common functions is desktop video conferencing from Microsoft Teams or Google. Desktop videoconferences are transmitted over data networks, and they typically require nothing more in terms of equipment than the personal computers or laptops of the participants. In particular, people working from home or traveling can participate in these conferences, incurring minimal or no charges. Consumers and small organizations still use Skype, but large organizations are transitioning to Microsoft Teams.
The Impact of VoIP and Wi-Fi on Traditional Carriers
Consumers and business people alike use Skype, social media features, and Wi-Fi via cell phones to call home and the office when they travel. The savings are significant when travelers use these low-cost services to call their home or business from international sites. In addition, many immigrants and international students use video and audio calling to stay in touch with family members in their native countries. Using these services for free or low cost video conferences is particularly meaningful as people see facial expressions, and grandparents and close relatives stay in touch with grandchildren with firsthand images of them as they grow.
In addition, social network apps WhatsApp, Weibo, Weixin (WeChat in English), QQ, and Viber provide low-cost or free international calls. Moreover, international calls on certain mobile phones are free if they’re made over Wi-Fi networks. Calls over Wi-Fi are particularly cost-effective on international calls.
The Demarcation Point at Which Telephone Companies Wire Trunks
The local telephone company brings telephone lines into buildings and wires them to interfaces. The interface is called a jack or a punch-down block. Each outside line is punched down (wired) to the connecting block. RJ11c jacks connect one line per jack. The RJ stands for registered jack. These are the jacks found in most homes. The RJ21x, which holds 25 lines, is the interface to which local telephone companies wire multiple, outside lines in businesses. The RJ21x jack is a point from which telephone lines and trunks can be tested. For instance, if there is a question with regard to where a problem lies, the telephone company can test its trunk to the RJ21x jack, and the equipment vendor can test service between the equipment or router and the interface. The RJ21x jack is the demarcation point between the telephone company line and the inside wiring.
The most common data jack is the RJ48 jack. Data trunks such as Carrier Gigabit Ethernet terminate on these connectors. Both these jacks are at customer premises, and they are the points at which telephone companies test trunks if there is an outage. The most common type of high-speed trunk for incoming customer contact centers is Carrier Gigabit Ethernet for data. Information on these services is in Chapter 4, “Managing Broadband Networks.”
Multi-Protocol Label Switching for Interoffice Connections
Multi-Protocol Label Switching (MPLS) is a Virtual Private Network (VPN) network service that large and midsize organizations deploy to link their domestic and international sites together. MPLS traffic is carried on a provider’s core private data network rather than on the Internet. MPLS is suitable for transmitting packetized voice (VoIP), video, and data between sites. MPLS is starting to be replaced by Wide Area Software Defined Networks (WA SDNs) services, which have more capacity and flexible treatment by type of content, as well as flexible, real time routing. An example is Comcast that no longer offers MPLS and is promoting WA SDNs instead for enterprise customers.
MPLS Virtual Private Network—A Managed Service
MPLS provides VPN (Virtual Private Network) features. VPNs have the features and functionality of private networks. However, unlike private lines, which are not shared and are for the exclusive use of a single organization, MPLS operates on network links shared by other customers. The links are virtually private, and offer many of the features found on private lines such as user control and privacy. In addition, they are less costly than private lines to lease and operate.
MPLS has the capability to classify traffic so that voice and video have higher priorities than services such as file transfer and e-mail, which are less sensitive to delay. Because of these and other capabilities managed by providers, MPLS is also referred to as a managed network service.
Routes and Security on MPLS
MPLS is inherently more secure than using the Internet for site-to-site traffic and access to other networks because it is transmitted over a carrier’s private data network. For added protection from hackers, customers often use separate circuits to access MPLS circuits and the Internet. This is more costly than combining access to both services on the same line, but it isolates MPLS transmissions even further from viruses and attacks sent over the Internet. Figure 5-2 illustrates an example of segregated circuits for Internet access and MPLS service.

Figure 5-2 Implementing separate access to the Internet and a Multi-Protocol Label Switching (MPLS) network.
MPLS minimizes traffic jams by selecting the shortest, least-congested route for all messages in each transmission. All packets in every message are sent over the same route. In contrast, in WA SDN networks, each packet can travel on a different path, depending on congestion or network failures.
MPLS Implementation
When customers sign up for MPLS service, they give their provider a list of the IP addresses associated with each site that they want included in their MPLS service. Each IP address identifies a specific location on a network. The carrier uses this list to define a closed group of sites that are allowed to communicate with one another over the MPLS network. The list can be amended by notifying carriers of IP addresses to be added or deleted.
In addition to an IP address, each location connected to the MPLS network requires an access line from the customer to the carrier’s network. However, a single link from each location can transmit messages to all sites. Each location does not need a separate physical connection to every other site on the MPLS network. The MPLS service is referred to as an any-to-any network.
Note
MPLS for Multinational Locations
Internationally, most large providers have a presence in Europe, the United States, the Middle East, and parts of Asia. However, they have less presence in fewer Latin American cities, and the lowest presence in Africa. The term presence means that they have a switch in a local provider’s Point of Presence (POP). A POP is the physical building in which a telephone company’s switch (central office) is located. The POP is connected to the Internet as well as to other central offices that are located close to customers.
For remote countries in which carriers have a switch, large carriers including Verizon and AT&T have agreements with local providers. These agreements specify the type of circuit (local access line) from the customer to the local provider’s network and at what price the local provider will lay cabling from the distant office to the MPLS carrier’s switch. MPLS carriers place orders with local providers for access lines to the remote offices of MPLS customers. This creates international MPLS networks.
An issue in designing MPLS networks for international organizations is that rural and sparsely populated areas often don’t have MPLS available from the same carrier that installs the service for the rest of the enterprise. (Because of technical and network management incompatibilities, MPLS requires that the same carrier supply end-to-end service for each site on the network.) This is particularly problematic in underdeveloped areas such as parts of Africa and outside of most populated cities in Latin America.
Prioritizing Traffic via Classes of Service
When customers want to differentiate certain traffic for specific treatment, they select from their carrier’s list of classes of service. These classes of service are used to define the priority given to traffic for each class. For example, there might be three classes for data, one for voice, and another (the most expensive) for video. Voice and video are generally assigned higher priorities than data. Routers at customer sites add bits to packet headers with Class of Service (CoS) designations. At the MPLS edge router, these designations are added to the MPLS labels, along with addressing data.
Some organizations use the lowest-priced CoS for most data and higher-priced CoS for database lookups. This can vary by industry. Retail organizations that depend on point-of-sale credit card lookups for revenue might assign these applications the highest priority. Carriers apply CoS according to tags attached to packets for each protocol. Routers attach a different type of tag to packets containing e-mail messages from those that contain video. Carriers that don’t meet these SLAs generally rebate agreed-upon credits to customers.
MPLS Service Components
In addition to classes of service, customers also specify the following:
 A port speed at the provider’s POP, often at a lower speed than their access line. The port speed refers to the number of bits per second that can enter the carrier’s network.
A port speed at the provider’s POP, often at a lower speed than their access line. The port speed refers to the number of bits per second that can enter the carrier’s network. Additional managed services including managed security, and the use of the provider’s network and staff for operating, setting up, and managing the videoconferences.
Additional managed services including managed security, and the use of the provider’s network and staff for operating, setting up, and managing the videoconferences. The speed of the access line, which is the circuit connecting the customer to the provider’s network. Typically, remote offices use slower-speed Gigabit Ethernet; higher-trafficked headquarters use Carrier Gigabit Ethernet at speeds ranging from 100Mbps to 400Gbps. Higher-capacity services cost more than slower services.
The speed of the access line, which is the circuit connecting the customer to the provider’s network. Typically, remote offices use slower-speed Gigabit Ethernet; higher-trafficked headquarters use Carrier Gigabit Ethernet at speeds ranging from 100Mbps to 400Gbps. Higher-capacity services cost more than slower services.
IP Virtual Private Networks over the Internet
Internet Protocol Virtual Private Networks (IP VPNs) provide the features of private dedicated links, without the cost of leasing dedicated circuits from ISPs or leasing MPLS. Rather, each location leases a line connected to the Internet from the local telephone company. These leased lines use IP VPN technology for site-to-site links, access to the cloud, and for remote access from:
 Branch offices
Branch offices Employees’ homes to access computer files at headquarters
Employees’ homes to access computer files at headquarters Other cities in which employees are traveling
Other cities in which employees are traveling
Using IP VPNs between Offices—Less Costly than MPLS
Organizations use IP VPNs to link sites together so that remote offices can share resources such as centrally located e-mail, Internet access, and applications. A particular difference between IP VPN, SDN, and MPLS services is that organizations that use IP VPNs only pay for Internet access. This is a major cost advantage in favor of IP VPNs. Some companies do pay carriers for security services to screen incoming traffic for viruses. However, IP VPNs do not offer Quality of Service (QoS) or Class of Service (CoS). Thus, voice, video, and remote desktop traffic are treated the same as e-mail messages.
However, IP VPNs do not guarantee quality of service (QoS). If there’s congestion, packets are dropped. IP-based networks such as the Internet are connectionless. With connectionless networks, each packet is transmitted as a separate entity. Unlike MPLS, a path is not saved in the network for the entire transmission. Rather, every packet can take a different route, and if there is congestion on a particular route, packets are dropped. The router at the receiving end reassembles packets into their original form, minus the dropped packets.
Real time applications such as voice, video, and remote desktop access are more vulnerable to dropped packets than e-mail messages. E-mail messages don’t have the urgency of delivery and gaps between delivery of parts of e-mails are not noticeable. However, dropping parts of voice or video streams can result in choppy voice and video with noticeably poor quality. As more long form video traffic is sent over the Internet from mobile devices and landline facilities, the likelihood of congestion and dropped packets increases.
Another issue with IP VPNs is that they are not inherently secure. Thus, organizations add security protocols to IP VPNs, bits at the beginning and end of each packet to hide packet content from snoopers and hackers. The main security protocols used in conjunction with IP VPNs are described below in the section “Adding Security on Traffic Sent Over IP VPNs.”
Avoiding Congestion on IP VPNs—Access to the Internet Service Provider
The most common points of congestion in IP VPNs are the access lines connecting organizations to the Internet and points in the Internet where carriers connect their networks together. Organizations can add capacity to their headquarters and branch office access lines, but they have no control over capacity on the Internet itself. If an organization experiences congestion on its access circuits, it has the option of adding access lines or increasing the capacity of its existing access circuits. It can upgrade to Carrier Gigabit Ethernet from slower data rate megabit Ethernet.
In addition to monitoring and upgrading access circuits, where possible, organizations lease Internet access from the same provider at all of their sites to limit the number of carriers from whom they get service. This is not possible in remote and international areas where the primary carrier does not provide coverage.
Adding Security on Traffic Sent Over IP VPNs
Because the Internet is open to users from all over the world, organizations deploy security software designed to protect information from snoopers. Most security protocols on IP VPNs employ tunneling and encryption. Tunnels surround packets with bits that protect privacy on the packets, and encryption uses complex mathematical algorithms to scramble bits so that only matching protocols at the receiving end of the transmission can unscramble (decrypt) the bits into readable formats. Virtual Private Networks have many of the features of private lines dedicated to single organizations, but they are not dedicated to single enterprises in a carrier’s private network. They are sent over the Internet where they share capacity other data sent over the Internet.
Security Protocols on Access to IP VPNs
Security protocols designed for IP VPNs all create a tunnel for their transmission. Tunnels are special bits at the beginning and end of each packet. In essence, the tunnel encapsulates messages so that others cannot see what is being transmitted.
Tunneling protocols establish a secure connection between the corporate Local Area Network (LAN) and the remote user by encrypting and tunneling the bits and hiding the IP header in each packet. This ensures privacy. Tunneling prevents hackers from learning corporate LAN IP addresses. Specific protocols encrypt packets to further protect their privacy. Encryption is the use of a complex mathematical algorithm to reorder bits so that only the receiving end with matching encryption is able to decipher and read them.
To access the corporate network, customers with broadband services log on to the public Internet. From there, traffic is routed to the Internet and then to the megabit or gigabit dedicated access line connected to their remote place of business. For organizations that allow remote access to headquarters applications and files, remote users are routed via the Internet to the organization’s headquarters, as indicated in Figure 5-3.

Figure 5-3 Secure access to headquarters’ files over an IP VPN with tunneling protocol to protect data transmitted over the Internet.
The most common security protocols on access networks are the following:
 Internet Protocol Security (IPsec) This is an older security protocol that requires software to be installed in every computer that accesses the network remotely.
Internet Protocol Security (IPsec) This is an older security protocol that requires software to be installed in every computer that accesses the network remotely. Layer 2 Tunneling Protocol (L2TP) This protocol evolved from an earlier protocol Point-to-Point Tunneling Protocol (PPTP) developed by Microsoft; it has stronger authentication security for screening devices that access the network. L2TP is also used with IPsec.
Layer 2 Tunneling Protocol (L2TP) This protocol evolved from an earlier protocol Point-to-Point Tunneling Protocol (PPTP) developed by Microsoft; it has stronger authentication security for screening devices that access the network. L2TP is also used with IPsec. Transport Layer Security (TLS) This is a newer access method that does not require client software. The earlier version was Secure Socket Layer.
Transport Layer Security (TLS) This is a newer access method that does not require client software. The earlier version was Secure Socket Layer.
The Complexities of Using VPNs with IPsec
Internet Protocal Security (IPsec) is a protocol that requires users to install IPSec software on their devices. IT staff members distribute software to each person’s computer. (They also handle calls from employees who are having trouble logging on to the VPN or who have lost their laptop or smartphone.) Employees can only access their e-mail and other applications from their own computer or supported mobile smartphone, such as an Android or iPhone.
Users work with IPsec client software installed on their computers launch the remote access client. Client software enables access to applications located on other computers or servers, usually in data centers or the cloud. It is supplied and licensed by the organization that develops the IPsec software. The client software is a special program written to interact with security software located in the data center and cloud.
Layer 2 Tunneling Protocol
Layer 2 Tunneling Protocol (L2TP) initial versions from Microsoft do not provide encryption and are often replaced by up-to-date versions. There is a new version of L2TP that has improved its tunneling. Like PPTP, it is also used with IPsec for encryption. In addition, IPsec has stronger authentication than L2TP.
Secure Sockets Layer/ Transport Layer Security
Secure Sockets Layer (SSL)/Transport Layer Security (TLS) is a newer VPN protocol than IPsec. SSL/TLS is a clientless protocol; that is, it does not require the installation of client software on each computer that’s used for remote access. Rather, SSL/TLS works from within standard browsers on computers and smartphones. This makes VPNs easier to use and requires less administrative support from IT personnel. The simplified login results in fewer user errors. Recent releases of SSL are referred to as Transport Layer Security (TLS). For added security, SSL is frequently used with tunneling protocols.
Because it is a higher-level security protocol, SSL installed on appliances can enable access to particular applications based on privileges granted to classes of employees. An appliance is a specialized computer that is dedicated to a particular application.
It’s possible for remote computers to pass viruses to corporate networks, so some SSL appliances have the capability to scan remote computers for antivirus software and automatically download patches to computers that don’t have the latest security updates. Other appliances have the capability to remotely wipe out passwords and corporate data from shared computers in public areas such as libraries and airports. This eliminates the possibility of computers in locations such as kiosks to store and pass on private information and passwords.
Adding Additional Layers of Protection with Two and Three-Factor Authentication
Most remote access requires two- and sometimes three-factor authentication. Two-factor authentication requires a password plus a way to identify that the user is who he or she claims to be. Two-factor security is a safeguard that prevents unauthorized users from using stolen passwords, social security numbers, or birthdays to log into files. Three-factor authentication might require a token ID in addition to a password plus biologic identification. A hacker with a stolen password would most likely not have the means to be authenticated. Authentication refers to the requirement that users prove to computer systems that they are who they claim to be and are authorized to log on to the network.
Security software at the user’s organization issues prompts for usernames, passwords, and a form or multiple forms of authentication such as:
 A token ID (identification), which is a small dongle with a screen, which can be attached to a key chain. Random numbers that change about every 60 seconds appear on the token’s screen and are typed into the users’ screen for access to the cloud, a secure area such as a lab, or particular files.
A token ID (identification), which is a small dongle with a screen, which can be attached to a key chain. Random numbers that change about every 60 seconds appear on the token’s screen and are typed into the users’ screen for access to the cloud, a secure area such as a lab, or particular files. A security app from iPhone, Amazon, or Google requesting a user ID and password plus a code sent by Apple, Amazon, or Google.
A security app from iPhone, Amazon, or Google requesting a user ID and password plus a code sent by Apple, Amazon, or Google. A text message with a code sent to a user’s phone that the user types in to gain access.
A text message with a code sent to a user’s phone that the user types in to gain access. Biologic authentication such as a fingerprint, iris, or facial recognition scan.
Biologic authentication such as a fingerprint, iris, or facial recognition scan.
To prevent remote users from passing viruses from the Internet to corporate networks, the client software will often not function if there is an open connection to the Internet while the user is logged on remotely.
Deploying Firewalls to Protect against Malicious Attacks
A firewall is a device, software application, or set of devices at carriers, enterprises, and homes that screens incoming and internal traffic to prevent hackers from accessing files. Firewalls deny hackers access by allowing only designated users to access networks. In an organization’s network, firewall software is installed on routers and appliances. For additional protection, organizations that use their carrier’s firewall protection have onsite firewall protection, as well.
Firewalls provide networks partial protection against Distributed Denial-of-Service (DDoS) attacks and intrusion. They use various techniques including address filtering, which looks at a user’s IP address and accepts or rejects messages based on that address. Important applications might contain their own firewalls for extra protection. Communications can also be restricted to certain addresses. Firewalls contain hundreds of ports and can filter on a port-by-port basis. In addition, they can be programmed to recognize applications and content and pass them through the firewall using a specific port. However, even with these filtering capabilities, DDoS attacks can congest access to the organization’s files.
Firewall ports can be virtual as well as associated with physical equipment within the firewall. A virtual port is programmed to allow certain traffic such as VoIP calls to pass through the firewall to its destination. A virtual port is represented in software.
Because employees use their laptops at home to surf the Web and then bring them into work, corporations monitor internal transmissions as well as communications from the Internet. Many organizations program employees’ remote computers to reach only locations on the Internet deemed secure to avoid contamination from Internet locations that have viruses that can spread to the corporate LAN.
Firewalls don’t protect against, for example, new (black day) viruses and all e-mail spam. Corporations often subscribe to security services that keep them posted about new software attacks. The security software monitors their networks for unusual amounts or types of traffic and downloads software patches for protection against new types of attacks.
Safeguarding Privacy and Intellectual Property by Employing Property Data Loss Management
Organizations are legally obligated to protect the privacy of their employees. There are privacy statutes that prohibit enterprises from sharing employee and customer personal information such as Social Security numbers, license numbers, credit card data, and data collected by human resources. In addition, companies need to protect their strategic plans, medicine formularies, and product designs from leaking. These assets are considered intellectual property.
To accomplish these goals, organizations use property data loss management software to scan outgoing e-mail. The software is programmed to flag specific words relating to their products or services as well as key phrases or formats which indicate that credit card data, social security numbers, or license numbers are included in a message. Flagged messages can be manually scrutinized. To protect privacy, enterprises and universities may have policies limiting which computers store private information such as social security numbers.
Managed Services
Managed services are add-on consulting, cloud-based, or software services that carriers offer customers. These offerings are intended to supplement carriers’ long distance and local calling service revenues. But an important goal is to make it more difficult and complex for customers to change providers. Managed services are considered “sticky.” The more managed services that customers use, the more dependent they are on carriers, and the more complex it is for these customers to change providers.
Managed Services Rather than Dumb Pipe Providers
Many carriers view broadband offerings such as private data lines, MPLS, and Gigabit Ethernet (GigE) as commodities available from other providers. To avoid being organizations whose only offerings are characterized as dumb pipes with commodity services, carriers often distinguish themselves from competing carriers by offering specialized and managed services. Without distinguishing features, customers can shop around for the lowest price on, for example, Gigabit Ethernet.
Managed services are one way that carriers differentiate themselves from smaller competitors. Moreover, managed services provide an additional monthly revenue stream for carriers and help to cement the relationship between themselves and their customers. This is because it is complex and potentially disruptive for international enterprises to change both their network and their security provider or data center service across all of their sites. Thus, supplying this wider range of services creates a “stickier” relationship with customers, and a sticky customer is one that is less likely to change vendors.
In addition, carriers such as Verizon, Sprint, and AT&T have the resources to build international data centers and hosting facilities as well as hire consultants with specialized skills in developing applications for vertical markets such as healthcare, transportation, and insurance.
Managed Services—For a Variety of Functions
Carriers have long offered managed services in conjunction with the networking devices connected to broadband services. In addition to managing servers, routers, and modems, they now offer to manage the NFV (Network Function Virtualization) hardware containing routers, firewalls, and security applications represented as software in off-the-shelf servers. The NFV server is connected to a customer’s broadband circuits. Carriers additionally offer more complex, varied services in the hope that customers will be attracted to the possibility of one provider managing their wide area, mobile, Wi-Fi, and computer networks. These offerings include the following:
 Hosting applications in carrier data centers
Hosting applications in carrier data centers Storing and backing up files remotely
Storing and backing up files remotely Developing software applications to be run in carrier data centers
Developing software applications to be run in carrier data centers Operating room type video conferences
Operating room type video conferences Security consulting
Security consulting GPS tracking solutions for fleet management
GPS tracking solutions for fleet management Consulting on call center services
Consulting on call center services Managing outsourced data centers at carrier facilities
Managing outsourced data centers at carrier facilities Providing and designing interactive voice response services with menus such as:
Providing and designing interactive voice response services with menus such as:– Press 1 for Sales
– Press 2 for Marketing
 Offering security services that protect against Distributed Denial of Service attacks and viruses
Offering security services that protect against Distributed Denial of Service attacks and viruses Connecting to cloud computing sites
Connecting to cloud computing sites Storing data in the cloud
Storing data in the cloud Managing employee mobile devices
Managing employee mobile devices
In conjunction with managed services, carriers have personnel who have expertise in particular managed services for wireline as well as mobile networks. These include experts in enterprise mobile devices, video conferencing, security, data centers, contact centers, and wireless LANs (Wi-Fi networks).
Many carriers that own mobile and landline networks recognize the potential of mobile services. Their sales staff who were previously dedicated to only landline or only mobile products and services now sell products and services for both mobile and landline networks. They actively promote mobile managed services that improve productivity such as developing applications for service organizations that dispatch technicians to homes or businesses. When a carrier’s account staff determines that there might be a mobile application to increase productivity, it brings in experts to meet with its customer. After learning about the customer’s needs, these experts propose a consulting service to develop a software application to address those needs.
Digital Subscriber Line—Distance Limitations; Operates on Copper Cabling
Local telephone companies introduced Digital Subscriber Line (DSL) technology in 1989. The telephone companies saw the advantage of using existing copper cabling to combine voice and data on the same copper cabling that was ubiquitous in developed countries. However, DSL has capacity and distance limitations that make it less suitable than transmissions now available over fiber cabling. Higher capacity broadband technologies are replacing DSL in areas with fiber-optic cabling.
How DSL Technology Works
DSL operates over the same copper cabling used for voice in last-mile networks close to homes and small businesses. Very-High-Data-Rate DSL (VDSL) gear supports high-definition TV, voice, and Internet access over short lengths of copper cabling. The most advanced DSL service, VDSL2, supports 200Mbps on cable lengths up to 1,000 feet. The copper cabling transmits these signals between a user’s premises and a provider’s fiber-optic cabling in cabinets or neighborhood nodes. (See Table 5-4 in the “Appendix” section at the end of this chapter for information on the types of DSL.)
DSL Limitations
On copper cabling, background noise intrudes, or “leaks,” from adjacent copper wires (crosstalk) or a nearby electric motor (electromagnetic interference). To prevent transmission degradation and speed loss, equipment on advanced DSL services constantly monitor the line for noise. Monitoring is complex because noise can change over time.
DSL services over higher frequencies carry more bits in shorter time spans than lower frequencies. Think of it in terms of a commuter subway system:
 If the trains don’t come very often (low frequencies), fewer people are moved in a given span of time;
If the trains don’t come very often (low frequencies), fewer people are moved in a given span of time; If the trains arrive more often (higher frequencies), more people will be moved through the system in the same time period.
If the trains arrive more often (higher frequencies), more people will be moved through the system in the same time period.
Both copper cabling used for DSL and wireless services carry signals that are made up of wavelengths (frequencies). Low frequencies have longer wavelengths that can carry signals over greater distances. High frequencies have shorter wavelengths that do not travel as far, but they can squeeze more bits into each transmission.
To achieve greater capacity, DSL must use high frequencies. However, the shorter wavelengths render high-frequency signals more vulnerable to damage from environmental sources such as magnetic interference. At the same time, vulnerability to attenuation (weakening and fading) means that high speeds are supported only on short lengths of copper cabling. Some carriers use bonding to increase the capacity on DSL. Bonding also has the advantage of increasing the length of cable over which high frequency DSL signals can travel before they fade.
Note

Figure 5-4 An example of bonding two DSL circuits together to double its capacity.
Replacing DSL with Higher-Capacity Fiber and Wireless
Carriers are replacing DSL because of its lower capacity and because enterprises and residential subscribers require higher broadband capacity to access cloud-based applications, stream video, make purchases, and access social networks. Carriers are replacing DSL with Gigabit Ethernet wherever increasing amounts of fiber cabling are available. In rural areas they are replacing DSL with fixed wireless to reach customers.
Carrier Gigabit Ethernet
Carrier Gigabit Ethernet (GigE) is a site-to-site and Internet access high-speed service. Gigabit Ethernet uses the Ethernet protocol to reach Gigabit capacity on broadband networks. It operates over fiber-optic cabling. GigE transmits data, video, images, and packetized voice (VoIP). It is the most commonly used broadband technology for enterprises.
Carrier GigE was first introduced in the late 1990s. At that time, it was not widely available, both because it required fiber-optic cabling to the customer and because the central offices of providers were not widely equipped with GigE switches. In contrast, carriers now offer GigE services to small and medium-sized organizations as well as large ones. GigE is now more widely available because more central offices have been equipped to support it and fiber is more widely deployed to business customers. These services start at speeds of 10Mbps and currently scale up to 100Gbps. Capacity is expected to increase to 400Gbps in the future. Facebook and Google are experimenting with 400 Gigabit Ethernet in the WAN.
Bandwidth demand by all types of organizations has created the impetus for carriers to invest in gear that meets this demand. Customers that previously used T3 service now have either Megabit or Gigabit Ethernet. Smaller organizations can order the slower Ethernet service of 20, 30, or 60 megabits with the option to easily upgrade later. Moreover, most carriers including Windstream, Verizon, and AT&T have retired all non-Ethernet services including T1 and T3 services.
Carrier Gigabit Ethernet Flexibility and Scalable Speeds
Gigabit Ethernet is offered by carriers for accessing the Internet, MPLS networks, and connections to other sites within cities. When used for accessing these networks, enterprises might use GigE at their headquarters. At remote sites, depending on the level of traffic at each site, slower data rates might be adequate. See Figure 5-5 for an example of Carrier Gig-E at a multi-site organization. Importantly, once Carrier GigE is installed, enterprise customers can request that their telephone company provider increase or decrease the capacity of their service remotely. This is done by modifying data rates remotely at the central office. Cabling does not have to be changed and most customers’ Carrier Ethernet switches can be programmed for added capacity. Because there are few requirements for technicians onsite to make changes, GigE is less costly to support than the older T1 and T3 services.

Figure 5-5 Carrier Ethernet in between buildings on a campus.
Organizations with many buildings within cities also use GigE for point-to-point private lines within the metropolitan area. See Figure 5-5 for Ethernet links between buildings in a campus. These organizations include large hospitals, universities, and government offices that use GigE to transfer large files between sites. One example is the connection between hospitals and the facilities where patient records and imaging files are stored. It is also used for connections to storage area networks (SANs) that hold backup files. Access to the backup files is via either the Internet or private lines. Finally, higher level services such as WA SDN services are carried on Carrier Gigabit networks. For an over view of broadband network services see Table 5-2 in the “Appendix.”
Dedicated Wavelengths
Organizations with high-capacity requirements often lease an entire wavelength on fiber optical cabling. The entire bandwidth of a dedicated wavelength is reserved for a customer. It is not shared with other organizations. Dedicated wavelengths may be used for connections to cloud services, between companies’ offices, at large data centers, carrier hotels, and long-haul networks that run between cities and between countries. Passive optical network service NG PON2 supports dedicated wavelength service. For information on NG PON, see Table 4-1, “PON Standards,” in the “Appendix” of Chapter 4. Dedicated wavelengths support gigabit and terabit speeds. A terabit is equal to 1,000 gigabits. Dedicated wavelengths are used in 5G cellular networks to connect small antennas to each other. See Chapter 7 for information on 5G cellular service.
T1 and T3: Services Largely Replaced by Higher-Capacity Broadband
T1 service is a digital broadband technology that utilizes a multiplexing scheme, which enables one circuit to carry 24 voice, video, or data channels. The entire circuit runs at 1.54Mbps. T3 is also able to carry a variety of traffic types but operates at 44Mbps. E1 and E3 are the multiplexed services used in Europe. Ethernet, where it’s available, is largely replacing T1 and T3 because it provides a more scalable solution and is not limited to 44Mbps.
In the United States, AT&T and Verizon no longer support T1 and T3. They are gradually replacing them with Carrier Gigabit Ethernet, which is not limited to 44Mbps and has more flexible speeds, and is less costly for telephone companies to support.
TDM Shortcomings—Wasted Capacity, Higher-Support Costs
Each device that communicates over a T1 or T3 line is assigned a time slot. If there are eight telephones or computers contending for any of the above channels, a time slot is saved for each telephone and computer for the duration of the particular telephone call or data session. Telephone or computer device 1 might be assigned time slot A; telephone or computer 2, time slot B; and so forth. During pauses in voice conversations, the slot is not assigned to another computer. The assigned time slot is transmitted without any information. These idle time slots result in wasted capacity. For this reason and because TDM capacity is limited to 44Mbps, TDM is not efficient for the higher capacities required for cloud and broadband services. In a network with millions of time slots, empty time slots result in many idle time slots and wasted bandwidth.
T1 and T3 – Costly to Support and Install
In addition to its lack of flexibility and capacity, T1/T3 service is costly for telephone companies to support. This is mainly due to the cost of equipment in the central office required for timing and the interfaces at customers, which providers support. These issues increase costs for space at the telephone company central offices, as well as installation, repair, and maintenance expenses. For details on T1 and T3 Digital Signal Levels See Table 5-3 in the “Appendix.”
Network Topology on Dedicated, Private Lines
As the name implies, private lines are those dedicated to a single institution; not shared by various organizations. In contrast to IP VPNs, the transmissions are not sent over the Internet. Private lines are used by organizations such as financial institutions, armed forces, weapons suppliers to armed forces, and government agencies that require the highest levels of security on transmissions to other sites. Other than these institutions, private lines dedicated to individual organizations have been largely replaced by newer, less costly and easier-to-maintain and configure MPLS, VPN, and WA SDN offerings. Network topology refers to how devices and sites are connected to one another in networks. It is essentially the “view from the top.” Topologies include straight lines, hub-and-spoke designs, and mesh designs.
Dedicated Private Lines—For Greater Security
Dedicated services, also known as private lines, are circuits leased by enterprises for their exclusive use. Private lines are expensive, and the number of them used by commercial organizations has decreased dramatically. For all but the largest organizations, MPLS, WA SDN, and IP VPNs have largely replaced private lines. These are less costly to maintain and boast lower monthly lease rates. However, large enterprises, utilities, armed forces, weapons suppliers to governments, and financial services organizations still use high-speed private lines for applications such as money transfers because they are the most secure method of transmitting data. Most of these organizations have the expertise for the initial design and sizing of the dedicated network, ongoing maintenance, and redesign for new applications.
Dedicated Services in Wide Area and Metropolitan Area Networks
Dedicated, private lines are available for the exclusive use of the customer that leases them from a network service provider. Large organizations such as the Department of Defense, large cloud computing organizations, and pharmaceutical companies connect their multistate sites via circuits running at 100 gigabit and greater data rates.
Metropolitan Area Networks (MANs), which are a type of Wide Area Network (WAN), consist of private lines that connect buildings within a city or metropolitan region. Large hospitals transmit customer records, research files, and radiology images over MANs; major universities also use them.
Private lines have the following characteristics.
 Fixed monthly fees Private, dedicated links are priced at flat monthly fees. The fees are not based on minutes used or the amount of data transmitted.
Fixed monthly fees Private, dedicated links are priced at flat monthly fees. The fees are not based on minutes used or the amount of data transmitted. Fixed, inflexible routes Dedicated lines are not flexible. Calls and data can only be sent between the fixed points to which the lines are connected. Thus, communication with a site that is not on the network is not possible.
Fixed, inflexible routes Dedicated lines are not flexible. Calls and data can only be sent between the fixed points to which the lines are connected. Thus, communication with a site that is not on the network is not possible. Exclusive use Only the organization that leases private lines can use them. For example, companies with dedicated connections to video conferencing equipment can only hold video calls with organizations that are a part of their private network.
Exclusive use Only the organization that leases private lines can use them. For example, companies with dedicated connections to video conferencing equipment can only hold video calls with organizations that are a part of their private network. Voice, video, and data Dedicated lines are suitable for transmission of video, voice, and data. These services can share the same dedicated services or they can use completely different dedicated lines.
Voice, video, and data Dedicated lines are suitable for transmission of video, voice, and data. These services can share the same dedicated services or they can use completely different dedicated lines. Fixed capacity Dedicated services are leased or built from carriers such as AT&T, Verizon, or CenturyLink with a fixed capacity or bandwidth. These speeds range from a low 10Gbps to higher Gigabit Ethernet speeds.
Fixed capacity Dedicated services are leased or built from carriers such as AT&T, Verizon, or CenturyLink with a fixed capacity or bandwidth. These speeds range from a low 10Gbps to higher Gigabit Ethernet speeds. Security GigE is used in large, private networks operated by entities such as financial firms and the military for data communications between sites. Some organizations feel that the extra fees and maintenance are justified. Private networks are more secure than even MPLS networks for transmitting sensitive military information and financial transactions.
Security GigE is used in large, private networks operated by entities such as financial firms and the military for data communications between sites. Some organizations feel that the extra fees and maintenance are justified. Private networks are more secure than even MPLS networks for transmitting sensitive military information and financial transactions.
An important factor when deciding to use dedicated services is the desire for secure transmissions. Some firms believe that network services such as MPLS are too public or prone to hacking for confidential applications such as funds transfer. They want to control their own networks and have staff members available to monitor transmissions over these facilities. Additionally, encryption is used to further ensure privacy and security.
Local and Inter-Exchange Channels
Rates for private lines are based on distance and speed. Higher-speed lines that run over longer distances cost more than slower circuits that run over shorter distances. A 10 Gigabit line is less expensive than a 100 Gigabit line.
Pricing for dedicated, private lines consists of two items:
 Local channels Local channels run from a customer’s premises to the carrier’s equipment. One local channel is required at each end of the private line in a point-to-point circuit. Local channels are also referred to as local loops. The incumbent telephone company often supplies local channels. Because of limited competition for this service, pricing on these short links is often close to the same as that for the longer inter-exchange circuit. Local channel fees are also charged for circuits used to access the Internet, SDN networks, and MPLS networks.
Local channels Local channels run from a customer’s premises to the carrier’s equipment. One local channel is required at each end of the private line in a point-to-point circuit. Local channels are also referred to as local loops. The incumbent telephone company often supplies local channels. Because of limited competition for this service, pricing on these short links is often close to the same as that for the longer inter-exchange circuit. Local channel fees are also charged for circuits used to access the Internet, SDN networks, and MPLS networks. Inter-exchange miles Inter-exchange mileage is the portion of the circuit located within a carrier’s network. The mileage runs from the access point, where it enters the carrier’s network, to the egress point, where it leaves the carrier’s switch.
Inter-exchange miles Inter-exchange mileage is the portion of the circuit located within a carrier’s network. The mileage runs from the access point, where it enters the carrier’s network, to the egress point, where it leaves the carrier’s switch.
Organizations that lease T1 circuits for Internet access also pay for the local loop that connects their site to their carrier. The local loop is a private, dedicated service from the customer to the local provider. When traffic reaches the Internet, it is carried over a shared network. The same is true for access lines to VPNs.
Network Topologies—The View from Above
Topology refers to the way nodes or circuits in a network are connected together. For example, are all the locations or computers connected in a straight line? Are all devices or locations connected to a central headquarters? Can every location reach every other location without going through a central site?
Topology is a consideration in designing private lines in the following:
 Carriers design of networks
Carriers design of networks Organizations design of internal networks
Organizations design of internal networks Large enterprises leasing or building their own private, dedicated line networks
Large enterprises leasing or building their own private, dedicated line networks
The shape of the network (the configuration in which lines are connected to one another), impacts cost, the ability to scale (add or delete sites), reliability, and access to the lines.
Consider the multipoint configuration in Figure 5-6. An application for multipoint design is one used by utilities for communications to monitor the control equipment in their plants. They run fiber-optic cabling on their existing rights of way, over which signals are sent. If the link to one of the large sites is out of service, the other sites cannot reach the main location. However, in the mesh configuration presented in Figure 5-8, if one link is out of service, traffic can be rerouted over other links. There is a trade-off between designing and constructing the more reliable mesh networks that are more costly and simply using a less reliable multipoint configuration.
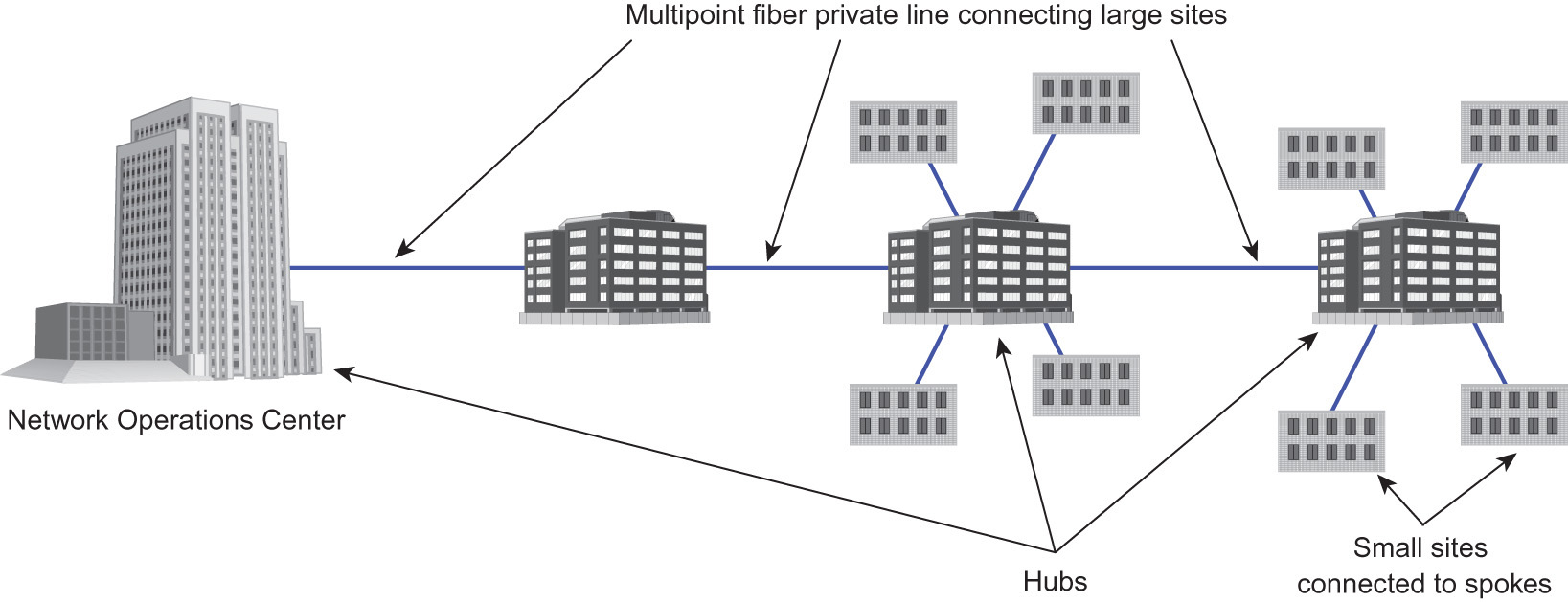
Figure 5-6 Multipoint private lines connecting large sites.
The following are common network configurations.
 Point-to-point One line connects two locations. An example is a hospital with a private line to a medical office where hospital doctors see patients.
Point-to-point One line connects two locations. An example is a hospital with a private line to a medical office where hospital doctors see patients. Multipoint One line connects more than two sites together. This is also referred to as multidrop.
Multipoint One line connects more than two sites together. This is also referred to as multidrop. Star (hub-and-spoke) All locations connect to, or “hub into,” a central site. Data switches in Local Area Networks (LANs) are configured in star topologies. Another example is a corporation with centralized e-mail, financial, and sales applications. If the central site, the switch, or headquarters crashes, all sites connected to it are also out of service. This is illustrated in Figure 5-7 with the sites connected by Carrier Gigabit Ethernet.
Star (hub-and-spoke) All locations connect to, or “hub into,” a central site. Data switches in Local Area Networks (LANs) are configured in star topologies. Another example is a corporation with centralized e-mail, financial, and sales applications. If the central site, the switch, or headquarters crashes, all sites connected to it are also out of service. This is illustrated in Figure 5-7 with the sites connected by Carrier Gigabit Ethernet.

Figure 5-7 A hub-and-spoke design for centralized applications such as e-mail. The disadvantage here is that if e-mail or another application at the central site crashes, all sites lose access to it.
 Secondary hub-and-spoke A secondary “hub” is wired to a central site and connects to a cluster of smaller locations. The secondary hub sends traffic from the small locations to the backup central site.
Secondary hub-and-spoke A secondary “hub” is wired to a central site and connects to a cluster of smaller locations. The secondary hub sends traffic from the small locations to the backup central site. Mesh design All points on the network nodes connect to one another in a flat or non-hierarchical manner. Peer-to-peer networks for music sharing are examples of mesh networks. Carriers often design their core, backbone networks in a mesh configured with multiple failover routes. Mesh networks are the most expensive because they require the most links. See Figure 5-8 for mesh topology.
Mesh design All points on the network nodes connect to one another in a flat or non-hierarchical manner. Peer-to-peer networks for music sharing are examples of mesh networks. Carriers often design their core, backbone networks in a mesh configured with multiple failover routes. Mesh networks are the most expensive because they require the most links. See Figure 5-8 for mesh topology.

Figure 5-8 A mesh network connecting all sites together.
Direct Dedicated Interconnections to the Cloud
Customers have a choice of accessing the cloud from the Internet or via a dedicated connection. To access the cloud via the Internet, residential and business customers log in via their same broadband connections from which they access the Internet. These connections are sometimes slower and can cause delays if there is congestion in the Internet. They additionally are not as secure as direct dedicated connections.
Large organizations with critical applications in the cloud often directly connect their locations to their servers and applications on the cloud. These direct interconnections can have capacity of 10 to 100 Gbps. The fact that the data is in the cloud or at a hosting center is seamless to end users because there are minimal delays. In this way they emulate connections within the building to internal data centers in the same organization. To ensure low latency, close to continuous uptime, and low mean time to repair problems, many companies sign a Service Level Agreement (SLA) with commitments from their interconnection provider, specifying the percent of uptime, mean time to repair, and the amount of latency in accessing the cloud. If the SLA conditions are not met, the customer has the option of discontinuing the service without a monetary penalty.
An additional option on dedicated interconnections is to bond multiple Gigabit Ethernet trunks together to double or triple the connection capacity. For example, Google supports bonding of up to eight connections to reach its services.
Amazon Web Services, Microsoft Azure, Oracle, and, Equinix all support direct, private interconnections to organizations’ cloud-based applications on their hosting and cloud data centers. Equinix and Coresite provide a service whereby multi-location enterprises connect to Equinix or Coresite from their main location. They both in turn connect enterprises to each of the cloud sites at which their applications are located. See Figure 5-9 for an example of direct interconnection to multiple clouds. This obviates the requirement for a separate connection directly to each provider’s site. In addition to minimizing latency (delays in getting responses to queries), direct dedicated connections provide more security and privacy than do Internet connections to cloud and hosting sites.

Figure 5-9 A direct connection to multiple cloud providers from corporate hub sites.
Session Initiation Protocol—Out-of-Band Signaling
SIP signaling is used for connections between telephone companies in:
 IP networks
IP networks Telephones connected to internal telephone systems
Telephones connected to internal telephone systems Trunks that carry traffic into enterprise locations.
Trunks that carry traffic into enterprise locations.
Using SIP Trunks for Caller Identification in Call Centers
Session Initiation Protocol (SIP) signaling is an IETF (Internet Engineering Task Force). It is used in broadband networks for connections between carriers and in on-premises telephone systems. Because SIP trunks carry signaling bits including those with the calling party’s names and telephone numbers, most call centers’ incoming calls are carried on SIP trunks. The telephone system captures the caller information and sends it to display-equipped telephones. Figure 5-10 illustrates a SIP trunk for transporting caller ID. Employees who receive heavy volumes of calls from vendors or who prefer to only take calls from certain callers use caller information on SIP trunks to screen calls. Unanswered calls are automatically forwarded into voice mail.

Figure 5-10 SIP trunks used in an organization to identify callers’ names and phone numbers. (Stock photo by Chun-Tso Lin/123RF)
Large call centers that use SIP trunks have an additional benefit—the caller ID data can be treated differently than the call itself. This is significant because it enables the telephone system to access information differently from the call. It can send the telephone number to a database that matches the telephone number to the customer account number. The data network sends the account number to the agent’s terminal to which the call is sent, which saves agents time by eliminating the need to key in account numbers.
Wide Area Software Defined Networks for Enterprises
In earlier generation networks, hardware—routers and switches—were key factors in operating local area and wide area networks. They were programmed to perform specific routing tasks such as routing packets to other networks. In software designed wide area networks (WA SDNs), software external to router and switching functions control the routing, switching, and other functions in the network. See Figure 5-11 for an overview of routing on WA SDNs. A controller is programmed with rules that are applied under specified conditions. For example, alternate routes are set up so that if there is congestion or a malfunctioning section, traffic is automatically sent over an alternate route. WA SDN is used to manage traffic at branch offices, headquarters, and data centers as well as in carriers’ core networks.

Figure 5-11 An overview of routing on Wide Area Software Defined Networks.
SDN software can be located in the cloud, or at the telephone company’s data center—within their CORD. CORD is short for Central Office Re-architected as a Data Center. For information on CORD, see the section “Central Office Re-architected as a Data Center (CORD)—Streamlined Central Offices” in Chapter 4, “Managing Broadband Networks.” Or, large enterprises may use WA SDN to manage traffic within their own broadband networks.
WA SDNs are used to invoke commonly used operations under specified conditions. For example, configurations for branch offices can also be defined and tested centrally before being downloaded to each location. In large organizations with many branch or warehouse locations, network configurations can be downloaded sequentially to each location once there are circuits installed at the locations.
An Application Program Interface (API) is used as an interface between external software and each device on the network that is configured for SDN. The API translates between external software on controllers and each device or service on the NFV server. NFV is a key element of WA SDNs.
The APIs used in WA SDNs are Open APIs. Open APIs are those which can be used by the public. They enable customers to access features in SDN from enterprises’ third-party applications. Private APIs give certain users access to only specified applications. Private APIs are most often deployed in enterprises to give access to particular parts of their network to contractors or employees. For information on NFV see the section “Network Function Virtualization (NFV)—Architecture” in Chapter 4.
Companies that supply hardware and software for SDNs include: ADVA, Advantech, Cisco, Ciena, Citrix, Dell, Riverbed Technology, VeloCloud, Versa Networks, and Viptela.
Orchestration and Automation
Orchestration and Automation are features within WA SDNs.
Automation is the use of software to control specific functions within the network. Scripts written in software are used to perform particular tasks. Examples are use of a script for routing traffic to alternate routes in networks if there is congestion on the main route. Or it may define when traffic should overflow to a private line from an Internet-connected IP VPN. Another example is when telephone companies automate turning on ports in optical equipment in response to traffic levels in broadband networks. For instance, a large bank used the same configuration at each of its 50 branch offices. A configuration might include policies on routing critical applications, videos, and the Internet. For the bank, a telephone company contact person first tested a configuration at one branch location. Once the test was completed, the same configuration was downloaded to each branch via access circuits at the branch. Note that a working circuit was already in place at each of the 50 branches.
Orchestration refers to the ability to use automation to control many functions within open source software on SD WANs. It may, for example, send instructions to configure all branch office locations within an organization uniformly. Orchestration is intended to automate on-demand services across multiple providers.
Automation and orchestration are challenging to implement for customers and telephone companies with hardware and software from multiple vendors. This greatly increases the complexity of implementing WA SDN. WA SDNs operate best and are least complex to implement and manage for customers and telephone companies with commodity hardware and servers with open source software.
The Hybrid Wide Area Network—MPLS and WA SDN
Many organizations keep their Multi-Protocol Label Switching (MPLS) service at some locations and deploy WA SDN at headquarters. MPLS’s primary advantage is that it prioritizes voice and video using bits in the MPLS label. Its disadvantage is the long lead time needed to configure and implement the service. However, once it’s in place, MPLS does have advantages in that it prioritizes voice and video. WA SDNs are able to control which traffic goes over the MPLS service so that MPLS links are integrated via control plane signaling into the SDN network. See Table 5-1 for a comparison of broadband services.
Table 5-1 A Comparison of Broadband Services*
|
SD WAN |
MPLS |
IP VPN |
Dedicated Wavelength |
|
|---|---|---|---|---|---|
A managed service |
Carriers manage traffic |
Carriers manage network |
Managed by customer |
No |
No |
Layer 2** broadband |
No |
No |
No |
Yes |
Yes |
Why used |
To prioritize and route traffic |
To prioritize voice and video between offices |
To secure site-to-site & remote access over the Internet |
To attain high speeds of 100 to 400 Gigabits |
To guarantee speeds up to a 1,000 Gigabits (1 TB) |
Factors |
Complex to install; routes applications |
Costly, limited capacity |
Speed not guaranteed, low cost |
Can carry SDN traffic |
Can carry SDN traffic |
*For additional broadband services, see Table 5-2 in the “Appendix.”
**Layer 2—Data layer of the Open System Interconnection (OSI)—The protocol of transferring data between networks.
Implementing WA SDN—Staff Buy in a Challenge
A major challenge in implementing WA SDN service at enterprises is IT employee resistance due to fears of being laid off because some operations are automated.
There is additionally often a lack of expertise to manage WA SDN service. This is because once automation is operational, fewer employees may be required to implement changes that are now automated. Additionally, some organizations hire their telephone company to implement and manage some or all of WA SDN’s functions. Moreover, SDN is new and requires new skills to program scripts for automation and knowledge of orchestration.
Another issue is that employees that manage the service might not have the authority to implement needed, more costly features. This creates delays and confusion.
Network Backups—Protection from Outages
Cellular services are a lower-cost backup to their fiber-optic–based broadband links than DSL because cabling is not required. Small organizations and even some medium sized companies use cellular as a backup. It may have less capacity than DSL, but the costs are lower, the fiber services rarely fail, and it’s possible to designate only to allow key staff to use the backup service.
DSL as a Backup Option for Business Customers
Medium-sized and large commercial and business customers lease DSL services primarily as a low-cost backup service in the event that their primary Internet access circuits fail. Many of these primary circuits are installed on fiber-optic cabling. The large volume of revenue generated by enterprise customers makes a carrier’s investment in fiber-optic cabling for business customers viable.
Fiber cabling supports higher speeds than the copper cabling used for DSL and requires less maintenance by providers than copper cabling. For these reasons, major telephone companies are adding more fiber to networks, eliminating DSL, and replacing it with Gigabit Ethernet circuits over newly installed fiber cabling. However, organizations may keep DSL for backup in case service on the fiber crashes or the fiber cable is cut.
Cellular Backups for Small and Medium-Sized Organizations—Outgoing Calls
Cellular backups are lower-cost options than adding duplicate fiber or DSL. However, in an outage the organization loses incoming calls. In these cases, customers can request that during an outage, their telephone company forward calls to their cellular service. Alternatively, onsite routers capable of load balancing traffic between cellular and fiber-optic lines may be able to automatically fail over to cellular service.
Employees generally have cell phones and can make outgoing calls even when there is a fiber cut and service to their building is lost. Cellular service is particularly suited to temporary locations such as pop-up stores, construction trailers, and other temporary locations. Cellular service is also faster to install than wired connections that require telephone company technicians onsite and remote programming.
Deploying Duplicate Fiber Cabling—Costly but High Capacity
Alternate fiber runs are the most costly option for backing up voice and data traffic to buildings. With fiber backups, organizations provision one set of fiber to, say, the left corner of their building and the other fibers at the right-hand corner. In this way, a backhaul digging up the earth that inadvertently slices fiber on one side would not cut the fibers on the other side of the building.
However, if the organization’s telephone company equipment malfunctions, service will be lost unless each set of fibers is routed to a different provider. Large financial institutions, large pharmaceuticals, and cloud data centers often provision fiber with different telephone companies as a precaution in case one provider has a service outage. Another commonly used option is to use cable TV providers as a backup option.
Emergency Call Reporting—911 in the U.S., the Philippines, and Canada
Almost all countries provide a way for residents to report dangerous situations and request help in emergencies in the event of fires, natural disasters, accidents and health crises. Per Trey Fogerty of the National Emergency Number Association, there are more than 240 million 911 calls answered each year by PSAP (Public Safety Answering Point) operators in the United States. A PSAP is a call center staffed with personnel that answer 911 calls. This statistic was published in a San Antonio publication, KTSA, on June 3, 2017, in an article titled, “911 Convention in S.A. This Week.” According to the article, which paraphrased Fogerty:
Soon, 9-1-1 systems will be able to accept text messages, photos and videos.... Some communities just don’t have the money needed to make the upgrades.
The main goal of emergency management staff is to quickly respond to calls or texts by contacting the appropriate emergency responders. If someone is choking, a delay of 60 seconds can make the difference between life and death. During a rapidly spreading fire or an armed robbery in progress delays can result in death and extensive property damage. These types of crises demand rapid responses.
Security, Financial and Technical Hurdles
In the United States, emergency call centers face a number of challenges:
 Adequate funding to purchase up-to-date technology. 911 call centers receive money from fees tacked onto landline and mobile telephone bills. These fees are not always adequate to meet the needs of PSAPs with fewer customers from which to collect fees.
Adequate funding to purchase up-to-date technology. 911 call centers receive money from fees tacked onto landline and mobile telephone bills. These fees are not always adequate to meet the needs of PSAPs with fewer customers from which to collect fees. Sustainability to keep their equipment up and running during natural disasters. 911 centers have duplicate cabling to their facilities in case one is disabled or cut. In addition, telephone companies prioritize repairs and outages at PSAPs. In an outage caused by, for example, hurricane damage, PSAPs forward all of their calls to another center.
Sustainability to keep their equipment up and running during natural disasters. 911 centers have duplicate cabling to their facilities in case one is disabled or cut. In addition, telephone companies prioritize repairs and outages at PSAPs. In an outage caused by, for example, hurricane damage, PSAPs forward all of their calls to another center. Security to protect their operations from hackers. Hackers sending massive amounts of calls to PSAPs with denial of service attacks have caused outages at 911 centers.
Security to protect their operations from hackers. Hackers sending massive amounts of calls to PSAPs with denial of service attacks have caused outages at 911 centers. Identification of callers’ locations when they reach 911 agents via text, VoIP telephone, enterprise telephone system, TTY (Teletypewriter), and mobile phones.
Identification of callers’ locations when they reach 911 agents via text, VoIP telephone, enterprise telephone system, TTY (Teletypewriter), and mobile phones.
When 911 was established in 1968, all people reached 911 call centers from their wired, home telephone. Signaling on these calls transmitted callers’ telephone numbers, which were matched up with the address for each telephone number in databases. Thus, dispatchers were able to quickly notify ambulance, firefighters, or police and let them know the location of the problem.
With the advent of mobile phones, the location of the nearest cell tower is transmitted to 911 agents. In locations where cell towers are far from each other, it’s difficult to precisely locate the caller. The issue of location identification is challenging when people contact 911 via text messaging and VoIP telephones as well. All of these types of messaging are not necessarily associated with a fixed address. However, text messages are important in situations such as when a victim is hiding and does not want to be overheard. The FCC and wireless service providers are working together to resolve these issues. The 5G cellular protocol specifies cells with antennas close to each other, narrowing down the location identification.
Note
Appendix
Table 5-2 An Overview of Broadband Network Services
Network Service |
Places Typically Used |
How Used |
|---|---|---|
30 to 60 Megabit services T1: 24 voice or data channels 1.54Mbps E1: 30 voice or data channels, 2Mbps plus one channel for signaling and one for framing and remote maintenance |
Commercial organizations Being replaced by Gigabit Ethernet |
Internet access, connections to long-distance and local telephone companies for voice and data, private lines between company sites. Each channel = 64Kbps. E1 is the European version of T1. |
T3: 672 voice or data channels, equivalent to 28 T1s E3: 480 voice or data channels |
Large and medium sized organizations Being replaced by Gigabit Ethernet |
Access to long-distance companies, Internet access, high-speed private lines between company sites. This is the European version of T3. |
BRI ISDN: Two voice or data channels and one signaling channel |
Organizations |
Video conferencing; but new systems mainly use IP; supplanted by other technologies. |
PRI ISDN: 23 voice/data channels and one signaling channel in the United States 30 voice/data channels and one signaling channel in Europe |
Business and commercial customers |
Call centers, videoconferencing; PRI ISDN has different speeds in the United States and Europe. |
Digital Subscriber Line (DSL): 128Kbps to 44Mbps |
Residential consumers, small and mid-size businesses where fiber to premises not available Telecommuters |
Internet access, television. Remote access to corporate files and e-mail. |
Carrier Gigabit Ethernet 1Mbps to 10Gbps over fiber |
Mid-size to large commercial customers Carrier networks and cable TV core and metropolitan networks |
Access to the Internet, connections to storage area networks, and LAN-to-LAN connections; data only. To aggregate traffic in metropolitan networks and send it as a single stream to central offices or cable headends. |
Asynchronous Transfer Mode (ATM): Up to 2.5Gbps |
Telephone companies |
Not suited to today’s capacity requirements. Transmits voice, video, and data traffic. Rarely used because ATM switches are required. |
Table 5-3 Digital Signal Levels—These Services are Being Replaced by Higher-Capacity Carrier Ethernet
Level |
North America |
|
Japan |
|
Europe |
|
|---|---|---|---|---|---|---|
User Chan. |
Speed |
User Chan. |
Speed |
User Chan. |
Speed |
|
DS-0 |
1 |
64Kbps |
1 |
64Kbps |
1 |
64Kbps |
T1 (DS-1) |
24 |
1.544Mbps |
24 |
1.544Mbps |
24 |
2.048Mbps |
T2 (DS-2) |
96 |
6.312Mbps |
96 |
6.312Mbps |
120 |
8.448Mbps |
T3 (DS-3) |
672 |
44.7Mbps |
480 |
32.06Mbps |
672 |
34.368Mbps |
Table 5-4 Digital Subscriber Line Standards
Digital Subscriber Line Service |
Upstream Top Data Rate |
Downstream Top Data Rate |
Voice |
Comments |
|---|---|---|---|---|
ADSL (Asymmetric DSL) |
800Kbps |
7Mbps |
Yes |
Offered to residential customers. Uses one pair of wires. |
ADSL2 |
1Mbps |
8Mbps |
Yes |
Most common standard worldwide for Internet access. |
ADSL2+ |
1Mbps |
24Mbps |
Yes |
Supports video on demand on short cable runs. |
ADSL2—Reach extended |
1Mbps |
8Mbps |
Yes |
Increases reach of ADSL2+. |
SHDSL—Symmetric High-Data Rate |
5.6Mbps |
5.6Mbps |
Yes |
Single or two pair. Two pair speeds higher than single pair. |
VDSL (Very-High-Bit-Rate DSL) |
1.5Mbps 2.3Mbps |
13Mbps 52Mbps |
Yes |
|
VDSL2—12MHz |
30Mbps |
55Mbps |
Voice |
Requires short cable length; TV/data/voice. |
VDSL2—30MHz |
100Mbps |
100Mbps |
Yes |
Requires short cable length; TV/data/voice. |
