the following lists and charts provide a quick reference version of social engineering methods discussed in Chapters 2 to 14, and verification procedures detailed in Chapter 16. Modify this information for your organization, and make it available for employees to refer to when an information security question arises.
These tables and checklists will assist you in spotting a social engineering attack.
The Social Engineering Cycle
ACTION | DESCRIPTION |
|---|---|
Research | May include open source information such as SEC filings and annual reports, marketing brochures, patent applications, press clippings, industry magazines, Web site content. Also Dumpster diving. |
Developing rapport and trust | Use of insider information, misrepresenting identity, citing those known to victim, need for help, or authority. |
Exploiting trust | Asking for information or an action on the part of the victim. In reverse sting, manipulate victim to ask attacker for help. |
Utilize information | If the information obtained is only a step to final goal, attacker returns to earlier steps in cycle till goal is reached. |
Common Social Engineering Methods
Posing as a fellow employee
Posing as an employee of a vendor, partner company, or law enforcement
Posing as someone in authority
Posing as a new employee requesting help
Posing as a vendor or systems manufacturer calling to offer a system patch or update
Offering help if a problem occurs, then making the problem occur, thereby manipulating the victim to call them for help
Sending free software or patch for victim to install
Sending a virus or Trojan Horse as an email attachment
Using a false pop-up window asking user to log in again or sign on with password
Capturing victim keystrokes with expendable computer system or program
Leaving a floppy disk or CD around the workplace with malicious software on it
Using insider lingo and terminology to gain trust
Offering a prize for registering at a Web site with username and password
Dropping a document or file at company mail room for intraoffice delivery
Modifying fax machine heading to appear to come from an internal location
Asking receptionist to receive then forward a fax
Asking for a file to be transferred to an apparently internal location
Getting a voice mailbox set up so callbacks perceive attacker as internal
Pretending to be from remote office and asking for email access locally
Warning Signs of an Attack
Refusal to give callback number
Out-of-ordinary request
Claim of authority
Stresses urgency
Threatens negative consequences of noncompliance
Shows discomfort when questioned
Name dropping
Compliments or flattery
Flirting
Common Targets of Attacks
TARGET TYPE | EXAMPLES |
|---|---|
Unaware of value of information | Receptionists, telephone operators, administrative assistants, security guards. |
Special privileges | Help desk or technical support, system administrators, computer operators, telephone system administrators. |
Manufacturer/vendor | Computer hardware, software manufacturers, voice mail systems vendors. |
Specific departments | Accounting, human resources. |
Factors That Make Companies More Vulnerable to Attacks
Large number of employees
Multiple facilities
Information on employee whereabouts left in voice mail messages
Phone extension information made available
Lack of security training
Lack of data classification system
No incident reporting/response plan in place
These tables and charts will help you to respond to requests for information or action that may be social engineering attacks.
Verification of Identity Procedure
Verification of Employment Status Procedure
ACTION | DESCRIPTION |
|---|---|
Employee directory check | Verify that requester is listed in on-line directory. |
Requester's manager verification | Call requester's manager using phone number listed in company directory. |
Requester's department or workgroup verification | Call requester's department or workgroup and determine that requester is still employed by company. |
Procedure to Determine Need to Know
ACTION | DESCRIPTION |
|---|---|
Consult job title/workgroup/responsibilities list | Check published lists of which employees are entitled to specific classified information. |
Obtain authority from manager | Contact your manager, or the manager of the requester, for authority to comply with the request. |
Obtain authority from the information Owner or designee | Ask Owner of information if requester has a need to know. |
Obtain authority with an automated tool | Check proprietary software database for authorized personnel. |
Criteria for Verifying Non-Employees
Data Classification
CLASSIFICATION | DESCRIPTION | PROCEDURE |
|---|---|---|
Can be freely released to the public. | No need to verify. | |
Internal | For use within the company. | Verify identity of requester as active employee orverify nondisclosure agreement on file andmanagement approvalfor nonemployees. |
Information of a personal nature intended for use only within the organization. | Verify identity of requester as active employee or nonemployee with authorization. Check with human resources department to disclose Private information to authorized employees or external requesters. | |
Shared only with people with an absolute need to know know within the organization. | Verify identity of requester and need to from designated information Owner. Release only with prior written consent of manager, or information Owner or designee. Check for nondisclosure agreement on file. Only management personnel may disclose to persons not employed by the company. |
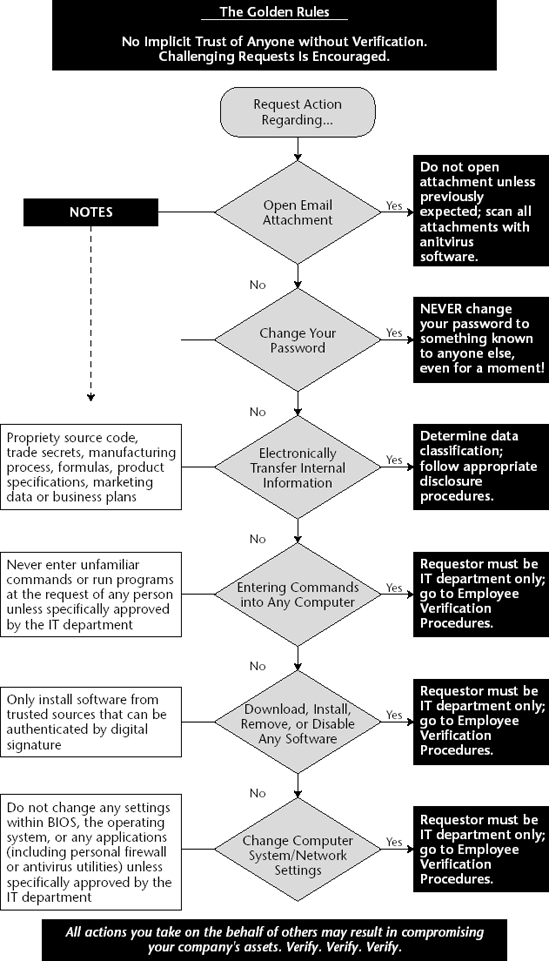
Responding to a Request for Information
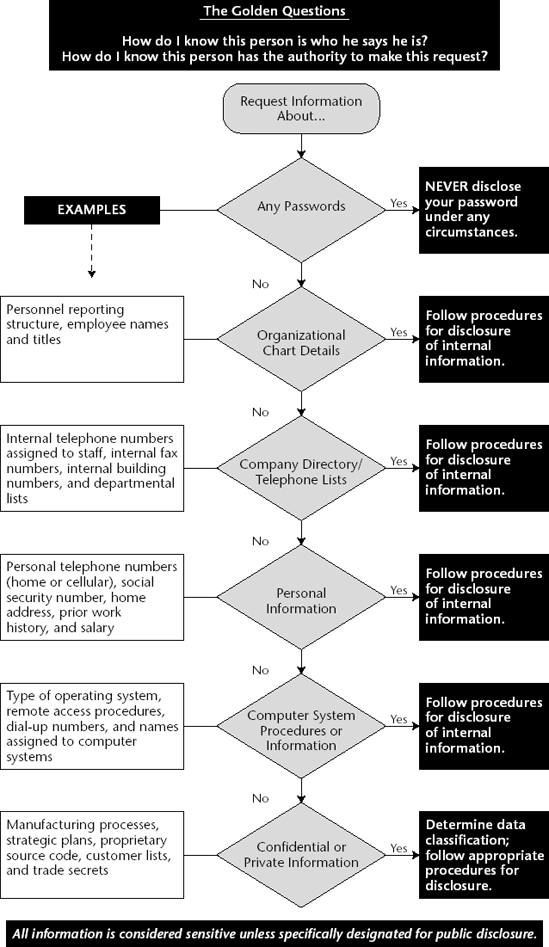
Responding to a Request for Action