<ENTERPRISE NAME>
<PLACE LOGO HERE>
<author><version><revision date>
This is a template for the Current Environment Assessment Specification. This page should be removed prior to publication of the specification. The template is a guide for the enterprise and should not be blindly followed. The organization should
Review the chapter in the book that refers to the template to understand its use.
Examine the template outline and determine what additions might be necessary based on unique organizational needs.
If absolutely necessary, remove any sections that will not apply. (The authors strongly discourage this practice.)
Save the template for future use.
Begin to develop the document.
Guidance is given for preparation of the document throughout the template.
Text shown as normal text should be used in the document. It may be modified as necessary.
Text shown in pointed brackets is either instructional guidance in the application of the document or a description of the type of information to be added and should be removed prior to publication.
Text shown in double pointed brackets is a placeholder for the insertion of text by the authors.
Headers and footers should be customized as necessary as a final step in the completion of the document.
Current Environment Assessment Specification
This document defines the current information technology environment as it pertains to the business integration strategy and architecture as of <<date>> for <<enterprise>>. <The introduction to the Current Environment Assessment should be a short executive overview of the specification. It should define the types of technologies that are being defined and any major constraints in the current environment, such as limitations imposed by legacy systems or the requirements for high security.>
<The purpose of the Current Environment Assessment is to document and assess the current integration technologies that support the business functions of the enterprise. This assessment will be used when determining recommended technologies and vendors in the Integration Architecture Document.>
<There are two types of participants that should be identified:
The team responsible for the creation of the current environment assessment in its initial form as well as for any on going improvements; anyone that provided information or review should be included in this list.
The audience of this document; include how they will apply it to their work.>
<The scope should define the boundaries for the current environment assessment. Does it cover the entire enterprise or only a segment? It should cover internal as well as external assets.>
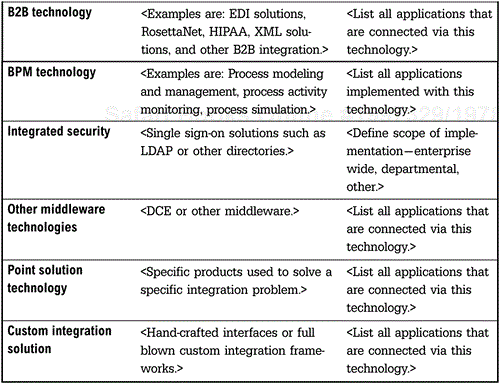
<This section should identify the integration technologies that are used by the type. It should describe the specific vendor technology and the applications that are connected using the technology. If there are technologies that are purchased but not used (shelfware) this should be identified as well.>

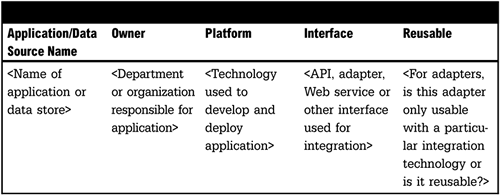
<Using the information on applications or data sources from the prior section's interfaces should be described in detail. This section should list all integrated applications or major data stores and connector information. The objective is to determine which applications or data stores already have installed adapters or other interfaces. An effort should be made to determine the reusability of the interface.>
<This section gives a unified view of the current environment's integrations, first by purpose and second by technology. Where there exist multiple integrations between each application, place all the descriptions of the purpose and each individual technology in the cell making sure there is a clear identification between the purpose and technology.>

<A diagram should be placed here that is a schematic of the current environment, identifying the current configuration including the servers, systems software versions, application software, adapters, databases, integration software, networking, administrative, and security systems. It may not be possible or desirable to have a single diagram; each diagram should be included. For example, there might be a separate physical network diagram and security diagram. There may need to be several diagrams of the applications, due to complexity. All diagrams should be clearly marked. In addition, any supporting diagrams that already exist should be included.>
<Security is defined separately because of the complexity and the importance of this topic to integration. In this section, a description of the security requirements and the implementation approach for each type of data, application, or process will need to be identified.>

<This section is a summary of all key discoveries found during the assessment process. This should include any areas of risk identified, such as holes in security or hand coded interfaces, and what will not scale and cannot be easily changed. This section should also note any areas of technical redundancy, such as multiple messaging technologies or multiple integration brokers already installed. Finally, any current problems that involve end users' use of the existing systems should also be captured.>
<The appendix should list any reference documents used in the creation of the document so that its contents can be traced back to their sources if necessary. This should be broken down into internal documents and external documents. Internal documents are those that belong to the organization. External documents are items such as articles, whitepapers, Web sites, or product documentation.>
