9
Alternative Coins
Since the initial success of Bitcoin, many alternative currency projects have been launched. Bitcoin was released in 2009, and the first alternative coin project (named Namecoin) was introduced in 2011. In 2013 and 2014, the alternative coins (altcoin) market grew exponentially, and many different types of alternative coin project were started.
A few of those became a success, whereas many were unpopular due to less interest and as a result, they did not succeed. A few were pump and dump scams that surfaced for some time but soon disappeared. Alternative approaches to Bitcoin can be divided broadly into two categories, based on the primary purpose of their development. If the primary goal is to build a decentralized blockchain platform, they are called alternative chains; if the sole purpose of the alternative project is to introduce a new virtual currency, it is called an altcoin.
Alternative blockchains are discussed in detail in this book's bonus online content pages, here: https://static.packt-cdn.com/downloads/Altcoins_Ethereum_Projects_and_More_Bonus_Content.pdf.
This chapter is mainly dedicated to the foundations and features of altcoins, whose primary purpose is to introduce a new virtual currency (coin), although some material will also be presented on the topic of alternative protocols built on top of Bitcoin to provide various services. These include concepts such as Namecoin, covered in this book's bonus content repository, the primary purpose of which is to provide decentralized naming and identity services instead of currency.
Introducing altcoins
Currently, as of mid-2020, there are thousands of altcoins on the market, and they hold some monetary value, such as Namecoin, Zcash, Litecoin, and many others. Zcash is a more successful altcoin, introduced in 2016. On the other hand, Primecoin did not gain much popularity, but it is still in use. Many of these alternative projects are direct forks of Bitcoin source code, although some have been written from scratch. Some altcoins set out to address Bitcoin limitations such as privacy. Some others offer different types of mining, changes in block times, and distribution schemes.
By definition, an altcoin is generated in the case of a hard fork. If Bitcoin has a harder fork, then the other, older chain is effectively considered another coin. However, there is no established rule as to which chain becomes the altcoin. This has happened with Ethereum, where a hard fork caused a new currency, Ethereum Classic (ETC), to come into existence in addition to the Ethereum (ETH) currency.
Ethereum classic is the old chain and Ethereum is the new chain after the fork. Such a contentious hard fork is not desirable for a few reasons. First, it is against the true spirit of decentralization as the Ethereum foundation, a central entity, decided to go ahead with the hard fork, even though not everyone agreed to the proposition; second, it also splits the user community due to disagreement over the hard fork. Although a hard fork, in theory, generates an altcoin, it is limited in what it can offer because, even if the change results in a hard fork, usually, there are no drastic changes around the fundamental parameters of the coin. They typically remain the same. For this reason, it is desirable to either write a new coin from scratch or fork the Bitcoin (or another coin's source code) to create a new currency with the desired parameters and features.
Altcoins must be able to attract new users, trades, and miners; otherwise, the currency will have no value. Currency gains its value, especially in the virtual currency space, due to the network effect and its acceptability by the community. If a coin fails to attract enough users, then soon, it will be forgotten. Users can be attracted by providing an initial amount of coins and can be achieved by using various methods. There is, however, a risk that if the new coin does not perform well, then their initial investment may be lost. Methods of providing an initial number of altcoins are as follows:
- Create a new blockchain: Altcoins can create a new blockchain and allocate coins to initial miners, but this approach is now unpopular due to many scam schemes, or pump and dump schemes, where initial miners made a profit with the launch of a new currency and then disappeared.
- Proof of Burn (PoB): Another approach to allocating initial funds to a new altcoin is PoB, also called a one-way peg or price ceiling. In this method, users permanently destroy a certain quantity of bitcoins in proportion to the number of altcoins to be claimed. For example, if 10 bitcoin were destroyed, then altcoins can have a value no greater than the Bitcoin that was destroyed. This means that bitcoins are being converted into altcoin by burning them.
- Proof of ownership: Instead of permanently destroying bitcoins, an alternative method is to prove that users own a certain number of bitcoins. This proof of ownership can be used to claim altcoins by tethering altcoin blocks to Bitcoin blocks. For example, this can be achieved by merged mining in which, effectively, Bitcoin miners can mine altcoin blocks while mining for bitcoins without any extra work. Merged mining will be explained later in this chapter.
- Pegged sidechains: Sidechains, as the name suggests, are blockchains separate from the Bitcoin network, but Bitcoin can be transferred to them. Altcoins can also be transferred back to the Bitcoin network. This concept is called a two-way peg.
Investing and trading these alternative coins is also big business, albeit not as big as Bitcoin but enough to attract new investors and traders and provide liquidity to the market. Alternative coin market capitalization is shown as follows:

Figure 9.1: Top 10 cryptocurrencies, excluding Bitcoin, which is the topmost
The current market cap (as of June, 2020), from https://coinmarketcap.com/) of the top 10 coins is shown as follows:
|
Cryptocurrency |
Market cap in US$ |
Price in US$ |
|
Bitcoin |
$173,083,267,448 |
$9,402.42 |
|
Ethereum |
$25,844,303,523 |
$231.98 |
|
Tether |
$9,217,432,271 |
$1.00 |
|
XRP |
$8,460,691,410 |
$0.191168 |
|
Bitcoin Cash |
$4,372,112,481 |
$237.11 |
|
Bitcoin SV |
$3,232,271,412 |
$175.31 |
|
Litecoin |
$2,831,861,371 |
$43.58 |
|
Binance Coin |
$2,521,729,503 |
$16.21 |
|
EOS |
$2,368,331,983 |
$2.54 |
|
Cardano |
$2,127,729,709 |
$0.08 |
This table shows that the Combined Altcoin Market Capitalization is roughly around USD 234 billion.
The following pie chart shows the market cap of the top three cryptocurrencies as of late 2019. This shows that Bitcoin has the largest market capitalization.

Figure 9.2: Top three cryptocurrencies
Note that market capitalization varies with time and up-to-date data can be obtained from https://coinmarketcap.com/charts/#dominance-percentage or similar websites on the internet.
There are various factors and new concepts that have been introduced with alternative coins. Many concepts were invented even before Bitcoin, but with Bitcoin, not only new concepts, such as a solution to the double spending problem, were introduced, but also previous ideas such as hashcash and Proof of Work (PoW) were used ingeniously and came into the limelight.
Since then, with the introduction of alternative coin projects, various new techniques and concepts have been developed and introduced. To appreciate the current landscape of alternative cryptocurrencies, it is essential to understand some theoretical concepts first.
Theoretical foundations
In this section, various theoretical concepts will be introduced that have been developed with the introduction of different altcoins in the past few years.
Alternatives to Proof of Work
The PoW scheme in the context of cryptocurrency was first used in Bitcoin and served as a mechanism to provide assurance that a miner had completed the required amount of work to find a block. This process, in turn, provided decentralization, security, and stability for the blockchain. This is the primary vehicle in Bitcoin for providing decentralized distributed consensus. PoW schemes are required to have a much-desired property called progress freeness, which means that the reward for consuming computational resources should be random and proportional to the contribution made by the miners. In this case, some chance of winning the block reward is given to even those miners who have comparatively less computational power.
The term progress freeness was introduced by Arvind Narayanan et al. in the book Bitcoin and Cryptocurrency Technologies: A Comprehensive Introduction (Princeton University Press, 2016). Other requirements for mining computational puzzles include adjustable difficulty and quick verification. Adjustable difficulty ensures that the difficulty target for mining on the blockchain is regulated accordingly in response to increased hashing power and the number of users.
Quick verification is a property that means that mining computational puzzles should be easy and quick to verify. Another aspect of the PoW scheme, especially the one used in Bitcoin (Double SHA-256), is that since the introduction of ASICs, the power is shifting toward miners or mining pools who can afford to operate large-scale ASIC farms. This power shift challenges the core philosophy of the decentralization of Bitcoin.
There are a few alternatives that have been proposed such as ASIC-resistant puzzles, which are designed in such a way that building ASICs for solving this puzzle is infeasible and does not result in a major performance gain over commodity hardware. A common technique used for this purpose is to apply a class of computationally hard problems called memory hard computational puzzles. The core idea behind this method is that as puzzle solving requires a large amount of memory, it is not feasible to be implemented on ASIC-based systems.
This technique was initially used in Litecoin and Tenebrix, where the Scrypt hash function was used as an ASIC-resistant PoW scheme. Even though this scheme was initially advertised as ASIC resistant, Scrypt ASICs became available a few years ago, disproving the original claim by Litecoin. This happened because even if Scrypt is a memory-intensive mechanism, initially, it was thought that building ASICs with large memories is difficult due to technical and cost limitations. This is no longer the case because memory hardware is increasingly becoming cheaper. Also, with the ability to produce nanometer-scale circuits, it is possible to build ASICs that can run the Scrypt algorithm.
Another approach to ASIC resistance is where multiple hash functions are required to be calculated to provide PoW. This is also called a chained hashing scheme. The rationale behind this idea is that designing multiple hash functions on an ASIC is not very feasible. The most common example is the X11 memory hard function implemented in Dash. X11 comprises 11 SHA-3 contestants where one algorithm outputs the calculated hash to the next algorithm until all 11 algorithms are used in a sequence. These algorithms include BLAKE, BMW, Groestl, JH, Keccak, Skein, Luffa, CubeHash, SHAvite, SIMD, and ECHO.
This approach did provide some resistance to ASIC development initially, but now, ASIC miners are available commercially and support mining of X11 and similar schemes. A recent example is ASIC Baikal Miner, which supports X11, X13, X14, and X15 mining. Other examples include miners such as the iBeLink DM384M X11 miner and the PinIdea X11 ASIC miner.
Perhaps another approach could be to design self-mutating puzzles that intelligently or randomly change the PoW scheme or its requirements as a function of time. This strategy will make it almost impossible to be implemented in ASICs as it will require multiple ASICs to be designed for each function. Also, randomly changing schemes would be practically impossible to handle in ASICs. At the moment, it is unclear how this can be achieved practically.
PoW does have various drawbacks, and the biggest of all is energy consumption. It is estimated that the total electricity consumed by Bitcoin miners currently is more than that of Greece at 59.61 Terawatt hash (TWh). This is huge, and all that power is, in a way, wasted; in fact, no useful purpose is served except mining. Environmentalists have raised real concerns about this situation. In addition to electricity consumption, the carbon footprint is also very high, with it currently being estimated at around 253 kg of CO2 per transaction.
The following graph shows the scale of Bitcoin energy consumption compared to other countries. This consumption is only expected to grow, and it is estimated that by the end of 2020, the energy consumption will reach approximately 125 TWh per year:

Figure 9.3: Energy consumption by country
The preceding graph has taken from the website that tracks this subject. It is available at https://digiconomist.net/bitcoin-energy-consumption.
It has been proposed that PoW puzzles can be designed in such a way that they serve two purposes. First, their primary purpose is in consensus mechanisms, and second, they serve to perform some useful scientific computation. This way, not only can the schemes be used in mining, but they can also help to solve other scientific problems. This proof of useful work has been recently put into practice by Primecoin, where the requirement is to find special prime number chains known as Cunningham chains and bi-twin chains. As the study of prime number distribution has special significance in scientific disciplines such as physics, mining Primecoin miners not only achieves the block reward but also helps in finding the special prime numbers.
Proof of Storage
Also known as proof of retrievability, this is another type of proof of useful work that requires storage of a large amount of data. Introduced by Microsoft Research, this scheme provides a useful benefit of distributing the storage of archival data. Miners are required to store a pseudo, randomly-selected subset of large data to perform mining.
Proof of Stake (PoS)
This proof is also called virtual mining. This is another type of mining puzzle that has been proposed as an alternative to traditional PoW schemes. It was first proposed in Peercoin in August 2012. In this scheme, the idea is that users are required to demonstrate the possession of a certain amount of currency (coins), thus proving that they have a stake in the coin.
The simplest form of this stake is where mining is made comparatively easier for those users who demonstrably own larger amounts of digital currency. The benefits of this scheme are twofold; first, acquiring large amounts of digital currency is relatively difficult as compared to buying high-end ASIC devices, and second, it results in saving computational resources. Various forms of stake have been proposed and are briefly discussed in the following subsection.
Various types of stake
Different type of stakes will now be introduced in the following subsections.
Proof of coinage
The age of a coin is the time since the coins were last used or held. This is a different approach from the usual form of PoS, where mining is made easier for users who have the highest stake in the altcoin. In the coin-age-based approach, the age of the coin (coinage) is reset every time a block is mined. The miner is rewarded for holding and not spending coins for a period of time. This mechanism has been implemented in Peercoin combined with PoW in a creative way.
The difficulty of mining puzzles (PoW) is inversely proportional to the coinage, meaning that if miners consume some coinage using coin-stake transactions, then the PoW requirements are relieved.
Proof of Deposit (PoD)
This is a type of PoS. The core idea behind this scheme is that newly minted blocks by miners are made unspendable for a certain period. More precisely, the coins get locked for a set number of blocks during the mining operation. The scheme works by allowing miners to perform mining at the cost of freezing a certain number of coins for some time.
Proof of Burn (PoB)
As an alternate expenditure to computing power, PoB, in fact, destroys a certain number of Bitcoins to get equivalent altcoins. This is commonly used when starting up a new coin projects as a means to provide a fair initial distribution. This can be considered an alternative mining scheme where the value of the new coins comes from the fact that, previously, a certain number of coins have been destroyed.
Proof of Activity (PoA)
This scheme is a hybrid of PoW and PoS. In this scheme, blocks are initially produced using PoW, but then each block randomly assigns three stakeholders that are required to digitally sign it. The validity of subsequent blocks is dependent on the successful signing of previously randomly chosen blocks.
There is, however, a possible issue known of the nothing at stake problem, where it would be trivial to create a fork of the blockchain. This is possible because in PoW, appropriate computational resources are required to mine, whereas in PoS, there is no such requirement; as a result, an attacker can try to mine on multiple chains using the same coin.
Non-outsourceable puzzles
The key motivation behind this puzzle is to develop resistance against the development of mining pools. Mining pools, as previously discussed, offer rewards to all participants in proportion to the computing power they consume. However, in this model, the mining pool operator is a central authority to whom all the rewards go and who can enforce specific rules. Also, in this model, all miners only trust each other because they are working toward a common goal, in the hope of the pool manager getting the reward. Non-outsourceable puzzles are a scheme that allows miners to claim rewards for themselves; consequently, pool formation becomes unlikely due to inherent mistrust between anonymous miners.
There are also various other alternatives to PoW, some of which have been described in Chapter 1, Blockchain 101. Some will be explained later in this book in Chapter 17, Hyperledger, and Chapter 21, Scalability and Other Challenges. As this is an ongoing area of research, new alternatives will keep emerging as blockchain technology grows.
In this section, we covered alternatives to PoW schemes. These schemes largely fall under the umbrella of PoS mechanisms. We know that PoW schemes are based on the difficulty of performing some work to prove that the required amount of resources has been spent to win the right to announce a new block. A question arises here regarding how this difficulty is calculated in a blockchain, as well as how the balance between difficulty and coin production is maintained. Also, in order to maintain a constant supply (production) of coins, the difficulty of the network also needs to be adjusted overtime. For this purpose, PoW algorithms use difficulty adjustment and retargeting algorithms, which are simple arithmetic formulas that help adjust the difficulty of solving the PoW problem. We'll introduce the core ideas of these calculations in the next section.
Difficulty adjustment and retargeting algorithms
The concept of difficulty retargeting algorithms has been introduced with the advent of Bitcoin and associated consensus mechanisms. In Bitcoin, a difficulty target is calculated simply by the following equation; other coins have either developed their own algorithms or implemented a modified version of the Bitcoin difficulty algorithm:
T = Time previous * time actual / 2016 * 10 min
The core idea behind difficulty regulation in Bitcoin is that a generation of 2016 blocks should take roughly around 2 weeks (inter-block time should be around 10 minutes). If it takes longer than 2 weeks to mine 2016 blocks, then the difficulty is decreased, and if it takes less than 2 weeks to mine 2016 blocks, then the difficulty is increased. When ASICs were introduced due to a high block generation rate, the difficulty increased exponentially, and that is one drawback of PoW algorithms that are not ASIC resistant. This leads to mining power centralization.
This also poses another problem; if a new coin starts now with the same PoW based on SHA-256 as Bitcoin uses, then it would be easy for a malicious adversary to use an ASIC miner and control the entire network. This attack would be more practical if there is less interest in the new altcoin, and someone decides to take over the network by consuming adequately high computing resources. This attack may not be possible if other miners with comparable computing power also join the altcoin network because then, miners will be competing with each other.
Also, multipools pose a more substantial threat, which is where a group of miners can automatically switch to the currency that is becoming profitable. This phenomenon is known as pool hopping and can adversely affect a blockchain and, consequently, the growth of the altcoin. Pool hopping impacts the network negatively because pool hoppers join the network only when the difficulty is low so that they can gain quick rewards. If the moment difficulty goes up (or is readjusted), they hop off and then come back again when the difficulty is adjusted back.
For example, if a multipool consumes its resources when mining a new coin too quick, the difficulty will increase very quickly; when the multipool leaves the currency network, it becomes almost unusable because now, the difficulty has risen to such a level that it is no longer profitable for solo miners and can no longer be maintained. The only fix for this problem is to initiate a hard fork, which is usually undesirable for the community.
There are a few algorithms that have come into existence to address this issue and are discussed next in this chapter. All these algorithms are based on the idea of readjusting various parameters in response to hash rate changes; these parameters include the number of previous blocks, the difficulty of previous blocks, the ratio of adjustment, and the number by which the difficulty can be readjusted back or up.
In the following section, you will be introduced to the few difficulty algorithms being used in and proposed for various altcoins.
Kimoto Gravity Well
This algorithm is used in various altcoins to regulate difficulty. This method was first introduced in Megacoin and used to adjust the difficulty of the network every block adaptively. The logic of the algorithm is shown as follows:
KGW = 1 + (0.7084 * pow((double(PastBlocksMass)/double(144)), -1.228))
The algorithm runs in a loop that goes through a set of predetermined blocks (PastBlocksMass) and calculates a new readjustment value. The core idea behind this algorithm is to develop an adaptive difficulty regulation mechanism that can readjust the difficulty in response to rapid spikes in hash rates. Kimoto Gravity Well (KGW) ensures that the time between blocks remains approximately the same. In Bitcoin, the difficulty is adjusted every 2016 blocks, but in KGW, the difficulty is adjusted at every block.
This algorithm is vulnerable to time warp attacks, which allow an attacker to enjoy less difficulty in creating new blocks temporarily. This attack allows a time window where the difficulty becomes low and the attacker can quickly generate many coins at a fast rate.
More information can be found at https://cryptofrenzy.wordpress.com/2014/02/09/multipools-vs-gravity-well/.
Dark Gravity Wave
Dark Gravity Wave (DGW) is a new algorithm designed to address certain flaws such as the time warp attack in the KGW algorithm. This concept was first introduced in Dash, previously known as Darkcoin. It makes use of multiple exponential moving averages and simple move averages to achieve a smoother readjustment mechanism. The formula is as follows:
2222222/ (((Difficulty+2600)/9)^2)
This formula is implemented in Dashcoin, Bitcoin SegWit2X, and various other altcoins as a mechanism to readjust difficulty.
DGW version 3.0 is the latest implementation of the DGW algorithm and allows improved difficulty retargeting compared to KGW.
More information can be found at https://dashpay.atlassian.net/wiki/spaces/DOC/pages/1146926/Dark+Gravity+Wave.
DigiShield
This is another difficulty retargeting algorithm that has recently been used in Zcash with slight variations and after adequate experimentation. This algorithm works by going through a fixed number of previous blocks to calculate the time they took to be generated, and then readjusts the difficulty to the difficulty of the previous block by dividing the actual time span by averaging the target time. In this scheme, the retargeting is calculated much more rapidly, and the recovery from a sudden increase or decrease in hash rate is quick. This algorithm protects against multi-pools, which can result in rapid hash rate increases.
The network difficulty is readjusted every block or every minute, depending on the implementation. The key innovation is that it has faster readjusting times compared to KGW.
Zcash uses DigiShield v3.0, which uses the following formula for difficulty adjustment:
(New difficulty) = (previous difficulty) x SQRT [ (150 seconds) / (last solve time)
There is a detailed discussion regarding this topic that is available at the following link: https://github.com/zcash/zcash/issues/147#issuecomment-245140908
MIDAS
Multi-Interval Difficulty Adjustment System (MIDAS) is an algorithm that is comparatively more complex than the algorithms discussed previously due to the number of parameters it uses. This method responds much more rapidly to abrupt changes in hash rates. This algorithm also protects against time warp attacks.
The original post about this is now available via web archive at https://web.archive.org/web/20161005171345/http://dillingers.com/blog/2015/04/21/altcoin-difficulty-adjustment-with-midas/.
This concludes our introduction to various difficulty adjustment algorithms.
Many alternative cryptocurrencies and protocols have emerged as an attempt to address various limitations in Bitcoin. We will introduce some of these now.
Bitcoin limitations
Various limitations in Bitcoin have also sparked some interest in altcoins. Some alternative coins were explicitly developed to address shortcomings in Bitcoin. The most prominent and widely discussed limitation is the lack of anonymity in Bitcoin. We will now discuss some of the limitations of Bitcoin.
Privacy and anonymity
As the blockchain is a public ledger of all transactions and is openly available, it becomes easy to analyze it. When combined with traffic analyses, transactions can be linked back to their source IP addresses, thus possibly revealing a transaction's originator. This is a big concern from a privacy point of view.
In the Bitcoin domain. it is a recommended and common practice to generate a new address for every transaction, which allows some level of unlinkability. However, this is not enough, and various techniques were developed and successfully used to trace the flow of transactions throughout the network and link them back to their originator. These techniques analyze blockchains by using transaction graphs, address graphs, and entity graphs, which facilitate linking users back to the transactions, thus raising privacy concerns.
The techniques mentioned earlier can be further enriched by using publicly available information (for example, public internet forum users' Bitcoin addresses) about transactions and linking them to the actual users. There are open source block parsers available that can be used to extract transaction information, balances, and scripts from the blockchain database.
Various proposals have been made to address the privacy issue in Bitcoin. These proposals fall into three categories: mixing protocols, third-party mixing networks, and inherent anonymity.
A brief discussion of each category is presented as follows.
Mixing protocols
These schemes are used to provide anonymity to Bitcoin transactions. In this model, a mixing service provider (an intermediary or a shared wallet) is used. Users send coins to this shared wallet as a deposit, and then the shared wallet can send some other coins (of the same value deposited by some other users) to the destination. Users can also receive coins that were sent by others via this intermediary. This way, the link between outputs and inputs is no longer there, and transaction graph analysis will not be able to reveal the actual relationship between senders and receivers:
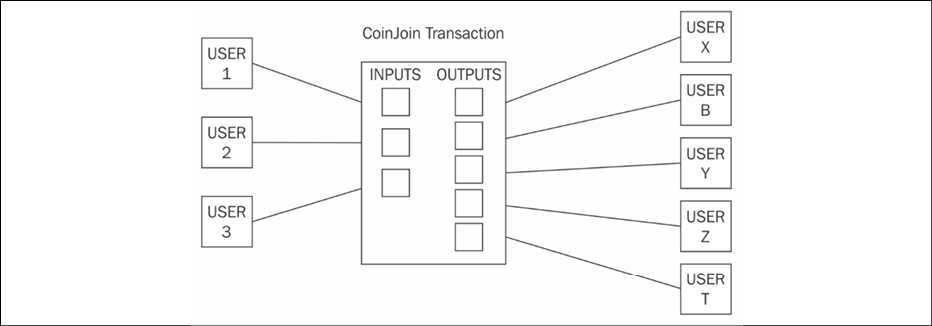
Figure 9.4: CoinJoin transaction with three users joining their transaction into a single larger CoinJoin transaction
CoinJoin is one example of mixing protocols, where two transactions are joined together to form a single transaction while keeping the inputs and outputs unchanged. The core idea behind CoinJoin is to build a shared transaction that is signed by all participants. This technique improves privacy for all participants involved in the transactions.
Third-party mixing protocols
Various third-party mixing services are available, but if the service is centralized, then it poses the threat of tracing the mapping between the senders and receivers. This is because the mixing service knows about all inputs and outputs. In addition to this, fully centralized miners pose the risk of the administrators of the service stealing the coins.
Various services, with varying degrees of complexity, such as CoinShuffle, Coinmux, and Darksend in Dash (coin), are available that are based on the idea of CoinJoin (mixing) transactions. CoinShuffle is a decentralized alternative to traditional mixing services as it does not require a trusted third party.
CoinJoin-based schemes, however, have some weaknesses, most prominently the possibility of launching a denial of service attack by users who committed to signing the transactions initially but now are not providing their signature, thus delaying or stopping joint transactions altogether.
Inherent anonymity
This category includes coins that support privacy inherently and is built into the design of the currency. The most popular is Zcash, which uses zero-knowledge proofs (ZKPs) to achieve anonymity. We discussed ZKPs in Chapter 4, Public Key Cryptography, and will discuss them in more detail in the section on Zcash in this chapter. Other examples include Monero (https://web.getmonero.org), which makes use of ring signatures to provide anonymity services.
Other schemes that have been proposed for Bitcoin privacy include:
- CoinSwap
- TumbleBit
- Dandelion
We will discuss each of these next.
CoinSwap
CoinSwap is a privacy mechanism that is based on the idea of atomic swaps. Atomic swaps allow two parties to exchange coins without requiring a trusted third party. CoinSwap can also be used for cross-chain swaps. CoinSwap works by utilizing a third party in the transaction flow and also requires private communication channels between all parties. This way, the addresses of the sender and the receiver cannot be linked. This third party receives funds from the sender and sends them to the receiver. The technique here is that the third party pays funds to the receiver by using a totally different source of funds, thus disconnecting the link between the sender and the receiver. This disconnection between the sender and the receiver results in providing an unlinkable transaction and thus privacy. The sender uses multi-signature transactions (usually 2 of 2—sender and third party) to allow transactions to be spent, while the receiver also requires multi-signature transactions (usually 2 of 2—receiver and third party) for transactions to be spent. In other words, the sender and the third party will sign the transaction output to send the Bitcoin to the third party, while the receiver and the third party will sign the transaction output to send the Bitcoin to the receiver. CoinSwap uses hash locked transactions where a pre-image of the hash is required to unlock the transaction. Using hash locked transactions prevents the third party from stealing the Bitcoin.
More information on CoinSwap can be found at the following link, where it was originally proposed by Gregory Maxwell:
TumbleBit
The TumbleBit protocol was introduced in 2016. TumbleBit is fully compatible with the Bitcoin protocol. It is an anonymous, fast, and off-chain payments (unlinkability) protocol that allows parties to transfer funds via an untrusted third party or intermediary called a tumbler. In this protocol, even the tumbler is unable to deanonymize the payers and payees involved in a payment. It involves using two fair exchange protocols that prevent any malicious activity, such as cheating participants or the tumbler. TumbleBit relies on a protocol called RSA puzzle solver, which allows a payer to make payments to the tumbler. Unless tumbler solves this RSA puzzle, it cannot claim any bitcoin paid by the payer. Another fair exchange protocol, called the puzzle-promise protocol, is used between the tumbler and the payee to claim the payment.
TumbleBit consists of three phases, as listed here:
- Escrow phase, where all payment channels are set up
- Payments phase, where payers transfer funds
- Cash-out phase, where payers and payees close the payment channels
More information on TumbleBit can be found here: https://eprint.iacr.org/2016/575.pdf.
A proof of concept implementation of TumbleBit is available here: https://github.com/BUSEC/TumbleBit.
A recent innovation is the introduction of TumbleBit++, which is an improved mixing protocol based on TumbleBit. It provides anonymity and confidentiality of transaction amounts by combining confidential transactions and a centralized untrusted anonymous payment hub.
More information regarding TumbleBit++ is available here:
https://link.springer.com/chapter/10.1007/978-3-030-31919-9_21.
We will now discuss Dandelion, which provides inherent anonymity and is implemented by redesigning the network layer of the Bitcoin protocol.
Dandelion
In addition to the approaches mentioned previously, a recent proposal called Dandelion has also been made. Dandelion (the improved version is called Dandelion++) is a proposal that aims to make transactions on a Bitcoin network untraceable. This protocol will allow anonymous transactions to occur on the Bitcoin network as opposed to pseudonymous transactions, where an adversary, by using network analysis methods, can trace the transaction back to its source node. Consequently, the adversary can then discover the original IP address of the transaction sender.
Deanonymization of Bitcoin users is a known problem, and a number of research papers are available on this topic. For example, the paper Deanonymization of clients in Bitcoin P2P network is available at https://arxiv.org/pdf/1405.7418.pdf.
We can say that Dandelion is a mechanism to provide inherent anonymity to the Bitcoin transactions because, once implemented, the P2P layer of the network Bitcoin protocol is modified in such a way that tracing transactions back to their source node and IP would become extremely difficult. A Bitcoin improvement proposal is available at https://github.com/bitcoin/bips/blob/master/bip-0156.mediawiki.
The original Dandelion proposal paper is available at https://arxiv.org/pdf/1701.04439.pdf. The Dandelion++ research paper is available at https://arxiv.org/pdf/1805.11060.pdf.
In the Bitcoin network, the epidemic flooding mechanism (Gossip protocol) is used for transaction propagation. On top of this mechanism, there is a somewhat effective method called diffusion, which is used to provide some level of anonymity. In this protocol, each node introduces independent and exponential delays for spreading transactions to its neighbors. This scheme results in reducing the symmetry of the epidemic protocol, which makes network analysis difficult and unreliable. However, this scheme is predictable and hence does not provide sufficient anonymity guarantees.
Dandelion proposes a new but backward compatible routing mechanism. In this protocol:
- First, a privacy graph (anonymity set) is constructed. This phase is called the private graph construction phase. It is a sub-graph of the existing Bitcoin P2P network and each node selects a subset of its outbound peers in this phase. This is where the random line of nodes is selected.
- The messages (transactions) are then routed through this privacy graph during the Stem phase. This is where the message is propagated on a random line of nodes.
- Finally, there is the Fluff phase, where the messages are routed (broadcast) to the entire network by diffusion.
In summary, the dandelion protocol is composed of an anonymity phase and a spreading phase. In the anonymity phase, this protocol spreads a message over a random line for a number of random hops. After this step, the message is broadcast over the whole network using diffusion. With this combination of random path selection and diffusion, the Dandelion protocol provides near-optimal anonymity guarantees.
This protocol can be visualized using the following diagram:

Figure 9.5: Dandelion protocol routing
In the preceding diagram, first, graph construction is performed, which is shown on the left-hand side. Then, in the middle, we have the transaction propagation along a random line of nodes. Finally, the broadcast, on the right-hand side, is shown.
More information on Dandelion is available in the following paper: https://arxiv.org/pdf/1701.04439.pdf.
Now that we have discussed various privacy techniques, let's move on to the next section, which introduces various other enhancements that have been made or have been proposed to extend the Bitcoin protocol.
Extended protocols on top of Bitcoin
Several protocols, as discussed in the following sections, have been proposed and implemented on top of Bitcoin to enhance and extend the Bitcoin protocol, as well as to be used for various other purposes instead of just as a virtual currency.
Colored coins
Colored coins are a set of methods that have been developed to represent digital assets on the Bitcoin blockchain. Coloring a bitcoin refers colloquially to updating it with some metadata representing a digital asset (smart property). The coin still works and operates as a Bitcoin, but additionally carries some metadata that represents some assets. This can be some information related to the asset, some calculations related to transactions, or any arbitrary data. This mechanism allows issuing and tracking specific bitcoins. Metadata can be recorded using the Bitcoin's OP_RETURN opcode or optionally in multi-signature addresses. The metadata can also be encrypted if required to address any privacy concerns. Some implementations also support the storage of metadata on publicly available torrent networks, which means that virtually unlimited amounts of metadata can be stored. Usually, these are JSON objects representing various attributes of the colored coin. Moreover, smart contracts are also supported.
Colored coins can be used to represent a multitude of assets, including, but not limited to, commodities, certificates, shares, bonds, and voting. It should also be noted that to work with colored coins, a wallet that interprets colored coins is necessary and that normal Bitcoin wallets will not work. Normal Bitcoin wallets will not work because they cannot differentiate between colored coins and not colored coins.
The idea of colored coins is very appealing as it does not require any modifications to be made to the existing Bitcoin protocol, and they can also make use of the already existing secure Bitcoin network. In addition to the traditional representation of digital assets, there is also the possibility of creating smart assets that behave according to the parameters and conditions defined for them. These parameters include time validation, restrictions on transferability, and fees. This opens up the possibility of creating smart contracts, which we will discuss in Chapter 10, Smart Contracts.
A significant use case can be the issuance of financial instruments on the blockchain. This will ensure low transaction fees, valid and mathematically secure proof of ownership, fast transferability without requiring some intermediary, and instant dividend payouts to investors.
There were a few services available online that used to provide colored coins services, such as Colu by Coinprism (https://en.bitcoin.it/wiki/Coinprism), but they are no longer active.
Counterparty
This is another service that can be used to create custom tokens that act as a cryptocurrency and can be used for various purposes, such as issuing digital assets on top of the Bitcoin blockchain. This is quite a robust platform and runs on Bitcoin blockchains at their core, but has developed its client and other components so that they support issuing digital assets. The architecture consists of the following components:
- Counterparty server: This is the reference client and implements the core counterparty protocol. It is a combination of
counterparty-libandcounterparty-cli. - Counter block: This component provides services in addition to the Counterparty server.
- Counter wallet: This is a web wallet for Bitcoin and Counterparty coin (XCP).
- armory_utxsvr: This is a service used for offline armory transactions.
Counterparty works based on the same idea as colored coins by embedding data into regular Bitcoin transactions, but provides a much more productive library and a set of powerful tools to support the handling of digital assets. This embedding is also called embedded consensus because the counterparty transactions are embedded within Bitcoin transactions. The method of embedding the data is by using OP_RETURN opcode in Bitcoin.
The currency produced and used by Counterparty is known as XCP and is used by smart contracts as the fee for running the contract. At the time of writing, its price is 1.03 USD. XCPs were created by using the PoB method discussed previously.
Counterparty allows the development of smart contracts on Ethereum using the Solidity language and allows interaction with the Bitcoin blockchain. To achieve this, BTC Relay is used as a means to provide interoperability between Ethereum and Bitcoin. This is a clever concept where Ethereum contracts can talk to the Bitcoin blockchain and transactions through BTC Relay. The relayers (the nodes that are running BTC Relay) fetch the Bitcoin block headers and relay them to a smart contract on the Ethereum network that verifies the PoW. This process verifies that a transaction has occurred on the Bitcoin network.
BTC Relay is available at http://btcrelay.org/.
Technically, this is an Ethereum contract that is capable of storing and verifying Bitcoin block headers, just like Bitcoin simple payment verification lightweight clients do by using bloom filters. SPV clients were discussed in detail in the previous chapter. This idea can be visualized with the following diagram:
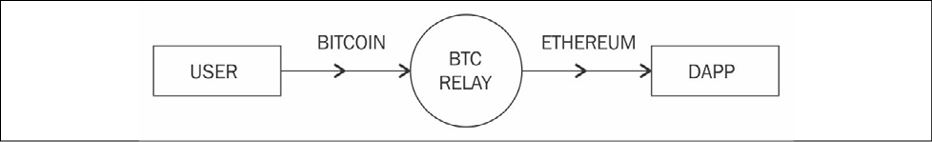
Figure 9.6: BTC relay concept
Counterparty is available at http://counterparty.io/.
Now, we will move on to a different topic, which explains how altcoins are developed, how they work, and how difficult it is to create a new coin.
Development of altcoins
Altcoin projects can be started very quickly from a coding point of view by simply forking the Bitcoin or another coin's source code, but this probably is not enough. When a new coin project is started, several things need to be considered to ensure a successful launch and the coin's longevity. Usually, the code base is written in C++, as was the case with Bitcoin, but almost any language can be used to develop coin projects; for example, Golang or Rust.
Writing code or forking the code for an existing coin is the easy part. The challenging issue is how to start a new currency so that investors and users can be attracted to it.
From a technical point of view, in the case of forking the code of another coin, for example, Bitcoin, there are various parameters that can be changed to effectively create a new coin. These parameters are required to be tweaked or introduced in order to create a new coin. These parameters can include, but are not limited to, the following.
Consensus algorithms
There is a choice of consensus algorithms available, for example, PoW, which is used in Bitcoin, or PoS, which is used in Peercoin. There are also other algorithms available, such as Proof of Capacity (PoC) and a few others, but PoW and PoS are the most common choices.
Hashing algorithms
This is either SHA-256, Scrypt, X11, X13, X15, or any other hashing algorithm that is adequate for use as a consensus algorithm.
Difficulty adjustment algorithms
Various options are available in this category to provide difficulty retargeting mechanisms. The most prominent examples are KGW, DGW, Nite's Gravity Wave, and DigiShield. Also, all these algorithms can be tweaked based on requirements to produce different results; therefore, many variants are possible.
Inter-block time
This is the time that has elapsed between the generation of each block. For Bitcoin, the blocks are generated every 10 minutes, while for Litecoin, it's 2.5 minutes. Any value can be used, but an appropriate value is usually around a few minutes. If the generation time is too fast, it might destabilize the blockchain, while if it's too slow, it may not attract many users.
Block rewards
A block reward is for the miner who solves the mining puzzle and is allowed to have a coinbase transaction that contains the reward. This used to be 50 coins in Bitcoin initially and now many altcoins set this parameter to a very high number; for example, in Dogecoin, currently, it is 10,000. However, changing the block reward is optional and depends on the choice of the coin creator.
Reward halving rate
This is another important factor; in Bitcoin, it is halved every 4 years and now is set to 12.5 Bitcoin. It's a variable number that can be set to any time period or none at all, depending on the requirements.
Block size and transaction size
This is another important factor that determines how high or low the transaction rate can be on the network. Block sizes in Bitcoin are limited to 1 MB, but in altcoins, it can vary depending on the requirements.
Interest rate
This property applies only to PoS systems where the owner of the coins can earn interest at a rate defined by the network, in return for some coins that are held on the network as a stake to protect the network. This interest rate keeps inflation under control. If the interest rate is too low, then it can cause hyperinflation.
Coinage
This parameter defines how long the coin has to remain unspent in order for it to become eligible to be considered stake worthy.
Total supply of coins
This number sets the total limit of the coins that can ever be generated. For example, in Bitcoin, the limit is 21 million, whereas in Dogecoin, it's unlimited. This limit is fixed by the block reward and halving schedule discussed earlier.
There are two options to create your own virtual currency: forking existing established cryptocurrency source code or writing a new one from scratch. The latter option is less popular, but the first option is easier and has allowed the creation of many virtual currencies. Fundamentally, the idea is that first a cryptocurrency source code is forked, and then appropriate changes are made at different strategic locations in the source code to effectively create a new currency.
In the earlier days of the evolution of the crypto landscape, any coin project other than Bitcoin was called alternative coin, or altcoin for short. Over the years, the term cryptocurrency or just crypto is now generally used to refer to either Bitcoin or any other digital currency. Cryptocurrency is defined as a currency that runs on a digital platform and makes use of cryptography to secure its operations.
It is not possible to cover all alternative coins (cryptocurrencies) in this chapter, but a few selected coins will be discussed in this book's bonus content pages, here: https://static.packt-cdn.com/downloads/Altcoins_Ethereum_Projects_and_More_Bonus_Content.pdf. The coins discussed in the resource pack have been selected based on longevity, market cap, and innovation. Each coin will be discussed from different perspectives, such as theoretical foundations, mining, and trading.
There are thousands of cryptocurrencies (as of June 2020) in the market. A list can be found at https://coinmarketcap.com/all/views/all/.
So far, we've discussed a number of the features of alternative coins, and you should now be familiar with the foundations of some different Altcoin protocols and algorithms. Before we move on to a different but relevant topic of tokens on blockchain, let's clarify a common ambiguity regarding the use of the terms token and cryptocurrency.
Token versus cryptocurrency
Sometimes, the terms token and cryptocurrency are used interchangeably, which is not correct. Tokens are a different concept from cryptocurrency. A cryptocurrency is a native coin for a standalone blockchain. In contrast, a token is a representation of the value of some asset. It is usually built on top of an existing blockchain. For example, ether is the native cryptocurrency or coin of the Ethereum blockchain.
Similarly, Bitcoin is the original (inherent) coin or cryptocurrency of the Bitcoin blockchain. On the other hand, a token is created on top of an existing blockchain and does not have its own native and dedicated blockchain. For example, Binance token, 0x, Tether, and Basic Attention Token (BAT) exist on top of the Ethereum blockchain and do not have their native blockchain. There are thousands of tokens that exist on Ethereum and other blockchains.
In this chapter, we touched briefly on the vast subject of tokenization. We will discuss tokenization and different tokens, such as Tether USD and Maker and related concepts, in greater detail in Chapter 18, Tokenization.
Certainly, launching new alternative coins or tokens requires some funding. Traditionally, new businesses are funded by methods like Initial public offering (IPOs), venture capital funds (VCs), and so on, but in the cryptocurrency world, an equivalent but different mechanism called Initial Coin Offering (ICO) is used. We will explain what an ICO is now.
Initial Coin Offerings (ICOs)
ICO is a method for crowdfunding. Crowdfunding is a method of raising money where the funds are acquired usually in smaller amounts from a large number of investors to fund a new business. This is done usually via the internet. ICOs has been the method of choice for crowdfunding startups offering new cryptocurrencies and tokens.
ICOs are comparable to the IPO. Just as an IPO is launched to raise capital by a firm, similarly, ICOs are launched to generate money for a startup project. The critical difference is that IPOs are regulated and fall under the umbrella of the securities market (shares in the company), whereas ICOs are unregulated and do not fall under any strict category of already established market structures.
However, there are a few suggestions stating that ICOs should be treated as securities in light of some scam ICO schemes that were launched in the past, as well as growing concerns around investor protection. The Securities and Exchange Commission (SEC) has suggested that all coins, ICOs, and digital assets should fall under the definition of security. This means that the same laws would be applicable to ICOs, Bitcoin, and other digital coins as are applicable to securities. Also, an introduction of formal Know Your Customer (KYC) and Anti-Money Laundering (AML) is also being recommended to addresses issues related to money laundering. Experts are recommending the Howey Test as part of the criteria for any ICO to be considered a security.
More information on the Howey Test can be found at https://www.investopedia.com/terms/h/howey-test.asp.
Another difference is that ICOs, by design, usually require investors to invest using cryptocurrencies and payouts are paid using cryptocurrencies. Most commonly, this is the new token (a new cryptocurrency) introduced by the ICO. This can also be Fiat currency, but most commonly, cryptocurrency is used. For example, in the Ethereum crowdfunding campaign, a new token, ether was introduced. The use of the name token sale instead of crowdfunding is also quite popular and both terms are sometimes used interchangeably. ICOs are also called crowd sales.
When a new blockchain-based application or organization is launched, a new token can be launched with it as a token to access and use the application, and also to gain incentives that are paid in the very same token that was introduced by the ICO. This token is released to the public in exchange for some already established cryptocurrency (for example, Bitcoin or Ethereum) or Fiat currency. The advantage is that when the usage of the application or product launched increases, the value of the new token also increases with it. This way, the investors who invested initially gain a good incentive.
Since 2017, ICOs have become a leading tool for raising capital for new startups. The first successful ICO was that of Ethereum, which raised 18 million USD in 2014. A recent success is Tezos, which made 232 million USD in a few weeks. Another example is Filecoin, which raised more than 250 million USD. A more recent example is EOS, which raised a record of over 4 billion USD.
The process of creating a new token has been standardized on Ethereum blockchain, thus making it relatively easy to launch an ICO and issue new tokens in exchange for ether, Bitcoin, or some other cryptocurrency. This standard is called ERC20 and is described in the next section. It's worth noting that using ERC20 is not a requirement, and a completely new cryptocurrency can be invented on a new blockchain to start an ICO, but ERC20 has been used in many ICOs and provides an easier and quicker way to build a token for an ICO.
ERC20 standard
The ERC20 standard is an interface that defines various functions dictating the requirements of the token. It does not, however, provide implementation details and has been left to the implementer to decide. ERC is an abbreviation for Ethereum Request for Comments, which is equivalent to Bitcoin's BIPs for suggesting improvements in the Ethereum blockchain.
This is defined under EIP 20, which you can read more about here:
https://github.com/ethereum/EIPs/blob/master/EIPS/eip-20-token-standard.md
Ethereum has become a platform of choice for ICOs due to its ability to create new tokens and with the ERC20 standard, it has become even more accessible.
The ERC20 token standard defines various functions that describe various properties, rules, and attributes of the new token. These include the total supply of the coins, the total balance of holders, transfer functions, and approval and allowance functions.
There are other standards making improvements on ERC20, such as ERC223, ERC777, and ERC827 that are also under development. You can refer to the followings links to learn more:
https://github.com/ethereum/EIPs/issues/827
We will cover tokenization and relevant concepts such as Security Token Offerings (STOs) and Initial Exchange Offerings (IEOs), which are alternatives to ICOs, in more detail in Chapter 18, Tokenization.
Summary
In this chapter, we introduced you to the overall cryptocurrency landscape. We discussed several altcoins in detail, especially Zcash and Namecoin. Cryptocurrencies are a very active area for research. Topics such as scalability, privacy, and security are the main focus of many researchers. Further research needs to be carried out in the areas of the privacy and scalability of blockchain. Some research has also been conducted to invent new difficulty retargeting algorithms to thwart the threat of centralization in cryptocurrencies. Altcoins or cryptocurrencies in general are a fascinating field of research, and they open many possibilities for a decentralized future.
We also discussed a few practical aspects, such as mining and starting a new currency project, which will give you a strong foundation, enabling you to explore these areas further. Now, you should be able to appreciate the subject of altcoins and understand the various motivations behind them.
In the next chapter, we will see what smart contracts are and discuss relevant ideas and concepts that are essential to understanding the blockchain technology fully.
