1
Blockchain 101
It is very likely that if you are reading this book, you already have heard about blockchain and have some fundamental appreciation of its enormous potential. If not, then let me tell you that this is a technology that has promised to positively alter the existing paradigms of nearly all industries including, but not limited to, the IT, finance, government, media, medical, and law sectors.
This chapter is an introduction to blockchain technology, its technical foundations, the theory behind it, and various techniques that have been combined together to build what is known today as blockchain.
In this chapter, the theoretical foundations of distributed systems are described first. Next, the precursors of Bitcoin are presented. Finally, blockchain technology is introduced. This approach is a logical way of understanding blockchain technology, as the roots of blockchain are in distributed systems and cryptography. We will be covering a lot of ground quickly here, but don't worry—we will go over a great deal of this material in much greater detail as you move throughout the book.
The growth of blockchain technology
With the invention of Bitcoin in 2008, the world was introduced to a new concept, which revolutionized the whole of society. It was something that promised to have an impact upon every industry. This new concept was blockchain; the underlying technology that underpins Bitcoin.
Some describe blockchain as a revolution, whereas another school of thought believes that it is going to be more evolutionary, and it will take many years before any practical benefits of blockchain reach fruition. This thinking is correct to some extent, but, in my opinion, the revolution has already begun. It is a technology that has an impact on current technologies too and possesses the ability to change them at a fundamental level.
Many prominent organizations all around the world have moved on from the proof-of-concept stage and are already writing production systems utilizing blockchain. The disruptive potential of blockchain has now been fully recognized. For example, Decentralized Finance (DeFi) has recently emerged as a new disruptive idea that aims to decentralize the existing financial system. DeFi offers individuals more control over their assets, allowing them to fully own and operate their financial strategy on blockchain without requiring any intermediaries. This is already challenging traditional finance by creating decentralized platforms for trading, investment, insurance, payments, and lending.
A glimpse of the potential of DeFi can be seen at https://defipulse.com. A noticeable fact is the amount of total value locked in the system, which is almost 5 billion US Dollars.
However, some organizations are still in the preliminary exploration stage, though they are expected to progress more quickly as the technology matures.
Progress toward maturity
If we look at the last few years, we notice that, in 2013, some ideas started to emerge that suggested that blockchain may have the potential for application in areas other than cryptocurrencies. Around that time, the primary usage of blockchain was in cryptocurrency space such as Bitcoin and Litecoin, and many new coins emerged during that period.
Cryptocurrency can be defined as a digital currency that is secured by cryptography.
The following graph shows a broad-spectrum outline of the year-wise progression and adoption trends of blockchain technology. The years shown on the x axis indicate the range of time in which a specific phase of blockchain technology falls. Each phase has a name that represents the stage at which the technology was reached, and this is shown on the x axis starting from the period of IDEAS AND THOUGHTS in 2013 to eventually MATURITY AND FURTHER PROGRESS, expected in 2025. The y axis shows the level of activity, involvement, and adoption of blockchain technology. The graph shows that, by roughly 2025, blockchain technology is expected to become mature and have a high number of users:
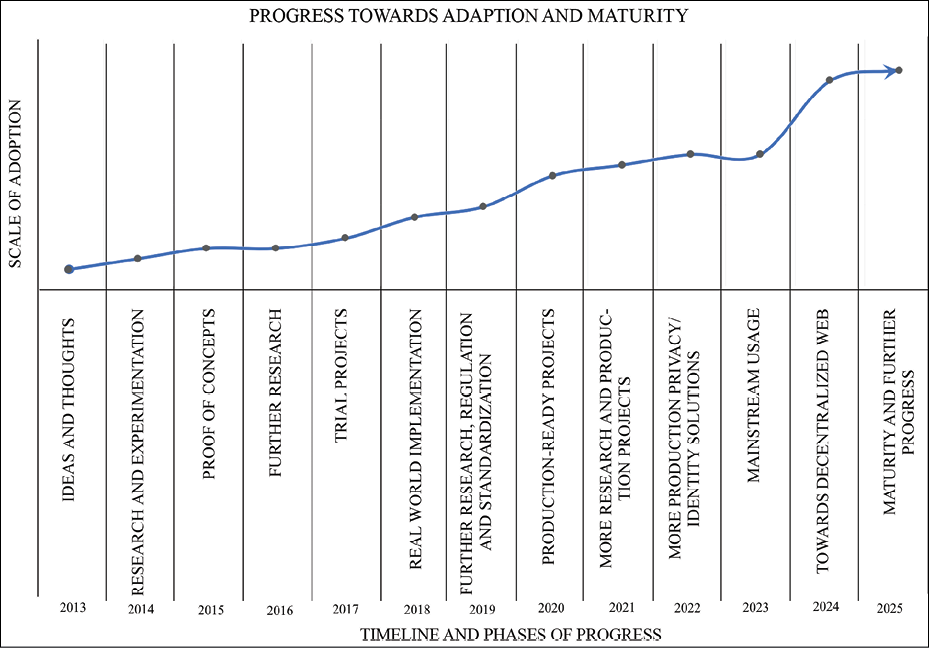
Figure 1.1: Blockchain technology adoption and maturity
The preceding graph shows that, in 2013, ideas and thoughts emerged regarding other usages of blockchain technology apart from cryptocurrencies. Then, in 2014, some research and experimentation began, which led to proofs of concept, further research, and full-scale trial projects between 2015 and 2017. In 2018, we saw real-world implementations. Already many projects are underway and set to replace existing systems; for example, the Australian Securities Exchange (ASX) is soon to become the first organization to replace its legacy clearing and settlement system with blockchain technology.
More information on this topic can be found at https://www.asx.com.au/services/chess-replacement.htm.
Another recent prominent example is that of a production-ready project implemented by Santander, where the first end-to-end blockchain bond has been issued. This is a significant step toward the mainstream adoption of blockchain.
You can read more about this at http://www.santander.com/csgs/Satellite/CFWCSancomQP01/en_GB/Corporate/Press-room/2019/09/12/Santander-launches-the-first-end-to-end-blockchain-bond.html.
It is expected that, during 2020, more research will be carried out, along with an increasing interest toward the regulation and standardization of blockchain technology. After this, production-ready projects and off-the-shelf projects will be available utilizing blockchain technology from 2020, and by 2021 mainstream production-level usage of blockchain technology is expected.
Progress in blockchain technology almost feels like the internet dot-com boom of the late 1990s.
In the next few years, research in the scalability of blockchains, where blockchains will be able to handle a large number of transactions similar to traditional financial networks, is expected to become more mature. Also, during the first few years of the 2020s, we will see more production-level usage of blockchain addressing issues such as privacy, decentralized identity, and some progress toward the decentralized web (or internet decentralization). Note that such solutions already exist but are not in mainstream use. The mainstream usage of such technologies is expected from the start of 2020.
It is expected that, at the start of the next decade, research in such areas will continue along with the adoption and further maturity of blockchain technology. Finally, in 2025, it is expected that the technology will be mature enough to be used on a day-to-day basis by, less tech-savvy people. For example, blockchain networks can be used as easily and naturally as consumers using the internet now. Further research is expected to continue even beyond this point. Please note that the timelines provided in the chart are not strict and may vary, as it is quite difficult to predict when exactly blockchain technology will become mature. This graph is based on the progress made in recent years and the current climate of research, interest, and enthusiasm regarding this technology, which can be extrapolated to predict that blockchain will progress to become a mature technology by 2025.
Increasing interest
Interest in blockchain technology has risen quite significantly over the last few years. Once dismissed simply as "geek money" from a cryptocurrency point of view, or as something that was just not considered worth pursuing, blockchain is now being researched by the largest companies and organizations around the world. Millions of dollars are being spent to adopt and experiment with this technology. This is evident from recent actions taken by the European Union, where they have announced plans to increase funding for blockchain research to almost 340 million Euros by 2020.
Interested readers can read more about this at https://www.irishtimes.com/business/technology/boost-for-blockchain-research-as-eu-increases-funding-four-fold-1.3383340.
Another report suggests that global spending on blockchain technology research could reach 9.2 billion US Dollars by 2021.
More information regarding this can be found at https://bitcoinmagazine.com/articles/report-suggests-global-spending-blockchain-tech-could-reach-92-billion-2021/.
Also, the interest in blockchain within academia is astounding, and many educational establishments—including prestigious universities around the world—are conducting research and development on blockchain technology. There are not only educational courses being offered by many institutions, but academics are also conducting high-quality research and producing a number of insightful research papers on the topic. There are also a number of research groups and conferences around the world that specifically focus on blockchain research. This is extremely useful for the growth of the entire blockchain ecosystem. A simple online search of "blockchain research groups" would reveal hundreds, if not thousands, of these research groups.
There are also various consortiums such as Enterprise Ethereum Alliance (EEA) at https://entethalliance.org and Hyperledger at https://www.hyperledger.org, which have been established for research, development, and the standardization of blockchain technology.
Moreover, a large number of start-ups are providing blockchain-based solutions already. A simple trend search on Google reveals the immense scale of interest in blockchain technology over the last few years.
Especially since early 2017, the increase in the search term "blockchain" is quite significant, as shown in the following graph:

Figure 1.2: A popularity graph for the search term "blockchain," based on data from Google trends
It should be noted that the decrease shown at the end of the graph does not necessarily directly translate into the decreased interest in blockchain technology, but it simply captures the fact that the search term was searched fewer times as compared to late 2017 and early 2018. This could be simply due to the fact that people interested in blockchain technology have already understood enough about blockchain to no longer warrant searching for it on Google. We do see, however, a significant and continued interest in blockchain technology.
Various benefits of this technology have already been envisioned, such as decentralized trust, cost savings, transparency, and efficiency. However, there are multiple challenges too that are actively being researched on blockchain, such as scalability and privacy.
In this book, we are going to see how blockchain technology can help to bring about the benefits mentioned previously. You are going to learn what exactly blockchain technology is and how it can reshape businesses, multiple industries, and indeed everyday life by bringing about a plenitude of benefits such as efficiency, cost savings, transparency, and security. We will also explore what distributed ledger technology (DLT) is, decentralization, and smart contracts, and how technology solutions can be developed and implemented using mainstream blockchain platforms such as Ethereum and Hyperledger. We will also investigate what challenges need to be addressed before blockchain can become a mainstream technology.
We'll also take a critical look at blockchain; Chapter 21, Scalability and Other Challenges, is dedicated to a discussion of the limitations and challenges of blockchain technology.
We shall begin our exploration of blockchain by looking at distributed systems in the following section. This is a foundational paradigm used within blockchain, and we must have a firm grasp on what distributed systems are before we can meaningfully discuss blockchain in detail.
Distributed systems
Understanding distributed systems is essential to our understanding blockchain, as blockchain was a distributed system at its core. It is a distributed ledger that can be centralized or decentralized. A blockchain is originally intended to be and is usually used as a decentralized platform. It can be thought of as a system that has properties of the both decentralized and distributed paradigms. It is a decentralized-distributed system.
Distributed systems are a computing paradigm whereby two or more nodes work with each other in a coordinated fashion to achieve a common outcome. It is modeled in such a way that end users see it as a single logical platform. For example, Google's search engine is based on a large distributed system; however, to a user, it looks like a single, coherent platform.
A node can be defined as an individual player in a distributed system. All nodes are capable of sending and receiving messages to and from each other. Nodes can be honest, faulty, or malicious, and they have memory and a processor. A node that exhibits irrational behavior is also known as a Byzantine node after the Byzantine Generals problem.
The Byzantine Generals problem
In 1982, a thought experiment was proposed by Lamport et al. in their research paper, The Byzantine Generals Problem, which is available here:
https://www.microsoft.com/en-us/research/publication/byzantine-generals-problem/
In this problem, a group of army generals who lead different parts of the Byzantine army is planning to attack or retreat from a city. The only way of communicating among them is via a messenger. They need to agree to strike at the same time in order to win. The issue is that one or more generals might be traitors who could send a misleading message. Therefore, there is a need for a viable mechanism that allows for agreement among the generals, even in the presence of the treacherous ones, so that the attack can still take place at the same time. As an analogy for distributed systems, the generals can be considered honest nodes, the traitors as Byzantine nodes (that is, nodes with arbitrary behavior), and the messenger can be thought of as a channel of communication among the generals.
This problem was solved in 1999 by Castro and Liskov who presented the Practical Byzantine Fault Tolerance (PBFT) algorithm, which solves the consensus problem in the presence of Byzantine faults in asynchronous networks by utilizing the state machine replication protocol. PBFT goes through a number of rounds to eventually reach an agreement between nodes on the proposed value. PBFT and other consensus protocols will be discussed in greater detail in Chapter 5, Consensus Algorithms.
This type of inconsistent behavior of Byzantine nodes can be intentionally malicious, which is detrimental to the operation of the network. Any unexpected behavior by a node on the network, whether malicious or not, can be categorized as Byzantine.
A small-scale example of a distributed system is shown in the following diagram. This distributed system has six nodes, out of which one (N4) is a Byzantine node leading to possible data inconsistency. L2 is a link that is broken or slow, and this can lead to a partition in the network:
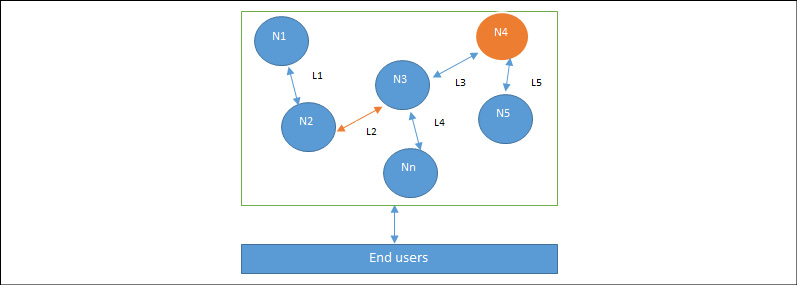
Figure 1.3: Design of a distributed system: N4 is a Byzantine node and L2 is broken or a slow network link
The primary challenge of a distributed system design is the coordination between nodes and fault tolerance. Even if some (a certain threshold dictated by the consensus protocol) of the nodes become faulty or network links break, the distributed system should be able to tolerate this and continue to work to achieve the desired result. This problem has been an active area of distributed system design research for many years, and several algorithms and mechanisms have been proposed to overcome these issues.
Distributed systems are so challenging to design that a theory known as the CAP theorem has been proven, which states that a distributed system cannot have all three of the much-desired properties simultaneously; that is, consistency, availability, and partition tolerance. We will dive into the CAP theorem in more detail later in this chapter.
Even though blockchain can be considered to be both a distributed and decentralized system, there are, however, critical differences between distributed systems and decentralized systems that make both of these systems architecturally different. We will discuss these differences in detail in Chapter 2, Decentralization.
With a better understanding of distributed systems, let's now move on to talking about blockchain itself. We'll begin with a brief rundown of the history of blockchain and Bitcoin.
The history of blockchain and Bitcoin
Blockchain was introduced with the invention of Bitcoin in 2008. Its practical implementation then occurred in 2009. For the purposes of this chapter, it is sufficient to review Bitcoin very briefly, as it will be explored in great depth in Chapter 6, Introducing Bitcoin. However, it is essential to refer to Bitcoin because, without it, the history of blockchain is not complete.
The events that led to blockchain
Now we will look at the early history of computing and computer networks and will discuss how these technologies evolved and contributed to the development of Bitcoin in 2008. We can view this in chronological order:
- 1960s – Invention of computer networks
- 1969 – Development of ARPANET
- 1970s – Early work on secure network communication including public key cryptography
- 1970s – Cryptographic hash functions
- 1973 – Extension of ARPANET to other geographic locations
- 1974 – First internet service provider, Telenet
- 1976 – Diffie–Hellman work on securely exchanging cryptographic keys
- 1978 – Invention of public key cryptography
- 1979 – Invention of Merkle Trees (hashes in a tree structure) by Ralph C. Merkle
- 1980s – Development of TCP/IP
- 1980 – Protocols for public key cryptosystems, Ralph C. Merkle
- 1982 – Blind signatures proposed by David Chaum
- 1982 – The Byzantine Generals Problem (Bitcoin can be considered a solution to the Byzantine Generals Problem; however, the original intention of the Bitcoin network was to address the previously unsolved double-spending problem)
- 1985 – Work on elliptic curve cryptography by Neal Koblitz and Victor Miller
- 1991 – Haber and Stornetta work on tamper proofing document timestamps. This can be considered the earliest idea of a chain of blocks or hash chains
- 1992 – Cynthia Dwork and Moni Naor publish Pricing via Processing or Combatting Junk Mail. This is considered the first use of Proof of Work (PoW)
- 1993 – Haber, Bayer, and Stornetta upgraded the tamper-proofing of document timestamps system with Merkle trees
- 1995 – David Chaum's Digicash system (an anonymous electronic cash system) started to be used in some banks
- 1998 – Bit Gold, a mechanism for decentralized digital currency, invented by Nick Szabo. It used hash chaining and Byzantine Quorums
- 1999 – Emergence of a file-sharing application mainly used for music sharing, Napster, which is a P2P network, but was centralized with the use of indexing servers
- 1999 – Development of a secure timestamping service for the Belgian project TIMESEC
- 2000 – Gnutella file-sharing network, which introduced decentralization
- 2001 – Emergence of BitTorrent and Distributed Hash Tables (DHTs)
- 2002 – Hashcash by Adam Back
- 2004 – Development of B-Money by Wei Dei using hashcash
- 2004 – Hal Finney, the invention of the reusable PoW system
- 2005 – Prevention of Sybil attacks by using computation puzzles, due to James Aspnes et al.
- 2009 – Bitcoin (first blockchain)
The aforementioned technologies contributed in some way to the development of Bitcoin, even if not directly; the work is relevant to the problem that Bitcoin solved. All previous attempts to create anonymous and decentralized digital currency were successful to some extent, but they could not solve the problem of preventing double spending in a completely trustless or permissionless environment. This problem was finally addressed by the Bitcoin blockchain, which introduced the Bitcoin cryptocurrency.
It should be noted that other concepts such as state machine replication (the SMR problem), introduced in 1978 by Leslie Lamport and formalized in 1980 by Fred Schneider, are also solvable by Bitcoin. Bitcoin solves the SMR problem (probabilistically) by allowing the replication of blocks and ensuring consistency via its PoW consensus mechanism.
The SMR, or state machine replication problem, is a technique used to provide fault-tolerant replication in distributed systems. We will explore this in greater detail in Chapter 5, Consensus Algorithms.
Now we will discuss some of the major milestones in the history of blockchain in more detail.
Electronic cash
The concept of electronic cash (e-cash), or digital currency, is not new. Since the 1980s, e-cash protocols have existed that are based on a model proposed by David Chaum.
Just as understanding the concept of distributed systems is necessary to comprehend blockchain technology, the idea of e-cash is also essential in order to appreciate the first, and astonishingly successful, application of blockchain, Bitcoin, and more broadly, cryptocurrencies in general.
Two fundamental e-cash system issues need to be addressed: accountability and anonymity.
Accountability is required to ensure that cash is spendable only once (addressing the double-spending problem) and that it can only be spent by its rightful owner. The double-spending problem arises when the same money can be spent twice. As it is quite easy to make copies of digital data, this becomes a big issue in digital currencies as you can make many copies of the same amount of digital cash.
Anonymity is required to protect users' privacy. With physical cash, it is almost impossible to trace back spending to the individual who actually paid the money, which provides adequate privacy should the consumer choose to hide their identity. In the digital world, however, providing such a level of privacy is difficult due to inherent personalization, tracing, and logging mechanisms in digital payment systems such as credit card payments. This is indeed a required feature for ensuring the security and safety of the financial network, but it is also often seen as a breach of privacy.
This is due to the fact that end users do not have any control over who their data might be shared with, even without their consent. Nevertheless, this is a solvable problem and cryptography is used to address such issues. Especially in blockchain networks, the privacy and anonymity of the participants on the blockchain are sought-after features. We will learn more about this in Chapter 4, Public Key Cryptography.
David Chaum solved both of these problems during his work in the 1980s by using two cryptographic operations, namely, blind signatures and secret sharing. These terminologies and related concepts will be discussed in detail in Chapter 4, Public Key Cryptography. For the moment, it is sufficient to say that blind signatures allow for signing a document without actually seeing it, and secret sharing is a concept that enables the detection of double-spending, that is, using the same e-cash token twice.
In 2009, the first practical implementation of an e-cash system named Bitcoin appeared. The term cryptocurrency emerged later. For the very first time, it solved the problem of distributed consensus in a trustless network. It used public key cryptography with a PoW mechanism to provide a secure, controlled, and decentralized method of minting digital currency. The key innovation was the idea of an ordered list of blocks composed of transactions which is cryptographically secured by the PoW mechanism to prevent double-spending in a trustless environment. This concept will be explained in greater detail in Chapter 6, Introducing Bitcoin.
Other technologies used in Bitcoin, but which existed before its invention, include Merkle trees, hash functions, and hash chains. All these concepts are explained in appropriate depth in Chapter 4, Public Key Cryptography.
Looking at all the technologies mentioned previously and their relevant history, it is easy to see how concepts from e-cash schemes and distributed systems were combined to create Bitcoin and what now is known as blockchain. This concept can also be visualized with the help of the following diagram:
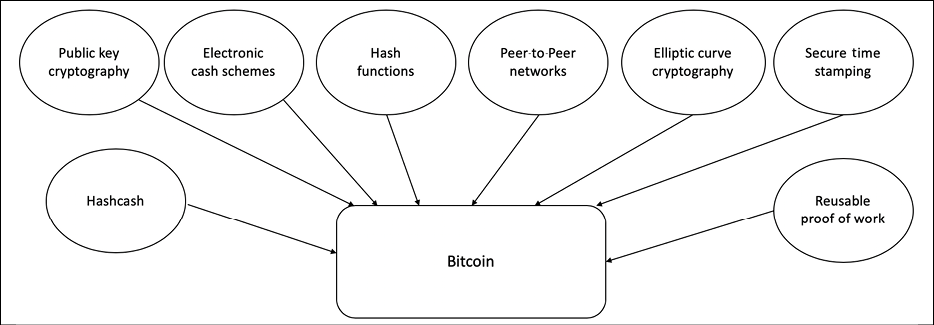
Figure 1.4: The various ideas that supported the invention of Bitcoin and blockchain
With the emergence of e-cash covered, along with the ideas that led to the formation of Bitcoin and blockchain, we can now begin to discuss blockchain itself.
Blockchain
In 2008, a groundbreaking paper, entitled Bitcoin: A Peer-to-Peer Electronic Cash System, was written on the topic of peer-to-peer e-cash under the pseudonym of Satoshi Nakamoto.
This paper is available at https://bitcoin.org/bitcoin.pdf.
It introduced the term chain of blocks. No one knows the actual identity of Satoshi Nakamoto. After introducing Bitcoin in 2009, he remained active in the Bitcoin developer community until 2011. He then handed over Bitcoin development to its core developers and simply disappeared. Since then, there has been no communication from him whatsoever, and his existence and identity are shrouded in mystery. The term "chain of blocks" evolved over the years into the word "blockchain."
As stated previously, blockchain technology incorporates a multitude of applications that can be implemented in various economic sectors. Particularly in the finance sector, significant improvement in the performance of financial transactions and settlements manifests as highly desirable time-and-cost reductions. Additional light will be shed on these aspects of blockchain in Chapter 19, Blockchain – Outside of Currencies, where practical use cases will be discussed in detail for various industries. For now, it is sufficient to say that parts of nearly all economic sectors have already realized the potential and promise of blockchain, and have embarked, or will do so soon, on the journey to capitalize on the benefits of blockchain technology.
Blockchain defined
A good place to start learning what blockchain is would be to see its definition. There are some different ways that blockchain may be defined; following are two of the most widely accepted definitions:
Layman's definition: Blockchain is an ever-growing, secure, shared recordkeeping system in which each user of the data holds a copy of the records, which can only be updated if all parties involved in a transaction agree to update.
Technical definition: Blockchain is a peer-to-peer, distributed ledger that is cryptographically secure, append-only, immutable (extremely hard to change), and updateable only via consensus or agreement among peers.
Now, let's examine things in some more detail. We will look at the keywords from the technical definition one by one.
Peer-to-peer
The first keyword in the technical definition is peer-to-peer, or P2P This means that there is no central controller in the network, and all participants (nodes) talk to each other directly. This property allows for transactions to be conducted directly among the peers without third-party involvement, such as by a bank.
Distributed ledger
Dissecting the technical definition further reveals that blockchain is a "distributed ledger," which means that a ledger is spread across the network among all peers in the network, and each peer holds a copy of the complete ledger.
Cryptographically secure
Next, we see that this ledger is "cryptographically secure," which means that cryptography has been used to provide security services that make this ledger secure against tampering and misuse. These services include non-repudiation, data integrity, and data origin authentication. You will see how this is achieved later in Chapter 4, Public Key Cryptography, which introduces the fascinating world of cryptography.
Append-only
Another property that we encounter is that blockchain is "append-only," which means that data can only be added to the blockchain in time-sequential order. This property implies that once data is added to the blockchain, it is almost impossible to change that data and it can be considered practically immutable. In other words, blocks added to the blockchain cannot be changed, which allows blockchain to become an immutable and tamper-proof ledger of transactions.
However, remember that it can be changed in rare scenarios wherein collusion against the blockchain network by bad actors succeeds in gaining more than 51 percent of the power. Otherwise, the blockchain is practically immutable.
There may be some legitimate reasons to change data in the blockchain once it has been added, such as the "right to be forgotten" or "right to erasure" (also defined in the GDPR ruling: https://gdpr-info.eu/art-17-gdpr/).
However, those are individual cases that need to be handled separately and that require an elegant technical solution. For all practical purposes, blockchain is indeed immutable and cannot be changed.
Updatable via consensus
The most critical attribute of a blockchain is that it is updateable only via consensus. This is what gives it the power of decentralization. In this scenario, no central authority is in control of updating the ledger. Instead, any update made to the blockchain is validated against strict criteria defined by the blockchain protocol and added to the blockchain only after a consensus has been reached among all participating peers/nodes on the network. To achieve consensus, there are various consensus facilitation algorithms that ensure all parties agree on the final state of the data on the blockchain network and resolutely agree upon it to be true. Consensus algorithms are introduced later in this chapter, and then in more detail in Chapter 5, Consensus Algorithms.
Blockchain architecture
Having detailed the primary features of blockchain, we are now in a position to begin to look at its actual architecture. We'll begin by looking at how blockchain acts as a layer within a distributed peer-to-peer network.
Blockchain by layers
Blockchain can be thought of as a layer of a distributed peer-to-peer network running on top of the internet, as can be seen in the following diagram. It is analogous to SMTP, HTTP, or FTP running on top of TCP/IP:

Figure 1.5: The architectural view of a generic blockchain
Now we'll discuss all these elements one by one:
- In the preceding diagram, the lowest layer is the Network, which is usually the internet and provides a base communication layer for any blockchain.
- A peer-to-peer network runs on top of the Network layer, which consists of information propagation protocols such as gossip or flooding protocols.
- After this comes the Cryptography layer, which contains crucial cryptographic protocols that ensure the security of the blockchain. These cryptographic protocols play a vital role in the integrity of blockchain processes, secure information dissemination, and blockchain consensus mechanisms. This layer consists of public key cryptography and relevant components such as digital signatures and cryptographic hash functions. Sometimes, this layer is abstracted away, but it has been included in the diagram because it plays a fundamental role in blockchain operations.
- Next comes the Consensus layer, which is concerned with the usage of various consensus mechanisms to ensure agreement among different participants of the blockchain. This is another crucial part of the blockchain architecture, which consists of various techniques such as SMR, proof-based consensus mechanisms, or traditional (from traditional distributed systems research) Byzantine fault-tolerant consensus protocols.
- Further to this, we have the Execution layer, which can consist of virtual machines, blocks, transaction, and smart contracts. This layer, as the name suggests, provides executions services on the blockchain and performs operations such as value transfer, smart contract execution, and block generation. Virtual machines such as Ethereum Virtual Machine (EVM) provide an execution environment for smart contracts to execute.
- Finally, we have the Applications layer, which is composed of smart contracts, decentralized applications, DAOs, and autonomous agents. This layer can effectively contain all sorts of various user level agents and programs that operate on the blockchain. Users interact with the blockchain via decentralized applications. We will discuss more about decentralized applications in Chapter 2, Decentralization.
All these concepts will be discussed in detail later in this book in various chapters. Next, we'll look at blockchain from more of a business-oriented perspective.
Blockchain in business
From a business standpoint, a blockchain can be defined as a platform where peers can exchange value/e-cash using transactions without the need for a centrally trusted arbitrator. For example, for cash transfers, banks act as a trusted third party. In financial trading, a central clearing house acts as a trusted third party between two or more trading parties. This concept is compelling, and, once you absorb it, you will realize the enormous potential of blockchain technology. This disintermediation allows blockchain to be a decentralized consensus mechanism where no single authority is in charge of the database. Immediately, you'll see a significant benefit of decentralization here, because if no banks or central clearing houses are required, then it immediately leads to cost savings, faster transaction speeds, and more trust.
We've now looked at what blockchain is at a fundamental level. Next, we'll go a little deeper and look at some of the elements that comprise a blockchain.
Generic elements of a blockchain
Now, let's walk through the generic elements of a blockchain. You can use this as a handy reference section if you ever need a reminder about the different parts of a blockchain. More precise elements will be discussed in the context of their respective blockchains in later chapters, for example, the Ethereum blockchain. The structure of a generic blockchain can be visualized with the help of the following diagram:

Figure 1.6: Generic structure of a blockchain
Elements of a generic blockchain are described here one by one. These are the elements that you will come across in relation to blockchain:
- Address: Addresses are unique identifiers used in a blockchain transaction to denote senders and recipients. An address is usually a public key or derived from a public key.
- Transaction: A transaction is the fundamental unit of a blockchain. A transaction represents a transfer of value from one address to another.
- Block: A block is composed of multiple transactions and other elements, such as the previous block hash (hash pointer), timestamp, and nonce. A block is composed of a block header and a selection of transactions bundled together and organized logically. A block contains several elements, which we introduce as follows:
- A reference to a previous block is also included in the block unless it is a genesis block. This reference is the hash of the header of the previous block. A genesis block is the first block in the blockchain that is hardcoded at the time the blockchain was first started. The structure of a block is also dependent on the type and design of a blockchain.
- A nonce is a number that is generated and used only once. A nonce is used extensively in many cryptographic operations to provide replay protection, authentication, and encryption. In blockchain, it's used in PoW consensus algorithms and for transaction replay protection. A block also includes the nonce value.
- A timestamp is the creation time of the block.
- Merkle root is a hash of all of the nodes of a Merkle tree. In a blockchain block, it is the combined hash of the transactions in the block. Merkle trees are widely used to validate large data structures securely and efficiently. In the blockchain world, Merkle trees are commonly used to allow efficient verification of transactions. Merkle root in a blockchain is present in the block header section of a block, which is the hash of all transactions in a block. This means that verifying only the Merkle root is required to verify all transactions present in the Merkle tree instead of verifying all transactions one by one. We will elaborate further on these concepts in Chapter 4, Public Key Cryptography.
- In addition to the block header, the block contains transactions that make up the block body. A transaction is a record of an event, for example, the event of transferring cash from a sender's account to a beneficiary's account. A block contains transactions and its size varies depending on the type and design of the blockchain.
The following structure is a simple block diagram that depicts a block. Specific block structures relative to their blockchain technologies will be discussed later in the book with greater in-depth technical detail:

Figure 1.7: The generic structure of a block
Generally, however, there are just a few attributes that are essential to the functionality of a block: the block header, which is composed of the hash of the previous block's header, the timestamp, nonce, Merkle root, and the block body that contains the transactions. There are also other attributes in a block, but generally, the components introduced in this section are usually available in a block.
- Peer-to-peer network: As the name implies, a peer-to-peer network is a network topology wherein all peers can communicate with each other and send and receive messages.
- The scripting or programming language: Scripts or programs perform various operations on a transaction in order to facilitate various functions. For example, in Bitcoin, transaction scripts are predefined in a language called Script, which consists of sets of commands that allow nodes to transfer bitcoins from one address to another. Script is a limited language, in the sense that it only allows essential operations that are necessary for executing transactions, but it does not allow for arbitrary program development.
Think of the scripting language as a calculator that only supports standard preprogrammed arithmetic operations. As such, the Bitcoin Script language cannot be called "Turing complete." In simple words, a Turing complete language means that it can perform any computation. It is named after Alan Turing, who developed the idea of a Turing machine that can run any algorithm however complex. Turing complete languages need loops and branching capability to perform complex computations. Therefore, Bitcoin's scripting language is not Turing complete, whereas Ethereum's Solidity language is.
To facilitate arbitrary program development on a blockchain, a Turing complete programming language is needed, and it is now a very desirable feature to have for blockchains. Think of this as a computer that allows the development of any program using programming languages. Nevertheless, the security of such languages is a crucial question and an essential and ongoing research area. We will discuss this in greater detail in Chapter 6, Introducing Bitcoin, Chapter 10, Smart Contracts, and the chapters on Ethereum Development, later in this book.
- Virtual machine: This is an extension of the transaction script introduced previously. A virtual machine allows Turing complete code to be run on a blockchain (as smart contracts); whereas a transaction script is limited in its operation. However, virtual machines are not available on all blockchains. Various blockchains use virtual machines to run programs such as Ethereum Virtual Machine (EVM) and Chain Virtual Machine (CVM). EVM is used in the Ethereum blockchain, while CVM is a virtual machine developed for and used in an enterprise-grade blockchain called "Chain Core."
- State machine: A blockchain can be viewed as a state transition mechanism whereby a state is modified from its initial form to the next one by nodes on the blockchain network as a result of transaction execution.
- Smart contracts: These programs run on top of the blockchain and encapsulate the business logic to be executed when certain conditions are met. These programs are enforceable and automatically executable. The smart contract feature is not available on all blockchain platforms, but it is now becoming a very desirable feature due to the flexibility and power that it provides to blockchain applications. Smart contracts have many use cases, including but not limited to identity management, capital markets, trade finance, record management, insurance, and e-governance. Smart contracts will be discussed in more detail in Chapter 10, Smart Contracts.
- Node: A node in a blockchain network performs various functions depending on the role that it takes on. A node can propose and validate transactions and perform mining to facilitate consensus and secure the blockchain. This goal is achieved by following a consensus protocol (most commonly PoW). Nodes can also perform other functions such as simple payment verification (lightweight nodes), validation, and many other functions depending on the type of the blockchain used and the role assigned to the node. Nodes also perform a transaction signing function. Transactions are first created by nodes and then also digitally signed by nodes using private keys as proof that they are the legitimate owner of the asset that they wish to transfer to someone else on the blockchain network. This asset is usually a token or virtual currency, such as Bitcoin, but it can also be any real-world asset represented on the blockchain by using tokens. There are also now standards related to tokens; for example, on Ethereum, there are ERC20, ERC721, and a few others that define the interfaces and semantics of tokenization. We will cover these in Chapter 12, Further Ethereum.
A high-level diagram of blockchain architecture highlighting the key elements mentioned previously is shown as follows:

Figure 1.8: Generic structure of a blockchain network
The preceding diagram shows a four-node blockchain network (top), each maintaining a chain of blocks, virtual machine, state machine, and address. The blockchain is then further magnified (middle) to show the structure of the chain of blocks, which is again magnified (bottom) to show the structure of a transaction. Note that this is a generic structure of a blockchain; we will see specific blockchains structures in detail in the context of Ethereum and Bitcoin blockchains later in this book.
How blockchain works
We have now defined and described blockchain. Now, let's see how a blockchain actually works. Nodes are either miners who create new blocks and mint cryptocurrency (coins) or block signers who validate and digitally sign the transactions. A critical decision that every blockchain network has to make is to figure out which node will append the next block to the blockchain. This decision is made using a consensus mechanism. The consensus mechanism will be described later in this chapter. For now, we will look at how a blockchain validates transactions and creates and adds blocks to grow the blockchain.
We will look at a general scheme for creating blocks. This scheme is presented here to give you a general idea of how blocks are generated and what the relationship is between transactions and blocks:
- Transaction is initiated: A node starts a transaction by first creating it and then digitally signing it with its private key. A transaction can represent various actions in a blockchain. Most commonly, this is a data structure that represents the transfer of value between users on the blockchain network. The transaction data structure usually consists of some logic of transfer of value, relevant rules, source and destination addresses, and other validation information. Transactions are usually either a cryptocurrency transfer (transfer of value) or smart contract invocation that can perform any desired operation. A transaction occurs between two or more parties. This will be covered in more detail in specific chapters on Bitcoin and Ethereum later in the book.
- Transaction is validated and broadcast: A transaction is propagated (broadcast) usually by using data-dissemination protocols, such as Gossip protocol, to other peers that validate the transaction based on preset validity criteria. Before a transaction is propagated, it is also verified to ensure that it is valid.
- Find new block: When the transaction is received and validated by special participants called miners on the blockchain network, it is included in a block, and the process of mining starts. This process is also sometimes referred to as "finding a new block." Here, nodes called miners race to finalize the block they've created by a process known as mining.
- New block found: Once a miner solves a mathematical puzzle (or fulfills the requirements of the consensus mechanism implemented in a blockchain), the block is considered "found" and finalized. At this point, the transaction is considered confirmed. Usually, in cryptocurrency blockchains such as Bitcoin, the miner who solves the mathematical puzzle is also rewarded with a certain number of coins as an incentive for their effort and the resources they spent in the mining process.
- Add new block to the blockchain: The newly created block is validated, transactions or smart contracts within it are executed, and it is propagated to other peers. Peers also validate and execute the block. It now becomes part of the blockchain (ledger), and the next block links itself cryptographically back to this block. This link is called a hash pointer.
This process can be visualized in the diagram as follows:
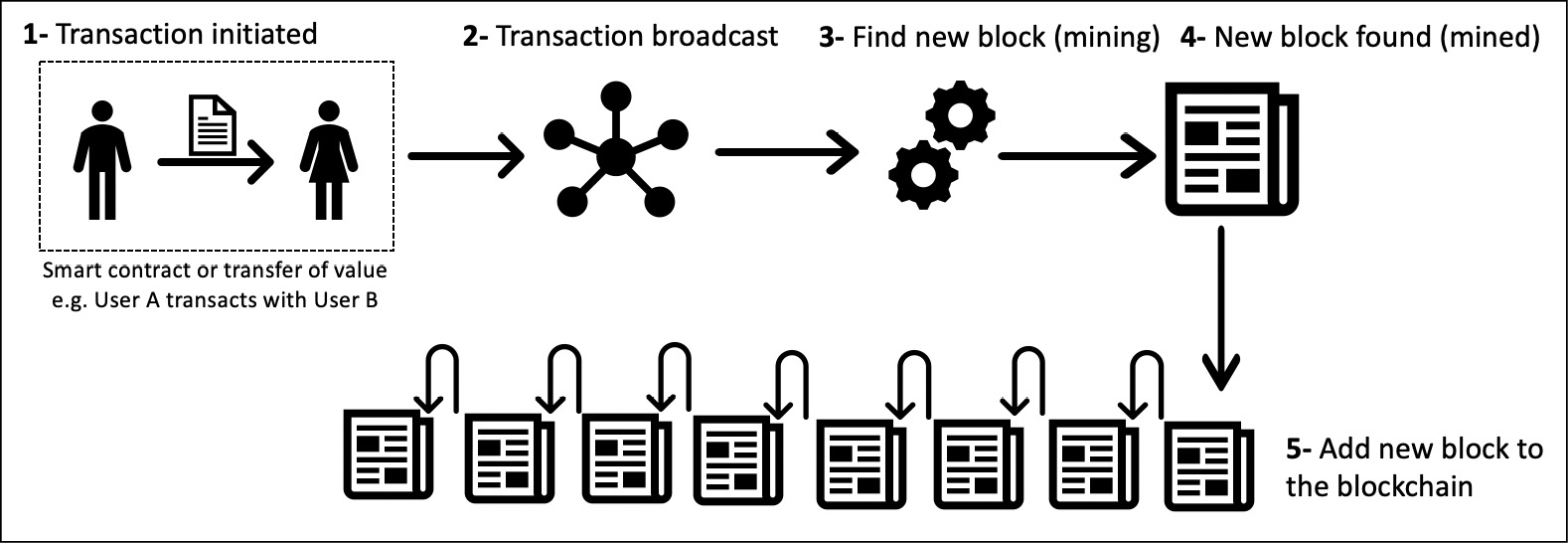
Figure 1.9: How a block is generated
This completes the basic introduction to blockchain. In the next section, you will learn about the benefits and limitations of this technology.
Benefits, features, and limitations of blockchain
Numerous advantages of blockchain technology have been discussed in many industries and proposed by thought leaders around the world who are participating in the blockchain space. The notable benefits of blockchain technology are as follows:
- Decentralization: This is a core concept and benefit of blockchain. There is no need for a trusted third party or intermediary to validate transactions; instead, a consensus mechanism is used to agree on the validity of transactions.
- Transparency and trust: As blockchains are shared and everyone can see what is on the blockchain, this allows the system to be transparent. As a result, trust is established. This is more relevant in scenarios such as the disbursement of funds or benefits where personal discretion in relation to selecting beneficiaries needs to be restricted.
- Immutability: Once the data has been written to the blockchain, it is extremely difficult to change it back. It is not genuinely immutable, but because changing data is so challenging and nearly impossible, this is seen as a benefit to maintaining an immutable ledger of transactions.
- High availability: As the system is based on thousands of nodes in a peer-to-peer network, and the data is replicated and updated on every node, the system becomes highly available. Even if some nodes leave the network or become inaccessible, the network as a whole continues to work, thus making it highly available. This redundancy results in high availability.
- Highly secure: All transactions on a blockchain are cryptographically secured and thus provide network integrity. Any transactions posted from the nodes on the blockchain are verified based on a predetermined set of rules. Only valid transactions are selected for inclusion in a block. The blockchain is based on proven cryptographic technology that ensures the integrity and availability of data. Generally, confidentiality is not provided due to the requirements of transparency. This limitation is the leading barrier to its adoption by financial institutions and other industries that require the privacy and confidentiality of transactions. As such, the privacy and confidentiality of transactions on the blockchain are being researched very actively, and advancements are already being made. It could be argued that, in many situations, confidentiality is not needed and transparency is preferred. For example, with Bitcoin, confidentiality is not an absolute requirement; however, it is desirable in some scenarios. A more recent example is Zcash (https://z.cash), which provides a platform for conducting anonymous transactions. Other security services, such as non-repudiation and authentication, are also provided by blockchain, as all actions are secured using private keys and digital signatures.
- Simplification of current paradigms: The current blockchain model in many industries, such as finance or health, is somewhat disorganized. In this model, multiple entities maintain their own databases and data sharing can become very difficult due to the disparate nature of the systems. However, as a blockchain can serve as a single shared ledger among many interested parties, this can result in simplifying the model by reducing the complexity of managing the separate systems maintained by each entity.
- Faster dealings: In the financial industry, especially in post-trade settlement functions, blockchain can play a vital role by enabling the quick settlement of trades. Blockchain does not require a lengthy process of verification, reconciliation, and clearance because a single version of agreed-upon data is already available on a shared ledger between financial organizations.
- Cost-saving: As no trusted third party or clearing house is required in the blockchain model, this can massively eliminate overhead costs in the form of the fees, which are paid to such parties.
- Platform for smart contracts: A blockchain is a platform on which programs can run that execute business logic on behalf of the users. This is a very useful feature but not all blockchains have a mechanism to execute smart contracts; however, this is a very desirable feature. It is available on newer blockchain platforms such as Ethereum and MultiChain, but not on Bitcoin.
Smart contracts
Blockchain technology provides a platform for running smart contracts. These are automated, autonomous programs that reside on the blockchain network and encapsulate the business logic and code needed to execute a required function when certain conditions are met. For example, think about an insurance contract where a claim is paid to the traveler if the flight is canceled. In the real world, this process normally takes a significant amount of time to make the claim, verify it, and pay the insurance amount to the claimant (traveler). What if this whole process were automated with cryptographically-enforced trust, transparency, and execution so that as soon as the smart contract received a feed that the flight in question has been canceled, it automatically triggers the insurance payment to the claimant? If the flight is on time, the smart contract pays itself.
This is indeed a revolutionary feature of blockchain, as it provides flexibility, speed, security, and automation for real-world scenarios that can lead to a completely trustworthy system with significant cost reductions. Smart contracts can be programmed to perform any actions that blockchain users need and according to their specific business requirements.
- Smart property: It is possible to link a digital or physical asset to the blockchain in such a secure and precise manner that it cannot be claimed by anyone else. You are in full control of your asset, and it cannot be double-spent or double-owned. Compare this with a digital music file, for example, which can be copied many times without any controls. While it is true that many Digital Rights Management (DRM)schemes are being used currently along with copyright laws, none of them are enforceable in the way a blockchain-based DRM can be. Blockchain can provide digital rights management functionality in such a way that it can be enforced fully. There are famously broken DRM schemes that looked great in theory but were hacked due to one limitation or another. One example is the Oculus hack: http://www.wired.co.uk/article/oculus-rift-drm-hacked. Another example is the PS3 hack; also, copyrighted digital music, films, and e-books are routinely shared on the internet without any limitations. We have had copyright protection in place for many years, but digital piracy refutes all attempts to fully enforce the law. On a blockchain, however, if you own an asset, no one else can claim it unless you decide to transfer it. This feature has far-reaching implications, especially in DRM and e-cash systems where double-spend detection is a crucial requirement. The double-spend problem was first solved without the requirement of a trusted third party in Bitcoin.
As with any technology, some challenges need to be addressed in order to make a system more robust, useful, and accessible. Blockchain technology is no exception. In fact, much effort is being made in both academia and industry to overcome the challenges posed by blockchain technology. The most sensitive blockchain problems are as follows:
- Scalability: Currently, blockchain networks are not as scalable as, for example, current financial networks. This is a known area of concern and a very ripe area for research.
- Adoption: Often, blockchain is seen as a nascent technology. Even though this perspective is rapidly changing, there is still a long way to go before the mass adoption of this technology. The challenge here is to allow blockchain networks to be easier to use so that adoption can increase. In addition, several other challenges such as scalability (introduced previously) exist, which must be solved in order to increase adoption.
- Regulation: Due to its decentralized nature, regulation is almost impossible on blockchain. This is sometimes seen as a barrier toward adoption because, traditionally, due to the existence of regulatory authorities, consumers have a certain level of confidence that if something goes wrong they can hold someone accountable. However, in blockchain networks, no such regulatory authority and control exists, which is an inhibiting factor for many consumers.
- Relatively immature technology: As compared to traditional IT systems that have benefited from decades of research, blockchain is still a new technology and requires a lot of research to achieve maturity.
- Privacy and confidentiality: Privacy is a concern on public blockchains such as Bitcoin where everyone can see every single transaction. This transparency is not desirable in many industries such as the financial, law, or medical sectors. This is also a known concern and a lot of valuable research with some impeccable solutions has already been developed. However, further research is still required to drive the mass adoption of blockchain.
All of these issues and possible solutions will be discussed in detail in Chapter 21, Scalability and Other Challenges.
You now know the basics of blockchain and its benefits and limitations. Now, let's take a look at the various types of blockchain that exist.
Types of blockchain
Based on the way that blockchain has evolved over the last few years, it can be divided into multiple categories with distinct, though sometimes partially overlapping attributes. You should note that the tiers described earlier in the chapter are a different concept, whereby the logical categorization of blockchain, based upon its evolution and usage, is presented.
In this section, we will examine the different types of blockchains from a technical and business use perspective. These blockchain types can occur on any blockchain tier, as there is no direct relationship between those tiers mentioned earlier and the various types of blockchain.
In this section, we'll examine:
- Distributed ledgers
- Distributed Ledger Technology (DLT)
- Blockchains
- Ledgers
Distributed ledgers
First, I need to clarify an ambiguity. It should be noted that a distributed ledger is a broad term describing shared databases; hence, all blockchains technically fall under the umbrella of shared databases or distributed ledgers. Although all blockchains are fundamentally distributed ledgers, all distributed ledgers are not necessarily blockchains.
A critical difference between a distributed ledger and a blockchain is that a distributed ledger does not necessarily consist of blocks of transactions to keep the ledger growing. Rather, a blockchain is a special type of shared database that is comprised of blocks of transactions. An example of a distributed ledger that does not use blocks of transactions is R3's Corda (https://www.corda.net). Corda is a distributed ledger that is developed to record and manage agreements and is especially focused on the financial services industry. On the other hand, more widely known blockchains like Bitcoin and Ethereum make use of blocks to update the shared database.
As the name suggests, a distributed ledger is distributed among its participants and spread across multiple sites or organizations. This type of ledger can be either private or public. The fundamental idea here is that, unlike many other blockchains, the records are stored contiguously instead of being sorted into blocks. This concept is used in Ripple, which is a blockchain- and cryptocurrency-based global payment network.
Distributed Ledger Technology
It should be noted that over the last few years, the terms distributed ledger or DLT have grown to be commonly used to describe blockchain in the finance industry. Sometimes, blockchain and DLT are used interchangeably. Though this is not entirely accurate, it is how the term has evolved recently, especially in the finance sector. In fact, DLT is now a very active and thriving area of research in the financial sector. From a financial sector point of view, DLTs are permissioned blockchains that are used by consortiums. DLTs usually serve as a shared database, with all participants known and verified. They do not have a cryptocurrency and do not require mining to secure the ledger.
At a broader level, DLT is an umbrella term that represents Distributed Ledger Technology as a whole, comprising of blockchains and distributed ledgers of different types.
Public blockchains
As the name suggests, public blockchains are not owned by anyone. They are open to the public, and anyone can participate as a node in the decision-making process. Users may or may not be rewarded for their participation. All users of these "permissionless" or "un-permissioned" ledgers maintain a copy of the ledger on their local nodes and use a distributed consensus mechanism to decide the eventual state of the ledger. Bitcoin and Ethereum are both considered public blockchains.
Private blockchains
As the name implies, private blockchains are just that—private. That is, they are open only to a consortium or group of individuals or organizations who have decided to share the ledger among themselves. There are various blockchains now available in this category, such as Kadena and Quorum. Optionally, both of these blockchains can also run in public mode if required, but their primary purpose is to provide a private blockchain.
Semi-private blockchains
With semi-private blockchains, part of the blockchain is private and part of it is public. Note that this is still just a concept today, and no real-world proofs of concept have yet been developed. With a semi-private blockchain, the private part is controlled by a group of individuals, while the public part is open for participation by anyone.
This hybrid model can be used in scenarios where the private part of the blockchain remains internal and shared among known participants, while the public part of the blockchain can still be used by anyone, optionally allowing mining to secure the blockchain. This way, the blockchain as a whole can be secured using PoW, thus providing consistency and validity for both the private and public parts. This type of blockchain can also be called a "semi-decentralized" model, where it is controlled by a single entity but still allows for multiple users to join the network by following appropriate procedures.
Sidechains
More precisely known as "pegged sidechains," this is a concept whereby coins can be moved from one blockchain to another and then back again. Typical uses include the creation of new altcoins (alternative cryptocurrencies) whereby coins are burnt as a proof of an adequate stake. "Burnt" or "burning the coins" in this context means that the coins are sent to an address that is un-spendable, and this process makes the "burnt" coins irrecoverable. This mechanism is used to bootstrap a new currency or introduce scarcity, which results in the increased value of the coin.
This mechanism is also called "Proof of Burn" and is used as an alternative method for distributed consensus to PoW and Proof of Stake (PoS). The example provided previously for burning coins applies to a one-way pegged sidechain. The second type is called a two-way pegged sidechain, which allows the movement of coins from the main chain to the sidechain and back to the main chain when required.
This process enables the building of smart contracts for the Bitcoin network. Rootstock is one of the leading examples of a sidechain, which enables smart contract development for Bitcoin using this paradigm. It works by allowing a two-way peg for the Bitcoin blockchain, and this results in much faster throughput.
Permissioned ledger
A permissioned ledger is a blockchain where participants of the network are already known and trusted. Permissioned ledgers do not need to use a distributed consensus mechanism; instead, an agreement protocol is used to maintain a shared version of the truth about the state of the records on the blockchain. In this case, for verification of transactions on the chain, all verifiers are already preselected by a central authority and, typically, there is no need for a mining mechanism.
By definition, there is also no requirement for a permissioned blockchain to be private, as it can be a public blockchain but with regulated access control. For example, Bitcoin can become a permissioned ledger if an access control layer is introduced on top of it that verifies the identity of a user and then allows access to the blockchain.
Shared ledger
This is a generic term that is used to describe any application or database that is shared by the public or a consortium. Generally, all blockchains fall into the category of a shared ledger.
Fully private and proprietary blockchains
There is no mainstream application of these types of blockchains, as they deviate from the core concept of decentralization in blockchain technology. Nonetheless, in specific private settings within an organization, there could be a need to share data and provide some level of guarantee of the authenticity of the data.
An example of this type of blockchain might be to allow for collaboration and the sharing of data between various government departments. In that case, no complex consensus mechanism is required, apart from simple SMR and an agreement protocol with known central validators. Even in private blockchains, tokens are not really required, but they can be used as a means of transferring value or representing some real-world assets.
Tokenized blockchains
These blockchains are standard blockchains that generate cryptocurrency as a result of a consensus process via mining or initial distribution. Bitcoin and Ethereum are prime examples of this type of blockchain.
Tokenless blockchains
These blockchains are designed in such a way that they do not have the basic unit for the transfer of value. However, they are still valuable in situations where there is no need to transfer value between nodes and only the sharing of data among various trusted parties is required. This is similar to fully private blockchains, the only difference being that the use of tokens is not required. This can also be thought of as a shared distributed ledger used for storing and sharing data between the participants. It does have its benefits when it comes to immutability, tamper proofing, security, and consensus-driven updates but is not used for a common blockchain application of value transfer or cryptocurrency. Most of the permissioned blockchains can be seen as an example of tokenless blockchains, for example, Hyperledger Fabric or Quorum. Tokens can be built on these chains as an application, but intrinsically these blockchains do not have a token associated with them.
All the aforementioned terminologies are used in literature, but fundamentally all these blockchains are distributed ledgers and fall under the top-level category of DLTs. We can view these different types in the simple chart as follows:
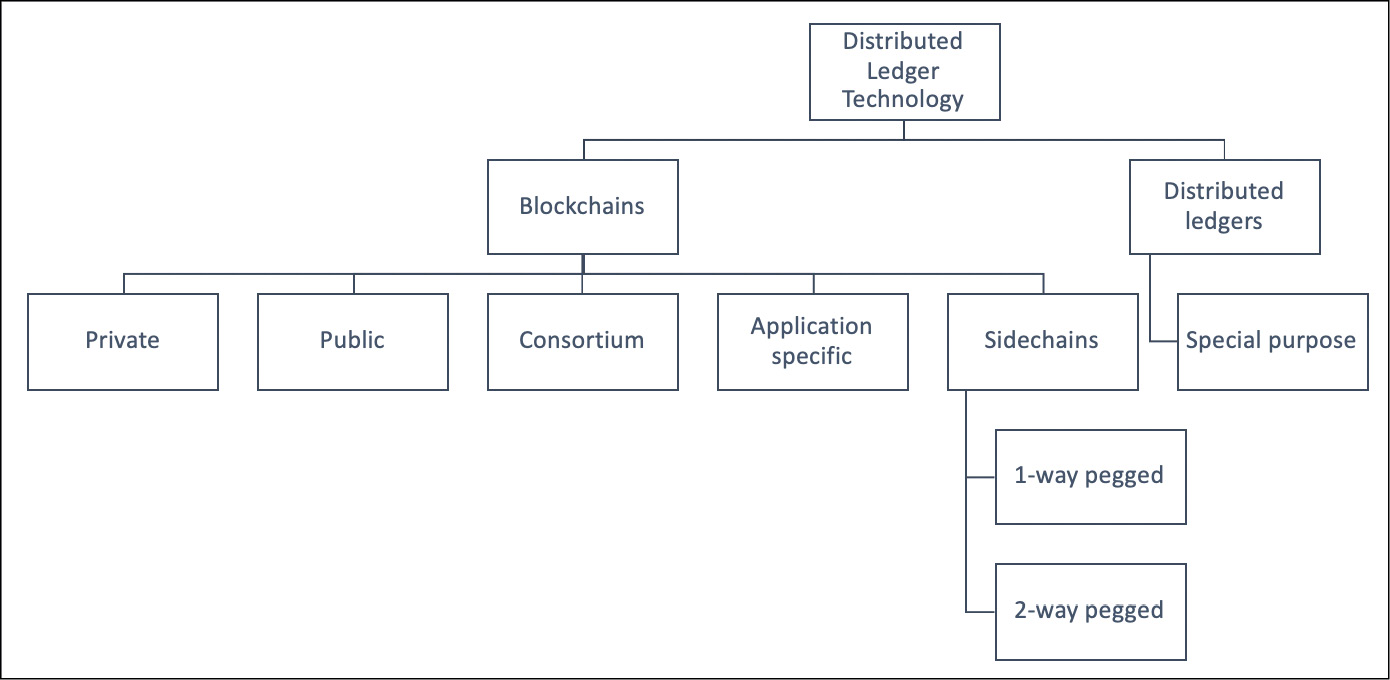
Figure 1.10: DLT hierarchy
This ends our examination of the various types of blockchain. We'll now move on to the next section to discuss the concept of consensus.
Consensus
Consensus is the backbone of a blockchain, as it provides the decentralization of control through an optional process known as mining. The choice of the consensus algorithm to utilize is governed by the type of blockchain in use; that is, not all consensus mechanisms are suitable for all types of blockchains. For example, in public permissionless blockchains, it would make sense to use PoW instead of mechanisms that are more suitable for permissioned blockchains, such as Proof of Authority (PoA) or traditional Byzantine fault-tolerant consensus mechanisms. Therefore, it is essential to choose an appropriate consensus algorithm for a particular blockchain project.
Consensus is a process of achieving agreement between distrusting nodes on the final state of data. To achieve consensus, different algorithms are used. It is easy to reach an agreement between two nodes (in client-server systems, for example), but when multiple nodes are participating in a distributed system and they need to agree on a single value, it becomes quite a challenge to achieve consensus. This process of attaining agreement on a common state or value among multiple nodes despite the failure of some nodes is known as distributed consensus.
Consensus mechanism
A consensus mechanism is a set of steps that are taken by most or all nodes in a blockchain to agree on a proposed state or value. For more than three decades, this concept has been researched by computer scientists in industry and academia. With the advent of blockchain and Bitcoin, consensus mechanisms have come into the limelight again and gained considerable popularity.
There are various requirements for a consensus mechanism. The following describes these requirements:
- Agreement: All honest nodes decide on the same value.
- Integrity: This is a requirement that no node can make the decision more than once in a single consensus cycle.
- Validity: The value agreed upon by all honest nodes must be the same as the initial value proposed by at least one honest node.
- Fault tolerant: The consensus algorithm should be able to run correctly in the presence of faulty or malicious nodes (Byzantine nodes).
- Termination: All honest nodes terminate the execution of the consensus process and eventually reach a decision.
Having seen these general requirements, we'll now look at the different types of consensus mechanisms.
Types of consensus mechanisms
All consensus mechanisms are developed to deal with faults in a distributed system and to allow distributed systems to reach a final state of agreement. There are two general categories of consensus mechanisms. These categories deal with all types of faults (fail-stop types or arbitrary). These common types of consensus mechanisms are as follows:
- Proof-based consensus mechanisms: This arrangement requires nodes to compete in a leader-election lottery, and the node that wins proposes the final value. The algorithm works on the principle of providing proof of some work and the possession of some authority or tokens to win the right of proposing the next block. For example, the PoW mechanism used in Bitcoin falls into this category, where a miner who solves the computational puzzle as proof of computational effort expended wins the right to add the next block to the blockchain.
- Traditional fault tolerance-based: With no compute-intensive operations, such as partial hash inversion (as in Bitcoin PoW), this type of consensus mechanism relies on a simple scheme of nodes that publish and verify signed messages in a number of phases. Eventually, when a certain number of messages are received over a period of rounds (phases), then an agreement is reached.
To achieve fault tolerance, replication is used. This is a standard and widely used method to achieve fault tolerance. In general, there are two types of faults that a node can experience:
- Fail-stop faults: This type of fault occurs when a node merely has crashed. Fail-stop faults are the easier ones to deal with of the two fault types. Paxos or the RAFT protocol, introduced earlier in this chapter, are normally used to deal with this type of fault. These faults are simpler to deal with.
- Byzantine faults: The second type of fault is one where the faulty node exhibits malicious or inconsistent behavior arbitrarily. This type is difficult to handle since it can create confusion due to misleading information. This can be a result of an attack by adversaries, a software bug, or data corruption. SMR protocols such as Practical Byzantine Fault Tolerance (PBFT) was developed to address this second type of faults.
Many other implementations of consensus protocols have been proposed in traditional distributed systems. Paxos is the most famous of these protocols. It was introduced by Leslie Lamport in 1989. With Paxos, nodes are assigned various roles such as Proposer, Acceptor, and Learner. Nodes or processes are named replicas, and consensus is achieved in the presence of faulty nodes by an agreement among a majority of nodes.
An alternative to Paxos is RAFT, which works by assigning any of three states; that is, Follower, Candidate, or Leader to the nodes. A Leader is elected after a Candidate node receives enough votes, and all changes then have to go through the Leader. The Leader commits the proposed changes once replication on the majority of the follower nodes is completed.
We will briefly touch on some aspects of consensus in blockchain now, but more detail on the theory of consensus mechanisms from a distributed system point of view and also from the blockchain perspective will be presented in Chapter 5, Consensus Algorithms.
Consensus in blockchain
Consensus is a distributed computing concept that has been used in blockchain in order to provide a means of agreeing to a single version of the truth by all peers on the blockchain network. This concept was previously discussed in the distributed systems section of this chapter. In this section, we will address consensus in the context of blockchain technology. Some concepts presented following are still relevant to the distributed systems theory, but they are explained from a blockchain perspective.
Roughly, the following describes the two main categories of consensus mechanisms:
- Proof-based, leader-election lottery-based, or the Nakamoto consensus whereby a leader is elected at random (using an algorithm) and proposes a final value. This category is also referred to as the fully decentralized or permissionless type of consensus mechanism. This type is well used in the Bitcoin and Ethereum blockchain in the form of a PoW mechanism.
- Byzantine fault tolerance (BFT)-based is a more traditional approach based on rounds of votes. This class of consensus is also known as the consortium or permissioned type of consensus mechanism.
BFT-based consensus mechanisms perform well when there are a limited number of nodes, but they do not scale well. On the other hand, leader-election lottery-based (PoW) consensus mechanisms scale very well but perform very slowly. As there is significant research being conducted in this area, new types of consensus mechanisms are also emerging, such as the semi-decentralized type, which is used in the Ripple network. The Ripple network will be discussed in detail in this book's online content pages, here: https://static.packt-cdn.com/downloads/Altcoins_Ethereum_Projects_and_More_Bonus_Content.pdf. There are also various other proposals out there, which are trying to find the right balance between scalability and performance. Some notable projects include PBFT, Hybrid BFT, BlockDAG, Tezos, Stellar, and GHOST.
The consensus algorithms available today, or that are being researched in the context of blockchain, are presented as follows. The following is not an exhaustive list, but it includes all notable algorithms:
- Proof of Work (PoW): This type of consensus mechanism relies on proof that adequate computational resources have been spent before proposing a value for acceptance by the network. This scheme is used in Bitcoin, Litecoin, and other cryptocurrency blockchains. Currently, it is the only algorithm that has proven to be astonishingly successful against any collusion attacks on a blockchain network, such as the Sybil attack. The Sybil attack will be discussed in Chapter 6, Introducing Bitcoin.
- Proof of Stake (PoS): This algorithm works on the idea that a node or user has an adequate stake in the system; that is, the user has invested enough in the system so that any malicious attempt by that user would outweigh the benefits of performing such an attack on the network. This idea was first introduced by Peercoin, and it is going to be used in the Ethereum blockchain version called Serenity. Another important concept in PoS is coin age, which is a criterion derived from the amount of time and number of coins that have not been spent. In this model, the chances of proposing and signing the next block increase with the coin age.
- Delegated Proof of Stake (DPoS): This is an innovation over standard PoS, whereby each node that has a stake in the system can delegate the validation of a transaction to other nodes by voting. It is used in the BitShares blockchain.
- Proof of Elapsed Time (PoET): Introduced by Intel in 2016, PoET uses a Trusted Execution Environment (TEE) to provide randomness and safety in the leader-election process via a guaranteed wait time. It requires the Intel SGX (Software Guard Extensions) processor to provide the security guarantee for it to be secure. This concept is discussed in more detail in Chapter 17, Hyperledger, in the context of the Intel Sawtooth Lake blockchain project.
- Proof of Deposit (PoD): In this case, nodes that wish to participate in the network have to make a security deposit before they can mine and propose blocks. This mechanism is used in the Tendermint blockchain.
- Proof of Importance (PoI): This idea is significant and different from PoS. PoI not only relies on how large a stake a user has in the system, but it also monitors the usage and movement of tokens by the user in order to establish a level of trust and importance. It is used in the NEM coin blockchain. More information about this coin is available from NEM's website (https://nem.io).
- Federated consensus or federated Byzantine consensus: This mechanism is used in the stellar consensus protocol. Nodes in this protocol retain a group of publicly-trusted peers and propagate only those transactions that have been validated by the majority of trusted nodes.
- Reputation-based mechanisms: As the name suggests, a leader is elected by the reputation it has built over time on the network. It is based on the votes of other members.
- Practical Byzantine Fault Tolerance (PBFT): This mechanism achieves SMR, which provides tolerance against Byzantine nodes. Various other protocols, including PBFT, PAXOS, RAFT, and Federated Byzantine Agreement (FBA), are also being used or have been proposed for use in many different implementations of distributed systems and blockchains.
- Proof of Activity (PoA): This scheme is a combination of PoS and PoW, which ensures that a stakeholder is selected in a pseudorandom but uniform fashion. This is a comparatively more energy-efficient mechanism as compared to PoW. It utilizes a new concept called "Follow the Satoshi." In this scheme, PoW and PoS are combined together to achieve consensus and a good level of security. This scheme is more energy efficient as PoW is used only in the first stage of the mechanism; after the first stage, it switches to PoS, which consumes negligible energy. We will discuss these ideas further in Chapter 7, Bitcoin Network and Payments, where protocols are reviewed in the context of advanced Bitcoin protocols.
- Proof of Capacity (PoC): This scheme uses hard disk space as a resource to mine the blocks. This is different from PoW, where CPU resources are used. In PoC, hard disk space is utilized for mining and, as such, is also known as hard drive mining. This concept was first introduced in the BurstCoin cryptocurrency.
- Proof of Storage: This scheme allows for the outsourcing of storage capacity. This scheme is based on the concept that a particular piece of data is probably stored by a node, which serves as a means to participate in the consensus mechanism. Several variations of this scheme have been proposed, such as Proof of Replication, Proof of Data Possession, Proof of Space, and Proof of Space-time.
- Proof of Authority (PoA): This scheme utilizes the identity of the participants called validators as a stake on the network. Validators are known and have the authority to propose new blocks. Validators propose the new blocks and validate them as per blockchain rules. Commonly used PoA algorithms are Clique and Aura.
Some prominent protocols in blockchain will be discussed in detail in Chapter 5, Consensus Algorithms. In this chapter, a light introduction is presented only.
Remember, earlier in this chapter we said that distributed systems are difficult to build and a distributed system cannot have consistency, availability, and partition tolerance at the same time. This is a proven result; however, in blockchain, it seems that this theorem is somehow violated. In the next section, we will introduce the CAP theorem formally and discuss why blockchain appears to achieve all three properties simultaneously.
CAP theorem and blockchain
The CAP theorem, also known as Brewer's theorem, was introduced by Eric Brewer in 1998 as a conjecture. In 2002, it was proven as a theorem by Seth Gilbert and Nancy Lynch. The theorem states that any distributed system cannot have consistency, availability, and partition tolerance simultaneously:
- Consistency is a property that ensures that all nodes in a distributed system have a single, current, and identical copy of the data.
- Availability means that the nodes in the system are up, accessible for use, and are accepting incoming requests and responding with data without any failures as and when required. In other words, data is available at each node and the nodes are responding to requests.
- Partition tolerance ensures that if a group of nodes is unable to communicate with other nodes due to network failures, the distributed system continues to operate correctly. This can occur due to network and node failures.
A Venn diagram is commonly used to visualize the CAP theorem:

Figure 1.11: CAP theorem
The preceding diagram shows that only two properties at a time can be achieved. Either AP, CA, or CP.
In summary:
- If we opt for CP (consistency and partition tolerance), we sacrifice availability.
- If we opt for AP (availability and partition tolerance), we sacrifice consistency.
- If we opt for AC (availability and consistency), we sacrifice partition tolerance.
Usually, a network partition cannot be ignored; therefore, the choice mostly becomes either consistency or availability in the case of a network partition.
As shown previously, a distributed system cannot have consistency, availability, and partition tolerance simultaneously. This can be explained with the following example.
Let's imagine that there is a distributed system with two nodes. Now, let's apply the three theorem properties on this smallest of possible distributed systems only with two nodes:
- Consistency is achieved if both nodes have the same shared state; that is, they have the same up-to-date copy of the data.
- Availability is achieved if both nodes are up and running and responding with the latest copy of data.
- Partition tolerance is achieved if, despite communication failure or delay between nodes, the network (distributed system) continues to operate.
Now think of a scenario where a partition occurs, and nodes can no longer communicate with each other. If new updated data comes in now, it can only be updated on one node only. In that case, if the node accepts the update, then only that one node in the network is updated and therefore consistency is lost. Now, if the update is rejected by the node, that would result in loss of availability. In that case, due to partition tolerance, both availability and consistency are unachievable.
This is strange because somehow blockchain manages to achieve all of these properties—or does it?
It seems that the CAP theorem is violated by blockchain, especially in its most successful implementation, Bitcoin. However, this is not the case. In blockchains, consistency is sacrificed in favor of availability and partition tolerance. In this scenario, Consistency (C) on the blockchain is not achieved simultaneously with Partition tolerance (P) and Availability (A), but it is achieved over time. This is called eventual consistency, where consistency is achieved as a result of validation from multiple nodes over time. It means that there can be a temporary disagreement between nodes on the final state, but it is eventually agreed upon. For example, in Bitcoin, multiple transaction confirmations are required to achieve a good level of confidence that transactions may not be rolled back in the future and eventually a consistent view of transaction history is available to all nodes. Multiple confirmations of a transaction over time provide eventual consistency in Bitcoin. For this purpose, the process of mining was introduced in Bitcoin. Mining is a process that facilitates the achievement of consensus by using the PoW algorithm. At a higher level, mining can be defined as a process that is used to add more blocks to the blockchain. We will cover more on this later in Chapter 6, Introducing Bitcoin.
Summary
This chapter introduced blockchain technology at an advanced level. First, we discussed blockchain's progress toward becoming a mature technology, followed by some basic concepts about distributed systems, and then the history of blockchain was reviewed. Concepts such as e-cash were also discussed.
Various definitions of blockchain from different points of view were presented. Some applications of blockchain technology were also introduced. Next, different types of blockchain were explored. Finally, the benefits and limitations of this new technology were also examined. Some topics such as blockchain scalability and adaptability issues were intentionally introduced only lightly, as they will be discussed in depth in later chapters.
In the next chapter, we will introduce the concept of decentralization, which is central to the idea behind blockchains and their vast number of applications.
