Study on Covert Networks of Terrorists Based on Interactive Relationship Hypothesis
Duoyong Sun, Wenju Li and Xiaopeng Liu , College of Information System & Management, National University of Defense Technology, P.R. China
Chapter Outline
8.3 Initial Network Construction
8.3.2 Network Construction of Terrorist Organization Members and Terrorist Organization Affiliation
8.3.4 Supporting Relationship Network Construction among Terrorist Organizations
8.3.5 Construction of Initial Multi-Element Network
8.4 Network Refinement Based on Interaction Relation Hypothesis
Entity and relationship missing cases
8.4.3 Interaction Relationship Hypothesis
Entity missing hypothesis based on action association
Tripartite relationship hypothesis based on the event
Spurious relationship hypothesis based on association differences
8.5.2 Final Multi-Element Network Model
8.6.1 Network Characteristics Analysis
8.6.2 Evaluation of Leading Figures
8.6.3 Important Organization Evaluation
8.1 Introduction
The events of 9/11 have made terrorism become the common enemy of people internationally. Striking against and facing up to terrorism are now global issues. Important measures have been taken by many countries as regards counter-terrorism, including understanding the terrorist organizations, breaking up terrorist organizations, and making emergency preparations. Currently, with the development of information technology and the international community’s fight against terrorism, great changes have taken place in the structure of terrorist organizations and the traditional pyramidal structure has been replaced by a network structure, which has become the most important feature of contemporary terrorist organizations [1]. Terrorist organizations can be regarded as relationship networks formed on the basis of specific beliefs. According to social network theory, any action of actors is not isolated but correlated. The relationship ties among them are transmission channels of information and resources, and the network relation structure decides their opportunities for action and results. It has become an important way to understand and break up networks of terrorist organizations by analyzing network characteristics of terrorist organizations by constructing a social network model of the terrorist organization’s members. Because of the concealment and dispersiveness of terrorist organization activities, the traditional social network modeling method is difficult to put into effect. Therefore, it is a very important task to develop new research means, construct social network models according to public information and clues of the activities of terrorist organization members, and explore the characteristics of the activities of terrorist organizations.
Public information contains telephone records, court trail records, bank transaction records, traffic violation records, boarding records, trade records, text records, mail records, Internet forum records, video records, involved event records, interactive relationship records, interrelationship records, and so on. In principle, any trace that reflects the activities of terrorist organization members can be taken as the basis for the construction of a social network model. However, we should also see that terrorist organization members usually live in a covert way and they seldom contact each other in normal time for reasons of personal safety and evading attack. Therefore, it is seen that the network of terrorist organization members has entirely different relationship characteristics from those of general interpersonal relationship networks. Due to the covert nature of the terrorist network, the terrorist organization may conceal the information positively, so a social network model established on the basis of public data information may omit some important relationships, and the result may therefore deviate from the actual situation. Hence, solving the problems of missing data is the unavoidable issue in constructing social networks of terrorist organizations.
This chapter takes text information from two groups of terrorist organization members published by the Ministry of Public Security of the People’s Republic of China in December 20031 and October 20082 as data sources3. The social network model of terrorist organization members is established by extracting the involved event records, interactive relationship records, and affiliations of personnel organizations in the public domain. The model aims to acquire missing information regarding individuals and relationships, and detect spurious relationship screening issues possibly encountered in the network model construction, and to conduct relationship deduction by introducing an interactive relationship hypothesis, perfect the network, and verify the rationality by empirical research.
The chapter is arranged as follows. Section 8.2 mainly introduces the relevant research and literature. Section 8.3 puts forward the initial network construction methods of terrorist organizations on the basis of affiliations. Section 8.4 aims to find the deficiencies in the data, discovers the basis, proposes a forward interactive relationship hypothesis, and improves the initial network. Section 8.5 refines the terrorist organization and incident relationship networks, and establishes the final relationship networks. Section 8.6 carries out the relevant network calculations, experimental analysis, and result verifications. Section 8.7 considers the conclusions and future prospects.
8.2 Relevant Works
Before the events of 9/11, many scholars attempted to use social network analysis methods to research the covert networks of terrorist organizations. In 1981, Bonnie Erickson proposed that the effective associations in a secret society depended on the trust between them [2]. For instance, whether receiving training together, living together, being close friends in a dormitory, or blood relationships might directly influence the reliability of the network relationships. In 1991, Malcolm Sparrow studied the existing problems in crime networks [3], i.e. a covert network would inevitably introduce imperfections of the node and relationship data, vagueness of network boundaries, and dynamic variability. In 1993, Baker and Faulkner found that terrorist organization networks and other covert networks were different from the normal interpersonal networks, and that their members rarely contacted each other, which constituted weak connections in models [4]. Strong connections might be the experience of receiving training or learning together several years ago. They suggested exploring the terrorist network relationship data using archive files, such as evidence of court proceedings and information provided by various witnesses. After 9/11, this field attracted much attention and gradually became a focus of research. Valdis E. Krebs constructed a terrorist organization member relationship network for 9/11 by using telephone records [5]. Aparna Basu constructed a social network structure of terrorist organizations according to records of terrorist incidents launched by 61 terrorist organizations in India between 2001 and 2003 [6]. Richard Rothenberg established an “Al-Qaeda” network structure according to newspapers and radio station information records [7]. Kathleen Carley clarified the application potential of the social network analysis and modeling method on the basis of the use of intelligent agents in breaking up the terrorist organizations [8].
Data missing from public information is a common problem in the construction of covert network models. Dombroski and colleagues paid close attention to the missing data phenomenon in the construction of social network models, and studied the construction of a covert network model under the condition of missing information [9]. José A. Rodriguez pointed out that “Incomplete connections make the terrorist organization members able to maintain the foremost relationship in the large network, providing substantial support and spiritual arousal for them” [10]. Sageman stated the importance of weak relationship contact in terrorist organization networks [1]. Jonathan Kennedy researched the weak relationship problems of the terrorists, and deemed that its importance was greater than knowing strong relationships [11]. This research laid the foundations for the hypothesis and network refinement considered in this chapter.
8.3 Initial Network Construction
The initial network mainly involves the construction of figures and incident relationship network, the construction of figures and organization relationship network, and the relationship network among figures and among organizations relevant to the terrorist organization members, with the purpose of providing the basis for finding the missing data.
8.3.1 Relationship Network Construction of Terrorist Organization Members and Terrorist Incident Participation
Analyzing the data sources, we found that 42 terrorist organization members and 28 terrorist incidents were involved by classifying the data obtained. We numbered the terrorist organization members as A01–A42, numbered terrorist incidents as E01–E28, and defined the matrix elements Zij according to whether members participated in the incidents or not. Zij = 1 indicated that member i participated in incident j, and Zij = 0 indicated that member i did not participate in incident j. Based on this definition, the relationship matrix of incident participation of terrorist organization members was established as shown in Table 8.1. See Figure 8.1 for the corresponding network topology.
Table 8.1
Relationship Matrix of Terrorist Organization Members and Terrorist Incidents
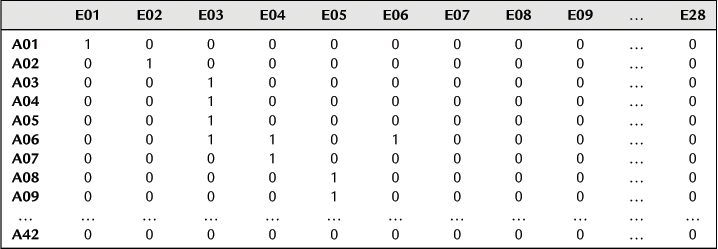

Figure 8.1 Relationship network of terrorist organization members and terrorist incidents.
8.3.2 Network Construction of Terrorist Organization Members and Terrorist Organization Affiliation
In the obtained text data, eight terrorist organizations are involved, numbered as G01–G08. We defined the matrix element Zij according to whether the members were affiliated to an organization or not. Zij = 1 indicated that member i was affiliated to organization j, and Zij = 0 indicated that member i was not affiliated to organization j. Based on this definition, the relationship matrix of terrorist organization members and organization affiliations was established as shown in Table 8.2. See Figure 8.2 for the corresponding network topology.
Table 8.2
Relationship Matrix of Terrorist Organization Members and Terrorist Organizations


Figure 8.2 Relationship network of terrorist organization members and terrorist organizations.
8.3.3 Assignment and Interactive Relationship Network Construction among Terrorist Organization Members
The assignment relationship among the terrorist organization members was largely determined by specific terms in public text information, such as dispatch, recruitment, command, and instigation. The matrix element Zij was defined according to whether the members were involved in the assignment relationship or not. Zij = 1 indicated that member i received an assignment from member j, and Zij = 0 indicated that member i did not receive an assignment from member j. The assignment relationship was unidirectional. Besides the unidirectional assignment relationship, a bidirectional interactive relationship also existed among terrorist organization members. The interactive relationship among terrorist organization members was mainly determined by terms such as deciding through consultation, discussion and reaching consensus, and was indicated as Zij = Zji = 1 in the matrix, as shown in Table 8.3. See Figure 8.3 for the corresponding network topology.
Table 8.3
Relationship Chart of Terrorist Organization Members
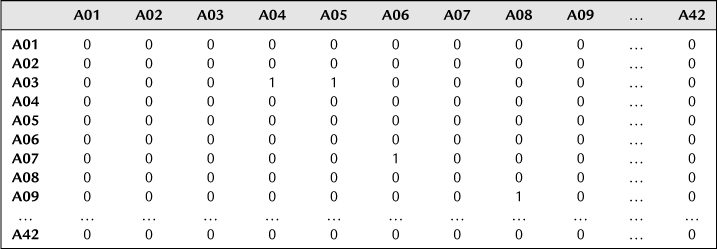
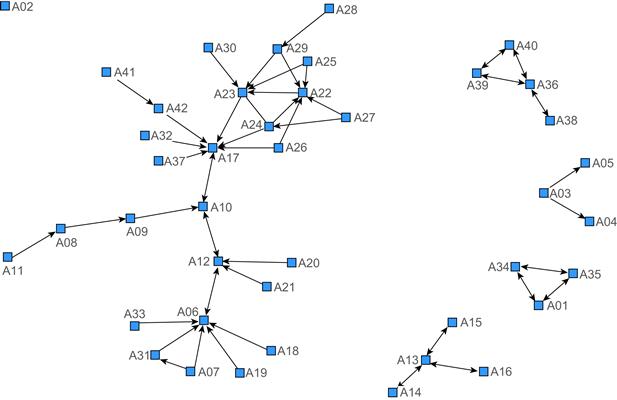
Figure 8.3 Relationship network of terrorist organization members.
The assignment and interactive relationship records in public information is actually the information about interactive relationships among terrorists in incidents released by relevant departments of the state based on facts. The relationship network of terrorist organization members established by the above is explicit and reliable, and its defects may be problems of individual deficiency and missing relationships.
8.3.4 Supporting Relationship Network Construction among Terrorist Organizations
The text data described the relationships among terrorist organizations in detail, and the supporting relationship matrix among terrorist organizations was constructed in the light of the connection and support among terrorist organizations, and the interactions among terrorist organization leaders. The element Zij = 1 in the matrix indicated that the organizations i and j had this supporting relationship, and Zij = 0 indicated that the organizations i and j did not have this supporting relationship, as shown in Table 8.4. See Figure 8.4 for the corresponding network topology.
Table 8.4
Relationship Matrix of Terrorist Organizations


Figure 8.4 Relationship network of terrorist organizations.
8.3.5 Construction of Initial Multi-Element Network
According to the above relationship matrices, the multi-element social relationship network model of terrorist organization members was established using ORA tools developed by Dr. Kathleen M. Carley of CASOS at the School of Computer Science at Carnegie Mellon University, as shown in Figure 8.5. In the figure, the round dots represent 42 terrorist organization members, the rhombus dots represent 28 terrorist incidents, and the square dots represent eight terrorist organizations. The relationships between dots are represented by the solid lines. The arrows point at the leaders, incidents and organizations, and reflect the affiliations among terrorist organization members, terrorist incidents and terrorist organizations. The bidirectional arrows indicate the interactive relationships among terrorist organization members, and supporting relationships among terrorist organizations.
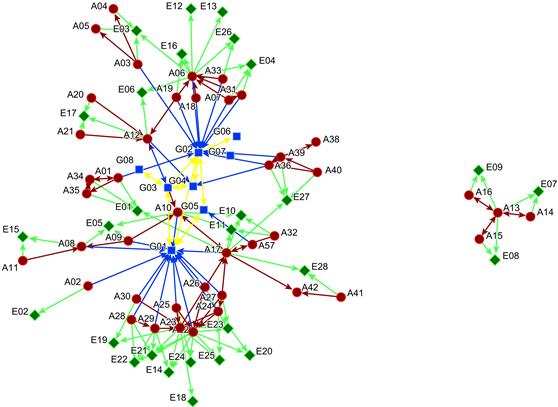
Figure 8.5 Multi-element network of terrorist organization members.
Compared with Figures 8.1 and 8.3, it can be seen that some terrorist organization members are connected by some terrorist incidents or terrorist organizations, such as A03 and A06 connected by E03. If all terrorist incidents and organizations are removed from the multi-element network of terrorist organization members, the network of terrorist organization members is as shown in Figure 8.3. The structure of the network has changed significantly and more isolated groups occur. This phenomenon is likely due to the relationships of partial terrorist organization members being concealed in various affiliations.
8.4 Network Refinement Based on Interaction Relation Hypothesis
In order to compensate for potentially missing data and to improve the network, this section first constructs a possible relationship network of the members of a terrorist organization on the basis of the matrix of mutually participated events; secondly, it finds the potentially missing data by comparing the assignments obtained from the possible relationship network and public information with the interaction relation network; thirdly, the interaction relation hypothesis is proposed in accordance with the characteristics of member relationship in terrorist activities; finally, the initial network of the members of the terrorist organization is improved in accordance with the hypothesis.
8.4.1 Construction of Possible Relationship Network of Members of a Terrorist Organization Based on Mutual Participation Relationship
It is supposed that there are m terrorists, who separately participate in n terrorist incidents. The participation matrix of the event is defined as PT; thus PT is the subordinate relationship matrix of m × n rank, among which:
![]()
In this formula, i = 1, 2, …, m; k = 1, 2, …, n.
In the social network theory, the interpersonal relationship network between members can be established in accordance with the fact that many people participate in some activities many times. For example, for the many people participating in club activities many times, it can be considered that a certain relationship exists between them. However, generally terrorist incidents are planned meticulously. The members involved are selected on a strict basis. Generally, the members may communicate secretly before the action in order to coordinate the action; although a single connection between members exists, the key information here is knowing this relationship in advance. Thus, we can establish the possible interpersonal relationship network (PRO) in accordance with the subordinate relationship matrix of the event. The advantage is that the relationships can be considered comprehensively while the disadvantage is that details of the relationship may be missing or a spurious relationship may exist.
Thus, in accordance with the participation matrix PT, we can get the adjacency matrix model PRO, including the possible relationships; PRO is an m × m rank matrix. In this situation, PRO = PT ×·PT′, and in this formula matrix PT′ is the transpose of the participation matrix PT. Obviously, if actors i and j have jointly participated in Event k, ptip = ptjp =1, where p = 1, 2, …, k; PROij = k, with k = 1, 2, …, n.
Certainly, in accordance with situations of individuals participating in the events, we can get the relation matrix ATCK of the event in the same way, i.e. ATCK = PT′·× PT.
In accordance with the subordinate relationship matrix between the members of the terrorist organization and the terrorist incidents in Table 8.1 and the above calculation method, the relationship matrix of the members of the terrorist organization based on joint participation in the terrorist incident is shown in Table 8.5.
Table 8.5
Relationship Matrix of the Members of a Terrorist Organization Based on Participation
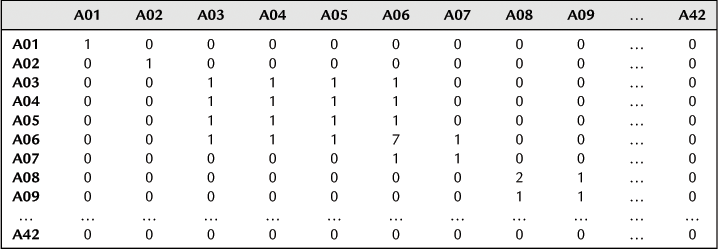
The relationship matrix above is a symmetrical matrix. The elements in the matrix represent the number of terrorist incidents in which the members of the terrorist organization jointly participate. For example, the value in the third line and the fifth column is 1, which means that A03 and A05 jointly participate in one terrorist incident. Inputting the content of Table 8.5 into UCINET software allows us to get a possible relationship network diagram of the members of terrorist organization based on the mutual participation relationship, as shown in Figure 8.6. In the figure, the dots represent 42 members of the terrorist organization; the lines between the dots represent the possible interrelationships between the members of the terrorist organization. Four isolated points in the figure indicate that they do not jointly participate in any terrorist incidents with other members of the terrorist organization.
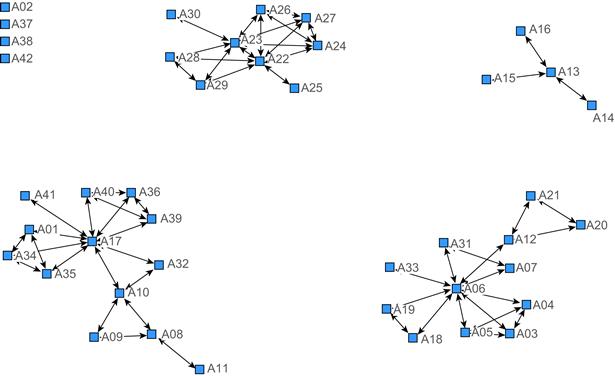
Figure 8.6 Possible relationship network diagram of the members of a terrorist organization based on mutual participation relationships.
8.4.2 Potential Missing Data
Compared with the relationship in Figure 8.3, the relationship between the members of the terrorist organization in Figure 8.6 is changed significantly, and some new relationships appear; meanwhile, some old relationships no longer exist. The reasons for these situations are as follows. Firstly, partial members of the terrorist organization jointly participate in a terrorist incident, but public information does not include information on the relationships between these members of the terrorist organization, which results in the relationships increasing. Secondly, some members of the terrorist organization do not jointly participate in a terrorist event, but they are interrelated, which constitutes missing relationships. For the newly increased relationships, some arise from the possible data missing in the public information while others may be spurious relationships.
Entity and relationship missing cases
Common data missing includes two types: entity missing and relationship missing. Entity missing mainly means there is a figure, event, or organization missing. Relationship missing mainly refers to the relationship between the entities being missing; that is, a relationship between people or between the people and the event is missing.
Comparing Figures 8.3 and 8.6, the entity missing and relationship missing cases obviously exist in Figure 8.3. The entity missing case refers to those members of terrorist organization who participate in the terrorist incident with a clear relationship, but where no relationship data are included in the public information. For example, in terrorist event E03, the members A03, A04, A05, and A06 jointly participate in this event; however, in accordance with public information, the members of these two terrorist organizations have no contact. The relationship missing case is where members are not directly related to each other, but they are linked through the co-leader or the people being led. For example, if A06, A18, and A19 jointly participate in event E16, A18 and A19 are led by A06, so A18 and A19 are linked through A06; however, A18 and A19 do not contact each other directly via public information, so their relationship is missed. Possible entity missing and relationship missing cases are shown in Table 8.6.
Table 8.6
Relationship Changes Between Members of a Terrorist Organization

Spurious relationships
A spurious relationship is one where a possible relationship network between members exists based on event correlation. Because these two members jointly participate in the same event, an association relationship is formed. However, due to regional and time differences, actually this relationship does not exist. The potential spurious relationships in Figure 8.6 are listed in Table 8.6. There are six spurious relationships in all, among which four are potentially spurious relationships appearing in the same chain of command. For example, A23 and A28 established a direct relationship in Figure 8.3, because both jointly participated in event E21. However, analysis of public information reveals that, in event E21, A29 went to a Middle Eastern country to develop the new member A28, which was arranged by A23. At this time, A23 was in a South Asian country. The regional difference makes the possibility of a direct relationship between A23 and A28 very unlikely. The possible spurious relationships are shown in Table 8.6.
8.4.3 Interaction Relationship Hypothesis
In this section, we propose three types of inference hypotheses. They are the entity missing hypothesis based on action association, the tripartite relationship hypothesis based on the event, and the spurious relationship hypothesis based on association differences. These hypotheses can help us to find missing entities, missing relations and false relations, and lay the foundations for improvement of the initial social networks.
Entity missing hypothesis based on action association
Most terrorist incidents are carefully planned. The implementation of terrorist actions requires close communication and cooperation between members. Thus, on the basis of the action association relationship in the terrorist incident, we can propose the entity missing hypothesis. That is, the appointed and interactive relationship network between the members is based on public information. For two individuals or action groups that participate in the same terrorist incident and have clear tasks, if they do not contact each other directly and do not have an indirect relationship, we can suppose that at least one middleman AE exists between these two individuals or action groups and acts as an intermediary, who takes charge of communication and coordination, as shown in Table 8.7.
Table 8.7
Entity Missing Hypothesis
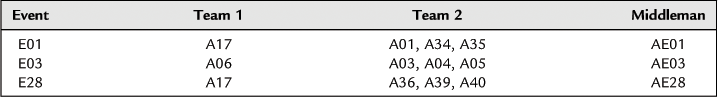
Taking event E01 as an example, A17, A01, A34, and A35 participate in this event. However, public information does not include any descriptions of a relationship between A17, A01, A34, and A35. Therefore, we can suppose that the middleman AE01 exists and is responsible for the contacts among them.
Tripartite relationship hypothesis based on the event
The tripartite relationship arises from analysis and research into the relationship between three points in the network. It is composed of a two-party relationship that researches the relationship of a pair of points in the network.
The two-party relationship includes two types in the undirected network, which are related and not related, and three types in the directed network, which are the two-way relationship, a single-way relationship, and no relationship. Similarly, the tripartite relationship includes many types of relationships in the undirected and directed networks. Cartwright and Harary [12] believe that the complex social structure is made up of simple structures. In particular, they are composed of multiple overlapping tripartite relationship groups. The simple three-party structure is the basis for a bigger social structure. Therefore, it is significant to research the tripartite relationship to analyze the network structure and the relationship between the points.
The tripartite relationship hypothesis means the assumption and reasoning of a missing relationship between three points in a network based on mathematics and probability. In 1954, Anatol Rapoport, a Russian mathematical psychologist, proposed the weak ties hypothesis [10]. The weak ties hypothesis means that if A has a certain relationship with B and C separately, there is a relationship between B and C. In 1973, Granovetter [13], an American sociologist, divided the relationships between people into strong ties, weak ties, and unrelated in accordance with the contact time, emotional intensity, familiarity, and situation of helping each other. He also proposed a tripartite relationship hypothesis based on speculation about interpersonal relationships: that is, if A and B have a strong tie, and B and C also have a strong tie, then a relationship may exist between A and C.
On the basis of the characteristics of the member relationship networks of a terrorist organization, we propose the tripartite relationship based on terrorist incidents. For three people A, B, and C jointly participating in the same terrorist incident at the same time in the same place, if B and C are related because A was the co-leader or the people being led, a relationship may exist between B and C. On the basis of this hypothesis, we obtain a new supplementary relationship, as shown in Table 8.8.
Table 8.8
Interaction Relationship Hypothesis

In Table 8.8, for the different events, A09, A17, A06, and A12 act as the co-leader or middleman in the terrorist incident. However, the remaining two members of the terrorist organization are not related to each other in public information. Here, we suppose that an interaction exists between the remaining two members of the terrorist organization.
Spurious relationship hypothesis based on association differences
In the possible relationship network of members based on an association event, an association relationship is formed, because both of them jointly participate in the same event. But this relationship does not actually exist because of regional and time differences. For this circumstance, we propose the spurious relationship hypothesis: that is, for three members of a terrorist organization in the same chain of command, A, B, and C, if A and C are at both ends of the chain of command separately, and regional and time difference exists, the possibility of a direct relationship between A and C is very unlikely.
For example, for A24 and A26, as well as A27 and A26, because A24, A26, and A27 jointly participate in E23, both of them establish the direct relationship shown in Figure 8.6. However, the method of participating in E23 is very different. A26 is instigated by A22 to participate in E23, while A27 actively contacts A22 and A24 and requires participation in E23 after finding A22 and A24 premeditating and planning E23 through a network video. Therefore, in accordance with the different methods of A26 and A27 participating in E23, we can suppose that the relationship between A24 and A26 is a spurious relationship, as well as that of A27 and A26.
8.4.4 Improvement of the Appointment and Interaction Relationship Network of the Members of a Terrorist Organization
On the basis of the entity missing case of action association and the tripartite relationship hypothesis of the event, we can refine the appointment and interaction network of the members of the terrorist organization in Figure 8.3, as shown in Figure 8.7. In the figure, the relationship between the members of terrorist organization with the entity missing is defined as the assumed middleman, and the relationship between the members of terrorist organization with the relationship missing is defined as the interaction relationship. As shown in the figure, A03, A04, A05, and A06 point at AE03 by the arrow, which means that they are the members of AE03, A08, and A10 are connected by a two-way arrow, which shows the interactions between them. Meanwhile, on the basis of the entity missing hypothesis of action association, the tripartite relationship of the event, and the spurious relationship of association differences, we can improve the relationship network (Figure 8.6) based on the event, get rid of the spurious relationship through increasing the entities and missing relationships, and finally get a consistent assignment and interaction relationship network.

Figure 8.7 Improved assignment and interaction relationship network.
8.5 Relationship Network Refinement and Final Relationship Network of Terrorist Organizations and Incidents
In this section, we first construct a possible relationship network between terrorist organizations and terrorist incidents. Then we compare the possible relationship network to the initial social network and obtain the final multi-element terrorist social network by refining the initial social network according to the possible relationship network.
8.5.1 Possible Relationship Network Construction and Perfection of Terrorist Organizations and Terrorist Incidents
As terrorist organization members and instigators of terrorist incidents, the terrorist organization members connect terrorist organizations with terrorist incidents indirectly. The terrorist organizations provide substantial and spiritual support for terrorist organization members to implement terrorist activities. To a certain extent, the existence of terrorist organizations might be regarded as the source of the occurrence of terrorist incidents. By analyzing the affiliations between terrorist organization members and terrorist incidents, as well as among terrorist organizations, a possible relationship between terrorist organizations and terrorist incidents can be established, which plays an important role in understanding the activities of terrorist organizations.
The relationship matrix between terrorist organization members and terrorist incidents, as well as among terrorist organizations, is shown in Tables 8.1 and 8.2. Multiplication of these two matrices gives the possible relationship matrix between terrorist organizations and terrorist incidents, as shown in Table 8.9.
Table 8.9
Relationship Matrix Between Terrorist Organizations and Terrorist Incidents

The relationships that may exist between terrorist organizations and terrorist incidents, on the basis of this matrix, are shown in Figure 8.8. In the figure, the round dots represent eight terrorist organizations, the square dots represent 28 terrorist incidents, and the arrows point to terrorist incidents by terrorist organizations.
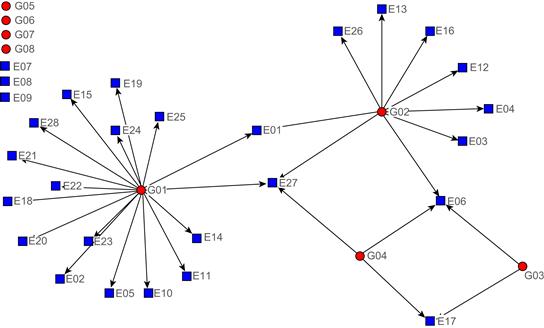
Figure 8.8 Initial possible relationship figure between terrorist organizations and terrorist incidents.
Figure 8.8 is a comprehensive illustration of the possible relationships between terrorist organizations and terrorist incidents. However, on analysis, Figure 8.8 was found to contain three obvious spurious relationships, involving E01 and G01, E01 and G02, and E02 and G01. The incidents E01 and E02 happened in 1991 and 1996 respectively, while G01 and G02 were established in 1997 and 1996 respectively. Due to the differences of incident time and the time the organizations were established, we could suppose that there was no direct relationship between E01 and G01, E01 and G02, or E02 and G01. Other incidents happened after the establishment of each terrorist organization, which were made by terrorist organization members affiliated with each terrorist organization. The relationship network between terrorist organizations and terrorist incidents after refinement is shown in Figure 8.9.

Figure 8.9 Relationship network refinement between terrorist organizations and terrorist incidents.
8.5.2 Final Multi-Element Network Model
Using the above analysis, we can obtain a relatively complete multi-element network model of the terrorist organization members, shown in Figure 8.10. This network provides a thorough representation of the multi-element relationships among organization members, terrorist incidents, and terrorist organizations. Moreover, through this network, we can not only find the perpetrators of terrorist incidents and the terrorist organizations behind them, but also find the designated, interactive relations among members of the terrorist organization, as well as the support relations in the organization.

Figure 8.10 Multi-element network figure of the terrorist organization after refinement.
8.6 Analysis and Verification
In this section, we first analyze some common characteristics of terrorist social networks. We then evaluate the organizations and people within them to find the key entities. Finally, we verify the effectiveness of the model.
8.6.1 Network Characteristics Analysis
On the basis of the social network theory, in this chapter indices, such as scale, density, diameter, and node degree (degree of association), are selected to analyze the general characteristics of terrorist networks; the results of basic characteristics for the above terrorist network from calculations using UCINET software are shown in Table 8.10.
Table 8.10
Egocentrality Network Calculation Results of the Terrorist Network
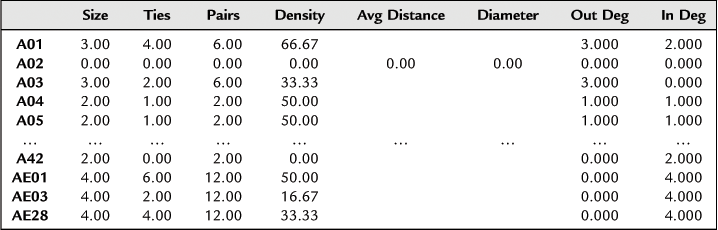
The results of the calculation show that, from the perspective of scale, 11 people had a direct relationship with more than four people among the network members of terrorists, and most members only had a relationship with one or two other members. This explains the distensibility and invisibility of the network relationship. From the perspective of density, there are two high-density relational members, 16 medium-density relational members, with most members being in the low-density connection relational network, with an overall network density of 0.0389. The network shows the local gang nature and the low density in the overall correlation. From the perspective of dimension, the relational path of the terrorists is rather short. Moreover, from the perspective of the node degree, the average click-in and -out degree is 1.711, the largest click-out degree is 5, and the largest click-in degree is 6, which shows the limitation of individual influence in a decentralized network.
8.6.2 Evaluation of Leading Figures
This refers to members in the network of terrorists who take up important positions and are capable of influencing and controlling the flow of information and resources. Some of them are either the command chiefs of the organization or play the special roles in the organization; thus, the absence of these members may seriously affect the operation of the terrorist organization. To analyze these people, social network analysis usually uses centrality and other methods to carry out positioning. The evaluation indices that are generally used are as follows. The degree centrality measures the active degree of the actors relating to the interactive communication aspects, the closeness centrality measures the distance with others, and the betweenness centrality measures the go-betweens. Because the requirements of closeness centrality to the digraph calculation is rather strict, and considering the positive correlation between this index and point centrality, the point centrality is generally considered as the reference; thus, we will omit it. The results of other centrality indices from both calculations using UCINET software and regulative treatment are shown in Table 8.11 (only the top 10 listed) and Figure 8.11.
Table 8.11
Core Figure Measurement and Estimation


Figure 8.11 Core index measurement and estimation for terrorist organization members.
It appears that, from the evaluation, the leading figures in the member network are A17, A10, A06, A23, A12, etc.
8.6.3 Important Organization Evaluation
Similarly, we can also measure and estimate the importance of the terrorist organization. Here, we use the number of members of the terrorist organization to represent its scale, the number of terrorist incidents perpetrated by the organization to represent the destructiveness of the organization, and the betweenness centrality to represent the centrality of the organization. The measured and estimated results are shown in Table 8.12 and Figure 8.12.
Table 8.12
Importance Measurement and Estimation of Terrorist Organization
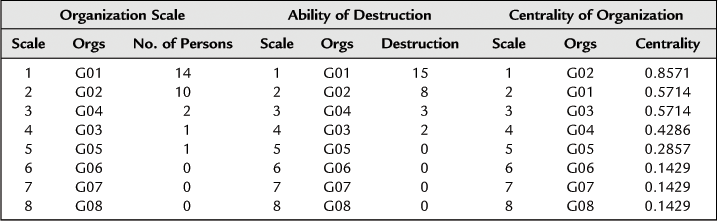

Figure 8.12 Important index measurement and estimation for terrorist organization.
8.6.4 Result Verification
The evaluation results of the missing figures and network key figures are found according to the assumption and deduction through confirmation conforming to the facts. The intermediary roles AE01, AE03, and AE08 and the missing relations exist in the deductions and assumptions. So, during the individual missing case, E03 stands for the Guns’ Secrete Transport Case in 1998, and by verification of the subsequent information, in that incident, several people have played the role of AE03 and have been responsible for contacts both at home and abroad. Moreover, during the relation missing case, taking incident E05 (Arms Private Manufacture Case in 1998) as an example, A09 was seized by the Public Security Organ, and during the trial proceedings, A09 confessed that he was designated by A08 and A10 to carry out terrorist activities; however, in available public information, there was no mention of the relation between A08 and A10.
The evaluation results for the leading figures agree with the facts; for example, A17 organized and established the “East Turkistan Islamic Movement,” and he was the chairman of this organization. Moreover, he had certain connections with al-Qaeda. The terrorist A23 took the place of A17 after A17 was shot dead. In 2005, A23 became a member of a leading organization of al-Qaeda, “Ijtima‘al-Shurra,” and terrorist A10 became vice-chairman of the “East Turkistan Islamic Movement,” etc.
8.7 Conclusions
Much previous research on network models of terrorist organization members took the viewpoint of interaction relationships among terrorist organization members available in public information. However, due to missing data problems, it may contribute to the outcome of the analysis deviating from the real-world situation. Thus, in this chapter, to obviate the missing data problem in the invisible network model construction of terrorist organization members, a type of terrorist construction method has been proposed based on the combination of interactive relation records and deductions and assumptions. Firstly, the initial relation network of the members is established according to the interactive relation in available public information. Secondly, a possible relation network of the members is established using the incidence relation. Based on these relation networks, we identify the missing data phenomenon by comparison of the two networks. We then propose the interactive relation assumption as a characteristic of theoretical activities, and thus improve the initial network. Finally, its effectiveness is proved via empirical research. The network construction method of terrorists based on the combination of the interactive relationship records and deductions and assumptions is found to be an effective method to refine social network model construction for terrorist groups.
It is also worth pointing out that this chapter has also studied the network construction method of terrorist organization members based on the interactive relation hypothesis, and that the source of these data is public interactive information. With the current availabitity of a huge quantity of information, there are many problems needing solutions. For example, there may be a large amount of false information in the relational network established on the basis of network and open source intelligence information, so how can we carry out the missing data and spurious analysis? Another example, relating to terrorist organization members in a particular terrorist incident, is how to carry out relationship deduction by analysis of the roles, knowledge, resources, skills, and other factors of terrorist organization members? Therefore, in the future, we still need to introduce several new means of analysis, such as the combination of the interactive relation assumption, the probability transition, and statistical inference. The combination of data mining and machine learning should also be a potential development direction in the future.
Acknowledgments
This research is supported by the National Natural Science Foundation of China under Grant No. 70973138.
References
1. Sageman M. Understanding Terror Networks. Philadelphia: University of Pennsylvania Press; 2004.
2. Erickson BH. Secret societies and social structure. J Soc Forces. 1981;60(1):188–210.
3. Sparrow M. The application of network analysis to criminal intelligence: An assessment of the prospects. J. Soc Netw. 1991;13(3):251–274.
4. Baker WE, Faulkner RR. The social organization of conspiration: Illegal networks in the heavy electrical equipment industry. J Am Sociol Rev. 1993;58(6):837–860.
5. Krebs VE. Mapping networks of terrorist cells. J Connect. 2002;24(3):43–52.
6. Basu A. Social network analysis of terrorist organizations in India. the North American Association for Computational Social and Organizational Science (NAACSOS) Conference 2005, Notre Dame, IN, June 26–28, 2005.
7. Rothenberg R. From whole cloth: Making up the terrorist network. J Connect. 2001;24(3):36–42.
8. Carley KM. Estimating vulnerabilities in large covert networks using multi-level data. Proceedings of the 2004 International Symposium on Command and Control Research and Technology 2004.
9. Carley KM, Dombroski M, Tsvetovat M, Reminga J, Kamneva N. Destabilizing dynamic covert networks. Vienna, VA: Proceedings of the 8th International Command and Control Research and Technology Symposium; 2003.
10. Rodriguez JA. The March 11th terrorist network: In its weakness lies its strength, Department of Sociology and Analysis of Organizations. Working Paper EPP-LEA:03 Barcelona (in Spanish) 2005.
11. Kennedy J, Weimann G. The strength of weak terrorist ties. Terror Polit Viol. 2011;23(2):201–212.
12. Cartwright D, Harary F. Structural balance: A generalization of Heider’s theory. J Psychol Rev. 1956;63(5):277–293.
13. Granovetter MS. The strength of weak ties. Am J Sociol. 1973;78(6):1360–1380.
