4
Precise Risk Assessment and Management
Ambika N.*
Department of Computer Science and Applications, St. Francis College Bangalore, India
Abstract
Cyber network is a huge system consisting of lot of terminals, hand-held devices with varying sizes and capacities communicating with each other. The size of the system has made it impossible or takes a lot of time to trace the terminals. Hence the hackers can introduce different kinds of attacks into the network without being traced for a very long time. As some of the confidential data is transmitted over the network, it becomes essential to safeguard the data and the terminals attached to the network.
The previous work suggested uses multi-criteria decision analysis. It evaluates the danger in a digital framework. It potentially selects an ideal therapeutic technique. The creators ascertain the general danger score utilizing the measures compared to the TVC segments. The standards separate into sub-criteria, etc. Its score is the weighted amount of the sub-criteria scores. On the most reduced level, scores for the rules can be allowed by topic specialists or gotten from quantifiable information. Utilizing a similar MCDA approach, countermeasures can be scored and organized. Scores allocate depending on how it compels the countermeasure is at the moderation of every part of the danger. Notwithstanding adequacy, countermeasure scores incorporate other models regarded significant by the partners and network protection supervisors, for example, cost and time. The incorporation of countermeasure prioritizes bringing the system past danger evaluation and toward hazard the board. The suggestion uses a better methodology to assess the risk of the framework. The client’s sources are jolted down to prioritize what has to be given preference. Based on the sources different risk issues are evaluated. It measures the risk based on the priority, usage of a particular technology and the risks associated with them. The contribution evaluates the same based on a particular scenario.
Keywords: Cyber security, multi-criteria decision analysis, risk issues, priority-based analysis, area-based analysis
4.1 Introduction
The Internet is an enormous network encompassing different kinds of terminals, devices, and gateways. The number of users is sizable in number. Hence, keeping track of each user doing is quite complicated. The clients can have the intent to inject different kinds of attacks. The expenses on the criminals are very less. They just need a computer, internet connection and a program that fructify their intentions. It also provides them the facility to reach beyond geographical location. On the other end, the identity of the guilty is difficult to be traced. Based on the report conducted by Symantec 69% of the population became victims of different types of cyber attacks [1–3]. The survey tells that more than one million attacks fructify a day. Hence it becomes essential to detect them and provide countermeasure to the same.
The previous work [4] uses multi-criteria decision analysis. It evaluates the danger in a digital framework. It potentially selects an ideal therapeutic technique. The creators ascertain the general danger score utilizing the measures compared to the TVC segments. The standards separate into sub-criteria, etc. Its score is the weighted amount of the sub-criteria scores. On the most reduced level, scores for the rules can be allowed by topic specialists or gotten from quantifiable information. Utilizing a similar MCDA approach, countermeasures can be scored and organized. Scores allocate depending on how it compels the countermeasure is at the moderation of every part of the danger. Notwithstanding adequacy, countermeasure scores incorporate other models regarded significant by the partners and network protection supervisors, for example, cost and time. The incorporation of countermeasure prioritizes bringing the system past danger evaluation and toward hazard the board. The suggestion uses a better methodology to assess the risk of the framework. The client’s sources are jolted down to prioritize what has to be given preference. Based on the sources different risk issues are evaluated. It measures the risk based on the priority, usage of a particular technology and the risks associated with them. The contribution evaluates the same based on a particular scenario.
The introduction starts in Section 4.1. The need for security is detailed in Section 4.2. Section 4.3 details different kinds of attacks existing over the Internet. Literary study is elaborated in Section 4.4. The proposed study is represented in Section 4.5. The contribution is concluded in Section 4.6.
4.2 Need for Security
The WannaCry ransomware exploits a natural weakness of Microsoft Windows, effectively investigated by the U.S. Public safety Bureau for concealed reconnaissance purposes. Other than influencing singular PCs, the WannaCry essentially upsets the regular activity of a few huge business and administrative organizations counting FedEx, Deutsche Bahn, Megafon, Telefónica, the Russian Central Bank, Russian Railways, and Russia’s Interior Service. In the United Kingdom, the cyber attack disabled the data innovation frameworks of medical clinics across the National Wellness Service. The final product of task drops, medical clinics put on redirection status, and wellbeing data reports, for example, diligent evidence being made inaccessible in both England and Scotland. Primer proof focuses on North Korea’s multitude of programmers as the primary guilty party of what has been advised by the network protection organization F-Secure is the greatest ransomware flare-up ever. The recurrence of cyber attacks has been dramatically expanding, with a few comparative occasions. It details in the United States in the previous few years, the most eminent one on February 2016, when the Hollywood Presbyterian Examination location in Los Angeles wound up salaried $17,000 emancipation in bitcoins to recapture control of its data innovation organization.
4.2.1 Confidentiality
The property [5] data isn’t made accessible or unveiled to unapproved people, elements, or cycles. Secrecy secures information away and in transmission. Privacy undermines at any point data can be seen or perused by unapproved substances or uncovered out of the ‘need to know’ gathering or local area. This trade-off could be either physical or electronic. The electronic secrecy bargains incorporate end-clients or elements getting to data, information, or assets does not imply for them. It guarantees that data is uncovered to approved clients as it were. The classification includes the ideas of information protection, encryption, and figure or cryptography.
The OCTAVE system [6] decides hazard levels and for arranging against digital assaults. Its design intends to limit association openness to dangers and to anticipate the likely results of assaults and address the ones that succeed. The structure is part into three complete stages—building resource-based danger profiles, distinguishing foundation weaknesses, and creating security systems and plans. There are two renditions of OCTAVE, with OCTAVE-S, giving an improved adaptation pointed at more modest associations with level progressive designs. OCTAVE Allegro is exhaustive form focused on huge organizations with diverse designs.
4.2.2 Integrity
It is the capacity [7, 8] to guarantee that data doesn’t change. It implies that information can’t alter without approval. Trustworthiness guarantees that the information has not been modified away or potentially in transmission. Honesty penetrates at whatever point data changes without express approval by the data proprietor. This trade-off could bring about the commission or oversight of either approved client or unapproved substance. Honesty bargain could be either unplanned or deliberate and through malevolent purpose. Pernicious uprightness bargain could be that a material purposefully adds, erases, or changes data set records. It can happen either through an approved gathering or by an unapproved party when the client approaches that they shouldn’t have. Inadvertent trustworthiness bargain is the point at which a framework alters or erases records that it shouldn’t. It can happen when an infection contaminates a framework or when a client accomplishes something that he didn’t mean to do. It frequently checks that you need a document erased before it does as such. Respectability alludes to the reliability of data assets.
4.2.3 Availability
It guarantees [9] that data resources are available at whatever point is required. It is a significant property since any disturbance of administration may unfavourably influence the business activities of SMEs. Accessibility [10] guarantees that an approved client or element or unit can get to a framework asset when a legitimate solicitation is made. Assuming this asset is a strategic resource, accessibility necessitates that reinforcement or excess arrangements ensure its accessibility. Its trade-off could happen because of inadvertent activities or mishaps or by pernicious or purposeful demonstrations, for example, a Denial-of-Service assault or botnets. Accessibility bargains could likewise arrange as specialized, human, or marvels, such as flood, quake, or blackout.
4.2.4 Accountability
The rule [11, 12] that an individual is endowed to protect and control hardware, keying material, and data and is responsible to an appropriate expert for the misfortune or abuse of that gear or data. The aspect expresses that each individual who works with an information model has explicit responsibility regarding information assertion. The errands for which a person is able are primary for the unspecific information surety arrangement and can be quickly quantitative by a single person who has administrative responsibility regarding information verification. One framework organizes a description that all representatives should try not to innovate external programming on an arrangement having information structure. The person responsible for information safety performs infrequent verification on the planning. People should know about the anticipated from them and guide persistent improvement.
4.2.5 Auditing
The motivation behind a network safety review [13] is to approve the strategies by the online protection group. There are control components set up to authorize them. An examination is formal than an evaluation. The free outsider of the association performs a review. The outsider has a certificate. An association can have an inner review group. The group should go about as a free organization. The network safety review discovers the presence of controls. The evaluators seldom test the viability of those controls. It doesn’t imply that it is taking care of its responsibility to alleviate the digital danger. A network protection review program has a period and a spot. Most reviews won’t uncover the genuine viability of the security controls you have set up.
4.3 Different Kinds of Attacks
4.3.1 Malware
It alludes to a gathering of attacks stacking on a model. It bargains the structure to the reward of a foe. Some model category of attack integrates corruptness [14], worms [15], Trojan [16], spyware [17], and bot executable [18]. Malware pollutes model in a categorization of framework proliferation from tainted devices, betraying clients to open debased evidences, or pleasing customers to see malware dissemination website. In more concrete instances of malware contamination, malware may pile itself onto a USB drive enclosed into a corrupt appliance and subsequently taint every framework into which that device embeds. Malware may engender from appliance and kind of mechanism that contain implanted model and procedure rationale. So, malware can be embedded anytime in the framework existence cycle. Victims of malware can trial anything from the end client frameworks, servers, network gadgets, and cycle dominance frameworks like Supervisory Command and Information Attainment.
The assaults occur at an only mark of boundary among instrumentation, types of gear, planning parts, or network tier victimization ofactive design and execution weaknesses at each layer. It ensures each asset, the edge protection methodology use dominantly to put a divider outside all inner assets to shield everything internal from any unenviable disruption from external. The border safeguard device uses a security system and hostile to ill health planning initiate inside disruption expectancy/discovery model. Any assemblage coming from external is captured and inspected to assurance there is no malware entering into within possession. Unspecific acceptance of this boundary precaution framework has occurred because it is far uncomplicated and little costly to get one borderline than to get a large measure of uses or countless interior organizations. The entrance control instruments utilize related to the edge protection system.
It composes as research often to characteristic safety weaknesses or now and again to display differentiated susceptibility. Today, the malware uses chiefly to take delicate private, monetary, or commercial enterprise information to support others. As per the report, Trojans represent part of the dangers. In 2009, Trojans were reported to have made up 60% of all malware. In 2011 it was 73%. The current pace exhibit that almost three out of each four fresh malware deformation made in 2011 were Trojans and shows that it is the arm of judgment for digital hoodlums to lead network disruption and info fetching.
Spam [19] adverts were used to send unimportant, unseen, and impulsive communication to millions of participant role. Spam has ended up being particular in the marketplace since junk e-mail is sent secretly without any reimbursement needed. Because of such devalued obstruction to the passage, electronic mail is different, and the measure of impulsive mail has formed hugely.
Phishing [20] is a methodology of undertaking to gain delicate info, for example, username, secret phrase, or Visa credentials by fetching on the happening of a reliable substance. Most phishing pranks depend on misleading a customer into seeing a noxious website affirmation to be from genuine firm and agency. The uninformed customer enters secluded information is then therefore utilized by noxious crooks. The strategies use specialized trickery supposed to make a relation in an email appear to have a place with an authentic unification, as a noteworthy financial institution. Incorrectly spelled URLs or the utilization of sub-spaces are basic deed used by phishers.
Drive-by Downloads [21] concern the accidental transfer of malware from the Cyberspace and are used by the aggressors to dispersed malware quickly. Drive-by transfer happen in a mixture of fortune. It initiates when a customer travel to a website while viewing an electronic mail content, or when customer click on a deceptive season up framework. However, the most well-known drive-by downloads happen by a broad border when seeing website.
4.3.2 Man-in-the-Middle Assault
Man-in-the-middle assault [22] occurs when the attacker tamper between the deuce agreement closes. Each content conveyed from origin A to communicator B comes at the assailant earlier arriving at its aim. The chances contain unapproved admittance to touchy data or conceivable outcomes to adjust the data/message.
4.3.3 Brute Force Assault
This [23] involves rehashed endeavors to access ensured data till the precise credential is established, and information will reach. The creator proposes [24] another technique known as the beast power assault approach to produce AEs against AI-based frameworks in online protection. The procedure is easy to carry out and maintains a strategic distance from the drawn-out preparation of GAN-based assault techniques. The tactics are slope-free techniques. It controls the highlights of info vectors in a determinate manner. It makes the strategy more reasonable for the ill-disposed assaults in network protection. It produces AEs dependent on the certainty scores of the objective classifiers heuristically. It is a discovery assault technique for which the designs and boundaries of the objective classifiers are pointless for assaults. The certainty scores of the objective models are the lone expected information to deliver AEs.
4.3.4 Distributed Denial of Service
This [25] is an attack that deals the availability of message. The assailant floods the injured party with orders, in this style acquiring unserviceable. The creator proposes [26] an insightful security framework against DDoS assaults in correspondence networks. It has two parts. A screen for recognition of DDoS assaults and a discriminator for the locate clients in the framework with noxious plans. A tale versatile continuous alteration-component model that trail the progressions in Mahalanobis spacing between examined highlight variables in the checked framework represents conceivable DDoS assaults. A grouping framework that trial over the comparability scores of personal conduct standards among the clients isolates the vindictive from the guiltless. It empowers the screen to adjust to the typical traffic system and diurnal or occasional varieties while simultaneously staying delicate to unusual changes. It is a solo way to deal with distinguishes traffic peculiarities. The framework makes noticed informing traffic type and power and doesn’t need any extra data, for example, trace backs. A strange change in the rush hour gridlock system proclaims on the off chance that the Mahalanobis spacing arrangement of the province variables in progressive period windows surpasses a limit work. It sets to a steady as an element of system boundaries or then again can be adaptive set.
4.4 Literature Survey
This section details the previous contributions made by various authors across different horizons. The work [4] uses multi-criteria decision analysis. It evaluates the danger in a digital framework. It potentially selects an ideal therapeutic technique. The creators ascertain the general danger score utilizing the measures compared to the TVC segments. The standards separate into sub-criteria, etc. Its score is the weighted amount of the sub-criteria scores. On the most reduced level, scores for the rules can be allowed by topic specialists or gotten from quantifiable information. Utilizing a similar MCDA approach, countermeasures can be scored and organized. Scores allocate depending on how it compels the countermeasure is at the moderation of every part of the danger. Notwithstanding adequacy, countermeasure scores incorporate other models regarded significant by the partners and network protection supervisors, for example, cost and time. The incorporation of countermeasure prioritizes bringing the system past danger evaluation and toward hazard the board. The proposal uses a better methodology to assess the risk of the framework.
The methodology [27] contains two circles. The external circle features that STPA-SafeSec is an iterative methodology that should be reapplied in the framework to deal with this advancing existence. In its center, STPA is about imperatives and the control circles of the framework. Each control circle is dissected independently during the investigation. The imperatives refine for the framework all in all dependent on the disasters. At that point, these requirements get refined and planned to the control layer. Risks and ensuing misfortunes occur when control activities disregard at least one of the recently characterized requirements supposed unsafe control moves. The examination gives the way to infer the causal elements that lead to unsafe control activities. These causal variables reach out by STPA-SafeSec to incorporate safety contemplation. The theoretical activity tier acquires planned to an execution explicit part tier. This segment layer gives the way to refine the limitations and determine more explicit causative variables. It can additionally control inside and out security investigation. The outcomes are a bunch of changes that apply to the framework engineering. It guarantees misfortune-free activities are at long last determined. It depends on the situations that portray risky control activities.
The principle objective of CySeMoL [28] is to permit clients to make models of their designs and make computations on the probability of various digital assaults being fruitful. The model remembers the hypothesis for how credits in the article model rely upon one another security skill from the client of CySeMoL. Clients should model their framework engineering and indicate their properties to make computations conceivable. The classes in CySeMoL incorporate different IT parts like Operating System and Firewall, cycles, for example, Security Awareness Program, and Persons that are clients. Every element has qualities that can be either assaults steps made against the substance or countermeasures related to it. These ascribe are connected differently. The passwords of secret-word records have a probability of this assault being fruitful. It relies upon an individual possessing the secret word account is in a security mindfulness program. Each trait in CySeMoL can have the worth true or False and addresses either the probability of an assault being fruitful or the probability of a countermeasure being utilitarian.
The creators [29] utilize the MulVAL assault diagram tool stash. It can reach out to other assault charts comparing with semantics. The MulVAL thinking framework can consolidate CVSS measurements from NVD information sources and yield the AC metric. Attack Action Node model has the presence of an assailant effectively misusing the system. A separate AAN assault hub opposes sharing a solitary device. The new instrument acquaints with the model the incorrect perception. A circular segment from the original state to the perception state addresses the way that the perception. It uses restrictive probabilities. It does not qualify with and or hubs. When an aggressor is available and sending the record worker an NFS shell abuse parcel, this activity identifies an organization-based IDS. Tripwire screen could report a dubious record adjustment. Every hub in a Bayesian organization relates with a CPT which is the likelihood dispersion of the hub’s potential states adapted on the guardians’ states. They use the specific qualities relating to possibility. They utilize the center estimations of the reaches comparing to other probability are some examples.
The work [30] breaks down the digital protection of the PSSE in the SCADA framework. They describe the aggressor by characterizing a bunch of goals. The approach incorporates subtle trickiness assaults, both for straight and non-linear assessors. Assaults influencing the assembly of the PSSE are identified with information accessibility, as they view as DoS attacks. They evaluate compromises between model precision and conceivable assault sway for various BDD plans. The PSSE issues find the solution using a measuring structure. It is a non-linear component focusing on the frame of the energy system used. It has a variable having zero-mean Gaussian measurements in the covariance system. It results in estimation value considered to minimize in different scenarios. These measures satisfy the first level conditions used to find optimization. It symbolizes Jacobian resultant. The answer obtained is symbolization resulting from Newton’s methodology. It is the result of using the iterative method to find an accurate value. The hessian resultant obtained is due to merging collapse. The second-order computation is expensive. The same applies to the PSSE methodology. The resultant leads to the Gauss–Newton resultant.
The CBC-MAC calculation [31] depends on the Triple Information Encryption Standard. It characterizes in subset-037 v.3.1.0 of the ERTMS particular. The credential material trades through credential administration framework secured by various solution substances. The system uses Tetrad unique keys, which orders in trio tiers. Session keys, KSMACs, are created from the verification key material, KMAC, for every meeting. This system depicts in detail in subset-037. It Exchanges two arbitrary numbers in content between two elements. It performs the 3DES-CBC-MAC calculation multiple times, utilizing these two arbitrary numbers as seed material and three squares of 64 bits taken from KMAC as keys.
The creators [32] have investigated the cost, effect, and hazard of ACT in the SHARPE programming bundle. ROA and ROI calculation completes by characterizing capacities in SHARPE. The measurements, for example, assault cost and ROA mirrors have security venture cost, hazard, effect, and ROI address the protector’s perspective. Cost and effect of assault were utilized as measures by Schneier for investigation of AT. In the ACT, the cost can be of two sorts; cost of assault and security speculation cost. When at least one occasion rehashes in the ACT, Rauzy’s calculation builds the double choice chart (BDD) relating to the ACT. The effect of the ACT min-cut shows the significant effect as assault sway for the ACT. Security venture cost registers by adding the expense of executing countermeasures in the ACT. Hazard calculation performs by the result of the likelihood of assault and effect. ROA is an action that evaluates the advantage acquired from a specific assault.
The digital actual security investigation approach [33] remembers experimentation for sensible testbeds. Methods and skills distinguish framework-level weaknesses. Results if the weak are misused, and secure ways to deal with kill the weak. Framework-level outcomes are hard to decide whether different defects abuses at the same time. Experiment on usable frameworks or test-beds is in deciding framework-level effects. Experiment on functional frameworks in nearly all the happening is beyond the realm of imagination on account of the danger to the operational framework and its central goal. Building a trial framework indistinguishable from the operational framework is cost restrictive. Programming models of the gadgets and framework are ordinarily not accessible or, if accessible, need highlights identified with network protection investigation. A compelling approach to make a digital actual security experimentation stage is through a half-breed testbed. The strategy empowers construction framework of both the SCADA framework and the framework. The framework of the SCADA incorporates its availability to the different commercial enterprise and the Cyberspace. The actual framework is chosen from divergent resolve for the framework under examination. In a half and half examination, the SCADA framework occasions and the framework occasions are participated in lockstep to make sensitive activity.
Undertaking design [34] is a way to deal with the executives of data structures. It includes control frameworks. It depends on models of the frameworks and their current circumstances. They portray how security speculations join with building models to reason arranged design models. Assault trees are graphical documentation advanced from deficiency trees, where the fundamental objective of an attacker. The numerical derivation motor that impact graphs give permits demonstrating complex choice issues. Coupled to this numerical motor is likewise graphical documentation where the factors address as a chart. The models permit thinking about the outcomes of different situations and accordingly support dynamic. A theoretical model involves four parts entities, entity connections, properties, and trait connections. The initial three of these segments can be perceived from standard demonstrating dialects, for example, the class outlines of the UML. Elements are a focal segment in demonstrating dialects. It is an in-class graph used to address ideas of pertinence for the model.
The theoretical model [35] starts by proof assortment. A security appraisal commonly includes information assortment regarding interviews, documentation examines, log surveys, determining different measurements, infiltration tests, and then some. One part of this data assortment recognizes the elements that researchers and their relationship to one another. Another piece of the information assortment concerns the nature of different ascribes and investigating how these characteristics impact security. Putting together a theoretical model concerning an all-encompassing impact chart that communicates the guard diagram has direct advantages. It guarantees that the model utilized for appraisal, and therefore the information gathered for it, contains the information expected for creating and surveying security using guard charts. The model covers the parts that are of significance to the evaluation. The appraisal will zero in on things of importance to its outcome. Besides, it is from a launched conceptual model direct and upheld by devices to infer and ascribes characteristic links and restrictive likelihood tables. Utilizing a theoretical model, the modeler will demonstrate the substances, their connections, and the condition w.r.t properties to survey the security. It starts up in the solid model. The relationship among them determines the organization of qualities. This organization will compare to an all-inclusive impact outline communicating a safeguard diagram. It ascribes to be incorporated can be gotten from the elements.
VAPT system [36] directs in deuce significant parts. The primary incomplete designed with the Investigation and Insight of active Weakness. The subsequent half patterns are with the Victimization of the important agreement of Weakness. It assesses their Intensity and Impacts over the Prey model. Weakness evaluation is an aloof method through infiltration testing is an operative method where safety proficients animate conflict and trial the target locate and its repercussion power against attacks. VAPT analyzer targets identifying essential data about the test target and examining the objective to discover the weaknesses. Weakness appraisal is a technique that follows the precise and proactive way to deal with find weakness. It is polished to find known and obscure issues in the framework.
The I4.0 creation plant Smart Factory OWL [37] portrays and breaks down the design of cloud-based administrations and their information. A creation framework for preparing mass material is considered a utilization case. It improves the item quality, accomplishes higher framework accessibility, and builds efficiency. In this way, information-based assistance for plant checking and enhancement dissects as a cloud arrangement. The sensors [38] procure information. The application is a reason for a hazard investigation. It determines the utilization case of “Condition Based Maintenance”, including availability and related information streams. This application is a plant administrator employing cloud administration. The rationale either peruses crude information or effectively totalled information from the sensor or plays out an ensuing information examination. It plays out condition-based support. It gives support rationale requires a ton of skill, specifically about the application. A merchant of programming arrangements may give this aptitude as a Cloud administration. The assistance facilitates by a Cloud specialist co-op and associated employing multi-point associations.
The work [39] follows an objective situated methodology for security danger displaying and examination by utilizing visual model components. The fundamental UAV model characterizes as a blend of six isolated frameworks: Data obtaining module, Elevation, and Direction Quotation Scheme, Transportation Organization, Dominance Component, Information Work Compartment, and the Measurement Compartment. The correspondence framework has not appeared as it incorporates every one of the component and control signs and information signals that goes through it. The UAV was planned by distinguishing significant segments of the framework and the UAV. The related and conceivable assault characterize alongside the potential dangers in the danger model of the framework.
4.5 Proposed Work
The work [4] uses multi-criteria decision analysis. It evaluates the danger in a digital framework. It potentially selects an ideal therapeutic technique. The creators ascertain the general danger score utilizing the measures compared to the TVC segments. The standards separate into sub-criteria, etc. Its score is the weighted amount of the sub-criteria scores. On the most reduced level, scores for the rules can be allowed by topic specialists or gotten from quantifiable information. Utilizing a similar MCDA approach, countermeasures can be scored and organized. Scores allocate depending on how it compels the countermeasure is at the moderation of every part of the danger. Notwithstanding adequacy, countermeasure scores incorporate other models regarded significant by the partners and network protection supervisors, for example, cost and time. The incorporation of countermeasure prioritizes bringing the system past danger evaluation and toward hazard the board. The proposal uses a better methodology to assess the risk of the framework.
4.5.1 Objective
- To evaluate appropriate risk and provide adequate countermeasure for the same that the customer is keen for.
- Prioritize the risk in the network. Sources of risk can be evaluated and appropriate measure can be adopted. The client can rank based on the facilities or the sources they are utilizing.
4.5.2 Notations Used in the Contribution
Table 4.1 represents the notations used in the contribution.
Table 4.1 Notations used in the contribution.
| Notations | Description |
| R | Total risk factor |
| Si | Source risk |
| Pi | Priority assigned |
| ωi | Weight of ith risk |
| Ri | ith risk |
4.5.3 Methodology
Based on different kinds of vulnerabilities and threats, the area based risk-score is computed. Figure 4.1 represents the different kinds of breaching incidents. Figure 4.2 provides the amount of malware infections year-wise.
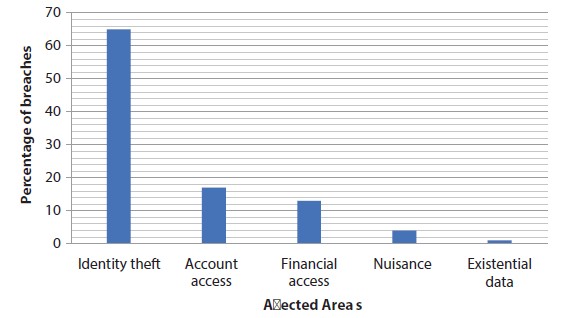
Figure 4.1 Cyber threats area-wise.
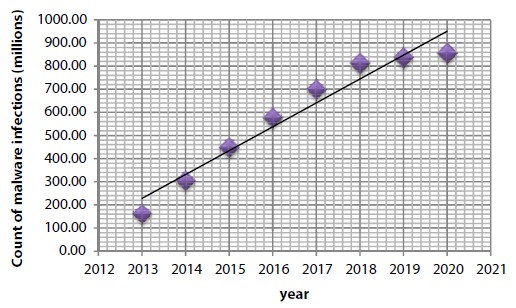
Figure 4.2 Malware infections year-wise.
The previous work [4] uses multi-criteria decision analysis. It evaluates the total work and the danger is in a digital framework. It potentially selects an ideal therapeutic technique. The creators ascertain the general danger score utilizing the measures compared to the TVC segments. The standards separate into sub-criteria, etc. Its score is the weighted amount of the sub-criteria scores. On the most reduced level, scores for the rules can be allowed by topic specialists or gotten from quantifiable information. Utilizing a similar MCDA approach, countermeasures can be scored and organized. Scores allocate depending on how it compels the countermeasure is at the moderation of every part of the danger. Notwithstanding adequacy, countermeasure scores incorporate other models regarded significant by the partners and network protection supervisors, for example, cost and time. The incorporation of countermeasure prioritizes bringing the system past danger evaluation and toward hazard the board.
The suggestions use a better methodology to assess the risk of the framework. The client’s sources are jolted down to prioritize what has to be given preference. Based on the sources different risk issues are evaluated. Let Si be the source from which a risk issue Ri is analyzed. It weighs ωi. Based on its usage (w.r.t client) its priority is set. Let its priority by Pi. The total risk R is calculated. Eq. (4.1) is used to calculate the risk factor based on source used by the clients. The sources used very often are given higher priority.
Total risk is calculated using Eq. (4.2)
Based on the client’s necessity, the risk counter measure is suggested.
4.5.4 Simulation and Analysis
The work [4] uses multi-criteria decision analysis. It evaluates the danger in a digital framework. It potentially selects an ideal therapeutic technique. The creators ascertain the general danger score utilizing the measures compared to the TVC segments. The standards separate into sub-criteria, etc. Its score is the weighted amount of the sub-criteria scores. On the most reduced level, scores for the rules can be allowed by topic specialists or gotten from quantifiable information. Utilizing a similar MCDA approach, countermeasures can be scored and organized. Scores allocate depending on how it compels the countermeasure is at the moderation of every part of the danger. Notwithstanding adequacy, countermeasure scores incorporate other models regarded significant by the partners and network protection supervisors, for example, cost and time. The incorporation of countermeasure prioritizes bringing the system past danger evaluation and toward hazard the board. The proposal uses a better methodology to assess the risk of the framework. Table 4.2 represents sources and its priorities. Table 4.3 represents the parameters used in the simulation.
Table 4.2 Representation of sources and its priorities.
| Sources | Number of employees | Access frequency per employee | Priority |
| Financial access (specific to account department employees) | 3 | Once a day (for a client) | 10 |
| Data access (provided to employees under manager-level and above) | 5 | three times a day | 5 |
| Email (used by all the employees regularly) | 40 | six times a day | 2 |
Table 4.3 Simulation parameters.
| Parameters | Description |
| Number of terminals used | 40 (five of them are given special access to data + 3 are given access to do online transactions) |
| Maximum limit to send email | 24,000 bytes |
| Maximum limit to download or upload data | 20,000 bytes |
| Amount of data transmitted during online money transaction | 800 bytes |
| Maximum time limit to transit online money | 4 min |
| Total simulation time | 30 min |
The following assumptions are made in the simulation:
- The client uses more of email, followed by data access, and later financial access.
- The priority is given based on their usage.
Figure 4.3 jolts down the parameters used in simulating the work.
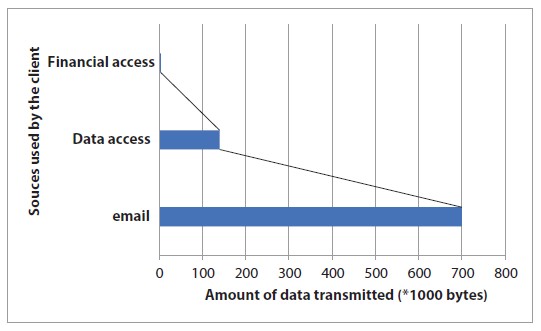
Figure 4.3 Simulated results.
4.6 Conclusion
Cyber security is an essential component in the system. The system or a part of the system may be under different kinds of threats. It becomes essential to detect them and find the countermeasure for the same. The previous contribution uses multi-criteria decision analysis. It evaluates the danger in a digital framework. It potentially selects an ideal therapeutic technique. The creators ascertain the general danger score utilizing the measures compared to the TVC segments. The standards separate into sub-criteria, etc. Its score is the weighted amount of the sub-criteria scores. On the most reduced level, scores for the rules can be allowed by topic specialists or gotten from quantifiable information. Utilizing a similar MCDA approach, countermeasures can be scored and organized. Scores allocate depending on how it compels the countermeasure is at the moderation of every part of the danger. Notwithstanding adequacy, countermeasure scores incorporate other models regarded significant by the partners and network protection supervisors, for example, cost and time. The incorporation of countermeasure prioritizes bringing the system past danger evaluation and toward hazard the board. The suggested proposal is aimed to satisfy client according to his needs. It measures the risk based on the priority, usage of a particular technology and the risks associated with them. The contribution evaluates the same based on a particular scenario.
References
1. Ambika, N., Chaubey, N.K., Prajapati, B.B., Improved Methodology to Detect Advanced Persistent Threat Attacks, in: Quantum Cryptography and the Future of Cyber Security, pp. 184–202, IGI Global, US, 2020.
2. Ambika, N. and Al-Turjman, F., An Improved Solution to Tackle Cyber Attacks, in: Advanced Controllers for Smart Cities: An Industry 4.0 Perspective, pp. 15–23, Springer, Switzerland, 2021.
3. Ten, C.W., Hong, J., Liu, C.C., Anomaly detection for cybersecurity of the substations. IEEE Trans. Smart Grid., 2, 4, 865–873, 2011.
4. Ganin, A.A. et al., Multicriteria decision framework for cybersecurity risk assessment and management. Risk Anal., 40, 1, 183–199, 2020.
5. Gamage, T.T., Roth, T.P., McMillin, B.M.M., Confidentiality preserving security properties for cyber-physical systems. IEEE 35th Annual Computer Software and Applications Conference, IEEE, Germany, pp. 28–37, 2011.
6. Aminzade, M., Confidentiality, integrity and availability–finding a balanced IT framework. Int. J. Netw. Secur., 2018, 5, 9–11, 2018.
7. Reed, J.H., Gonzalez, C.R.A., Gatlinburg, T.N., Enhancing smart grid cyber security using power fingerprinting: Integrity assessment and intrusion detection. Future of Instrumentation International Workshop (FIIW), IEEE., USA, pp. 1–3, 2012.
8. Mo, Y. and Sinopoli, B., On the performance degradation of cyber-physical systems under stealthy integrity attacks. IEEE Trans. Automat. Contr., 61, 9, 2618–2624, 2015.
9. Parvin, S. et al., Multi-cyber framework for availability enhancement of cyber physical systems. Comput. J., 95, 927–948, 2013.
10. Walker-Roberts, S., Hammoudeh, M., Dehghantanha, A., A systematic review of the availability and efficacy of countermeasures to internal threats in healthcare critical infrastructure. IEEE Access, 6, 25167–25177, 2018.
11. Liu, J., Xiao, Y., Gao, J., Achieving accountability in smart grid. IEEE Syst. J., 8, 2, 493–508, 2013.
12. Kacianka, S. and Pretschner, A., Understanding and formalizing accountability for cyber-physical systems. IEEE International Conference on Systems, Man, and Cybernetics (SMC), IEEE, Miyazaki, Japan, pp. 3165–3170, 2018.
13. Greitzer, F.L. and Frincke, D.A., Combining traditional cyber security audit data with psychosocial data: towards predictive modeling for insider threat mitigation, in: Insider threats in cyber security, pp. 85–113, s.l. : Springer, Boston, MA, 2010.
14. Bou-Harb, E., Debbabi, M., Assi, C., A novel cyber security capability: Inferring Internet-scale infections by correlating malware and probing activities. Comput. Netw., 94, 327–343, 2016.
15. Chaudhary, P., Gupta, S., Gupta, B.B., Auditing defense against XSS worms in online social network-based web applications, in: Handbook of research on modern cryptographic solutions for computer and cyber security, pp. 216–245, IGI Global., US, 2016.
16. Vincent, H. et al., Trojan detection and side-channel analyses for cyber-security in cyber-physical manufacturing systems. 43rd North American Manufacturing Research Conference, vol. 1, elsevier, North Carolina, United States, 201577-85.
17. Boiko, A., Shendryk, V., Boiko, O., Information systems for supply chain management: uncertainties, risks and cyber security, in: ICTE in Transportation and Logistics 2018, vol. 149, s.l. : elsevier, Elsevier journal Procedia Computer Science, 201965-70. http://www.wikicfp.com/cfp/servlet/event.showcfp?eventid=72728©ownerid=13988
18. Chatterjee, M., Namin, A.S., Datta, P., Evidence fusion for malicious bot detection in IoT. IEEE International Conference on Big Data, IEEE., Seattle WA, USA, pp. 4545–4548, 2018.
19. Abdulhamid, S., II et al., Comparative Analysis of Classification Algorithms for Email Spam Detection. Int. J. Comput. Netw., 10, 1, 60–67, 2018.
20. Dodge, Jr, R. C., Carver, C., Ferguson, A.J., Phishing for user security awareness. Comput. Secur., 26, 1, 73–80, 2007.
21. Egele, M. et al., Defending browsers against drive-by downloads: Mitigating heap-spraying code injection attacks. International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, s.l. : Springer, Berlin, Heidelberg, pp. 88–106, 2009.
22. Yang, Y. et al., Man-in-the-middle attack test-bed investigating cyber-security vulnerabilities in smart grid SCADA systems. International Conference on Sustainable Power Generation and Supply (SUPERGEN 2012), IET, Hangzhou, China, pp. 138–146, 2012.
23. Hafiz, M.M. and Ali, F.H.M., Profiling and mitigating brute force attack in home wireless LAN. International Conference on Computational Science and Technology (ICCST), IEEE, Kota Kinabalu, Malaysia, pp. 1–6, 2014.
24. Zhang, S., Xie, X., Xu, Y., A Brute-Force Black-Box Method to Attack Machine Learning-Based Systems in Cybersecurity. IEEE Access, 8, 128250–128263, 2020.
25. Spyridopoulos, T. et al., A game theoretic defence framework against DoS/DDoS cyber attacks. Comput. Secur., 38, 39–50, 2013.
26. Semerci, M., Cemgil, A.T., Sankur, B., An intelligent cyber security system against DDoS attacks in SIP networks. Comput. Netw., 136, 137–154, 2018.
27. Friedberg, I. et al., STPA-SafeSec: Safety and security analysis for cyber-physical systems. J. Inf. Secur. Appl., 34, 183–196, 2017.
28. Holm, H. et al., CySeMoL: A tool for cyber security analysis of enterprises. 22nd International Conference and Exhibition on Electricity Distribution (CIRED 2013), IET, Stockholm, pp. 1–4, 2013.
29. Xie, P. et al., Using Bayesian networks for cyber security analysis. IEEE/IFIP International Conference on Dependable Systems & Networks (DSN), IEEE, Chicago, IL, USA, pp. 211–220, 2010.
30. Teixeira, A. et al., Cyber security analysis of state estimators in electric power systems. 49th IEEE conference on decision and control (CDC), IEEE, Atlanta, GA, USA, pp. 5991–5998, 2010.
31. Lopez, I. and Aguado, M., Cyber security analysis of the European train control system. IEEE Commun. Mag., 53, 10, 110–116, 2015.
32. Roy, A., Kim, D.S., Trivedi, K.S., Cyber security analysis using attack countermeasure trees. Sixth Annual Workshop on Cyber Security and Information Intelligence Research, ACM, Oak Ridge Tennessee, USA, pp. 1–4, 2010.
33. Urias, V., Van Leeuwen, B., Richardson, B., Supervisory Command and Data Acquisition (SCADA) system cyber security analysis using a live, virtual, and constructive (LVC) testbed. IEEE Military Communications Conference, IEEE, Orlando, FL, USA, pp. 1–8, 2012.
34. Ekstedt, M. and Sommestad, T., Enterprise architecture models for cyber security analysis. IEEE/PES Power Systems Conference and Exposition, IEEE., Seattle, WA, USA, pp. 1–6, 2009.
35. Sommestad, T., Ekstedt, M., Johnson, P., Cyber security risks assessment with bayesian defense graphs and architectural models. 42nd Hawaii International Conference on System Sciences, IEEE., Waikoloa, HI, USA, pp. 1–10, 2009.
36. Shinde, P.S. and Ardhapurkar, S.B., Cyber security analysis using vulnerability assessment and penetration testing. World Conference on Futuristic Trends in Research and Innovation for Social Welfare (Startup Conclave), IEEE, Coimbatore, India, pp. 1–5, 2016.
37. Flatt, H. et al., Analysis of the Cyber-Security of industry 4.0 technologies based on RAMI 4.0 and identification of requirements. IEEE 21st International Conference on Emerging Technologies and Factory Automation (ETFA), IEEE, Berlin, Germany, pp. 1–4, 2016.
38. Dewal, P. et al., Security attacks in wireless sensor networks: a survey. In Cyber Security. J. Cybersecur, 729, 47–58, 2018.
39. Javaid, A.Y. et al., Cyber security threat analysis and modeling of an unmanned aerial vehicle system. IEEE Conference on Technologies for Homeland Security (HST), IEEE, Waltham, MA, USA, pp. 585–590, 2012.
- *Email: [email protected]
