Chapter 5
Operational Aspects of a Cyberattack: Intelligence, Planning and Conduct 1
5.1. Introduction
Since the beginning of 2000, the increased amount of computerized attacks has triggered an increasing number of investigations. In particular, the generalized computer attack on Estonia in 2007 gave way to a wide field of reflection on what we call cyberwar and cyberattacks, without the difference between the two being clearly defined.
These reflections have gotten straight down to the State prerogative, and that States themselves have quickly come to understand, in an inevitable context of national security, the urgent need to rigorously define the concept. In addition, they have also seen the need for legislation, on the international front as much as the national, and to organize themselves in an aim for defense (defensive cyberwar). But more recently, as an unavoidable consequence from any field related to the State context, this may be in an aim to attack (offensive cyberwar). The publication of the French White Paper on Defense and National Security [LBD 08] has initiated this last aspect, as also other countries have.
If there is a relatively successful reflection on the human aspects (legal, societal, historical, etc.) of what a cyberwar might be, then on the other hand there is no open study on the technical and especially operational aspects regarding the materialization of a cyberattack. Yet, from a purely military point of view, this “practical” question is very important. Any reflection on the matter, then, will inevitably lead to a certain number of questions:
– How do we conduct a cyberwar?
– Is there a cybernetic reality which is independent of the real world where cyberwars will exclusively take place? In other words, are our computerized systems and networks an independent territory, disconnected from the real world?
– Is computerized war fundamentally different (both technically and operationally) from a conventional war?
– Must we create weapons and (military) units in their own right with digital engineering, a digital infantry, etc?
– What are the targets (tactically and strategically), and what is a critical infrastructure in this context? The concept of a bunker itself, does it still have meaning?
– Are the concepts of law in cyberwar and the ethics of the cyberwarrior still valid on technical and operational fronts?
It is fundamental to answer these questions if we want to define a rigorous and applicable operational approach.
This double operational (military, police) and scientific/technical culture is vital. Simply understanding how a weapon works is not enough. It is incredibly important to know how to use it in the chosen context, and to know its boundaries and possibilities. The best hacker in the world will be useless if he cannot organize his tools and skills for a more general maneuver. The culture of intelligence is indeed essential. This concerns the technical aspect, but also and above all, the other forms of intelligence (human, electromagnetic, communications, etc.).
It is also fundamental to know our target perfectly, including its characteristics and its ability to act and react, its potential, etc. The target is often said to be a “critical” structure, so complex that it is vital to discover all its features beforehand.
Not only are these answers important, but they must lead on to an operational approach and a methodology which must confirm and convince others of the reality of cyberattacks, or at least of their technical feasibility. Too many authors (whose technical legitimacy is somewhat doubtful) are confirming that these threats are only a myth [GRE 02] in order to legitimize the existence of specialized agencies, whereas even since 2000 we have been made aware of the real, studied and valid attacks.
In this chapter, we will explain what attackers can do, and how. From this point of view, it is a fundamental point to cast out any ethical notion, and to think how the enemy would think. We will also endeavor to generalize the concept of a cyberattack. For our decision-makers, such an attack boils down to a distributed denial of service (DDoS) or defacing websites. This would also allow us to widen the concept of a critical infrastructure and to show that the line of defense, which consists of building bunkers, is deceptive.
We will use the different feedback we have acquired to construct this operational approach:
– the technical analysis of real attacks;
– the analysis of military doctrines in particular, and the author’s 20 year experience in infantry weapons;
– legal expertises in attacks or computer crimes;
– NATO’s InfoOps (information operations) followed by the author who has provided a very rich source of information and reflection [OTA 08];
– scientific and technical research in the computer security domain, favoring the hacker and attacker’s vision, and going from theory to (and for) practice and the operational.
5.2. Towards a broader concept of cyberwar
5.2.1. War and cyberwar: common ground
The concept of cyberwar has not really been defined, or at least, nobody has managed to set a single definition which is universally accepted and recognized. In this chapter we will not consider the definitions and conceptions which already exist, as they will be presented in detail in other chapters, and because we wish to offer an alternative vision, one which is principally based on an operational vision.
The only founding text which relates to our approach (and which inspired our train of thought and approach) is that written by the Chinese colonels Qiao and Wang in their book Unrestricted Warfare [LAN 02]. In this major publication, there are two sentences which illustrate particularly well the real context where we wish to be: “The first rule of unrestricted warfare is that there are no rules, nothing is forbidden […]. There is nothing in the world today that cannot become a weapon”.
First of all, the concept of cyberwar uses a concept of war that we may define as an extreme form of communication1 between two or several groups trying to protect or increase their wealth, interests or their influence, via actions on:
– resources (mining, oil, etc.);
– populations (human element);
– mindsets (intellectual or spiritual element);
– territory (geographic element);
– information (immaterial element), etc.
In other words, the final aim of war is for action on the physical and real world. The cybernetic dimension of it only constitutes an additional tool through new systems and tools in order to act on the physical world.
The computerized dimension (systems and networks) only adds a dimension which is comparable to the 3rd dimension, which was exploited by the use of flight at the beginning of the 20th Century. This is precisely the vision that Colonels Liang Qiao and Xiangsui Wang developed [LAN 02]: no dimension should be overlooked, and no dimension should be favored exclusively. The following passage from their work clearly shows that the digital field is just one dimension amongst others. It is namely the coordination of several dimensions, targeting the physical and real sphere, which is indeed the ultimate objective: “if the attacking side secretly musters large amounts of capital without the enemy nation being aware of this at all and launches a sneak attack against its financial markets, then after causing a financial crisis, buries a computer virus and hacker detachment in the opponent's computer system in advance, while at the same time carrying out a network attack against the enemy so that the civilian electricity network, traffic dispatching network, financial transaction network, telephone communications network, and mass media network are completely paralyzed, this will cause the enemy nation to fall into social panic, street riots, and a political crisis.” [LAN 02].
The vision of a war which only aims at a purely digital realm, a sort of Second Life type, seems to be extremely limited. It would be possible (author’s thesis) to compare it with one which consists of replacing conflicts and other armed confrontations with football tournaments. This leads us to define the concepts of cyberattacks and cyberwar in the following way:
– cyberwar is a classic war where at least one of its elements, in its materialization, namely the motivations and tools (weapons in the broadest sense) relies on the computerized or digital field. These elements are called cyberattacks; – a cyberattack is an attack on the real realm:
- either directly, by going through an information and communication system (ICS). In this case, the computerized field is only a tool or a means (attack on people, for instance);
- or indirectly, by attacking an ICS where one or several components from the real realm depend on it (for instance, an attack on an electronic voting machine network).
From this point of view, we will take the legal definition of cybercrime2.
5.2.2. New orders in cyberwar
If cyberwar (or cyberattacks which make it a war) is only one new dimension in the domain of armed conflict, then on the other hand it has intrinsic features which radically change the order, and above all power relationships between belligerents. There are essentially three of these features: obliterating the concept of time, the concept of space and above all, the concept of proof. These three characteristics are interdependent of each other, even if for the purpose of simplicity we will set them out separately. They help to make the relations between attacker and target very asymmetric, and this is for the benefit of these relationships.
5.2.2.1. Obliterating space
Whereas in the case of conventional warfare, the spatial dimension is a critical strategic and tactical set of data – an air attack happens after the planes have had to travel a long distance with the possibility of being detected by satellites and radars. In the case of a cyberattack, it is possible to strike any point in space instantly from any other space.
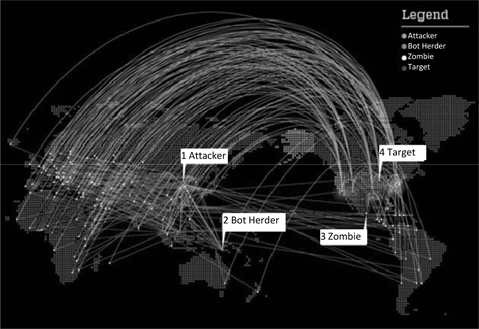
Figure 5.1 which describes the action of a botnet (malicious network made of thousands of infected machines and controlled by a pirate) shows this obliteration of space.
This disappearance of the concept of space consequently removes the target’s capacity to react, who then cannot easily link the attack to a specific origin. With no geographic reference, the target is then no longer able to identify with certainty the nature of the enemy. Without an enemy, war is impossible.
Figure 5.1. General principle of a botnet operation
5.2.2.2. Obliterating time
This primarily concerns the victim who perceives the attack as being sudden and immediate. On the other hand, if the attacker must make his move that very instant, then his preparations and planning may be spread over time, up to months beforehand. With the attack perceived of as sudden, then this will consequently deny the target of:
– the possibilities of obtaining intelligence, due to the loss of time references (real sequence of events and their chronology). Its analysis capacities are more than limited;
– reacting and leading its own maneuver. With no temporal reference, the target can no longer organize its retaliation in a way which is adapted to the attacker.
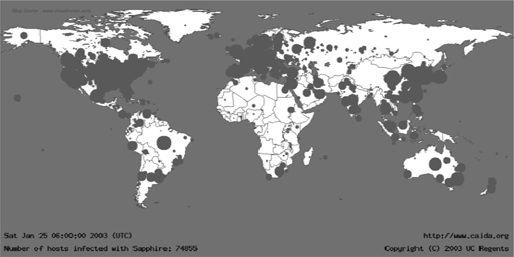
If the attack is powerful and well led, then its sudden nature and its consequence (surprise) remove all abilities to react. Or rather the target, in the worst case, never manages to take the initiative. Figure 5.2 shows such an attack by the Slammer worm.
Current research shows that such an attack could be led in 2009 and would have had a global effect in a matter of minutes.
Figure 5.2. Slammer worm attack in January 2003 (15 minutes after the attack started)
5.2.2.3. Obliterating proof
This is probably the most important characteristic, to the extent that not only does it remove any exact image from the “battlefield” and from the tactical situation, but also allows the attacker to send a potentially falsified image, and one which is distorted from reality.
In the digital world, everything can be falsified (MAC address, IP address, documents, etc.) and the notion of proof (in the legal sense) no longer means anything. Due to the single fact that the concept of copying is dying out – we cannot copy an electric phenomenon – the very idea of proof is no longer valid. A worm such as Blaster could not be traced because it was connected to target machines through the theft of IP address [FIL 06]. Moreover, it was possible to trace the attacker either. An attacker might also use the certainty of tools such as cryptography against the person trying to analyze the available data [FIL 10] and wrongly incriminate an innocent third party. Furthermore, with the disappearance of the concept of proof (and therefore intelligence, in a military context), the idea of repercussion and legitimate defense is no longer valid either [BEN 05]. The target’s operational capacity is obliterated.
In this context, it is getting easier to understand that, devoid of truth, any idea of legislation is getting trickier, and the application of some unspecific law (in an international court) is more fanciful still
5.2.3. Who are cyberwarriors?
First of all, let us draw out the main consequences of what happens initially. Total dematerialization related to the computerized and digital realm, with the removal of all concepts of proof as a main primary effect (digital in particular), means that any attempt to obtain an ethical or lawful notion of cyberwar is in vain. Moreover, a cyber attacker who no longer fears being identified, revealed and incriminated, will exploit all the possibilities offered to him entirely. This is total warfare, in the Qia and Wang definition [LAN 02]. The very notion of control (of weapons) no longer means anything: if we can count warheads, tanks and planes, essentially all material, if we can trace the critical know-how for weapons of mass destruction, then this becomes completely deceptive in the case of weapons of mass infection (viruses, for instance). It is hard to imagine NATO inspectors trying to control cross-border digital influxes and streams.
In such a context, it is easy to understand how the computerized domain, more than any form of terrorism, gives an excellent dimension to the relationship from the weak to strong. Any individual with a sound knowledge of ICS’s (or ICT’s) is a potential cyber attacker. This makes any grad student studying computer science a potential hacker. Knowledge in computer science is freely available, universally spread (free software has greatly contributed to this irrefutable fact, opening up a real Pandora’s box) and therefore accessible to a large number of people: we just need a laptop, or even the latest cell phone, and an Internet connection to get up and running and have access to the most sophisticated techniques and tools.
On a more serious note, the responsibility of Western countries may also be incriminated via the real transfer of critical knowledge in our grad school classes (computer sciences, security, etc.) which welcome many foreign students whose experience shows, for some of them, that they had been connected with radical environments or movements.
Yet, if technical knowledge is indeed necessary, then it is far from being enough to lead large scale cyberattacks. It is essential to have a logistic ability offering coordination, planning and conduct. In this context, cyberattackers are just a link, obviously an important once, in the general chain. The main terrorist movements3 (al-Qaeda, Hezbollah), mafias and above all certain States offer this logistic support [ALM 08], [MES 99], [BAN 06], [PAR 10].
Since 2009, new actors have appeared on the scene as a structured movement: the hacker movement. Groups such as Antisec or more recently, The Anonymous have launched high-level structured operations on States (Iran, Zimbabwe, France, the European Union member states, etc.), entities (churches of scientology) and large companies (Mastercard, RSA Laboratories, HBGary, Maersk, etc.) These groups, structured into many sub-groups and layers have a high technical expertise at their disposal, and have access to the most vital technical resources. This is because a vast number of them work for the benefit of large software or security companies. Through what is called the “digital alter-globalist” [MAN 11], this international hacker is beginning to get a real political awareness and has technical means to make himself known and impose himself on others.
5.2.4. Is formalization possible?
After having put forward a definition of the concept of a cyberattack, the temptation might be to try to define it more formally. Probability theory or fuzzy logic are the two domains which come to mind naturally. Logically, operational thinking imagines the attacker’s movement or its very own, in terms of events, hypothesis or options which we could attach probabilities to initially, or even afterwards within a Bayesian approach. But, if this means something in the safety/reliability domain4, then on the other hand in the security domain, this approach cannot be applied. Security deals with managing intentional threats, which can be summarized by the famous duo of “sword versus shield”. These threats are unpredictable by nature, cannot be modeled and are adaptive. A good attacker will make sure to permanently innovate and above all, as a feature of the computerized field, to delete all traces of proof but, especially, to make up false proof.
In this context, assigning probabilities or using a more descriptive model, such as fuzzy logic for instance, to manage events which cannot be defined by nature, are no longer scientifically valid5.
5.3. Concept of critical infrastructure
This is the key concept in the warfare domain: the target must be known, evaluated, and its weakest elements identified. This is the role of the intelligence stage. Moreover, we must have an acceptable definition of the notion of the criticality of infrastructures. It is also necessary to have useful methodology so as to accurately determine the target’s weak point.
5.3.1. Generalized definition of the notion of critical infrastructure
In the computer security domain, the concept of critical infrastructures came about at the beginning of 2000. However the definitions proposed and then adopted are a far cry from being satisfactory, particularly if we are not coming from the defender’s point of view, but the attacker’s.
Let us take the example from the European Council in 2006: “Critical infrastructures are those physical and information technology facilities, networks, services and assets which, if disrupted or destroyed, would have a serious impact on the health, safety, security or economic well-being of citizens or the effective functioning of governments in European Union (EU) countries. Critical infrastructure includes: energy installations and networks, communications and information technology; finance, health care, food, water, transport, production, storage and transport of dangerous goods and government” [EUR 10].
This definition is too restrictive because it only takes into account the infrastructure itself, without considering its environment and some of its elements. It is important to greatly expand what we understand by critical infrastructure, and to add a certain number of additional elements.
5.3.1.1. The human element
Considering the human element, which is nearly always forgotten, is fundamental. No system or infrastructure can function without humans.
It starts by the decision maker. An attacker will always aim for the top6. Experience (and particularly the author’s, in the military field) shows that not only does a decision maker (often of a more humanist culture than scientific) not know about computer science, but above all, his role as decision maker and his importance in the hierarchy lets him think that the rules which apply to others do not apply to him. He is above rules. In the security domain (low material contingency), this is an everyday reality: the heart of the job, whatever it may be, is the priority and would not be vassalized by technical considerations, were they to determine the security of the job. This guilty and dangerous self-interest, and this narrow-minded view will be exploited with the attacker benefiting the most.
But often an infrastructure (or an organization) depends on a human. Let us imagine a serious crisis in a city known as “X” (riots, for example): the critical infrastructure is the head of the police force and, moreover, the head of the police and his high assistants. A preliminary computer attack (via the personal computers belonging to these forces, which are never secure) which attacks people (see section 5.5) will put these people out of action and will harm the operational capacity of the police’s infrastructure.
In the same line of ideas, a leader with contempt for the most basic rules of security, who connects a PDA (personal digital assistant) to an internal network, slipping past all the security devices of the DMZ could put this network in danger7.
But this also affects other types of staff:
– technical staff (not only computing staff);
– the staff or people with high media potential (Union representatives, journalists, etc.);
– any staff or person that the infrastructure depends on to function correctly, or any person able to impact this infrastructure through links or dependences.
These human elements, within system interdependence (section 5.3.2.) will be top targets.
5.3.1.2. External elements
Never taken into account, the target infrastructure will depend on these elements. They generally seem to be non-critical and are only somewhat protected. They are (non-exhaustive list):
– subcontractors;
– providers (of resources, services, basic products, etc.);
– data-centers (hosting company data);
– supervising services (e.g. telephone operators have relocated these services into countries where the culture of security is very far removed from our own);
– foreign or relocated sub-contractors;
– the target’s environment, political and cultural in particular.
It is important to take into account the political and public dimension (particularly the media). There is a high level of asymmetry between what public power could be in practice, and what an attacker might authorize.
Triggering a hard strike in a factory via a computerized attack, or causing a riot in sensitive areas will count as a series of diverted attacks which cannot simply be managed by sending in the police force. In the face of a sudden attack, the public power will be condemned to a long and perilous management strategy.
To reiterate our discussion, let us take the example of the possible introduction of one of the first flaws in the Windows XP core in 2001. The Microsoft editor subcontracts the largest aspect of its operating system (OS) developments in India.
In 2001, a one Abdul Afroze Razzak was arrested in Bombay. As a proven member of al-Qaeda, he was an IT technician recruited into the Indian development teams for Microsoft. It was highly suspected that he had willingly introduced a critical vulnerability into Windows XP [GAR 01]. If Microsoft and the US service immediately denied it (nobody wanted to see such a terrible fact being confirmed), then this situation shows us just how dangerous sub-contracting abroad can be. On this point, let us note that introducing such a flaw is very easy and can easily be taken for a programming error.
As an example (taken from a real case of an attempt to introduce a serious security glitch in the Linux core), let us consider the following (healthy) code:
If (CriticalVar == function (arguments))
{…. }
And let us change it as follows (just by deleting the single sign =):
If (CriticalVar = function(arguments))
{ …. }
A critical vulnerability has been introduced. In fact, the correct version of the tested code (operator ==), the value of the variable “CriticalVar” in relation to the value returned by the function. Changing the == symbol to = gets rid of the value of this variable for this value, thus creating a security glitch. Amongst the hundreds of thousands of lines of code, we can bet that this one will go unnoticed.
5.3.2. System interdependence
In the previous section, we saw how an infrastructure is built up of several interdependent components, which have a more or less critical role, and which are not all protected in the same way.
Today, analyses and experience show that trying to determine how many of them there are, and the dependent links between them, is an extremely complex task, if not impossible, in practice. It is necessary to construct a cartographic design, the most accurate as possible, of the interdependence of these different elements.
Let us now define more accurately the concept of system interdependence in our context. It describes all the direct and indirect dependencies between a target (final aim) and one or several components (primary aim) that this target depends on. The main tool is the dependence matrix8.
This matrix is established during the intelligence stage (see section 5.4). Processing it makes it possible to identify and to chart all the dependencies and interdependencies within a complex infrastructure, particularly those which are invisible or difficult to see.
From the attacker’s point of view, this makes it possible to identify a chain of dependence between the target and a sub-set of components. It will then be enough to attack the most external component, which is generally the least secure, and to play on the domino effect.
How can we define this matrix?
Let C0 be the aimed target and a sub-set of components C1, C2, C3…, Ci… These are physical and human elements, and services gravitating around the target.
Each entry Mi,j of the matrix M is defined by the matrix Mi,j which is worth 1 if the component j depends on the component i, and is worth 0 otherwise.
If the binary factors are more intuitive, it is nevertheless possible to consider whole factors, or even real factors (weighting of the dependences), but this goes beyond the limits of this chapter (for more detail, see [PRI 94]).
In order to identify a chain of dependence between the target C0 and any other dependence of length k, then it is enough to calculate the k-th power of the matrix.
Let us take the first simple and didactic example for low dependence: the matrix is said to be hollow (Figure 5.3, left). Let us find a dependence with a rating of 5. It is sufficient to take the 5th power of this matrix (Figure 5.3, right).
Figure 5.3. Dependence matrices (left) and chain of dependence matrix to the power of 5 (right) in the simplest (sparse) case

We can see here that such a chain exists between component 5 and the target. Therefore, it would be enough to strike component 5 in order to trigger a domino effect and to reach the final target.
If we consider a real case where the dependences are richer (heavy matrix, Figure 5.4), then we also see that there are 93 chains of dependence between component 5 and the target.
Figure 5.4. Dependence matrix and chain of dependence matrix to the 5th order (right) in a real example

This case is interesting because, on the one hand, there is a high number of “maneuver option switching” for the attacker, which is an advantage during the stages of planning and conduct (richness of the maneuver means more possibilities to adapt the attack to the actions/reactions of the target).
On the other hand, this means (from the point of view of the target defender) that the complexity of the dependence cartography is such that it cannot envisage and manage all of them.
A recent example9 of this domino effect was given at the beginning of 2009 during global infection by the Win32.Conficker worm. This attack struck the French Defense and the British Marines hard. On January 15th and 16th 2009 [BSD 09], Rafale fighter planes from the French air force were “nailed to the ground”. The attack had not aimed for the on-board computer system (it is hyper protected), but the air system control which, using Windows, was attacked and put out of service. It never released the flight settings, however10. The dependence on the systems did the rest. But this is an exceptional case and remains limited, because it was a direct dependence and therefore easily identifiable – at least we might think it is, above all it is limited to a purely technical frame.
It is precisely here that computer security still maintains a too restricted vision of the reality of the systems it is supposed to protect. Only considering the technical aspect, when identifying a system’s dependences, can be deceptive. We often notice such a phenomenon when using FEROS11 methods or implementing others such as Ebios12. Moreover, only the immediate vicinity is generally taken into account.
Matrix formalization – which only processes a graph structure on an algebraic level via its incidence matrix – allows for very in depth analysis of the interdependences.
Looking for a chain with a given length k (by taking the k-th power of the matrix) allows us to identify a chain dependence between k components which are more or less linked directly to the target infrastructure. It is possible to understand matters in a more qualitative way by searching, for example, specific combinations of structures. Thus, searching for a vertex cover – minimum set of point on the graph, or the components to strike, making it possible to hit all the other point/components – can be extremely interesting for a sudden, devastating attack [FIL 08].
5.4. Different phases of a cyberattack
As with any coordinated military operation, there are three phases which must be considered:
– the intelligence phase;
– the planning phase and generating forces;
– the conduct phase.
It is important to note here that in no case can these phases be exclusive or independent. It is precisely for this reason that this type of operation can be reduced to a single digital aspect and requires a relatively high level of coordination. This is a complex task which is dealt with on an army rank structure, organized into offices or cells, each one responsible for a part of the operation.
5.4.1. Intelligence phase
This is the essential phase, without which any attack would be destined for failure, especially in a complex domain such as the computerized realm.
It is vital because it allows us to:
– identify the potential critical and non-critical components;
– establish the dependence matrix and to mathematically process them, then to draw an accurate precision of the target and its environment;
– provide elements for planning and conduct (using definite “maneuver option switchings” for heavy dependences).
This corresponds to the famous motto of infantry and cavalry soldiers: “nature, volume, behavior” of the enemy. Prior to this, during the initial phase, this intelligence is more strategic than during the course of action, it is more tactical, and it mainly functions as a way of supporting the maneuver and conduct. The intelligence phase is, by nature, the phase which contributes the most to the asymmetry between the target and the attacker:
– the attacker will plan his attack with a reverse temporal vision, starting with the desired effect and going towards the initial conditions and information which will allow him to carry out his plan. In other words, it is a question of organizing time to achieve a given effect. In this way, the approach is likened to that of a chess player;
– on the other hand, for the victim, the attack must seem sudden, inexplicable and without explanation. The intelligence phase – with all its deception techniques – has to think ahead of this phase, according to the general principle.
In the digital domain, contrary to generally accepted ideas, getting this intelligence is particularly easy, for two reasons which we will discuss now.
First of all, technically all the systems we use (systems of exploitation, materials, networks, etc.) leave behind a number of relatively exploitable tracks and hidden information, and which practically nobody – except for a few specialists in the forensics field – is truly aware of.
Secondly, on the human and sociological front, the digital field (because it is perceived of as a world apart, with no perceptible connection to the physical world) does not evoke a feeling of mistrust on behalf of those who use it. It is only a technique, and speaking about it openly will not cause serious consequences.
This is forgetting that intelligence is essentially very meticulous work, consisting of collating many pieces of meaningless information and to fusing them together with the aim of discovering closed information, or even information revealing the secrets of defense.
Consequently, this gives the attacker many different types of intelligence and, thus, sources. In each case, it is a matter of acquiring a precise image and all aspects of the target which is both static (“nature, volume”) and dynamic (“attitude”).
5.4.1.1. Technical intelligence
This is very easy to acquire, for the little that we know about where and how to look for it. The possibilities are virtually endless. Between used hard disks taken from the target’s vicinity13, laptops or other mass storage hardware left unwatched in a hotel room (notably abroad), mobile computing devices detained by customs over several hours (systematic in Israel, frequent in USA, to just name two countries), the attacker is spoilt for choice.
But the simplest is to exploit metadata which literally infests most document formats: PDF files, MS Word documents, images, audio files, etc., the range is huge.
This metadata is information on the system, the user, his environment, etc., which is concealed in these files, with the user being completely unaware of it. This metadata, which is essentially passive, may be active in some cases [CHA 03] and transform into real data vacuums.
To illustrate this fact, let us consider two examples taken from real causes, out of many others studied by the author.
The first involves the fake report14 drawn up by the British and presented by General Colin Powell before the United Nations, in order to try to legitimize the 3rd Gulf War, christened Iraqi Freedom.
This report, initially published in Word format, allowed the discovery, other than the clear manipulation of the British, of a certain amount of critical data, not only in the context of the time but in the absolute.
Figure 5.5. Analysis of the British “report” on weapons of mass destruction. The circled section indicates the MAC address of a computer in Tony Blair’s entourage

This document made it possible to locate:
– the MAC address of a computer in 10 Downing Street (ex-Prime Minister Tony Blair’s headquarters). The MAC address is unique data meaning that the computer’s network card can be specifically identified;
– the complete history of the document with names, affiliations with the “real” different writers of this document. In particular, the first author of this document was simply identified as being Peter Hamill from CICR 22, Tony Blair’s internal communication service.
Another more ordinary example, it seems, deals with image formats containing metadata in EXIF format. They contain a large amount of information which, this time, concerns the user and his private life, rather than his computerized, technical environment (Figure 5.6).
Figure 5.6. GPS coordinates in the EXIF metadata from an image

Amongst this data, we find the following to be critical:
– the data and time of the photo;
– the GPS coordinates of the photo location (since 2008, several cameras have been integrated with this data).
Let us imagine now the photo of a person symbolizing an interesting target (system administrator, decision-maker, union leader, etc.) which he/she has posted on a site (Facebook, for instance). Analyzing this photo will enable us to locate, for example, the place where this person lives, if the photo is taken in their immediate environment
Finally, and still to illustrate above all the ease of collecting technical information, let us finish by analyzing public market offers, in an example where the State is the target.
In 2005 a shrewd journalist showed [MAN 05] how such an analysis had made it possible to determine what the latest equipment/exploitation systems were, from one of the most sensitive units of the French army, the 785th electronic warfare company. The French article is shown in Figure 5.7.
Figure 5.7. “Why is the 785th electronic warfare company using Microsoft/Office?” Public market offer analysis (785th electronic warfare company)

Through concerns of transparency, the French State is making a high number of technical or peri-technical information available. Once it has been written, compared and cross-checked, it is completed with a relatively accurate image of the target.
With regard to organizations and companies, checking information is just as easy (professional open sources, chambers of commerce, account publications, etc.).
5.4.1.2. Human intelligence
This type of intelligence is even easier to obtain, as our organizations have forgotten the basic rules of professional discretion and have lost the culture of security. The other reason stems from the fact that we are living in an culture which does not consider the opening and sharing of information.
In a professional context, this is controlled by the desire to convince a client, to give him/her an image and, finally, to go away with a contract or the markets. Finally, the evolution of different mentalities means that modern organization probably no longer want to complicate their lives and have stopped asking questions. The attacker will exploit all of this. A simple piece of “soft” intelligence is often sufficient to collect a lot of information.
It would be laborious to list all cases (it is never possible to be exhaustive). Let us be limited to just a few cases, all taken from real situations:
– The analysis of blogs and other social networks (Facebook, Twitter, Flickr, Linkedln, etc.) can reveal a terrifying situation. Between the senior officer explaining all our past, present and future activities through the menu (external operations, for instance); the engineer working for the defense industry talking about the project he is working on; the union leader exposing the internal problems within that business; the smallest executive exposing everything happening in his job and this, with plenty of details which make him the guilty party, the minimum of reaching a professional secret; etc. The examples are legion, and with an exasperating ease enable us to draw up a faithful image, both technical as much as human, of the next target very quickly (or of a component that the target depends on).
– The people who are guilty of deliberately leaking information act as much out of permissiveness as through a lack of knowledge of intelligence methods. From this point of view, the explosion of social networks is a golden opportunity for the attackers, but a source of calamity for the targets. Several tools make the search automatic, along with the extraction and multi-criteria processing of these forums and other networks. A tool such as Maltego15 may act as a true cartography of relations and links between people, according to one or several criteria.
– The use of public places (function rooms, transport, restaurants, etc.) is also just as profitable. A simple discussion between different members of staff in a target-company is enough to give a clear image of it. As an example, let us consider the following real case, which is no less different, which our author was a direct witness to. During the journey from Rennes to Paris in a TVG (French high speed train), three engineers from a sensitive administration were discussing trivial matters which very quickly took a turn towards the professional domain. In a two hour journey, it was possible to:
- determine which organization they were dependent on (seats for a soccer game at Rennes stadium had been sold by their company committee);
- learn what projects they were currently working on (including technical details such as the identification of those in charge, the clients, short and mid-term evolutions, the next meetings);
- obtain details on the personalities of some of their co-workers and people in the hierarchy, making it possible to get an exact idea of the nature of the relationships between them;
- get information on the computer environment through an observation of the Windows program on one of the engineer’s laptops (what version of the system was being used, what security software was being used, and what applications were being used, etc.).
In sum, the mass of information collected had made it possible, probably, to at least perform a computer intrusion using telephone theft identify techniques (social engineering [COS 09])16.
Figure 5.8. Analysis of social networks with Maltego and information retrieval

5.4.2. Planning phase
The objective consists of:
– predicting the general maneuver;
– generating the necessary forces (which includes those responsible for leading computer attacks);
– coordinating the different attacks on the “terrain” (conventional or computerized);
– incorporating the intelligence (afterwards) and conduct phases of the maneuver (before phase) in order to anticipate and to manage best as possible the unpredicted (target reactions, changes in the environment, etc.) and to allow the choice for the best “maneuver option switching” and the best available options.
From this point of view, this planning work corresponds, in a complex military operation, to the B5 army staff office17. The strictly cyberattack part, in this context, is built-in to the general maneuver within the framework of the desired global effect.
In other words, we could foresee this planning phase by using the Black Info Ops version [OTA 08].
5.4.3. Conduct phase
This is indeed the operational part. Each element of the attack (conventional, human, computerized) is not part of an isolated framework but is, in fact, in support of or in the preparation of another action, conforming to what has been planned. It is not only important to respect a strict timing, but also to cast out any form of improvisation on the terrain.
This conduct phase itself generates intelligence (intelligence in action) either willingly (first step of reconnaissance function, observation probes), or indirectly by using the outcomes of one or many specific actions (target’s reaction, gained effects, etc.). Whether this is for the planning phase or the conduct phase, the reader will notice that there is no specific mention of the strictly computerized part. This underlines the fact that this is only one element in the general maneuver. As for any conventional force, a cyberattack will rely on:
– support forces. A DDoS will be similar to artillery bombing when a Denial of Service aimed at a server can be compared to the work of a combatant soldier. We could easily identify many other examples in order to establish correspondences with the transportation corps or transmissions;
– mixed forces (digital infantry, digital cavalry).
However, the cyberattack aspect is distinguished from others because it can and must apply methods which are inherent to it, and first of all, the partition principle which aims to:
– ensure that the attacker remains anonymous, either directly by deleting all traces leading back to him, or indirectly by laying false tracks so as to incriminate a third party as being the author of the attack;
– more generally, deleting any coherent vision and the entire target in order to annihilate any capacity for reaction and counter-offensive.
The wrongful incrimination of innocent third parties is a particularly interesting approach which must be favored so as to distort the victim’s vision and for the attacker to lead in a “non-dangerous direction”.
This is quite easy to carry out, and the basic principle is to create false tracks which must – as in the classic principles of intelligence and misinformation – be coherent with reality and the operational context (see the fictional scenario presented in section 5.6).
5.5. A few “elementary building blocks”
We will now endeavor to show the “building blocks” of existing computer attacks. We just need to have a coordinated vision in order to combine them in a wide scale attack by exploiting the methodology described previously.
Reading the publication by Qiao and Wang [LAN 02] from this point of view is fundamental. Studying it shows this exact coordinated line of thinking and the strategic and tactical framework of what constitutes a high amplitude computer attack, particularly as a precursor to more conventional operations/conflicts.
These foundation blocks are essentially used to demonstrate the technical feasibility of computer attacks: the problem is no longer a matter of knowing whether it is possible, but rather knowing when it will happen.
5.5.1. General tactical framework
A high magnitude systematic cyberattack on national or regional infrastructures can be set out into three main phases. The references for the principles used here are available in [BRU 09]:
– the first phase aims to disorganize, or even stop transport networks: rail networks, air controls, signaling, roads, communication channels, etc. In a more localized way, this includes area controls (starting a riot, for instance). There are three desired effects: trigger a social panic which cannot be managed by the authorities, limit its capacity to react and its mobility, and support other actions (computerized and/or conventional). The attacks on these types of infrastructures or services are in abundance: interference in the Los Angeles signaling network in January 2007, blocking rail traffic in 23 states in the south of the USA in August 2003 (via a virus striking the signaling system), paralysis of the Boston air control in March 1998 (via a computer virus which can be compared with the grounding of two French fighter planes in February 2009 [BSD 09]);
– the second phase is aimed at financial structures and those linked to the telecommunication network: stocks (Russian Stock Exchange in February 2006, all quotations frozen for an hour, alert systems on for the London stock exchange in June 2007 for 48 hours, European CO2 emission recordings in February 2010 with markets frozen for a few hours, etc.), and messaging or telephone networks (diversion of transport messaging network in Canada in May 2006). Other than cutting off the target’s capacities to react and reorganize, it strikes vital resources that the State’s internal stability and functioning relies on;
– the third phase finishes by totally disorganizing the target by cutting off or seriously disorganizing the distribution of basic human services and resources for the State’s inhabitants: the electric network (SCADA attacks in the USA revealed by the SANS Institute, January 2008), the network for distributing drinking water (attack in October 2008 in Harrisburg, USA), the nuclear industry (Slammer worm in the nuclear plant computer network in Besse-Davies, Ohio, USA), hospital structures (attack on a hospital18 in 2006 in Seattle, USA).
The resultant social panic19 and disorder monopolizes and puts a strain on the target’s capacities to act, and in the mean time it removes all the resources necessary for its own action and survival.
In the end, everything which is managed and/or depends on information and communication systems falls. In fact (even if this is still a fictional scenario) this affects virtually all sectors, giving a maximum effect on a State’s governmental functions, except if it has been able to anticipate such a situation by keeping independent resources which are exclusively intended to be used for these functions, and by ensuring the integrity of the operational availability (and its capacity) of the decision-making chain. The domino effect must be exploited by the attacker to the maximum. It would be sufficient (see section 5.3.2 with the vertex-cover problem [FIL 08]) to strike a restricted number of secondary targets, which would make it possible to hit a maximum number of final targets. The question that immediately comes to mind concerns the apparent ease which seems to stem from what has just been presented here – even if it is still, once again, a prospective vision. Why have these cyberattacks not already happened? Is this really the case?
Faced with the complexity of an attack such as the Conficker worm and its impact, it is very difficult to imagine, as had already been the case with Blaster in 2003, that this does not involve the minimum amount of repetitions or making marks for a more systematic attack. Secondly, when such an attack really takes place and the effect of the surprise has passed (as was the case for the Estonia crisis), then intelligence will be drawn from it and an understanding will dawn on the victims. A cyberattack is, then, a single-strike weapon.
Finally this mainly stems from the fact (from the author’s point of view) that a single cyberattack, outside a wider operational framework (military and tactical, political and strategic) is precisely something which cannot be considered. Therefore cyberwar does not fully exist on its own, but constitutes an additional dimension in conflict (particular before phases). These isolated attacks can be put into a system and coordinated to have a real devastating effect. A general scenario would consist of accumulating the effects by coordinating different blocks during the planning phase. The imagination and tactical creativeness do the rest. Once again, it is important to remember that the single technical vision (hackers, pirates) is insufficient if it does not take place within a true strategic and tactical mindset.
5.5.2. Attacks on people
Attacks on people aim to put any person with a vital role in management (particularly crisis management) out of operation for a somewhat long period of time in a critical infrastructure.
This aspect is systematically ignored in security policies. Moreover, these attacks are extremely simple to carry out. All we need is either the home computer system (which is never protected to the same level as the target where the future victim is working) or by mobile computer systems (cell phones, smart phone, pocket PC, etc.).
We can easily understand that, in these conditions, the notion of a bunker still remains fanciful, and that the boundary of the security target is at the very least fuzzy and unstable.
Let us use two examples, taken from real facts:
– The first example deals with an attack on the domestic computer belonging to the union leader of a large company (for example, by dropping compromising data). The choice of such a person is a well-thought out decision. This is due to the fact that the sensitivity of opinions with regard to the union, essentially, and the capacity to react and manage through employer or public power are limited. This is followed by anonymous denunciations, and the press is warned; this can lead to a climate where company strikes can be triggered. A second offensive consists of having new data which incriminates the company’s management system, thus aggravating the strike even further and grinding the factory to an entire halt. If this (see section 5.6) is an element that the final target depends on, then the domino effect – due to the operational dependencies between them – will do the rest.
– The second example concerns a coordinated attack on a small innovative company to liquidize it or re-buy it. This company will play a key role in a vaster, delicate program, part of a bigger plan in which is it only a component, an essential one of course, but not exactly a critical one. The attacker is, for instance, an international consortium abroad. In this type of approach, the attack is far ahead of the desired effect. First of all, the decision-maker’s computers and engineers are attacked. Data accrediting the use of industrial counterfeiting, and pirating are concealed in these computers20. A civil complaint is made against this start-up for counterfeiting. Searches and preliminary instructions, based on false proof, conclude by accepting the complaint. Investigating the main people in charge, and then a loss of trust in financial backers will follow on from this. In the end, a long legal procedure (that the consortium can allow, financially) will lead to the startup assessment.
5.5.3. Opinion manipulation and area control
Another type of approach may aim at opinions, through a few clicks of the mouse (and by combining the approaches presented in section 5.5.2) in order to achieve diverse effects. Moreover, the weighting of the opinion is a vital aspect, even explosive, which may, in itself, complicate police force tasks. Here we will use the example of an area control (physical effect) which may be used as a support for a future conventional attack. We are inspired by real events occurring at the end of 2008 in suburbs which are usually very susceptible areas.
In this case, let us imagine that the attacker wants to paralyze a given zone, by starting up riots or confrontations (blocking communication channels or areas). Firstly, videos of a highly racist, community-based and violent nature are posted on very popular sites (such as France’s dailymotion, similar to YouTube), whose character is particularly insulting and offensive for a section of the population living in this sensitive area (see Figure 5.9). These videos received other videos as a response, heightening the tension during aggravation via interfering videograms (some coming from the real attacker to make the tension rise). Using classic intrusion techniques on computers belonging to the gang members (see previous section), and spreading rumors or facts on blogs etc., all contributed to the hornet’s nest21, kicking off riots and confrontations. Public power, taken as a hostage, only has a limited means of reaction. The concomitant exploitation of international, critical news also helped to facilitate this scenario (see Figure 5.10).
Figure 5.9. Videos posted in 2008 on France’s site “dailymotion” to exacerbate hatred between rival gangs, one of which was said to be Muslim (Vince versus Morsay). The video titles include offensive and vulgar language of a sexual nature

Figure 5.10. Exploiting the news to provoke riots: “child decapitated by Israel” (top), “Gaza, Arab leaders are Zionists” (bottom)

5.5.4. Military computer attack in a conventional operation
To show how a computer attack may also be led alongside a bigger conventional attack, we will consider the air raid from Israeli planes in October 2007 on Syrian plants suspected of harboring a nuclear plant for military means.
To monitor their air space, the Syrians had bought a system to digitalize this space from the Russians. This system has a certain number of ground receivers, linked to a computer center. In order to protect their planes from the Syrian anti-aircraft defense, Israeli soldiers infiltrated this computer network, directed some of the receivers so as to create a blind corridor that their planes could go through for their mission, without fear of danger [FIL 09a]
In this example: on the other hand, using a foreign critical military system was a major weak point. On the other hand, for the Israelis, without a preconditioned support by a purely computerized attack, then this conventional operation would have been impossible.
5.6. Example scenario
In this chapter we will firmly illustrate the subject and methodology by a fictional scenario. We will show how a military operation can be countered by cyberattacks.
We want to show that, in the end, a cyberattack is especially the best combination of InfoOps (Information operations) such as those formalized by NATO [OTA 08], and classic computer attacks…and a total lack of ethics.
To illustrate this vision, we will give a detailed tactical scenario22 where all the elements, all the data, all the events, etc., are mostly inspired by recent events and solid cases, which are clearly limited. For clear ethical reasons, we will not discuss the real operational mode of the techniques and means used by the attackers who will be put on our stage in the following section. This will not hinder the general understanding. We will firstly present the tactics, then the apparent succession of the operations. Next, we will explain what actually happened and why. The reader will be able to find a similar scenario of a political attack in [FIL 09b].
5.6.1. Tactical scenario
5.6.1.1. General situation
September 20th, 2009. A conflict has broken out between two Mediterranean countries: on the one hand, we have the GREEN country, dominated by a fundamentalist faction which is widely supported by the population, and partly by national forces. On the other, the national forces of a bordering RED country which started the conflict as a result of repeated raids by fundamental GREEN militia. The population of the GREEN country is made up of a high fraction of foreign nationals from a BLUE country, also located in the Mediterranean.
Officially, the BLUE country is an ally with the GREEN and RED countries, but does not want to be politically involved for the moment, when its foreign nationals are at risk. There is a great fear that each belligerent section will use, for political or military means (hostage taking, civilians being killed, etc.), the existence of these nationals as a way of pressuring their country.
Faced with the worrying situation in terms of safety on the land (several bombings), an operation to remove the nationals was decided on by the political power in a state of emergency (less than 12 hours after the events started). The official statement from the BLUE government’s spokes person is published on September 22nd 2009. After 9 hours, the BLUE country sends in a vessel from its fleet, a VPC/LCT23 type, with a few members from its special forces on board, an infantry unit (220 men) and 5 transport troop helicopters.
The BLUE National Marines has 48 hours to be put into place (latest departure, September 24th at 09:00). The vessel must go to the GREEN country’s main port. The UN’s Security Council, NATO’s Commander and the European Council have authorized the BLUE country’s intervention, and condemn any use of force on the BLUE country’s military detachment, exposing countries guilty of economic and diplomatic sanctions. Officially, the two belligerents accept this mission to remove nationals on the basis of the proposed schedule.
In truth, analyzes show that the GREEN country’s objective was to prevent the nationals being sent home, who could be used either as an implicit human shield (dissuade or at least delay this process), or on the other hand, for the BLUE country to lead a military intervention (nationals become victims of the RED forces). The aim of the RED country is also to delay the BLUE country’s intervention, which is suspected of also covering an intelligence operation, partly to the benefit of the GREEN country. The BLUE country is an old colonial power in the region, and moreover, has kept its capacities to influence and its interests in this region of the world.
In summary, for both countries, a delay of 96 hours for the BLUE vessel is considered as a success. Each party must make others believe in the other’s action, and not be incriminated. The ideal situation would be to ensure that the BLUE country is incapable of launching such an operation, which would demonstrate the vanity of its claims to intervene in the region.
5.6.1.2. Environment and INT situation24
The BLUE country has a very high diaspora from the two belligerent parties. The BLUE country is a democratic state where individual, union, and religious freedom is a sensitive societal aspect. The country is in its electoral period (renewing the Lower House).
The GREEN and RED countries officially (on the diplomatic front) approve of the operation to remove nationals. The GREEN country condemns it internally and informs its allies.
The GREEN’s propaganda extends to the communities present in the BLUE country. The GREEN and RED countries have a high capacity in the CNO (computer network operation) domain:
– in the GREEN country or its allies, several organized pirate groups (malevolent hackers), and e-terrorist groups connected with world-known terrorist groups actively work to benefit the GREEN fundamentalist faction;
– in the RED country, state-governed structures, controlling hacker groups from time to time, are known to have a high activity involved in computer attacks; moreover, intelligence reports have established that the RED country manipulates certain hacker groups from the GREEN country.
The two belligerents have strong INT capacities.
Furthermore, intelligence reports from the BLUE country show that certain member states from the UN’s Security Council secretly support one or the other of the two sides to counter the influence of the BLUE country in the area.
These countries have a high activity in the intelligence domain and in CNO type operations. The BLUE telephone operator, historical and the majority operator, has relocated its main call center into the GREEN country, along with a large portion of its telephonically supervised network, in particular managing the telegraphic network of the BLUE capital.
Several years ago, the BLUE country relocated its software production and data processing into the RED country (countable data, directories, data centers, etc.).
5.6.1.3. Geographical situation
The BLUE country has two military ports. Only the port in the SOUTH of Riencourt25 may be used as a departure port, with the port in the NORTH of Chouest being too far away. Only a single road gives access to the Riencourt port, where the city is in between the sea and a mountain range. At 3 km from the port, the road passes through an important industrial zone.
In the GREEN country, the BLUE nationals (2,000) are mostly gathered in the city housing the main port. Around 150 BLUE nationals and their families are in the main city in the SOUTH, 250 km from the port.
The distance between the port/SOUTH city can be made by using a single road in the partially mountainous area, and is controlled by the RED forces. The RED country has control over the skies, outside a half of the country’s South-West region, where forces can move freely. Using transport helicopters was judged by the BLUE country as being the only possible solution.
Figure 5.11. Geographical situation of the RED, GREEN and BLUE countries

5.6.2. The order of events
5.6.2.1. Phase 1: before September 22nd
September 21st, a serious strike has begun in the Oils SOUTH company, located in the industrial zone of the Riencourt port. The company’s official documents were sent on the 18th to a daily newspaper, which triggered a massive plan for dismissal, motivated by heavy losses in the organization caused by, according to these documents, embezzlement on behalf of the factory manager. On the 21st, an investigation by the financial authorities into the company’s computers confirms the truth inside these documents. The factory comes to a halt.
On September 22nd, confrontations between gangs get worse in the North region of Riencourt. This is a relatively frequent occurrence in these districts. Cars go up in flames, several people have knife wounds and an explosive situation monopolizes the police force’s attention. The origin of these confrontations seems to stem from the threats and insults of a community and racial nature, in particular posted on sites such as YouTube and Dailymotion26. Tensions gradually rise but the powers that be, in this electoral period, want to manage the crisis carefully.
5.6.2.2. Phase 2: from September 22nd to the 24th
Following the new videos on the 23rd, new confrontations arise in the Northern districts of Riencourt, leaving two deaths in their wake by firearms. The situation is getting worse, and the police force intervenes. The situation is blocked: demonstrations are taking place in the city of Riencourt in memory of the victims. The authorities are beginning to fear that the violence could increase.
On the 23rd at 06:00, a new investigation into the Oils SOUTH organization takes place, upon request by the court’s finance sector and the Vice Quad, as well as at the main Union leader’s home, who was taken into police custody and his computer seized. Indiscretions in the press show an aggravated matter for the Vice Quad. The trade-union denounces an attempt to break the strike and decides to strengthen it.
The 24th, at 06:00, in the city of Choucoulis, a 28 year-old soldier is arrested and investigated for serious matters. He is caught out through an analysis of his computer and his cell phone.
5.6.2.3. Phase 3: from September 24th to the 28th
On the 25th, following new revelations published in the press which gives a report on the prolonged custody of the union leader, the strike movement becomes even more serious. The trade-union, the majority in the region, manages to convince other factories in the industrial zone to join their movement. On the 26th, picket lines are drawn up, blocking off the single road giving access the military port.
Between the 24th and the 27th, frequent breakdowns in the telephone network affect certain regions, including the capital and large cities. These disturbances intermittently involve the mobile telephone network and Internet communications. Several journalists speak of a computer worm attack. The operator speaks of a breakdown in some of the network’s hardware, which is being replaced.
On the 27th at midday, several BLUE nationals, many of whom are women and children, are victims of RED bombings. The BLUE beliefs are unsettled. On the 28th September, the BLUE National Marine vessel comes in with a 99 hour delay. The government’s spokes person attempts to talk down this delay by speaking about logistic problems. The opposition bears witness to this opinion. The government accuses the unions of anti-patriotic behavior.
5.6.3. Analysis
Before presenting what actually happened, it is important to remember that in any conflict, the side(s) which start it have a depth in time that the other players do not have. Any operational planning foresees all the possible options for the opposite forces, by weighing them up against the time factor.
In the case of our tactical scenario, the operation to remove nationals by the BLUE country was easy to predict, and the INT analysts from the GREEN and RED country were able to anticipate this decision beforehand, and to include it in the tactical and strategic preparation, and then in their conduct and respective maneuver. Thus, such an analysis led these experts to reassure their operational leaders by saying that the BLUE vessel could only go from the port at Riencourt, as the VPC/LCT vessels were only available in this port. It is easy to study and identify the zones with local weaknesses from this, in order to act on an operational front.
This explains how the operations on the BLUE country had really started several days before the official date of the conflict and the country’s political decision. It does not matter who started the conflict, the GREEN or the RED country. What matters is the nature and the conduct of the operations: uniquely through computer attacks, leaving no traces, leaving the analysts all the time in the world to endlessly go over and over the real responsibilities.
Figure 5.12. Situation on the terrain at the port of Riencourt

An initial computer attack strikes against the Oils SOUTH company on September 18th: fake documents, imitated from information processed offshore, were planted into the general director’s computer. Then, later, they were put in the main union delegate’s computer. Next, these documents just needed to reach the press, with a good timing which was compatible with the conduct of other operations. The Oils SOUTH organization provides the BLUE marines with specific vessel oil (public market study). Extra information (indiscretions on engineer’s and marine officer’s blogs, etc.) made it possible to assume that the BLUE Marines oil stocks were lower, and that the delivery was meant to come in as soon as the extra budget for the BLUE country’s defense had been agreed at the beginning of October. Other indiscretions led us to determine that the BLUE country’s Marines were short of parts for helicopters and that the delivery was meant to arrive at the end of September.
The parts in question are made by the HeliMeca group, located at the entrance of the Riencourt industrial zone. By starting this strike, the aim was to:
– block the emergency oil supplies (Oils SOUTH factory coming to a halt);
– block the access road to the military port (no access for HeliMeca trucks, for the sailors and the supplies on board and equipment);
– block the HeliMeca group’s activity by extension in the long term, and reinforce the strike.
The second “attack” concerns the posting of provocative videos on two sites regularly visited by young people to exacerbate their rival groups and start riots. The idea, according to the classic covering principle, is to trigger a second zone for the police forces to attend to, and to deflect attention from social problems from the Riencourt industrial port zone.
Faced with these problems, the BLUE country’s power tries to organize itself. This involves an increase in the communication needs between the different decision-making centers. The third attack aims to considerably obstruct these communications and to extend the times for decision making. Knowing the architecture of the national telephone network has made it possible to see that the R&D network is connected to the computer network exploitation.
A virus attack aimed at personal computers belonging to the many engineers and researchers of this operator (intelligence collection through blogs, social networks, etc.), enabled them to attack the network owing to the direct connection of their laptop on their internal network.
Finally, the soldier arrested on the 24th was no other than the Commander of the unit who was supposed to embark on the VPC/LCT with his brigade. A blog written by one of his warrant officers27 revealed that on the 23rd, his brigade was on the vessel in question.
The attack was achieved in two phases: planting compromising data on the personal computer belonging to this officer and manipulating his cell phone (a model with a vital vulnerability) to further incriminate him with regard to the accusations. Arresting this officer involved, for internal reasons, having to find another brigade, starting off new delays.
In the end, the vessel, adding up more delays, could only come in 99 hours later.
5.7. Conclusion
The different aspects with regard to planning and conduct of cyberattacks allow us to draw out three main lessons:
– the technical vision alone is not enough, if it is not expressed in a coordinated and operational vision. This implies that behind the hacker or pirate, we must always look for the purpose and the mind behind it all, which reflects the classic and timeless principles of warfare;
– the final target must only be considered in a complex, fuzzy and moving environment. Considering this target as an unassailable bunker is simply fanciful. Knowing this environment perfectly guarantees the attacker the best action possible. The defender’s lack of knowledge makes him extremely weak. Experience shows that, except in cases of very sophisticated, targeted attacks, it is more the victim’s weakness rather than the attacker’s real force which is decisive;
– the total and unrestricted exploitation of the human element is the key for any successful attack. Exploiting and revisiting the InfoOps potential and classic human intelligence techniques is therefore essential, as much for the attacker as for he who wants to be protected himself.
In this context, how can we consider a policy for defense and security? Is it possible to protect ourselves easily? The answer is clearly no, particularly with regard to the facility of doing so, so long as we admit and accept our dependence on information and communication systems to be inescapable and impossible to overcome. This is precisely the difference between the Estonian scenario and the case in Georgia. Where Estonia is weak, Georgia, whose computer infrastructure is somewhat non-existent, really had nothing to fear from these so-called Russian attacks, contrary to what might have been suggested in an objectively anti-Russian capacity to resist when we use uncontrolled means: exploitation systems, security software, cryptological concepts, etc. From this point of view, any solution must go through a necessary economical revolution which must:
– relocate important companies, particularly in all industries connected to governmental functions;
– relocate critical sources (data centers, supervision services, critical resource manufacturers, etc.).
In no way is it a question of creating a new Maginot line but of having a reasoned vision of our own desire for security. Since 1994, the USA (champions of free competition when it concerns countries other than itself) relocated and renationalized everything which affects the defense heritage and governmental functions (President Ronald Reegan’s Union discourse). An interesting parallel to make is with the fall of the Roman Empire: it coincided with the instant when the Roman armies were recruiting mainly from the Empire’s population, and no longer from Rome’s strong forces. Sub-contracting security needs is the worst solution. Security must go through digital sovereignty!
A cultural revolution must also be led. This is probably the hardest thing to do. It is necessary to create a true security culture and professional discretion, which is a priority for decision-makers. This is another important point concerning a form of technological hegemony. There is too small a number of people who have understood that the problem begins much earlier: it is not so much the products but the concepts and norms which are important. As Bernard Carayon28 quite right recalls: “the power of a country lies in its ability to impose standards and norms”. Managing to impose a unique and controlled vision is a fearsome way of influencing and having power over mindsets.
5.8. Bibliography
[ALM 08] AL-MADHOUN O., Islamic Jihad’s Cyber War Brigades, www.menassat.com/ ?q=en/news-articles/3966-islamic-jihad-s-cyber-war-brigades, July 17th 2008.
[BAN 06] BANGARÉ H., Maroc-Israël: la Webtifada est lancée. www.afrik.com/article 10160.html, July 27th 2006.
[BEN 05] BENICHOU D., LEFRANC S., “Introduction to network self-defense: technical and judicial issues”, Journal in Computer Virology, vol. 1, no. 1-2, Springer Verlag, New York, USA, 2005.
[BSD 09] BLOG SECRET DEFENSE, Les armées attaquées par un virus informatique, secretdefense.blogs.liberation.fr/defense/2009/02/les-armes-attaq.html, February 5th 2009.
[CHA 03] CHAMBET P., DETOISIEN E., FILIOL E., “La fuite d’informations dans les documents propriétaires”, MISC - Le Journal de la sécurité informatique, no. 7, May 2003.
[CON 09] CONHEADY S, Social Engineering for Penetration Testers, Brucon conference www.brucon.org/articles/p/r/e/Presentations.html#Social_engineering_for_penetration_testers, Brussels, October 2009.
[DUN 06] DUNN J., DETOISIEN E., US Military Struggles with Data Loss, Techworld, features.techworld.com/security/2436/us-military-struggles-with-data-loss, April 2006.
[EUR 06] EUROPEAN PARLIAMENT, Fight against terrorism: identification, designation and protection of European critical infrastructures ECI, Procedure File CNS/2006/0276, www.europarl.europa.eu/oeil/file.jsp?id=5425462, 2006.
[EUR 10] EUROPEAN UNION LEGISLATION SUMMARIES, Critical infrastructure protection, European Union, available at: http://europa.eu/legislation_summaries/justice_freedom_ security/fight_against_terrorism/l33259_en.htm, 2010.
[FIL 06] FILIOL E., “Le ver Blaster/LovSan”, MISC, Le Journal de la sécurité informatique, no. 11, July 2004.
[FIL 08] FILIOL E., FRANC E., GUBBIOLI A., MOQUET B., ROBLOT G., “Combinatorial optimisation of worm propagation on an unknown network”, International Journal in Computer Science, vol. 2, no. 2, p. 124–131, 2008.
[FIL 09a] FILIOL E, RAYNAL F., “Cyberguerre: de l’attaque du bunker à l’attaque dans la profondeur”, Revue de défense nationale et sécurité collective, vol. 2009-3, p. 74–86, March 2009.
[FIL 09b] FILIOL E., “Operational Aspects of cyberwarfare of cyber-terrorist attacks: what a truly devastating attack could do”, 8th European Conference on Information Warfare and Security 2009, p. 71–79, Lisbon, Portugal, 6-7th July 2009.
[FIL 09c] FILIOL E., How to Prepare, Coordinate and Conduct a Cyber Attack, Brucon conference 2009, www.brucon.org, Brussels, Belgium, October 2009.
[FIL 10] FILIOL E., “Anti-forensic techniques based on malicious cryptography”, 9th European Conference in Information Warfare 201011th, Salonika, Greece, July 2010.
[FOL 09] FOLLATH E, STARK H., The Story of Operation Orchard: How Israel Destroyed Syria’s Al Kibar Nuclear Reactor, www.spiegel.de/ international/world/0,1518,658663-2,00.html, February 11th 2009.
[GAR 01] GARDINER J., Has Osama bin Laden bin Codin’ XP?, www.silicon.com/technology/hardware/2001/12/19/has-osama-bin-laden-bin-codin-xp-11030037/, December 19th 2001.
[GRE 02] GREEN J., The Myth of Cyberterrorism, www.washingtonmonthly.com/features/2001/0211.green.html, Washington Monthly, November 2002.
[LAN 02] LANG Q., XIANQSUI W., Unrestricted Warfare: China’s Master Plan to Destroy America, Pan American Publishing Company, USA, 2002.
[LBD 08] GOUVERNEMENT FRANÇAIS, Le livre blanc sur la défense et la sécurité nationale, Odile Jacob, Paris, France, 2008.
[MAN 05] MANACH J.-M., Mais pourquoi la 785e compagnie de guerre électronique utiliset’elle Microsoft/Office?, rewriting.net/2005/06/09/mais-pourquoi-la-785e-compagnie-deguerre- electronique-utilise-microsoft-office/, June 9th 2005.
[MAN 11] MANACH J.-M., “Bercy: la piste de l’altermondialisme numérique”, http://owni.fr/2011/03/07/bercy-la-piste-de-laltermondialisme-numerique/, Owni, March 7th 2011.
[MES 99] MESSNER E., Kosovo Cyber-war Intensifies: Chinese Hackers Targeting US Sites, Government Says, www.cnn.com/TECH/computing/9905/12/cyberwar.idg/, May 12th 1999.
[OTA 08] OTAN, Information Operations – Analysis Support and Capability Requirements, Research and Technology Organization, TR-SAS-057, ftp.rta.nato.int/public//PubFullText/RTO/TR/RTO-TR-SAS-057/$$TR-SAS-057-ALL.pdf.
[PAR 10] PARR B., Did Chinese Hackers Exploit Internet Explorer to Attack Google? mashable.com/2010/01/14/google-china-attack-anatomy/, January 14th 2010.
[PRI 94] PRINS C.H., Algorithmes de graphes avec programmes en Pascal, Eyrolles, Paris, France, 1994.
[VEN 07] VENTRE D., “La guerre de l’information en Russie”, no. 30, MISC, March 2007.
[VEN 09] VENTRE D., Information Warfare, ISTE Ltd, London and John Wiley & Sons, New York, 2009.
1 Chapter written by Eric FILIOL.
1 Expression adapted from Wikipedia (fr.wikipedia.org/wiki/Guerre), the rest is the author’s own.
2 We will use the definition Computer Crime Research Center, http://www.crimeresearch.org/articles/joseph06/.
3 However, let us note that it is difficult to assess the real capacity of these groups. On the other hand, it has been perfectly established that these groups have understood all the potential of the computer domain for terrorist means. The operational capacity will come with time, and our own inconsistencies regarding security management.
4 Discipline mainly dealing with unintentional threats and therefore which are predictable because they can be modeled; the code theory and reliability theory are very powerful tools in this context.
5 Let us remember that the concept of probability relates to predicting the occurrence of events. It is not possible to attach such a probability to an event which is still unidentified and undefined.
6 A Chinese proverb which says “a fish always rots from the head down!”
7 DMZ (demilitarized zone). This is the zone with all the network’s security and protection functions. A real case occured in 2004 in many large companies whose activity was blocked.
8 This mathematical formalization was developed at ESAT– (C + V)O, in the Gorgias project and the eponymous software aiming to gain techniques and a platform for analyzing the security of complex systems.
9 This type of attack had struck the US Air Force in a similar way a few months beforehand.
10 This type of problem recently occured in a brigade of Chinese tanks.
11 Feros is a document expressing security objectives.
12 Ebios is the main method for identifying and managing risks, created by the DCSSI, www.ysosecure.com/methode-securite/methode-ebios.asp.
13 On many occasions, the author has personally had the chance to check the second-hand market, the sales in certain domains, garbage analysis, etc., which has given some unbelievable findings and the ability to collect some, sometimes, very sensitive information (see [DUN 06]).
14 “Iraq – Its infrastructure of concealment, deception and intimidation”.
15 www.paterva.com/web4/index.php/maltego.
16 In 2003, such an attack was carried out on an organization, using elements collected in a public environment. The attacker with a very high knowledge of the internal life, structure and operation of this company, was able to get an account opened on the server by pretending to be a business engineer.
17 In NATO’s nomenclature, the name is J5.
18 In February 2009, the attack by the Conficker worm caused similar damage on computer networks which the intensive care units depend on in the South of France. These cases were never made public.
19 We can get a fairly accurate idea of the kind of panic that a situation of high disorganization in the main vital services of a country could generate. It is enough to observe the irrational reactions (mass buying and storing food, looting, etc.) during less severe situations (cyclone, for example).
20 This attack, to be coherent and credible, needs to have made this “proof” pre-conditionally after an analysis of the products developed by this company.
21 A similar case occurred in Italy in 2009: following comments on blogs and rumors spread on the Internet, ethnic and urban guerilla riots took place in Rosarno (Calabre). The Italian population blamed the demonstrators and the African rioters.
22 This scenario was initially published in [FIL 09]. Here we give an alternative of it based on more recent techniques. All the places here are imaginary, and any likeness is purely coincidental.
23 Vessel Projection and Command and Landing-Craft Transport.
24 INT, military abbreviation for the “intelligence” in an operation.
25 The choice of the name Riencourt bears no relation to the two French towns with the same name (one in the Somme, one in the Northern region).
26 This is inspired by a similar, real event in France, luckily in a very localized way, in November 2008.
27 These cases are not hypothetical. With the lack of professional discretion, all the professional sectors together become a major worry for police and security forces.
28 French Member of Parliament, specialist reporter for questions of Defense at the National Assembly, during the opening conference at the SSTIC 2004, www.sstic.org.
