Compliance Assessment Throughout the IT Infrastructure
The results of a compliance assessment should clearly address whether specific requirements are met. For example, consider the following:
Compliant—This indicates that there is enough credible evidence to show that a particular requirement has been met.
Noncompliant—This indicates that enough credible evidence was collected to show that policies were not adequately followed.
Not determined—This indicates that not enough evidence was collected to make an appropriate compliance determination.
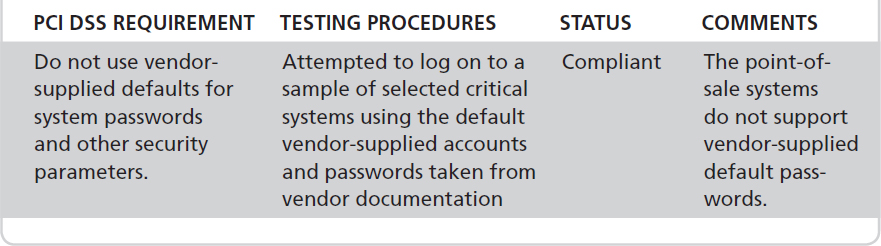
The testing procedures used should be documented. This should also include comments regarding the determination. For example, consider compliance with the Payment Card Industry Data Security Standard (PCI DSS). PCI DSS requires that vendor-supplied default passwords be changed before installing a system on the network. The report would include this along with the other requirements followed by the corresponding testing procedures and results. Table 7-8 provides an example of the documented results for this requirement.
TABLE 7-8 A sample documented PCI DSS compliance test result.