Chapter 5. Packet Sniffing and Social Engineering
This chapter covers the following CEH exam objectives:
• Understand what social engineering is
• Know the various types of social engineering
• Be able to use phishing
• Be able to conduct packet sniffing
Social Engineering
Social engineering is a substantial security threat. Many people studying hacking want to focus on just the technical items. However, even technical attacks depend on some level of social engineering. Social engineering is the art of using people skills to either get information or to get someone to take some particular action. Many attacks have an element of social engineering. Consider ransomware, which has frequently been in the news in recent years. It often begins with an email that appears to be from a well-known contact or a trusted colleague that tries to get the recipient to click on some link or open some attachment. That process is social engineering.
Social engineering involves communication that is designed to encourage the recipient to perform some action or provide some information. There are a variety of approaches to social engineering, the most common of which are briefly described here:
• Authority: With this approach, the attacker attempts to convince the target that the attacker is actually a person of authority, and the target must comply. Phishing scams that claim to be from the FBI or IRS fall into this category. Figure 5.1 shows an example of such an email.
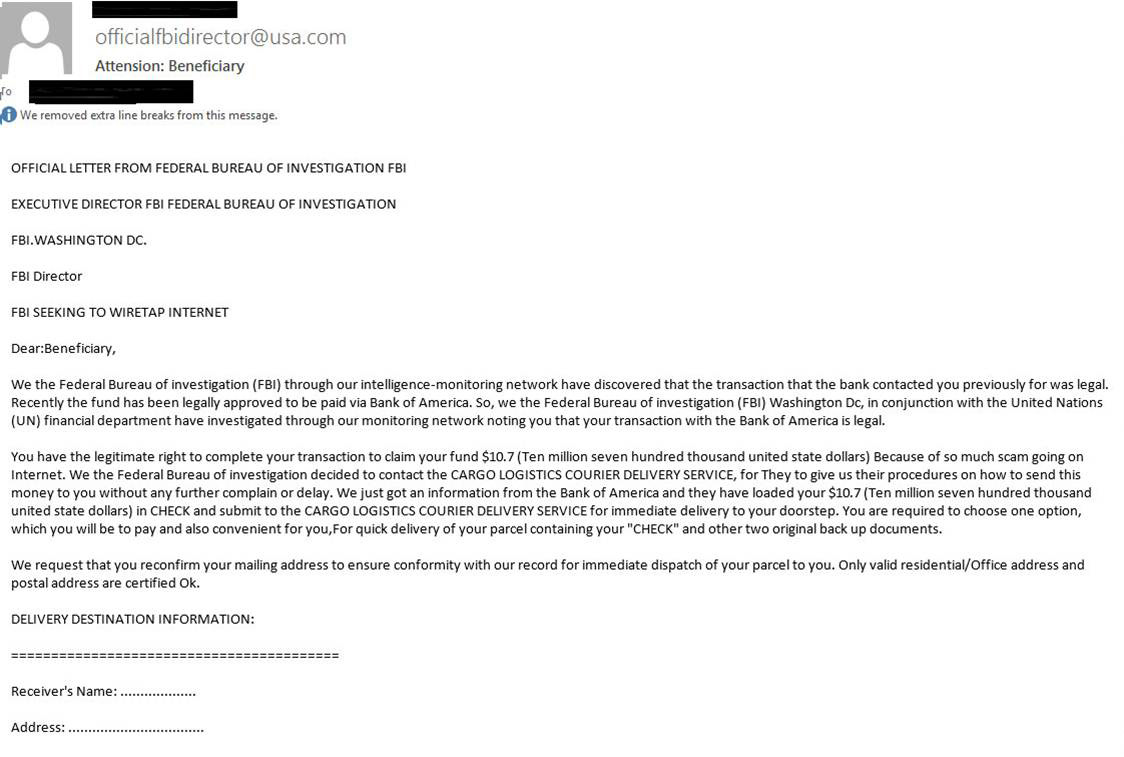
Figure 5.1 Authority Phishing Scam
It is important to keep in mind that if the real FBI wishes to speak with you, a couple of serious-looking agents will show up at your door. And the IRS always contacts people through postal mail, not email.
• Urgency: This approach attempts to persuade the recipient that if they don’t act promptly, something bad will happen or they will miss out on something. The latter exploits FOMO (fear of missing out). Figure 5.2 shows an example of a phishing email I received while writing this chapter. Note that it uses both urgency (in fact, the subject is “Urgent Attention”) and authority. It is purportedly from a doctor and references contacting a diplomat.
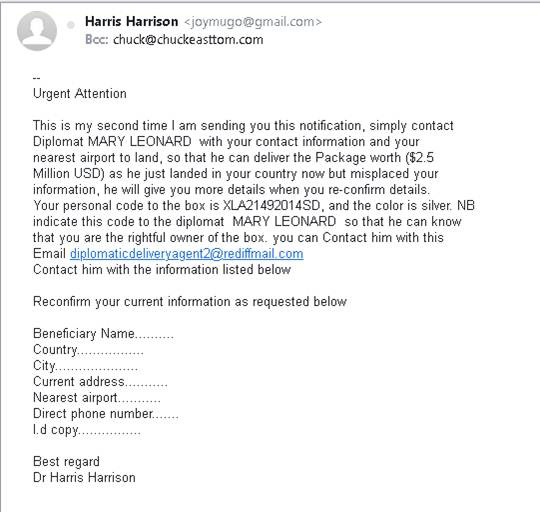
Figure 5.2 Urgency Phishing Scam
• Greed: This approach simply plays to the target's greed. Scams might claim, for example, that you have won some lottery or are entitled to an inheritance and ask you to provide some information. Figure 5.3 is an example of a greed-based email I received while writing this chapter.

Figure 5.3 Greed Phishing Scam
It should be clear that these techniques can be combined in multiple ways. Urgency is commonly used in conjunction with one of the other two. For example, an email might indicate that the recipient’s computer has a substantial security flaw, and the attached patch must be applied immediately in order to protect that computer. Or an email may indicate that there is a problem with the recipient’s bank account or credit card, and if the recipient does not click on the link and address it immediately, their account will be suspended. The goal is to get the user to act immediately, without thinking.
Use of authority is best explained by describing an actual attack that has been used for some years. The attacker sends an email that purports to be from the FBI—and it may even include the FBI logo. The email claims that the recipient has visited some website that is prohibited and should click on a link to pay a fine. The email is likely to use urgency by saying that if the recipient does not pay the fine immediately, they may face jail time.
Greed is a common basis for many phishing emails. An email may claim that there is some very large sum of money the recipient can have if they take action. Usually, the user must click a link or provide some information. Again, the goal is to take advantage of the recipient’s greed.
For a penetration tester, it is often a good idea to send out some phishing emails to certain employees in the target company. The only way to see if the staff at a company will resist phishing emails is to send some.
Social engineering is also sometimes used to physically access target facilities. Essentially, the attacker pretends to be someone with legitimate access to the facility and attempts to gain entry. The attacker may claim to be there to execute some repair or delivery. Regardless of the specific approach or goal, there are a variety of factors that impact the likely success of social engineering. Some of them are listed here:
• Lack of security policies: If there are no policies to address phishing, social engineering phone calls, or other forms of social engineering, then it is quite unlikely that employees will react properly. Policies do not guarantee compliance, but a lack of policies virtually guarantees mistakes.
• Insufficient security training: Having policies is only part of the process. Employees must be trained in those policies.
• Easy access to the physical facilities: If the issue is physical access, lack of controlled access will make an attack even easier.
Real social engineering starts with gathering information. Some of the techniques discussed in Chapters 1, “Reconnaissance and Scanning,” and 2, “Enumeration and Vulnerability Scanning,” can help with that. Scanning social media for information on employees is often a good place to start.
There are three types of social engineering. The first type, human based, is what we have already discussed in this section. is the second type, computer based, is what is discussed in the next section. The third type, mobile based, is essentially the computer-based social engineering done on a mobile device.
The CEH exam has a specific four step methodology for social engineering. While it may not have occurred to you, when doing ethical hacking/penetration testing, it is a good idea to test the organization’s resistance to social engineering as well, provided that it is included in the scope of service agreement. Here are the four steps:
1. Research the company. This can be via search engines, social media, Dumpster diving, websites, and other sources of reliable information.
2. Select a victim. Based on your research, you will have identified one or more employees within the company who are most likely to be susceptible and most likely to have access that you can exploit.
3. Develop a relationship. In some cases, this process is quite brief—such as just an email. In other cases, you may need to exchange communication over a period of time to develop trust.
4. Exploit the relationship by getting some sort of information from the victim.
Human-Based Social Engineering
Human-based social engineering involves a human being actually interacting with another human being. Phishing emails are not human based. The following subsections describe a number of types of human-based social engineering, most of which are surprisingly simple.
Tailgating
Tailgating is a process whereby the attacker simply tries to follow a legitimate employee to gain access to a building. If there is a turnstile or door that requires some sort of access, such as with a key card, the attacker may simply follow someone in. This usually works best when two conditions are met:
• The organization is relatively large. If a company has very few employees, they all know each other, and a stranger attempting to gain access will be quite obvious. But in an organization with 1000 or more employees, it would be impossible to know everyone.
• The attacker blends in. If most employees are wearing suits, an attacker can also wear a suit to blend in. If, however, most employees wear jeans and t-shirts, someone wearing a suit would draw attention. An attacker might wear coveralls and carry a toolbelt to look like a maintenance worker. An attacker may even have some generic name badge on their clothing but obscured so others cannot readily tell if it is a legitimate company badge or not.
Tailgating is sometimes referred to as piggybacking.
Shoulder Surfing
When you use your computer in a crowded public area, such as a coffee shop or an airport, it is not always possible to know who might be walking behind you. The idea of shoulder surfing is to literally walk behind someone and see if you can observe their password (or some other sensitive information) when they type it in. It is amazing how frequently this does indeed yield some level of data. It can even happen accidentally. People on airplanes frequently open their laptops and work on them. Anyone sitting near such a person might see what the person is working on, and it might be of a confidential nature. I have lost track of how many times I have casually glanced around a flight and seen confidential financial data, internal company documents, and even more serious confidential data.
Related to shoulder surfing is eavesdropping. I am frequently shocked by the things people discuss in public. I was on a flight to Baltimore a few years ago when such an incident happened. The Baltimore area, if you were not aware, is home to a number of defense contractors. It is also home to the NSA. On this particular flight, two engineers in the row in front of me had a rather lengthy and detailed discussion about a failed missile test. I feel quite certain that sort of information was not public data.
Dumpster Diving
Dumpster diving is primarily information gathering, though it does have a social engineering component. It is amazing how often organizations throw out documents that have not been shredded. It is sometimes possible to gather rather sensitive information from trash bins. Consider your own home. Do you throw out utility bills, credit card statements, bank statements, health insurance documents, or any other sensitive documents without shredding them? If so, then someone who goes through your garbage could gather enough information to successfully steal your identity.
Reverse Social Engineering
Reverse social engineering is an interesting twist on social engineering. An attacker might to a target and email that containing some malware. Then, a bit later, the attacker might contact the target organization, posing as a cybersecurity firm marketing its services. Due to virus that was earlier emailed, the target company might be currently experiencing computer problems and grateful for the sales call. The target company might then give the attacker access to the network so that the virus can be fixed.
Computer-Based Social Engineering
Computer-based social engineering is more common than human-based social engineering today. This was not always the case. Also, it should be noted that if the goal is physical access to facilities, then human-based social engineering will be more successful. In the following subsections, you will see the various methods of computer-based social engineering.
Phishing and Related Attacks
Social engineering can be accomplished over the phone, but the use of email for social engineering is far more common today. For example, an attacker might send out an email, purporting to be from a bank and telling recipient that there is a problem with their bank account. The email then directs them to click on a link to the bank website, where they can log in and verify their account. However, the link really goes to a fake website set up by the attacker. When the target goes to that website and enters their information, they give their username and password to the attacker.
Phishing involves sending out mass emails and not targeting any person or group in particular. The idea is that if you send out a large enough volume of emails, someone is likely to respond. An attacker needs only a small number of responses to make a phishing campaign worth the effort.
Many end users today are aware of these sorts of tactics and avoid clicking on email links. But unfortunately, not everyone is so prudent, and this attack is still often effective. In addition, attackers have come up with new ways of phishing. One of these methods is called cross-site scripting (XSS). If a website allows users to post content that other users can see (such as product reviews), the attacker may post a script (JavaScript or something similar) instead of a review or other legitimate content. Then, when other users visit that web page, instead of loading a review or comment, the page will load the attacker’s script. That script may do any number of things, but it is common for such a script to redirect the end user to a phishing website. If the attacker is clever, the phishing website looks identical to the real one, and end users are not aware that they have been redirected. Web developers can prevent cross-site scripting by filtering all user input.
Phishing, as just discussed, is the process of attempting to get personal information from a target in order to steal the target’s identity or compromise the target’s system. A common technique is to send out a mass email that is designed to entice recipients into clicking a link that purports to be some financial institution’s website but is actually a phishing website.
Spear phishing uses the same technology as phishing but in a targeted manner. For example, an attacker who wants to get into the servers at a defense contractor might craft email and phishing websites specifically to target software and network engineers at that company. The emails might be made to appear of interest to a specific subgroup of people. Or the attacker might take the time to learn personal details of a few of these individuals and target them specifically. This technique has been used against executives at various companies.
Spear phishing has been expanded even further into the process of whaling. With whaling, an attacker attempts to compromise information regarding a specific highly valuable employee. Whaling uses the same techniques as phishing but is highly customized to increase the chances that the single individual target will be fooled and actually respond to the phishing attempt.
A similar attack is called pharming. An attacker redirects web traffic to a fraudulent website by installing a malicious program on a personal computer or server. Sometimes this process is carried out using technical tactics, such as DNS cache poisoning or host file modification, and is called “phishing without a lure.”
There are tools to help combat phishing. The website PhishTank.com is a phishing cyberthreat intelligence website and a good place to start. There are many countermeasures to all types of social engineering. They all start with robust policies that employees are well trained in. Additional tactics can also help, such as:
• Limited access privileges
• Anti-phishing cyberthreat intelligence
• Background checks and termination processes to mitigate insider threats
• Good change management processes
• Regular software updates, including on mobile devices
Fake Security Apps
One of the cleverest methods of circumventing security is the use of fake security apps. These applications claim to be antivirus or other security applications, when in fact they are malware. There are quite a few fake security apps out there. Here is a sample of some of the most well-known fake security apps:
• ANG Antivirus
• Antivirus System PRO
• Security Shield
• MacSweeper
• Malware Alarm
• Virus Heat
Some of these applications actually are spyware. Others are scareware. Such an application performs a scan of a target machine and reports a host of errors on the machine. Then the software either states that the free version cannot fix the problems, and the user has to pay to get the computer fixed, or directs the user to call a number. Either way, the goal is to get the user to pay for fixes that simply are not necessary. Antivirus System PRO is shown in Figure 5.4.
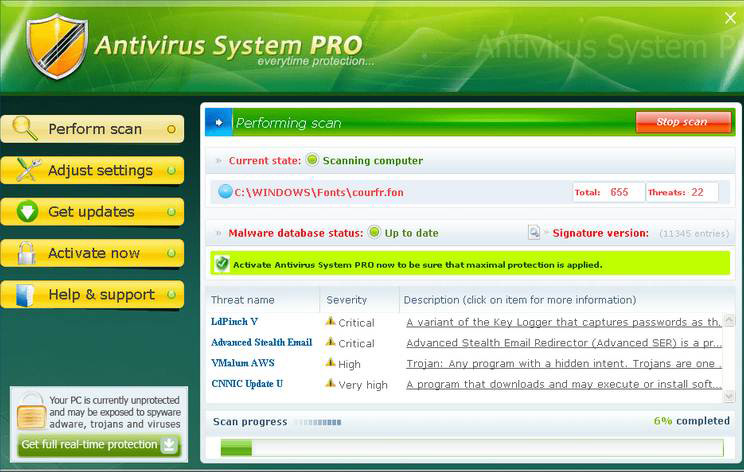
Figure 5.4 Antivirus System PRO
Mobile-Based Social Engineering
A mobile form of phishing is called SMSishing (or SMS phishing). It can be accomplished via spimming, which is sending spam via instant messaging. Sometimes the goal is just to get data. In other cases, it is to install malicious applications on the target device. At one point, it was estimated that one-third of the flashlight apps in Google Play were spyware. Articles in 2021 warned of malware and spyware, as well as banking Trojans, in Google Play.[1],[2] In some cases, legitimate apps are infected with malware. As one example, Cake VPN is a legitimate VPN application that is available today in Google Play. However, it was at one point infected with a banking Trojan.
Insider Threats
No one wants to think that a fellow employee could be a threat, but it does happen—and there may be any number of reasons. An employee could be disgruntled, feel unappreciated, or have financial motivations for stealing company data and either selling it to a competitor for profit or trying to destroy data on the servers. Insider threats are some of the most difficult threats to combat. Insiders, by definition, have some level of access to a system that external attackers do not.
Countermeasures for insider threats include:
• Least privileges: Someone who has only enough access to do a job can cause only a limited amount of damage.
• Logging and auditing: Simply being aware of what a person is accessing can help. If someone is accessing files they don’t need for work, or perhaps accessing an unusual volume of data, these can be signs of insider threats.
• Employee training: As with most other social engineering, training employees is the primary countermeasure for insider threats.
• Termination policies: Ex-employees, particularly those who were involuntarily terminated, can always be threats. Ensuring that their access is also terminated is an elementary step an organization can take.
• Controlled access: Keeping confidential information confidential is a key step. Ensuring that sensitive data is secured and not just anyone can access it can minimize damage due to an insider threat.
In addition to the malicious insiders, there are also negligent insiders. Earlier I mentioned seeing confidential information on laptops on an airplane. Those displaying their work on laptops in public are not acting maliciously. These negligent insiders who are, nonetheless, exposing sensitive information. A compromised insider also poses a threat. An outside party may use threats or blackmail to force an insider to reveal data, thus compromising the individual.
More on Social Engineering
While some social engineering attempts are rather obvious, others are quite sophisticated. An attacker might set up fake social media accounts or even a fake website to make a fake identity seem more realistic. These sorts of techniques can enhance both computer-based and human-based social engineering. A phishing email is more likely to entice someone if it is associated with an identity that appears to be legitimate. In 2020 and 2021, there were reports of nation-state spy agencies using fake LinkedIn profiles in order to connect with people in the United States who held security clearances.
[1] https://threatpost.com/google-play-malware-spy-trojans/164601/
[2] https://www.zdnet.com/article/malicious-apps-on-google-play-dropped-banking-trojans-on-user-devices/
While social engineering can be used for a wide range of purposes, one purpose is to facilitate identity theft. Even fake social media accounts can assist with that. If an attacker wishes to steal your identity, connecting with you on social media can be a good first step. Other techniques we have discussed, such as Dumpster diving and phishing, can also help in getting information needed to steal a target's identity.
Social Engineering Countermeasures
Some countermeasures have been discussed previously in this chapter. For example, security training is an important countermeasure to social engineering, and least privileges is a countermeasure for insider threats. This section discusses additional techniques.
Multifactor authentication can mitigate some social engineering. Even if an attacker steals a password, two-factor authentication limits what can be done with that password. Regularly updating software and using antimalware (legitimate antimalware) can mitigate spyware threats.
Another countermeasure is to implement separation of duties and rotation of duties. Separation of duties means that, for any critical task, no single employee can perform the task. Say that your company has a server that contains backup private keys for all employee email cryptographic keys in case users lose their private keys. However, this server would clearly be a target for attackers. Separation of duties can be used to protect this server: Your organization can set up this server offline so that in the event of a request for a backup key, three employees are needed to access the key. One employee would have a key to the room where the server is located. Another would have administrative privileges to the machine. A third employee would have the key to unlock the encrypted folder that holds the backup cryptography keys. With such a countermeasure, one employee could not simply go rogue and steal people's cryptography keys.
A countermeasure related to separation of duties is periodic job rotation. Obviously, this measure means multiple people must hold similar jobs. For example, say that an organization has three Windows administrators—one who is responsible for the DNS server, another for the domain controller, and another for a file server. Every six months, these administrators rotate their duties. This rotation means the employees are cross-trained, and it does even more from a security perspective. If one of the employees is doing something that is insecure, whether it is intentional or through negligence/ignorance, there will be someone else in that job to possibly catch the problem.
Dumpster diving was mentioned earlier, and paper shredding is a good countermeasure for that form of social engineering. It is also important to avoid unnecessarily revealing personal information publicly. For example, I don’t list my address or phone number on any social media. Periodically monitoring banking data and credit reports can provide early detection of identity theft.
There are also technical countermeasures. Obviously, using a legitimate antimalware product is recommended. Netcraft has an anti-phishing extension for browsers, mobile devices, and email clients; see https://www.netcraft.com/apps/. Using the Netcraft plugin for Firefox, I visited a known phishing website. You can see the results in Figure 5.5.

Figure 5.5 Netcraft Anti-phishing
Specific targets, techniques, and countermeasures are listed in Table 5.1.
Table 5.1 Phishing Techniques and Countermeasures

Ethical hackers/penetration testers often use phishing techniques to test the security of a target organization. There are a variety of tools to assist with this. The Social-Engineer Toolkit (SET) is a Python tool for aiding with social engineering. It is available at https://github.com/trustedsec/social-engineer-toolkit. The menu for SET is shown in Figure 5.6.

Figure 5.6 Social Engineer Toolkit
There are several other similar tools, including:
• SpeedPhish Framework (SPF): https://github.com/tatanus/SPF
• King Phisher: https://github.com/rsmusllp/king-phisher
• Gophish: https://getgophish.com
Packet Sniffing
Packet sniffing has long been a method for gathering information on a target. Although this is not commonly done today, at one time passwords were often sent in plaintext. Packet sniffing could be used to determine those passwords. Today it is unlikely that you will stumble upon anything so obvious with packet sniffing, but this technique can help you find useful information. Wireshark and tcpdump are introduced in Chapter 2. This section we explores more tools and dives more deeply into sniffing techniques.
Passive Versus Active Sniffing
Passive sniffing simply grabs packets as they come by. The previously mentioned tools Wireshark and tcpdump are excellent for passive sniffing. Active sniffing involves actually injecting packets into the network to observe the network’s behavior. One active sniffing technique involves injecting Address Resolution Protocol (ARP) packets into the network to flood the switch’s content addressable memory (CAM) table, which keeps track of host/port connections.
Many protocols are susceptible to both active and passive sniffing attacks. Essentially any unencrypted protocol—for example, HTTP, Telnet, rlogin, POP3, IMAP, SMTP, and FTP, among others—is vulnerable to sniffing. The obvious countermeasure is to use encrypted alternatives, such as HTTPS, SSH, POP3S, IMAPS, SMTPS, SFTP, and so on.
Hardware Protocol Analyzers
In addition to software applications like tcpdump and Wireshark, there are hardware protocol analyzers. A hardware protocol analyzer is a piece of equipment that captures signals without altering the traffic in a cable segment. It allows an attacker to see individual data bytes of each packet passing through the cable. There are a number of such tools:
• RADCOM Prism Lite Protocol Analyzer: https://cybarcode.com/radcom/analyzer/protocol/prism_lite
• Keysight's U4431A M-PHY Protocol Analyzer: https://www.keysight.com/us/en/product/U4431A/mipi-m-phy-protocol-analyzer.html
• STINGA Protocol Analyzer: http://utelsystems.com
• NETSCOUT's OneTouch AT Network Assistant: http://enterprise.netscout.com
• NETSCOUT's OptiView XG Network Analysis Tablet: http://enterprise.netscout.com
• Agilent (Keysight) Technologies 8753ES: https://www.electrorent.com/us/manufacturers/keysight-technologies
• Xgig 5P8 Analyzer Platform for PCI Express 5.0: https://www.viavisolutions.com/en-us/products/xgig-5p8-analyzer-platform-pci-express-50
• Aukua protocol analyzer: https://www.aukua.com/products/inline-analyzer.html
A picture of the Aukua protocol analyzer is shown in Figure 5.7.

Figure 5.7 Aukua Protocol Analyzer
The SPAN (Switched Port Analyzer) port of a switch gets a mirror of all traffic on all ports. This information is usually more useful for defensive cybersecurity than for hacking. A network TAP (test access point) serves a similar purpose. A TAP is a hardware device that sits in a network segment and gives access to all traffic in that segment.
Network Information
When monitoring traffic, you have to understand the traffic and flows.
A media access control (MAC) address, which is the physical identification number of a device on a network. This number is a 6-byte, or 48-bit, hexadecimal number, such as 21 B0 22 2B 17 D5. It is a sublayer of Layer 2 of the OSI model.
The CAM (content addressable memory) table on network switches stores information such as MAC addresses available on physical ports with their associated virtual LAN (VLAN) parameters.
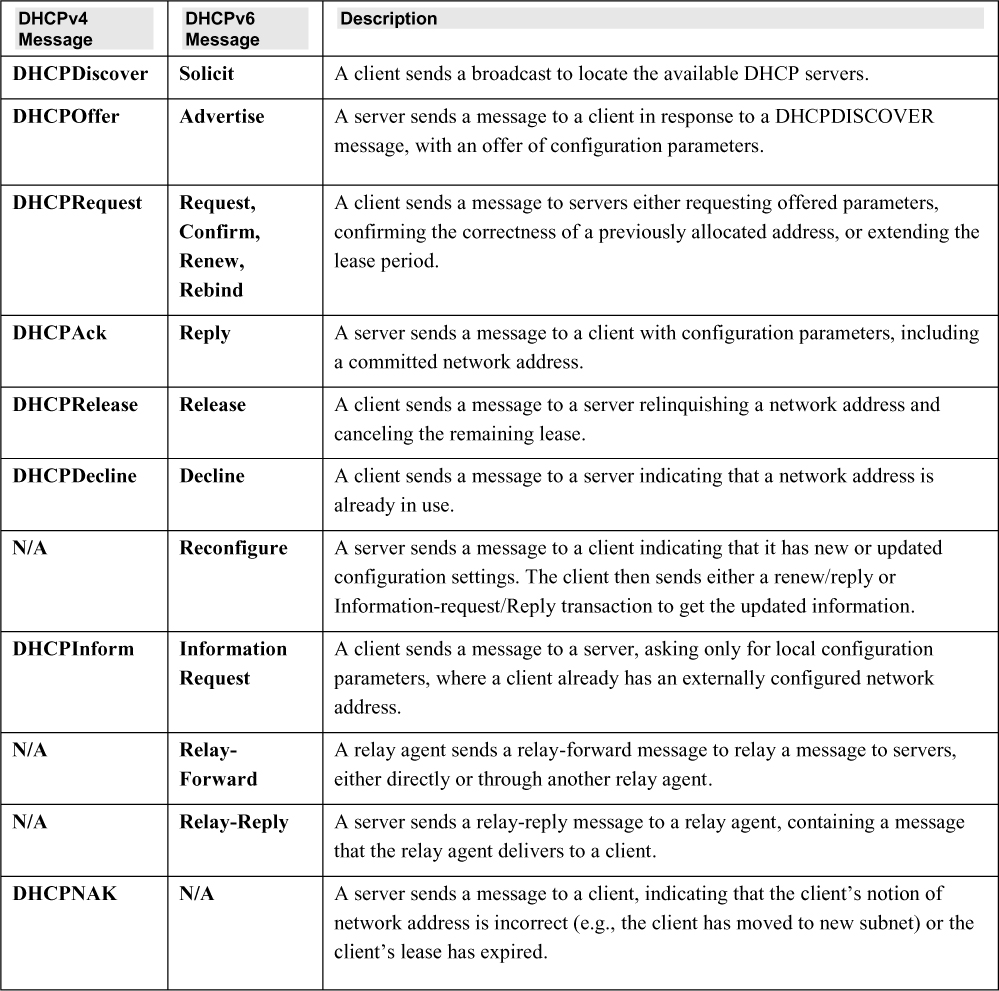
Dynamic Host Configuration Protocol (DHCP) is a network management protocol that assigns an IP address automatically when a client connects to a network. A DHCP server has a pool of IP addresses available for use. Each computer that logs on to the network is temporarily assigned an address from the pool. The address is released after a period of time and may then be issued to another computer. The specific steps are listed here:
1. The client broadcasts a DHCPDISCOVER/SOLICIT request, asking for DHCP configuration information.
2. A DHCP relay agent captures the client request and unicasts it to the DHCP servers available in the network.
3. The DHCP server unicasts a DHCPOFFER/ADVERTISE message that contains the client’s and server’s MAC addresses.
4. The relay agent broadcasts a DHCPOFFER/ADVERTISE message in the client’s subnet.
5. A client broadcasts a DHCPREQUEST/REQUEST message, asking the DHCP server to provide the DHCP configuration information.
6. The DHCP server sends a unicast DHCPACK/REPLY message to the client with the IP configuration information.
DHCP messages for IPv4 and IPv6 are shown in Table 5.2.
Table 5.2 DHCP Messages
DNS (Domain Name System) translates domains to IP addresses. At the local network segment, another protocol is used. ARP (Address Resolution Protocol) translates IP addresses into MAC addresses at the switch level. When one machine needs to communicate with another, it looks up its ARP table. If the MAC address is not found in the table, an ARP_REQUEST message is broadcast over the network. All machines on the network then compare this IP address to their MAC address. If one of the machines in the network identifies with this address, it responds to the ARP_REQUEST message with its IP and MAC addresses. The requesting machine stores the address pair in the ARP table and begins communicating with the sender.
Active Attack Techniques
There are a number of active techniques that attackers can use. Some of them are used to improve packet sniffing. Others can facilitate additional attacks. We examine common active attack techniques in this section.
MAC Flooding
MAC flooding involves flooding the CAM table with fake MAC address/IP address pairs until the table is full. This forces the switch to then work like a hub, simply blasting all traffic out all ports (because it cannot look up routes in the CAM table) and making it easy to sniff all traffic. There are tools for this. For example, macof is a part of the dsniff suite of tools. macof creates and sends random MAC address/IP address pairs. The Linux man (manual) page for macof can be found at https://linux.die.net/man/8/macof. You can see macof in use in Figure 5.8.

Figure 5.8 macof
Switch port stealing is a technique that begins with MAC flooding. The target is flooded with packets that have the target MAC address as source and the attacker’s MAC address as destination. This causes the switch to try to change its MAC address binding. If the flood is sufficient in size and speed, the attacker can direct all packets intended for the switch to the attacker's machine.
Depending on what switch you use, there are different ways to defend against MAC attacks. The CEH exam is rather Cisco-centric and won’t ask you about Juniper devices. Some Cisco commands that can be used to mitigate or prevent MAC attacks are shown here:
• switchport port-security
• switchport port-security maximum 1 vlan access
• switchport port-security violation restrict
• switchport port-security aging time 2
• switchport port-security aging type inactivity
• snmp-server enable traps port-security trap-rate 5
ExamAlert
Objective The CEH exam has been including more and more Cisco questions. Make sure you are familiar with them.
DHCP Starvation
DHCP starvation is an attack in which the attacker sends forged DHCP requests in an attempt to take up all the available IP addresses in the pool. There are many tools, often called gobblers, that can automate this process. Some are listed here:
• Hyenae: https://sourceforge.net/projects/hyenae/
• dhcpstarv: http://dhcpstarv.sourceforge.net
• The Gobbler: http://gobbler.sourceforge.net
• DHCPig: https://github.com/kamorin/DHCPig
• Yersinia: https://tools.kali.org/vulnerability-analysis/yersinia
Related to DHCP starvation is the rogue DHCP server attack. With this type of attack, the attacker often starts with DHCP starvation and then attempts to get the user to connect to the rogue DHCP server. There are countermeasures to such attacks. And again, the CEH exam is Cisco-centric and does not ask about Juniper devices. Some Cisco commands that can assist in mitigating these attacks are listed here:
• switchport port-security
• switchport port-security maximum 1
• switchport port-security violation restrict
• switchport port-security aging time 2
• switchport port-security aging type inactivity
• switchport port-security mac-address sticky
• no ip dhcp snooping information option
• ip dhcp snooping
ARP Poisoning/Spoofing
In ARP spoofing, the attacker creates a large number of forged ARP request and reply packages in an attempt to overwhelm the target switch. Once the ARP table is flooded, the switch changes to forwarding mode, and the attacker can sniff all packets on the network. As you have probably guessed, there are quite a few tools that can automate this process. These are a few of them:
• BetterCAP: https://www.bettercap.org
• Ettercap: https://www.ettercap-project.org
• ArpSpoofTool: https://github.com/ickerwx/arpspoof
• MITMf: https://github.com/byt3bl33d3r/MITMf
• Cain & Abel: https://www.darknet.org.uk/2007/01/cain-and-abel-download-windows-password-cracker/
In addition, there are some Cisco router/switch commands that can help you defend against ARP poisoning attacks. Setting up ARP inspection is the best way for Cisco to defend against ARP attacks (e.g., ip arp inspection vlan 10). There are also tools that can help thwart these attacks. A few are listed here:
• ARP AntiSpoofer: https://sourceforge.net/projects/arpantispoofer/
• ARPStraw: https://github.com/he2ss/arpstraw
• ArpON: https://arpon.sourceforge.io
MAC Spoofing
MAC spoofing is a common attack type. It can be done to either connect to a secure port or simply to hide the attacker’s identity. This type of attack is actually rather easy in Windows 10.
To change a Windows machine’s MAC address, search the machine for Network Connections, and you will see a screen with all of your network adapters. Right-click on the adapter you are interested in and choose Properties. Then click the Configure button and navigate to the Advanced tab. You can then change the network address, as shown in Figure 5.9.

Figure 5.9 Changing a MAC Address in Windows 10
Alternatively, you can do this in the Windows registry editor. It is recommended that you search for regedt32, but the older regedit also works. Then you go to the key HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlClass{4d36e972-e325-11ce-bfc1-08002be10318}. (Yes, that last part will be the same on your machine.) You hen see all of your network adapters represented by the numbers 0000, 0001, 0002, and so on. If you look at the DriverDesc subkey, you will see a user-friendly name that helps you identify the right network adapter. Then find the network address and change it. You need to disable and reenable that adapter in order for the change to take place.
As you have probably guessed, there are also tools to help with MAC spoofing:
• MAC Address Changer: https://technitium.com/tmac/
• Spoof-Me-Now: https://sourceforge.net/projects/spoof-me-now/
• SMAC: https://www.klcconsulting.net/smac/
• Technitium: https://technitium.com/tmac/
• Smart DNS Changer: https://www.downloadcrew.com/article/32320-smart_dns_changer
Technitium is shown in Figure 5.10. As you can see, it is a very easy-to-use GUI that makes MAC spoofing a simple issue.
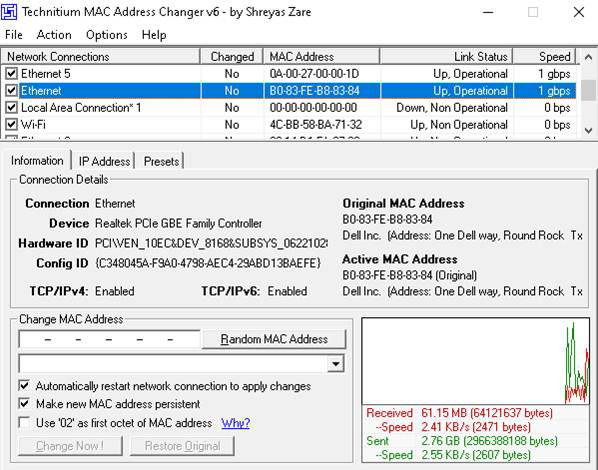
Figure 5.10 Technitium MAC Spoofer
IRDP Spoofing
IRDP spoofing is another type of attack. ICMP Router Discovery Protocol (IRDP) is a routing protocol that allows a host to discover the IP addresses of active routers on a subnet by listening to router advertisement and soliciting messages on the network. In this type of attack, the attacker sends spoofed IRDP router advertisement message to the host on the subnet, causing it to change its default router to whatever the attacker chooses. This allows the attacker to sniff all traffic.
DNS Poisoning
DNS spoofing can be done in many different ways. DNS poisoning, also known as DNS cache poisoning, involves tricking a DNS server into believing it has received authentic information when, in reality, it has not. Once the DNS server has been poisoned, the information is generally cached for a while, spreading the effect of the attack to the users of the server.
Another form of DNS spoofing involves an attacker running their own domain (e.g., mydomain.com) with their own hacked DNS server (e.g., ns.mydomain.com). The attacker sends a request to your DNS server, asking it to resolve www.mydomain.com. Since the DNS server is not aware of this machine’s IP address, and it doesn't belong to your domain, the server needs to ask some other DNS servers. So, it tries to find that domain by asking other DNS server.
The hacked DNS server replies to your DNS server, and at the same time, it gives all its records (including “poisoned records”).
There are several methods for defending against DNS poisoning. Some of them are listed here:
• Configure a DNS resolver to use a new random source port for each outgoing query.
• Resolve all DNS queries to the local DNS server.
• Implement Domain Name System Security Extension (DNSSEC).
• Use DNS Non-Existent Domain (NXDOMAIN) rate limiting.
• Do not allow outgoing traffic to use UDP port 53 as a default source port.
• Audit the DNS server regularly to remove vulnerabilities.
Protocol Scanning
It is possible to scan networks for various services in order to gather network information. SMB (Server Message Block) scanning, as mentioned in Chapter 3, “System Hacking,” can enumerate Windows machines on a network. You also saw in Chapter 3 how to use Metasploit to scan for SMB information.
SMB is not the only protocol that provides information about a target system. NFS (Network File System), which was developed by Sun Microsystems, allows access to network resources. NFS is supported on UNIX, Windows, macOS, and many other systems.
BGP (Border Gateway Protocol) enables gateway routers to share router information. By sniffing BGP traffic, you can enumerate resources on a given network. Given that the entire purpose of BGP is to share routing information, it is usually quite easy to capture such data in transit.
ExamAlert
Objective As you prepare for the CEH exam, make certain you are very familiar with all of these active attack techniques.
What Next?
If you want more practice on this chapter's exam objectives before you move on, remember that you can access all of the Cram Quiz questions on the book web page. The next chapter covers denial of service attacks and session hijacking.
