With the help of Microsoft Azure, you can create Virtual Machines that run within Microsoft data centers. These virtual machines that you create eventually form a part of a workgroup. Traditionally, you can have an application hosted on your virtual machine and the data could reside on SQL Server, which could be on a different virtual machine. These machines need to talk to each other, so you not only need to connect, you also need to communicate between them. In order to connect from the application, you can use SQL Authentication or a pass-through Windows authentication to connect to SQL Server since these machines resides on a workgroup.
There are different data centers spread across the globe where different customers and businesses run in Microsoft Azure. It provides the perfect platform to host your business in cloud and reduce the TCO. Thus in order to have your business hosted in Microsoft Azure or store data, you can use one of these data centers spread across globe.
As shown in Figure 4-1, you can connect to these data centers in three different ways:
Connect the on-premises network to a separate network that has set of virtual machines.
Use *Azure AD Connect to link the Microsoft Azure application to the on-premises Windows servers.
See https://azure.microsoft.com/en-in/documentation/articles/active-directory-aadconnect/ .
Use Microsoft Azure Traffic Manager to route requests to multiple data centers where the different instances of the Microsoft Azure application run.

Figure 4-1. Typical setups using different components
You can also create Virtual Networks in the cloud. You could create your test environment in Microsoft Azure with a domain controller (DC) for user authentication, and you can host your application servers. Your data resides in SQL Servers which is provisioned in Microsoft Azure, which utilizes the massively scalable, highly secure Microsoft Azure storage. You need to create a Virtual Network to configure secure site-to-site connectivity as well as protected private Virtual Network in the cloud. Thus you can build your complete office network within Microsoft Azure.
In this chapter, you’ll see how Microsoft Azure allows you to create a VPN and allows your on-premise networks to connect and talk to each other. You can also connect Azure applications on-premises as well as distribute load across different data centers. You will also be introduced to a few key networking components/concepts, which you can study further if you are interested.
Networking Primer
Connecting your on-premise securely to a Virtual Network can help in expanding your business and reduce cost by leveraging the Microsoft Azure Services. There are at least three options that could help you connect and expand your hybrid network: Site-to-Site, Point-to-Site, and ExpressRoute. See Figure 4-2 and Table 4-1 for more detail.

Figure 4-2. Typical hybrid setup
Table 4-1. Choosing the Best Connectivity Options
Point-to-Site | Site-to-Site | ExpressRoute | |
|---|---|---|---|
Azure Services | Cloud Service and Virtual Machine | Cloud Service and Virtual Machine | Most services, Refer to the link in PS |
Bandwidth | Less than 100MBPS | Less than 100MBPS | 50MBPS-10GBPS |
Supported Protocols | Secure Socket Tunneling Protocol (SSTP) | IPSec | Direct connections over VLANs, NSPs, and VPN technologies |
Connection Resiliency | Active-Passive | Active–Passive | Active-Active |
Before you opt for one of these options, you should consider few points, such as the following questions. How much throughput does your application require? Does your application connect via a public Internet? Do you have a public IP available? Do you need VPN gateways?
More information can be found here:
https://azure.microsoft.com/en-in/documentation/articles/expressroute-faqs/#supported-services
https://azure.microsoft.com/en-in/documentation/articles/vpn-gateway-cross-premises-options/
In today’s world where businesses span multiple regions across different parts of the world, a public cloud can be cleverly used as an extension of the on-Premise data center. The cloud provides you the flexibility as you can create virtual machines on demand, you can pause/stop them if you don't need them, and you can delete them once your work is done and you don't need them anymore, i.e., you use the compute whenever your business needs it. In addition, your existing applications running on-premises continue to run smoothly. You can spin Virtual Machines with SharePoint and SQL Server, and have an Active Directory that can talk to your existing on-premises Active Directory as well.
Site-to-Site Connections
Site-to-Site can be used to connect the branch office to the main office, which is the headquarters. In this type of connection, hosts would not have VPN client software installed. The VPN device that is located in the on-premises environment is configured to create a secured connection with the Azure VPN Gateway. It sends the TCP/IP packets through VPN gateways, which encapsulate and encrypt the packets and send it through the VPN tunnel. There is then a VPN gateway at the destination that receives the packets, deciphers the header and the content from the packet, and then sends the same to the destination host.
The following describe a few scenarios when you would use the Site-to-Site connections:
For creating a hybrid solution.
The requirement for the business is a consistent and reliable network connection.
You don't need any client-side configuration for connecting your on-premises network to your VPN.
The requirement for setting up a Site-to-Site connections is primarily that you need a compatible VPN device having an Internet-facing IP address. This device should be compatible with the VPN gateway type.
Point-to-Site Connections
You can use this to create a secure connection to your Virtual Network. Unlike with Site-to-Site, you need to install a VPN client and configure it on every client that intends to connect to the Virtual Network. You also don't need a VPN device with an Internet-facing IP address.
The following describes a few scenarios when you would use the Point-to-Site connections:
You have a handful of clients who want to connect to the Virtual Network.
Remote connectivity is a requirement by your clients.
There is an existing Site-to-Site connection; however, a few clients have to connect to the Virtual Network from a remote location.
Virtual Networks provide you with an option to create a private network within Azure. Using this, different services can talk to each other or to on-premises resources.
This concept is quite interesting and useful as well; however, in order to make it beneficial, the users should treat the applications as if it were running on their own on-premises data center. Your network administrator can set up a Microsoft Azure Virtual Private Network between your local on-premises network and Microsoft Azure, where multiple Virtual Machines can run. This can be done with the help of a VPN gateway device. You can choose your own IP v4 address and assign it to these Virtual Machines that run in the cloud VMs. This means it would appear that this is an extension of your existing network. The end users would be able to access the application running on those Virtual Machines seamlessly, as if they were accessing them on their local network.
ExpressRoute
ExpressRoute is a pretty neat concept, whereby you get your own private connection to Azure. ExpressRoute is a connection that bypasses the public Internet that connects your on-premises infrastructure to Microsoft Azure data centers (see Figure 4-3). This helps Azure act like your own private cloud.

Figure 4-3. Hybrid setup with ExpressRoute
There are two ways to establish your private connections to Microsoft Azure. The first way is to connect through a exchange provider facility; if you are using a exchange provider facility, you could directly connect to the Azure. Alternatively, you can establish a direct connection through your network service provider between the on-premises site and the Microsoft Azure data center.
Microsoft Azure would appear as just another site on your WAN. ExpressRoute is seamless and it works great with all sorts of technology. It also provides built-in redundancy. Microsoft works directly with your network service provider. It delivers throughput that is faster, nearly 10Gbps. Thus, with ExpressRoute you have your network infrastructure superbly secured, with low latency, high throughput and great reliability. If you use ExpressRoute for data transfer between on-premises and the Microsoft Azure data center, you can enjoy cost benefits as well. Since it is fast and reliable, it can be used for data migration, replication for business continuity, disaster recovery, and high-availability strategies.
With ExpressRoute, you can leverage the compute and storage capacity of Microsoft Azure and add that to your existing data centers. Since it is reliable and offers high throughput connections, you could build a hybrid application that expands from your existing data center through the Microsoft Azure data center. Interestingly, you get all of this without compromising on security or performance.
Azure AD Connect
Using Azure AD Connect , you can connect your on-premises identity infrastructure to the active directory hosted in Microsoft Azure. It presents you with a wizard that guides you with the prerequisites and the components needed for the connection. Using this tool, you can configure common identity for your users for Office 365, Azure, and SaaS applications, which are integrated along with Azure AD. When you install the tool, it installs the prerequisites like .NET Framework, Azure Active Directory, the PowerShell module, and the Microsoft Online Service assistant for sign-in. It configures sync for one of the multiple active directory forests. It also helps you configure password hash sync or Active Directory Federation with a web application. You can read more about it at https://azure.microsoft.com/en-in/documentation/articles/active-directory-aadconnect/ .
Traffic Manager
In today’s world where users are spread around the globe, the challenge is running an application instance in multiple data centers. The main challenge is how to intelligently redirect the traffic to the application instances running in the dispersed data centers. The aim is usually to assign users access to the application that’s running in closest proximity to them, in order to get the best response time and throughput.
Traffic Manager helps you control the distribution of the traffic and route it to specific end points like website, cloud services, etc. Basically, you define rules that determine how the traffic will be routed/distributed to the data centers for the Traffic Manager to follow. For example, usually the request could be routed to the closest data center from the user location; however, it’s not always true that the response time from that data center will be best. In such cases, users could be routed to other data centers. This type of service is very useful in modern-day business, where your users are spread across the planet.
The following are the main benefits that Traffic Manager provides:
It helps improve availability of mission-critical applications.
You get better response time for high-performant applications.
You could perform application upgrades by disabling your endpoints and enable the same once the service is complete.
Finally, you can specify an endpoint to another Traffic Manager, thereby distributing complex application deployments.
Figure 4-4 shows how the rules enable Traffic Manager to route global traffic.

Figure 4-4. Traffic Manager workflow
Virtual Private Network
In today’s world, most organizations opt for a hybrid kind of a scenario, putting their data in the cloud as well as in an on-premises data center. For example, you could create a Virtual Private Network (VPN) and link your cloud environment to the branch office (see Figure 4-5).
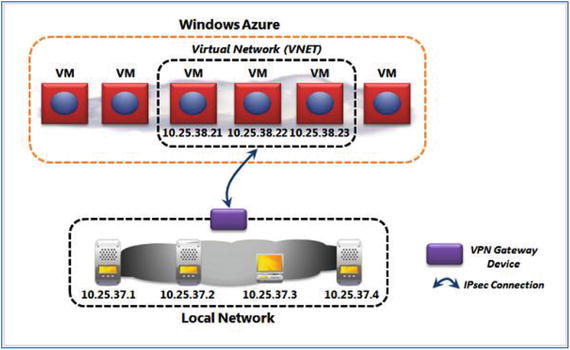
Figure 4-5. Typical VPN setup
Using Microsoft Azure Virtual Network, you can create a logical boundary by grouping the virtual machines together, called Virtual Network or VNet. Once the VNet is set up, you can establish a IPsec connection between your local on-premises data center and the VNet. This, however, is not needed for ExpressRoute setup. You can create the virtual machines in the Virtual Network by using the Microsoft Azure VMs or Microsoft Azure Cloud Services, or both. You could choose the IaaS or the PaaS service offering from Microsoft Azure to create Virtual Machines or services. When you create the IPsec connection, it basically requires the following:
You need a virtual private network (VPN) gateway device.
You need specialized hardware that will be connected to your on-premises network.
You need a network administrator who will help set this up for you.
Once this network and setup is ready, the virtual machines running within the VNet will appear as an extension of your on-premises network.
Notice that the IP addresses in Figure 4-5 are allocated from the same IP address range that is available for your on-premises local network. The software that runs on the local network will be able to see the Virtual Machines as if they were available within their own on-premises local network. It is interesting to note that the physical machines that host these Virtual Machines on either side of the network could run any operating system, as the connection happens at the IP layer and is thus transparent. For example, the Microsoft Azure VMs running a Linux operating system can talk to your on-premise machines that run Windows or vice versa. You can use the infrastructure tools like SCCM to manage the cloud’s Virtual Machines.
A very important aspect of having such an expanded network is that you can easily extend your existing on-premises active directory domain to the Microsoft Azure Virtual Network and give users single sign-in so that they can run applications from anywhere. If need be, you could have a domain created in the Microsoft Azure cloud and connect it to your existing on-premises domain. As your Virtual Network is an extension of your on-premises network, the reverse is also true.
You could technically use the software running in your local network from your Microsoft Azure Network as well. If you prefer to keep your data local for privacy reasons, such as many hospitals and medical facilities do, you can use this concept of the Virtual Network and expand your network so that the data remains in your on-premises network (stored locally) and yet the users can access the data from application instances running across multiple data centers in Microsoft Azure.
This gives you the flexibility to access a large pool of resources as per your needs. Elasticity in the cloud space is a great concept and directly impacts your financials, as it reduces the total cost of ownership. You can spin a Virtual Machine when you need it and upon completion just remove/release the resource (virtual machine in this context). You will only be charged for the period that you used them. Imagine you have a request to get a machine ready and the requirement is urgent. Using Microsoft Azure, you could set up the Virtual Machine in no time and you are all set in few minutes.
Load Balancer
Using Azure Load Balancer , you get high availability and a boost to your network applications. It balances and spreads out the load using layer 4 TCP/UDP load balancer and distributes it through different, healthy services. Load balancing is accomplished using endpoints, which have a one-to-many relationship between the public IP and the local ports that are assigned to the virtual machines where the load will be eventually distributed. Here are a few of the scenarios when using Load Balancer is a good idea:
It would load balance Internet traffic to Virtual Machines.
It can also load balance the incoming traffic between the Virtual Machines within the Virtual Network. It can be Used To Distribute the load between different virtual machines within a cloud service.
It can also forward external traffic to a specific Virtual Machine.
Azure DNS
Any service or website will be associated with a IP address. Domain Naming System (DNS) helps translate the IP address to user-friendly names for the service or website.
Azure DNS provides name resolution using the Microsoft Azure infrastructure. You can host your domains within Microsoft Azure data centers and yet manage your DNS records using the same credentials that you have been using. DNS domains within Azure DNS are hosted within the global DNS network name servers. This service provides faster performance and high availability for your domains. You need to purchase the domains from a third-party registrar and then they can be hosted in Azure DNS for managing DNS records.
Summary
Microsoft Azure allows you to create a VPN and allows your on-premises network connections to talk to each other. You can connect an Azure application on-premises as well as distribute loads across different data centers. You can extend your existing business with minimal impact and save a lot of money. Be sure to go through the references at the end of the chapter, which are a part of the rich Azure documentation.
