7
Novel Defending and Prevention Technique for Man-in-the-Middle Attacks in Cyber-Physical Networks
Gaurav Narula1*, Preeti Nagrath1, Drishti Hans2 and Anand Nayyar3,4
1Computer Science Engineering Department, Bharati Vidyapeeth’s College of Engineering, New Delhi, India
2Electrical and Electronics Engineering Department, Bharati Vidyapeeth’s College of Engineering, New Delhi, India
3Graduate School, Duy Tan University, Da Nang, Vietnam
4Faculty of Information Technology, Duy Tan University, Da Nang, Vietnam
Abstract
Cyber security is now a global and heated debate. Man-in-the-Middle Attack is a type of cyber-attack in which an unauthorized person enters the online network between the two users, avoiding the sight of both users. The recent Chinese cyber-attack has prompted India to ban 59 Chinese apps, the issue is acute, and the system is likely to be threatened/hacked by this malware without adequate authentication security, this can cause a lot of potential data loss. This paper is mainly aimed at understanding the term ‘man in middle attacks’, along with various techniques such as rogue access points, Address Resolution Protocol (ARP) spoofing, Domain Name Server (DNS) and multicast Domain Name Server (mDNS) spoofing etc. The authors devised algorithms for detection and prevention of any potential data loss from such attacks. The algorithms devised were implemented on virtual servers and machines to replicate the real time scenarios. The scripts developed successfully defended the deployed virtual machines from the Man in the Middle Attacks. Also, it was observed that the user was also alerted if an attack was happening so that the vulnerability can be secured in the future. The main purpose behind this topic is to make readers aware of the title of the paper and to be beware of cyber-attacks.
Keywords: ARP spoofing, DNS spoofing, SSL (Secure Sockets Layer), access point, man in the middle attacks
7.1 Introduction
A cyber-physical (CPS) system is a computer system in which a computer-based algorithm controls a process. Physical and software elements in cyber-physical structures are deeply consolidated, able to act on a range of spatial and temporal levels, displaying many more special modes of action, as well as individual communication with others. Smart grids, stand-alone automotive systems, medical supervision, industrial control systems, automation and automatic pilot avionics are some of the examples of CPS. All these systems communicate with networks, and these connections can be intercepted by people in man in the middle attacks, and the safety of these systems can be affected.
In 1992 the National Aeronautics and Space Administration (NASA) first proposed the concept of cyber-physical systems (CPSs), and it was detailed by Baheti and Gill [1], respectively. Now, in the next phase of the Industrial Revolution [2], they became the core technology, and a number of works to show their value have been done, such as the Top-Eight Intelligence Technologies [3], German Industry 4.0 [4], US Industrial Internet [5], Artemis [6] and CPS European Roadmap and Strategy [7].
CPS is widely applied in industrial control systems, advanced communication, smart grids [8], transportation systems [9] and social vehicle networks [10, 11]. In order to track and control processes [13, 14], computing, communication and control (3C) technologies [12] are incorporated into CPS, and their overall structure is shown in Figure 7.1. A CPS may arise, depending on the outline. It can be split into three layers: layer of perception execution, layer of data transfer, and layer of application control [15, 16]. The perception execution layer consists of mainly physical components like sensors, etc. User services are provided by the application control layers which consist of various services for users. An intermediary for transfer of data between these two layers is data transmission layer which consists of a communication array for smooth transfer of data.
The MITM is a cryptographic and computer security attack in which the attacker secretly relies on, and may be intercepting, messages between two parties that believe they are communicating directly with each other. An example of an MITM attack is an active wake-up call where the attacker contacts the victim independently and discovers that they are talking to each other directly through a private network, while the attacker is monitoring the whole conversation. All relevant messages passing between the two victims must be intercepted and new injections made by the attacker. It is simple in some cases; for example, an intruder may insert itself in a non-encrypted Wi-Fi port as a man in the receiving portfolio [17].

Figure 7.1 Different layers in a cyber-physical network.
MITM attacks can be avoided or detected using two methods: authentication and detection of manipulations. Authentication ensures that a specific message comes from a valid source. Tamper detection is the only sign that the message has been changed.
The main objectives of this paper are:
- Understanding what Man in the Middle attacks are, analyzing its different types and techniques used in each one if it.
- Developing techniques and algorithms to detect the attacks and prevent them from stealing any data or harming the client.
- Various algorithms were developed that were implemented in form of scripts on virtual servers and machines and were attacked to check the working efficiency of the algorithms proposed.
- Deploy Test websites to validate the DNS spoofing attack prevention technique.
Organization of the Chapter
Section 7.2 presents a literature review regarding studies and research presented by various researchers in past years about different types of analysis on Man in the middle attacks and cyber-physical systems and how different techniques are used to bypass the security in these systems. Section 7.3 first discusses the various techniques that are implemented in different layers of the cyber-physical system and also various attacks on a particular layer of such systems which involve attacks like ARP (Address Resolution Protocol) Spoofing, DNS Spoofing, SSL Stripping, etc. deployed by the attackers in such systems and networks to implement such attacks. Section 7.4 discusses the proposed algorithms to prevent the attacks along with the real time deployment of the scripts. Section 7.5 presents the results achieved from the algorithms and the research. The paper concludes with Section 7.6.
7.2 Literature Review
Zegzhda et al. [18] discussed in their article how powerful rogue access points can be and how popular they are becoming as a method to attack clients. Even having WEP (Wired Equivalent Privacy), WPA (Wi-Fi Protected Access), and WPA2 security protocols, no protocol is there to check the AP (Access Point) and the enterprise version makes it easier to add another access point due to availability of multiple APs. They also analyzed that there are multiple ways by which a Rogue AP can be setup.
Yang et al. in their paper discussed how man in the middle attacks are used widely to gain potential information. In detail the authors discussed how evil twin attacks, a version of rogue access point attack, are used widely now-a-days. They mainly classified the attack in two different categories, one of which monitors the Radio Frequencies while the other monitors the traffic on the network [19].
Ramachandran and Nandi discussed in their paper how ARP spoofing attacks are imminent and how it is a main and foremost attack to implement man in the middle attack. They also discussed various already implemented techniques to detect the attack, what are the lags in the existing techniques and how important it is to detect the attack and prevent it from happening [20].
Nam et al. [21] in their paper suggested how to mount attacks on ARP poisoning, like DoS (Denial of Service), Spoofing and other MITM attacks, by means of ARP poisoning. He also talks about various tries to address the problem of poisoning ARPcache. Dynamic ARP (DAI) inspection conducted on the Ethernet switch may prevent spoofing and poisoning of the ARP but requires the network manager to manually configure the network and will not protect the network part of the Can-incapable DAI Ethernet switch.
Maksutov et al. [22] addressed that, people transmit data across the network, which is of great benefit. Shopping in online stores, paying the fine and booking a ticket in the theater—all these include transmitting private data through the network, such as passport or credit card details. They studied how DNS spoofing can affect and rob these data, and what role SSL stripping plays in this.
Wander et al. [23] analyzed the strength of DNS attacks happening worldwide and how these attacks affect the security of a country and compromise confidential information. They analyzed despite various measures, how attackers steal information using different techniques. Also, they discussed DNS injection which is used to bring firewalls down giving access to private information. They mentioned how these attacks affect third parties and individuals. They also discussed how particular domains are targeted from which users are targeted to gain access over the whole network thus proving how social engineering is effective in such attacks.
In their chapter, Prowell and others discussed how deadly cyberattacks can be like man in the middle attacks, and what strategies are now used to execute various variations of the same attack to circumvent security protocols, and how potential data is lost every second to these attacks [24].
Khalif et al. proposed a new man in the middle attack on hardware devices. They have introduced a new PCIe attack vector based on man-in-the-middle hardware. This device allows for real-time data processing, data-replay, and a shadow-copy affected copy technique [25].
Sandhya and Devi proposed a method to implement man in middle attacks in Bluetooth networks, thus increasing the area of attack but reducing the attack range [28].
Deng in the paper discussed how DoS attacks are done in cyber-physical systems, what are the effects on the system and proposed a method to prevent such kind of attacks [29].
Li et al. [30] reviewed the intensity of attacks that happen on cyber-physical systems and how it interferes with proper functioning of the system and what were some of the drastic attacks that happened and why it is important to develop methods to prevent such attacks.
All the researchers conclude that the intensity of attacks on the cyber-physical system is increasing day by day. The protection measures used in the systems are not capable of defending against such attacks like ARP Poisoning, DNS Spoofing, DDoS attacks, etc. These allow an attacker to exploit an application to reveal sensitive data such as technical details of the application, developer comments, environment, or user-specific data. An attacker may use this sensitive data to exploit the target application, its hosting network, or its users. The authors addressed these issues to develop some scripts to defend against these attacks.
7.3 Classification of Attacks
Currently, three kinds of CPS network attacks are based on Figure 7.1.
- Network attack on the perception execution layer
- Network attack on results, i.e.
- a. Network attack on the transmission layer
- b. Network attack on the application control layer [15].
7.3.1 The Perception Layer Network Attacks
There are various sensor and actuator nodes in the perception execution layer where physical components are data received and controls are transmitted from the control center. Most nodes in this layer are deployed in an unsafe environment. So, it’s safe to be a victim of the assailant.
Work on network assault in the layer of perception mainly focuses on safety issues for sensors and actuators. In essence, the perceptual execution layer contains four types of network attack: Actuator Enabled (AE Attack), Actuator Disability (AD attack), Sensor Erasure (SE Attack) and Sensor Insertion (SI-Attack) Attack [31, 41]. Unless the sensor or actuator is targeted, plant information or instructions to be implemented may be flawed. Therefore, the device may be damaged in an unstable state. Other common attacks are attacks by manipulation, powerful attacks on pole dynamics, covert attacks and powerful attacks.
7.3.2 Network Attacks on the Application Control Layer
This layer consists of different user program applications and some controllers. This layer makes a decision based on the data received from the data transmission layer, it will execute some commands and it would give the results to the physical unit of the network i.e. the perception execution layer via the intermediary data transmission layer. The actuators perform the relevant operations on the basis of information received.
Personal data of users including their usage habits of the network is stored in this later. An attacker can simply inject a script to kill the database or can gain unauthorized access to the system via a reverse shell which can severely affect the application control layer, also jeopardising user privacy. A single security strategy is difficult to satisfy the security needs of these layers as it is based on multiple applications systems thus requiring different security layers to protect the user’s data.
7.3.3 Data Transmission Layer Network Attacks
In order for data to be transmitted between these two levels, the transmission layers include the perception execution and application control layers. A network of contacts is the central carrier network of the data relay layer. Through communication networks like the Internet, a private network or a LAN (Local Area Network), this layer is used to transmit data between them. These communication networks consist of various vulnerable points as they have access to the equipment’s, the system design and several security procedures this presenting with certain risks to the CPSs.
The layer has the ability to process big data and handle it. It is possible to transmit large amounts of data across the data transmission layer of the network, so the CPS will be vulnerable to network attacks.
When an intruder is hard to attack the data transmission layer, the attacker may alter the information transmitted on the network channel freely after the attacker passes the data channel successfully. Man-in-themiddle attacks [32], one of the most effective network attacks against a data layer, observe, hide and even change information transmitted from one computer to another through communications channels [33]. In other words, an attacking party collects false information and then pushes the CPS into an unstable state that harms the system.
DoS (Denial-of-Service) [34–36] is an attack to reduce resources which exploits protocol/software errors in the network or too many unprofitable requests to redirect assets of an object for the Send Attack. Finally, the server or network of contacts cannot be provided with services [37].
In CPSs, malicious software uses a DoS attack to consume contact bandwidth to prevent the controller and the actuator from communicating information. DoS attacks are mostly triggered by malicious attacks. These attacks would interrupt the communication between the controller and the actuator, so the controller cannot receive the data input in time. The routing and server resources will be consumed by large numbers of invalid service requests [37], finally deteriorating and even collapsing outputs. No message is sent or sent on the channel during a DoS attack.
7.3.3.1 Rogue Access Point
In essence, the rogue access point is an access point linked to the CPS network, without anyone knowing it. The individual is not fully mindful of his presence there. This is a kind of scenario, especially if no one interacts with it and manages it perfectly, that can create a type of back door. With considerable security concerns, it is an access point. This is because the wireless access point can be very easily plugged in. If a network user does not execute a protocol to control access to a network, it is very easy to attach extra workstations and access points to a network.
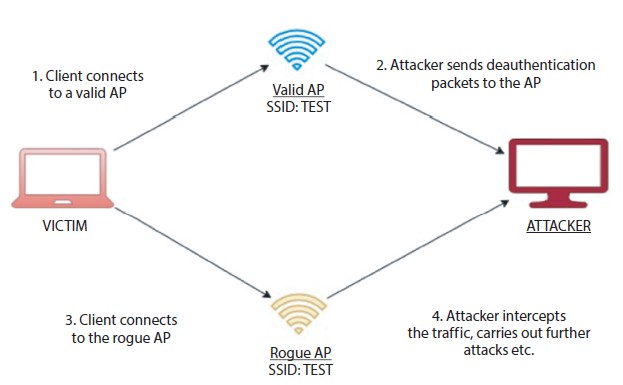
Figure 7.2 Attacker creating a rogue access point with the same SSID and forcing the user to connect to it by DE authenticating the user from the valid access point.
The attacker usually names the access point to be hacked, and it is shown in Figure 7.2 with various packets because there are many access points in the company, customers and machines that cannot connect to that access point, So the hacker sets its access point with the same name so that things are not suspicious, and the hacker becomes the middleman when customers enter and can now steal information and control the entire network.
The danger is that unauthorized wireless access points may be used outside of the organization to leak sensitive data, including passwords and cardholder information. The local administrator does not approve this, but works on the network anyway. This can be installed by a naïve user who has no malicious intent or who may be purposely installed for testing or for some other purpose by internal IT staff. A hacker who is supposedly attempting to carry out an attack can also mount it. For outsiders, a rogue access point offers a wireless backdoor channel into the private network. It can bypass firewalls and other security devices on the network and open up attacks on the network. In any event, a rogue access point may pose a serious safety danger or even a personal home network to large corporations because anyone who reaches this access point uses private networks, what can be downloaded, and even misleads the user. Inform the hackers of websites of hazardous information. It may also lead the user to a website which would cause him/her without the user to download the malicious software.
7.3.3.2 ARP Spoofing
Spoofing of ARP is a kind of network assault where an incorrect message is sent to a local area network by a malicious user/hacker. It is applied to the MAC (Media Access Control) address of an intruder, along with the IP address (Internet Protocol) of a valid network device or server. The attacker can start collecting any data for that IP address when the attacker’s MAC address is associated with a valid IP address. ARP spoofing may allow inter-transit, modification or even interception of transit data by malicious parties. ARP spoofing attacks can only occur on local area networks that have protocols of address resolution. A typical network connecting hackers and victims to the same gateway is shown in Figure 7.3. The network is scanned for attacks on IP addresses using a basic network scanner. If found, the hacker robs the gateway by retaining the IP address of the victim and telling the victim that he or she has the IP address of the gateway, as shown in Figure 7.4. The hacker becomes the middleman after this spoof, and all requests and answers start to flow through the hacker, as shown in Figure 7.5. The attack can be transmitted to all devices connected to the network, too.
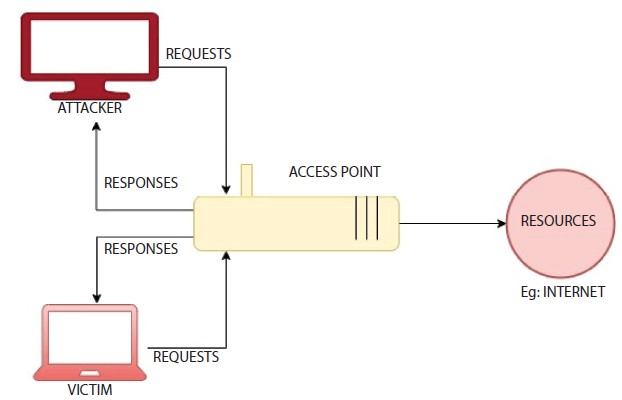
Figure 7.3 Diagram showing a typical network with two different devices connected to an access point.
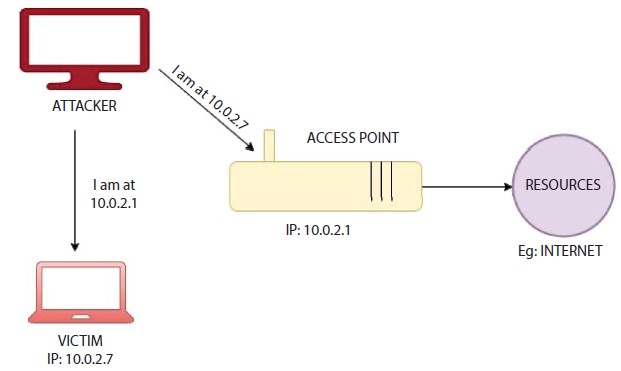
Figure 7.4 Diagram showing attacker spoofing the access point as the victim and spoofing the victim as access point placing itself in the middle of the connection.

Figure 7.5 A spoofed network with attacker as man in the middle hijacking every request and response made by the victim.
For enterprises, the results of ARP spoofing attacks may have significant repercussions. In its most fundamental implementation, ARP spoofing attack is used by the extraction of confidential information to take control over the entire CPS network. Furthermore, to simplify other attacks, ARP spoofing attacks are also used, such as:
- Service-related attacks: DoS attacks mostly use ARP spoofing to connect multiple IP addresses to the same target MAC address. The destination traffic is then sent to the MAC address of the destination for several different IP addresses, which is then overloaded with traffic.
- Session hijacking: ARP spoofing can be used by Session Hijacking to steal session IDs, giving private systems and attackers access to data.
- Change contact, such as pushing a malicious file or website to the workstation.
7.3.3.3 DNS Spoofing
Clients have the IP address linked with the domain name on the DNS resolutioner/server. They take addresses from human-readable sites, for example abc.com, and convert them into machine-readable IP addresses. Your operating system would search for a DNS resolver if a user is interested in accessing a website. As shown in Figure 7.6, the DNS solver responds to IP address and the web explorer takes that address and starts loading the website.

Figure 7.6 A typical DNS server with records stored to resolve domain names to their IPs along with certificates.
The user requests the IP address from the DNS server by assigning it a domain name, receives the IP address in return, and routes the user to that same IP address, as seen in Figures 7.7 and 7.8. Domain Name System (DNS) Spoofing is an attack that redirects internet traffic to a bogus website that matches its intended destination using the changed DNS record.
When users are asked to sign in (which they believe) to their account, allowing the perpetrator the ability to steal their access credentials and other confidential information.
Furthermore, a malicious website is also used to install a worm or virus on a user’s computer, providing long access to the attacker and the data he or she stores. The DNS cache server can be poisoned by DNS cache attackers by a request for a DNS resolver, a request for a DNS resolver, and then pressured to react when a name server queries the DNS resolver. This is possible because UDP instead of TCP is used by DNS clients, and because there is actually no validation of DNS information. Usually, by ARP spoofing, the first attacker to carry out this assault will be a middleman. If this attack is successful, user requests are spoiled by the attacker and stopped from flowing to the DNS domain, as seen in Figure 7.9, the attacker begins their site with a spoof of those pages. The UDP or datagram protocol allows all communicators to start communication and perform a handshake to check system identity instead of using TCP. In addition, it is a UDP that allows all the communication parties in this process. UDP does not ensure a connection is open, that the receiver will be pleased to receive or that the sender will be who it believes to be. This is why the UDP is susceptible to forging. By forging header data, an attacker can send a message over UDP and claim to be a reaction from a legitimate server. Instantly, the customer is routed to the spoof page rather than to the official website. Now since it is an intruder’s server, stealing all the information entered into it is straightforward.
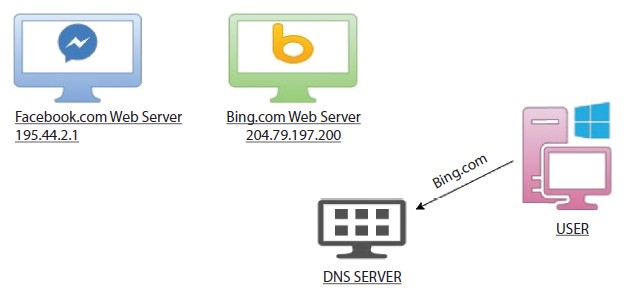
Figure 7.7 Diagram showing how every request made by any user is first redirected to the DNS server to resolve the IP of that domain.
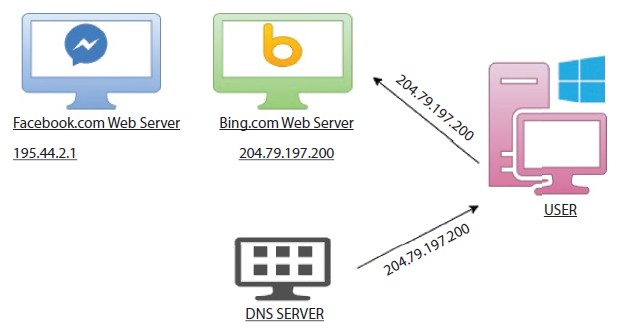
Figure 7.8 DNS server responding with a redirection request to the user for the requested domain and user redirected to the server of that domain.
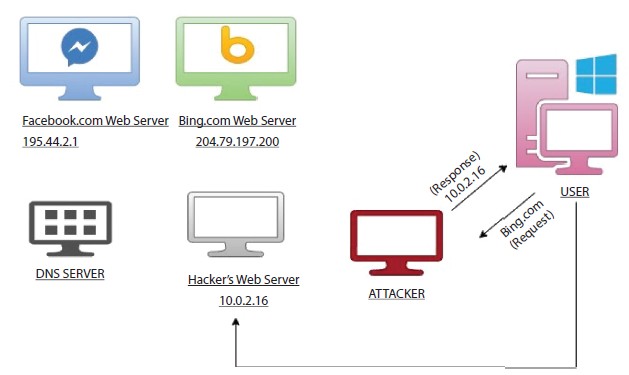
Figure 7.9 Attacker using DNS spoofing to redirect any request by the user to its own web server and thus gaining potential information using spoofed pages.
7.3.3.4 mDNS Spoofing
A protocol that uses, but utilises otherwise, the same API as Unicast DNS system is Multicast DNS (mDNS). Each of the machines on the LAN stores their respective DNS record list (such as A, MX, PTR, SRV, etc.), and is named if both the IP address of the PC and the recording are to be known from the mDNS client. With its IP address, the PC responds.
Unless the attack is performed on a network where DNS requests cannot be sniffed at and eventually modified by attackers, mDNS spoofing attacks are likely because it makes a difference. No matter what kind of transportation. mDNS spoofing attacks impact several items like not just iTunes, Firefox, Xbox 360, different routers, most printers, and more. Figure 7.10 demonstrates that the request is transmitted when no server is identified and the attacker with the mDNS spoofing attack convinces the user that it is the file server because it has collected all requests on each server and hence the hacker has become a man in the middle of it. Now that can escalate this situation into any attack.
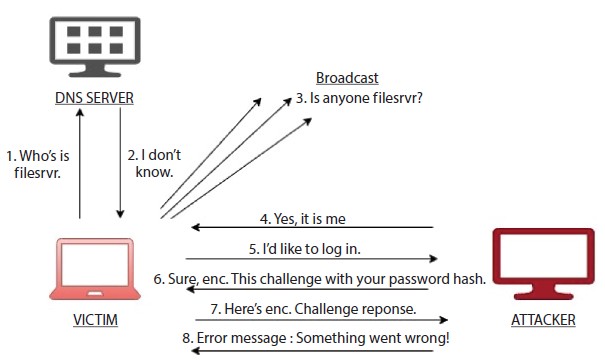
Figure 7.10 mDNS spoofing attack by capturing every broadcast request and spoofing the user into believing that the attacker is the file server.
MDNS can be queried at a multicast address by an mDNS enabled client. In return, all clients listening to that address will answer with their name. Today, if we have two same-name clients, they are always the first, they win. For example, if your word processing program tries to print a document by searching for printer. Local, a false response to that DNS query is easy for attackers to upload, enabling them to search for a printer that has a different IP address. Gives directions. Thus, the local name is essentially stolen/poisoned for a period of time.
This method of attack is not as successful on a WiFi network as it is easier to fire DNS packets and to forge DNS answers, so mDNS attacks are very useful in occasions. A case of this kind happens when you estimate. Since most devices support MDNS to one degree or another, attackers can learn a variety of useful objects, such as user-friendly versions and tool forms, administrative URLs and user email addresses, support information, etc.
7.3.3.5 SSL Stripping
SSL/TLS is a static protocol that is used to share confidential data. This protocol is used, for example, for sharing private documents, such as banking and email communications. The protocol is protected through the creation of an encrypted connection between two parties (typically a client application and a server). This protocol is also used by browsers and web servers when a secure connection is required. In most circumstances, the following accidents occur when a stable link is established:
- An unsecured HTTP request is submitted by the user.
- The server responds via HTTP and forwards the user to a secure protocol (HTTPS).
- A secure HTTPS request is submitted by the user, and the secure session begins.
SSL striped or down gradable attacks on websites that are capable of removing the safety measures imposed by Secure Socket Layer (SSL) certificates are attacks on HTTPS (Hypertext Transfer Protocol Protected) sites. SSL stripping is a technique which reduces your HTTPS—Hypertext Transfer Protocol connection from a secure HTTP, which makes the connection unsafe and makes your data easy to handle. The attacker redirects the attacker to a secure HTTP to strip SSL. The HTTPS protocol receives a user request to the server. The attacker would then establish an HTTPS connection between him and the server and, as a bridge, unsecured connections with the user.
The SSL strip benefits from accessing SSL sites for the majority of users. Most visitors connect to a web page that redirects to the SSL page with a 302 redirect or through a link to a non-SSL domain. For instance, if the user wants to buy a product and enter the URL www.abc.com in the address bar the browser connects to the attached device and the server awaits the response. In short, the assailant sends the victim’s application on the online store server in the SSL strip and receives HTTPS secured payment tab. For starters, https://www.abc.com. At this point the intruder is fully controlled by the secure payment page. It downgrades and returns it to the HTTPS browser of the victim. You have now redirected your web to http://www.abc.com. From now on, all the data from the victim will be sent in plain text format and interrupted by the intruder. In the meantime, the server on the website should assume that it has successfully created a stable link on the machine of the victim, but not to the attacker.
The KRACK attack ultimately showed that the media connecting companies with the Internet cannot rely blindly on the consumer. It shows that encryption, even though the website requires HTTPS, can be completely removed. After the SSL strip attack was successfully performed, victim information is sent in plain text format and is avoidable by anyone, including the attacker. This violates integrity and confidentiality of PIIs, such as login passwords, bank accounts, sensitive business records, and other information that is publicly identified. The possibility of this vulnerability is obvious and it will have different consequences for your digital presence.
7.4 Proposed Algorithm of Detection and Prevention
7.4.1 ARP Spoofing
Generally, man in the middle attacks happen by changing a property of the system like the MAC address of the router, server address or even the access point. For the detection of such attacks special scripts can be made which will monitor the device while it is running for any such change and alert the user and prevent any data loss to the attacker.
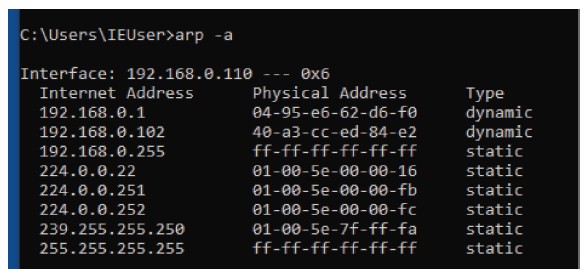
Figure 7.11 ARP table of a typical network with 192.168.0.1 as the gateway and other devices connected to the network.
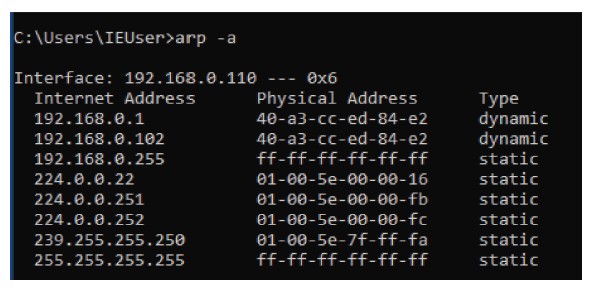
Figure 7.12 ARP table of a spoofed network with two different IP 192.168.0.1 and 192.168.0.102 having the same MAC address depicting the attacker’s IP as 192.168.0.102.
ARP attacks generally alter the ARP table of the system. In a network,
- No two IP addresses can have the same MAC address.
- When connected to a network the MAC address of the gateway cannot change until and unless the network changes.
Figure 7.11 shows the ARP table of a typical network. Figure 7.12 shows the ARP table of a spoofed network.
For detection, avoidance and avoidance of ARP spoofing attacks, the following approaches are recommended:
- Filtering packets: packet filters scan packets when sent over the network. Packet filters Packet filters are useful in ARP spoofing protection because they can filter and block packets with contradictory source address data (packets from outside the network that show source addresses from inside the network and vice versa).
- Stop untrustful relationships: organisations should maintain at least processes that are trust-dependent. Confidence relationships only depend on the IP address for authentication, so that attackers are able to spoof ARP attacks much easier.
- Tools to detect spoofing of ARP: Applications that support organisations in tracking attacks from Spoofing ARP are available for most applications. These programmes work before the transmission and authentication of data sent and authenticated.
- The use of encrypted network protocols is to prevent data encryption attacks before transmission and data are handled by the ARP bolster, such as Transport Layer Protection (TLS), Secure SSH, HTTP Secure and other secure networking protocols.
For prevention, the script developed works on the theory that when one connects to a new network, the ARP table of the system is updated to store the MAC address of the gateway. This table gets updated each time a user connects to a new network. This new record is then monitored over by the script. As soon as the attacker tries to poison the user into MITM attack, the MAC address following that IP address will automatically get changed. As the IP is being monitored over, as soon as the change happens it is notified to the user in the form of an alert box, also asking them to disconnect from the network they are being connected to and thus prevents any information from flowing through to the attacker. Figure 7.13 depicts the algorithm used to develop the script.
Figure 7.14 shows that the user is being alerted that there was an ARP attack and then he/she is asked if they want to disconnect from the network as shown in Figure 7.15. If the user clicks on OK, then the user gets disconnected to protect the information as shown in Figure 7.16. But if for some reason the user decides to continue with the network, then a warning sign is shown, and no further action will be taken as according to Figure 7.17.

Figure 7.13 The ARP detection script explained using a detailed algorithm with all choices taken from the user.
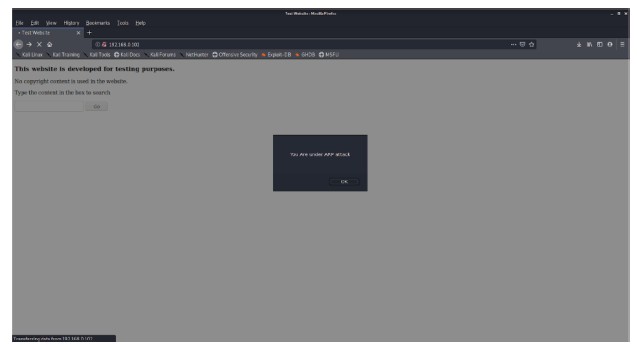
Figure 7.14 A test web page was developed, when the attacker tries to become man in the middle the alert is shown that the user is under attack to prevent loss of potential information.
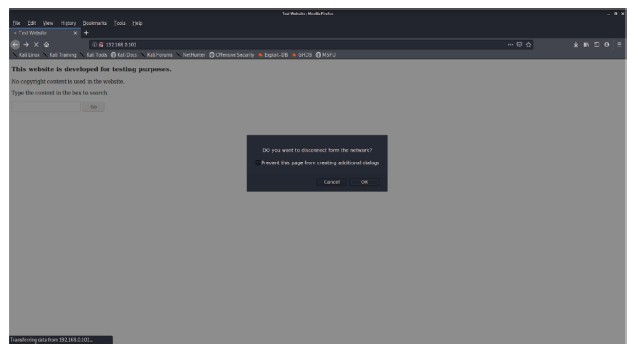
Figure 7.15 Script asking the user if he/she wants to disconnect from the network as they are under ARP spoofing attack.

Figure 7.16 User disconnected from the attacked network on choosing to disconnect, preventing any information loss.

Figure 7.17 No action taken even under ARP attack as the user decided to continue even after alerting.
Also, the script monitors the ARP table for same MAC address as sometimes the poisoning is done through different gateway, and as no two IP addresses can have same MAC address, so as soon as the poisoning is done, the MAC address of two IP’s become same as shown in Figure 7.14 and the script once again alerts the user as above asking with the same protocol.
7.4.2 Rogue Access Point and SSL Stripping
Usually, there are legal APs for hotels, colleges and companies, and an intruder may have access to a cellular network. Here, the attacker’s purpose is to provide friends with network access. Instead of exchanging keys, the intruder links the AP to the current AP, allowing friends to exchange allowed contacts. Since many wired identification systems focus on switch port use rules, wireless traffic that does not detect RAP that appears to be legitimate will be observed.
This is not only a security concern, but it also limits the business model for hotels that offer wireless connectivity. This is because the attacker will now be an ISP and sell the link, which is part of the Mac OS, through Internet sharing (or users can install Open App on Linux machines).
For detection of Rogue access points, the user can be made aware of some of the facts that these access points are generally open with no security key as compared to other protected APs with WEP/WPA/WPA2/WPA2PSK (Wi-Fi Protected Access2 PreShared Key) protection. Also, on the network manager’s side a network login page can be administered in which each user should have different login information. And HSTS (Hypertext transfer protocol Strict Transport Security) should be forced on the above said login page. Thus, the authors developed a script which helps to force HTTPS on the login page, so all the information transferred will be in an encrypted form, and the script developed also runs on the user’s side giving them alerts if they try to access a HTTP page so that they should not continue with their sign in as the information can be stolen.
The HTTPS force script works in the following way:
- It has an SSL certificate checker which checks for authenticity of the certificates on the flow.
- The network login page is strictly directed to HTTPS with 301 permanently moved.
- A HSTS header is served under base domain for HTTPS requests.
- Also, all subdomain directives and predictive are specified.
- All subdomains of the login page are then again covered with SSL certificates.
The script works in the way that if during a network connection the user is displayed a login page over HTTP instead of HTTPS then the user gets alerted. The script monitors the browser for the SSL certificates as shown in the algorithm in Figure 7.18.
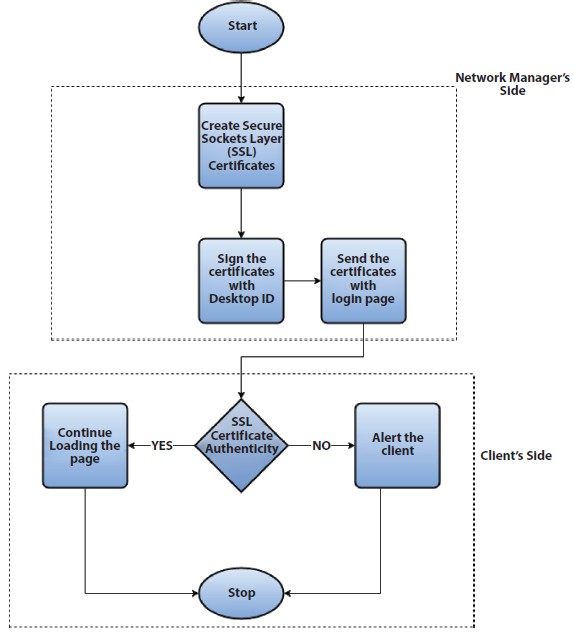
Figure 7.18 Algorithm for creation of SSL Certificates and its validation to prevent rogue access point from doing any damage.
7.4.3 DNS Spoofing
DNS spoofing is a serious threat. Fortunately, there are several simple measures you can take that provide effective protection against DNS spoofing.
- Using Transport Encryption
You should at least be able to detect DNS spoofing attacks if your links are secured by transport encryption. Since the malicious host does not have the security certificate that the real host will have, when the connection is created, the browser and email client can submit warnings. It provides you an opportunity to terminate the connection and introduce additional security measures. - Encrypt DNS traffic
If the data transmission is secured by transport encryption, the connection to the DNS server is still vulnerable and is called the weakest link. On the user side, though, there are dedicated implementations for DNS request encryption. Furthermore, DNS servers must also support DNS encryption-related authentication technologies for this to function. - Using virtual private networks
Using virtual private networks (VPNs) can also help guard against DNS spoofing, in addition to transport security and protecting DNS service connections. All the links are routed into an encrypted tunnel while using a VPN. You should bear in mind, though, that the IP address of the DNS server will still be stored in most VPN programs. The VPN’s defence against DNS spoofing would become inadequate if it is a malicious address. - Using a public DNS resolver network
Using a public DNS resolver is one of the most important security precautions you24 can take against DNS spoofing. The following advantages are offered by the use of public DNS solvers:- ○ High-speed DNS responses: thousands of servers worldwide are powered by massive DNS resolver networks. The physically nearest servers are still used for name resolution thanks to Anycast routing, which is reflected in shorter response times.
- ○ High data protection and confidentiality level: Many Internet service providers sell data generated by DNS traffic from their users. Usually, these common public resolutions store little or no user data, giving a high degree of data protection and confidentiality.
- ○ Censorship imposes no measures: Laws of state censorship are applicable only inside national borders. Usually, Internet service providers work within the homes of their customers and are expected to enforce state censorship. However, without contemplating state-governed censorship, a resolute network based abroad will serve its networks worldwide.
- ○ Supports current norms of security: Specializing in responding to DNS requests, wide public DNS resolver networks. Using current security protocols like DNSSEC, DoH, DoT and DNSCrypt, they are also trailblazers.
- ○ Blocks malicious domains: Since they hold a blacklist of established malicious domains, using public DNS resolver networks will help protect against ransomware [39] and phishing. Trying to enter these domains would result in the redirection of the user to the alert page.
But all these have their limitations and can be broken or by passed easily so, as in DNS spoofing, as the attacker redirects to the spoofed page, the developed script checks for authenticity of the redirected page by first checking the domain name as generally the spoofed domain doesn’t exactly match the exact domain of the page. So, if there is any change then it again alerts the user that it isn’t an authenticated web page as shown in Figure 7.19. After which the user can decide to test its server for DNS spoofing attack. The spoofing attack can be tested using overloading the request server. The script so developed is used in such a manner that it sends an adequate number of requests over a very less period. If the server crashes readily then it is not a real server but a spoofed one and the user is alerted about it, but if the server doesn’t crash then it is of no problem. It works on the theory that a company server is configured to handle multiple requests at a single time whereas this feature is not available in a hacker’s or an individual’s server. So, then the crash time is noted and if that time is less than the given time, it means that the user is being DNS Spoofed and is alerted at that time as shown in the algorithm developed in Figure 7.20.

Figure 7.19 A spoofed login page of Facebook.com but the domain contains three o’s which are generally neglected by any user the script alerted the domain was not authentic thus preventing information loss.

Figure 7.20 Steps implemented in detection of DNS spoofing script and testing the server for the spoof based on crashing time.
7.5 Results and Discussion
Oppliger et al. [26] in their article discussed how all the methods to provide security against SSL/TLS attacks fail to provide security with the advanced attacks. They also argued how these sessions even running on SSL fail to provide security by impersonation of tokens. Zheng et al. [27] analyzed various ARP spoof detection techniques and classified them based on which part of attack they stopped to protect the system. But these techniques are not yet effective as they work on specific parts which make them vulnerable to other attacks.
Authors developed novel scripts that check for different variations of cyberattacks mainly man in the middle attacks like ARP Poisoning, DNS Spoofing, SSL Stripping, each of which scripts runs in the background preventing a specific type of attack and if any of the attacks happen, the user is alerted at that time only to take any necessary actions to prevent potential data loss. Though the method of attacking is being advanced day by day, these scripts provide a general and novel way to prevent these attacks from happening instead of already existing applications to prevent the attack which were focused on a specific type of attack thus, not very successful in defending the network and machines.
7.6 Conclusion and Future Scope
Although with growing dependence on wireless technology, the threats are rising day by day and it is impossible to stop the attacks altogether but detection of these in early stages can prevent potential data loss. For each attack a different method is designed which monitors the specific component which is affected by that attack which helps in detection of such attacks. Such as ARP poisoning can’t be done without having two same IPs in the ARP table, any method of implementing ARP will result in the same MAC address of two different IPs (Internet Protocols), so monitoring the base component helps to detect the attack in any form.
Every attack has a different script, and these can be packaged into a single application which will try to prevent the attacks altogether. Authors tried to replicate real time scenarios and it was achieved using virtual machines and the scripts were tested on them. It was found that they are working properly, and all the figures attached in the paper are the tests performed on these machines. This led to a conclusion that even if the attacks cannot be prevented; if the user can be educated enough and these scripts are used properly data loss can be prevented.
Social networking has become an inevitable catchline among teenagers as well as today’s older generation. In recent years, there has been observed remarkable growth in social networking sites, especially in terms of adaptability as well as popularity both in the media and academia [38, 40, 41]. The sharing of sensitive information can be spoofed or changed using different MITM attacks. Thus, the scripts developed by the authors can be used in such online social networks on users’ end to increase the security and privacy. Also, with the boom in the internet age with the ongoing pandemic the need to secure individual and commercial devices from such attacks is the most important concern and the scripts developed thus can be integrated in the security systems implemented in the PC and laptops thus providing a sense of privacy and security.
References
1. Baheti, R. and Gill, H., Cyber-physical systems. Impact Control Technol., 12, 161–166, Mar. 2011.
2. Ge, H., Yue, D., Xie, X.P., Deng, S., Hu, S.L., Analysis of cyber physical systems security issue via uncertainty approaches. Proc. Adv. Comput. Methods Life Syst. Model. Simulation, pp. 421–431, 2017.
3. Liu, Y., Peng, Y., Wang, B., Yao, S., Liu, Z., Review on cyber-physical systems. IEEE/CAA J. Autom. Sin., 4, 1, 27–40, 2017.
4. Kagermann, H., Change through digitization-value creation in the age of Industry 4.0, in: Management of Permanent Change National Academy of Science and Engineering, pp. 23–45, Springer, Berlin, Germany, 2015.
5. Annunziata, M. and Evans, P.C., The industrial Internet@ work, General Electric White Paper, 2013.
6. Advanced Research and Technology for Embedded Intelligence and Systems, ARTEMIS Industry Association, 2007.
7. Schätz, B., Törngren, M., Passerone, R., Pfeifer, H., Bensalem, S., McDermid, J., Sangiovanni-Vincentelli, A., Cengarle, M.V., CyPhERS-cyber-physical European roadmap and strategy.pp 1-48 Fortiss GmbH, Munich, Germany, Tech. Rep, 611430, 2015.
8. Rana, M.M., Li, L., Su, S.W., Cyber-attack protection and control of microgrids. IEEE/CAA J. Autom. Sin., 5, 2, 602–609, Mar. 2018.
9. Teixeira, A., Shames, I., Sandberg, H., Johansson, K.H., A secure control framework for resource-limited adversaries. Automatica, 51, 135–148, Jan. 2015.
10. Wang, X., Ning, Z., Zhou, M., Hu, X., Wang, L., Zhang, Y. et al., Privacy-preserving content dissemination for vehicular social networks: Challenges and solutions. IEEE Commun. Surv. Tutor., 21, 2, 1314–1345, 2nd Quart, 2019.
11. Xie, Y., Liu, L., Li, R., Hu, J., Han, Y., Peng, X., Security-aware signal packing algorithm for CAN-based automotive cyber-physical systems. IEEE/CAA J. Autom. Sin., 2, 4, 422–430, Oct. 2015.
12. Lee, E.A., Cyber physical systems: Design challenges. Proc. 11th IEEE Int. Symp. Object Compon. -Oriented Real-Time Distrib. Comput. (ISORC), pp. 363–369, May 2008.
13. Shi, J., Wan, J., Yan, H., Suo, H., A survey of cyber-physical systems. Proc. Int. Conf. Wireless Commun. Signal Process. (WCSP), pp. 1–6, 2011.
14. Mo, Y., Kim, T.H.-J., Brancik, K., Dickinson, D., Lee, H., Perrig, A. et al., Cyber–physical security of a smart grid infrastructure. Proc. IEEE, vol. 100, pp. 195–209, Jan. 2012.
15. Lu, T., Xu, B., Guo, X., Zhao, L., Xie, F., A new multilevel framework for cyber-physical system security. Proc. 1st Int. Workshop Swarm Edge Cloud, pp. 1–2, 2013.
16. Liu, Y., Peng, Y., Wang, B., Yao, S., Liu, Z., Review on cyber-physical systems. IEEE/CAA J. Autom. Sin., 4, 1, 27–40, Jan. 2017.
17. Callegati, F., Cerroni, W., Ramilli, M., Man-in-the-Middle Attack to the HTTPS Protocol. IEEE Secur. Priv., 7, 1, 78–81, 2009.
18. Callegati, F., Cerroni, W., Ramilli, M., Man-in-the-Middle Attack to the HTTPS Protocol. IEEE Secur. Priv. Mag., 7, 1, 78–81, 2009.
19. Yang, C., Song, Y., Gu, G., Active User-Side Evil Twin Access Point Detection Using Statistical Techniques. IEEE Trans. Inf. Forensics Secur., 7, 5, 1638– 1651, 2012.
20. Ramachandran, V. and Nandi, S., Detecting ARP Spoofing: An Active Techniqu. Inf. Syst. Secur. Lect. Notes Comput. Sci., 3803, 239–250, 2005.
21. Nam, S., Kim, D., Kim, J., Enhanced ARP: preventing ARP poisoning-based man-in-the-middle attacks. IEEE Commun. Lett., 14, 2, 187–189, 2010.
22. Maksutov, A.A., Cherepanov, I.A., Alekseev, M.S., Detection and prevention of DNS spoofing attacks. 2017 Siberian Symposium on Data Science and Engineering (SSDSE), 2017.
23. Wander, M., Boelmann, C., Schwittmann, L., Weis, T., Measurement of Globally Visible DNS Injection. IEEE Access, 2, 526–536, 2014.
24. Prowell, S., Kraus, R., Borkin, M., Man-in-the-Middle, in: Seven Deadliest Network Attacks, pp. 101–120, 2010.
25. Khelif, M.A., Lorandel, J., Romain, O., Regnery, M., Baheux, D., Barbu, G., Toward a hardware man-in-the-middle attack on PCIe bus. Microprocessors and Microsystems, vol. 77, p. 103198, 2020.
26. Oppliger, R., Hauser, R., Basin, D., SSL/TLS session-aware user authentication – Or how to effectively thwart the man-in-the-middle. Comput. Commun., 29, 12, 2238–2246, 2006.
27. Zheng, M., Yang, S., Piao, X., Sun, W., Research on ARP Spoof Detection Strategies in Unreliable LAN. Hum. Centered Comput. Lect. Notes Comput. Sci., 8944, 216–225, 2015.
28. Sandhya, S. and Devi, K.S., Contention for Man-in-the-Middle Attacks in Bluetooth Networks. 2012 Fourth International Conference on Computational Intelligence and Communication Networks, 2012.
29. Deng, C., Distributed Resilient Control for Cyber-Physical Systems under Denial-of-Service Attacks. 2019 23rd International Conference on Mechatronics Technology (ICMT), 2019.
30. Li, F., Yan, X., Xie, Y., Sang, Z., Yuan, X., A Review of Cyber-Attack Methods in Cyber-Physical Power System. 2019 IEEE 8th International Conference on Advanced Power System Automation and Protection (APAP), 2019.
31. Carvalho, L.K., Wu, Y.-C., Kwong, R., Lafortune, S., Detection and mitigation of classes of attacks in supervisory control systems. Automatica, 97, 121–133, Nov. 2018.
32. Comer, D.E. and Droms, R.E., Computer Networks and Internets, Prentice-Hall, Upper Saddle River, NJ, USA, 2003, [online] Available: https://dl.acm.org/doi/book/10.5555/861590.
33. Lima, P.M., Alves, M.V.S., Carvalho, L.K., Moreira, M.V., Security against network attacks in supervisory control systems, in: IFAC-PapersOnLine, vol. 50, pp. 12333–12338, Jul. 2017.
34. Wood, A.D. and Stankovic, J.A., Denial of service in sensor networks. Comput. J., 35, 10, 54–62, Oct. 2002.
35. Xu, W., Ma, K., Trappe, W., Zhang, Y., Jamming sensor networks: Attack and defense strategies. IEEE Netw., 20, 3, 41–47, May/Jun. 2006.
36. Liu, S., Liu, X.P., El Saddik, A., Denial-of-Service (dos) attacks on load frequency control in smart grids. Proc. IEEE PES Innov. Smart Grid Technol. Conf. (ISGT), pp. 1–6, Feb. 2013.
37. Srikantha, P. and Kundur, D., Denial of service attacks and mitigation for stability in cyber-enabled power grid. Proc. IEEE Power Energy Soc. Innov. Smart Grid Technol. Conf. (ISGT), pp. 1–5, Feb. 2015.
38. Le, D.N., Kumar, R., Mishra, B.K., Chatterjee, J.M., Khari, M. (Eds.), Cyber Security in Parallel and Distributed Computing: Concepts, Techniques, in: Applications and Case Studies, John Wiley & Sons, USA, 2019.
39. Tandon, A. and Nayyar, A., A comprehensive survey on ransomware attack: a growing havoc cyberthreat, in: Data Management, Analytics and Innovation, pp. 403–420, 2019.
40. Jain, R., Jain, N., Nayyar, A., Security and privacy in social networks: data and structural anonymity, in: In Handbook of Computer Networks and Cyber Security, pp. 265–293, Springer, Cham, 2020.
41. Vasaki, P., Jhanjhi, N.Z., Humayun, M., Fostering Public-Private Partnership: Between Governments and Technologists in Developing National Cybersecurity Framework, in: Employing Recent Technologies for Improved Digital Governance, pp. 237–255, IGI Global, USA, 2020.
*Corresponding author: [email protected]
